HI5019 Case Study: Strategic Information Systems for Bell Studio
VerifiedAdded on 2022/12/27
|27
|5546
|405
Case Study
AI Summary
This assignment analyzes the strategic information systems (SIS) implemented at Bell Studio, examining various aspects such as transaction cycles (sales, purchasing, financing, expenditure, and payroll), financial reporting, management reporting systems, and e-commerce. The analysis identifies weaknesses in the current systems, particularly within the purchase system and cash disbursement processes, highlighting the reliance on manual processes and potential for human error. The study then explores the risks associated with these weaknesses, including computer viruses, hardware and software failures, human errors, and hacking, and provides a comprehensive overview of other SIS components such as financial and management reporting and e-commerce. Furthermore, it addresses opportunities for computer fraud, erroneous perceptions of information system risks, technical perceptions of information systems security, financing for security, and the implementation of inappropriate security controls, concluding with recommendations for improvement and enhanced security measures.

Running head: INFORMATION SYSTEMS 1
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
STUDENT NAME
INSTITUTION
COURSE
DATE
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
STUDENT NAME
INSTITUTION
COURSE
DATE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEMS 2
EXECUTIVE SUMMARY
A Strategic Information System (SIS) is a system which helps to determine how
to deal and work alongside changes in business strategies and structure (Alamri et al.,
2016). The main purpose of this system is to enhance time taken to react to
environmental changes and helps leverage a competitive advantage for businesses and
enterprises. The introduction of strategic systems into businesses and Enterprises is a
major step in acknowledging the impact of technology in business environment. Using
these systems, it is possible to deliver innovative services which are cheaper than the
existing ones. As technology undergoes rapid changes, businesses have to have a well
laid plan on how to go about issues that may arise. They also have to find ways of
incorporating the emerging technology into their business operations.
The main functions in a business firm are marketing and sales, production,
accounting and finance and human resource. Information systems are created in order
to enhance operations and management in a business firm. Among the sources of
business decisions are transaction processing systems which can be used by other
systems to derive relevant information. There also exist other information systems that
are relevant in decision making in their respective levels of application.
The key features of a strategic Information system are decision support systems,
primary enterprise resource planning systems, database systems and real-time
information systems which play important roles in provision of information. Even as this
system is being used by business firms, there exists challenges posed by these
systems on the operations of the business in terms of data security. Since these
EXECUTIVE SUMMARY
A Strategic Information System (SIS) is a system which helps to determine how
to deal and work alongside changes in business strategies and structure (Alamri et al.,
2016). The main purpose of this system is to enhance time taken to react to
environmental changes and helps leverage a competitive advantage for businesses and
enterprises. The introduction of strategic systems into businesses and Enterprises is a
major step in acknowledging the impact of technology in business environment. Using
these systems, it is possible to deliver innovative services which are cheaper than the
existing ones. As technology undergoes rapid changes, businesses have to have a well
laid plan on how to go about issues that may arise. They also have to find ways of
incorporating the emerging technology into their business operations.
The main functions in a business firm are marketing and sales, production,
accounting and finance and human resource. Information systems are created in order
to enhance operations and management in a business firm. Among the sources of
business decisions are transaction processing systems which can be used by other
systems to derive relevant information. There also exist other information systems that
are relevant in decision making in their respective levels of application.
The key features of a strategic Information system are decision support systems,
primary enterprise resource planning systems, database systems and real-time
information systems which play important roles in provision of information. Even as this
system is being used by business firms, there exists challenges posed by these
systems on the operations of the business in terms of data security. Since these
INFORMATION SYSTEMS 3
systems are computer based, the risks that affect computing environments will also be
present in such a system (Cassidy, 2016).
systems are computer based, the risks that affect computing environments will also be
present in such a system (Cassidy, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SYSTEMS 4
Table of Contents
INTRODUCTION......................................................................................................................................5
Transactional cycles..............................................................................................................................6
Sales cycle...........................................................................................................................................6
Purchasing cycle................................................................................................................................8
Financing cycle.................................................................................................................................10
Expenditure cycle.............................................................................................................................10
Payroll cycle.......................................................................................................................................11
Weaknesses in the Bell Studio system...........................................................................................13
Purchase system..............................................................................................................................13
Cash Disbursement system...........................................................................................................14
Risks associated with the weaknesses in the Bell Studio system...........................................15
Computer Viruses and Malwares..................................................................................................15
Hardware and software failure......................................................................................................16
Human error.......................................................................................................................................17
Hacking, fraud, denial-of-service..................................................................................................17
Other strategic information systems...............................................................................................18
Financial reporting systems..........................................................................................................18
Management Reporting system....................................................................................................19
E-commerce.......................................................................................................................................20
Opportunities for computer fraud.....................................................................................................21
Erroneous perception of Information Systems risk.................................................................21
Technical perception of Information systems security...........................................................21
Financing for security......................................................................................................................22
Implementation of inappropriate security controls..................................................................23
CONCLUSION........................................................................................................................................23
References.............................................................................................................................................25
Table of Contents
INTRODUCTION......................................................................................................................................5
Transactional cycles..............................................................................................................................6
Sales cycle...........................................................................................................................................6
Purchasing cycle................................................................................................................................8
Financing cycle.................................................................................................................................10
Expenditure cycle.............................................................................................................................10
Payroll cycle.......................................................................................................................................11
Weaknesses in the Bell Studio system...........................................................................................13
Purchase system..............................................................................................................................13
Cash Disbursement system...........................................................................................................14
Risks associated with the weaknesses in the Bell Studio system...........................................15
Computer Viruses and Malwares..................................................................................................15
Hardware and software failure......................................................................................................16
Human error.......................................................................................................................................17
Hacking, fraud, denial-of-service..................................................................................................17
Other strategic information systems...............................................................................................18
Financial reporting systems..........................................................................................................18
Management Reporting system....................................................................................................19
E-commerce.......................................................................................................................................20
Opportunities for computer fraud.....................................................................................................21
Erroneous perception of Information Systems risk.................................................................21
Technical perception of Information systems security...........................................................21
Financing for security......................................................................................................................22
Implementation of inappropriate security controls..................................................................23
CONCLUSION........................................................................................................................................23
References.............................................................................................................................................25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEMS 5
INTRODUCTION
Strategic Information System is defined as the process of identifying applications
that can be used to provide a channel for alignment with business strategies.
Organizations all over the world have found it very essential to be at par with the trends
in technological advancements. As technology advances, there is a universal
expectation for the business environments to adapt to the new way of life, in order to
reach their customers. There needs to exist a general plan on how to include these
trends into business processes. The incorporated parts of technology should be
interoperable with the existing systems, and should not affect the flow of operations. All
these integrations make it compulsory for a business company to come up with a plan
on how to include these things.
Information is an integral part of any organization, since most operations rely on
the existence of information. With this in mind, business organizations need to come up
with ways on how to make use of this information for their advantage. Different systems
have to be harnessed in order to harvest enough and relevant information that will
enhance decision making. The existence of information in the past has not been keenly
interpreted to produce maximum profit into a business. Currently, there are approaches
that are being used to mine this information has been stored in bulk, and therefore,
appropriate systems are needed in order to make use of the information that has
remained useless for long.
INTRODUCTION
Strategic Information System is defined as the process of identifying applications
that can be used to provide a channel for alignment with business strategies.
Organizations all over the world have found it very essential to be at par with the trends
in technological advancements. As technology advances, there is a universal
expectation for the business environments to adapt to the new way of life, in order to
reach their customers. There needs to exist a general plan on how to include these
trends into business processes. The incorporated parts of technology should be
interoperable with the existing systems, and should not affect the flow of operations. All
these integrations make it compulsory for a business company to come up with a plan
on how to include these things.
Information is an integral part of any organization, since most operations rely on
the existence of information. With this in mind, business organizations need to come up
with ways on how to make use of this information for their advantage. Different systems
have to be harnessed in order to harvest enough and relevant information that will
enhance decision making. The existence of information in the past has not been keenly
interpreted to produce maximum profit into a business. Currently, there are approaches
that are being used to mine this information has been stored in bulk, and therefore,
appropriate systems are needed in order to make use of the information that has
remained useless for long.

INFORMATION SYSTEMS 6
Strategic systems is important for any company that aims at achieving
competitive advantage, as it involves use of technology to develop a company’s
services and products and also to aid in advertising the organization’s products. It also
provides the procedural information involved in the process of purchasing a product for
an organization. It mainly features the database system which aims at making use of
the company information in marketing and advertising of products. The Strategic
Information System also ensures that the business dealings align with the organization’s
strategies, and provides the measures that are to be used in carrying out a business in
an organization. This includes drafting, planning, advertising and the actual selling or
purchasing of goods.
In Bell’s studio, the Strategic Information System information is obtained by
analyzing the organization’s transactional cycle. This cycle is described below, and the
ways in which it affects processes in the organization.
Transactional cycles
A transactional cycle is an interlocking cycle that explains the procedures
involved in a business, including all the financial transactions of a company. These
cycles are related to the sale of goods and the payment to employees and suppliers.
These transactional cycles are carried out as: -
Sales cycle
Involves sequential procedure from the time a customer orders goods from a
company to the time they receive the goods after payment. The company will receive
Strategic systems is important for any company that aims at achieving
competitive advantage, as it involves use of technology to develop a company’s
services and products and also to aid in advertising the organization’s products. It also
provides the procedural information involved in the process of purchasing a product for
an organization. It mainly features the database system which aims at making use of
the company information in marketing and advertising of products. The Strategic
Information System also ensures that the business dealings align with the organization’s
strategies, and provides the measures that are to be used in carrying out a business in
an organization. This includes drafting, planning, advertising and the actual selling or
purchasing of goods.
In Bell’s studio, the Strategic Information System information is obtained by
analyzing the organization’s transactional cycle. This cycle is described below, and the
ways in which it affects processes in the organization.
Transactional cycles
A transactional cycle is an interlocking cycle that explains the procedures
involved in a business, including all the financial transactions of a company. These
cycles are related to the sale of goods and the payment to employees and suppliers.
These transactional cycles are carried out as: -
Sales cycle
Involves sequential procedure from the time a customer orders goods from a
company to the time they receive the goods after payment. The company will receive
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SYSTEMS 7
the order, examine its credibility, send the goods or services required and obtain
payment for the goods. It is a recurring process that enhances exchange of goods and
services to customers for their finances. The essence of sales cycle is to ensure correct
selling price of the correct product at an appropriate time. While building the strategic
information system, management should ensure efficiency and effectiveness of the
sales cycle in the system. Most sales cycles have a definite process, which begins with
making an order, delivering the order and receipting it.
Sales order department is the one that performs sales order entry. There are
definite processes that are followed in entering an order. Customer orders are first
taken, then checked in the credits file. Availability of the inventory is then determined
and a feedback given to the customer through customer service. While integrating this
process into an online platform, customers need to be the ones to enter their details into
the system. This helps reduce human error. Orders need to be directly reflected in the
packing store for sealing and shipping. Efficiency can also be increased by using history
of previous sales to determine the types of products to stock more. To enhance this
approach, choice boards can be used. Checking of credit should be automated.
Figure: Dataflow Diagram for Sales cycle
the order, examine its credibility, send the goods or services required and obtain
payment for the goods. It is a recurring process that enhances exchange of goods and
services to customers for their finances. The essence of sales cycle is to ensure correct
selling price of the correct product at an appropriate time. While building the strategic
information system, management should ensure efficiency and effectiveness of the
sales cycle in the system. Most sales cycles have a definite process, which begins with
making an order, delivering the order and receipting it.
Sales order department is the one that performs sales order entry. There are
definite processes that are followed in entering an order. Customer orders are first
taken, then checked in the credits file. Availability of the inventory is then determined
and a feedback given to the customer through customer service. While integrating this
process into an online platform, customers need to be the ones to enter their details into
the system. This helps reduce human error. Orders need to be directly reflected in the
packing store for sealing and shipping. Efficiency can also be increased by using history
of previous sales to determine the types of products to stock more. To enhance this
approach, choice boards can be used. Checking of credit should be automated.
Figure: Dataflow Diagram for Sales cycle
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SYSTEMS 8
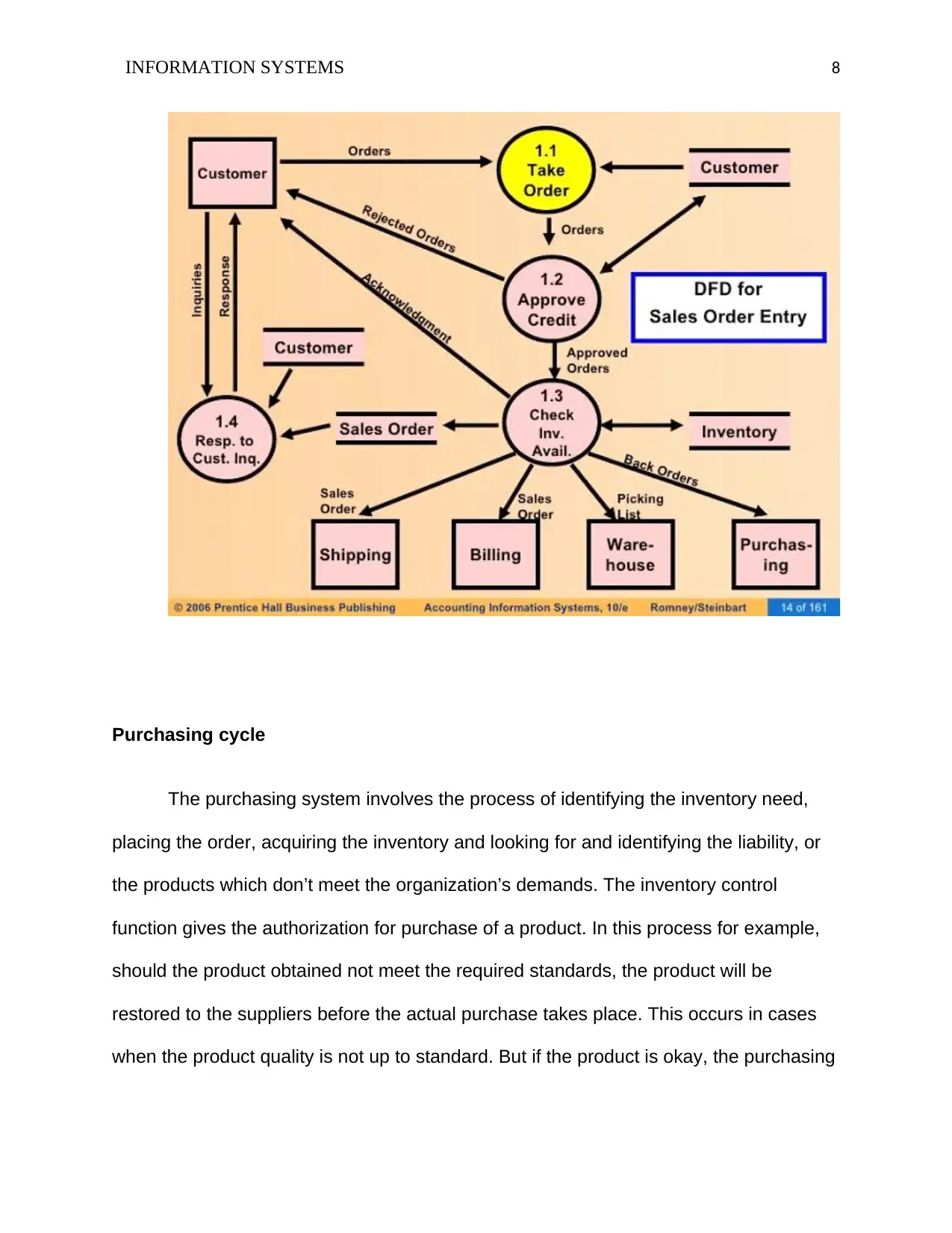
Purchasing cycle
The purchasing system involves the process of identifying the inventory need,
placing the order, acquiring the inventory and looking for and identifying the liability, or
the products which don’t meet the organization’s demands. The inventory control
function gives the authorization for purchase of a product. In this process for example,
should the product obtained not meet the required standards, the product will be
restored to the suppliers before the actual purchase takes place. This occurs in cases
when the product quality is not up to standard. But if the product is okay, the purchasing
Purchasing cycle
The purchasing system involves the process of identifying the inventory need,
placing the order, acquiring the inventory and looking for and identifying the liability, or
the products which don’t meet the organization’s demands. The inventory control
function gives the authorization for purchase of a product. In this process for example,
should the product obtained not meet the required standards, the product will be
restored to the suppliers before the actual purchase takes place. This occurs in cases
when the product quality is not up to standard. But if the product is okay, the purchasing
INFORMATION SYSTEMS 9
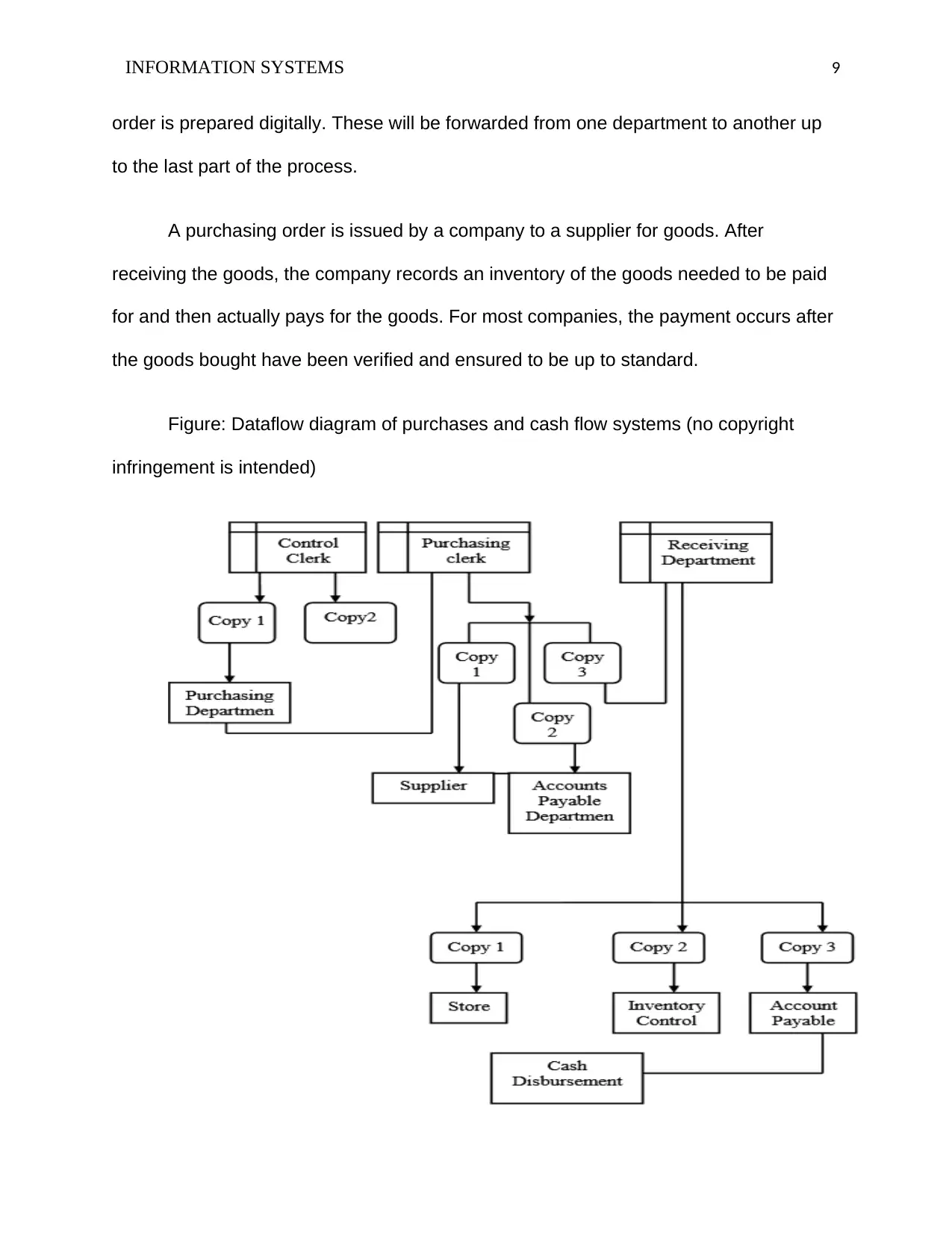
order is prepared digitally. These will be forwarded from one department to another up
to the last part of the process.
A purchasing order is issued by a company to a supplier for goods. After
receiving the goods, the company records an inventory of the goods needed to be paid
for and then actually pays for the goods. For most companies, the payment occurs after
the goods bought have been verified and ensured to be up to standard.
Figure: Dataflow diagram of purchases and cash flow systems (no copyright
infringement is intended)
order is prepared digitally. These will be forwarded from one department to another up
to the last part of the process.
A purchasing order is issued by a company to a supplier for goods. After
receiving the goods, the company records an inventory of the goods needed to be paid
for and then actually pays for the goods. For most companies, the payment occurs after
the goods bought have been verified and ensured to be up to standard.
Figure: Dataflow diagram of purchases and cash flow systems (no copyright
infringement is intended)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SYSTEMS 10
Financing cycle
It records the transactions concerned with getting funds from the owners and
creditors. It involves the issuing out of loans to customers and the flow of payment of
interest and the repayment of the debt given. It also involves the giving out of company
shares and stock to investors in exchange for payment of dividends over a given time.
Furthermore, it entails using the available capital within a company to acquire assets. It
can be explained by the source of capital, property system and the financial reporting
system.
As demand increases forcing business owners to enter in to loans, financial
analysts have the task to know the purpose for taking the loan and the source of the
loan, the creditor. Having such metrics puts them at a better position to create a rough
positional placement of a business in terms of finances and policies. Moreover, it gives
a clear picture of the amount of working capital in a business. As the working capital is
very important to business operations, having knowledge of financing cycle enables
better decision making. The finance cycle is important since most business operations
rely on finances.
Expenditure cycle
The expenditure cycle provides a review of the procedures taken to ensure a
product reaches its required destination on time. It involves keeping a record of all the
financial transactions of an organization. It incorporates all journal entries and
inventories that a company records in the process of acquiring raw materials or
Financing cycle
It records the transactions concerned with getting funds from the owners and
creditors. It involves the issuing out of loans to customers and the flow of payment of
interest and the repayment of the debt given. It also involves the giving out of company
shares and stock to investors in exchange for payment of dividends over a given time.
Furthermore, it entails using the available capital within a company to acquire assets. It
can be explained by the source of capital, property system and the financial reporting
system.
As demand increases forcing business owners to enter in to loans, financial
analysts have the task to know the purpose for taking the loan and the source of the
loan, the creditor. Having such metrics puts them at a better position to create a rough
positional placement of a business in terms of finances and policies. Moreover, it gives
a clear picture of the amount of working capital in a business. As the working capital is
very important to business operations, having knowledge of financing cycle enables
better decision making. The finance cycle is important since most business operations
rely on finances.
Expenditure cycle
The expenditure cycle provides a review of the procedures taken to ensure a
product reaches its required destination on time. It involves keeping a record of all the
financial transactions of an organization. It incorporates all journal entries and
inventories that a company records in the process of acquiring raw materials or
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEMS 11
products from the suppliers.in order for a company to ensure credibility, most
organizations withhold the payment process until after the product is acquired.
It is therefore necessary to record each process involved in the acquisition of the
product. The processes include the request for product, obtaining the product and
paying up for the product bought. These processes can be done manually or digitally
using a computer software and their objective is to minimize the cost of obtaining and
maintaining inventories and other services necessary for the full functioning and running
of an organization.
Payroll cycle
Occurs within a company and involves its employees. The company examines
the time that an employee works per day. This includes the time and overtime worked.
The employees are then paid based on the total time they have worked within the
company. The payment is made after deducting the necessary taxes and advances.
Figure: Dataflow Diagram for payroll system
products from the suppliers.in order for a company to ensure credibility, most
organizations withhold the payment process until after the product is acquired.
It is therefore necessary to record each process involved in the acquisition of the
product. The processes include the request for product, obtaining the product and
paying up for the product bought. These processes can be done manually or digitally
using a computer software and their objective is to minimize the cost of obtaining and
maintaining inventories and other services necessary for the full functioning and running
of an organization.
Payroll cycle
Occurs within a company and involves its employees. The company examines
the time that an employee works per day. This includes the time and overtime worked.
The employees are then paid based on the total time they have worked within the
company. The payment is made after deducting the necessary taxes and advances.
Figure: Dataflow Diagram for payroll system
INFORMATION SYSTEMS 12
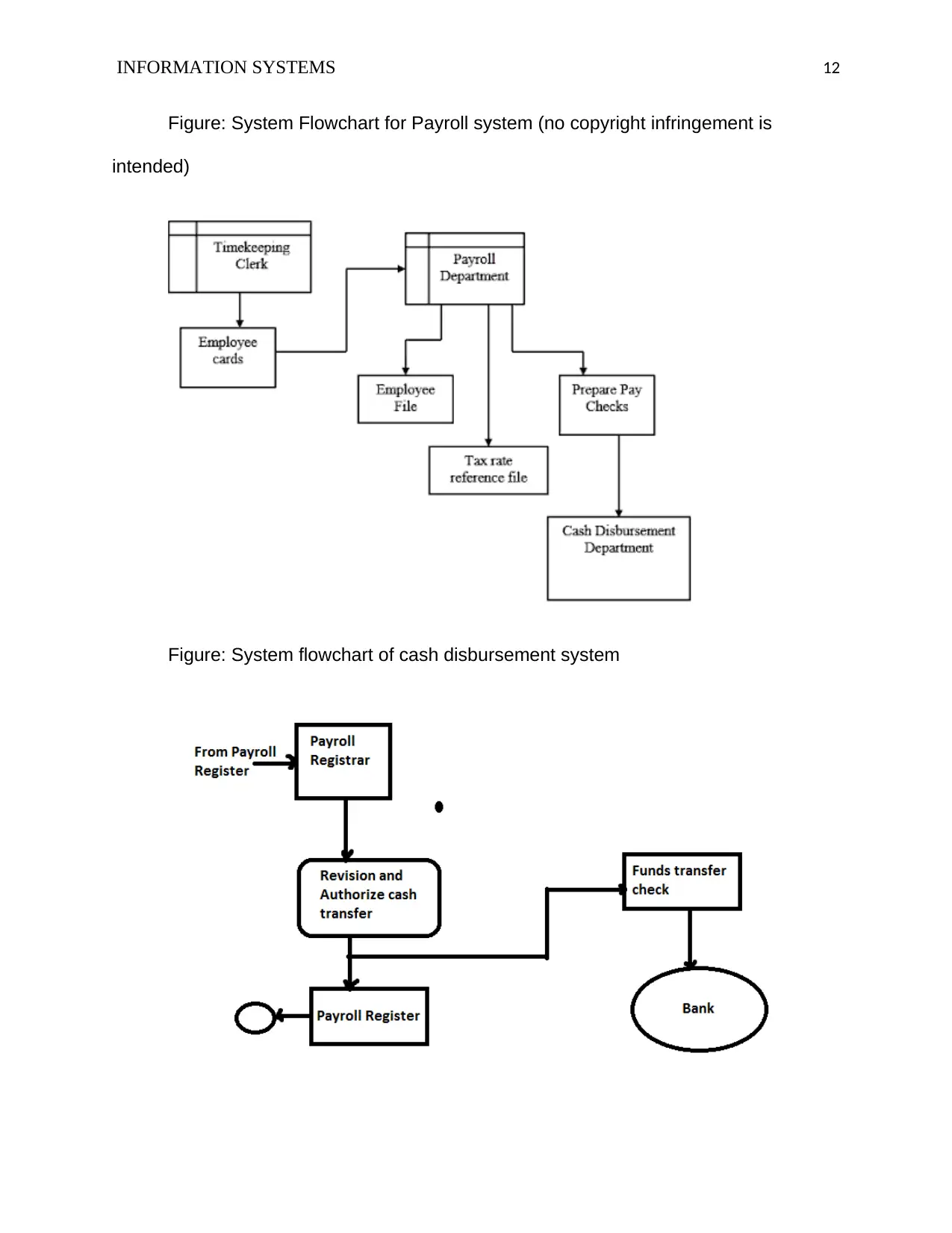
Figure: System Flowchart for Payroll system (no copyright infringement is
intended)
Figure: System flowchart of cash disbursement system
Figure: System Flowchart for Payroll system (no copyright infringement is
intended)
Figure: System flowchart of cash disbursement system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





