Strategic Information Systems Analysis of Bell Studio: Recommendations
VerifiedAdded on 2022/11/24
|17
|2412
|91
Report
AI Summary
This report examines Bell Studio, an Adelaide-based art supplies wholesaler, and its strategic information systems. It analyzes the company's expenditure cycle, including purchasing, cash disbursements, and payroll systems, using data flow diagrams and system flowcharts. The report identifies several internal control weaknesses, such as paper-based documentation, manual payment processing, outdated computer systems, and payroll system vulnerabilities. These weaknesses lead to associated risks, including calculation errors, manual payment process risks, cyber security threats, and incorrect payroll processing. The report recommends implementing a technically updated information system to automate operations, digitalize documents, enhance security, and integrate a biometric attendance system. Furthermore, it suggests electronic payments to mitigate identified risks and improve the overall efficiency and security of Bell Studio's information systems.

Running Head: STRATEGIC INFORMATION SYSTEMS
Strategic Information Systems
Name of the Student
Name of the University
Strategic Information Systems
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION SYSTEMS
Executive Summary
The organisation under focus in this report is Bell Studio, a wholesaler of art supplies that is
based in Adelaide, Australia. Bell Studio utilizes a centralized accounting system that is
connected to various network terminals at different locations. In this system, there are some
control weaknesses that include use of hard copies and paper documents, manual recording and
data processing, manual payment processing through paper cheques, lack of information security
in the company computers and others. Due to these control weaknesses, many risks arise that
include cyber security threat, incorrect data processing, errors in payments, tampering of
important and critical documents, incorrect payroll records and others. For mitigating these risks,
it has been recommended for Bell Studio to deploy an information system with technically
updated hardware and software.
Executive Summary
The organisation under focus in this report is Bell Studio, a wholesaler of art supplies that is
based in Adelaide, Australia. Bell Studio utilizes a centralized accounting system that is
connected to various network terminals at different locations. In this system, there are some
control weaknesses that include use of hard copies and paper documents, manual recording and
data processing, manual payment processing through paper cheques, lack of information security
in the company computers and others. Due to these control weaknesses, many risks arise that
include cyber security threat, incorrect data processing, errors in payments, tampering of
important and critical documents, incorrect payroll records and others. For mitigating these risks,
it has been recommended for Bell Studio to deploy an information system with technically
updated hardware and software.

2STRATEGIC INFORMATION SYSTEMS
Table of Contents
1. Introduction and Overview of the Report....................................................................................3
2. Discussion of the Case of Bell Studio.........................................................................................4
2.1 Data Flow Diagrams..............................................................................................................4
2.1.1 Purchase and Cash Disbursement Systems.....................................................................4
2.1.2 Payroll System................................................................................................................6
2.2 System Flowcharts.................................................................................................................7
2.2.1 Purchases System............................................................................................................7
2.2.2 Cash Disbursements System...........................................................................................8
2.2.3 Payroll System................................................................................................................9
2.3 Internal Control Weaknesses with the Systems and Associated Risks................................10
2.3.1 Internal Control Weaknesses........................................................................................10
2.3.2 Associated Risks...........................................................................................................11
2.4 Recommendations................................................................................................................13
3. Conclusion.................................................................................................................................14
References......................................................................................................................................15
Table of Contents
1. Introduction and Overview of the Report....................................................................................3
2. Discussion of the Case of Bell Studio.........................................................................................4
2.1 Data Flow Diagrams..............................................................................................................4
2.1.1 Purchase and Cash Disbursement Systems.....................................................................4
2.1.2 Payroll System................................................................................................................6
2.2 System Flowcharts.................................................................................................................7
2.2.1 Purchases System............................................................................................................7
2.2.2 Cash Disbursements System...........................................................................................8
2.2.3 Payroll System................................................................................................................9
2.3 Internal Control Weaknesses with the Systems and Associated Risks................................10
2.3.1 Internal Control Weaknesses........................................................................................10
2.3.2 Associated Risks...........................................................................................................11
2.4 Recommendations................................................................................................................13
3. Conclusion.................................................................................................................................14
References......................................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3STRATEGIC INFORMATION SYSTEMS
1. Introduction and Overview of the Report
Bell Studio is a wholesaler of art supplies that is based in Adelaide, Australia. Bell Studio
utilizes a centralized accounting system that is connected to various network terminals at
different locations. The company’s expenditure cycle procedures include a purchases system,
cash disbursements system and a payroll system. These procedures determine the cash flow
within the organisation through a specific and structured approach.
This report discusses about the various processes within the expenditure cycle along with
detailed elaboration using data flow diagrams and flowcharts. Furthermore, the internal control
weaknesses of the company have been discussed and the risks associated with these weaknesses
have been explored.
1. Introduction and Overview of the Report
Bell Studio is a wholesaler of art supplies that is based in Adelaide, Australia. Bell Studio
utilizes a centralized accounting system that is connected to various network terminals at
different locations. The company’s expenditure cycle procedures include a purchases system,
cash disbursements system and a payroll system. These procedures determine the cash flow
within the organisation through a specific and structured approach.
This report discusses about the various processes within the expenditure cycle along with
detailed elaboration using data flow diagrams and flowcharts. Furthermore, the internal control
weaknesses of the company have been discussed and the risks associated with these weaknesses
have been explored.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
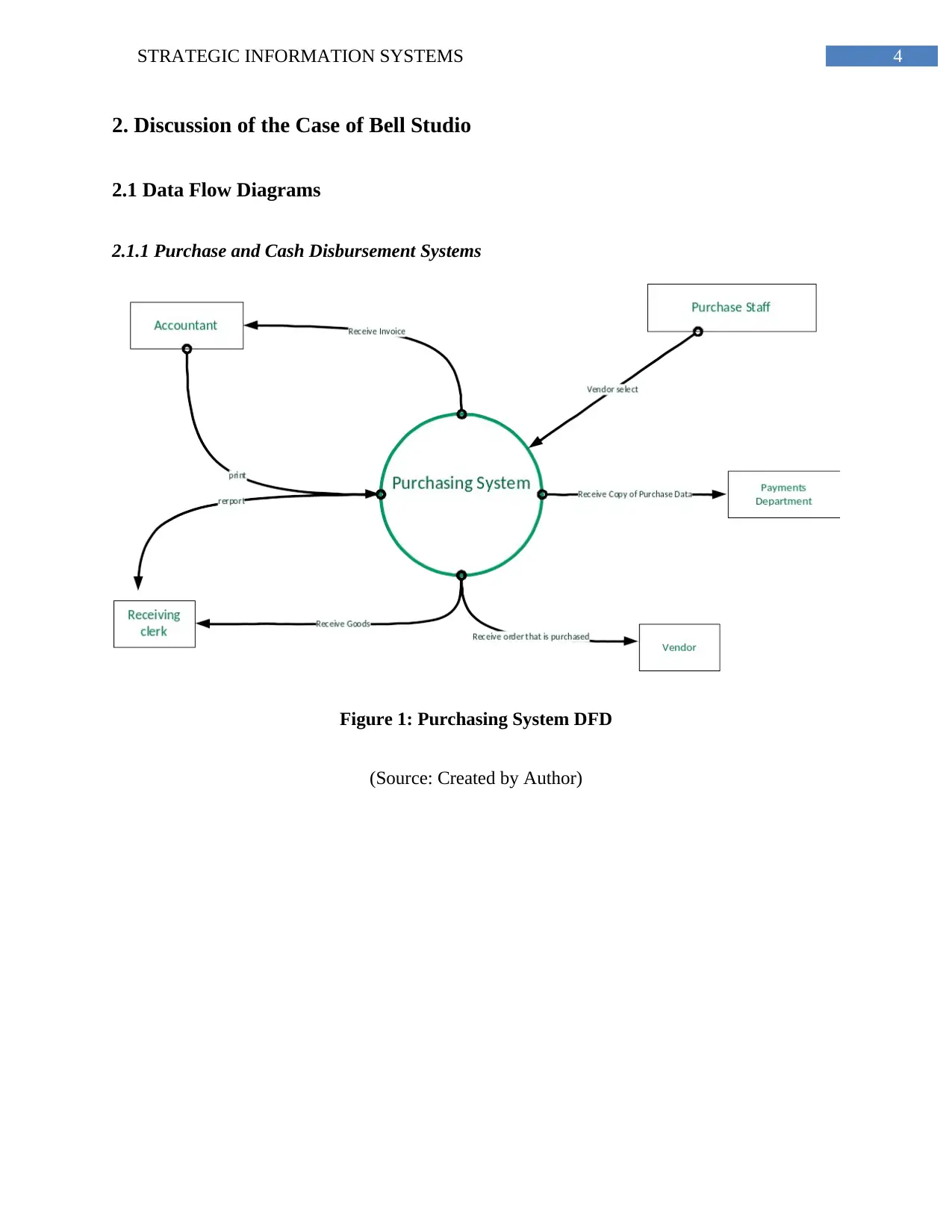
4STRATEGIC INFORMATION SYSTEMS
2. Discussion of the Case of Bell Studio
2.1 Data Flow Diagrams
2.1.1 Purchase and Cash Disbursement Systems
Figure 1: Purchasing System DFD
(Source: Created by Author)
2. Discussion of the Case of Bell Studio
2.1 Data Flow Diagrams
2.1.1 Purchase and Cash Disbursement Systems
Figure 1: Purchasing System DFD
(Source: Created by Author)
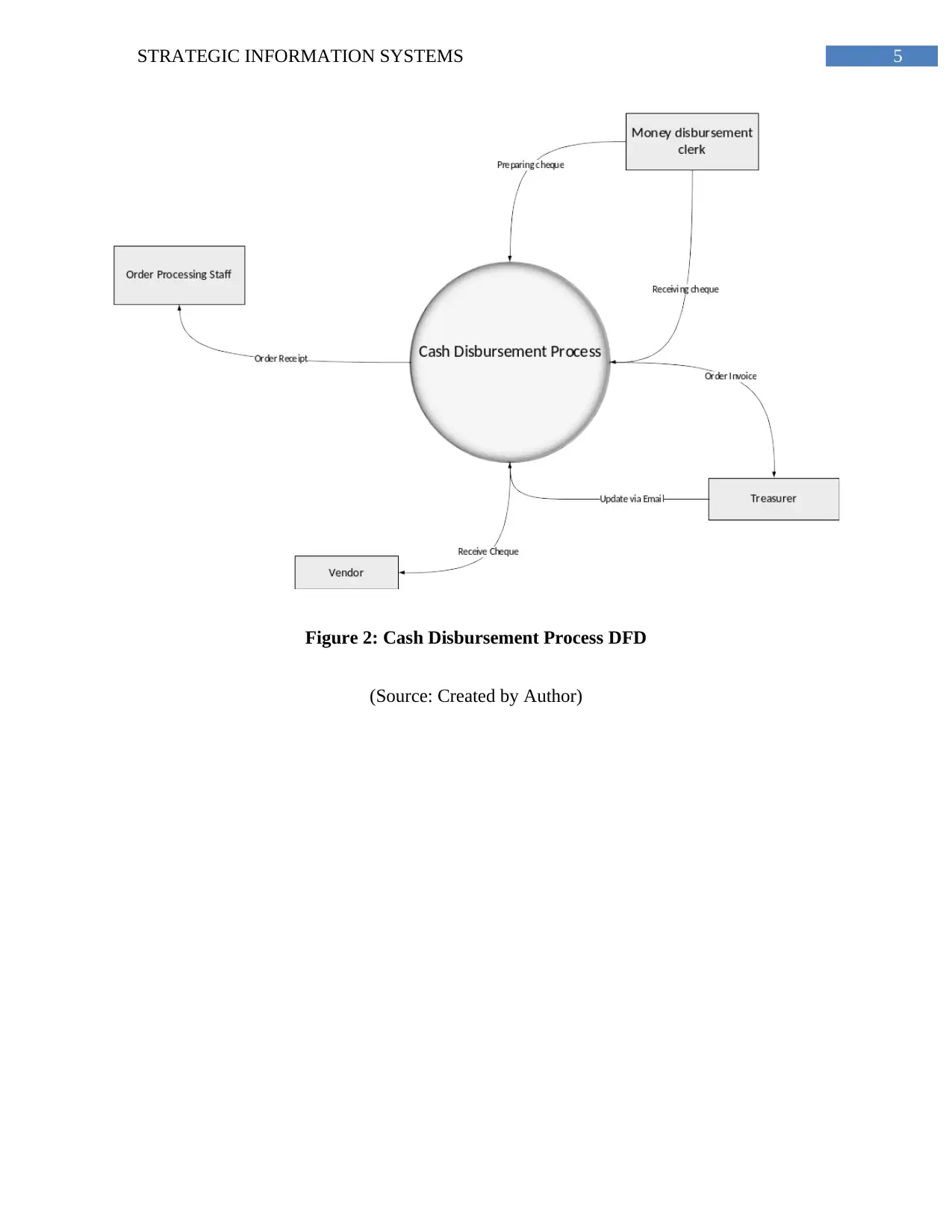
5STRATEGIC INFORMATION SYSTEMS
Figure 2: Cash Disbursement Process DFD
(Source: Created by Author)
Figure 2: Cash Disbursement Process DFD
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
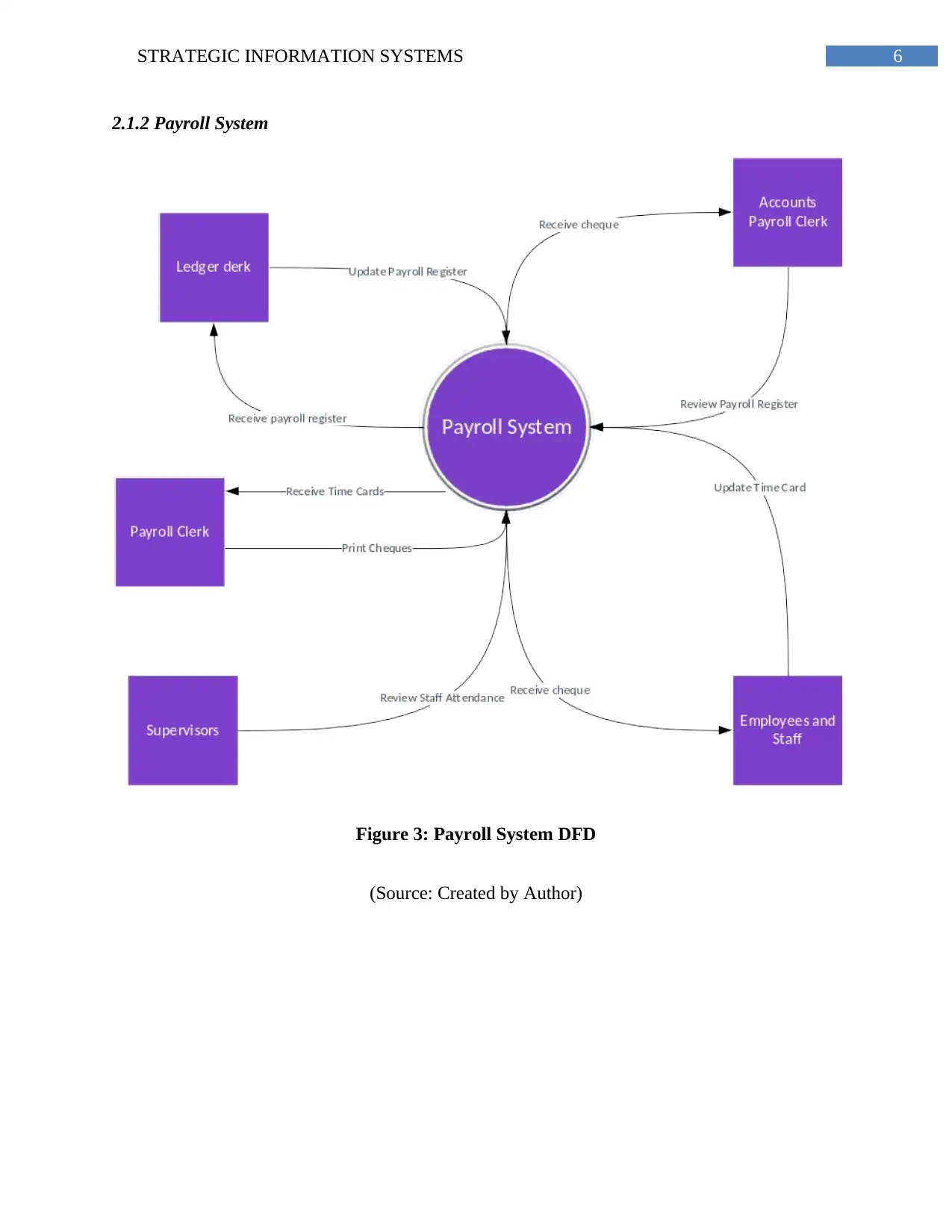
6STRATEGIC INFORMATION SYSTEMS
2.1.2 Payroll System
Figure 3: Payroll System DFD
(Source: Created by Author)
2.1.2 Payroll System
Figure 3: Payroll System DFD
(Source: Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
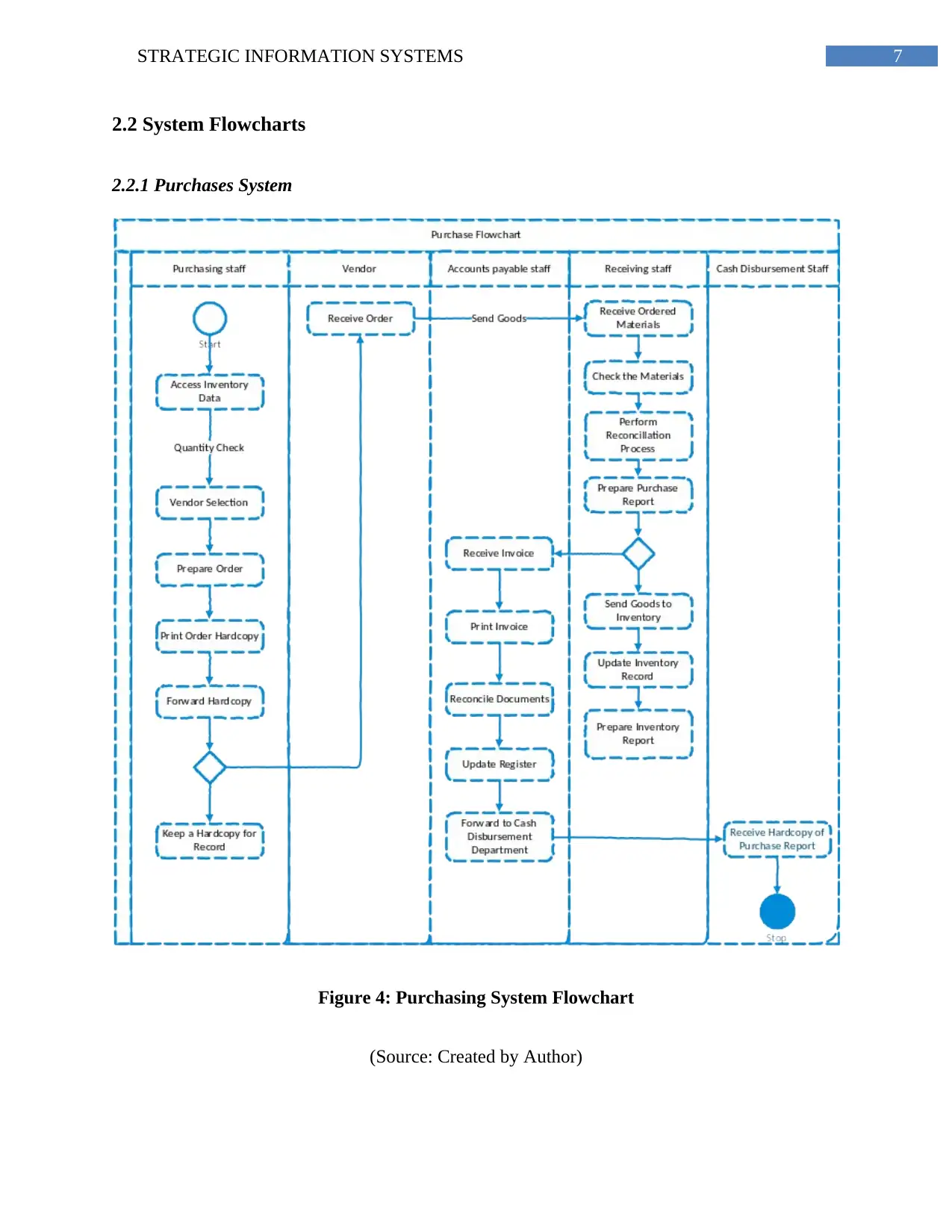
7STRATEGIC INFORMATION SYSTEMS
2.2 System Flowcharts
2.2.1 Purchases System
Figure 4: Purchasing System Flowchart
(Source: Created by Author)
2.2 System Flowcharts
2.2.1 Purchases System
Figure 4: Purchasing System Flowchart
(Source: Created by Author)
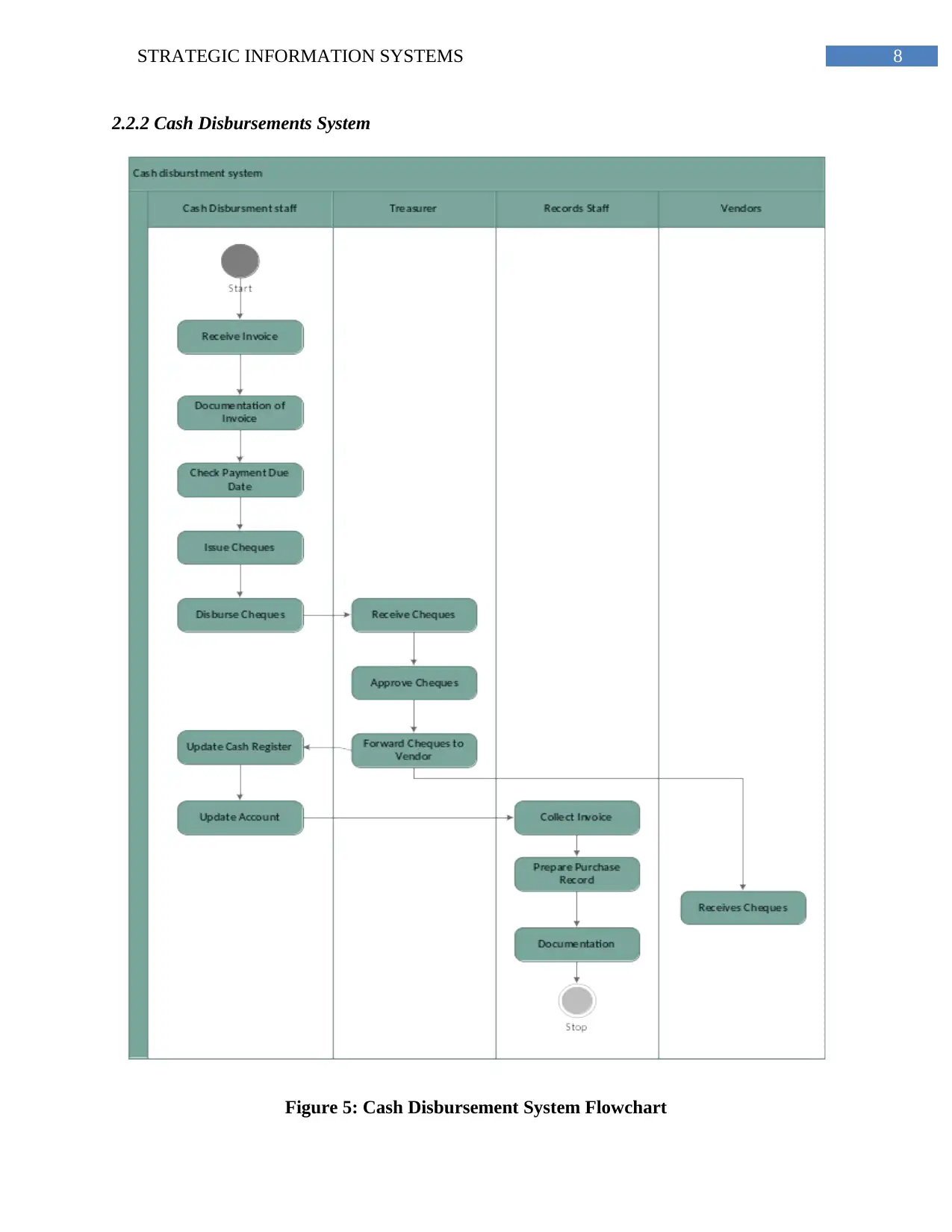
8STRATEGIC INFORMATION SYSTEMS
2.2.2 Cash Disbursements System
Figure 5: Cash Disbursement System Flowchart
2.2.2 Cash Disbursements System
Figure 5: Cash Disbursement System Flowchart
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9STRATEGIC INFORMATION SYSTEMS
(Source: Created by Author)
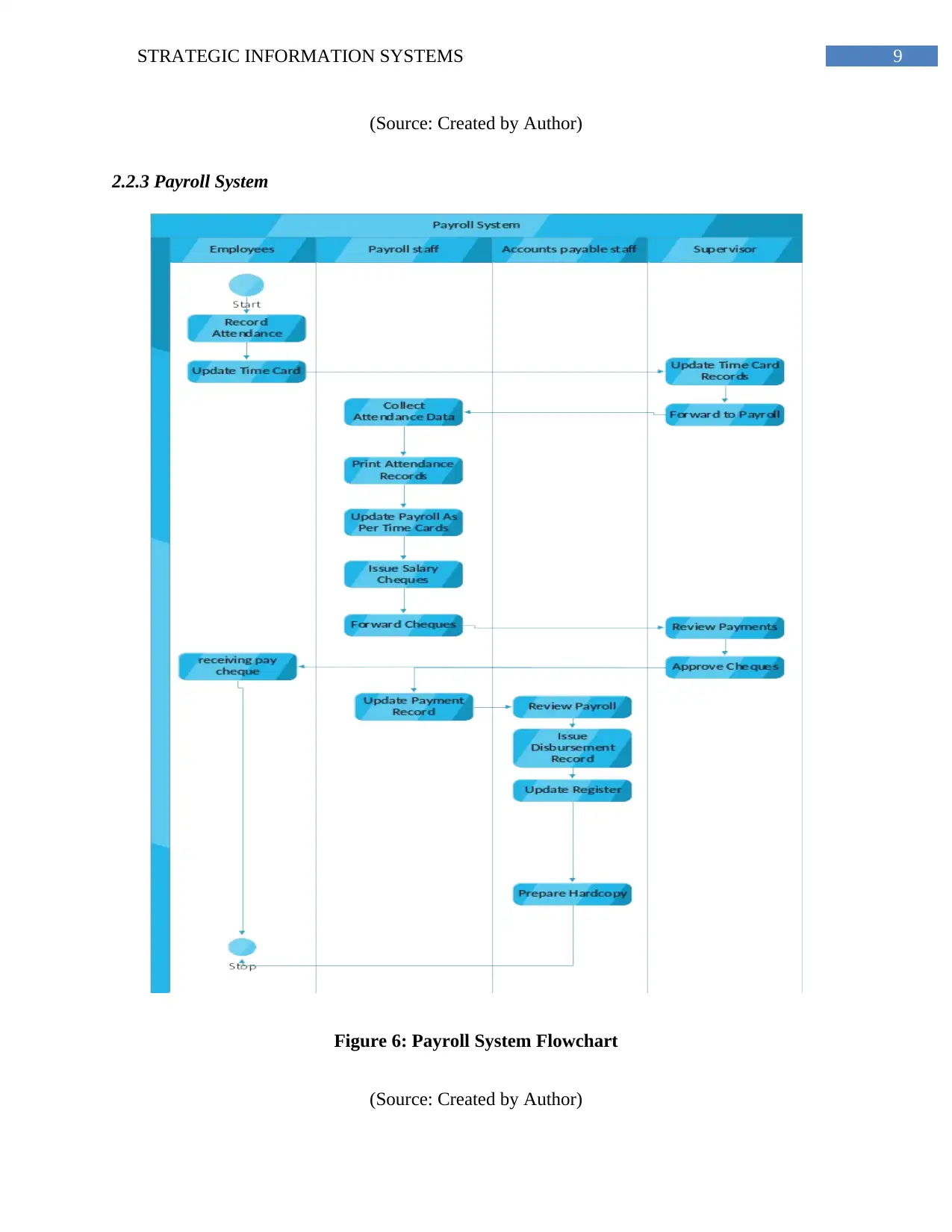
2.2.3 Payroll System
Figure 6: Payroll System Flowchart
(Source: Created by Author)
(Source: Created by Author)
2.2.3 Payroll System
Figure 6: Payroll System Flowchart
(Source: Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION SYSTEMS
2.3 Internal Control Weaknesses with the Systems and Associated Risks
2.3.1 Internal Control Weaknesses
In the current expenditure cycle processes of Bell Studio, there are a number of internal
control weaknesses that can serious risks and threats to the system. These control weaknesses
arise from a number of systems and processes that are completely backdated and pose security
and other threats to the system. Some of the control weaknesses of Bell Studio are as follows.
Paper Oriented Documentation System – The first main control weakness of the
expenditure cycle of Bell Studio is that the entire process is paper oriented. All the transaction
processes, invoice generations, processing of the cheques, sending reports and others are done
through paper documents (hard copies) (Galliers & Leidner, 2014). This is a significant
weakness in the system as the entire process is very slow and error prone that is mainly due to
manual processing throughout the life cycle. Moreover, the hard copies are needed to be passed
through a large number of stakeholders that consume a lot of time. Again, the hardcopies can be
easily stolen or destroyed that is not desired for the organisation of the scale of Bell Studio.
Manual Payment System – All payments are done through manually operated systems in
which based on the records, cheques are processed by the payroll staff and are sent to the
employees of the organisation. Once the cheques are issued, they can be tampered or stolen by
some unauthorized personnel (Pearlson, Saunders & Galletta, 2016). Again, these cheques can be
lost or easily destroyed as a result of which, the payments of some of the employees may not be
processed at all.
Backdated Computer System – The computers of Bell Studio are completely backdated
and have very limited features as opposed to the features that are desired for Bell Studio.
2.3 Internal Control Weaknesses with the Systems and Associated Risks
2.3.1 Internal Control Weaknesses
In the current expenditure cycle processes of Bell Studio, there are a number of internal
control weaknesses that can serious risks and threats to the system. These control weaknesses
arise from a number of systems and processes that are completely backdated and pose security
and other threats to the system. Some of the control weaknesses of Bell Studio are as follows.
Paper Oriented Documentation System – The first main control weakness of the
expenditure cycle of Bell Studio is that the entire process is paper oriented. All the transaction
processes, invoice generations, processing of the cheques, sending reports and others are done
through paper documents (hard copies) (Galliers & Leidner, 2014). This is a significant
weakness in the system as the entire process is very slow and error prone that is mainly due to
manual processing throughout the life cycle. Moreover, the hard copies are needed to be passed
through a large number of stakeholders that consume a lot of time. Again, the hardcopies can be
easily stolen or destroyed that is not desired for the organisation of the scale of Bell Studio.
Manual Payment System – All payments are done through manually operated systems in
which based on the records, cheques are processed by the payroll staff and are sent to the
employees of the organisation. Once the cheques are issued, they can be tampered or stolen by
some unauthorized personnel (Pearlson, Saunders & Galletta, 2016). Again, these cheques can be
lost or easily destroyed as a result of which, the payments of some of the employees may not be
processed at all.
Backdated Computer System – The computers of Bell Studio are completely backdated
and have very limited features as opposed to the features that are desired for Bell Studio.

11STRATEGIC INFORMATION SYSTEMS
Moreover, the use of backdated computers makes the system vulnerable to the external cyber
security attacks (Arvidsson, Holmström & Lyytinen, 2014). The backdated systems are least
resistant to the security threats as they have limited system protection functionalities.
Payroll System – The control weakness associated with the payroll system of the
employees is that the wages are processed based on the attendance records from the time card
data recorded (Cassidy, 2016). The weakness factor in this regard is that the time cards can be
easily tampered or altered that will result in misinformation about the attendance of the employee
that will in turn lead to the wrong amount of salary processed for that particular employee.
Again, this is not desired for the company of the scale of Bell Studio.
2.3.2 Associated Risks
Following the analysis of the control weaknesses analysed above, there risks associated
with the system based on the control weaknesses are explored and discussed as follows.
Errors in Calculations and Statistical Data Records – One major risk that arises from the
control weakness of the system is the increase in the chances of errors in the calculations and
statistical data processed within the company. The entire process is manually handled on paper
documents and hence, there are numerous errors in the records. These errors often go through the
attention of the control staff and hence, remain unchanged (Whittington, 2014). These errors
result in significant problems within the internal processes of the company. In addition to the
manual errors, the entire process is extremely slow as the operations are time consuming and the
hard copies need to be transferred through a large number of staff and employees that consume a
lot of time (Ismail & King, 2014). Hence, the overall processing and response time for a
Moreover, the use of backdated computers makes the system vulnerable to the external cyber
security attacks (Arvidsson, Holmström & Lyytinen, 2014). The backdated systems are least
resistant to the security threats as they have limited system protection functionalities.
Payroll System – The control weakness associated with the payroll system of the
employees is that the wages are processed based on the attendance records from the time card
data recorded (Cassidy, 2016). The weakness factor in this regard is that the time cards can be
easily tampered or altered that will result in misinformation about the attendance of the employee
that will in turn lead to the wrong amount of salary processed for that particular employee.
Again, this is not desired for the company of the scale of Bell Studio.
2.3.2 Associated Risks
Following the analysis of the control weaknesses analysed above, there risks associated
with the system based on the control weaknesses are explored and discussed as follows.
Errors in Calculations and Statistical Data Records – One major risk that arises from the
control weakness of the system is the increase in the chances of errors in the calculations and
statistical data processed within the company. The entire process is manually handled on paper
documents and hence, there are numerous errors in the records. These errors often go through the
attention of the control staff and hence, remain unchanged (Whittington, 2014). These errors
result in significant problems within the internal processes of the company. In addition to the
manual errors, the entire process is extremely slow as the operations are time consuming and the
hard copies need to be transferred through a large number of staff and employees that consume a
lot of time (Ismail & King, 2014). Hence, the overall processing and response time for a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




