University Project: Network Management and Security for STP Limited
VerifiedAdded on 2020/05/11
|14
|3727
|51
Project
AI Summary
This project provides a comprehensive analysis of network management and security for STP Limited, a kitchen cabinet provider with multiple offices. The project explores the background of STP Limited's network, including its expansion to cloud services, and outlines the scope, goals, and strategic alignment of the project. It delves into network security, covering data security measures, people, products, policies, and procedures. It examines ISP security and privacy considerations, as well as the security challenges associated with mobile devices and BYOD risks. Furthermore, the project details a plan for hardware purchases, including acquisition strategies, end-user feedback, and asset register management. It also addresses business continuity planning, including data backup, physical security, and successful planning strategies. Risk management aspects are also included with security policies, training, and technology integration. The project concludes with recommendations and a bibliography, offering a detailed overview of network security and management best practices for STP Limited's business operations and future growth.

Running head: NETWORK MANAGEMENT AND SECURITY
Network Management and Security
Name of the Student
Name of the University
Author’s note
Network Management and Security
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK MANAGEMENT AND SECURITY
Table of Contents
1.0. Project Background.............................................................................................................2
1.1. Network Project Background..........................................................................................2
1.2. Project enhancing the future growth of STP...................................................................2
1.2.1. Project scope............................................................................................................2
1.2.2. Project goal...............................................................................................................3
1.2.3. Strategic alignment of project..................................................................................3
2.0. Network Security................................................................................................................4
2.1. Securing data...................................................................................................................4
2.1.1. People, products, policies and procedures...............................................................4
2.1.2. ISP security and privacy considerations..................................................................4
2.2. Mobile device security....................................................................................................4
2.2.1. Wireless Local Area Network (WLAN) attacks......................................................4
2.2.2. BYOD risks..............................................................................................................5
3. Plan for hardware purchases..................................................................................................5
3.1. Acquisition of new hardware..........................................................................................5
3.2. End-user feedback and reviews.......................................................................................5
3.3. Purchasing strategies.......................................................................................................6
3.4. Asset register...................................................................................................................6
4.0. Business continuity.............................................................................................................7
4.1. Data Backup....................................................................................................................7
4.2. Physical Security.............................................................................................................7
4.3. Successful planning.........................................................................................................8
4.4. Stock Control system......................................................................................................8
5.0. Risk management................................................................................................................8
5.1. Security Policy................................................................................................................9
5.2. Training and awareness...................................................................................................9
5.3. Integration technology....................................................................................................9
6.0. Conclusions.........................................................................................................................9
7.0. Recommendations.............................................................................................................10
8.0. Bibliography......................................................................................................................11
Table of Contents
1.0. Project Background.............................................................................................................2
1.1. Network Project Background..........................................................................................2
1.2. Project enhancing the future growth of STP...................................................................2
1.2.1. Project scope............................................................................................................2
1.2.2. Project goal...............................................................................................................3
1.2.3. Strategic alignment of project..................................................................................3
2.0. Network Security................................................................................................................4
2.1. Securing data...................................................................................................................4
2.1.1. People, products, policies and procedures...............................................................4
2.1.2. ISP security and privacy considerations..................................................................4
2.2. Mobile device security....................................................................................................4
2.2.1. Wireless Local Area Network (WLAN) attacks......................................................4
2.2.2. BYOD risks..............................................................................................................5
3. Plan for hardware purchases..................................................................................................5
3.1. Acquisition of new hardware..........................................................................................5
3.2. End-user feedback and reviews.......................................................................................5
3.3. Purchasing strategies.......................................................................................................6
3.4. Asset register...................................................................................................................6
4.0. Business continuity.............................................................................................................7
4.1. Data Backup....................................................................................................................7
4.2. Physical Security.............................................................................................................7
4.3. Successful planning.........................................................................................................8
4.4. Stock Control system......................................................................................................8
5.0. Risk management................................................................................................................8
5.1. Security Policy................................................................................................................9
5.2. Training and awareness...................................................................................................9
5.3. Integration technology....................................................................................................9
6.0. Conclusions.........................................................................................................................9
7.0. Recommendations.............................................................................................................10
8.0. Bibliography......................................................................................................................11

2NETWORK MANAGEMENT AND SECURITY
1.0. Project Background
1.1. Network Project Background
STP Limited is the kitchen cabinet providers. STP Limited currently has four offices
and those offices are situated in Lithgow, Sydney, Bathurst and Wollongong. The enterprise
is known to manufacture drawer fronts as well as the cupboards to all the consumers based in
Australia. Now they want to scale up their business that is why they have decided to move to
the cloud. STP Limited’s business operations can get embellished with the help of stock
control system as well as the accounting software (Laudon and Laudon 2016). The
organisation has decided that they want to adopt the information system; the information
system is bound to provide them with the benefits by which they can serve the customers
well.
The report has highlighted all the aspects of information technology and along with
that the threats and the vulnerabilities involved with the cloud technology and the information
technology has been raised. The report also states that the staffs of the enterprise must have
the desired technical knowledge to serve the customers and the enterprise as a whole.
1.2. Project enhancing the future growth of STP
1.2.1. Project scope
The Project Scope includes the installation of the database and the system in proper
manner across the four offices in Australia. The Wi-Fi connectivity helps STP Limited to stay
connected all the time to BYOD (Bring Your Own Device). The network connectivity has
been set up in such a way such that the office employees can connect with each other across
the four offices. This can be helpful to know about the stock availability of the company. The
employees must be trained in technical knowledge so that they must be capable to solve the
queries of the customers’ online (Xu et al. 2014). They can solve the technical problems of
1.0. Project Background
1.1. Network Project Background
STP Limited is the kitchen cabinet providers. STP Limited currently has four offices
and those offices are situated in Lithgow, Sydney, Bathurst and Wollongong. The enterprise
is known to manufacture drawer fronts as well as the cupboards to all the consumers based in
Australia. Now they want to scale up their business that is why they have decided to move to
the cloud. STP Limited’s business operations can get embellished with the help of stock
control system as well as the accounting software (Laudon and Laudon 2016). The
organisation has decided that they want to adopt the information system; the information
system is bound to provide them with the benefits by which they can serve the customers
well.
The report has highlighted all the aspects of information technology and along with
that the threats and the vulnerabilities involved with the cloud technology and the information
technology has been raised. The report also states that the staffs of the enterprise must have
the desired technical knowledge to serve the customers and the enterprise as a whole.
1.2. Project enhancing the future growth of STP
1.2.1. Project scope
The Project Scope includes the installation of the database and the system in proper
manner across the four offices in Australia. The Wi-Fi connectivity helps STP Limited to stay
connected all the time to BYOD (Bring Your Own Device). The network connectivity has
been set up in such a way such that the office employees can connect with each other across
the four offices. This can be helpful to know about the stock availability of the company. The
employees must be trained in technical knowledge so that they must be capable to solve the
queries of the customers’ online (Xu et al. 2014). They can solve the technical problems of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK MANAGEMENT AND SECURITY
the customers. Thus it can be said the information service can scale up the business of STP.
The website can be better managed and the web staffs can get benefits due to the technology
advancement and information service management.
1.2.2. Project goal
The project goal is based on the tools and the management staffs, as well as the
employees and the technical staff, must use the tools efficiently for better outcomes, the
network equipment that can furnish the business growth has been elaborated in details
(Beletskaya et al. 2013). The project goal is to facilitate the customer employees’ relation or
the CRM.
1.2.3. Strategic alignment of project
The strategic alignment of the project can be made only on the basis of the SWOT
analysis. The SWOT analysis highlights the threats, strength, opportunities and weakness.
The role of system analyst is to determine all the SWOT analysis aspects and in this way,
STP Limited can be aware of the potential benefits the information system can bring in to
their enterprise (Benner et al. 2014). STP should look upon the weakness and the threats and
should try to mitigate those risks and the threats, should look for the opportunities by which
they can furnish their business activities.
SWOT analysis of STP Limited network project
Internal POSITIVE NEGATIVE
Strengths Weaknesses
Large number of customers
Augmented Sales targets
Diligent workers
Insider Threat
Technically unskilled employees
Not maintaining rules and procedures
Externa
l
Opportunities Threats
The information system gets
integrated
The employees’ empowerment
The data related to finance gets leaked
and the customer information gets
leaked.
the customers. Thus it can be said the information service can scale up the business of STP.
The website can be better managed and the web staffs can get benefits due to the technology
advancement and information service management.
1.2.2. Project goal
The project goal is based on the tools and the management staffs, as well as the
employees and the technical staff, must use the tools efficiently for better outcomes, the
network equipment that can furnish the business growth has been elaborated in details
(Beletskaya et al. 2013). The project goal is to facilitate the customer employees’ relation or
the CRM.
1.2.3. Strategic alignment of project
The strategic alignment of the project can be made only on the basis of the SWOT
analysis. The SWOT analysis highlights the threats, strength, opportunities and weakness.
The role of system analyst is to determine all the SWOT analysis aspects and in this way,
STP Limited can be aware of the potential benefits the information system can bring in to
their enterprise (Benner et al. 2014). STP should look upon the weakness and the threats and
should try to mitigate those risks and the threats, should look for the opportunities by which
they can furnish their business activities.
SWOT analysis of STP Limited network project
Internal POSITIVE NEGATIVE
Strengths Weaknesses
Large number of customers
Augmented Sales targets
Diligent workers
Insider Threat
Technically unskilled employees
Not maintaining rules and procedures
Externa
l
Opportunities Threats
The information system gets
integrated
The employees’ empowerment
The data related to finance gets leaked
and the customer information gets
leaked.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK MANAGEMENT AND SECURITY
2.0. Network Security
2.1. Securing data
The information system can assist STP Limited in gaining the competitive advantage
over others, it can also help them to augment their productivity. The internal layers of the
information system can act as a fruitful medium with regards to products, people and the
people that if established properly can cater the maximum productivity to STP Limited
(Bernus, Mertins and Schmidt 2013).
2.1.1. People, products, policies and procedures
The information system installed in the enterprise has the potential to embellish the
core business activities. The rules and regulations if followed in a proper way the business
activities can be significantly enriched (Castronova, Goodall and Ercan 2013). The
procedures, policies and the proper workforce can change the entire scenario of STP Limited
and their profit and market will significantly rise.
2.1.2. ISP security and privacy considerations
Since STP heavily relies on the Internet, the advanced Internet connection is bound to
offer the benefits to conduct the business activities in the more significant way. The Big Pond
Network has the potential to defend the negative effect of the cyber threats and STP Limited
can choose it for their betterment (Erich, Amrit and Daneva 2014). The ISP can make the
payment secure, can make the business operations agile and secure.
2.2. Mobile device security
2.2.1. Wireless Local Area Network (WLAN) attacks
The employees of STP Limited basically give preference to wireless networking
while conducting the business activities. If the network is not secured enough the intruders
can take advantage of. They can attack STP Limited’s system and the database and can make
2.0. Network Security
2.1. Securing data
The information system can assist STP Limited in gaining the competitive advantage
over others, it can also help them to augment their productivity. The internal layers of the
information system can act as a fruitful medium with regards to products, people and the
people that if established properly can cater the maximum productivity to STP Limited
(Bernus, Mertins and Schmidt 2013).
2.1.1. People, products, policies and procedures
The information system installed in the enterprise has the potential to embellish the
core business activities. The rules and regulations if followed in a proper way the business
activities can be significantly enriched (Castronova, Goodall and Ercan 2013). The
procedures, policies and the proper workforce can change the entire scenario of STP Limited
and their profit and market will significantly rise.
2.1.2. ISP security and privacy considerations
Since STP heavily relies on the Internet, the advanced Internet connection is bound to
offer the benefits to conduct the business activities in the more significant way. The Big Pond
Network has the potential to defend the negative effect of the cyber threats and STP Limited
can choose it for their betterment (Erich, Amrit and Daneva 2014). The ISP can make the
payment secure, can make the business operations agile and secure.
2.2. Mobile device security
2.2.1. Wireless Local Area Network (WLAN) attacks
The employees of STP Limited basically give preference to wireless networking
while conducting the business activities. If the network is not secured enough the intruders
can take advantage of. They can attack STP Limited’s system and the database and can make

5NETWORK MANAGEMENT AND SECURITY
the entire system vulnerable to malware attack. There stays the risk of sensitive data of
getting stolen (McKeen et al. 2013).
2.2.2. BYOD risks
The financial risks erupt due to the BYOD risks. The personal sensitive data of the
consumers can get compromised. Also, the sensitive financial data of STP Limited can get
compromised due to the malicious activities conducted by the attackers and the hackers. The
software applications along with the operating system can get disrupted as a result of BYOD
risks (Erich, Amrit and Daneva 2014). Thus, BYOD must be installed in an effective manner
as they are capable to cater the productivity and the security against the data and security
breaches.
3. Plan for hardware purchases
3.1. Acquisition of new hardware
STP Limited has planned to take up new hardware technologies and this new
hardware configuration must have the capability to comply with latest software applications
and the advanced information system (Tao et al. 2014). The hardware change can definitely
ease the information technology system implementation that can provide extra security to the
system.
3.2. End-user feedback and reviews
The software applications are getting revolutionised every day with the advent of new
innovation from researchers, this software advancement is capable of lessening the scope of
malware attack and so there is a lesser chance of security breaches (Motus and Kääramees
2014). However, they must comply with the existing hardware resources of the company, and
if this occurs the security breaches can happen and the hackers taking advantage of that can
the entire system vulnerable to malware attack. There stays the risk of sensitive data of
getting stolen (McKeen et al. 2013).
2.2.2. BYOD risks
The financial risks erupt due to the BYOD risks. The personal sensitive data of the
consumers can get compromised. Also, the sensitive financial data of STP Limited can get
compromised due to the malicious activities conducted by the attackers and the hackers. The
software applications along with the operating system can get disrupted as a result of BYOD
risks (Erich, Amrit and Daneva 2014). Thus, BYOD must be installed in an effective manner
as they are capable to cater the productivity and the security against the data and security
breaches.
3. Plan for hardware purchases
3.1. Acquisition of new hardware
STP Limited has planned to take up new hardware technologies and this new
hardware configuration must have the capability to comply with latest software applications
and the advanced information system (Tao et al. 2014). The hardware change can definitely
ease the information technology system implementation that can provide extra security to the
system.
3.2. End-user feedback and reviews
The software applications are getting revolutionised every day with the advent of new
innovation from researchers, this software advancement is capable of lessening the scope of
malware attack and so there is a lesser chance of security breaches (Motus and Kääramees
2014). However, they must comply with the existing hardware resources of the company, and
if this occurs the security breaches can happen and the hackers taking advantage of that can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6NETWORK MANAGEMENT AND SECURITY
gain entry into the vulnerable system (Grabara, Kolcun and Kot 2014). The end user must
take into consideration this issue or the fact and must take a decision based on that.
3.3. Purchasing strategies
STP Limited must make proper monetary planning that can facilitate the spending of
money on important aspects on future occasions. The enterprise must save and protect money
for the future use so that they can collectively take the best decision and best strategy to take
the best decision to carry out the business (Fedushko 2014). Via asset register they must serve
the suppliers, they must utilise the save money to buy the hardware as per the business
requirements.
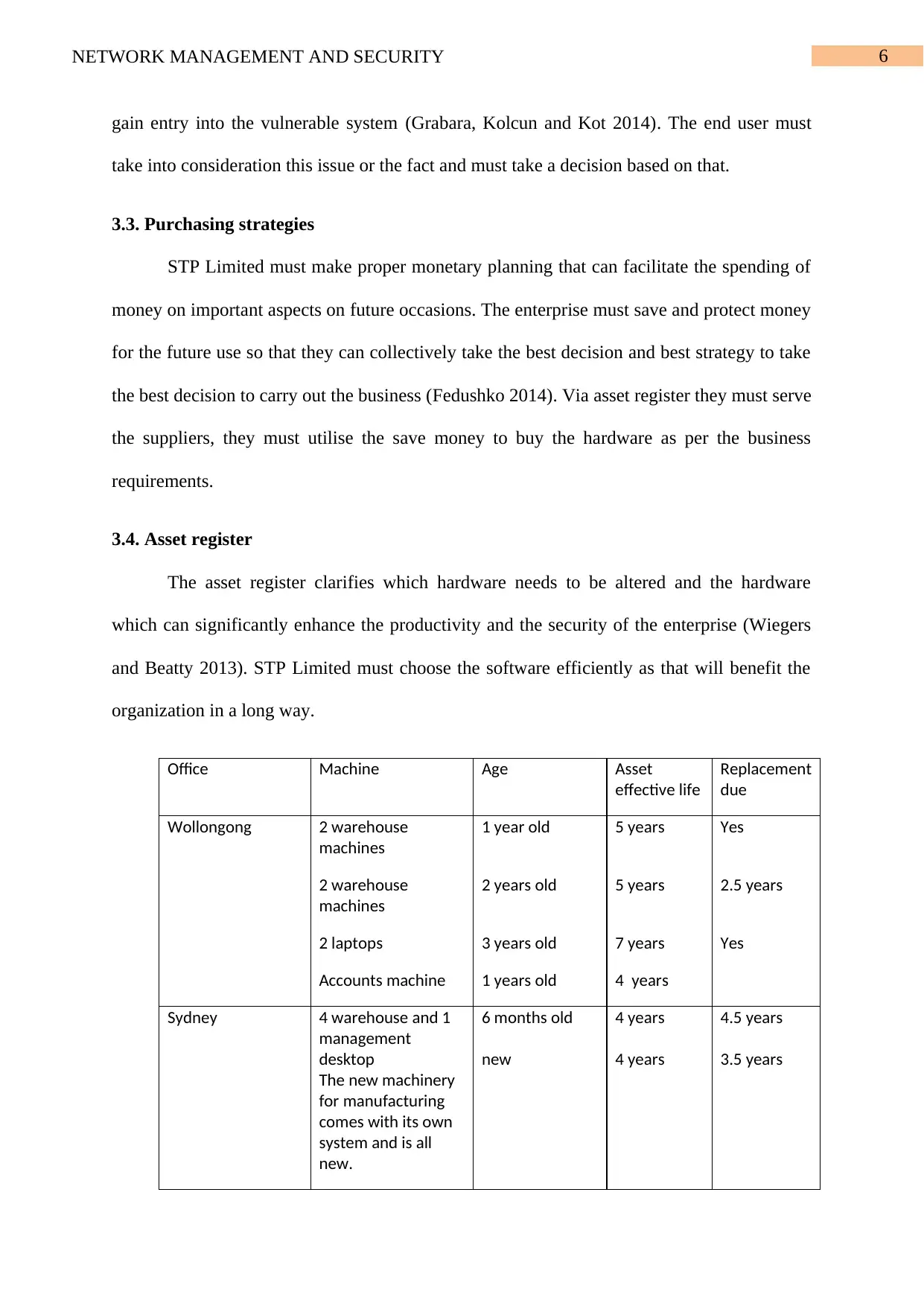
3.4. Asset register
The asset register clarifies which hardware needs to be altered and the hardware
which can significantly enhance the productivity and the security of the enterprise (Wiegers
and Beatty 2013). STP Limited must choose the software efficiently as that will benefit the
organization in a long way.
Office Machine Age Asset
effective life
Replacement
due
Wollongong 2 warehouse
machines
1 year old 5 years Yes
2 warehouse
machines
2 years old 5 years 2.5 years
2 laptops 3 years old 7 years Yes
Accounts machine 1 years old 4 years
Sydney 4 warehouse and 1
management
desktop
The new machinery
for manufacturing
comes with its own
system and is all
new.
6 months old
new
4 years
4 years
4.5 years
3.5 years
gain entry into the vulnerable system (Grabara, Kolcun and Kot 2014). The end user must
take into consideration this issue or the fact and must take a decision based on that.
3.3. Purchasing strategies
STP Limited must make proper monetary planning that can facilitate the spending of
money on important aspects on future occasions. The enterprise must save and protect money
for the future use so that they can collectively take the best decision and best strategy to take
the best decision to carry out the business (Fedushko 2014). Via asset register they must serve
the suppliers, they must utilise the save money to buy the hardware as per the business
requirements.
3.4. Asset register
The asset register clarifies which hardware needs to be altered and the hardware
which can significantly enhance the productivity and the security of the enterprise (Wiegers
and Beatty 2013). STP Limited must choose the software efficiently as that will benefit the
organization in a long way.
Office Machine Age Asset
effective life
Replacement
due
Wollongong 2 warehouse
machines
1 year old 5 years Yes
2 warehouse
machines
2 years old 5 years 2.5 years
2 laptops 3 years old 7 years Yes
Accounts machine 1 years old 4 years
Sydney 4 warehouse and 1
management
desktop
The new machinery
for manufacturing
comes with its own
system and is all
new.
6 months old
new
4 years
4 years
4.5 years
3.5 years
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7NETWORK MANAGEMENT AND SECURITY
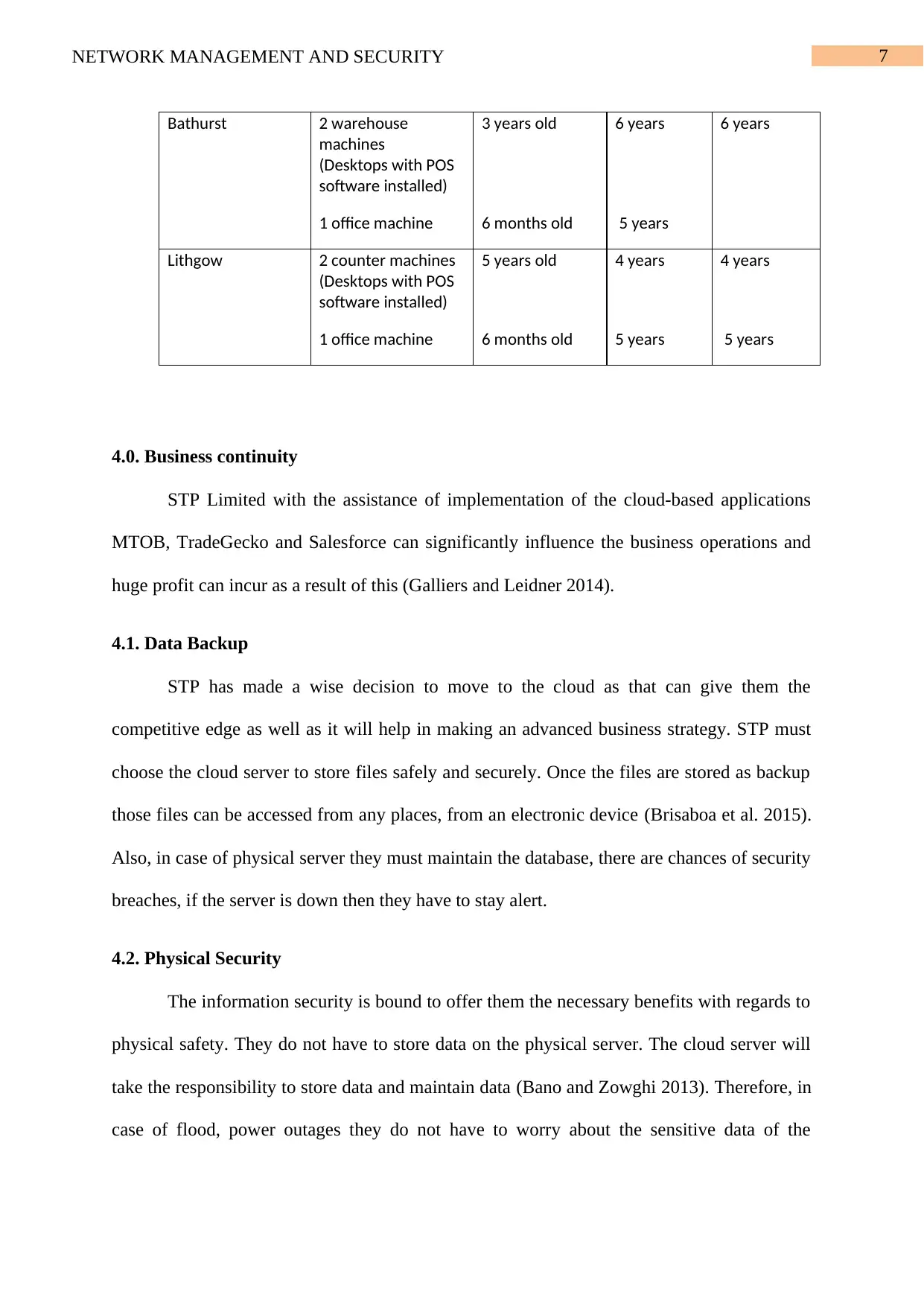
Bathurst 2 warehouse
machines
(Desktops with POS
software installed)
3 years old 6 years 6 years
1 office machine 6 months old 5 years
Lithgow 2 counter machines
(Desktops with POS
software installed)
5 years old 4 years 4 years
1 office machine 6 months old 5 years 5 years
4.0. Business continuity
STP Limited with the assistance of implementation of the cloud-based applications
MTOB, TradeGecko and Salesforce can significantly influence the business operations and
huge profit can incur as a result of this (Galliers and Leidner 2014).
4.1. Data Backup
STP has made a wise decision to move to the cloud as that can give them the
competitive edge as well as it will help in making an advanced business strategy. STP must
choose the cloud server to store files safely and securely. Once the files are stored as backup
those files can be accessed from any places, from an electronic device (Brisaboa et al. 2015).
Also, in case of physical server they must maintain the database, there are chances of security
breaches, if the server is down then they have to stay alert.
4.2. Physical Security
The information security is bound to offer them the necessary benefits with regards to
physical safety. They do not have to store data on the physical server. The cloud server will
take the responsibility to store data and maintain data (Bano and Zowghi 2013). Therefore, in
case of flood, power outages they do not have to worry about the sensitive data of the
Bathurst 2 warehouse
machines
(Desktops with POS
software installed)
3 years old 6 years 6 years
1 office machine 6 months old 5 years
Lithgow 2 counter machines
(Desktops with POS
software installed)
5 years old 4 years 4 years
1 office machine 6 months old 5 years 5 years
4.0. Business continuity
STP Limited with the assistance of implementation of the cloud-based applications
MTOB, TradeGecko and Salesforce can significantly influence the business operations and
huge profit can incur as a result of this (Galliers and Leidner 2014).
4.1. Data Backup
STP has made a wise decision to move to the cloud as that can give them the
competitive edge as well as it will help in making an advanced business strategy. STP must
choose the cloud server to store files safely and securely. Once the files are stored as backup
those files can be accessed from any places, from an electronic device (Brisaboa et al. 2015).
Also, in case of physical server they must maintain the database, there are chances of security
breaches, if the server is down then they have to stay alert.
4.2. Physical Security
The information security is bound to offer them the necessary benefits with regards to
physical safety. They do not have to store data on the physical server. The cloud server will
take the responsibility to store data and maintain data (Bano and Zowghi 2013). Therefore, in
case of flood, power outages they do not have to worry about the sensitive data of the

8NETWORK MANAGEMENT AND SECURITY
customers and the financial data of STP Limited. They may minimal effects due to calamities
bust the most important thing the data will stay protected in their cloud database.
4.3. Successful planning
For any reasons any employees can remain absent, he or she may suffer from illness
(Chakraborty et al. 2015). It may happen the individual is in charge of a specific task of the
project and he dies so STP Limited must appoint a successor and STP must prepare him or
her for the replacement, so that the appointed individual can be ready to handle the job role at
the time of need and can handle the difficult scenario.
4.4. Stock Control system
STP Limited with the aid of information system must develop a website that will
show all the available kitchen cabinets ranging from drawer fronts and the cupboards. The
cabinets must be displayed in such a way that their colours and the textures can be attractive.
Now, once an item gets ordered and shipped the website must be updated and the availability
of the stock products must be reflected in that manner accordingly (Chakraborty et al. 2015).
Thus all the four offices of STP Limited can be aware of the stock products.
5.0. Risk management
The threats, risks and the vulnerabilities correlated with the cloud computing must be
taken into consideration and analysing them in details, STP Limited should take safety
measures and precautions to mitigate all these risks and threats (Brisaboa et al. 2015).
5.1. Security Policy
A security model can be beneficial to analyse the risk, threats and the vulnerabilities
of the information system that can affect STP Limited and thus a security model can assist to
conduct the business operations in a secure and effective manner (Wiegers and Beatty 2013).
customers and the financial data of STP Limited. They may minimal effects due to calamities
bust the most important thing the data will stay protected in their cloud database.
4.3. Successful planning
For any reasons any employees can remain absent, he or she may suffer from illness
(Chakraborty et al. 2015). It may happen the individual is in charge of a specific task of the
project and he dies so STP Limited must appoint a successor and STP must prepare him or
her for the replacement, so that the appointed individual can be ready to handle the job role at
the time of need and can handle the difficult scenario.
4.4. Stock Control system
STP Limited with the aid of information system must develop a website that will
show all the available kitchen cabinets ranging from drawer fronts and the cupboards. The
cabinets must be displayed in such a way that their colours and the textures can be attractive.
Now, once an item gets ordered and shipped the website must be updated and the availability
of the stock products must be reflected in that manner accordingly (Chakraborty et al. 2015).
Thus all the four offices of STP Limited can be aware of the stock products.
5.0. Risk management
The threats, risks and the vulnerabilities correlated with the cloud computing must be
taken into consideration and analysing them in details, STP Limited should take safety
measures and precautions to mitigate all these risks and threats (Brisaboa et al. 2015).
5.1. Security Policy
A security model can be beneficial to analyse the risk, threats and the vulnerabilities
of the information system that can affect STP Limited and thus a security model can assist to
conduct the business operations in a secure and effective manner (Wiegers and Beatty 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK MANAGEMENT AND SECURITY
The change management along with the incident management can provide assistance to
install and configure the regulations and the policies within STP Limited.
5.2. Training and awareness
STP Limited must educate their staffs about the significance of information system
and the benefits that the information system can bring into the organisation (Galliers and
Leidner 2014). All these aspects can assist an employee to take steps against any security
breach that occurs within the enterprise.
5.3. Integration technology
Integration of various cloud architecture can enrich productivity of STP Limited. The
SaaS model and the PaaS model in collaboration can provide advanced business solutions,
PaaS provides more functionality that can be helpful to conduct the business activities over
the cloud platform and Salesforce.com is popular to serve the SaaS functionality to STP
Limited (Xu et al. 2014).
6.0. Conclusions
It can be concluded from the above discourse STP Limited can enhance their business
operations with aid of information system, and with the effective implementation of the
information system, they can mitigate the security risks incurred within the organization as
well. The report has elaborated all the security policies, people and the procedures associated
to ensure the safety and security of the enterprise. The solutions to secure the website, as well
as the four offices of STP Limited, has been highlighted and defined elaborately. STP
Limited if stays aware all the time then business operations can get embellished in a grand
way, STP can get maximum profits and can increase their market share and market growth.
The change management along with the incident management can provide assistance to
install and configure the regulations and the policies within STP Limited.
5.2. Training and awareness
STP Limited must educate their staffs about the significance of information system
and the benefits that the information system can bring into the organisation (Galliers and
Leidner 2014). All these aspects can assist an employee to take steps against any security
breach that occurs within the enterprise.
5.3. Integration technology
Integration of various cloud architecture can enrich productivity of STP Limited. The
SaaS model and the PaaS model in collaboration can provide advanced business solutions,
PaaS provides more functionality that can be helpful to conduct the business activities over
the cloud platform and Salesforce.com is popular to serve the SaaS functionality to STP
Limited (Xu et al. 2014).
6.0. Conclusions
It can be concluded from the above discourse STP Limited can enhance their business
operations with aid of information system, and with the effective implementation of the
information system, they can mitigate the security risks incurred within the organization as
well. The report has elaborated all the security policies, people and the procedures associated
to ensure the safety and security of the enterprise. The solutions to secure the website, as well
as the four offices of STP Limited, has been highlighted and defined elaborately. STP
Limited if stays aware all the time then business operations can get embellished in a grand
way, STP can get maximum profits and can increase their market share and market growth.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORK MANAGEMENT AND SECURITY
7.0. Recommendations
i. The implementation of procedures and policies in an effective manner can root out the
chances of security breaches and can help to conduct business activities in the smooth,
effective and secured way.
ii. STP Limited must be careful about the money transactions initially as their network is not
secured enough, it will take time for all the things to get set up in time, it will take time for
the website to get fully developed, thus STP Limited can carry out the operations once the
portal access and the rogue delivery tools are implied.
iii. The asset register should be carefully looked upon and STP must be clear about the
security policies, procedures and techniques.
iv. The enterprise must keep back up of all the sensitive data of the customers and financial
data of the business in a safe way.
v. The employees of the four offices must be aware of all the information techniques
procedures and the security techniques by which they can both serve STP Limited along with
the customers of the company well.
vi. The stock control system must be enhanced with the latest information system technology,
the website should forecast all the latest kitchen cabinets, cupboards and drawers, once any
customer purchases any product, the website must update the same and the exact stock
availability must get shown all across the four offices. In this way, the employees of the four
offices will be aware of all the available resources and in turn, can update the customers.
7.0. Recommendations
i. The implementation of procedures and policies in an effective manner can root out the
chances of security breaches and can help to conduct business activities in the smooth,
effective and secured way.
ii. STP Limited must be careful about the money transactions initially as their network is not
secured enough, it will take time for all the things to get set up in time, it will take time for
the website to get fully developed, thus STP Limited can carry out the operations once the
portal access and the rogue delivery tools are implied.
iii. The asset register should be carefully looked upon and STP must be clear about the
security policies, procedures and techniques.
iv. The enterprise must keep back up of all the sensitive data of the customers and financial
data of the business in a safe way.
v. The employees of the four offices must be aware of all the information techniques
procedures and the security techniques by which they can both serve STP Limited along with
the customers of the company well.
vi. The stock control system must be enhanced with the latest information system technology,
the website should forecast all the latest kitchen cabinets, cupboards and drawers, once any
customer purchases any product, the website must update the same and the exact stock
availability must get shown all across the four offices. In this way, the employees of the four
offices will be aware of all the available resources and in turn, can update the customers.

11NETWORK MANAGEMENT AND SECURITY
8.0. Bibliography
Bano, M. and Zowghi, D., 2013, April. User involvement in software development and
system success: a systematic literature review. In Proceedings of the 17th International
Conference on Evaluation and Assessment in Software Engineering (pp. 125-130). ACM.
Beletskaya, S.Y., Zolnikov, V.K., Kravets, O.J., Lapshina, M.L. and Podvalny, E.S., 2013.
Specific features of modeling and developing the mathematical and program software for
designing intranet-interfaces during competitive development of information systems. World
Applied Sciences Journal, 23(12), p.64.
Benner, K.M., Feather, M.S., Johnson, W.L. and Zorman, L.A., 2014. Utilizing scenarios in
the software development process. Information system development process, 30, pp.117-134.
Bernus, P., Mertins, K. and Schmidt, G.J. eds., 2013. Handbook on architectures of
information systems. Springer Science & Business Media.
Brisaboa, N.R., Cortiñas, A., Luaces, M.R. and Pol’la, M., 2015. A reusable software
architecture for geographic information systems based on software product line engineering.
In Model and Data Engineering (pp. 320-331). Springer International Publishing.
Castronova, A.M., Goodall, J.L. and Ercan, M.B., 2013. Integrated modeling within a
hydrologic information system: an OpenMI based approach. Environmental Modelling &
Software, 39, pp.263-273.
Chakraborty, D., Sarkar, D., Agarwal, S., Dutta, D. and Sharma, J.R., 2015. Web based GIS
application using Open Source software for sharing Geospatial Data. International Journal of
Advanced Remote Sensing and GIS, 4(1), pp.pp-1224.
8.0. Bibliography
Bano, M. and Zowghi, D., 2013, April. User involvement in software development and
system success: a systematic literature review. In Proceedings of the 17th International
Conference on Evaluation and Assessment in Software Engineering (pp. 125-130). ACM.
Beletskaya, S.Y., Zolnikov, V.K., Kravets, O.J., Lapshina, M.L. and Podvalny, E.S., 2013.
Specific features of modeling and developing the mathematical and program software for
designing intranet-interfaces during competitive development of information systems. World
Applied Sciences Journal, 23(12), p.64.
Benner, K.M., Feather, M.S., Johnson, W.L. and Zorman, L.A., 2014. Utilizing scenarios in
the software development process. Information system development process, 30, pp.117-134.
Bernus, P., Mertins, K. and Schmidt, G.J. eds., 2013. Handbook on architectures of
information systems. Springer Science & Business Media.
Brisaboa, N.R., Cortiñas, A., Luaces, M.R. and Pol’la, M., 2015. A reusable software
architecture for geographic information systems based on software product line engineering.
In Model and Data Engineering (pp. 320-331). Springer International Publishing.
Castronova, A.M., Goodall, J.L. and Ercan, M.B., 2013. Integrated modeling within a
hydrologic information system: an OpenMI based approach. Environmental Modelling &
Software, 39, pp.263-273.
Chakraborty, D., Sarkar, D., Agarwal, S., Dutta, D. and Sharma, J.R., 2015. Web based GIS
application using Open Source software for sharing Geospatial Data. International Journal of
Advanced Remote Sensing and GIS, 4(1), pp.pp-1224.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





