Strategic Information Systems Analysis of Bell Studio: HI5019 Report
VerifiedAdded on 2023/01/12
|19
|3301
|69
Report
AI Summary
This report provides a comprehensive analysis of Bell Studio's strategic information systems, focusing on transaction cycles, financial reporting, and the identification of internal weaknesses and associated risks. The analysis encompasses the payment, cash disbursement, and payroll systems, utilizing data flow and system flow diagrams to illustrate processes. The report identifies vulnerabilities in the existing systems, including outdated technology, manual processes, and lack of robust security measures. It highlights the risks of data breaches, human errors, and cyberattacks. The report also discusses the need for implementing risk assessment strategies, updating systems, and enhancing security protocols to mitigate potential negative impacts. It emphasizes the importance of ethical considerations and internal controls to safeguard the integrity and efficiency of Bell Studio's operations. The report also provides a detailed overview of the weaknesses associated with each system and the associated risks. The report concludes by emphasizing the need for implementing risk assessment strategies, updating systems, and enhancing security protocols.

Running head: STRATEGIC INFORMATION SYSTEM
Strategic Information System: Bells Studio
[Name of the Student]
[Name of the university]
[Author note]
Strategic Information System: Bells Studio
[Name of the Student]
[Name of the university]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION SYSTEM
Table of Contents
Introduction:....................................................................................................................................2
Discussion........................................................................................................................................4
Data flow diagram of purchases and cash disbursements systems..............................................4
Data flow diagram of payroll system...........................................................................................5
System flowchart of payroll system............................................................................................6
System flowchart of cash disbursements system.........................................................................7
System flowchart of purchases system........................................................................................8
Identified Internal Weaknesses and the risks:.................................................................................9
Conclusion:....................................................................................................................................16
References:....................................................................................................................................17
Table of Contents
Introduction:....................................................................................................................................2
Discussion........................................................................................................................................4
Data flow diagram of purchases and cash disbursements systems..............................................4
Data flow diagram of payroll system...........................................................................................5
System flowchart of payroll system............................................................................................6
System flowchart of cash disbursements system.........................................................................7
System flowchart of purchases system........................................................................................8
Identified Internal Weaknesses and the risks:.................................................................................9
Conclusion:....................................................................................................................................16
References:....................................................................................................................................17

2STRATEGIC INFORMATION SYSTEM
Introduction:
Bells Studio is associated with providing of Adeline based art materials which is responsible for
making this organization one of the most famous and top listed wholesaler. Different countries
are associated with acting as the investment source for Bells Studio and this countries mainly
includes the Japan, China, New Zealand and Australia. From the analysis it has also been
identified that there exists a centralized accounting system which is associated with including
terminals that are networked together and are based in different geographical locations. This
report is created with an aim of analyzing the entire organization Bells Studio for the purpose of
putting forward the different systems which are utilized by Bells Studio so as to facilitate its
processes with outmost efficiency (Goepp & Avila, 2015). For a better overview of the systems
being used by Bells Studio three major systems of the organization has been chosen and this are
Payment System, Cash Disbursement System and the Payroll System. From the analysis it can be
stated that the usage of the centralized form of accounting system is associated with highlighting
the fact that the organization Bells Studio is associated with the usage of Computers for
conducting its different operations. In addition to this there also exists some other processes as
well that has been adopted by Bells Studio for facilitating its operations and this includes the
ledger. Ledger is something which includes manual data entering and is generally used for the
data storage which includes the data gathered from different operations of Bell Studio.
The in-depth case study analysis of Bells Studio have also been highlighting the fact that
there exists certain internal weaknesses as well which are seen to be existing within the process
of Bells Studio. Along with the internal weaknesses certain faults have also been identified after
conducting the analysis (Abdolvand & Sepehri, 2016). It is only possible for the organization to
achieve efficiency if Bell Studio indulges itself in adaptation of certain measures which would
Introduction:
Bells Studio is associated with providing of Adeline based art materials which is responsible for
making this organization one of the most famous and top listed wholesaler. Different countries
are associated with acting as the investment source for Bells Studio and this countries mainly
includes the Japan, China, New Zealand and Australia. From the analysis it has also been
identified that there exists a centralized accounting system which is associated with including
terminals that are networked together and are based in different geographical locations. This
report is created with an aim of analyzing the entire organization Bells Studio for the purpose of
putting forward the different systems which are utilized by Bells Studio so as to facilitate its
processes with outmost efficiency (Goepp & Avila, 2015). For a better overview of the systems
being used by Bells Studio three major systems of the organization has been chosen and this are
Payment System, Cash Disbursement System and the Payroll System. From the analysis it can be
stated that the usage of the centralized form of accounting system is associated with highlighting
the fact that the organization Bells Studio is associated with the usage of Computers for
conducting its different operations. In addition to this there also exists some other processes as
well that has been adopted by Bells Studio for facilitating its operations and this includes the
ledger. Ledger is something which includes manual data entering and is generally used for the
data storage which includes the data gathered from different operations of Bell Studio.
The in-depth case study analysis of Bells Studio have also been highlighting the fact that
there exists certain internal weaknesses as well which are seen to be existing within the process
of Bells Studio. Along with the internal weaknesses certain faults have also been identified after
conducting the analysis (Abdolvand & Sepehri, 2016). It is only possible for the organization to
achieve efficiency if Bell Studio indulges itself in adaptation of certain measures which would
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3STRATEGIC INFORMATION SYSTEM
not only be helping in understanding of the internal weaknesses but would also be responsible
for providing of clear view of the different faults of the organization as well. The faults along
with the internal weaknesses are responsible for the bringing of certain risks which are associated
with them and this risks are considered to be highly responsible for having a huge negative
impact upon the processes of Bells studio (Mostaghel et al., 2015). One of the most important
factor which is responsible for putting forward of this type of risk is the usage of human
resources for the different process of the organization.
After analyzing all the processes of Bells Studio the Dataflow Diagram along with the
flow chart diagram has been used for depicting the different process. The processes which have
been depicted in the diagrams includes the finance reporting, various transactions and many
more. The flowchart diagram has mainly been used for the purpose of depicting the flow of data
through all the main systems as well as through the associated subsystems.
not only be helping in understanding of the internal weaknesses but would also be responsible
for providing of clear view of the different faults of the organization as well. The faults along
with the internal weaknesses are responsible for the bringing of certain risks which are associated
with them and this risks are considered to be highly responsible for having a huge negative
impact upon the processes of Bells studio (Mostaghel et al., 2015). One of the most important
factor which is responsible for putting forward of this type of risk is the usage of human
resources for the different process of the organization.
After analyzing all the processes of Bells Studio the Dataflow Diagram along with the
flow chart diagram has been used for depicting the different process. The processes which have
been depicted in the diagrams includes the finance reporting, various transactions and many
more. The flowchart diagram has mainly been used for the purpose of depicting the flow of data
through all the main systems as well as through the associated subsystems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4STRATEGIC INFORMATION SYSTEM
Discussion
Data flow diagram of purchases and cash disbursements systems
Fig 1: Data flow diagram of purchases and cash disbursements systems
Source: Created by Author
Discussion
Data flow diagram of purchases and cash disbursements systems
Fig 1: Data flow diagram of purchases and cash disbursements systems
Source: Created by Author
5STRATEGIC INFORMATION SYSTEM
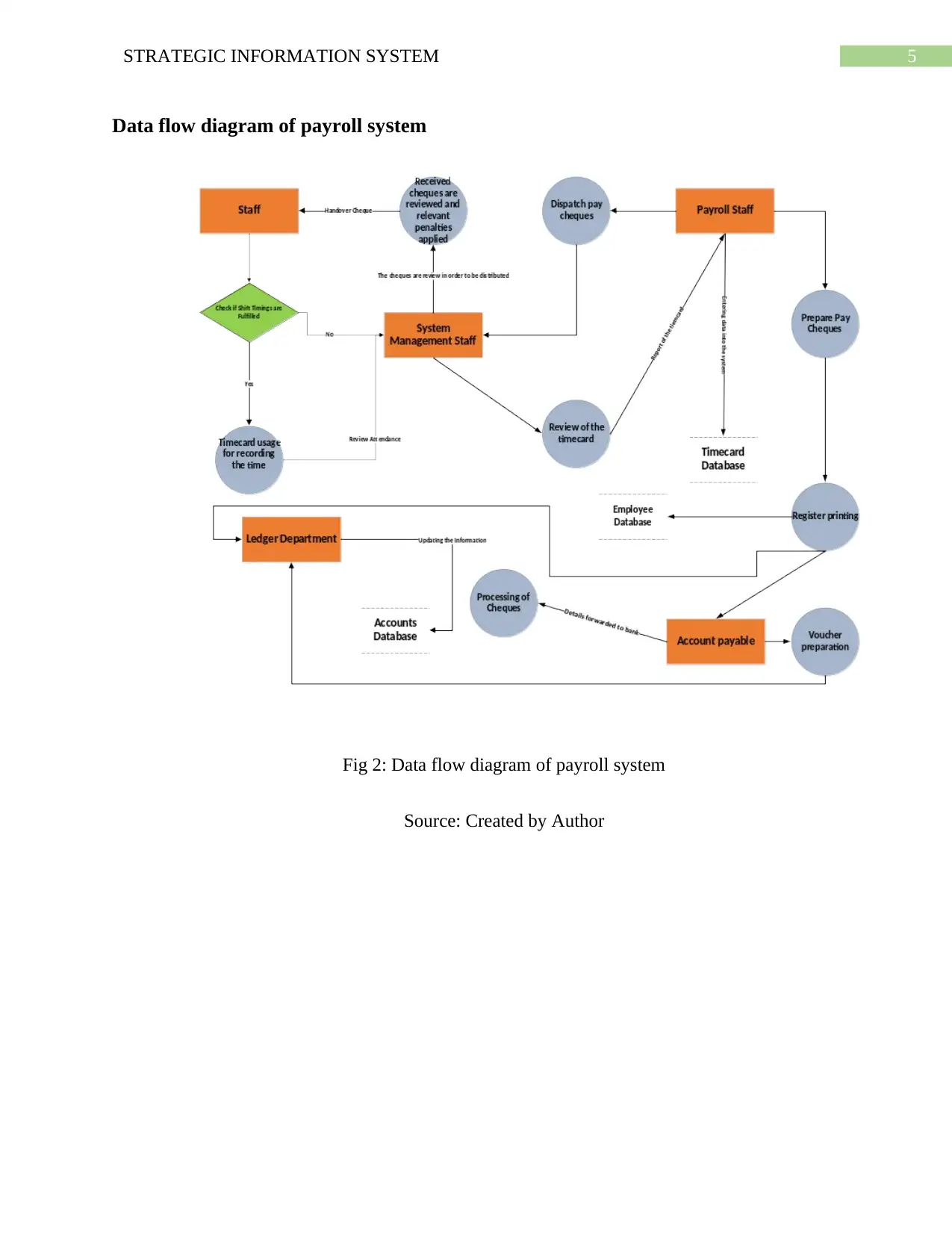
Data flow diagram of payroll system
Fig 2: Data flow diagram of payroll system
Source: Created by Author
Data flow diagram of payroll system
Fig 2: Data flow diagram of payroll system
Source: Created by Author
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6STRATEGIC INFORMATION SYSTEM
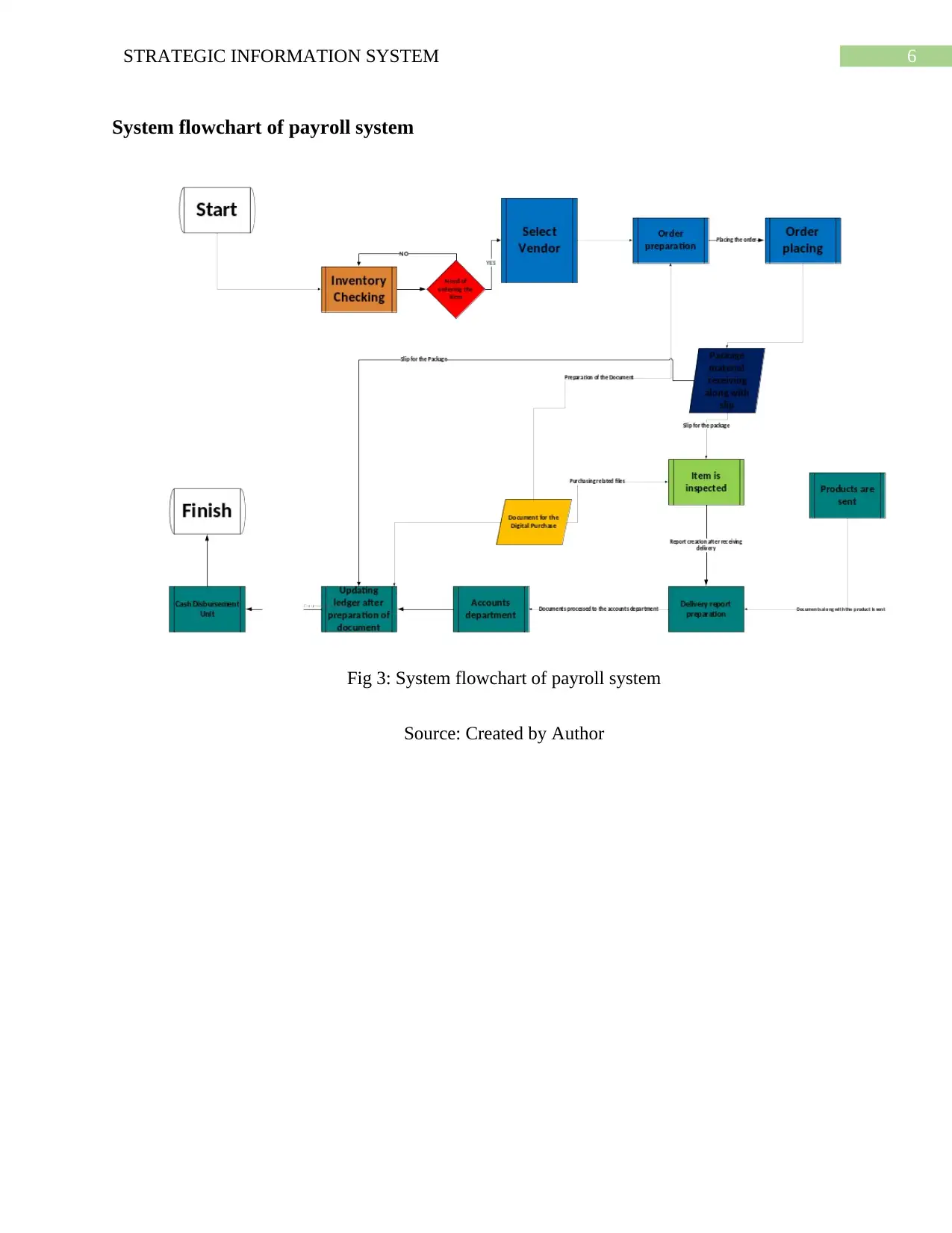
System flowchart of payroll system
Fig 3: System flowchart of payroll system
Source: Created by Author
System flowchart of payroll system
Fig 3: System flowchart of payroll system
Source: Created by Author
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7STRATEGIC INFORMATION SYSTEM
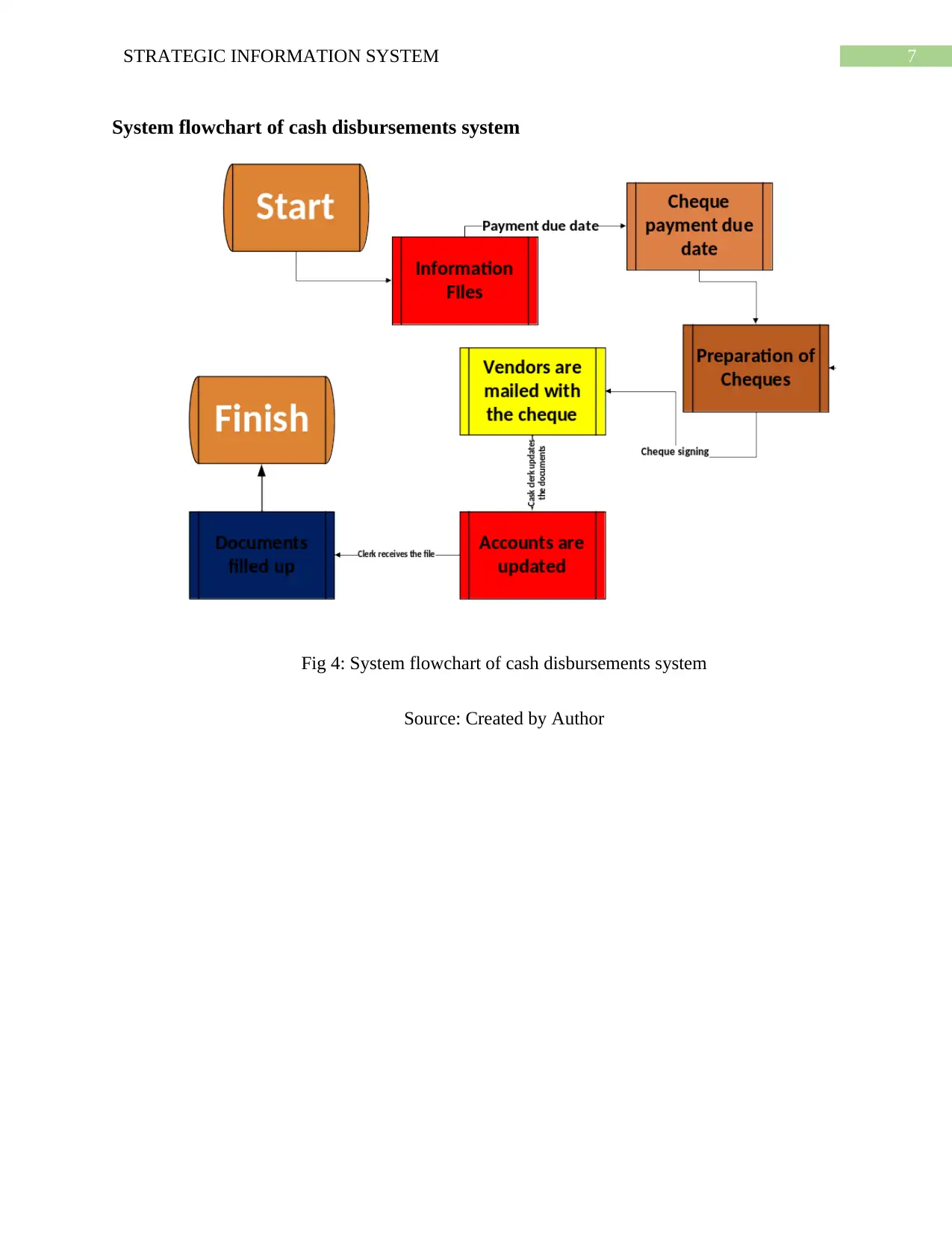
System flowchart of cash disbursements system
Fig 4: System flowchart of cash disbursements system
Source: Created by Author
System flowchart of cash disbursements system
Fig 4: System flowchart of cash disbursements system
Source: Created by Author
8STRATEGIC INFORMATION SYSTEM
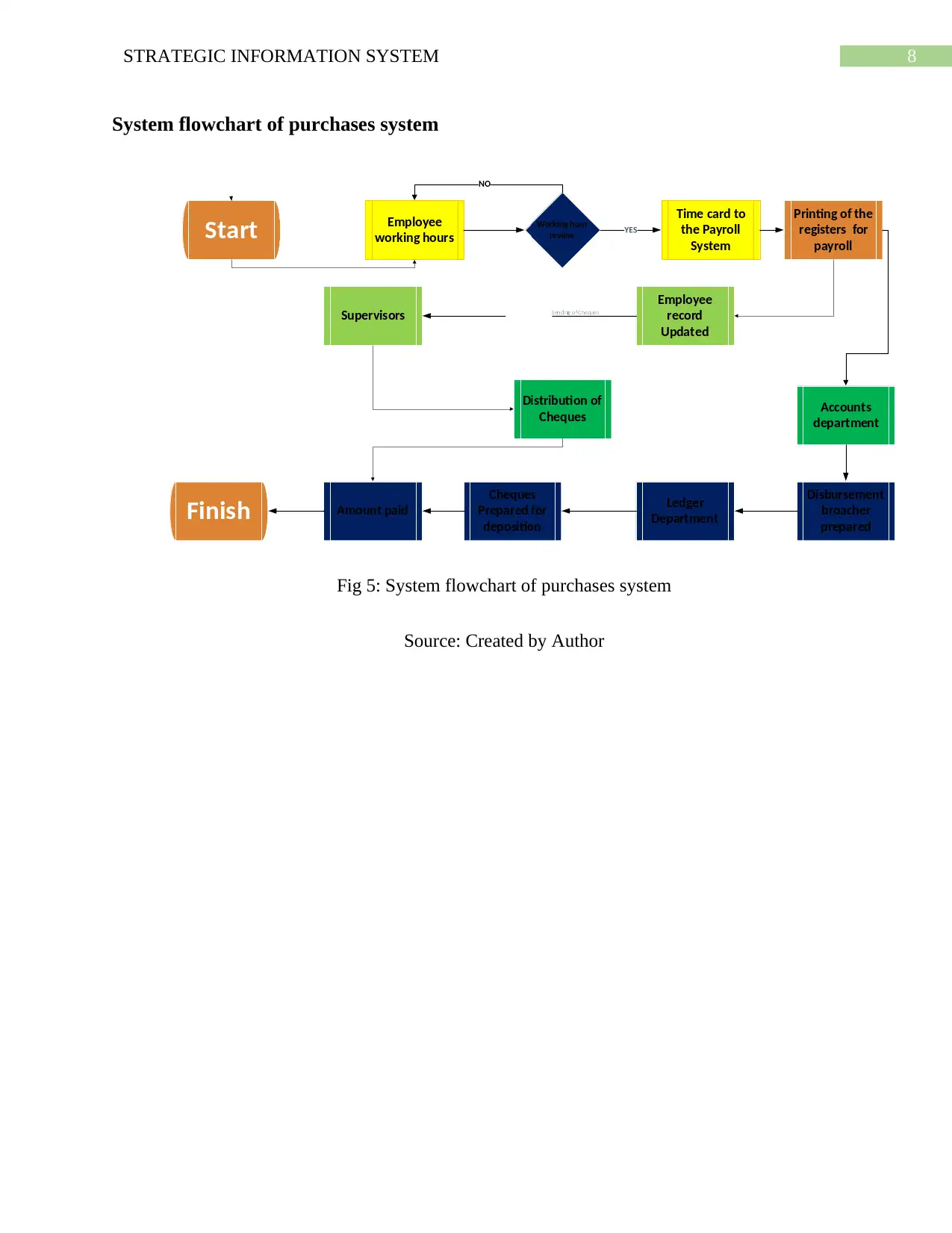
System flowchart of purchases system
Fig 5: System flowchart of purchases system
Source: Created by Author
System flowchart of purchases system
Fig 5: System flowchart of purchases system
Source: Created by Author
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION SYSTEM
Identified Internal Weaknesses and the risks:
The in-depth analysis of the entire case study of Bells Studio have been associated with
helping in getting an overview of the various internal weaknesses which the different systems are
of Bells Studio is having along with getting an overview of the risks associated with it (Newell &
Marabelli, 2015). Amongst the identified weaknesses some of them can be ignored whereas
some of them needs to be considered necessarily and the reason behind this is that this risks
would be severely associated with hampering the processes of the entire organization. For this
reason it is very important to understand the risks which are put forward and an in-depth analysis
needs to be conducted. This would be helping in the determination of certain strategies or
procedures which would be used for the purpose of mitigating the risk impacts (Ho &
O'Sullivan, 2017). In addition to all this the implementation of the strategy would also be
associated with assisting in getting improved processes which in turn would be helping in proper
functioning of the entire organization in an efficient manner. The later section of the report is
associated with some of the major internal weaknesses of the organization.
From the analysis it can also be stated that there exists a high level of criticalness along
with complexity in the different systems of the organization which mainly includes the Cash
Disbursement system and the Purchasing system. So from here it can be stated that the any type
of change in the system is necessarily to be highlighted so as to makes sure that changes are not
being ignored (Wager, Lee & Glaser, 2017). In addition to all this the organization also needs to
formulate a proper risk assessment strategy which would be helping the entire organization in
complete elimination or mitigation of the risks which would rise. The reason behind the
adaptation of the risk assessment strategy is because any kind of changes in the processes would
be highly responsible for the disruption of the operations.
Identified Internal Weaknesses and the risks:
The in-depth analysis of the entire case study of Bells Studio have been associated with
helping in getting an overview of the various internal weaknesses which the different systems are
of Bells Studio is having along with getting an overview of the risks associated with it (Newell &
Marabelli, 2015). Amongst the identified weaknesses some of them can be ignored whereas
some of them needs to be considered necessarily and the reason behind this is that this risks
would be severely associated with hampering the processes of the entire organization. For this
reason it is very important to understand the risks which are put forward and an in-depth analysis
needs to be conducted. This would be helping in the determination of certain strategies or
procedures which would be used for the purpose of mitigating the risk impacts (Ho &
O'Sullivan, 2017). In addition to all this the implementation of the strategy would also be
associated with assisting in getting improved processes which in turn would be helping in proper
functioning of the entire organization in an efficient manner. The later section of the report is
associated with some of the major internal weaknesses of the organization.
From the analysis it can also be stated that there exists a high level of criticalness along
with complexity in the different systems of the organization which mainly includes the Cash
Disbursement system and the Purchasing system. So from here it can be stated that the any type
of change in the system is necessarily to be highlighted so as to makes sure that changes are not
being ignored (Wager, Lee & Glaser, 2017). In addition to all this the organization also needs to
formulate a proper risk assessment strategy which would be helping the entire organization in
complete elimination or mitigation of the risks which would rise. The reason behind the
adaptation of the risk assessment strategy is because any kind of changes in the processes would
be highly responsible for the disruption of the operations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION SYSTEM
In addition to this another major weakness is seen to be faced because of the existence of some
administrators who are associated with providing of updates that are entirely delayed during the
process of preventing a shutdown of a particular process or for the downtime faced by the
system. The analysis has also highlighted the fact that the organization is associated with the
usage of traditional means which includes the usage of the outdated systems and this in turn is
associated with making the systems face a lag in terms of the patches needed. This in turn is seen
to be associated with putting the organization Bells Studio in front of huge amount of risks.
The usage of the outdated systems by Bells Studio is seen to be having lots of gaps which
have been identified and along with this might also be seen to be associated with prevailing for a
couple of years (Patil & Wongsurawat, 2015). This in turn has been associated with indicating
the fact that the system is entirely deprived from the entire existence of the software patches or
are having a delayed security software patch. All this facts are initially responsible for extending
all the major risks that are faced because of the internal weaknesses.
Along with the risks associated with the internal weaknesses there also exists certain
external risks as well which are faced by the organization Bells Studio. The risks which are
considered to external are mainly associated with including those risks which are faced because
of the different external sources such as the hackers or stakeholders of the organization. The
usage of the manual method of managing the hardcopies of the various documents is associated
with putting forward of the risks which might occur because of the errors occurring in the work
done by humans and this might be associated with leading to misplacement or loss of data due to
theft or any kind of disasters such as fire and many more (Obeidat, Al-Dmour & Tarhini, 2015).
The usage of the computers by eth organization is associated with putting forward of the risks
related to data breach by hackers or by malicious insiders. The computers are generally used for
In addition to this another major weakness is seen to be faced because of the existence of some
administrators who are associated with providing of updates that are entirely delayed during the
process of preventing a shutdown of a particular process or for the downtime faced by the
system. The analysis has also highlighted the fact that the organization is associated with the
usage of traditional means which includes the usage of the outdated systems and this in turn is
associated with making the systems face a lag in terms of the patches needed. This in turn is seen
to be associated with putting the organization Bells Studio in front of huge amount of risks.
The usage of the outdated systems by Bells Studio is seen to be having lots of gaps which
have been identified and along with this might also be seen to be associated with prevailing for a
couple of years (Patil & Wongsurawat, 2015). This in turn has been associated with indicating
the fact that the system is entirely deprived from the entire existence of the software patches or
are having a delayed security software patch. All this facts are initially responsible for extending
all the major risks that are faced because of the internal weaknesses.
Along with the risks associated with the internal weaknesses there also exists certain
external risks as well which are faced by the organization Bells Studio. The risks which are
considered to external are mainly associated with including those risks which are faced because
of the different external sources such as the hackers or stakeholders of the organization. The
usage of the manual method of managing the hardcopies of the various documents is associated
with putting forward of the risks which might occur because of the errors occurring in the work
done by humans and this might be associated with leading to misplacement or loss of data due to
theft or any kind of disasters such as fire and many more (Obeidat, Al-Dmour & Tarhini, 2015).
The usage of the computers by eth organization is associated with putting forward of the risks
related to data breach by hackers or by malicious insiders. The computers are generally used for

11STRATEGIC INFORMATION SYSTEM
managing the vital invoices of the organization along with the data which are critical for the
operations of the organization. The reason which lies behind the data breach is associated with
including the involvement of the hackers continuously for the purpose of finding the loopholes
which would be helping them in entering the system and would be providing them with the
capability of extracting all the vital information of the organization which are needed by them or
might be associated with leading to entire compromise of the organizational data (Singh et al.,
2017). The organization is also associated with eth usage of the database for the purpose of
storing the information and from the analysis it has been identified that the database is not having
any kind of appropriate as well as strong security mechanism for the purpose of providing
security to the entire data. This kind of absence of the security measures is associated with
putting the systems of the organization in front of numerous threats which are mainly seen to be
imposed by the cybercriminals or from the malicious employees. So for this reason after
conducting the analysis it can be stated that there is an essential need of implementing certain
security measures along with the appropriate policies, procedures and regulations which would
be helping the organization in finding out certain ways by which they would become capable of
mitigating the risks or would be helping entire elimination of the risks. This strategies would be
responsible for the strengthening of the entire security mechanism of the organization along with
being associated with immense strengthening of the Bell Studios capabilities so as to help them
in performing in an efficient way.
In addition to all this it is also possible for the external sources which mainly includes the
cybercriminals, to exploit all the systems of the organization which would be initially responsible
for making the organization have an essential need of focusing extensively upon the different
security mechanisms in order to provide protection to the vital assets of the organization as well
managing the vital invoices of the organization along with the data which are critical for the
operations of the organization. The reason which lies behind the data breach is associated with
including the involvement of the hackers continuously for the purpose of finding the loopholes
which would be helping them in entering the system and would be providing them with the
capability of extracting all the vital information of the organization which are needed by them or
might be associated with leading to entire compromise of the organizational data (Singh et al.,
2017). The organization is also associated with eth usage of the database for the purpose of
storing the information and from the analysis it has been identified that the database is not having
any kind of appropriate as well as strong security mechanism for the purpose of providing
security to the entire data. This kind of absence of the security measures is associated with
putting the systems of the organization in front of numerous threats which are mainly seen to be
imposed by the cybercriminals or from the malicious employees. So for this reason after
conducting the analysis it can be stated that there is an essential need of implementing certain
security measures along with the appropriate policies, procedures and regulations which would
be helping the organization in finding out certain ways by which they would become capable of
mitigating the risks or would be helping entire elimination of the risks. This strategies would be
responsible for the strengthening of the entire security mechanism of the organization along with
being associated with immense strengthening of the Bell Studios capabilities so as to help them
in performing in an efficient way.
In addition to all this it is also possible for the external sources which mainly includes the
cybercriminals, to exploit all the systems of the organization which would be initially responsible
for making the organization have an essential need of focusing extensively upon the different
security mechanisms in order to provide protection to the vital assets of the organization as well
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




