Analysis of Bell Studio's Strategic Information Systems (HI5019)
VerifiedAdded on 2022/12/22
|12
|2215
|88
Report
AI Summary
This report analyzes the Bell Studio case study, a company specializing in art supplies, focusing on its strategic information systems. It details the company's centralized accounting information system, including transaction cycles, financial and management reporting. The report presents data flow diagrams for purchases, cash disbursements, and payroll systems, along with system flowcharts for each. It identifies internal control weaknesses within the purchasing, cash disbursement, and payroll systems, and assesses the associated risks such as human error, system failures, and security vulnerabilities. The report concludes with recommendations for system improvements and enhanced risk mitigation strategies, emphasizing the need for a more advanced and secure information system to optimize business processes and profitability.

Running head: STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
Strategic Information for Business and Enterprise
Name of Student-
Name of University-
Author’s Note
Strategic Information for Business and Enterprise
Name of Student-
Name of University-
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
Executive Summary
The case study in this report states the working procedure of the Bell Studio. The
company is the largest supplier of art materials and imports their raw materials from the
different other countries. The company follows a centralized accounting information
system that includes the transaction cycle, the management reporting and the other
accounts reports in the organization. The centralized accounting information has some
weakness internally and those risks are introduced in this report. Along with the internal
weakness, there are many risks that are associated with the central information system.
This report consists of data flow diagrams of the accounting system and the system
flowchart that are included in the Bell Studio.
Executive Summary
The case study in this report states the working procedure of the Bell Studio. The
company is the largest supplier of art materials and imports their raw materials from the
different other countries. The company follows a centralized accounting information
system that includes the transaction cycle, the management reporting and the other
accounts reports in the organization. The centralized accounting information has some
weakness internally and those risks are introduced in this report. Along with the internal
weakness, there are many risks that are associated with the central information system.
This report consists of data flow diagrams of the accounting system and the system
flowchart that are included in the Bell Studio.

2STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
Table of Contents
Introduction........................................................................................................................2
Data Flow Diagram of Purchases and Cash Disbursements Systems.............................3
Data Flow Diagram of Payroll System...............................................................................4
System Flowchart of Purchases System...........................................................................5
System Flowchart of Cash Disbursements System..........................................................6
System Flowchart of Payroll System.................................................................................7
Internal Control Weakness and Risk Associated..............................................................8
Conclusion.........................................................................................................................9
Bibliography.....................................................................................................................10
Table of Contents
Introduction........................................................................................................................2
Data Flow Diagram of Purchases and Cash Disbursements Systems.............................3
Data Flow Diagram of Payroll System...............................................................................4
System Flowchart of Purchases System...........................................................................5
System Flowchart of Cash Disbursements System..........................................................6
System Flowchart of Payroll System.................................................................................7
Internal Control Weakness and Risk Associated..............................................................8
Conclusion.........................................................................................................................9
Bibliography.....................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
1. Introduction
Business analyst has the role of developing the technical solutions that are
included in the system or provide those solutions that helps to advance the sales of the
company, analyses the documents related to business requirements, and helps to fulfil
all the needs of the business. A business analyst plays the lead role in conducting the
business process. The case involved in this report is the business case of Bell Studio.
The Bell Studio is famous company for serving the people with art suppliers. The
organization uses strategic information system for conducting its business processes.
This report details the business that is conducted by the organization. The
organization follows traditional business process to conduct it businesses. This report
elaborates the business procedure in the form of data flow diagram for all systems that
are included in Bell Studio. This report states the transaction cycle of the system, the
way by which financial reporting is done in the business and how the reports are
managed in the business system. The following report states the weakness of business
processes that are carried out in the organization. As the business follows accounting
information system, the internal weaknesses brings many risks in the organization and
those risks are also described in this particular report. As a business analyst of the Bell
Studio, this report is being written for describing the working procedure of the company.
1. Introduction
Business analyst has the role of developing the technical solutions that are
included in the system or provide those solutions that helps to advance the sales of the
company, analyses the documents related to business requirements, and helps to fulfil
all the needs of the business. A business analyst plays the lead role in conducting the
business process. The case involved in this report is the business case of Bell Studio.
The Bell Studio is famous company for serving the people with art suppliers. The
organization uses strategic information system for conducting its business processes.
This report details the business that is conducted by the organization. The
organization follows traditional business process to conduct it businesses. This report
elaborates the business procedure in the form of data flow diagram for all systems that
are included in Bell Studio. This report states the transaction cycle of the system, the
way by which financial reporting is done in the business and how the reports are
managed in the business system. The following report states the weakness of business
processes that are carried out in the organization. As the business follows accounting
information system, the internal weaknesses brings many risks in the organization and
those risks are also described in this particular report. As a business analyst of the Bell
Studio, this report is being written for describing the working procedure of the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
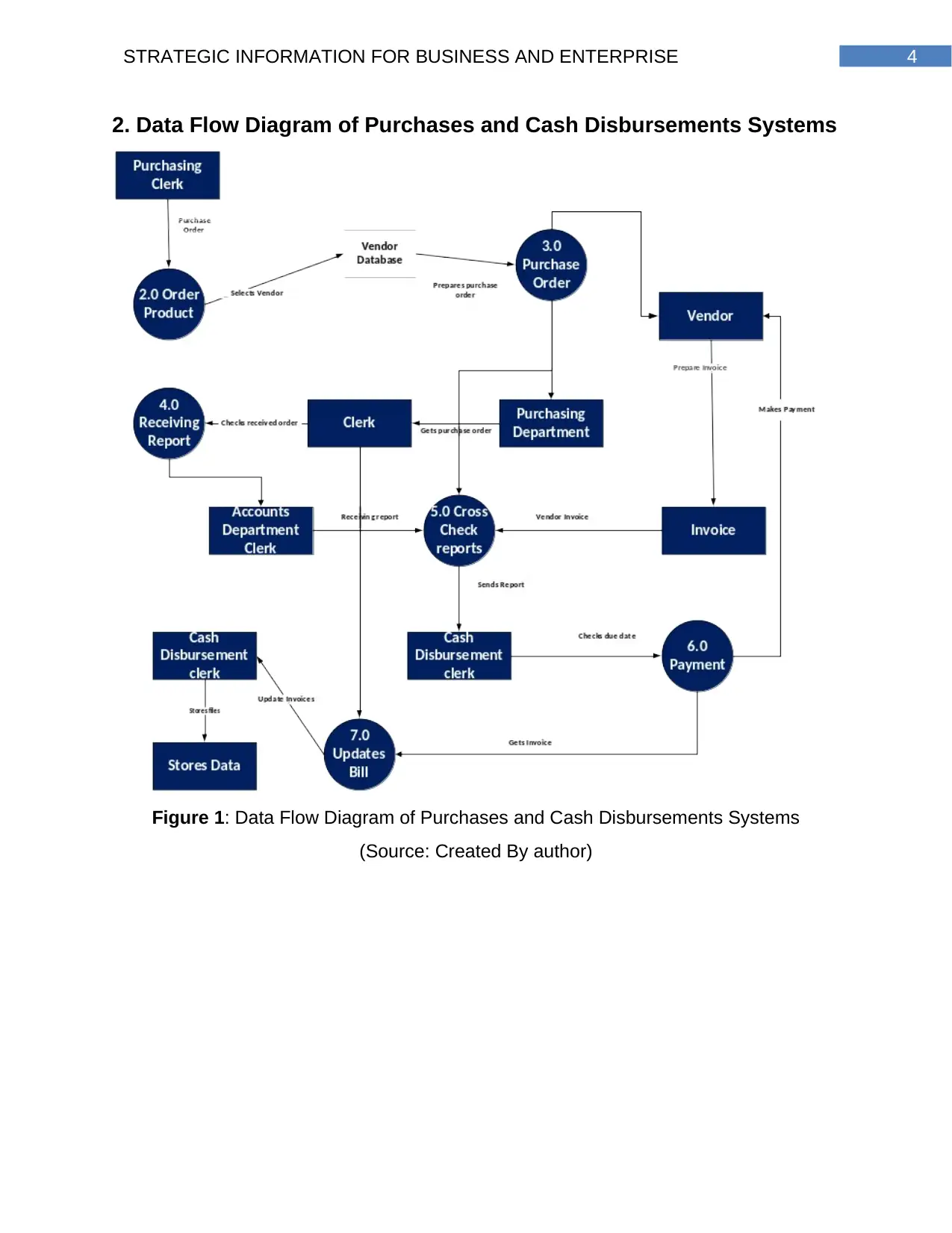
2. Data Flow Diagram of Purchases and Cash Disbursements Systems
Figure 1: Data Flow Diagram of Purchases and Cash Disbursements Systems
(Source: Created By author)
2. Data Flow Diagram of Purchases and Cash Disbursements Systems
Figure 1: Data Flow Diagram of Purchases and Cash Disbursements Systems
(Source: Created By author)
5STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
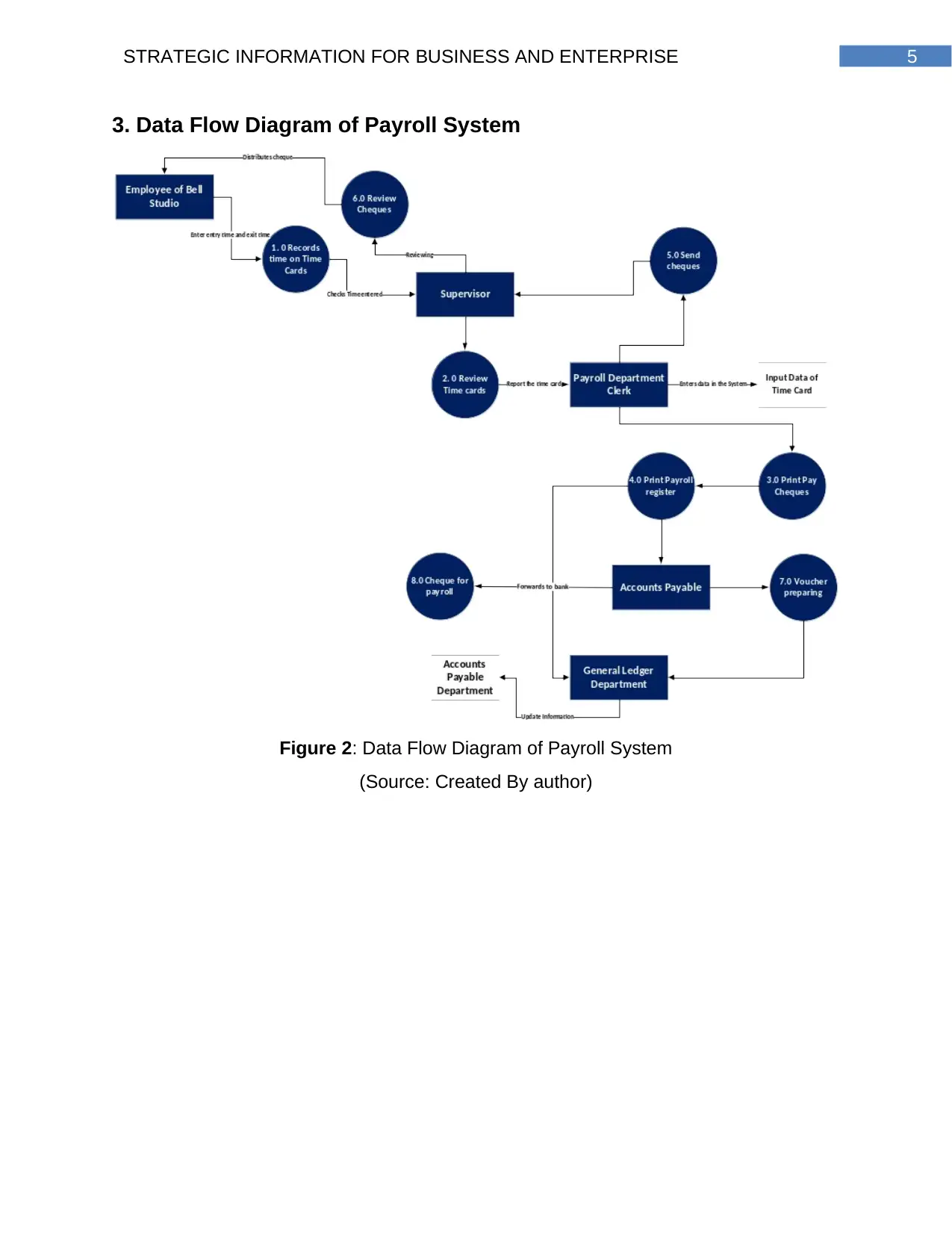
3. Data Flow Diagram of Payroll System
Figure 2: Data Flow Diagram of Payroll System
(Source: Created By author)
3. Data Flow Diagram of Payroll System
Figure 2: Data Flow Diagram of Payroll System
(Source: Created By author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
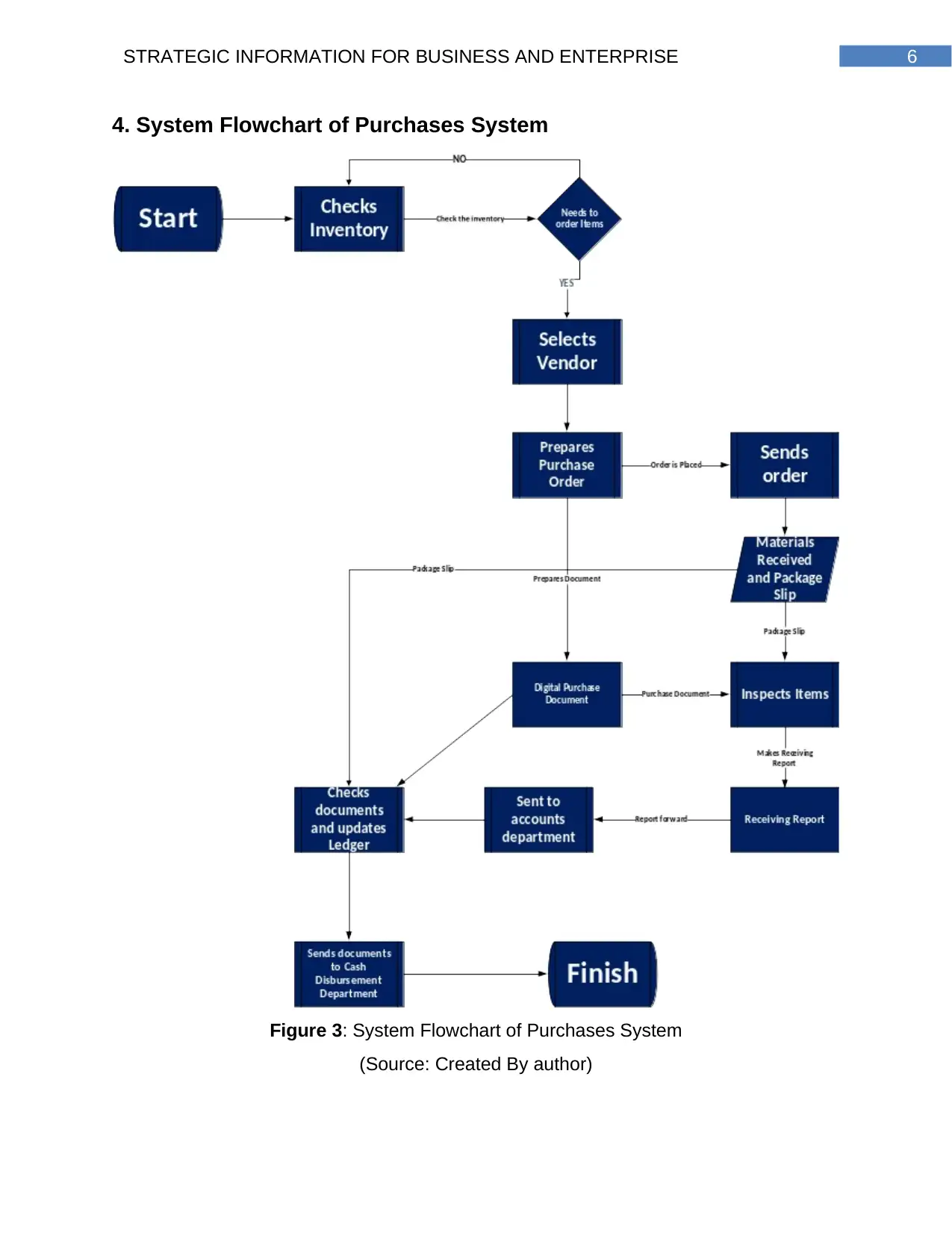
4. System Flowchart of Purchases System
Figure 3: System Flowchart of Purchases System
(Source: Created By author)
4. System Flowchart of Purchases System
Figure 3: System Flowchart of Purchases System
(Source: Created By author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
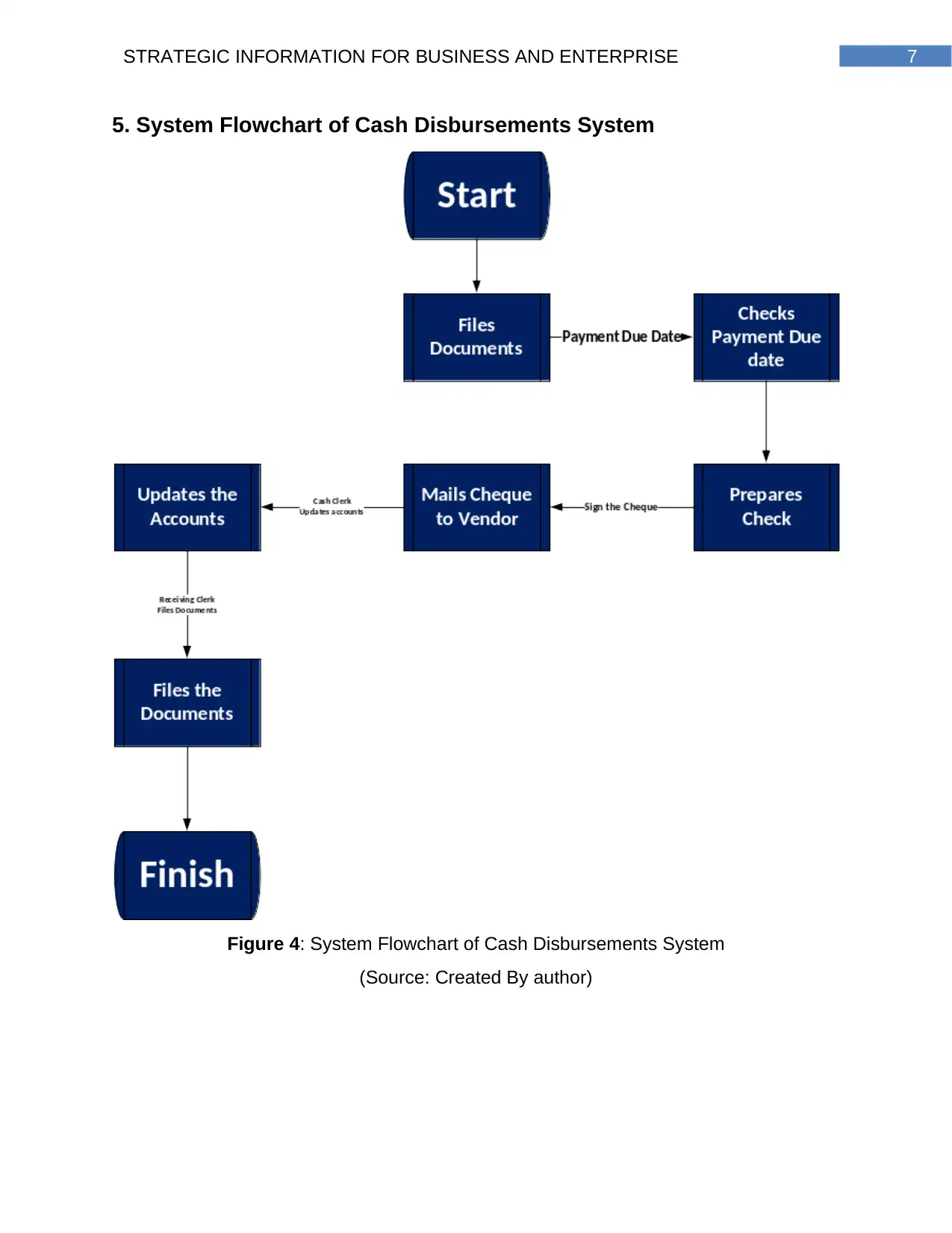
5. System Flowchart of Cash Disbursements System
Figure 4: System Flowchart of Cash Disbursements System
(Source: Created By author)
5. System Flowchart of Cash Disbursements System
Figure 4: System Flowchart of Cash Disbursements System
(Source: Created By author)
8STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
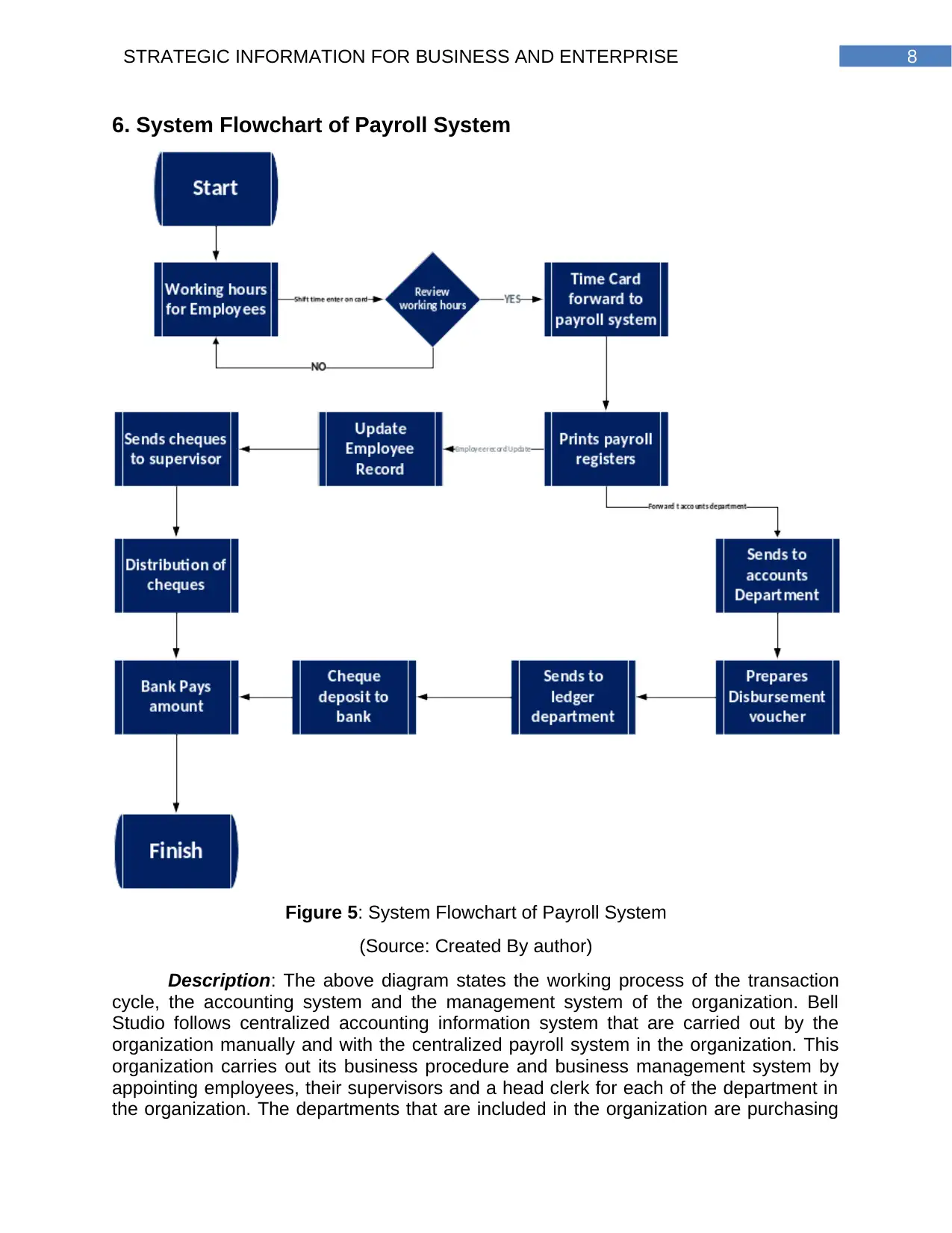
6. System Flowchart of Payroll System
Figure 5: System Flowchart of Payroll System
(Source: Created By author)
Description: The above diagram states the working process of the transaction
cycle, the accounting system and the management system of the organization. Bell
Studio follows centralized accounting information system that are carried out by the
organization manually and with the centralized payroll system in the organization. This
organization carries out its business procedure and business management system by
appointing employees, their supervisors and a head clerk for each of the department in
the organization. The departments that are included in the organization are purchasing
6. System Flowchart of Payroll System
Figure 5: System Flowchart of Payroll System
(Source: Created By author)
Description: The above diagram states the working process of the transaction
cycle, the accounting system and the management system of the organization. Bell
Studio follows centralized accounting information system that are carried out by the
organization manually and with the centralized payroll system in the organization. This
organization carries out its business procedure and business management system by
appointing employees, their supervisors and a head clerk for each of the department in
the organization. The departments that are included in the organization are purchasing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
department, receiving department, payroll department, accounting system and the
management system of all the processes that are included in the Bell Studio. The above
diagrams shows the details of the business case included in the organization. The data
that flows in the organization are shown in the data flow diagram of the payroll system,
the cash disbursement system, and the purchasing system. The above diagram also
shows the system flowchart that are included in the organization.
The system flowchart shows the working process of the system included in the
organization. The flowchart also shows starting and ending of a particular process with
all the processes and the input and output of the system.
7. Internal Control Weakness and Risk Associated
Purchasing system of the organization:
Internal Control Weakness: The internal control weakness of the system are
listed in the point below.
1. The purchasing process of the Bell Studio depends on the purchasing clerk of the
system and if the purchasing clerk is not able to maintain the system, the whole process
will slow down (Rao, Guo and Chen 2015).
2. The security of the system that is include in the Bell Studio is also not updated. The
organization use one centralized system for conducting the business procedure.
3. The purchasing is done through mail and that might face problem as a security issue.
Hacking can occur in the system and that can bring intruder to the company.
Risks Associated with the system: The weakness associated with the system
has many internal weakness. The internal weakness might lead to risks in the company.
The risks that can occur in the organization are stated below:
1. Human risks; as the system depends on the purchasing clerk, there is always a risk
of human error in the organization (Zimmermann, Rentrop and Felden 2016).
2. System failure risk; as the system uses centralized system for the internal
procedures, there is a risk of system failure. The system might fail at any time (Sun
2016).
3. Security risk; the purchasing system is carried out through mail and that might lead to
security issue in the organization (Haislip et al. 2015).
Cash Disbursement system of the organization:
Internal Control Weakness: The internal weakness that occurs while carrying
out the cash disbursement are listed below.
1. The payment is done in cheque which makes the process lengthy. The printing of
cheques, signing of cheques, and putting digital value causes internal weakness of the
system (Feeney and Pierce 2016).
department, receiving department, payroll department, accounting system and the
management system of all the processes that are included in the Bell Studio. The above
diagrams shows the details of the business case included in the organization. The data
that flows in the organization are shown in the data flow diagram of the payroll system,
the cash disbursement system, and the purchasing system. The above diagram also
shows the system flowchart that are included in the organization.
The system flowchart shows the working process of the system included in the
organization. The flowchart also shows starting and ending of a particular process with
all the processes and the input and output of the system.
7. Internal Control Weakness and Risk Associated
Purchasing system of the organization:
Internal Control Weakness: The internal control weakness of the system are
listed in the point below.
1. The purchasing process of the Bell Studio depends on the purchasing clerk of the
system and if the purchasing clerk is not able to maintain the system, the whole process
will slow down (Rao, Guo and Chen 2015).
2. The security of the system that is include in the Bell Studio is also not updated. The
organization use one centralized system for conducting the business procedure.
3. The purchasing is done through mail and that might face problem as a security issue.
Hacking can occur in the system and that can bring intruder to the company.
Risks Associated with the system: The weakness associated with the system
has many internal weakness. The internal weakness might lead to risks in the company.
The risks that can occur in the organization are stated below:
1. Human risks; as the system depends on the purchasing clerk, there is always a risk
of human error in the organization (Zimmermann, Rentrop and Felden 2016).
2. System failure risk; as the system uses centralized system for the internal
procedures, there is a risk of system failure. The system might fail at any time (Sun
2016).
3. Security risk; the purchasing system is carried out through mail and that might lead to
security issue in the organization (Haislip et al. 2015).
Cash Disbursement system of the organization:
Internal Control Weakness: The internal weakness that occurs while carrying
out the cash disbursement are listed below.
1. The payment is done in cheque which makes the process lengthy. The printing of
cheques, signing of cheques, and putting digital value causes internal weakness of the
system (Feeney and Pierce 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
2. As the updating of the payroll register, the employees account and the ledger is done
by the clerks of the respective department. That can be considered as internal
weakness of the system (Kim, Lee and Park 2016).
Risks Associated with the system:
1. Process slow down; the process of the cash disbursement might slow down as the
process involves signing the cheques and the printing the cheques (Gallemore and
Labro 2015).
2. Human error; while updating the register and updating the system human error might
occur accidently (Heeks 2017).
3. Password theft; the user id and password of the clerk for the centralized system
might be hacked (Ji, Lu and Qu 2017).
Payroll system of the organization: The internal weakness that occurs while
carrying out the payroll system are listed below.
1. The employees use time cards to enter their duty hours in the office and that is one of
the biggest internal weakness of the system.
2. Hard copy of the payroll registers is handled manually and that register might get lost
or misplaced (Duncan and Whittington 2016).
Risks Associated with the system:
1. Staff dishonesty; as the employees enter their timing themselves in the system that
might lead to a risk of staff risk. The staffs might not enter the time properly (Chen et al.
2016).
2. System failure; the central information payroll system might fail because of the not
updating the system at the required time (Chalmers, Hay and Khlif 2019).
8. Conclusion
There are many risks that occurs in the system and the risks occurs because of
the internal workflow weakness of the system. The business system in the organization
follows centralized payroll system that included including the purchasing system, the
management system and the transaction system.
The risks that can occur because of the internal weakness are also stated in the
report. The report shows the internal workflow of all the system along with the internal
workflow of the system. There is a payment system in the organization, and there is
also a purchasing system in the system. The data flow of the payment system and the
data flow of the purchasing system is included in this report. As a business analyst of
Bell Studio, new improved system is to be included in the system for making its
procedure more advanced and making more profit from the system.
This report details states the data flow diagram of three working process of the
organization including the purchasing system, the payroll system and the cash
disbursement system of the organization. The system flowchart of all three systems that
2. As the updating of the payroll register, the employees account and the ledger is done
by the clerks of the respective department. That can be considered as internal
weakness of the system (Kim, Lee and Park 2016).
Risks Associated with the system:
1. Process slow down; the process of the cash disbursement might slow down as the
process involves signing the cheques and the printing the cheques (Gallemore and
Labro 2015).
2. Human error; while updating the register and updating the system human error might
occur accidently (Heeks 2017).
3. Password theft; the user id and password of the clerk for the centralized system
might be hacked (Ji, Lu and Qu 2017).
Payroll system of the organization: The internal weakness that occurs while
carrying out the payroll system are listed below.
1. The employees use time cards to enter their duty hours in the office and that is one of
the biggest internal weakness of the system.
2. Hard copy of the payroll registers is handled manually and that register might get lost
or misplaced (Duncan and Whittington 2016).
Risks Associated with the system:
1. Staff dishonesty; as the employees enter their timing themselves in the system that
might lead to a risk of staff risk. The staffs might not enter the time properly (Chen et al.
2016).
2. System failure; the central information payroll system might fail because of the not
updating the system at the required time (Chalmers, Hay and Khlif 2019).
8. Conclusion
There are many risks that occurs in the system and the risks occurs because of
the internal workflow weakness of the system. The business system in the organization
follows centralized payroll system that included including the purchasing system, the
management system and the transaction system.
The risks that can occur because of the internal weakness are also stated in the
report. The report shows the internal workflow of all the system along with the internal
workflow of the system. There is a payment system in the organization, and there is
also a purchasing system in the system. The data flow of the payment system and the
data flow of the purchasing system is included in this report. As a business analyst of
Bell Studio, new improved system is to be included in the system for making its
procedure more advanced and making more profit from the system.
This report details states the data flow diagram of three working process of the
organization including the purchasing system, the payroll system and the cash
disbursement system of the organization. The system flowchart of all three systems that

11STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
refers the working process of the system are shown in this report. Lastly, the weakness
of all the system stated above are identified and the related risks of the identified
system are discussed in a table format.
Reference
Chalmers, K., Hay, D. and Khlif, H., 2019. Internal control in accounting research: A
review. Journal of Accounting Literature, 42, pp.80-103.
Chen, Y., Knechel, W.R., Marisetty, V.B., Truong, C. and Veeraraghavan, M., 2016.
Board independence and internal control weakness: Evidence from SOX 404
disclosures. Auditing: A Journal of Practice & Theory, 36(2), pp.45-62.
Duncan, R.A.K. and Whittington, M., 2016. Enhancing cloud security and privacy: the
power and the weakness of the audit trail. CLOUD COMPUTING 2016.
Feeney, O. and Pierce, B., 2016. Strong structuration theory and accounting
information: an empirical study. Accounting, auditing & accountability journal, 29(7),
pp.1152-1176.
Gallemore, J. and Labro, E., 2015. The importance of the internal information
environment for tax avoidance. Journal of Accounting and Economics, 60(1), pp.149-
167.
Haislip, J.Z., Masli, A., Richardson, V.J. and Sanchez, J.M., 2015. Repairing
organizational legitimacy following information technology (IT) material weaknesses:
Executive turnover, IT expertise, and IT system upgrades. Journal of Information
Systems, 30(1), pp.41-70.
Heeks, R., 2017. Information technology, information systems and public sector
accountability. In Information Technology in Context: Studies from the Perspective of
Developing Countries (pp. 201-219). Routledge.
Ji, X.D., Lu, W. and Qu, W., 2017. Voluntary disclosure of internal control weakness and
earnings quality: Evidence from China. The International Journal of Accounting, 52(1),
pp.27-44.
Kim, J.B., Lee, J.J. and Park, J.C., 2016. Internal control weakness and the
asymmetrical behavior of selling, general, and administrative costs. General, and
Administrative Costs (December 3, 2016).
Rao, Y., Guo, K.H. and Chen, Y., 2015. Information systems maturity, knowledge
sharing, and firm performance. International Journal of Accounting & Information
Management, 23(2), pp.106-127.
Sun, Y., 2016. Internal control weakness disclosure and firm investment. Journal of
Accounting, Auditing & Finance, 31(2), pp.277-307.
Zimmermann, S., Rentrop, C. and Felden, C., 2016. A multiple case study on the nature
and management of shadow information technology. Journal of Information
Systems, 31(1), pp.79-101.
refers the working process of the system are shown in this report. Lastly, the weakness
of all the system stated above are identified and the related risks of the identified
system are discussed in a table format.
Reference
Chalmers, K., Hay, D. and Khlif, H., 2019. Internal control in accounting research: A
review. Journal of Accounting Literature, 42, pp.80-103.
Chen, Y., Knechel, W.R., Marisetty, V.B., Truong, C. and Veeraraghavan, M., 2016.
Board independence and internal control weakness: Evidence from SOX 404
disclosures. Auditing: A Journal of Practice & Theory, 36(2), pp.45-62.
Duncan, R.A.K. and Whittington, M., 2016. Enhancing cloud security and privacy: the
power and the weakness of the audit trail. CLOUD COMPUTING 2016.
Feeney, O. and Pierce, B., 2016. Strong structuration theory and accounting
information: an empirical study. Accounting, auditing & accountability journal, 29(7),
pp.1152-1176.
Gallemore, J. and Labro, E., 2015. The importance of the internal information
environment for tax avoidance. Journal of Accounting and Economics, 60(1), pp.149-
167.
Haislip, J.Z., Masli, A., Richardson, V.J. and Sanchez, J.M., 2015. Repairing
organizational legitimacy following information technology (IT) material weaknesses:
Executive turnover, IT expertise, and IT system upgrades. Journal of Information
Systems, 30(1), pp.41-70.
Heeks, R., 2017. Information technology, information systems and public sector
accountability. In Information Technology in Context: Studies from the Perspective of
Developing Countries (pp. 201-219). Routledge.
Ji, X.D., Lu, W. and Qu, W., 2017. Voluntary disclosure of internal control weakness and
earnings quality: Evidence from China. The International Journal of Accounting, 52(1),
pp.27-44.
Kim, J.B., Lee, J.J. and Park, J.C., 2016. Internal control weakness and the
asymmetrical behavior of selling, general, and administrative costs. General, and
Administrative Costs (December 3, 2016).
Rao, Y., Guo, K.H. and Chen, Y., 2015. Information systems maturity, knowledge
sharing, and firm performance. International Journal of Accounting & Information
Management, 23(2), pp.106-127.
Sun, Y., 2016. Internal control weakness disclosure and firm investment. Journal of
Accounting, Auditing & Finance, 31(2), pp.277-307.
Zimmermann, S., Rentrop, C. and Felden, C., 2016. A multiple case study on the nature
and management of shadow information technology. Journal of Information
Systems, 31(1), pp.79-101.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




