HI5019 Strategic Information Systems Assignment: Tutorial Questions
VerifiedAdded on 2023/01/06
|15
|3298
|21
Homework Assignment
AI Summary
This document presents a comprehensive analysis of strategic information systems within a business and enterprise context. It begins with an introduction that highlights the efficiency gains technology offers across various business functions like accounting, management reporting, and ethical operations, while also addressing information system privacy. The main body of the document then addresses six key questions. Question 1 explores transaction processing systems (TPS), their fraud-reduction capabilities, and analyzes a flowchart of business processes, identifying potential vulnerabilities. Question 2 examines the advantages of alternative purchase order processes, contrasts purchase requisitions and orders, and discusses scenarios where different approaches are suitable. Question 3 delves into the risks associated with a payroll system and proposes control measures to mitigate them. Question 4 identifies risks within a manufacturing company, including supply chain, inventory, and labor-related issues, and proposes mitigation strategies. Question 5 presents a memo to the Chief Operating Officer outlining the risks associated with consulting firms during the implementation of an Enterprise Resource Planning (ERP) system. Finally, the conclusion summarizes the key findings and recommendations, emphasizing the importance of strategic information systems in achieving organizational goals, reducing fraud, and enhancing productivity. The document references various academic sources to support its analysis.

Strategic Information Systems for
Business and Enterprise
Business and Enterprise
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction.................................................................................................................................................3
Main body...................................................................................................................................................3
Question 1...............................................................................................................................................3
Question 2...............................................................................................................................................4
Question 3...............................................................................................................................................6
Question 4...............................................................................................................................................6
Question 5...............................................................................................................................................7
Question 6...............................................................................................................................................8
Conclusion...................................................................................................................................................9
References.................................................................................................................................................10
Introduction.................................................................................................................................................3
Main body...................................................................................................................................................3
Question 1...............................................................................................................................................3
Question 2...............................................................................................................................................4
Question 3...............................................................................................................................................6
Question 4...............................................................................................................................................6
Question 5...............................................................................................................................................7
Question 6...............................................................................................................................................8
Conclusion...................................................................................................................................................9
References.................................................................................................................................................10

Introduction
This is a look into report throwing light on efficiency that technology provides to various
business operations and transaction like accounting operations, management reporting systems,
maintaining ethical operations and privacy of information systems. In this report, study is made
related to use of various technologies in business operations like accounting systems, internal
control management, payroll system, business processes of manufacturing company, system
development life cycle. This report is categorized into five categories that will answering to
prescribes question by developing an understanding of flowcharts. These information systems
that will be learnt during this report assist in strategies effective strategies and policies which are
directed in achieving organizational goals and objectives. Information system also helps in
decreasing fraudulent activities and increasing productivity of company.
Main body
Question 1
A.
Transaction processing system refers to a support system that helps in recording and
monitoring day to day transactions in an organization. They help in decreasing fraudulent
activities in following ways:
Real time processing of transaction: If transaction is recorded at the time of occurrence only,
than chances of omission are minimized and hence, frauds are automatically reduced (Ha,
Kankanhalli and Huang, 2017).
Reduced processing time: Earlier there was huge time consumed in processing and
finalizing transactions, during this time, chances of fraudulent activities were higher but
now due to advanced transaction processing system, processing time has been reduced
drastically and hence low chances of frauds.
Transaction processing system allows only few authorized user to access the data, this
improves the security of confidential data of organization and also reduces fraud that can
happen if this data is leaked from organization.
Improved communication: With the help of TPS communication is improved many folds
in organization. This communication helps in reducing frauds as now everyone in
organization is clear about all the transactions and hence, no confusion is there.
This is a look into report throwing light on efficiency that technology provides to various
business operations and transaction like accounting operations, management reporting systems,
maintaining ethical operations and privacy of information systems. In this report, study is made
related to use of various technologies in business operations like accounting systems, internal
control management, payroll system, business processes of manufacturing company, system
development life cycle. This report is categorized into five categories that will answering to
prescribes question by developing an understanding of flowcharts. These information systems
that will be learnt during this report assist in strategies effective strategies and policies which are
directed in achieving organizational goals and objectives. Information system also helps in
decreasing fraudulent activities and increasing productivity of company.
Main body
Question 1
A.
Transaction processing system refers to a support system that helps in recording and
monitoring day to day transactions in an organization. They help in decreasing fraudulent
activities in following ways:
Real time processing of transaction: If transaction is recorded at the time of occurrence only,
than chances of omission are minimized and hence, frauds are automatically reduced (Ha,
Kankanhalli and Huang, 2017).
Reduced processing time: Earlier there was huge time consumed in processing and
finalizing transactions, during this time, chances of fraudulent activities were higher but
now due to advanced transaction processing system, processing time has been reduced
drastically and hence low chances of frauds.
Transaction processing system allows only few authorized user to access the data, this
improves the security of confidential data of organization and also reduces fraud that can
happen if this data is leaked from organization.
Improved communication: With the help of TPS communication is improved many folds
in organization. This communication helps in reducing frauds as now everyone in
organization is clear about all the transactions and hence, no confusion is there.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Reduces manual errors that will lead to less errors and hence less frauds. In this system, every
transaction and its related details are clear. This transparency leads to better management and
fewer frauds (Banaeianjahromi and Smolander, 2019).
B.
Above flowchart has some of the salient feature which is there are four
departments namely: sales department, accounting department, warehouse, shipping
department and billing department. They are playing their prescribed roles in company
but still have some loopholes those can be used for any fraudulent activities which are
listed below:
Sales invoice directly goes to billing department and does not undergoes any cross
verification from accounts department; this gap can be used as taking extra amount from
customer or creating any other flaw in payment process.
Sales order and stock release are merged into one process which can create a loophole in
process as it will lead to no cross check from billing department.
There is duplication of various processes in given flowchart. Duplication of a single task
in not only costly and time consuming but also it can lead to fraudulent activities as
employees are confused over the process and there will be less coordination within them.
Some of the processes are ended at abrupt note in between of the process only; this can also be a
gap which can be used for unfair practices. This flowchart does not symbolize all processes
clearly which results in confusion and a loophole for unfair practice (Papke-Shields and Boyer-
Wright, 2017).
Question 2
A.
Advantages of alternative two are described below:
In option two, there is no duplication of work as purchase order is directly going into
their respective departments for example, blind copy goes directly to receiving
department, accounts payable copy goes directly to accounts payable department, and
same other document also.
There is no duplication of work, these results in increased productivity and efficient
operations in organization.
There is no file copy in alternative two, directly transaction list is prepared which reduces
manual efforts and hence, increased productivity.
Due to reduced duplicate efforts and transparent operations, everyone is clear about their
roles and responsibilities.
transaction and its related details are clear. This transparency leads to better management and
fewer frauds (Banaeianjahromi and Smolander, 2019).
B.
Above flowchart has some of the salient feature which is there are four
departments namely: sales department, accounting department, warehouse, shipping
department and billing department. They are playing their prescribed roles in company
but still have some loopholes those can be used for any fraudulent activities which are
listed below:
Sales invoice directly goes to billing department and does not undergoes any cross
verification from accounts department; this gap can be used as taking extra amount from
customer or creating any other flaw in payment process.
Sales order and stock release are merged into one process which can create a loophole in
process as it will lead to no cross check from billing department.
There is duplication of various processes in given flowchart. Duplication of a single task
in not only costly and time consuming but also it can lead to fraudulent activities as
employees are confused over the process and there will be less coordination within them.
Some of the processes are ended at abrupt note in between of the process only; this can also be a
gap which can be used for unfair practices. This flowchart does not symbolize all processes
clearly which results in confusion and a loophole for unfair practice (Papke-Shields and Boyer-
Wright, 2017).
Question 2
A.
Advantages of alternative two are described below:
In option two, there is no duplication of work as purchase order is directly going into
their respective departments for example, blind copy goes directly to receiving
department, accounts payable copy goes directly to accounts payable department, and
same other document also.
There is no duplication of work, these results in increased productivity and efficient
operations in organization.
There is no file copy in alternative two, directly transaction list is prepared which reduces
manual efforts and hence, increased productivity.
Due to reduced duplicate efforts and transparent operations, everyone is clear about their
roles and responsibilities.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
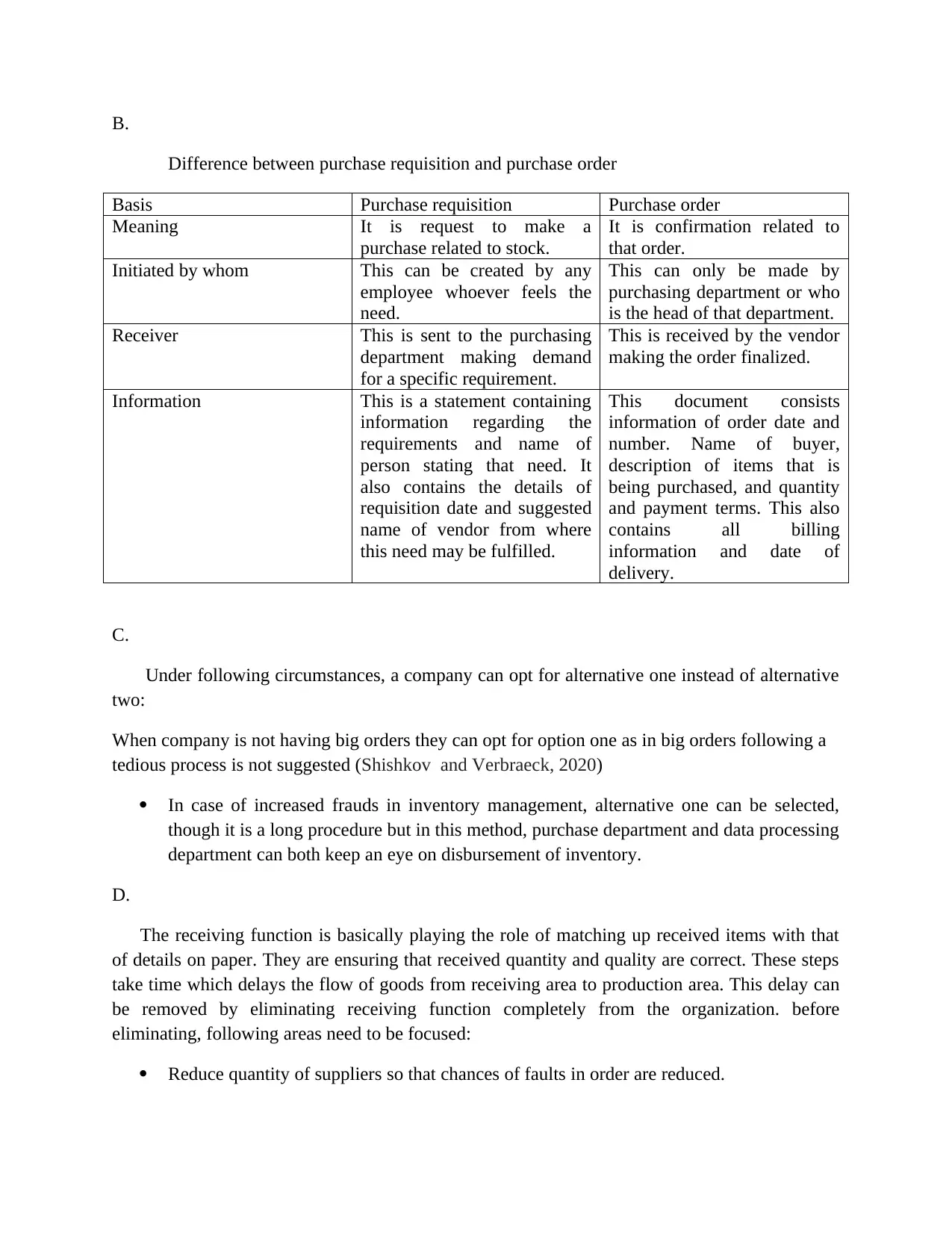
B.
Difference between purchase requisition and purchase order
Basis Purchase requisition Purchase order
Meaning It is request to make a
purchase related to stock.
It is confirmation related to
that order.
Initiated by whom This can be created by any
employee whoever feels the
need.
This can only be made by
purchasing department or who
is the head of that department.
Receiver This is sent to the purchasing
department making demand
for a specific requirement.
This is received by the vendor
making the order finalized.
Information This is a statement containing
information regarding the
requirements and name of
person stating that need. It
also contains the details of
requisition date and suggested
name of vendor from where
this need may be fulfilled.
This document consists
information of order date and
number. Name of buyer,
description of items that is
being purchased, and quantity
and payment terms. This also
contains all billing
information and date of
delivery.
C.
Under following circumstances, a company can opt for alternative one instead of alternative
two:
When company is not having big orders they can opt for option one as in big orders following a
tedious process is not suggested (Shishkov and Verbraeck, 2020)
In case of increased frauds in inventory management, alternative one can be selected,
though it is a long procedure but in this method, purchase department and data processing
department can both keep an eye on disbursement of inventory.
D.
The receiving function is basically playing the role of matching up received items with that
of details on paper. They are ensuring that received quantity and quality are correct. These steps
take time which delays the flow of goods from receiving area to production area. This delay can
be removed by eliminating receiving function completely from the organization. before
eliminating, following areas need to be focused:
Reduce quantity of suppliers so that chances of faults in order are reduced.
Difference between purchase requisition and purchase order
Basis Purchase requisition Purchase order
Meaning It is request to make a
purchase related to stock.
It is confirmation related to
that order.
Initiated by whom This can be created by any
employee whoever feels the
need.
This can only be made by
purchasing department or who
is the head of that department.
Receiver This is sent to the purchasing
department making demand
for a specific requirement.
This is received by the vendor
making the order finalized.
Information This is a statement containing
information regarding the
requirements and name of
person stating that need. It
also contains the details of
requisition date and suggested
name of vendor from where
this need may be fulfilled.
This document consists
information of order date and
number. Name of buyer,
description of items that is
being purchased, and quantity
and payment terms. This also
contains all billing
information and date of
delivery.
C.
Under following circumstances, a company can opt for alternative one instead of alternative
two:
When company is not having big orders they can opt for option one as in big orders following a
tedious process is not suggested (Shishkov and Verbraeck, 2020)
In case of increased frauds in inventory management, alternative one can be selected,
though it is a long procedure but in this method, purchase department and data processing
department can both keep an eye on disbursement of inventory.
D.
The receiving function is basically playing the role of matching up received items with that
of details on paper. They are ensuring that received quantity and quality are correct. These steps
take time which delays the flow of goods from receiving area to production area. This delay can
be removed by eliminating receiving function completely from the organization. before
eliminating, following areas need to be focused:
Reduce quantity of suppliers so that chances of faults in order are reduced.

Certify selected suppliers so that orders do match the requirements (Dzwigol and et.al., 2019).
Link suppliers to company’s scheduling system, so that suppliers know about the time of
order on their own. They are also aware about the requirement in quality and quantity as
well.
Setting up of an efficient accounting system, which will initiate payment of supplier on
its own. Cross checking of supplier invoices in not required.
Question 3
A.
Following are some of the risk involved in payroll system of HARDA limited
Time keeping- Employees can falsely mark wrong timings on their time card, which may
lead to generation of inflated pay. This is a strong risk poised to this organization.
Remote situation of clock machine- As mentioned in the case study, the clock machine
area is far from the production area, therefore, it is easy for an employee to go and
window dress with the timings and other data kept in that rear.
Biasness of supervisors- Whole attendance system in under control of supervisors,
therefore, it is possible that supervisors are sometimes biased over specific sun ordinates.
This will lead to unfair towards other employees. There biasness can result into changes
with their time in and time out.
Supervisors are also reflecting information regarding newly hired or terminated employees. This
process may result in creation of ghost employees, which means there is no newly hired
employees in real but on paper, a new hiring is shown so that pay can be generated on that name
(Verdecho, Alfaro-Saiz, and Rodríguez-Rodríguez, 2019).
B.
Following controls can be implemented in order to mitigate above risks:
Company should keep a regular check on employees when they are marking their time in
and out of time cards. In this way, chances of marking false timings are minimized.
There should be a permanent authority on clock machine area safeguarding it. In this
way, unfair access to this area will be stopped.
A two tired level of review should be implemented. In this way, all those powers that are
presently with the supervisor will be divided and chances of biasness and over
compensation will be mitigated.
Two tired level handling payroll system will solve the issue of ghost employees as now
there is segregation of duties. Unauthorized changes to payroll master data or creation of
fictitious employees will be prevented and misuse of company’s funds will not be there.
Link suppliers to company’s scheduling system, so that suppliers know about the time of
order on their own. They are also aware about the requirement in quality and quantity as
well.
Setting up of an efficient accounting system, which will initiate payment of supplier on
its own. Cross checking of supplier invoices in not required.
Question 3
A.
Following are some of the risk involved in payroll system of HARDA limited
Time keeping- Employees can falsely mark wrong timings on their time card, which may
lead to generation of inflated pay. This is a strong risk poised to this organization.
Remote situation of clock machine- As mentioned in the case study, the clock machine
area is far from the production area, therefore, it is easy for an employee to go and
window dress with the timings and other data kept in that rear.
Biasness of supervisors- Whole attendance system in under control of supervisors,
therefore, it is possible that supervisors are sometimes biased over specific sun ordinates.
This will lead to unfair towards other employees. There biasness can result into changes
with their time in and time out.
Supervisors are also reflecting information regarding newly hired or terminated employees. This
process may result in creation of ghost employees, which means there is no newly hired
employees in real but on paper, a new hiring is shown so that pay can be generated on that name
(Verdecho, Alfaro-Saiz, and Rodríguez-Rodríguez, 2019).
B.
Following controls can be implemented in order to mitigate above risks:
Company should keep a regular check on employees when they are marking their time in
and out of time cards. In this way, chances of marking false timings are minimized.
There should be a permanent authority on clock machine area safeguarding it. In this
way, unfair access to this area will be stopped.
A two tired level of review should be implemented. In this way, all those powers that are
presently with the supervisor will be divided and chances of biasness and over
compensation will be mitigated.
Two tired level handling payroll system will solve the issue of ghost employees as now
there is segregation of duties. Unauthorized changes to payroll master data or creation of
fictitious employees will be prevented and misuse of company’s funds will not be there.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Question 4
Risks associated with manufacturing company are listed below:
Effective supply chain management is necessary to be maintained. Adopting latest
technologies will help in reducing risks and cost to a greater extent.
Effective inventory management system, otherwise chances of frauds are increased as if
on paper and physical quantity does not match than it means that some error is there.
Quality also plays a measure role in manufacturing company. If on paper quality and
actual quality differs than it poses a heavy risk on productivity and profitability of
company (Roland Weistroffer, Roztocki and Soja, 2015).
Labor turnover is also a threat and risk for a manufacturing company. As this type of
company is basically standing on the base of a strong set of efficient employees. If these
employees leave the company frequently, it will affect company’s productivity.
In the given case study, there is a long procedure of circulation of documents in
organization; this long procedure also affects the company’s productivity. Instead of
using manual procedure, company can opt for digital process which will not only ease the
process but will also make it way faster and efficient.
Physical timings of labor can also lead to unnecessary inflated disposal of funds as
wages. As manual timing can also represent wrong values, thus it is necessary to adopt
for a new controlled method. For example, a digital bio metric method for attendance.
Another risk relates to regulatory, trade and policy area. In manufacturing company, it is
necessary that trademarks and intellectual property rights are established in time, so that
no other company is able to steal original work. Development of understanding of impact
of trade deals and tariffs is also important so that business operations are not interrupted.
Climate changes are also a big risk for business operations of a manufacturing company.
If the climatic conditions are unfavorable than it may lead to a strong interruption in
whole process (Ruhi, 2016).
Question 5
To: David Savage (Chief Operation Officer)
From: Chief Information Officer
Date: 12th October 20XX
Subject: Risks associated with consultants.
It has been proposed that company is going to adopt Enterprise Resource Planning (ERP)
system. For this purpose a consulting firm’s name has been proposed. This memo presents some
of the considerable risks for the same. First of all the authenticity of the firm should be checked
as during the process of installation of ERP system in organization, all the confidential
information will be shared with the outsider firm. Another factor relates with the cost. Company
should invite proposals from different organizations as well so that cost proposed by this firm is
evaluated. This will also lead to cost effective installation. Next risk associated with the firm is
their credibility in market. It can be a chance that they promise completion of work in certain
Risks associated with manufacturing company are listed below:
Effective supply chain management is necessary to be maintained. Adopting latest
technologies will help in reducing risks and cost to a greater extent.
Effective inventory management system, otherwise chances of frauds are increased as if
on paper and physical quantity does not match than it means that some error is there.
Quality also plays a measure role in manufacturing company. If on paper quality and
actual quality differs than it poses a heavy risk on productivity and profitability of
company (Roland Weistroffer, Roztocki and Soja, 2015).
Labor turnover is also a threat and risk for a manufacturing company. As this type of
company is basically standing on the base of a strong set of efficient employees. If these
employees leave the company frequently, it will affect company’s productivity.
In the given case study, there is a long procedure of circulation of documents in
organization; this long procedure also affects the company’s productivity. Instead of
using manual procedure, company can opt for digital process which will not only ease the
process but will also make it way faster and efficient.
Physical timings of labor can also lead to unnecessary inflated disposal of funds as
wages. As manual timing can also represent wrong values, thus it is necessary to adopt
for a new controlled method. For example, a digital bio metric method for attendance.
Another risk relates to regulatory, trade and policy area. In manufacturing company, it is
necessary that trademarks and intellectual property rights are established in time, so that
no other company is able to steal original work. Development of understanding of impact
of trade deals and tariffs is also important so that business operations are not interrupted.
Climate changes are also a big risk for business operations of a manufacturing company.
If the climatic conditions are unfavorable than it may lead to a strong interruption in
whole process (Ruhi, 2016).
Question 5
To: David Savage (Chief Operation Officer)
From: Chief Information Officer
Date: 12th October 20XX
Subject: Risks associated with consultants.
It has been proposed that company is going to adopt Enterprise Resource Planning (ERP)
system. For this purpose a consulting firm’s name has been proposed. This memo presents some
of the considerable risks for the same. First of all the authenticity of the firm should be checked
as during the process of installation of ERP system in organization, all the confidential
information will be shared with the outsider firm. Another factor relates with the cost. Company
should invite proposals from different organizations as well so that cost proposed by this firm is
evaluated. This will also lead to cost effective installation. Next risk associated with the firm is
their credibility in market. It can be a chance that they promise completion of work in certain
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

time but it will not be fulfilled, thus it may lead top interruption in business operations and also
wastage of company’s funds. It is advisable, that after considering above risks and factors,
decision should be made.
Following is a set of procedure that can be followed before choosing one consultant:
First of all, requirements of company related to ERP needs to be identified. This means
that managers need to identify that for actually what purpose they want this system to be
installed.
Second comes up the set of budget, this means a fixed amount of funds after all analyses
is allocated for the installation of system in company.
Next comes up the search for a suitable solution or system that fulfills all requirements
identified in step. This is done by inviting different consultants offering their products.
Now in this step, an evaluation of different offers by consultants is performed in order to
choose the best one.
Only that one consultant is chosen, who offers the best fir solution for the issue at the
most reasonable price.
In last step discussed, risks associated (discussed in memo) are also considered so that no
hindrance is created in business operations (Gattorna, 2016).
Question 6
A.
A feasibility study of project means evaluation of project’s potential to reach the
expected results. Therefore, on this ground, a project is analyzed in five different areas which are
technical, economical, legal, operational and schedule. These all are termed as TELOS analysis
which studies overall potential of a proposed project. These areas are discussed in brief:
Technical: This studies the availability if technical resources with the company. This
will help in determining that whether the available resources will be helpful n meeting the
capabilities of the project or not. This helps in identification of capability of technical
department of converting ideas into working systems.
Economic: This inspection includes cost- benefit analysis of the proposed project, which
helps in determining the costs and benefits associated with the project. This analysis is
performed before allocation of financial resources. This is basically a measure of
profitability index of the proposed project. This technique helps in assisting managers to
formulate their decisions as it enhances project’s credibility.
Legal: This feasibility studies makes it clear that project does not contradict any law or
legal requirement. For example, social media laws, data protection laws, etc. If the
project is not matching up the legal requirements than it is better to dispose that idea there
only as carrying that project further can lead to intervention of authority (Lyytinen, and
Newman, 2015).
wastage of company’s funds. It is advisable, that after considering above risks and factors,
decision should be made.
Following is a set of procedure that can be followed before choosing one consultant:
First of all, requirements of company related to ERP needs to be identified. This means
that managers need to identify that for actually what purpose they want this system to be
installed.
Second comes up the set of budget, this means a fixed amount of funds after all analyses
is allocated for the installation of system in company.
Next comes up the search for a suitable solution or system that fulfills all requirements
identified in step. This is done by inviting different consultants offering their products.
Now in this step, an evaluation of different offers by consultants is performed in order to
choose the best one.
Only that one consultant is chosen, who offers the best fir solution for the issue at the
most reasonable price.
In last step discussed, risks associated (discussed in memo) are also considered so that no
hindrance is created in business operations (Gattorna, 2016).
Question 6
A.
A feasibility study of project means evaluation of project’s potential to reach the
expected results. Therefore, on this ground, a project is analyzed in five different areas which are
technical, economical, legal, operational and schedule. These all are termed as TELOS analysis
which studies overall potential of a proposed project. These areas are discussed in brief:
Technical: This studies the availability if technical resources with the company. This
will help in determining that whether the available resources will be helpful n meeting the
capabilities of the project or not. This helps in identification of capability of technical
department of converting ideas into working systems.
Economic: This inspection includes cost- benefit analysis of the proposed project, which
helps in determining the costs and benefits associated with the project. This analysis is
performed before allocation of financial resources. This is basically a measure of
profitability index of the proposed project. This technique helps in assisting managers to
formulate their decisions as it enhances project’s credibility.
Legal: This feasibility studies makes it clear that project does not contradict any law or
legal requirement. For example, social media laws, data protection laws, etc. If the
project is not matching up the legal requirements than it is better to dispose that idea there
only as carrying that project further can lead to intervention of authority (Lyytinen, and
Newman, 2015).

Operational: This step examines how that proposed idea or project meets up the
requirements identified in the requirement analysis phase of system development. In
simple terms, it can be stated that, this area study that whether adoption of this project
will lead to requirements of company or not.
Scheduling: This area focuses on determining the time constraint of project. This means
it is necessary for the success of any project that it is completed within the expected time.
Otherwise, it will lead to delay in other business operations as well and it will also be
time consuming process.
Accountants play a crucial role in system development cycle in following ways:
The provide a clear view of issues and requirements
They act as important members of development team as they provide their input is
preparation of a good well- controlled system.
They also act as auditors, so that a regular check can be made on proper design of system,
this can be done through computer audit technique.
They provide a expertise in evaluating feasibility of projects during the planning process.
Accountants ensure that system’s weak points are eliminated while saving its strong
points.
Accountants play an important role as if important accounting considerations are
overlooked at this stage that company will be exposed to heavy losses later in the period
(Paré and et.al., 2015).
Conclusion
In this report, various studies have been made related to various systems that improve
efficiency and effectiveness of various business operations. In this statement, an in depth study is
made of payroll system and its related risks, threats of manufacturing company, benefits of
transaction processing system, etc. all these systems enhances productivity of organization.
requirements identified in the requirement analysis phase of system development. In
simple terms, it can be stated that, this area study that whether adoption of this project
will lead to requirements of company or not.
Scheduling: This area focuses on determining the time constraint of project. This means
it is necessary for the success of any project that it is completed within the expected time.
Otherwise, it will lead to delay in other business operations as well and it will also be
time consuming process.
Accountants play a crucial role in system development cycle in following ways:
The provide a clear view of issues and requirements
They act as important members of development team as they provide their input is
preparation of a good well- controlled system.
They also act as auditors, so that a regular check can be made on proper design of system,
this can be done through computer audit technique.
They provide a expertise in evaluating feasibility of projects during the planning process.
Accountants ensure that system’s weak points are eliminated while saving its strong
points.
Accountants play an important role as if important accounting considerations are
overlooked at this stage that company will be exposed to heavy losses later in the period
(Paré and et.al., 2015).
Conclusion
In this report, various studies have been made related to various systems that improve
efficiency and effectiveness of various business operations. In this statement, an in depth study is
made of payroll system and its related risks, threats of manufacturing company, benefits of
transaction processing system, etc. all these systems enhances productivity of organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Books and Journals
Ha, S., Kankanhalli, A. and Huang, K.W., 2017. Does IT Help Firms to Become More
Entrepreneurial?: The Role of Enterprise IT.
Banaeianjahromi, N. and Smolander, K., 2019. Lack of communication and collaboration in
enterprise architecture development. Information Systems Frontiers. 21(4). pp.877-908.
Papke-Shields, K.E. and Boyer-Wright, K.M., 2017. Strategic planning characteristics applied
to project management. International Journal of Project Management. 35(2). pp.169-179.
Shishkov, B. and Verbraeck, A., 2020, July. Making Enterprise Information Systems Resilient
Against Disruptive Events: A Conceptual View. In International Symposium on Business
Modeling and Software Design (pp. 38-54). Springer, Cham.
Dzwigol, H. and et.al., 2019. Formation of Strategic Change Management System at an
Enterprise. Academy of Strategic Management Journal. 18. pp.1-8.
Verdecho, M.J., Alfaro-Saiz, J.J. and Rodríguez-Rodríguez, R., 2019. Integrating business
process interoperability into an inter-enterprise performance management system.
In Enterprise Interoperability VIII (pp. 265-273). Springer, Cham.
Roland Weistroffer, H., Roztocki, N. and Soja, P., 2015. Enterprise Systems in Transition
Economies: An Initial Literature Review.
Ruhi, U., 2016. An experiential learning pedagogical framework for enterprise systems
education in business schools. The International Journal of Management
Education. 14(2). pp.198-211.
Gattorna, J., 2016. Dynamic supply chain alignment: a new business model for peak
performance in enterprise supply chains across all geographies. CRC Press.
Lyytinen, K. and Newman, M., 2015. A tale of two coalitions–marginalising the users while
successfully implementing an enterprise resource planning system. Information Systems
Journal. 25(2). pp.71-101.
Paré, G. and et.al., 2015. Synthesizing information systems knowledge: A typology of literature
reviews. Information & Management. 52(2). pp.183-199.
Books and Journals
Ha, S., Kankanhalli, A. and Huang, K.W., 2017. Does IT Help Firms to Become More
Entrepreneurial?: The Role of Enterprise IT.
Banaeianjahromi, N. and Smolander, K., 2019. Lack of communication and collaboration in
enterprise architecture development. Information Systems Frontiers. 21(4). pp.877-908.
Papke-Shields, K.E. and Boyer-Wright, K.M., 2017. Strategic planning characteristics applied
to project management. International Journal of Project Management. 35(2). pp.169-179.
Shishkov, B. and Verbraeck, A., 2020, July. Making Enterprise Information Systems Resilient
Against Disruptive Events: A Conceptual View. In International Symposium on Business
Modeling and Software Design (pp. 38-54). Springer, Cham.
Dzwigol, H. and et.al., 2019. Formation of Strategic Change Management System at an
Enterprise. Academy of Strategic Management Journal. 18. pp.1-8.
Verdecho, M.J., Alfaro-Saiz, J.J. and Rodríguez-Rodríguez, R., 2019. Integrating business
process interoperability into an inter-enterprise performance management system.
In Enterprise Interoperability VIII (pp. 265-273). Springer, Cham.
Roland Weistroffer, H., Roztocki, N. and Soja, P., 2015. Enterprise Systems in Transition
Economies: An Initial Literature Review.
Ruhi, U., 2016. An experiential learning pedagogical framework for enterprise systems
education in business schools. The International Journal of Management
Education. 14(2). pp.198-211.
Gattorna, J., 2016. Dynamic supply chain alignment: a new business model for peak
performance in enterprise supply chains across all geographies. CRC Press.
Lyytinen, K. and Newman, M., 2015. A tale of two coalitions–marginalising the users while
successfully implementing an enterprise resource planning system. Information Systems
Journal. 25(2). pp.71-101.
Paré, G. and et.al., 2015. Synthesizing information systems knowledge: A typology of literature
reviews. Information & Management. 52(2). pp.183-199.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





