STP Limited: Networking and Communication Project for Business Growth
VerifiedAdded on 2020/03/16
|22
|6029
|449
Project
AI Summary
This project report focuses on STP Limited, an Australian company expanding its services. It analyzes the company's networking and communication requirements, including project background, scope, objectives, and strategic alignment. The report covers network, data, and mobile security, along with risk management strategies, business continuity plans, and hardware purchase recommendations. It details security solutions for branch offices, data security measures, and the security of mobile devices. Furthermore, it outlines a comprehensive risk management strategy, including identification, assessment, and treatment methods. The report concludes with recommendations for improving STP Limited's network infrastructure and communication channels, aiming to enhance customer service and business operations. The goal is to create a secure, efficient, and integrated network across all four office locations, improving information sharing and streamlining processes. The project emphasizes the use of advanced networking protocols, security measures, and the importance of adapting to evolving security threats.

STP Limited
Networking & Communication Project
10/11/2017
Networking & Communication Project
10/11/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STP Limited
Table of Contents
Overview.....................................................................................................................................................3
Background of the Project...........................................................................................................................3
Scope of the Project.................................................................................................................................4
Goals and Objectives...............................................................................................................................4
Strategic Alignment.................................................................................................................................4
Management and Security of the Networks.................................................................................................7
Security Solutions: Branch Office...........................................................................................................8
Data Security...........................................................................................................................................9
Security of Mobile Devices...................................................................................................................10
Plan to be Used for Hardware Purchases...................................................................................................11
Business Continuity...................................................................................................................................12
Risk Management......................................................................................................................................13
Strategy.................................................................................................................................................13
Identification.....................................................................................................................................13
Responsibilities and Accountability...................................................................................................13
Assessment and Analysis...................................................................................................................14
Suitable Strategy................................................................................................................................17
Treatment Methods............................................................................................................................17
Monitoring, Tracking and Review.....................................................................................................17
Conclusions...............................................................................................................................................17
Recommendations & Evaluations..............................................................................................................18
References.................................................................................................................................................20
2
Table of Contents
Overview.....................................................................................................................................................3
Background of the Project...........................................................................................................................3
Scope of the Project.................................................................................................................................4
Goals and Objectives...............................................................................................................................4
Strategic Alignment.................................................................................................................................4
Management and Security of the Networks.................................................................................................7
Security Solutions: Branch Office...........................................................................................................8
Data Security...........................................................................................................................................9
Security of Mobile Devices...................................................................................................................10
Plan to be Used for Hardware Purchases...................................................................................................11
Business Continuity...................................................................................................................................12
Risk Management......................................................................................................................................13
Strategy.................................................................................................................................................13
Identification.....................................................................................................................................13
Responsibilities and Accountability...................................................................................................13
Assessment and Analysis...................................................................................................................14
Suitable Strategy................................................................................................................................17
Treatment Methods............................................................................................................................17
Monitoring, Tracking and Review.....................................................................................................17
Conclusions...............................................................................................................................................17
Recommendations & Evaluations..............................................................................................................18
References.................................................................................................................................................20
2

STP Limited
Executive Summary
STP Limited is an Australian company that is expanding to include new set of services and
operations. The company has decided to improve its networking and communication mediums
that are being used.
The report has been prepared to analyze and understand the associated networking and
communication requirements along with the various details. The report covers the project
background, scope, objectives and strategic alignment. Analysis of network, data and mobile
security along with risk management strategy, business continuity steps and plan for hardware
purchase has been covered as well.
3
Executive Summary
STP Limited is an Australian company that is expanding to include new set of services and
operations. The company has decided to improve its networking and communication mediums
that are being used.
The report has been prepared to analyze and understand the associated networking and
communication requirements along with the various details. The report covers the project
background, scope, objectives and strategic alignment. Analysis of network, data and mobile
security along with risk management strategy, business continuity steps and plan for hardware
purchase has been covered as well.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STP Limited
Overview
STP Limited is an Australian manufacturer of cabinets and these cabinets are made in a factory
that is owned by the company. The headquarters of the company are located in Wollongong and
there are three other office locations as well in Sydney, Bathurst and Lithgow. The most recent
out of all is the office that is located in Sydney and there are computerized mechanisms in place
in this office for the manufacturing of cupboard and drawer fronts. Some clients have the
capability to install these fronts on their own while other needs them to be installed by the
company representatives. It is being considered to make use of vans for the purpose of
installation which may be owned by the company or another franchise. With the current office
arrangements and infrastructure, the recent expansion of the office and business activities can no
longer be managed correctly. There are many changes that are being done in the organization in
terms of the implementation of the website, updates in the information system, new customer
management and accounting system along with improved stock control system. There are
distributed databases that are used in STP Limited. The organization is now looking to work
upon the improvement in its networking and communication channel.
Background of the Project
The company is working on the initiatives to enhance its network architecture and the
communication framework that is followed. There are a number of tools and new techniques that
are already in place in terms of the networking architecture of the company. There are a lot many
tools, gadgets and equipment that are being used and are present in the company in all of its
office locations. All the four office locations are connected and equipped with the Internet
through the ADSL connection. The company has also implemented the Bring Your Own Devices
(BYOD) strategy and scheme in the organization which provides the permission to the
employees to carry and use their personally owned devices for the fulfillment and execution of
the organizational activities.
Communication is the key to the success of the projects and the organizations. It is necessary for
STP Limited to ensure that the internal and external stakeholders associated with the company
are offered updated details and enhanced information sharing at any hour of the day. With the
4
Overview
STP Limited is an Australian manufacturer of cabinets and these cabinets are made in a factory
that is owned by the company. The headquarters of the company are located in Wollongong and
there are three other office locations as well in Sydney, Bathurst and Lithgow. The most recent
out of all is the office that is located in Sydney and there are computerized mechanisms in place
in this office for the manufacturing of cupboard and drawer fronts. Some clients have the
capability to install these fronts on their own while other needs them to be installed by the
company representatives. It is being considered to make use of vans for the purpose of
installation which may be owned by the company or another franchise. With the current office
arrangements and infrastructure, the recent expansion of the office and business activities can no
longer be managed correctly. There are many changes that are being done in the organization in
terms of the implementation of the website, updates in the information system, new customer
management and accounting system along with improved stock control system. There are
distributed databases that are used in STP Limited. The organization is now looking to work
upon the improvement in its networking and communication channel.
Background of the Project
The company is working on the initiatives to enhance its network architecture and the
communication framework that is followed. There are a number of tools and new techniques that
are already in place in terms of the networking architecture of the company. There are a lot many
tools, gadgets and equipment that are being used and are present in the company in all of its
office locations. All the four office locations are connected and equipped with the Internet
through the ADSL connection. The company has also implemented the Bring Your Own Devices
(BYOD) strategy and scheme in the organization which provides the permission to the
employees to carry and use their personally owned devices for the fulfillment and execution of
the organizational activities.
Communication is the key to the success of the projects and the organizations. It is necessary for
STP Limited to ensure that the internal and external stakeholders associated with the company
are offered updated details and enhanced information sharing at any hour of the day. With the
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STP Limited
advancements that will be done in regards to the communication framework, there will be a
number of advantages that will be offered to the company. These benefits will be in the form of
enhanced information sharing and streamlining of the process of information management. The
customers always look for the organizations that may provide them with the details on services
being provided at a non-stop basis and the ones that are readily available for the resolution of the
queries1.
Scope of the Project
The scope of the project that will be implemented for STP Limited will include the activities and
phases that will assist the deployment of the advanced networking and communication channel.
The requirements that are associated with the networks and communication systems shall be
analyzed so that the upgrades and modifications that need to be done are highlighted. The
planning shall then be carried out in terms of the networking design and architecture and the
changes to be developed. The network integration and compatibility checks, implementation and
testing will come under the scope of the project.
Goals and Objectives
Advanced and assured integration of the four locations and all of the warehouses of the
company as a single unit in terms of the execution of operations and information
management.
Setting up of the security of the networks and communication mediums that are designed
to make sure that the information and communication channels are secured and
protected2.
Improvement in the quality and cohesiveness of the services that are provided to the
customers.
Increase in the levels of the customer satisfaction and customer engagement with the
company.
1 Cisco, "Wireless and Network Security Integration Solution Overview", in , , 2008,
<https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Mobility/secwlandg20/
sec_wireless_overview.pdf> [accessed 11 October 2017].
2 R Pareek, "Network Security: An Approach towards Secure Computing", in , , 2011, <https://www.rroij.com/open-
access/network-security-an-approach-towards-secure-computing-160-163.pdf> [accessed 11 October 2017].
5
advancements that will be done in regards to the communication framework, there will be a
number of advantages that will be offered to the company. These benefits will be in the form of
enhanced information sharing and streamlining of the process of information management. The
customers always look for the organizations that may provide them with the details on services
being provided at a non-stop basis and the ones that are readily available for the resolution of the
queries1.
Scope of the Project
The scope of the project that will be implemented for STP Limited will include the activities and
phases that will assist the deployment of the advanced networking and communication channel.
The requirements that are associated with the networks and communication systems shall be
analyzed so that the upgrades and modifications that need to be done are highlighted. The
planning shall then be carried out in terms of the networking design and architecture and the
changes to be developed. The network integration and compatibility checks, implementation and
testing will come under the scope of the project.
Goals and Objectives
Advanced and assured integration of the four locations and all of the warehouses of the
company as a single unit in terms of the execution of operations and information
management.
Setting up of the security of the networks and communication mediums that are designed
to make sure that the information and communication channels are secured and
protected2.
Improvement in the quality and cohesiveness of the services that are provided to the
customers.
Increase in the levels of the customer satisfaction and customer engagement with the
company.
1 Cisco, "Wireless and Network Security Integration Solution Overview", in , , 2008,
<https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Mobility/secwlandg20/
sec_wireless_overview.pdf> [accessed 11 October 2017].
2 R Pareek, "Network Security: An Approach towards Secure Computing", in , , 2011, <https://www.rroij.com/open-
access/network-security-an-approach-towards-secure-computing-160-163.pdf> [accessed 11 October 2017].
5
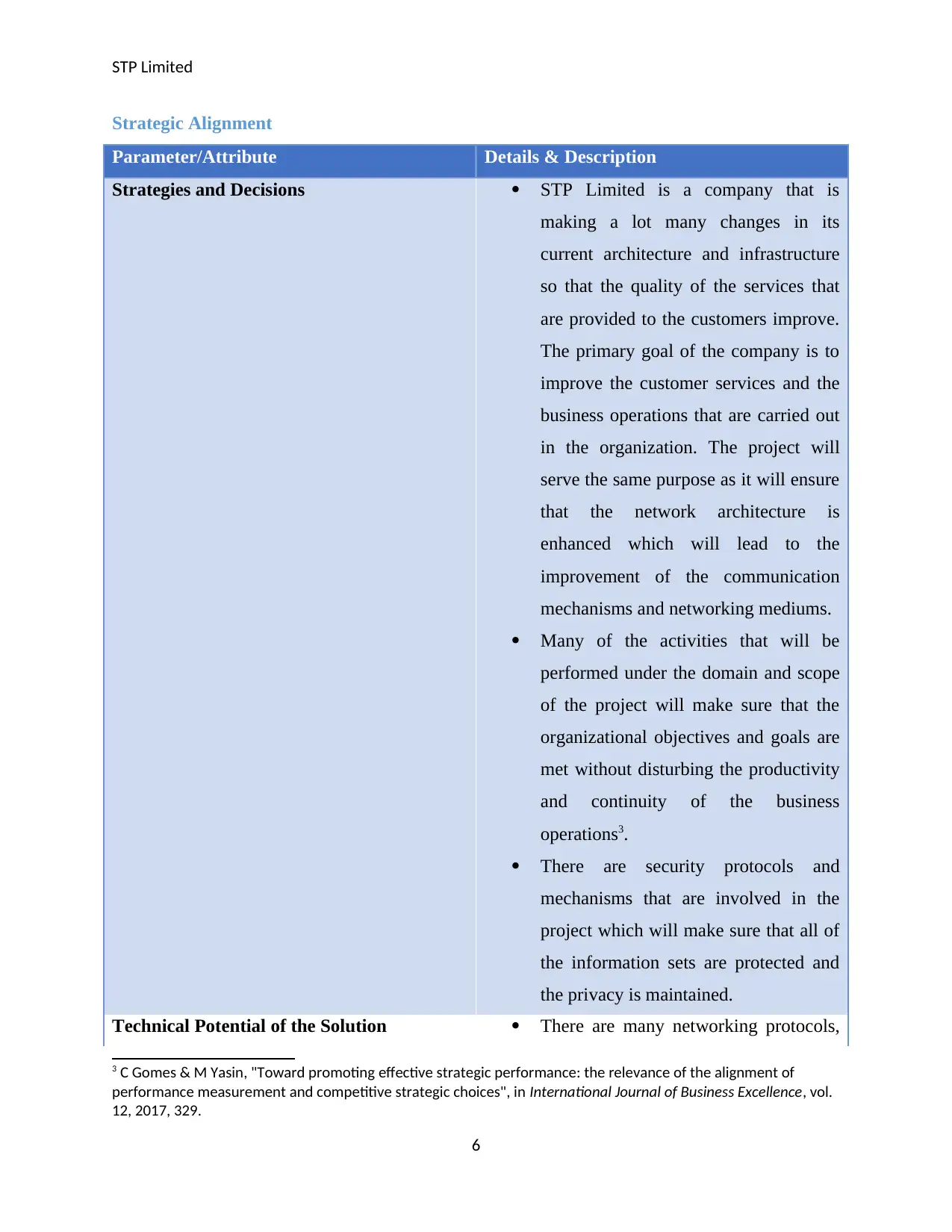
STP Limited
Strategic Alignment
Parameter/Attribute Details & Description
Strategies and Decisions STP Limited is a company that is
making a lot many changes in its
current architecture and infrastructure
so that the quality of the services that
are provided to the customers improve.
The primary goal of the company is to
improve the customer services and the
business operations that are carried out
in the organization. The project will
serve the same purpose as it will ensure
that the network architecture is
enhanced which will lead to the
improvement of the communication
mechanisms and networking mediums.
Many of the activities that will be
performed under the domain and scope
of the project will make sure that the
organizational objectives and goals are
met without disturbing the productivity
and continuity of the business
operations3.
There are security protocols and
mechanisms that are involved in the
project which will make sure that all of
the information sets are protected and
the privacy is maintained.
Technical Potential of the Solution There are many networking protocols,
3 C Gomes & M Yasin, "Toward promoting effective strategic performance: the relevance of the alignment of
performance measurement and competitive strategic choices", in International Journal of Business Excellence, vol.
12, 2017, 329.
6
Strategic Alignment
Parameter/Attribute Details & Description
Strategies and Decisions STP Limited is a company that is
making a lot many changes in its
current architecture and infrastructure
so that the quality of the services that
are provided to the customers improve.
The primary goal of the company is to
improve the customer services and the
business operations that are carried out
in the organization. The project will
serve the same purpose as it will ensure
that the network architecture is
enhanced which will lead to the
improvement of the communication
mechanisms and networking mediums.
Many of the activities that will be
performed under the domain and scope
of the project will make sure that the
organizational objectives and goals are
met without disturbing the productivity
and continuity of the business
operations3.
There are security protocols and
mechanisms that are involved in the
project which will make sure that all of
the information sets are protected and
the privacy is maintained.
Technical Potential of the Solution There are many networking protocols,
3 C Gomes & M Yasin, "Toward promoting effective strategic performance: the relevance of the alignment of
performance measurement and competitive strategic choices", in International Journal of Business Excellence, vol.
12, 2017, 329.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STP Limited
devices, gadgets and equipment that
will be launched to be used in the four
office locations of STP Limited. These
components will be based on the latest
security and technical aspects and there
will not be any issues around
compatibility of these components with
other tools.
The project will be feasible from the
technical point of view as it would be
compatible with the rest of the tools
and there will be enhanced integration
that will be involved.
Competitive Gains The organizations and firms that are
ahead of their competitors in terms of
the use of technology gain an edge in
the market and among the customers.
The same will happen in the case of
STP Limited with the use and
implementation of latest networking
practices4.
The quality and the performance of the
business operations and activities will
improve. This will lead to the better
operational continuity along with the
better satisfaction of the customers.
Service Level The management resources and the
senior leadership that is associated with
STP Limited will decide upon the
approach and methodology that shall be
4 T Chi, "Alignment between business environment characteristics, competitive priorities, supply chain structures,
and firm business performance", in Strategic Direction, vol. 26, 2010.
7
devices, gadgets and equipment that
will be launched to be used in the four
office locations of STP Limited. These
components will be based on the latest
security and technical aspects and there
will not be any issues around
compatibility of these components with
other tools.
The project will be feasible from the
technical point of view as it would be
compatible with the rest of the tools
and there will be enhanced integration
that will be involved.
Competitive Gains The organizations and firms that are
ahead of their competitors in terms of
the use of technology gain an edge in
the market and among the customers.
The same will happen in the case of
STP Limited with the use and
implementation of latest networking
practices4.
The quality and the performance of the
business operations and activities will
improve. This will lead to the better
operational continuity along with the
better satisfaction of the customers.
Service Level The management resources and the
senior leadership that is associated with
STP Limited will decide upon the
approach and methodology that shall be
4 T Chi, "Alignment between business environment characteristics, competitive priorities, supply chain structures,
and firm business performance", in Strategic Direction, vol. 26, 2010.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STP Limited
used in the project. It will ensure that
the project goals and the service
excellence are achieved.
The resources that will be used in the
project will be allocated as per their
skills and knowledge. An analysis of
their skill sets will be done which
would make sure that the project tasks
are successfully completed.
Management and Security of the Networks
There are many risks and security attacks that may take place in association with the networks.
This has led to the development of a discipline called Network Security. This has become one of
the integral parts of the organizations so that the security of the organizational networks can be
ensured. With the use of different types of networks along with the increase in the number of
networks involved, the likelihood of the network attacks has also increased.
There are many activities that are carried out in STP Limited. This has led to the setting up of
different teams and departments. There is also the presence of local IT support and services
department for the reporting and resolution of the IT related incidents. The management must
analyze and make sure that there are enough resources present in this department for the easy and
smooth execution of the services5. There are technologies that have been developed that shall be
used for remotely managing the support and maintenance tasks. Enhanced form of control and
monitoring shall be carried out by network administrators and managers along with the security
team to keep a track of all the technical and operational issues for their avoidance and
prevention.
With the increase in the frequency of the security risks and attacks, there are many different
protocols that have been developed and implemented in the company. The use of web and cloud
computing is also necessary in the current times. To avoid the associated risks, the company
5 R Sampangi, "A Security Suite for Wireless Body Area Networks", in International Journal of Network Security & Its
Applications, vol. 4, 2012, 97-116.
8
used in the project. It will ensure that
the project goals and the service
excellence are achieved.
The resources that will be used in the
project will be allocated as per their
skills and knowledge. An analysis of
their skill sets will be done which
would make sure that the project tasks
are successfully completed.
Management and Security of the Networks
There are many risks and security attacks that may take place in association with the networks.
This has led to the development of a discipline called Network Security. This has become one of
the integral parts of the organizations so that the security of the organizational networks can be
ensured. With the use of different types of networks along with the increase in the number of
networks involved, the likelihood of the network attacks has also increased.
There are many activities that are carried out in STP Limited. This has led to the setting up of
different teams and departments. There is also the presence of local IT support and services
department for the reporting and resolution of the IT related incidents. The management must
analyze and make sure that there are enough resources present in this department for the easy and
smooth execution of the services5. There are technologies that have been developed that shall be
used for remotely managing the support and maintenance tasks. Enhanced form of control and
monitoring shall be carried out by network administrators and managers along with the security
team to keep a track of all the technical and operational issues for their avoidance and
prevention.
With the increase in the frequency of the security risks and attacks, there are many different
protocols that have been developed and implemented in the company. The use of web and cloud
computing is also necessary in the current times. To avoid the associated risks, the company
5 R Sampangi, "A Security Suite for Wireless Body Area Networks", in International Journal of Network Security & Its
Applications, vol. 4, 2012, 97-116.
8

STP Limited
makes use of secure HTTP, Server Socket Layer (SSL) and many other protocols for the security
of the network and transport layers.
The offices of STP Limited are located and have been set up in four different locations. It is
important to ensure that the security of the offices and the information sets that are associated
with each office are maintained and protected. Due to this reason, an integrated networking
scheme is required to be implemented so that the network security and the tracking of network
activities become easier and easy to implement.
Secure routing is also one of the prime necessities of the networks and networking operations
that are carried out in the organization. With the aid of this practice, the data packets that will be
transferred from one location to the other will be done securely and with enhanced for of
protection as well. This will also eliminate nay necessity to install the security tools and gadgets
separately for all the four locations.
The types of the network security attacks are not constant. There are newer forms of network
security attacks and risks that are being created and launched by the attackers. Also, there are
many changes that are being done in the form of the existing security attacks. Due to the
changing form of the threats that are involved, it is very essential to ensure that the controls that
are implemented are not static. Currently, the controls that are being used are signature based in
nature. These controls do not have the potential to manage and track the threats that are not
known in advance6.
It is, therefore, required that the controls are developed and implemented in such a manner that
they are reactive in nature. These controls shall have the ability to handle the dynamic nature of
the threats and shall be ad-hoc so that the changes in terms of the type of the threats are handled
carefully and correctly.
Security Solutions: Branch Office
STP Limited has its branch office that is located in Wollongong. There are many security
controls and threats that are associated with the branch office and there are security controls that
shall be implemented in the branch office as listed below.
6 J Canavan, "Fundamentals of Network Security", in , , 2001, <https://whc.es/Network/Fundamentals%20of
%20Network%20Security.pdf.1.pdf> [accessed 11 October 2017].
9
makes use of secure HTTP, Server Socket Layer (SSL) and many other protocols for the security
of the network and transport layers.
The offices of STP Limited are located and have been set up in four different locations. It is
important to ensure that the security of the offices and the information sets that are associated
with each office are maintained and protected. Due to this reason, an integrated networking
scheme is required to be implemented so that the network security and the tracking of network
activities become easier and easy to implement.
Secure routing is also one of the prime necessities of the networks and networking operations
that are carried out in the organization. With the aid of this practice, the data packets that will be
transferred from one location to the other will be done securely and with enhanced for of
protection as well. This will also eliminate nay necessity to install the security tools and gadgets
separately for all the four locations.
The types of the network security attacks are not constant. There are newer forms of network
security attacks and risks that are being created and launched by the attackers. Also, there are
many changes that are being done in the form of the existing security attacks. Due to the
changing form of the threats that are involved, it is very essential to ensure that the controls that
are implemented are not static. Currently, the controls that are being used are signature based in
nature. These controls do not have the potential to manage and track the threats that are not
known in advance6.
It is, therefore, required that the controls are developed and implemented in such a manner that
they are reactive in nature. These controls shall have the ability to handle the dynamic nature of
the threats and shall be ad-hoc so that the changes in terms of the type of the threats are handled
carefully and correctly.
Security Solutions: Branch Office
STP Limited has its branch office that is located in Wollongong. There are many security
controls and threats that are associated with the branch office and there are security controls that
shall be implemented in the branch office as listed below.
6 J Canavan, "Fundamentals of Network Security", in , , 2001, <https://whc.es/Network/Fundamentals%20of
%20Network%20Security.pdf.1.pdf> [accessed 11 October 2017].
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STP Limited
Virtual Private Networks (VPNs) shall be used in case of the branch office. This will
improve the end to end connectivity and security of the branch office and all the entities
connected with the branch office. The security of the overall office and the business
activities will be improved with the aid of the VPN connections.
The use of internet connection is a necessity in every sector and organization. The same
is the case with STP Limited. The security of these connections shall be improved and
enhanced with the aid of the security tools and protocols at the internet layer.
The set of the services that are associated with the company can be divided in different
types, such as, internal activities, core services and external activities. All of the core
services are carried out in the branch office. The security of these services shall be
improved by making use of logical and administrative controls7.
It is necessary to make sure that all the information sets that are present in the application
are secure and the reliability of the operations is also ensured.
Data Security
Virtual Private Networks shall be used in case of the branch office. This will improve the
end to end connectivity and security of the branch office and all the entities connected
with the branch office. The security of the overall office and the business activities will
be improved with the aid of the VPN connections8.
Encryption is one of the most important and necessary aspects that are involved and
associated with the information and data sets. There are many encryption algorithms that
are present which shall be used in case of STP Limited. Some of these encryption
protocols include advanced encryption and triple DES.
Firewalls are being used since a long period of time. These are the data security controls
which are normally installed at the network layer to verify the authenticity of the traffic
and to grant permission only to the traffic that is passed on these authentication checks.
However, the installation of the firewalls only at the network layer is not sufficient from
7 S Alabady, "Design and Implementation of a Network Security Model for Cooperative Network.", in , , 2009,
<http://www.iajet.org/iajet_files/vol.1/no.2/Design%20and%20Implementation%20of%20a%20Network
%20Security%20Model%20for%20Cooperative%20Network.pdf> [accessed 11 October 2017].
8 M Joshi & R Karkade, "Network Security with Cryptography", in , , 2015,
<http://www.ijcsmc.com/docs/papers/January2015/V4I1201544.pdf> [accessed 11 October 2017].
10
Virtual Private Networks (VPNs) shall be used in case of the branch office. This will
improve the end to end connectivity and security of the branch office and all the entities
connected with the branch office. The security of the overall office and the business
activities will be improved with the aid of the VPN connections.
The use of internet connection is a necessity in every sector and organization. The same
is the case with STP Limited. The security of these connections shall be improved and
enhanced with the aid of the security tools and protocols at the internet layer.
The set of the services that are associated with the company can be divided in different
types, such as, internal activities, core services and external activities. All of the core
services are carried out in the branch office. The security of these services shall be
improved by making use of logical and administrative controls7.
It is necessary to make sure that all the information sets that are present in the application
are secure and the reliability of the operations is also ensured.
Data Security
Virtual Private Networks shall be used in case of the branch office. This will improve the
end to end connectivity and security of the branch office and all the entities connected
with the branch office. The security of the overall office and the business activities will
be improved with the aid of the VPN connections8.
Encryption is one of the most important and necessary aspects that are involved and
associated with the information and data sets. There are many encryption algorithms that
are present which shall be used in case of STP Limited. Some of these encryption
protocols include advanced encryption and triple DES.
Firewalls are being used since a long period of time. These are the data security controls
which are normally installed at the network layer to verify the authenticity of the traffic
and to grant permission only to the traffic that is passed on these authentication checks.
However, the installation of the firewalls only at the network layer is not sufficient from
7 S Alabady, "Design and Implementation of a Network Security Model for Cooperative Network.", in , , 2009,
<http://www.iajet.org/iajet_files/vol.1/no.2/Design%20and%20Implementation%20of%20a%20Network
%20Security%20Model%20for%20Cooperative%20Network.pdf> [accessed 11 October 2017].
8 M Joshi & R Karkade, "Network Security with Cryptography", in , , 2015,
<http://www.ijcsmc.com/docs/papers/January2015/V4I1201544.pdf> [accessed 11 October 2017].
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STP Limited
the security point of view. It is required to install firewalls in other layers as well so that
the overall security and access control can be implemented. There are many vendors that
have created and launched their advanced firewalls in the market. These shall be analyzed
and used by STP Limited to make sure that the network security along with data security
is maintained.
The use of firewalls is a basic step and mechanism for the maintenance of security in the
organization. There are many forms of risks and attacks that have been created by the
attackers which cannot be controlled with the use and implementation of firewalls. It is
therefore required to make sure that the advanced access control is used and implemented
with the use of latest network security tools and protocols. Many of the data related
security controls are also present and have been implemented so that the security of the
information sets is maintained9.
Filtering as the name suggests is a security control which is done with a view to filter the
traffic on the basis of clean and suspicious traffic. There is URL and web based filtering
techniques that have been developed for making sure that the unwanted and suspicious
traffic is avoided. There are many Business Intelligence tools that have also been set up
for the same purpose which can be used for the enhancement of the security of the data
sets and the networking mediums10.
The information and data sets that are associated with STP Limited shall be divided and
classified in different categories. These categories shall include the division of the
information as per the type of the information which may include internal data, security
logs, sensitive information, confidential details and likewise. The data security protocols
that are developed shall be done according to these information categories only.
Security of Mobile Devices
Mobile devices are being increasingly used in the business units for the execution and
accomplishment of the business tasks and activities. The use of these devices cannot be ruled out
any longer since they serve many of the business necessities and operations. However, with the
9 M Strebe, "Network Security Foundations", in , , 2004,
<https://imcs.dvfu.ru/lib.int/docs/Networks/Security/Network%20Security%20Foundations.pdf> [accessed 11
October 2017].
10 M Soriano, "Information and Network Security", in , , 2011,
<http://improvet.cvut.cz/project/download/C2EN/Information_and_network_security.pdf> [accessed 11 October
2017].
11
the security point of view. It is required to install firewalls in other layers as well so that
the overall security and access control can be implemented. There are many vendors that
have created and launched their advanced firewalls in the market. These shall be analyzed
and used by STP Limited to make sure that the network security along with data security
is maintained.
The use of firewalls is a basic step and mechanism for the maintenance of security in the
organization. There are many forms of risks and attacks that have been created by the
attackers which cannot be controlled with the use and implementation of firewalls. It is
therefore required to make sure that the advanced access control is used and implemented
with the use of latest network security tools and protocols. Many of the data related
security controls are also present and have been implemented so that the security of the
information sets is maintained9.
Filtering as the name suggests is a security control which is done with a view to filter the
traffic on the basis of clean and suspicious traffic. There is URL and web based filtering
techniques that have been developed for making sure that the unwanted and suspicious
traffic is avoided. There are many Business Intelligence tools that have also been set up
for the same purpose which can be used for the enhancement of the security of the data
sets and the networking mediums10.
The information and data sets that are associated with STP Limited shall be divided and
classified in different categories. These categories shall include the division of the
information as per the type of the information which may include internal data, security
logs, sensitive information, confidential details and likewise. The data security protocols
that are developed shall be done according to these information categories only.
Security of Mobile Devices
Mobile devices are being increasingly used in the business units for the execution and
accomplishment of the business tasks and activities. The use of these devices cannot be ruled out
any longer since they serve many of the business necessities and operations. However, with the
9 M Strebe, "Network Security Foundations", in , , 2004,
<https://imcs.dvfu.ru/lib.int/docs/Networks/Security/Network%20Security%20Foundations.pdf> [accessed 11
October 2017].
10 M Soriano, "Information and Network Security", in , , 2011,
<http://improvet.cvut.cz/project/download/C2EN/Information_and_network_security.pdf> [accessed 11 October
2017].
11

STP Limited
use of the mobile devices, there are many security risks and attacks that take place in terms of the
loss of device, breaching of information that is present in these devices, unauthorized access to
the device, denial of service and malware attacks and many more.
It is necessary to follow certain steps and procedures for maintaining and assuring the safety of
the mobile devices and platforms.
Fingerprinting: This is a technique in which a complete review and analysis of the
mobile device is carried out. In this process, the information on the mobile device type,
the security status of the device, browser and applications being used in the device,
device version and its security scenario and many more information are gathered. This
information is then analyzed from the point of view of the security of the organization or
the party in which the device will be used11.
Network Access Controls: There are many automated tools and applications that have
been developed which may be used for controlling the access to the networks that are
connected with the mobile devices that are connected with STP Limited. These controls
and measures include the use of network based intrusion detection systems that are
equipped with data analytics tools to study the patterns being followed by the intruders.
There are also anti-denial tools and anti-malware tools that are used which can be used
for controlling the access of the networks and the traffic associated with the same.
Authentication: Many new forms of authentication and associated protocols for the
enhancement of security shall be used in case of STP Limited. These authentication
measures shall include the use of multi-fold authentication systems and schemes12.
Plan to be Used for Hardware Purchases
There are many hardware and tools that will be required for the execution of the services and
networking operations in association with STP Limited.
Computer Systems: Computer systems will be required for the occurrence and execution
of many of the project activities. These activities will include integration of the networks
11 M Souppaya, "Guidelines for Managing the Security of Mobile Devices in the Enterprise", in , , 2013,
<http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-124r1.pdf> [accessed 11 October 2017].
12 M Sujithra & G Padmavathi, "Mobile Device Security: A Survey on Mobile Device Threats, Vulnerabilities and
their Defensive Mechanism", in , , 2012, <http://dl.icdst.org/pdfs/files/35dc646a4630971fd27c6b2d32661555.pdf>
[accessed 11 October 2017].
12
use of the mobile devices, there are many security risks and attacks that take place in terms of the
loss of device, breaching of information that is present in these devices, unauthorized access to
the device, denial of service and malware attacks and many more.
It is necessary to follow certain steps and procedures for maintaining and assuring the safety of
the mobile devices and platforms.
Fingerprinting: This is a technique in which a complete review and analysis of the
mobile device is carried out. In this process, the information on the mobile device type,
the security status of the device, browser and applications being used in the device,
device version and its security scenario and many more information are gathered. This
information is then analyzed from the point of view of the security of the organization or
the party in which the device will be used11.
Network Access Controls: There are many automated tools and applications that have
been developed which may be used for controlling the access to the networks that are
connected with the mobile devices that are connected with STP Limited. These controls
and measures include the use of network based intrusion detection systems that are
equipped with data analytics tools to study the patterns being followed by the intruders.
There are also anti-denial tools and anti-malware tools that are used which can be used
for controlling the access of the networks and the traffic associated with the same.
Authentication: Many new forms of authentication and associated protocols for the
enhancement of security shall be used in case of STP Limited. These authentication
measures shall include the use of multi-fold authentication systems and schemes12.
Plan to be Used for Hardware Purchases
There are many hardware and tools that will be required for the execution of the services and
networking operations in association with STP Limited.
Computer Systems: Computer systems will be required for the occurrence and execution
of many of the project activities. These activities will include integration of the networks
11 M Souppaya, "Guidelines for Managing the Security of Mobile Devices in the Enterprise", in , , 2013,
<http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-124r1.pdf> [accessed 11 October 2017].
12 M Sujithra & G Padmavathi, "Mobile Device Security: A Survey on Mobile Device Threats, Vulnerabilities and
their Defensive Mechanism", in , , 2012, <http://dl.icdst.org/pdfs/files/35dc646a4630971fd27c6b2d32661555.pdf>
[accessed 11 October 2017].
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





