Strategic Information Systems Analysis for Bell Studio - HI5019
VerifiedAdded on 2023/01/03
|12
|3143
|81
Case Study
AI Summary
This case study analyzes the strategic information systems of Bell Studio, covering transaction cycles, financial reporting, and management reporting systems, including e-commerce aspects. The report delves into data flow diagrams for the payroll, purchases, and cash disbursement systems. It examines the inherent risks in computer-based systems and ERP, including e-commerce, emphasizing the role of ethics and internal control processes. The study identifies organizational weaknesses, such as outdated systems and vulnerabilities to external threats, and assesses associated risks, like unauthorized access, sniffing, and spoofing. System flowcharts for various processes are provided, alongside descriptions of internal control weaknesses and potential security threats. The analysis highlights the importance of robust security measures to mitigate risks and protect sensitive data.

Running head: STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
Name of the Student
Name of the Organization
Author Note
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
Name of the Student
Name of the Organization
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
Table of Contents
Introduction........................................................................................................................2
Discussion..........................................................................................................................2
Data flow diagram of payroll system..............................................................................2
Data flow diagram of purchases and cash disbursements systems..............................3
System flowchart of cash disbursements system..........................................................4
System flowchart of payroll system................................................................................5
System flowchart of purchases system..........................................................................7
Description of internal control weakness in each system and the risks............................8
Organizational Weakness..............................................................................................8
Risks associated with the weaknesses.............................................................................8
Unauthorized access......................................................................................................8
Sniffing and Spoofing.....................................................................................................9
Conclusion.......................................................................................................................10
Bibliography.....................................................................................................................11
Table of Contents
Introduction........................................................................................................................2
Discussion..........................................................................................................................2
Data flow diagram of payroll system..............................................................................2
Data flow diagram of purchases and cash disbursements systems..............................3
System flowchart of cash disbursements system..........................................................4
System flowchart of payroll system................................................................................5
System flowchart of purchases system..........................................................................7
Description of internal control weakness in each system and the risks............................8
Organizational Weakness..............................................................................................8
Risks associated with the weaknesses.............................................................................8
Unauthorized access......................................................................................................8
Sniffing and Spoofing.....................................................................................................9
Conclusion.......................................................................................................................10
Bibliography.....................................................................................................................11
2STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
Introduction
The main aim of the report is to clearly describe about the situation of the Bell
studio and then evaluate all the risks, procedures as well as all the internal controls for
the cycle of expenditure. The flow diagram of data of all the purchases as well as all the
systems of the disbursements of cash has been provided within the report. A brief
description is present about all the weakness which is internally controlled in each of the
system as well as all the risks which are linked with a number of weaknesses which are
identified.
Discussion
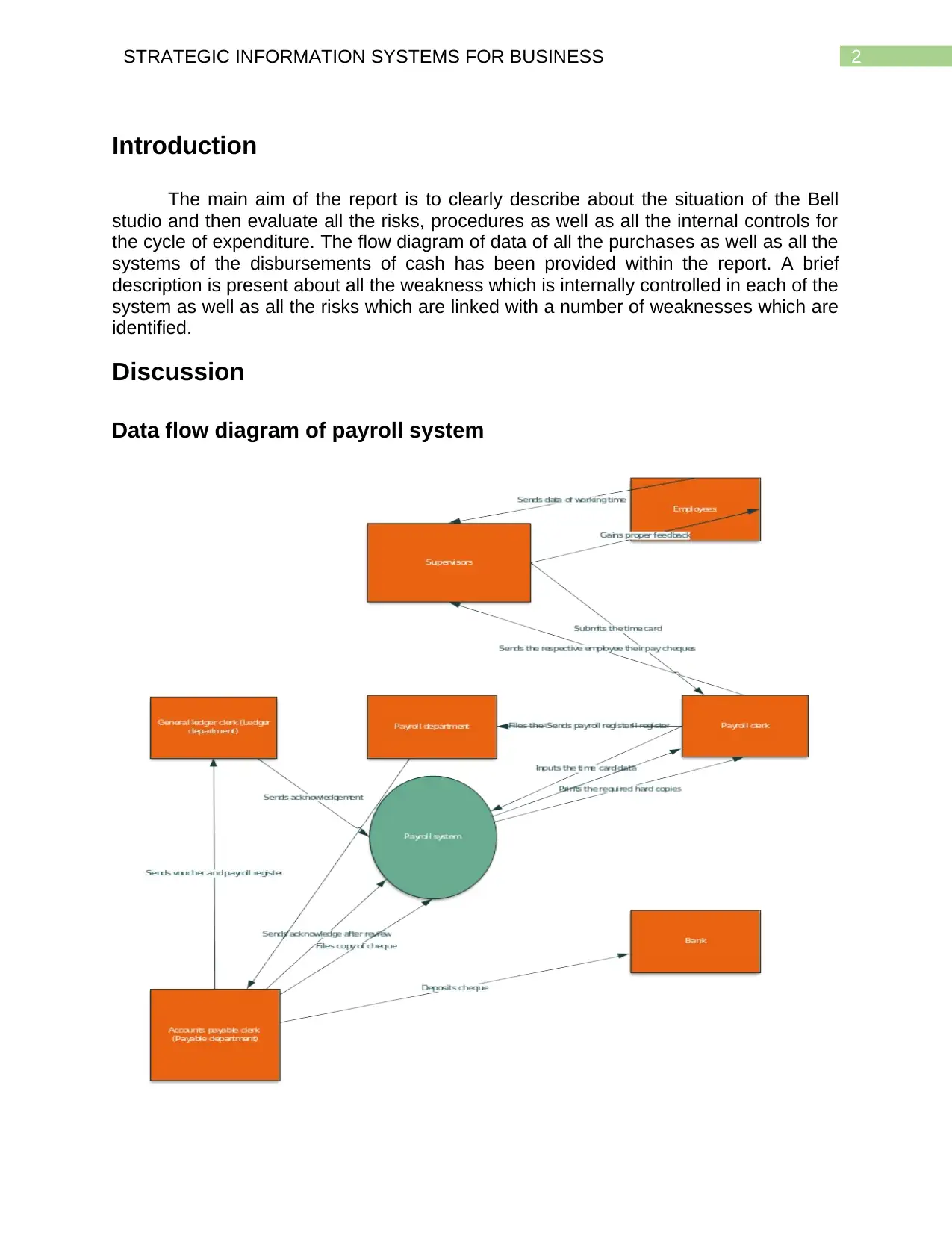
Data flow diagram of payroll system
Introduction
The main aim of the report is to clearly describe about the situation of the Bell
studio and then evaluate all the risks, procedures as well as all the internal controls for
the cycle of expenditure. The flow diagram of data of all the purchases as well as all the
systems of the disbursements of cash has been provided within the report. A brief
description is present about all the weakness which is internally controlled in each of the
system as well as all the risks which are linked with a number of weaknesses which are
identified.
Discussion
Data flow diagram of payroll system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
The data flow diagram helps in the understanding of the flow of the data among
the various interactors of the organisation. It helps in the understanding of the gaining
various perspective about the data flow. The organisation implemented the proper
mechanisms for monitoring the proper data flow. In the data flow diagram of the payroll
system the employees are provided with their salary in the form of the cheques and the
proper management of the supervisors has been done.
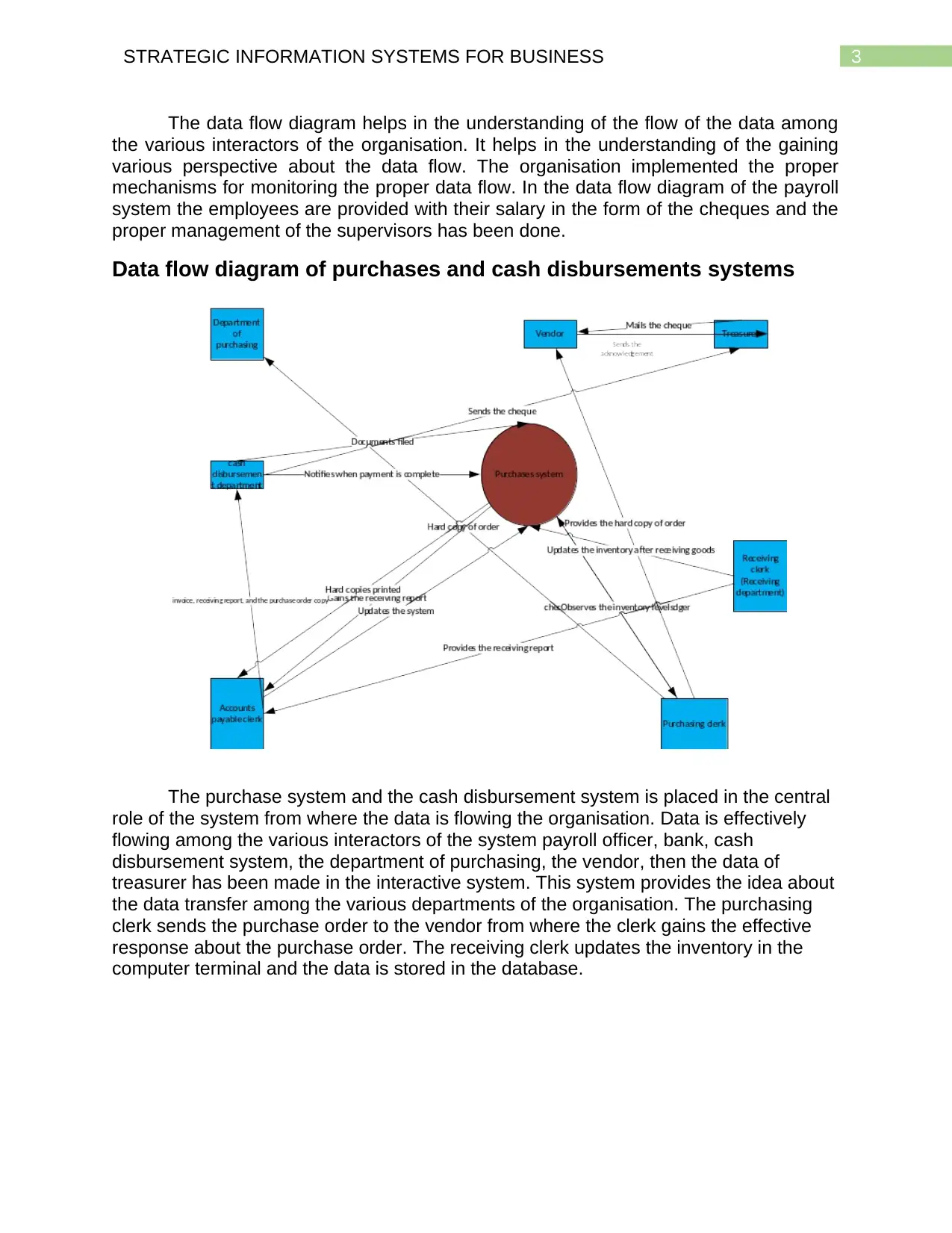
Data flow diagram of purchases and cash disbursements systems
The purchase system and the cash disbursement system is placed in the central
role of the system from where the data is flowing the organisation. Data is effectively
flowing among the various interactors of the system payroll officer, bank, cash
disbursement system, the department of purchasing, the vendor, then the data of
treasurer has been made in the interactive system. This system provides the idea about
the data transfer among the various departments of the organisation. The purchasing
clerk sends the purchase order to the vendor from where the clerk gains the effective
response about the purchase order. The receiving clerk updates the inventory in the
computer terminal and the data is stored in the database.
The data flow diagram helps in the understanding of the flow of the data among
the various interactors of the organisation. It helps in the understanding of the gaining
various perspective about the data flow. The organisation implemented the proper
mechanisms for monitoring the proper data flow. In the data flow diagram of the payroll
system the employees are provided with their salary in the form of the cheques and the
proper management of the supervisors has been done.
Data flow diagram of purchases and cash disbursements systems
The purchase system and the cash disbursement system is placed in the central
role of the system from where the data is flowing the organisation. Data is effectively
flowing among the various interactors of the system payroll officer, bank, cash
disbursement system, the department of purchasing, the vendor, then the data of
treasurer has been made in the interactive system. This system provides the idea about
the data transfer among the various departments of the organisation. The purchasing
clerk sends the purchase order to the vendor from where the clerk gains the effective
response about the purchase order. The receiving clerk updates the inventory in the
computer terminal and the data is stored in the database.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
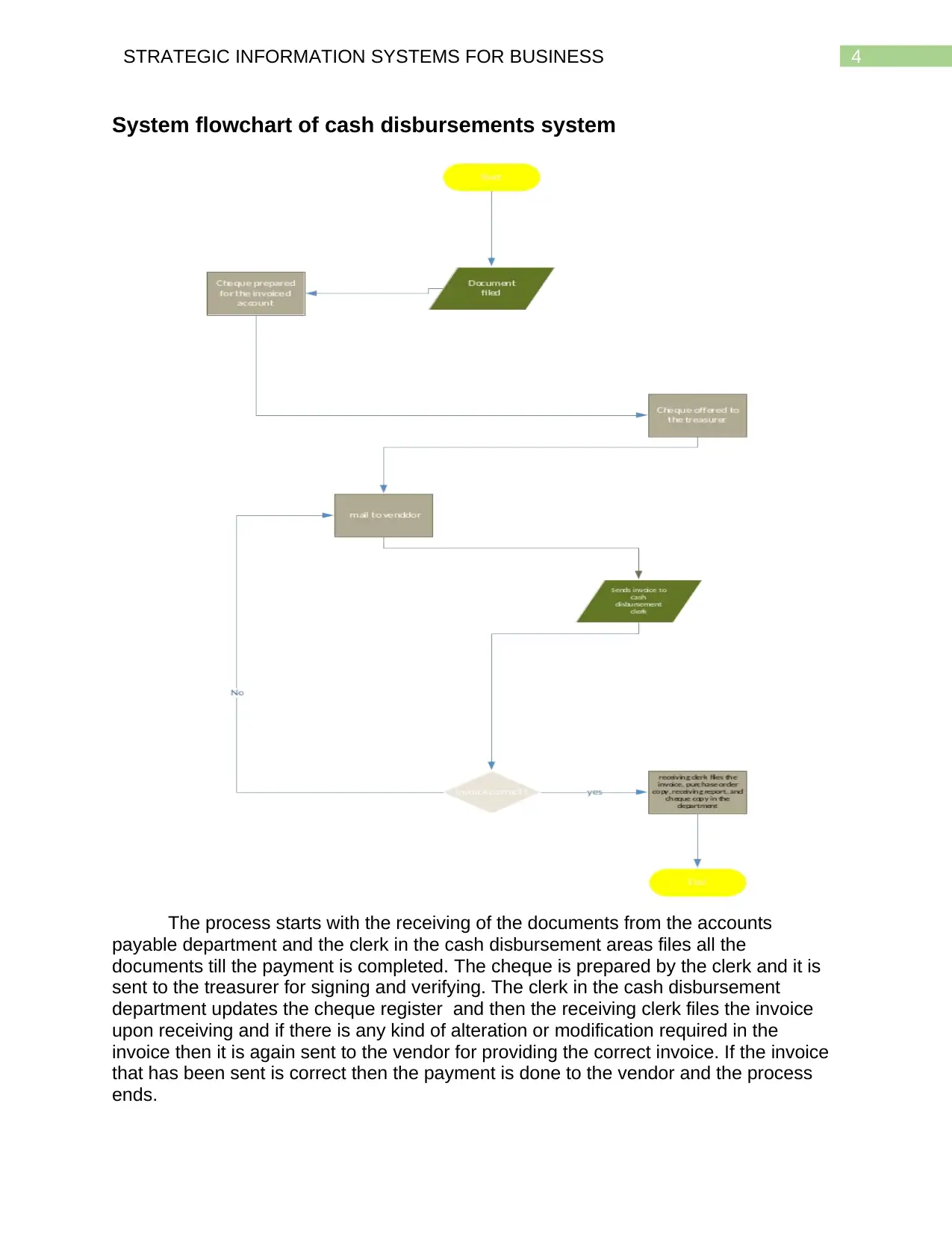
System flowchart of cash disbursements system
The process starts with the receiving of the documents from the accounts
payable department and the clerk in the cash disbursement areas files all the
documents till the payment is completed. The cheque is prepared by the clerk and it is
sent to the treasurer for signing and verifying. The clerk in the cash disbursement
department updates the cheque register and then the receiving clerk files the invoice
upon receiving and if there is any kind of alteration or modification required in the
invoice then it is again sent to the vendor for providing the correct invoice. If the invoice
that has been sent is correct then the payment is done to the vendor and the process
ends.
System flowchart of cash disbursements system
The process starts with the receiving of the documents from the accounts
payable department and the clerk in the cash disbursement areas files all the
documents till the payment is completed. The cheque is prepared by the clerk and it is
sent to the treasurer for signing and verifying. The clerk in the cash disbursement
department updates the cheque register and then the receiving clerk files the invoice
upon receiving and if there is any kind of alteration or modification required in the
invoice then it is again sent to the vendor for providing the correct invoice. If the invoice
that has been sent is correct then the payment is done to the vendor and the process
ends.
5STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
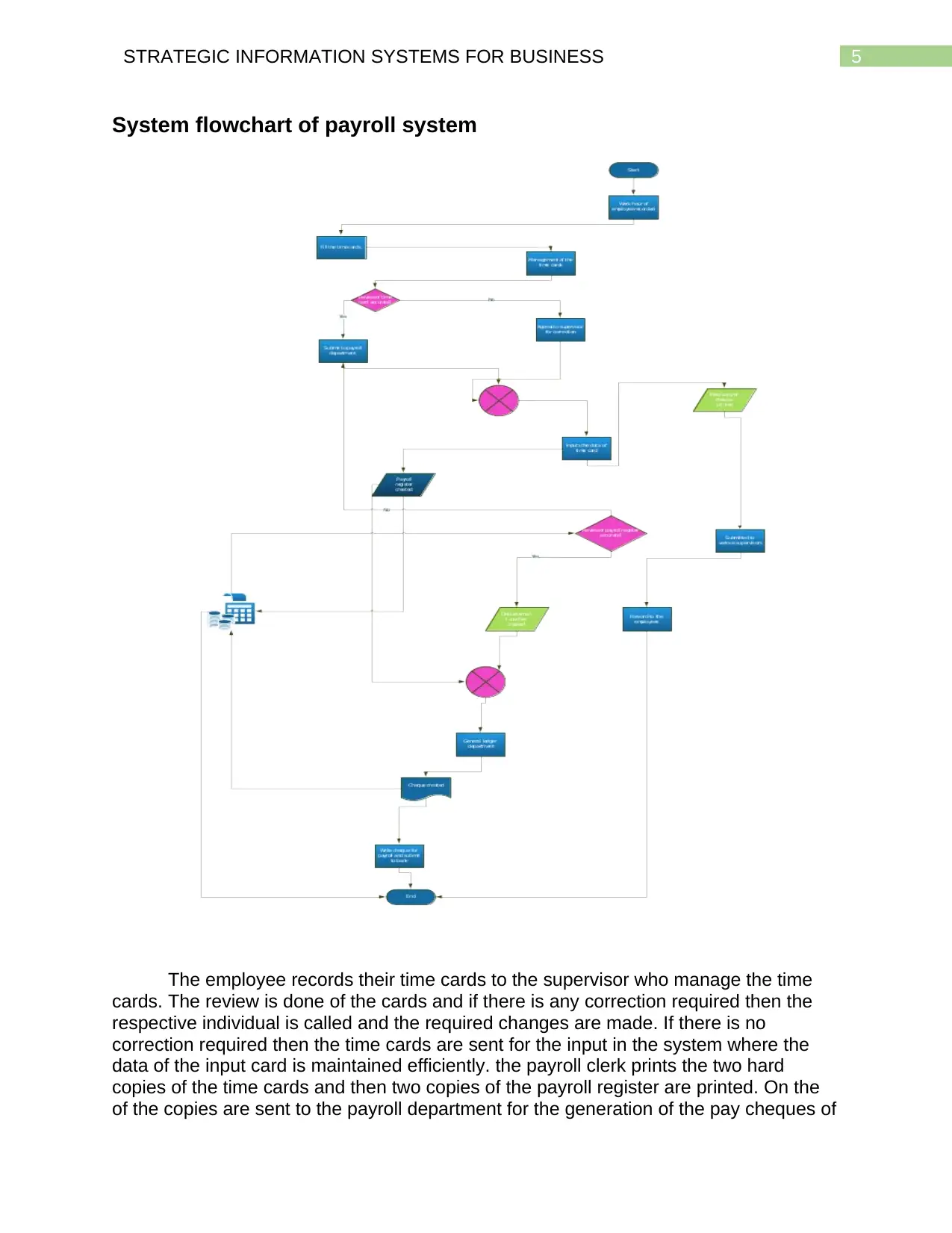
System flowchart of payroll system
The employee records their time cards to the supervisor who manage the time
cards. The review is done of the cards and if there is any correction required then the
respective individual is called and the required changes are made. If there is no
correction required then the time cards are sent for the input in the system where the
data of the input card is maintained efficiently. the payroll clerk prints the two hard
copies of the time cards and then two copies of the payroll register are printed. On the
of the copies are sent to the payroll department for the generation of the pay cheques of
System flowchart of payroll system
The employee records their time cards to the supervisor who manage the time
cards. The review is done of the cards and if there is any correction required then the
respective individual is called and the required changes are made. If there is no
correction required then the time cards are sent for the input in the system where the
data of the input card is maintained efficiently. the payroll clerk prints the two hard
copies of the time cards and then two copies of the payroll register are printed. On the
of the copies are sent to the payroll department for the generation of the pay cheques of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
the employees and the other one is sent to the accounts payable department for the
filed with the time cards in the payroll department. The clerk in the accounts payable
reviews the payroll register and if the accurate data is provided then they prepare the
disbursement voucher and if there is any correction required then it is sent back to the
previous step for the correction. The voucher is sent to the clerk along with the payroll
register to the common ledger department. The accounts payable clerk writes the
cheque for the complete payroll and then deposits in the bank. The clerk posts the
general ledger from the computer terminal in the department and also files the voucher
in department. Two hard copy of the received order is created and one is sent with the
goods to inventory warehouse and the other copy has been sent to the accounts
payable department where it is filed. The invoice is received by the accounts payable
clerk then the three documents is combined and the clerk updates the digital accounts
payable ledger. The clerk then sends the three documents to the cash disbursement
department and the process ends.
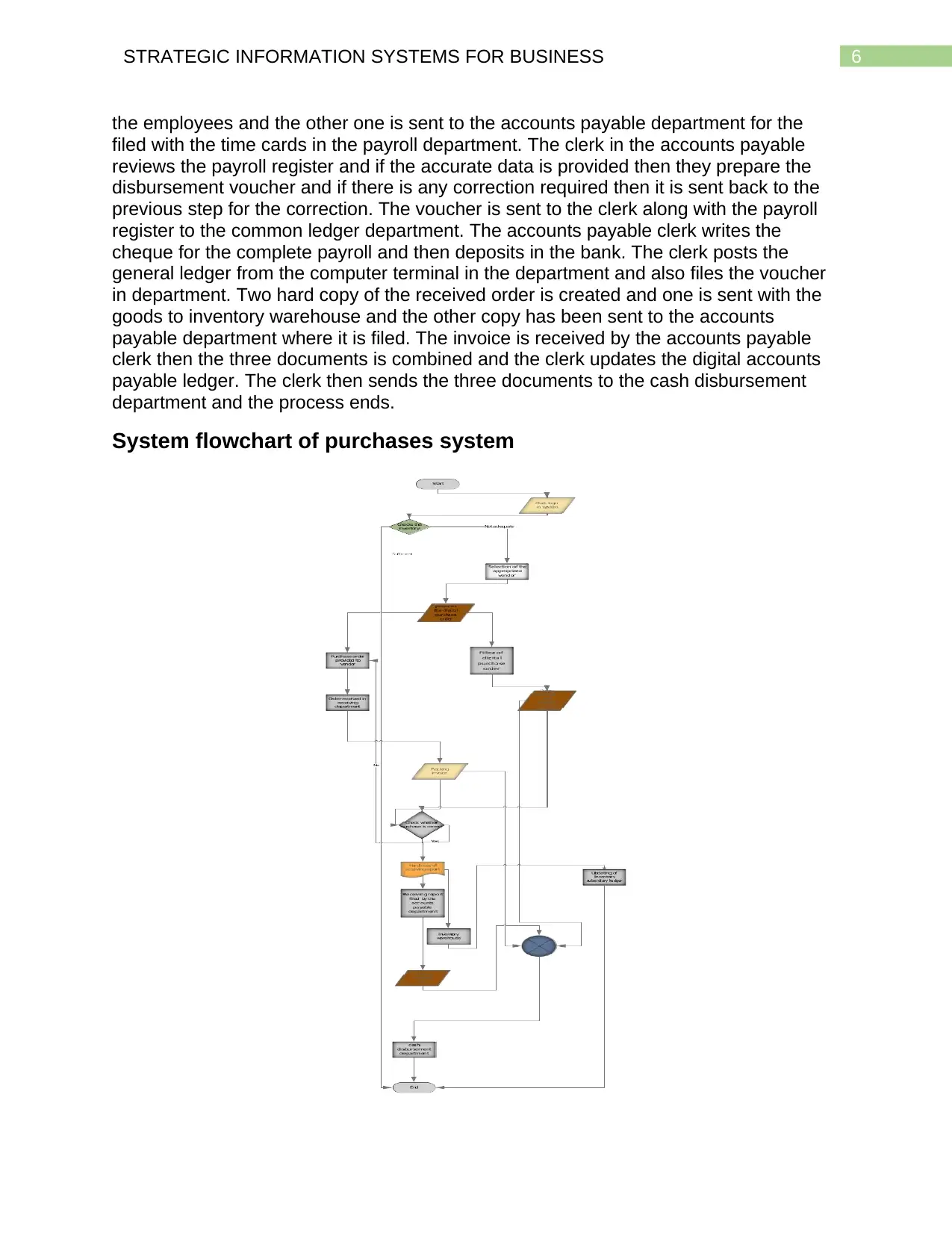
System flowchart of purchases system
the employees and the other one is sent to the accounts payable department for the
filed with the time cards in the payroll department. The clerk in the accounts payable
reviews the payroll register and if the accurate data is provided then they prepare the
disbursement voucher and if there is any correction required then it is sent back to the
previous step for the correction. The voucher is sent to the clerk along with the payroll
register to the common ledger department. The accounts payable clerk writes the
cheque for the complete payroll and then deposits in the bank. The clerk posts the
general ledger from the computer terminal in the department and also files the voucher
in department. Two hard copy of the received order is created and one is sent with the
goods to inventory warehouse and the other copy has been sent to the accounts
payable department where it is filed. The invoice is received by the accounts payable
clerk then the three documents is combined and the clerk updates the digital accounts
payable ledger. The clerk then sends the three documents to the cash disbursement
department and the process ends.
System flowchart of purchases system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
The clerk logs in the system for checking the inventory and if the inventory level
is lower than the required inventory then the appropriate vendor is selected for
purchasing and the digital purchase order is created and stored in the system. The clerk
then prints the two hard copies where one copy is directly sent to the vendor one more
hard copy is filed in purchasing department. When the goods are received in the
receiving department then the checking of the invoice is done with the hard copy of the
purchase order gained from the system and if the proper order is not received then the
file is sent back to the vendor for sending the correct order. If the received order is
correct then the goods are sent to the inventory warehouse
Description of internal control weakness in each system and
the risks
Organizational Weakness
There are a number of weaknesses which are seen to be associated with several
systems of purchasing, systems of cash disbursements as well as the system of payroll
and there is also a need for an appropriate assessment of risk. The main importance
which is critical and also the system’s complexity of purchasing and the disbursement of
cash has unfortunately denoted that all kinds of alterations which are made to the
system can even lead to a number of disruptions which are mostly operational by
relying upon the way how the main system has been properly implemented and then
finally deployed. There are even some systems of the particular company which are
totally outdated and most of them are seen to be already lagging behind on several
patches which are crucial so that the extra suspension of all the updates may subject
organization’s systems at a risk which will be significant. There is even a weakness
within the organization’s system which can make all the systems as well as the
organization’s software very much vulnerable to a number of threats which are external.
There are several computers where invoice data is kept which is mainly subjected to the
security risk of data. Any hacker may easily discover a number of methods with the help
of which organizational data managed within the organization’s system can be stolen
easily. An extra danger has been seen to have been emerged due to the
implementation of modern technology within the organization.
All kinds of resources which are both financial as well as professional are both
stored as well as managed within the organization’s database where there are a
number of weaknesses present because of the lack of appropriate measures of
security. All the system’s weaknesses which can be easily exploited by several cyber
attackers are seen to be extensively focusses which are mainly needed to be protected.
Another company’s weakness is the culture of the organization which mainly leads to
the main opening of the system’s weakness within the organization.
The clerk logs in the system for checking the inventory and if the inventory level
is lower than the required inventory then the appropriate vendor is selected for
purchasing and the digital purchase order is created and stored in the system. The clerk
then prints the two hard copies where one copy is directly sent to the vendor one more
hard copy is filed in purchasing department. When the goods are received in the
receiving department then the checking of the invoice is done with the hard copy of the
purchase order gained from the system and if the proper order is not received then the
file is sent back to the vendor for sending the correct order. If the received order is
correct then the goods are sent to the inventory warehouse
Description of internal control weakness in each system and
the risks
Organizational Weakness
There are a number of weaknesses which are seen to be associated with several
systems of purchasing, systems of cash disbursements as well as the system of payroll
and there is also a need for an appropriate assessment of risk. The main importance
which is critical and also the system’s complexity of purchasing and the disbursement of
cash has unfortunately denoted that all kinds of alterations which are made to the
system can even lead to a number of disruptions which are mostly operational by
relying upon the way how the main system has been properly implemented and then
finally deployed. There are even some systems of the particular company which are
totally outdated and most of them are seen to be already lagging behind on several
patches which are crucial so that the extra suspension of all the updates may subject
organization’s systems at a risk which will be significant. There is even a weakness
within the organization’s system which can make all the systems as well as the
organization’s software very much vulnerable to a number of threats which are external.
There are several computers where invoice data is kept which is mainly subjected to the
security risk of data. Any hacker may easily discover a number of methods with the help
of which organizational data managed within the organization’s system can be stolen
easily. An extra danger has been seen to have been emerged due to the
implementation of modern technology within the organization.
All kinds of resources which are both financial as well as professional are both
stored as well as managed within the organization’s database where there are a
number of weaknesses present because of the lack of appropriate measures of
security. All the system’s weaknesses which can be easily exploited by several cyber
attackers are seen to be extensively focusses which are mainly needed to be protected.
Another company’s weakness is the culture of the organization which mainly leads to
the main opening of the system’s weakness within the organization.

8STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
Risks associated with the weaknesses
Unauthorized access
The most common risk related to security for the organization related to the
particular information system which is computerized is mainly the danger of several
accesses which are totally unauthorized to the data confidentiality. The main concern
emerges from several intruders who are fully unwanted or rather hackers who may use
all the modern technologies as well as skills for getting access within all the computers
of the organizations which are secure. The risk which mostly comes from all the viruses
of the computer in the organization’s system can be some other issue which is capable
of creating several risks of data. Computer virus is mainly a kind of a software which is
malicious and which has been written deliberately for getting access which has been
deprived of the main permission of the users with the capability of duplicating itself and
then finally continuing by spreading to a number of sectors of the organizational
systems.
With the regard to systems of information within the organization, all the
damages which have been done to several systems can be executed on a particular
purpose or it can be accidental as well. It is mainly executed on the basis of any
particular individual or rather as a particular act of the sabotage of industry. The
systems of the organization which are mainly hugely impacted can be both the
infrastructure as well as hardware, altering the data, software deletion and rather virus
implementation. The most deliberate intention of several individuals for damaging the
data and also the software is considered as one of the most serious threats to the
organization which can lead to a huge loss of organizational data. The vandalism’s
threat mainly lies upon the fact that the organization has been denied temporarily for the
system’s access and also resources for some type of individuals. Even it has also been
noticed that minor damages which are caused within the organization’s system can
have a huge effect upon that particular organization fully. It has also been noticed that
errors caused by humans can also have a high impact upon the information system’s
security of the organization rather than all the manmade threats which are mostly
caused by all attacks which are purposeful.
Sniffing and Spoofing
Most of the hackers are attempting and trying a lot for hiding the identity spoof
which is mainly authentic. The redirecting of spoofing is actually the redirection of any
kind of link of web to any address which is dissimilar from the one which is mainly
intended along the site which is masquerading as some other destination which has
been intended. While any kind of sniffer is mainly a kind of program like eavesdropping
which mainly performs the information monitoring travelling over a specified network.
When it is seen to be operated and used in a legitimate manner, the sniffers can help a
lot in assisting in the process of the identification of all the trouble shots which are very
much potential within the network and also in exploiting that particular vulnerability to
their respective advantage. It has also been discovered that sniffer program detection
Risks associated with the weaknesses
Unauthorized access
The most common risk related to security for the organization related to the
particular information system which is computerized is mainly the danger of several
accesses which are totally unauthorized to the data confidentiality. The main concern
emerges from several intruders who are fully unwanted or rather hackers who may use
all the modern technologies as well as skills for getting access within all the computers
of the organizations which are secure. The risk which mostly comes from all the viruses
of the computer in the organization’s system can be some other issue which is capable
of creating several risks of data. Computer virus is mainly a kind of a software which is
malicious and which has been written deliberately for getting access which has been
deprived of the main permission of the users with the capability of duplicating itself and
then finally continuing by spreading to a number of sectors of the organizational
systems.
With the regard to systems of information within the organization, all the
damages which have been done to several systems can be executed on a particular
purpose or it can be accidental as well. It is mainly executed on the basis of any
particular individual or rather as a particular act of the sabotage of industry. The
systems of the organization which are mainly hugely impacted can be both the
infrastructure as well as hardware, altering the data, software deletion and rather virus
implementation. The most deliberate intention of several individuals for damaging the
data and also the software is considered as one of the most serious threats to the
organization which can lead to a huge loss of organizational data. The vandalism’s
threat mainly lies upon the fact that the organization has been denied temporarily for the
system’s access and also resources for some type of individuals. Even it has also been
noticed that minor damages which are caused within the organization’s system can
have a huge effect upon that particular organization fully. It has also been noticed that
errors caused by humans can also have a high impact upon the information system’s
security of the organization rather than all the manmade threats which are mostly
caused by all attacks which are purposeful.
Sniffing and Spoofing
Most of the hackers are attempting and trying a lot for hiding the identity spoof
which is mainly authentic. The redirecting of spoofing is actually the redirection of any
kind of link of web to any address which is dissimilar from the one which is mainly
intended along the site which is masquerading as some other destination which has
been intended. While any kind of sniffer is mainly a kind of program like eavesdropping
which mainly performs the information monitoring travelling over a specified network.
When it is seen to be operated and used in a legitimate manner, the sniffers can help a
lot in assisting in the process of the identification of all the trouble shots which are very
much potential within the network and also in exploiting that particular vulnerability to
their respective advantage. It has also been discovered that sniffer program detection
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
are very much difficult for the organization in execution. The sniffer mainly allows all the
hackers for stealing all the information which are proprietary from one particular place
upon the network involving all the messages of email, reports which are confidential and
some other files within the company. The Trojan is mainly emerged as the legitimate for
obtaining access to several computers. The use of the Trojan horses may be done for
the execution of several attacks of the computer upon the organization which can even
harm the organization in a significant manner. The use of Trojan horses which can
disrupt several activities or even an access gaining to all kinds of information which are
highly confidential has been evolved within the current years in a significant way. Most
commonly, the Trojan can even involve the facility of key logging which is also known as
the recorder of keystroke for mainly capturing the input of the keyboard from any
computer which has been provided. Maximum of all the Trojans which have been
encountered by the organization of business have been specially designed for collecting
information and also for transmitting all the reports back to the owner on a regular basis.
All the hackers can even use the malware for the execution of several attacks of the
system of the organization which is mainly controlling may even lead to a huge data
loss. The theft of data mainly involves the preparation of copies of all the essential files
without the execution of any kind of physical damage. The organizational information
system can even face this particular issue and will be mainly involving the sensitive
information stealing or rather making any kind of alteration for the records of the
computer which is totally unauthorized. Another risk which can be discovered from the
system’s weaknesses is the individual sabotage which is mainly executed by any kind of
employee who is disgruntled having the main intention for extracting revenge on any
employer.
Conclusion
It can be concluded that the Bell Studio comprises of a number of weaknesses
within the organizational systems which can be easily exploited by all the users who are
totally malicious for mainly gaining system’s access. The importance which is very much
critical and the system’s complexity mainly denotes all the alterations which have been
made to the system can even lead to several disruptions which are operational relying
upon the way how the particular system has been first implemented and then finally
deployed. Some of the administrators will be choosing the segmentation or rather the
updates of the delays towards the prevention of the shutdown of process and downtime.
There is a huge weakness in the organizational system which can make all the systems
vulnerable to all the threats which are external. The virus of the computer is a type of
software which is very much malicious and which is written mainly for gaining access
which has been deprived of the permission with the capability of duplicating itself and
hence continuing the spread to several sectors of the organizational systems.
are very much difficult for the organization in execution. The sniffer mainly allows all the
hackers for stealing all the information which are proprietary from one particular place
upon the network involving all the messages of email, reports which are confidential and
some other files within the company. The Trojan is mainly emerged as the legitimate for
obtaining access to several computers. The use of the Trojan horses may be done for
the execution of several attacks of the computer upon the organization which can even
harm the organization in a significant manner. The use of Trojan horses which can
disrupt several activities or even an access gaining to all kinds of information which are
highly confidential has been evolved within the current years in a significant way. Most
commonly, the Trojan can even involve the facility of key logging which is also known as
the recorder of keystroke for mainly capturing the input of the keyboard from any
computer which has been provided. Maximum of all the Trojans which have been
encountered by the organization of business have been specially designed for collecting
information and also for transmitting all the reports back to the owner on a regular basis.
All the hackers can even use the malware for the execution of several attacks of the
system of the organization which is mainly controlling may even lead to a huge data
loss. The theft of data mainly involves the preparation of copies of all the essential files
without the execution of any kind of physical damage. The organizational information
system can even face this particular issue and will be mainly involving the sensitive
information stealing or rather making any kind of alteration for the records of the
computer which is totally unauthorized. Another risk which can be discovered from the
system’s weaknesses is the individual sabotage which is mainly executed by any kind of
employee who is disgruntled having the main intention for extracting revenge on any
employer.
Conclusion
It can be concluded that the Bell Studio comprises of a number of weaknesses
within the organizational systems which can be easily exploited by all the users who are
totally malicious for mainly gaining system’s access. The importance which is very much
critical and the system’s complexity mainly denotes all the alterations which have been
made to the system can even lead to several disruptions which are operational relying
upon the way how the particular system has been first implemented and then finally
deployed. Some of the administrators will be choosing the segmentation or rather the
updates of the delays towards the prevention of the shutdown of process and downtime.
There is a huge weakness in the organizational system which can make all the systems
vulnerable to all the threats which are external. The virus of the computer is a type of
software which is very much malicious and which is written mainly for gaining access
which has been deprived of the permission with the capability of duplicating itself and
hence continuing the spread to several sectors of the organizational systems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
Bibliography
Enck, W., Gilbert, P., Han, S., Tendulkar, V., Chun, B.G., Cox, L.P., Jung, J., McDaniel,
P. and Sheth, A.N., 2014. TaintDroid: an information-flow tracking system for realtime
privacy monitoring on smartphones. ACM Transactions on Computer Systems
(TOCS), 32(2), p.5.
Jouini, M., Rabai, L.B.A. and Aissa, A.B., 2014. Classification of security threats in
information systems. Procedia Computer Science, 32, pp.489-496.
Laudon, K.C. and Laudon, J.P., 2016. Management information system. Pearson
Education India.
Mahdi, A.O., Alhabbash, M.I. and Naser, S.S.A., 2016. An intelligent tutoring system for
teaching advanced topics in information security.
Elnajjar, A.E.A. and Naser, S.S.A., 2017. DES-Tutor: An Intelligent Tutoring System for
Teaching DES Information Security Algorithm.
AbdAllah, E.G., Hassanein, H.S. and Zulkernine, M., 2015. A survey of security attacks
in information-centric networking. IEEE Communications Surveys & Tutorials, 17(3),
pp.1441-1454.
B. Kim, E., 2014. Recommendations for information security awareness training for
college students. Information Management & Computer Security, 22(1), pp.115-126.
Huang, C.D., Behara, R.S. and Goo, J., 2014. Optimal information security investment
in a Healthcare Information Exchange: An economic analysis. Decision Support
Systems, 61, pp.1-11.
Lebek, B., Uffen, J., Neumann, M., Hohler, B. and H. Breitner, M., 2014. Information
security awareness and behavior: a theory-based literature review. Management
Research Review, 37(12), pp.1049-1092.
Webb, J., Ahmad, A., Maynard, S.B. and Shanks, G., 2014. A situation awareness
model for information security risk management. Computers & security, 44, pp.1-15.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2014, June.
Game theory meets information security management. In IFIP International Information
Security Conference (pp. 15-29). Springer, Berlin, Heidelberg.
Yener, A. and Ulukus, S., 2015. Wireless physical-layer security: Lessons learned from
information theory. Proceedings of the IEEE, 103(10), pp.1814-1825.
Lavenex, S., 2017. Revival: The Europeanisation of Refugee Policies (2001): Between
Human Rights and Internal Security. Routledge.
Bibliography
Enck, W., Gilbert, P., Han, S., Tendulkar, V., Chun, B.G., Cox, L.P., Jung, J., McDaniel,
P. and Sheth, A.N., 2014. TaintDroid: an information-flow tracking system for realtime
privacy monitoring on smartphones. ACM Transactions on Computer Systems
(TOCS), 32(2), p.5.
Jouini, M., Rabai, L.B.A. and Aissa, A.B., 2014. Classification of security threats in
information systems. Procedia Computer Science, 32, pp.489-496.
Laudon, K.C. and Laudon, J.P., 2016. Management information system. Pearson
Education India.
Mahdi, A.O., Alhabbash, M.I. and Naser, S.S.A., 2016. An intelligent tutoring system for
teaching advanced topics in information security.
Elnajjar, A.E.A. and Naser, S.S.A., 2017. DES-Tutor: An Intelligent Tutoring System for
Teaching DES Information Security Algorithm.
AbdAllah, E.G., Hassanein, H.S. and Zulkernine, M., 2015. A survey of security attacks
in information-centric networking. IEEE Communications Surveys & Tutorials, 17(3),
pp.1441-1454.
B. Kim, E., 2014. Recommendations for information security awareness training for
college students. Information Management & Computer Security, 22(1), pp.115-126.
Huang, C.D., Behara, R.S. and Goo, J., 2014. Optimal information security investment
in a Healthcare Information Exchange: An economic analysis. Decision Support
Systems, 61, pp.1-11.
Lebek, B., Uffen, J., Neumann, M., Hohler, B. and H. Breitner, M., 2014. Information
security awareness and behavior: a theory-based literature review. Management
Research Review, 37(12), pp.1049-1092.
Webb, J., Ahmad, A., Maynard, S.B. and Shanks, G., 2014. A situation awareness
model for information security risk management. Computers & security, 44, pp.1-15.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2014, June.
Game theory meets information security management. In IFIP International Information
Security Conference (pp. 15-29). Springer, Berlin, Heidelberg.
Yener, A. and Ulukus, S., 2015. Wireless physical-layer security: Lessons learned from
information theory. Proceedings of the IEEE, 103(10), pp.1814-1825.
Lavenex, S., 2017. Revival: The Europeanisation of Refugee Policies (2001): Between
Human Rights and Internal Security. Routledge.

11STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
Narain Singh, A., Gupta, M.P. and Ojha, A., 2014. Identifying factors of “organizational
information security management”. Journal of Enterprise Information
Management, 27(5), pp.644-667.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
Posey, C., Roberts, T.L., Lowry, P.B. and Hightower, R.T., 2014. Bridging the divide: A
qualitative comparison of information security thought patterns between information
security professionals and ordinary organizational insiders. Information &
management, 51(5), pp.551-567.
Narain Singh, A., Gupta, M.P. and Ojha, A., 2014. Identifying factors of “organizational
information security management”. Journal of Enterprise Information
Management, 27(5), pp.644-667.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
Posey, C., Roberts, T.L., Lowry, P.B. and Hightower, R.T., 2014. Bridging the divide: A
qualitative comparison of information security thought patterns between information
security professionals and ordinary organizational insiders. Information &
management, 51(5), pp.551-567.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





