Bell Studio Case Study: Analyzing Security Risks and Weaknesses
VerifiedAdded on 2023/01/04
|15
|2406
|46
Case Study
AI Summary
This case study report analyzes the security vulnerabilities of Bell Studio, focusing on its weaknesses in various transaction cycles, financial reporting, and management reporting systems. The report identifies potential risks, including unauthorized access, spoofing, and sniffing, and examines the impact of these threats on the organization. Data flow diagrams and system flowcharts are used to illustrate the processes and highlight areas of concern within the payroll, purchasing, and cash disbursement systems. The report emphasizes the need for improved security measures and internal controls to mitigate risks and protect sensitive data. It explores the potential for computer fraud and the importance of ethical considerations in managing information systems, concluding with a discussion of the various threats faced by the company and the importance of addressing system vulnerabilities.

Running head: BELL STUDIO
BELL STUDIO
Name of the Student
Name of the University
Author’s Note
BELL STUDIO
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BELL STUDIO
Table of Contents
Introduction................................................................................................................................3
Weaknesses and connected risks................................................................................................5
Unauthorized access...............................................................................................................5
Spoofing and Sniffing............................................................................................................6
Conclusion..................................................................................................................................8
Table of Contents
Introduction................................................................................................................................3
Weaknesses and connected risks................................................................................................5
Unauthorized access...............................................................................................................5
Spoofing and Sniffing............................................................................................................6
Conclusion..................................................................................................................................8

2BELL STUDIO
1.0 Introduction
Organization faces security threats all around the clock. This report highlights the
condition of Bell Studio and evaluates the potential risks the company faces and the intrinsic
control for the expenditure cycle. The discussion briefly points out the major internal
weakness in each of the system of the organization and the potential risks associated with it.
The report concluded with the information of various threats that are faced by the company.
The flow chart as well as the data flow diagram of the various departments of the
organization is provided in this report for the analysis of the working of the processes of the
organization.
1.0 Introduction
Organization faces security threats all around the clock. This report highlights the
condition of Bell Studio and evaluates the potential risks the company faces and the intrinsic
control for the expenditure cycle. The discussion briefly points out the major internal
weakness in each of the system of the organization and the potential risks associated with it.
The report concluded with the information of various threats that are faced by the company.
The flow chart as well as the data flow diagram of the various departments of the
organization is provided in this report for the analysis of the working of the processes of the
organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3BELL STUDIO
2.0 Discussion
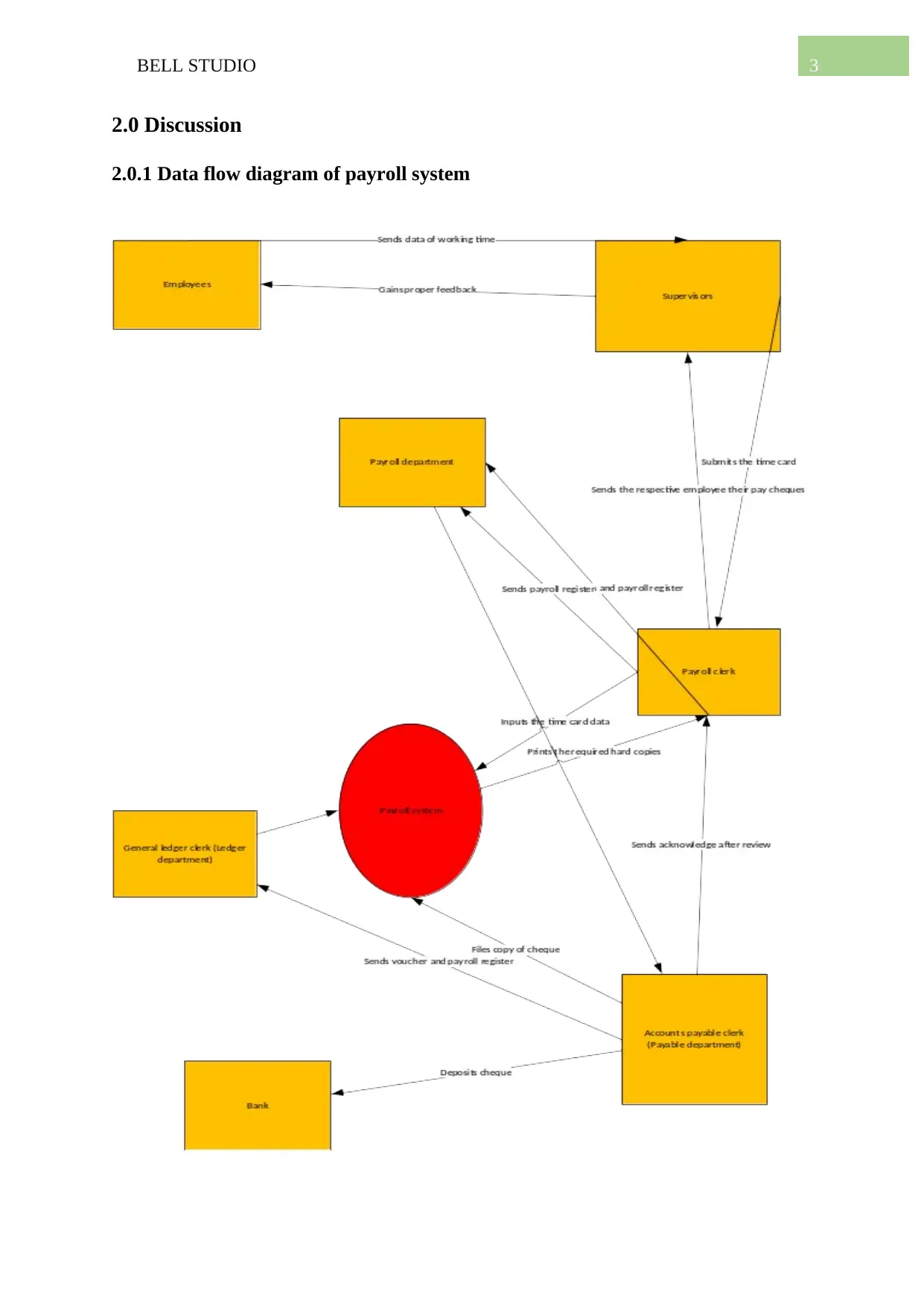
2.0.1 Data flow diagram of payroll system
2.0 Discussion
2.0.1 Data flow diagram of payroll system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4BELL STUDIO
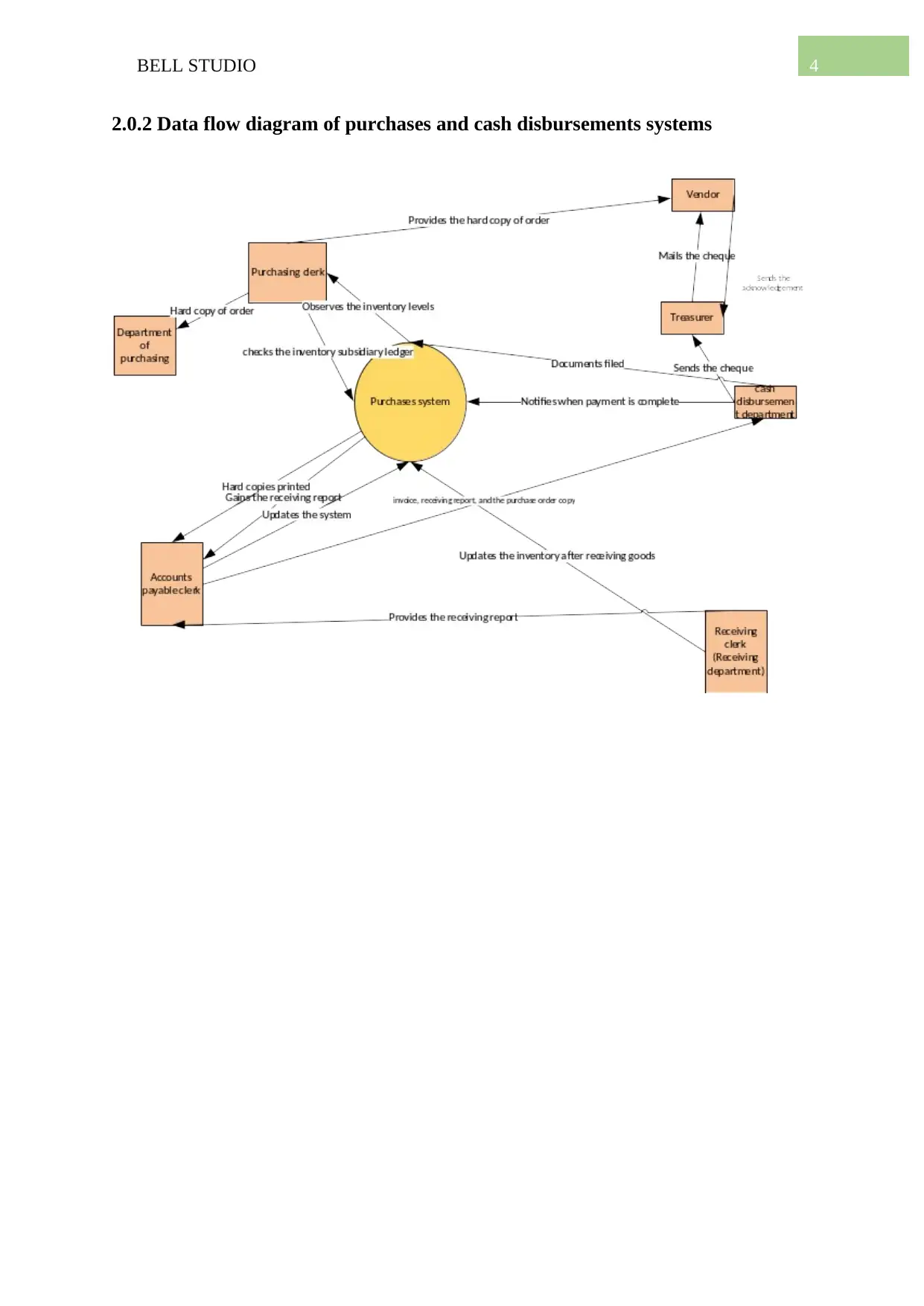
2.0.2 Data flow diagram of purchases and cash disbursements systems
2.0.2 Data flow diagram of purchases and cash disbursements systems
5BELL STUDIO
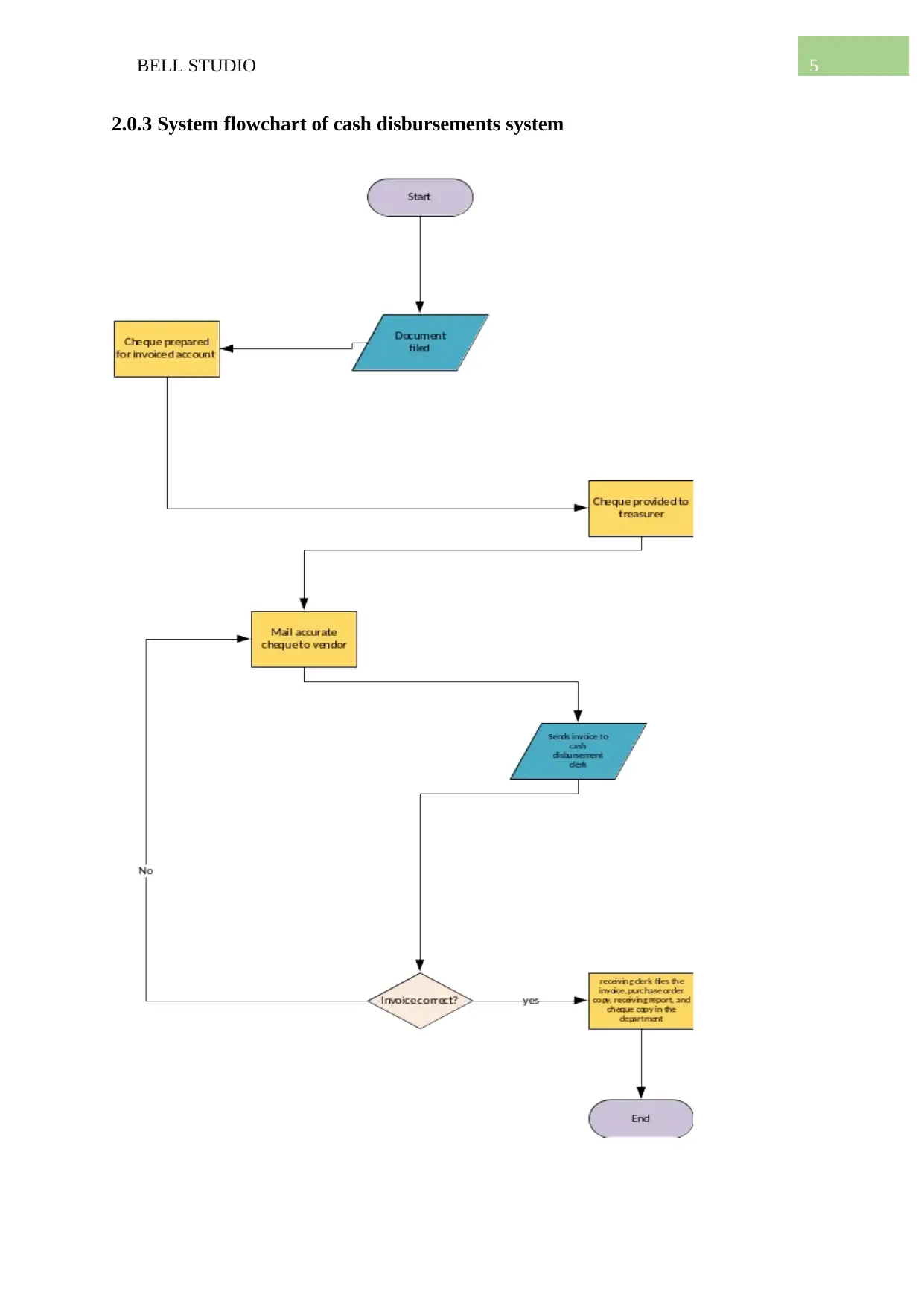
2.0.3 System flowchart of cash disbursements system
2.0.3 System flowchart of cash disbursements system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6BELL STUDIO
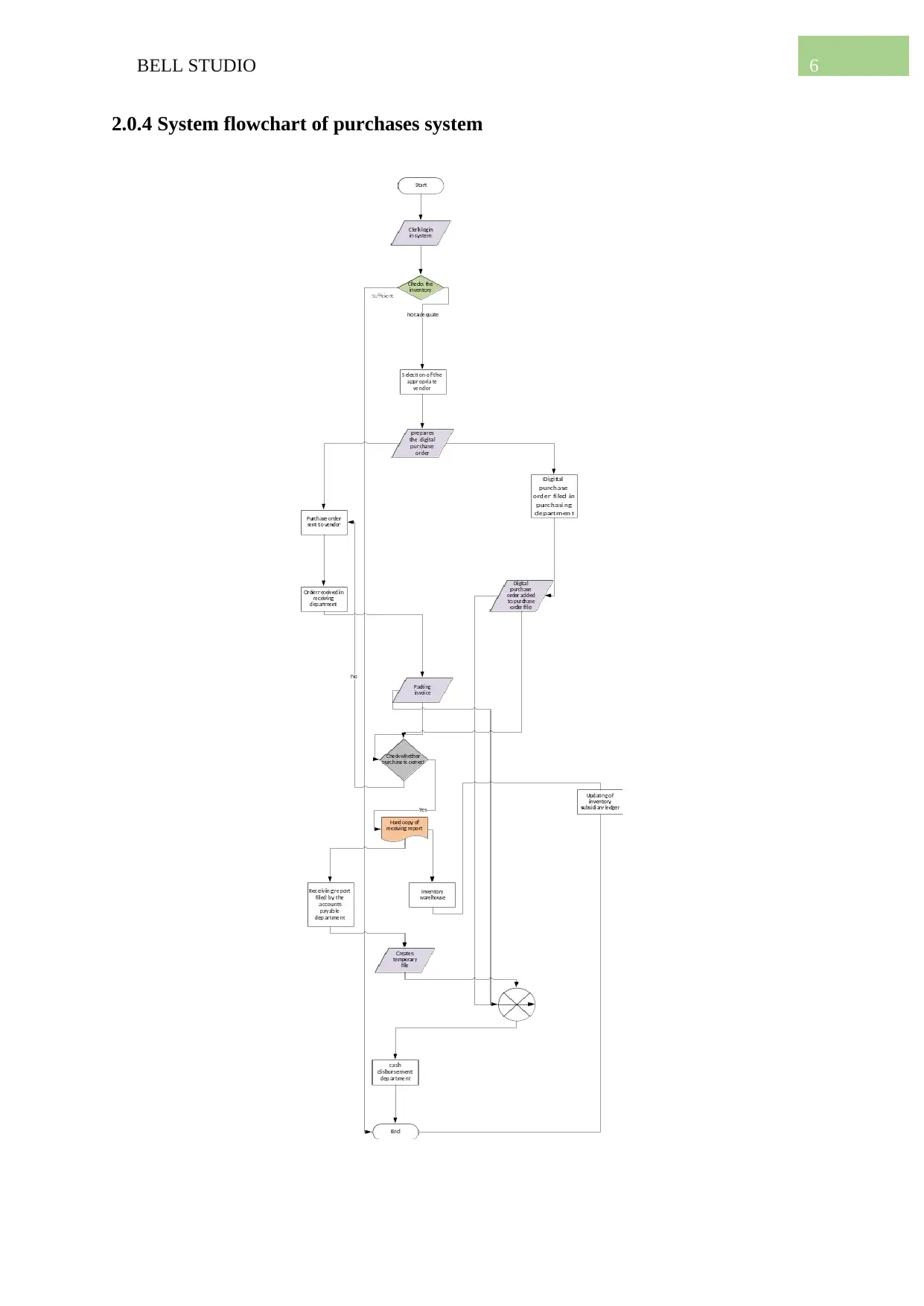
2.0.4 System flowchart of purchases system
2.0.4 System flowchart of purchases system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7BELL STUDIO
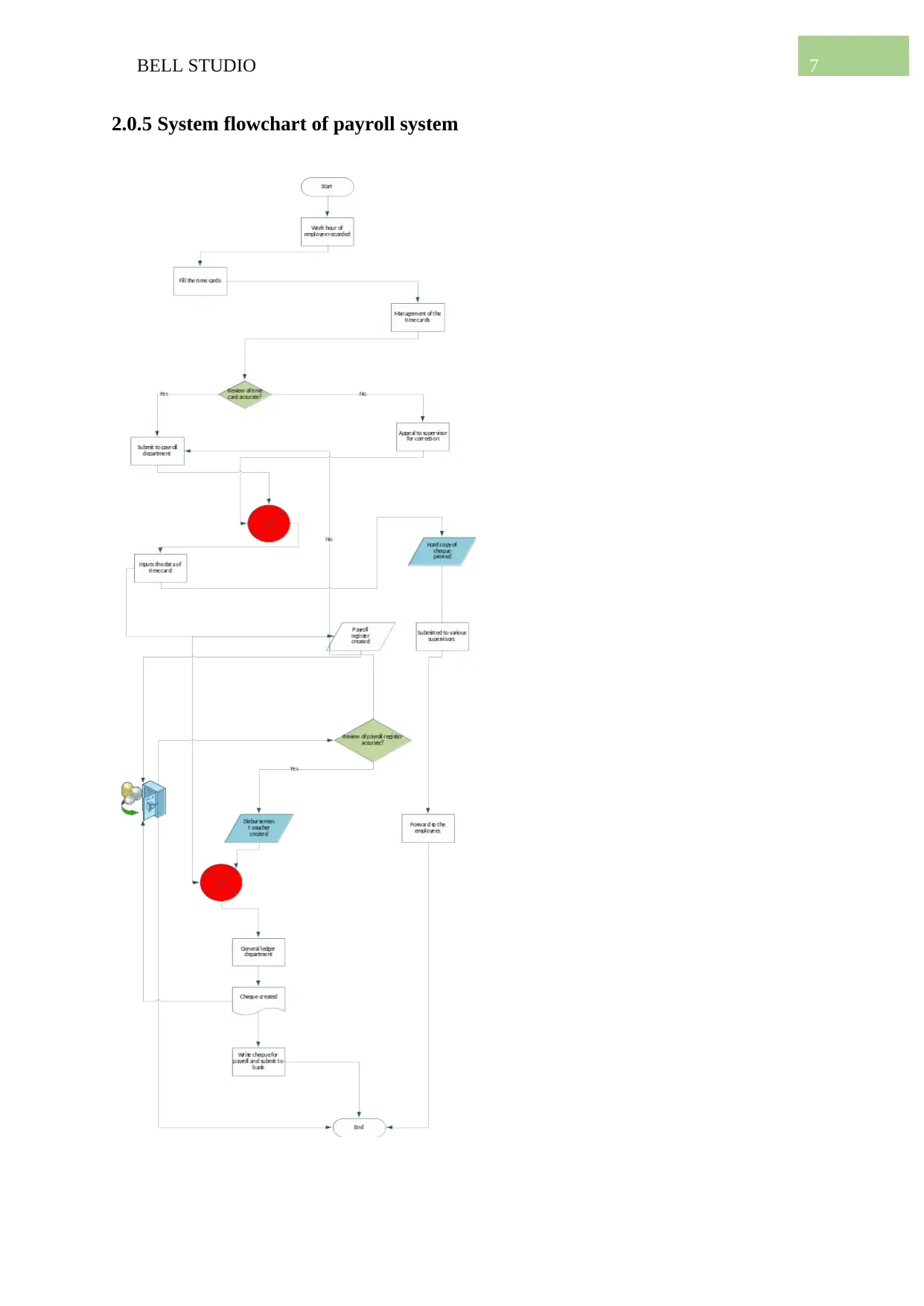
2.0.5 System flowchart of payroll system
2.0.5 System flowchart of payroll system

8BELL STUDIO
2.0.6 Weaknesses and connected risks
It is observed that there are numerous weaknesses in the purchase system, payroll
system and in the disbursement system of cash. For the smooth functioning of the enterprise,
the weaknesses cannot be ignored and there is an immediate need for proper assessment of
the risks involved. The following are the weaknesses that are related to the system, they are
as follows:
The complexity and the significance of the purchasing system and the cash
disbursement system denotes that there can be changes which when implemented on the
system can lead to disruptions in operations on the manner as how it has been deployed on
the system. Administrators might choose delay updates or the segmentation to prevent any
kind of downtime and process shut down. The outdated structures of the enterprise would be
lagging behind on the crucial patches so that suspension of the updates might subject the
system of the enterprise at potential risk. The gaps identified can stay in the system for years
in incognito mode and the security patches in the software would extend the danger.
The weaknesses in the software of the system in the enterprise possess significant risk
of external threats as the system becomes vulnerable. The vulnerability in the system leads to
major risk for the enterprise. The hardcopies of the enterprise can also face risk of loss of
sensitive data. The computer system which stores the invoices, that data might be facing risk
as well. A hacker could easily find out means to get the information out of the system, the
methods of data handling the enterprise and its storage location. There are other reports in the
system of the enterprise which contains valuable data about the enterprise. If the system is
managed poorly, the vulnerabilities in the system will lead to threats of data loss or theft of
2.0.6 Weaknesses and connected risks
It is observed that there are numerous weaknesses in the purchase system, payroll
system and in the disbursement system of cash. For the smooth functioning of the enterprise,
the weaknesses cannot be ignored and there is an immediate need for proper assessment of
the risks involved. The following are the weaknesses that are related to the system, they are
as follows:
The complexity and the significance of the purchasing system and the cash
disbursement system denotes that there can be changes which when implemented on the
system can lead to disruptions in operations on the manner as how it has been deployed on
the system. Administrators might choose delay updates or the segmentation to prevent any
kind of downtime and process shut down. The outdated structures of the enterprise would be
lagging behind on the crucial patches so that suspension of the updates might subject the
system of the enterprise at potential risk. The gaps identified can stay in the system for years
in incognito mode and the security patches in the software would extend the danger.
The weaknesses in the software of the system in the enterprise possess significant risk
of external threats as the system becomes vulnerable. The vulnerability in the system leads to
major risk for the enterprise. The hardcopies of the enterprise can also face risk of loss of
sensitive data. The computer system which stores the invoices, that data might be facing risk
as well. A hacker could easily find out means to get the information out of the system, the
methods of data handling the enterprise and its storage location. There are other reports in the
system of the enterprise which contains valuable data about the enterprise. If the system is
managed poorly, the vulnerabilities in the system will lead to threats of data loss or theft of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BELL STUDIO
confidential data. The policies and regulations need to be strengthened to respond to security
breaches in the network system.
The weaknesses in the systems are the gateways for the attackers to enter into the
system and hamper the working of the system. Such leak ways need to identified and focused
on to provide extensive protection for the same. Since the business is utilization outdated
system modules, the software is subjected to severe security threats and there is a probable
chance of exploitation of data. Data can be easily siphoned in such a case where the
information is unsecured. An additional weakness of the enterprise is the culture of the work
which further adds to the weaknesses of the system in the enterprise. When company polices
are not abided by the employees of the enterprise, the situation lead to opening of more
vulnerable spots in the system of the enterprise.
Unauthorized access
The common risk for any enterprise or organization in the information system of the
company is unauthorized access of sensitive and confidential data. Unauthorized access
creates major security risks and severe damage. The serious concerns evolves from the fact
that the attackers or the intruders can easily take the help of modern technologies and
methodologies to gain access into the system or may be disable the system of the
organization.
Malware and computer viruses are another set of risks for the organizational system.
The viruses are designed and developed with the motive to secretly plant them in the
computer system to gain access of the system in lieu of the security permissions and multiply
and duplicate quickly to spread in the entire system of the enterprise. The viruses can easily
confidential data. The policies and regulations need to be strengthened to respond to security
breaches in the network system.
The weaknesses in the systems are the gateways for the attackers to enter into the
system and hamper the working of the system. Such leak ways need to identified and focused
on to provide extensive protection for the same. Since the business is utilization outdated
system modules, the software is subjected to severe security threats and there is a probable
chance of exploitation of data. Data can be easily siphoned in such a case where the
information is unsecured. An additional weakness of the enterprise is the culture of the work
which further adds to the weaknesses of the system in the enterprise. When company polices
are not abided by the employees of the enterprise, the situation lead to opening of more
vulnerable spots in the system of the enterprise.
Unauthorized access
The common risk for any enterprise or organization in the information system of the
company is unauthorized access of sensitive and confidential data. Unauthorized access
creates major security risks and severe damage. The serious concerns evolves from the fact
that the attackers or the intruders can easily take the help of modern technologies and
methodologies to gain access into the system or may be disable the system of the
organization.
Malware and computer viruses are another set of risks for the organizational system.
The viruses are designed and developed with the motive to secretly plant them in the
computer system to gain access of the system in lieu of the security permissions and multiply
and duplicate quickly to spread in the entire system of the enterprise. The viruses can easily
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10BELL STUDIO
slow down the working of the system and result in system crash. Sometimes it has been
noticed that the virus attacks happened accidentally simply because of poor programming.
The damages done to the information systems in an enterprise might be executed on
purpose or the reason can be accidental or there can be selfish reasons or motive to cause
industrial sabotage. The insiders has the knowledge that offers immense capabilities to the
attackers to severely sabotage the working of the enterprises’ system. The entities that can
face the attacks are the hardware, altering data, infrastructure, incorrect data entered, software
deletion, logic bomb implementation and virus implementation. Selfish and deliberate
motives to damage the software, hardware and data of the enterprise can lead to data loss
which will in turn, turn out to be a major threat for the enterprise or the company. The minor
damages done to the system also adds to the sum of damages faced by the system of the
organization. Temporary denial of access is the sole reason for the threat of vandalism.
Human errors leads to the minor and major damages caused to the system. The accidental
damages can later be handled and saved from further escalations and disputes over a period
of time and this requires decent employee disposition. Human errors have the most
significant impact on the security of the organizational system more that purposeful manmade
threats and attacks. The majority of the threats to the information system of the organization
can be mitigated extensively.
Spoofing and Sniffing
The attackers when attack a system, design a mean to hide their identity in the attack
or spoof themselves, that is misrepresenting their identity to get the job done. Spoofing
involves misleading web links to other channels and masquerade the intended destination.
The links which are mostly send through emails can mislead the users to different web pages
slow down the working of the system and result in system crash. Sometimes it has been
noticed that the virus attacks happened accidentally simply because of poor programming.
The damages done to the information systems in an enterprise might be executed on
purpose or the reason can be accidental or there can be selfish reasons or motive to cause
industrial sabotage. The insiders has the knowledge that offers immense capabilities to the
attackers to severely sabotage the working of the enterprises’ system. The entities that can
face the attacks are the hardware, altering data, infrastructure, incorrect data entered, software
deletion, logic bomb implementation and virus implementation. Selfish and deliberate
motives to damage the software, hardware and data of the enterprise can lead to data loss
which will in turn, turn out to be a major threat for the enterprise or the company. The minor
damages done to the system also adds to the sum of damages faced by the system of the
organization. Temporary denial of access is the sole reason for the threat of vandalism.
Human errors leads to the minor and major damages caused to the system. The accidental
damages can later be handled and saved from further escalations and disputes over a period
of time and this requires decent employee disposition. Human errors have the most
significant impact on the security of the organizational system more that purposeful manmade
threats and attacks. The majority of the threats to the information system of the organization
can be mitigated extensively.
Spoofing and Sniffing
The attackers when attack a system, design a mean to hide their identity in the attack
or spoof themselves, that is misrepresenting their identity to get the job done. Spoofing
involves misleading web links to other channels and masquerade the intended destination.
The links which are mostly send through emails can mislead the users to different web pages

11BELL STUDIO
and the attackers gets the key to the lock of the entry and hence can launch the attack.
Sniffing is different from spoofing as it involves eavesdropping to gather important
information from the organization’s system and data base. The sniffing tools are utilised
legitimately as the sniffers could help in identification of potential trouble spots of the
network system and exploit the identified vulnerability to their advantage. The sniffer
programs are to be decoded by the organizations. The sniffers pave the way for the hackers to
steal proprietary information from the network system which includes reports, emails and
confidential messages and files of the organization.
The infamous Trojan surface is a legitimate entity to gain access of the computers.
Trojan horses the utilized to impose severe damage to the organization’s system. In recent
time, the Trojan horses have evolved in design and capacity to be completely utilized to bring
down a organization’s server system and network channel. The Trojans which are frequently
encountered by enterprises are so designed to draw information from the enterprise’s data
base and transporting the collected reports. Trojan incorporates keystroke recorder to capture
keyboard inputs from any computer system provided. The Trojan can collect real time data
from outgoing messages and emails. Breaches in the security of the network system of the
organization by the Trojan can cause major damage to the organization’s assets. Any leak of
data or stolen confidential data of the organization can hamper the brand of the company and
damage the working of the organization as a whole. Destruction of authentic files and
classifies data increases the valuation of copied data. The competitor of the organization
gains valuable knowledge about the clientele of the organization and can hence develop
strategies to improve business in the market and the other organization can run the risk of a
huge loss. Such acts brings out the vulnerabilities of the company which leads to corporate
takeovers and damage to the brand value of the organization.
and the attackers gets the key to the lock of the entry and hence can launch the attack.
Sniffing is different from spoofing as it involves eavesdropping to gather important
information from the organization’s system and data base. The sniffing tools are utilised
legitimately as the sniffers could help in identification of potential trouble spots of the
network system and exploit the identified vulnerability to their advantage. The sniffer
programs are to be decoded by the organizations. The sniffers pave the way for the hackers to
steal proprietary information from the network system which includes reports, emails and
confidential messages and files of the organization.
The infamous Trojan surface is a legitimate entity to gain access of the computers.
Trojan horses the utilized to impose severe damage to the organization’s system. In recent
time, the Trojan horses have evolved in design and capacity to be completely utilized to bring
down a organization’s server system and network channel. The Trojans which are frequently
encountered by enterprises are so designed to draw information from the enterprise’s data
base and transporting the collected reports. Trojan incorporates keystroke recorder to capture
keyboard inputs from any computer system provided. The Trojan can collect real time data
from outgoing messages and emails. Breaches in the security of the network system of the
organization by the Trojan can cause major damage to the organization’s assets. Any leak of
data or stolen confidential data of the organization can hamper the brand of the company and
damage the working of the organization as a whole. Destruction of authentic files and
classifies data increases the valuation of copied data. The competitor of the organization
gains valuable knowledge about the clientele of the organization and can hence develop
strategies to improve business in the market and the other organization can run the risk of a
huge loss. Such acts brings out the vulnerabilities of the company which leads to corporate
takeovers and damage to the brand value of the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





