STP Organization: Advanced Network Topics Report Analysis
VerifiedAdded on 2020/05/11
|12
|3272
|32
Report
AI Summary
This report provides a comprehensive analysis of the STP Organization's network infrastructure, addressing key challenges and proposing solutions. The executive summary highlights the organization's growth and need for improved communication and order management. The report covers network security, including data and mobile device security, emphasizing the importance of protecting sensitive information and ensuring authorized access. It includes a plan for hardware purchases, considering asset age and replacement cycles, and emphasizes the strategic alignment of hardware with business goals. A business continuity plan is presented to maintain essential functions and prevent network interruptions. The report also addresses risk management, outlining procedures to mitigate potential threats and ensure a secure network infrastructure. Recommendations are provided to resolve existing network issues and enhance overall organizational efficiency.
Advanced Network Topics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive summary
The STP organizations is the popular cabinet makers and it located at Wollongong. It
has own factory and head office. The STP organization sales have been going well and it
recently bought operations of competitors located at Lithgow and Bathurst. It also opened a
new store in Sydney also interest to open a new store in many places. It manufactures the
cupboard and drawer fronts. It using the three styles of cupboard and drawer fronts. It
decided to create the new network infrastructure. Because, STP organization has the
problems like customers are does not check the order delivery time by ringing the office
phones. Sometimes employees are does not pick the phones. So, customers are not satisfying
with the order. To resolve this problem to create the best communication services for an
organization.
1
The STP organizations is the popular cabinet makers and it located at Wollongong. It
has own factory and head office. The STP organization sales have been going well and it
recently bought operations of competitors located at Lithgow and Bathurst. It also opened a
new store in Sydney also interest to open a new store in many places. It manufactures the
cupboard and drawer fronts. It using the three styles of cupboard and drawer fronts. It
decided to create the new network infrastructure. Because, STP organization has the
problems like customers are does not check the order delivery time by ringing the office
phones. Sometimes employees are does not pick the phones. So, customers are not satisfying
with the order. To resolve this problem to create the best communication services for an
organization.
1

Table of Contents
Executive summary.............................................................................................................................1
1. Introduction.................................................................................................................................3
1.1 Project Background.............................................................................................................3
1.2 Project Scope........................................................................................................................3
1.3 Project Goal..........................................................................................................................4
1.4 Strategic alignment of project.............................................................................................4
2. Network Security.........................................................................................................................5
2.1 Data security........................................................................................................................5
2.2 Mobile device Security.........................................................................................................6
3. Plan for hardware purchases......................................................................................................7
4. Business continuity......................................................................................................................8
5. Risk Management........................................................................................................................9
6. Conclusions................................................................................................................................10
7. Recommendations......................................................................................................................10
References..........................................................................................................................................10
2
Executive summary.............................................................................................................................1
1. Introduction.................................................................................................................................3
1.1 Project Background.............................................................................................................3
1.2 Project Scope........................................................................................................................3
1.3 Project Goal..........................................................................................................................4
1.4 Strategic alignment of project.............................................................................................4
2. Network Security.........................................................................................................................5
2.1 Data security........................................................................................................................5
2.2 Mobile device Security.........................................................................................................6
3. Plan for hardware purchases......................................................................................................7
4. Business continuity......................................................................................................................8
5. Risk Management........................................................................................................................9
6. Conclusions................................................................................................................................10
7. Recommendations......................................................................................................................10
References..........................................................................................................................................10
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction
The STP organization interest to create the new network infrastructure. Because, STP
organization has the problems like customers are does not check the order delivery time by
ringing the office phones. Sometimes employees are does not pick the phones. So, customers
are not satisfying with the order. To resolve this problem to create the best communication
services for an organization. It also has another problem that is customer replace the products
but some locations are does not have the products on locations. It has these products to
another location. So, it takes more time to replacement the products to the customers. The
Existing problems are resolved by creating the fresh network infrastructure. To resolving the
existing issues by creating the business continuity plan and secure network services. The
business continuity plan and risk management will be discussed.
1.1 Project Background
The STP organizations is the popular cabinet makers and it located at Wollongong. It has
own factory and head office. The STP organization sales have been going well and it recently
bought operations of competitors located at Lithgow and Bathurst. It also opened a new store
in Sydney also interest to open a new store in many places. It manufactures the cupboard and
drawer fronts. The organization using the three styles of cupboard and drawers. It also
produces the new fronts. The STP organization currently considering van carrying samples of
their products. It has high cost interest in home renovation has driven a lot of enquiry and lot
of sales from outside of current STP locations. It recently bought the two existing stores and
opened a new branch in Sydney but it currently does not run lot of customer accounts and pay
cash on delivering. It also receiving the lot of enquiry form developers and builders to
implement the customer accounts. The STP limited also creating the website to publish their
variety of products. It has the stock control system to buying the new model cup board,
hinges and drawer material. The Lithgow and Bathurst offices are working with previous
owners. These two offices are working in small standalone locations and it contains the
limited products.
1.2 Project Scope
Main scope of this project is to create the effective STP organization. It has two main
problems such as The STP organization has the problems like customers are does not check
the order delivery time by ringing the office phones. Sometimes employees are does not pick
3
The STP organization interest to create the new network infrastructure. Because, STP
organization has the problems like customers are does not check the order delivery time by
ringing the office phones. Sometimes employees are does not pick the phones. So, customers
are not satisfying with the order. To resolve this problem to create the best communication
services for an organization. It also has another problem that is customer replace the products
but some locations are does not have the products on locations. It has these products to
another location. So, it takes more time to replacement the products to the customers. The
Existing problems are resolved by creating the fresh network infrastructure. To resolving the
existing issues by creating the business continuity plan and secure network services. The
business continuity plan and risk management will be discussed.
1.1 Project Background
The STP organizations is the popular cabinet makers and it located at Wollongong. It has
own factory and head office. The STP organization sales have been going well and it recently
bought operations of competitors located at Lithgow and Bathurst. It also opened a new store
in Sydney also interest to open a new store in many places. It manufactures the cupboard and
drawer fronts. The organization using the three styles of cupboard and drawers. It also
produces the new fronts. The STP organization currently considering van carrying samples of
their products. It has high cost interest in home renovation has driven a lot of enquiry and lot
of sales from outside of current STP locations. It recently bought the two existing stores and
opened a new branch in Sydney but it currently does not run lot of customer accounts and pay
cash on delivering. It also receiving the lot of enquiry form developers and builders to
implement the customer accounts. The STP limited also creating the website to publish their
variety of products. It has the stock control system to buying the new model cup board,
hinges and drawer material. The Lithgow and Bathurst offices are working with previous
owners. These two offices are working in small standalone locations and it contains the
limited products.
1.2 Project Scope
Main scope of this project is to create the effective STP organization. It has two main
problems such as The STP organization has the problems like customers are does not check
the order delivery time by ringing the office phones. Sometimes employees are does not pick
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the phones (Oppenheimer, 2011). These two problems were resolved by creating the effective
organization. It also identifies the risks in the organization. It provides the business continuity
plan to provide the effective infrastructure. The project boundaries are auditable and
measurable characteristics that define the organization objectives and creates the holistic
perception of a network infrastructures. The project boundaries are defines the software
systems on computer workstations both head offices and branch offices. STP organization
needs to resolve the existing network issues.
1.3 Project Goal
The STP organization main goal is to create the fresh network infrastructure. The Project
goals are listed below.
• Create the Create proposed network infrastructure.
• Create the best communication services to satisfies the customer
• Creates the best strategic alignment of project because it provides the secure business
continuity operations and process.
• Makes the business continuity plan to establish the risk management processes and
procedures.
• Makes the secure risk management plan to provides the secure network infrastructure
and resolve the existing network issues.
• Risk management plan re-establish the network issues and processes for STP
organization.
• Create the best plan for hardware purchases.
• Implement the organization policies and procedures.
1.4 Strategic alignment of project
The strategic alignment of project is to provide the business continuity operations. The
business continuity plan is easily establishing the risk management procedures and processes
that aim to prevent the network interruptions to re-establish and critical services for
organization functions. It is the very important for STP organization because it maintain the
overall organization functions for the disaster duration. It identified the business environment
and investigate the information system (Hagan et al., 2016). The IT architecture support the
STP organization to provide the effective voice communications between the employees and
customers. The proposed infrastructure provides the security and productivity for an
4
organization. It also identifies the risks in the organization. It provides the business continuity
plan to provide the effective infrastructure. The project boundaries are auditable and
measurable characteristics that define the organization objectives and creates the holistic
perception of a network infrastructures. The project boundaries are defines the software
systems on computer workstations both head offices and branch offices. STP organization
needs to resolve the existing network issues.
1.3 Project Goal
The STP organization main goal is to create the fresh network infrastructure. The Project
goals are listed below.
• Create the Create proposed network infrastructure.
• Create the best communication services to satisfies the customer
• Creates the best strategic alignment of project because it provides the secure business
continuity operations and process.
• Makes the business continuity plan to establish the risk management processes and
procedures.
• Makes the secure risk management plan to provides the secure network infrastructure
and resolve the existing network issues.
• Risk management plan re-establish the network issues and processes for STP
organization.
• Create the best plan for hardware purchases.
• Implement the organization policies and procedures.
1.4 Strategic alignment of project
The strategic alignment of project is to provide the business continuity operations. The
business continuity plan is easily establishing the risk management procedures and processes
that aim to prevent the network interruptions to re-establish and critical services for
organization functions. It is the very important for STP organization because it maintain the
overall organization functions for the disaster duration. It identified the business environment
and investigate the information system (Hagan et al., 2016). The IT architecture support the
STP organization to provide the effective voice communications between the employees and
customers. The proposed infrastructure provides the security and productivity for an
4

organization. The proposed network infrastructure must implement the current strategy
alignment to provide the effective organization. The strategic alignment support the proposed
network infrastructure by using the business continuity operations and processes.
2. Network Security
The Network security is a process of taking the software and physical preventative
measures to protect the STP network infrastructure from unauthorized access, modification,
destruction, malfunction and misuse by creating a secure platform for programs, users and
computers to perform the critical function within a secure environment. The network security
consists of the practices and policies adopted to prevent the authorised access. It involves the
access authorization to data in STP network infrastructure and it controlled by a STP network
administrator. It covers the computer network variety and both private and public network
connection (Kurose and Ross, n.d.). It easily conducting the communications and transactions
among government, businesses and individuals. It designed to protect the usability and
integrity of STP network and data. It includes the software and hardware technologies. The
proposed STP network infrastructure provides the effective network security and it manages
the overall network access. It focuses on variety of threats and stops them from spreading or
entering on STP network. It combines the various defence’s layers at the edge and in the STP
network. It easily implements the network controls and policies. The STP network security
does not allow the malicious actors use the STP network resources. The authorised users only
access the network resources in the STP network.
2.1 Data security
The network security mainly focusses on the securing the data for an STP organization by
using the data security method (NETworking, 2013). The data security techniques are used to
protecting the STP organization sensitive information and data like data base from destructive
forces or unauthorised users. The Malicious users are accessing the STP data by using the
following attacks like data breach and cyber-attack. To secure the STP organization sensitive
information data by using the following technologies. These are discussed in below.
• Data encryption
• Software versus hardware based mechanisms for data protection
• Backups
• Data masking
5
alignment to provide the effective organization. The strategic alignment support the proposed
network infrastructure by using the business continuity operations and processes.
2. Network Security
The Network security is a process of taking the software and physical preventative
measures to protect the STP network infrastructure from unauthorized access, modification,
destruction, malfunction and misuse by creating a secure platform for programs, users and
computers to perform the critical function within a secure environment. The network security
consists of the practices and policies adopted to prevent the authorised access. It involves the
access authorization to data in STP network infrastructure and it controlled by a STP network
administrator. It covers the computer network variety and both private and public network
connection (Kurose and Ross, n.d.). It easily conducting the communications and transactions
among government, businesses and individuals. It designed to protect the usability and
integrity of STP network and data. It includes the software and hardware technologies. The
proposed STP network infrastructure provides the effective network security and it manages
the overall network access. It focuses on variety of threats and stops them from spreading or
entering on STP network. It combines the various defence’s layers at the edge and in the STP
network. It easily implements the network controls and policies. The STP network security
does not allow the malicious actors use the STP network resources. The authorised users only
access the network resources in the STP network.
2.1 Data security
The network security mainly focusses on the securing the data for an STP organization by
using the data security method (NETworking, 2013). The data security techniques are used to
protecting the STP organization sensitive information and data like data base from destructive
forces or unauthorised users. The Malicious users are accessing the STP data by using the
following attacks like data breach and cyber-attack. To secure the STP organization sensitive
information data by using the following technologies. These are discussed in below.
• Data encryption
• Software versus hardware based mechanisms for data protection
• Backups
• Data masking
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
• Data erasure
The data security involves preventing the unauthorised users from accessing it as well as
preventing intentional and accidental infection, corruption and destruction of data or
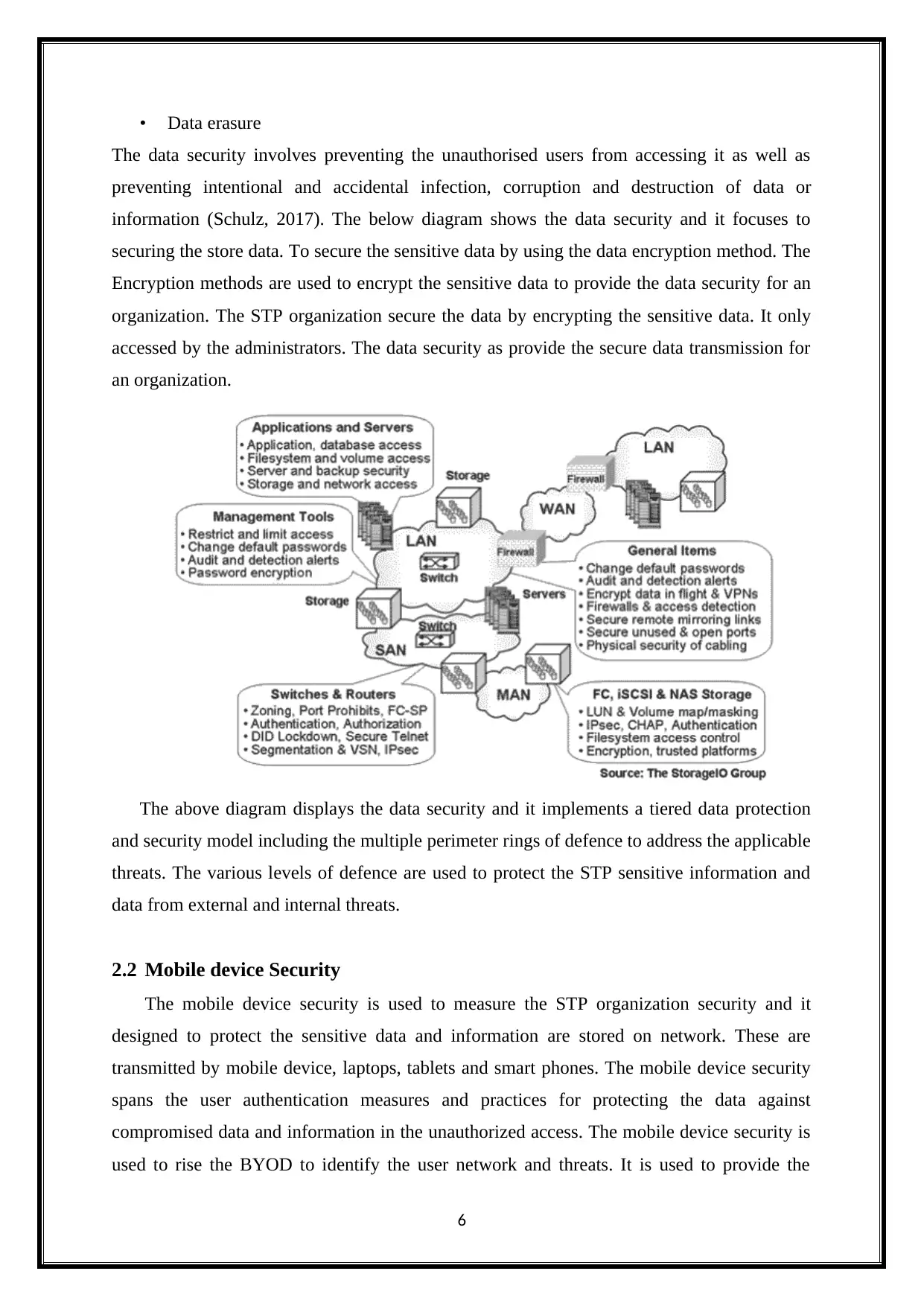
information (Schulz, 2017). The below diagram shows the data security and it focuses to
securing the store data. To secure the sensitive data by using the data encryption method. The
Encryption methods are used to encrypt the sensitive data to provide the data security for an
organization. The STP organization secure the data by encrypting the sensitive data. It only
accessed by the administrators. The data security as provide the secure data transmission for
an organization.
The above diagram displays the data security and it implements a tiered data protection
and security model including the multiple perimeter rings of defence to address the applicable
threats. The various levels of defence are used to protect the STP sensitive information and
data from external and internal threats.
2.2 Mobile device Security
The mobile device security is used to measure the STP organization security and it
designed to protect the sensitive data and information are stored on network. These are
transmitted by mobile device, laptops, tablets and smart phones. The mobile device security
spans the user authentication measures and practices for protecting the data against
compromised data and information in the unauthorized access. The mobile device security is
used to rise the BYOD to identify the user network and threats. It is used to provide the
6
The data security involves preventing the unauthorised users from accessing it as well as
preventing intentional and accidental infection, corruption and destruction of data or
information (Schulz, 2017). The below diagram shows the data security and it focuses to
securing the store data. To secure the sensitive data by using the data encryption method. The
Encryption methods are used to encrypt the sensitive data to provide the data security for an
organization. The STP organization secure the data by encrypting the sensitive data. It only
accessed by the administrators. The data security as provide the secure data transmission for
an organization.
The above diagram displays the data security and it implements a tiered data protection
and security model including the multiple perimeter rings of defence to address the applicable
threats. The various levels of defence are used to protect the STP sensitive information and
data from external and internal threats.
2.2 Mobile device Security
The mobile device security is used to measure the STP organization security and it
designed to protect the sensitive data and information are stored on network. These are
transmitted by mobile device, laptops, tablets and smart phones. The mobile device security
spans the user authentication measures and practices for protecting the data against
compromised data and information in the unauthorized access. The mobile device security is
used to rise the BYOD to identify the user network and threats. It is used to provide the
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

unparalleled visibility into STP network to address the security vulnerabilities and gaps. It
reduces the risk and demonstrate the compliance. It used to allow users to improve the user
productivity and security. It optimally integrates the business processes. The Proposed
network security also provides the secure network for guest network. Because it using the
high level network infrastructure. The mobile device security also provides the secure
network for guest network by implement user authentication procedures and policies.
3. Plan for hardware purchases
Planning for hardware purchases is vital if STP organization wants to have an
advantage over the competitors. The hardware purchases are used to align the organization
strategic and increases the organization performance. It enhanced the business continuity of
the operations. The STP organization hardware are failure, damage or loss, it requires the
hardware purchases. The failure hardware was does not provides the security and
productivity for an organization. It needs to refer the risk by insuring the businesses assets.
To maintain the organization asset register, budget forecasts, reviews, procedures, policies
and strategies by replacing the failure hardware’s. The organization teams were first
understanding the how employees are using the hardware (Thomas, 2012). After purchase the
hardware. Because it incorporated into the planning of hardware purchases. So, organization
teams were using the scheduling reviews and end user opportunity to provide the
performance evaluation of hardware there by providing the informed decision-making
process for an organization. The scheduling reviews are used to identifying the potential risks
to reduce the risks in an organization. The Planning of hardware purchasing for strategic
alignment was ensures the enough money to access the organization finance to purchase the
hardware and safeguarding cash flow by requires the forward planning. It indicates the better
alignment with strategic positioning. It understanding the business requirements through the
organization asset register. The proposed hardware purchase plan was provides the five years
of replacement due. The Hardware purchase planning next 5 years of replacement is shown in
below based on asset register.
Office Machine Age Asset
Effective Life
Replacement
due
Wollongong 2 warehouse machines 1 year old 4 years Yes
2 warehouse machines 2 years old 3 years 2 years
7
reduces the risk and demonstrate the compliance. It used to allow users to improve the user
productivity and security. It optimally integrates the business processes. The Proposed
network security also provides the secure network for guest network. Because it using the
high level network infrastructure. The mobile device security also provides the secure
network for guest network by implement user authentication procedures and policies.
3. Plan for hardware purchases
Planning for hardware purchases is vital if STP organization wants to have an
advantage over the competitors. The hardware purchases are used to align the organization
strategic and increases the organization performance. It enhanced the business continuity of
the operations. The STP organization hardware are failure, damage or loss, it requires the
hardware purchases. The failure hardware was does not provides the security and
productivity for an organization. It needs to refer the risk by insuring the businesses assets.
To maintain the organization asset register, budget forecasts, reviews, procedures, policies
and strategies by replacing the failure hardware’s. The organization teams were first
understanding the how employees are using the hardware (Thomas, 2012). After purchase the
hardware. Because it incorporated into the planning of hardware purchases. So, organization
teams were using the scheduling reviews and end user opportunity to provide the
performance evaluation of hardware there by providing the informed decision-making
process for an organization. The scheduling reviews are used to identifying the potential risks
to reduce the risks in an organization. The Planning of hardware purchasing for strategic
alignment was ensures the enough money to access the organization finance to purchase the
hardware and safeguarding cash flow by requires the forward planning. It indicates the better
alignment with strategic positioning. It understanding the business requirements through the
organization asset register. The proposed hardware purchase plan was provides the five years
of replacement due. The Hardware purchase planning next 5 years of replacement is shown in
below based on asset register.
Office Machine Age Asset
Effective Life
Replacement
due
Wollongong 2 warehouse machines 1 year old 4 years Yes
2 warehouse machines 2 years old 3 years 2 years
7
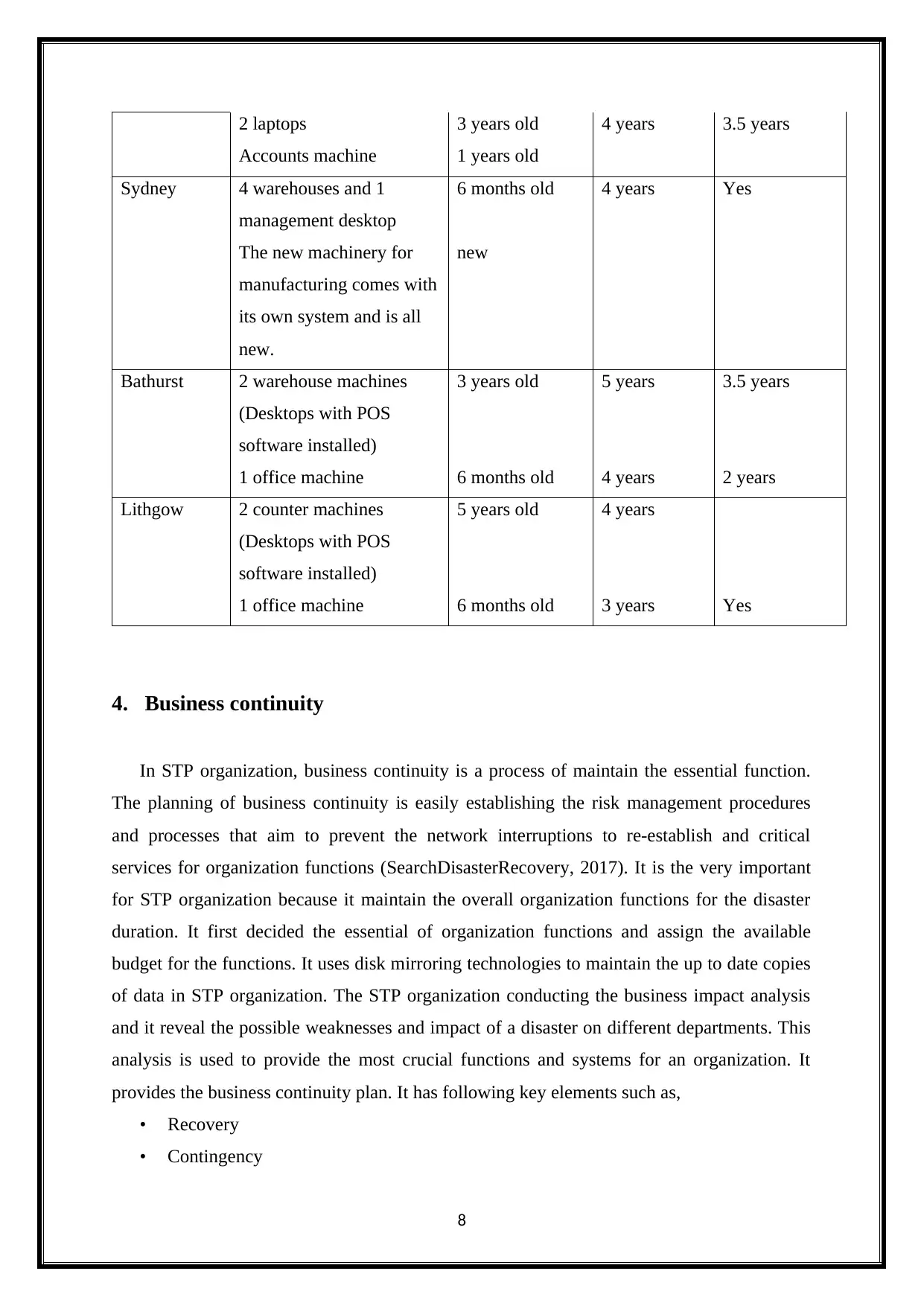
2 laptops 3 years old 4 years 3.5 years
Accounts machine 1 years old
Sydney 4 warehouses and 1
management desktop
The new machinery for
manufacturing comes with
its own system and is all
new.
6 months old
new
4 years Yes
Bathurst 2 warehouse machines
(Desktops with POS
software installed)
3 years old 5 years 3.5 years
1 office machine 6 months old 4 years 2 years
Lithgow 2 counter machines
(Desktops with POS
software installed)
5 years old 4 years
1 office machine 6 months old 3 years Yes
4. Business continuity
In STP organization, business continuity is a process of maintain the essential function.
The planning of business continuity is easily establishing the risk management procedures
and processes that aim to prevent the network interruptions to re-establish and critical
services for organization functions (SearchDisasterRecovery, 2017). It is the very important
for STP organization because it maintain the overall organization functions for the disaster
duration. It first decided the essential of organization functions and assign the available
budget for the functions. It uses disk mirroring technologies to maintain the up to date copies
of data in STP organization. The STP organization conducting the business impact analysis
and it reveal the possible weaknesses and impact of a disaster on different departments. This
analysis is used to provide the most crucial functions and systems for an organization. It
provides the business continuity plan. It has following key elements such as,
• Recovery
• Contingency
8
Accounts machine 1 years old
Sydney 4 warehouses and 1
management desktop
The new machinery for
manufacturing comes with
its own system and is all
new.
6 months old
new
4 years Yes
Bathurst 2 warehouse machines
(Desktops with POS
software installed)
3 years old 5 years 3.5 years
1 office machine 6 months old 4 years 2 years
Lithgow 2 counter machines
(Desktops with POS
software installed)
5 years old 4 years
1 office machine 6 months old 3 years Yes
4. Business continuity
In STP organization, business continuity is a process of maintain the essential function.
The planning of business continuity is easily establishing the risk management procedures
and processes that aim to prevent the network interruptions to re-establish and critical
services for organization functions (SearchDisasterRecovery, 2017). It is the very important
for STP organization because it maintain the overall organization functions for the disaster
duration. It first decided the essential of organization functions and assign the available
budget for the functions. It uses disk mirroring technologies to maintain the up to date copies
of data in STP organization. The STP organization conducting the business impact analysis
and it reveal the possible weaknesses and impact of a disaster on different departments. This
analysis is used to provide the most crucial functions and systems for an organization. It
provides the business continuity plan. It has following key elements such as,
• Recovery
• Contingency
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

• Resilience
The Recovery elements is used to restore the business functions after disaster is crucial. It
easily setting the recovery time objectives for various systems, applications and network. It
can help to prioritize the key elements in the organization. It uses recovery technologies to
provide the organization activity. The technologies are resource inventories and agreement
with third parties. The contingency plan has the procedures to distribute the STP organization
responsibilities (Stallings, n.d.). It includes the leasing emergency office spaces, damage
assessment, contracting third party vendors and hardware replacement for assistance. The
STP organization should be increase the resilience by designing the critical infrastructure and
functions with different disaster possibilities. It includes the data redundancy, staffing
rotations and maintaining a surplus of capacity. It ensures the business essential services on
off site and location without interruptions. The business continuity plan was providing the
effective infrastructure for STP organization by provide the organization overall functions
and processes based on key elements.
5. Risk Management
In STP organization, risk managements require the organization to plan how to track,
manage and monitor the security risks because the STP organization connected to the internet
need to having their exposure to cyber-crime (SearchCompliance, 2017). The internet
vulnerabilities are allowing criminals to steal sensitive information or data in an organization.
Then access the organization data and information. Because the hackers are using the various
technology to get the organization information. The STP organization worry about the threat
of hackers and cyber criminals. The threats are unmanageable because it’s come from various
directions. Also, these threats are random attacks that can be stopped after they occurred and
it also expensive view to take. To resolve these threats by takes high level of effort and
expensive. So, the STP organization look to stop the gap measures to protect their
organization assets. It uses the risk management to avoid the threats. It reduces the exposures
to potential attacks and spread the risk between other organizations and departments. It easily
manages and retain the risk each time. finally, it presents the risks itself. The risk
management must start with looking at the border picture in the cyber-crime after towards to
reducing the risks to reasonable amounts of risks (Solarwindsmsp.com, 2017). The risk
management provides the organization by identifying, mitigating and prioritize the risk. The
STP organization risk management team follows the ISO standards and technology to
9
The Recovery elements is used to restore the business functions after disaster is crucial. It
easily setting the recovery time objectives for various systems, applications and network. It
can help to prioritize the key elements in the organization. It uses recovery technologies to
provide the organization activity. The technologies are resource inventories and agreement
with third parties. The contingency plan has the procedures to distribute the STP organization
responsibilities (Stallings, n.d.). It includes the leasing emergency office spaces, damage
assessment, contracting third party vendors and hardware replacement for assistance. The
STP organization should be increase the resilience by designing the critical infrastructure and
functions with different disaster possibilities. It includes the data redundancy, staffing
rotations and maintaining a surplus of capacity. It ensures the business essential services on
off site and location without interruptions. The business continuity plan was providing the
effective infrastructure for STP organization by provide the organization overall functions
and processes based on key elements.
5. Risk Management
In STP organization, risk managements require the organization to plan how to track,
manage and monitor the security risks because the STP organization connected to the internet
need to having their exposure to cyber-crime (SearchCompliance, 2017). The internet
vulnerabilities are allowing criminals to steal sensitive information or data in an organization.
Then access the organization data and information. Because the hackers are using the various
technology to get the organization information. The STP organization worry about the threat
of hackers and cyber criminals. The threats are unmanageable because it’s come from various
directions. Also, these threats are random attacks that can be stopped after they occurred and
it also expensive view to take. To resolve these threats by takes high level of effort and
expensive. So, the STP organization look to stop the gap measures to protect their
organization assets. It uses the risk management to avoid the threats. It reduces the exposures
to potential attacks and spread the risk between other organizations and departments. It easily
manages and retain the risk each time. finally, it presents the risks itself. The risk
management must start with looking at the border picture in the cyber-crime after towards to
reducing the risks to reasonable amounts of risks (Solarwindsmsp.com, 2017). The risk
management provides the organization by identifying, mitigating and prioritize the risk. The
STP organization risk management team follows the ISO standards and technology to
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

developing the risk management standards. The ISO technology and standards provides the
risks management methods to integrate the overall organization schema, factor risks into all
major decision making and monitor continuously risks in an organization. The Risk
management provides the STP organization risk details by identifying the risk categories and
descriptions. Once it identified the risk and implement the STP organization security policies
to protect the organization assets. After the risk management teams was provide the training
and awareness for organization employees and it helps to support the organization.
6. Conclusions
The STP organization has the more than one branch offices and head offices. These
are located at Wollongong, Lithgow, Sydney and Bathurst. The STP organization needs to
creates the effective organization. It sales the cupboard and drawer fronts. But current
infrastructure has two main problems. These are solved by using the business continuity plan.
It established the organization processes and operations. It Increase the organization
performances. The business continuity process was discussed in detail. The Planning for
purchases the hardware was analysed in detail. The Risk management strategy was analysed
and discussed.
7. Recommendations
The STP organization needs to implement the organization procedures and policies
that support the business continuity a strategy. It incorporates the consideration of security for
securing the data. After, organization limited use the wireless LAN and mobile devices to
reduce the risks. It provides the security protections for an organization. The STP
organization needs to create and manage the asset register to support the business continuity
and risk management processes. The hardware purchasing planning is needs to use the more
than 5 years because it reduce the operational costs and maintenance costs for an
organization. Also security plan needs to implement. The security plan implementation
provides the high security for an STP organization.
References
10
risks management methods to integrate the overall organization schema, factor risks into all
major decision making and monitor continuously risks in an organization. The Risk
management provides the STP organization risk details by identifying the risk categories and
descriptions. Once it identified the risk and implement the STP organization security policies
to protect the organization assets. After the risk management teams was provide the training
and awareness for organization employees and it helps to support the organization.
6. Conclusions
The STP organization has the more than one branch offices and head offices. These
are located at Wollongong, Lithgow, Sydney and Bathurst. The STP organization needs to
creates the effective organization. It sales the cupboard and drawer fronts. But current
infrastructure has two main problems. These are solved by using the business continuity plan.
It established the organization processes and operations. It Increase the organization
performances. The business continuity process was discussed in detail. The Planning for
purchases the hardware was analysed in detail. The Risk management strategy was analysed
and discussed.
7. Recommendations
The STP organization needs to implement the organization procedures and policies
that support the business continuity a strategy. It incorporates the consideration of security for
securing the data. After, organization limited use the wireless LAN and mobile devices to
reduce the risks. It provides the security protections for an organization. The STP
organization needs to create and manage the asset register to support the business continuity
and risk management processes. The hardware purchasing planning is needs to use the more
than 5 years because it reduce the operational costs and maintenance costs for an
organization. Also security plan needs to implement. The security plan implementation
provides the high security for an STP organization.
References
10

Hagan, M., Demuth, H., Beale, M. and De Jesús, O. (2016). Neural network design. [S. l.: s.
n.].
Kurose, J. and Ross, K. (n.d.). Computer networking.
NETworking. (2013). [Hong Kong]: Regional NET Coordinating Team, NET Section, CDI,
EDB.
Oppenheimer, P. (2011). Top-down network design. Indianapolis, Ind.: Cisco Press.
Schulz, G. (2017). Top 10 ways to secure your stored data. [online] Computerworld.
SearchCompliance. (2017). What is risk management? - Definition from WhatIs.com. [online]
Available at: http://searchcompliance.techtarget.com/definition/risk-management [Accessed
11 Oct. 2017].
SearchDisasterRecovery. (2017). What is business continuity and disaster recovery (BCDR)?
- Definition from WhatIs.com. [online] Available at:
http://searchdisasterrecovery.techtarget.com/definition/Business-Continuity-and-Disaster-
Recovery-BCDR [Accessed 11 Oct. 2017].
Solarwindsmsp.com. (2017). Risk Management In Network Security. [online] Available at:
https://www.solarwindsmsp.com/content/risk-management-in-network-security [Accessed 11
Oct. 2017].
Stallings, W. (n.d.). Network security essentials.
Thomas, T. (2012). Network security first-step. Indianapolis, Ind.: Cisco.
11
n.].
Kurose, J. and Ross, K. (n.d.). Computer networking.
NETworking. (2013). [Hong Kong]: Regional NET Coordinating Team, NET Section, CDI,
EDB.
Oppenheimer, P. (2011). Top-down network design. Indianapolis, Ind.: Cisco Press.
Schulz, G. (2017). Top 10 ways to secure your stored data. [online] Computerworld.
SearchCompliance. (2017). What is risk management? - Definition from WhatIs.com. [online]
Available at: http://searchcompliance.techtarget.com/definition/risk-management [Accessed
11 Oct. 2017].
SearchDisasterRecovery. (2017). What is business continuity and disaster recovery (BCDR)?
- Definition from WhatIs.com. [online] Available at:
http://searchdisasterrecovery.techtarget.com/definition/Business-Continuity-and-Disaster-
Recovery-BCDR [Accessed 11 Oct. 2017].
Solarwindsmsp.com. (2017). Risk Management In Network Security. [online] Available at:
https://www.solarwindsmsp.com/content/risk-management-in-network-security [Accessed 11
Oct. 2017].
Stallings, W. (n.d.). Network security essentials.
Thomas, T. (2012). Network security first-step. Indianapolis, Ind.: Cisco.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





