Strategic Information Systems Analysis: Bell Studio Case Study, HI5019
VerifiedAdded on 2022/11/26
|13
|2684
|144
Case Study
AI Summary
This case study analyzes the strategic information systems of Bell Studio, a wholesaler of art supplies using a centralized accounting system. The report details various transaction cycles, financial and management reporting systems, and e-commerce operations. It includes data flow diagrams and system flowcharts for the purchasing, payroll, and cash disbursement systems. The analysis identifies internal control weaknesses and associated risks, such as slow processes, human error, security breaches, and potential fraud. The report also discusses security measures to mitigate these risks within the context of electronic commerce. The overall objective is to assess the efficiency, security, and potential vulnerabilities of Bell Studio's information systems and propose improvements.

Running head: STRATEGIC INFORMATION SYSTEM
Strategic Information for Business and Enterprise
Name of Student-
Name of University-
Author’s Note
Strategic Information for Business and Enterprise
Name of Student-
Name of University-
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION SYSTEM
Executive Summary
Bell Studio is the wholesaler of the art supplies and follows the centralized accounting
information system to execute all the business operations in the organization. The
enterprise of Bell Studio includes different transaction cycles, different financial
reporting for the business operations, the management reporting of the system and the
e-commerce that is involved in the system. This particular report includes the operating
system of the Bell studio stating its working of the computer based systems. This report
also contains the opportunities that can be involved to overcome the computer fraud as
well as the security measures in the form of electronic commerce. The evaluation in this
report is done in the form of data flow diagram and system flowcharts of the related
system of Bell Studio.
Executive Summary
Bell Studio is the wholesaler of the art supplies and follows the centralized accounting
information system to execute all the business operations in the organization. The
enterprise of Bell Studio includes different transaction cycles, different financial
reporting for the business operations, the management reporting of the system and the
e-commerce that is involved in the system. This particular report includes the operating
system of the Bell studio stating its working of the computer based systems. This report
also contains the opportunities that can be involved to overcome the computer fraud as
well as the security measures in the form of electronic commerce. The evaluation in this
report is done in the form of data flow diagram and system flowcharts of the related
system of Bell Studio.

2STRATEGIC INFORMATION SYSTEM
Table of Contents
1. Introduction....................................................................................................................3
2. Data Flow Diagram for the Purchasing system and system of Cash Disbursements...4
3. Data Flow Diagram of Payroll System...........................................................................5
4. System Flowchart of Purchases System.......................................................................6
5. System Flowchart of Cash Disbursements System......................................................6
6. System Flowchart of Payroll System.............................................................................8
7. Internal Control Weakness and Risk Associated..........................................................8
8. Conclusion.....................................................................................................................9
Reference........................................................................................................................11
Table of Contents
1. Introduction....................................................................................................................3
2. Data Flow Diagram for the Purchasing system and system of Cash Disbursements...4
3. Data Flow Diagram of Payroll System...........................................................................5
4. System Flowchart of Purchases System.......................................................................6
5. System Flowchart of Cash Disbursements System......................................................6
6. System Flowchart of Payroll System.............................................................................8
7. Internal Control Weakness and Risk Associated..........................................................8
8. Conclusion.....................................................................................................................9
Reference........................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3STRATEGIC INFORMATION SYSTEM
1. Introduction
Centralization is referred as a process that includes the activities involving the planning
as well as decision making of the system of Bell Studio (Kanodia and Sapra 2016).
Centralization involves decision making and planning is done by the particular leaders
of the organization. The executives of an organization and the specialists of an
organization takes most critical decisions that are actually based on the head office.
The case study of Bell Studio includes centralized accounting system for business
operations (Haislip et al. 2015). Using the centralized system, the organization has
many advantages. The benefits that Bell Studio gets from their centralized payroll
system are having a clear chain of all the commands in the organization, fulfils the
vision of the company very easily, have low cost maintaining costs, and as the decisions
are mainly taken by the supervisors and the clerks, the enterprise is able to take quick
decisions relation to the process of the organisation.
But the centralized system in the Bell Studio also has many disadvantages that are
needed to be taken care off (Sun 2016). This report explains the business operation of
the system from the perspective of the business analyst and those business operations
area shown in the form of data flow diagram and system flowchart in this report. This
report also states the internal weakens of controlling the transaction cycles, the
management cycles and the financial cycle of the business operations and addresses
the risks that are associated with the internal weakness in controlling the system. Some
security measures are also explained in this report related to the risks addressed
(Zimmermann, Rentrop and Felden 2016).
1. Introduction
Centralization is referred as a process that includes the activities involving the planning
as well as decision making of the system of Bell Studio (Kanodia and Sapra 2016).
Centralization involves decision making and planning is done by the particular leaders
of the organization. The executives of an organization and the specialists of an
organization takes most critical decisions that are actually based on the head office.
The case study of Bell Studio includes centralized accounting system for business
operations (Haislip et al. 2015). Using the centralized system, the organization has
many advantages. The benefits that Bell Studio gets from their centralized payroll
system are having a clear chain of all the commands in the organization, fulfils the
vision of the company very easily, have low cost maintaining costs, and as the decisions
are mainly taken by the supervisors and the clerks, the enterprise is able to take quick
decisions relation to the process of the organisation.
But the centralized system in the Bell Studio also has many disadvantages that are
needed to be taken care off (Sun 2016). This report explains the business operation of
the system from the perspective of the business analyst and those business operations
area shown in the form of data flow diagram and system flowchart in this report. This
report also states the internal weakens of controlling the transaction cycles, the
management cycles and the financial cycle of the business operations and addresses
the risks that are associated with the internal weakness in controlling the system. Some
security measures are also explained in this report related to the risks addressed
(Zimmermann, Rentrop and Felden 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
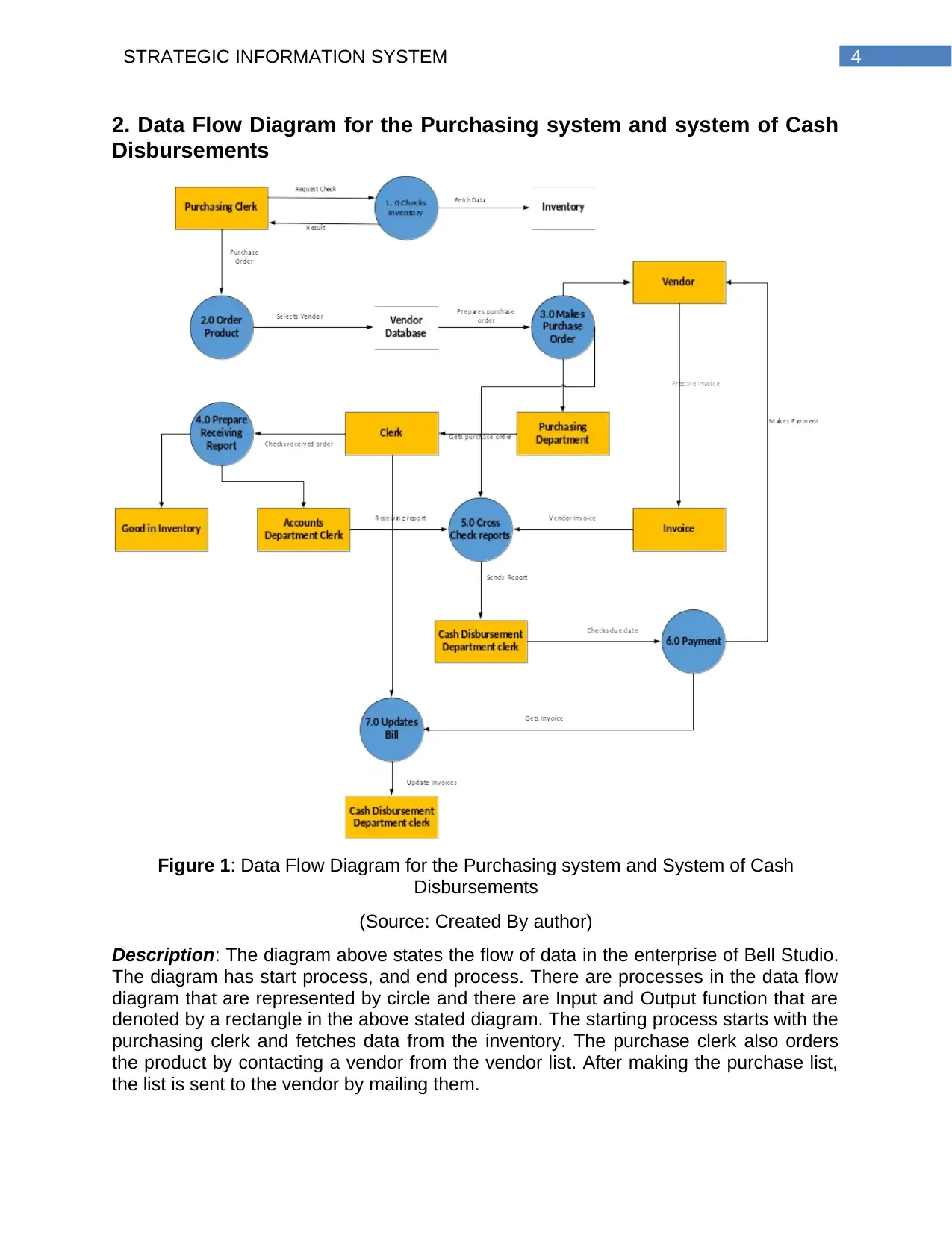
4STRATEGIC INFORMATION SYSTEM
2. Data Flow Diagram for the Purchasing system and system of Cash
Disbursements
Figure 1: Data Flow Diagram for the Purchasing system and System of Cash
Disbursements
(Source: Created By author)
Description: The diagram above states the flow of data in the enterprise of Bell Studio.
The diagram has start process, and end process. There are processes in the data flow
diagram that are represented by circle and there are Input and Output function that are
denoted by a rectangle in the above stated diagram. The starting process starts with the
purchasing clerk and fetches data from the inventory. The purchase clerk also orders
the product by contacting a vendor from the vendor list. After making the purchase list,
the list is sent to the vendor by mailing them.
2. Data Flow Diagram for the Purchasing system and system of Cash
Disbursements
Figure 1: Data Flow Diagram for the Purchasing system and System of Cash
Disbursements
(Source: Created By author)
Description: The diagram above states the flow of data in the enterprise of Bell Studio.
The diagram has start process, and end process. There are processes in the data flow
diagram that are represented by circle and there are Input and Output function that are
denoted by a rectangle in the above stated diagram. The starting process starts with the
purchasing clerk and fetches data from the inventory. The purchase clerk also orders
the product by contacting a vendor from the vendor list. After making the purchase list,
the list is sent to the vendor by mailing them.
5STRATEGIC INFORMATION SYSTEM
The purchasing list is then sent to the receiving department. When the goods are
received, the receiving clerk gets the supplier slip, and checks it with the purchasing list.
One hard copy with the receiving list is sent with the goods in the inventory and the
other is sent to the accounts department clerk. The account clerk checks purchasing
list, the invoice sent by the vendor and the receiving report. The file is then forwarded to
the clerk of cash disbursement department. The cheques is prepared by the clerk and
payment is done via email. The clerk of the purchasing department updates the bill and
sent to the cash disbursement clerk for updating them to the central payroll system.
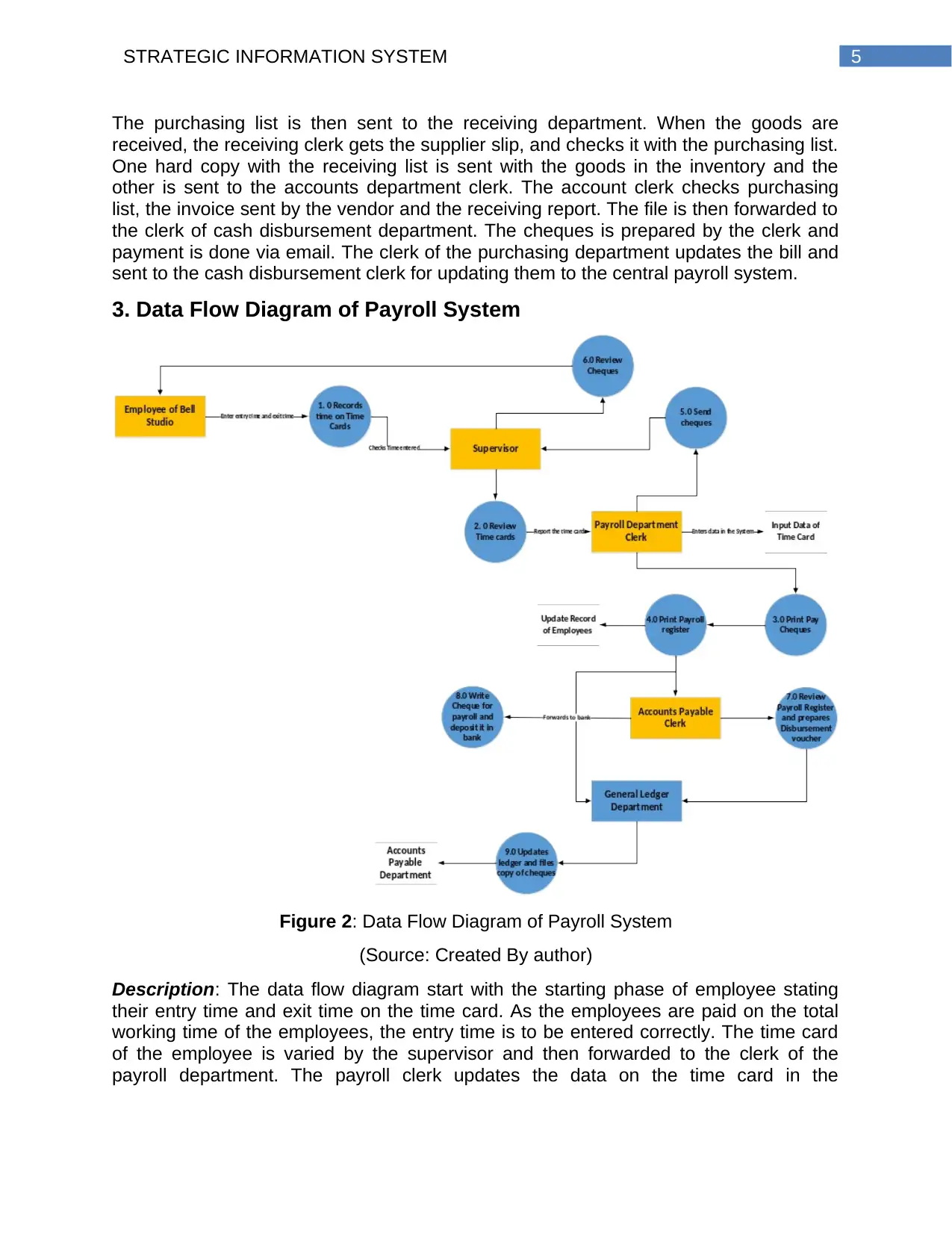
3. Data Flow Diagram of Payroll System
Figure 2: Data Flow Diagram of Payroll System
(Source: Created By author)
Description: The data flow diagram start with the starting phase of employee stating
their entry time and exit time on the time card. As the employees are paid on the total
working time of the employees, the entry time is to be entered correctly. The time card
of the employee is varied by the supervisor and then forwarded to the clerk of the
payroll department. The payroll clerk updates the data on the time card in the
The purchasing list is then sent to the receiving department. When the goods are
received, the receiving clerk gets the supplier slip, and checks it with the purchasing list.
One hard copy with the receiving list is sent with the goods in the inventory and the
other is sent to the accounts department clerk. The account clerk checks purchasing
list, the invoice sent by the vendor and the receiving report. The file is then forwarded to
the clerk of cash disbursement department. The cheques is prepared by the clerk and
payment is done via email. The clerk of the purchasing department updates the bill and
sent to the cash disbursement clerk for updating them to the central payroll system.
3. Data Flow Diagram of Payroll System
Figure 2: Data Flow Diagram of Payroll System
(Source: Created By author)
Description: The data flow diagram start with the starting phase of employee stating
their entry time and exit time on the time card. As the employees are paid on the total
working time of the employees, the entry time is to be entered correctly. The time card
of the employee is varied by the supervisor and then forwarded to the clerk of the
payroll department. The payroll clerk updates the data on the time card in the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6STRATEGIC INFORMATION SYSTEM
employee’s record in the database. The clerk prints the cheques that are to be paid and
update the payroll registers.
The file is then given to the account payable clerk. The clerk then first reviews the
register and prepares the disbursement voucher. The clerk there writes the cheque for
the entire payroll amount and deposit it to the bank. The payroll register is updated by
the ledger department and finally the files are stored in the account payable department.
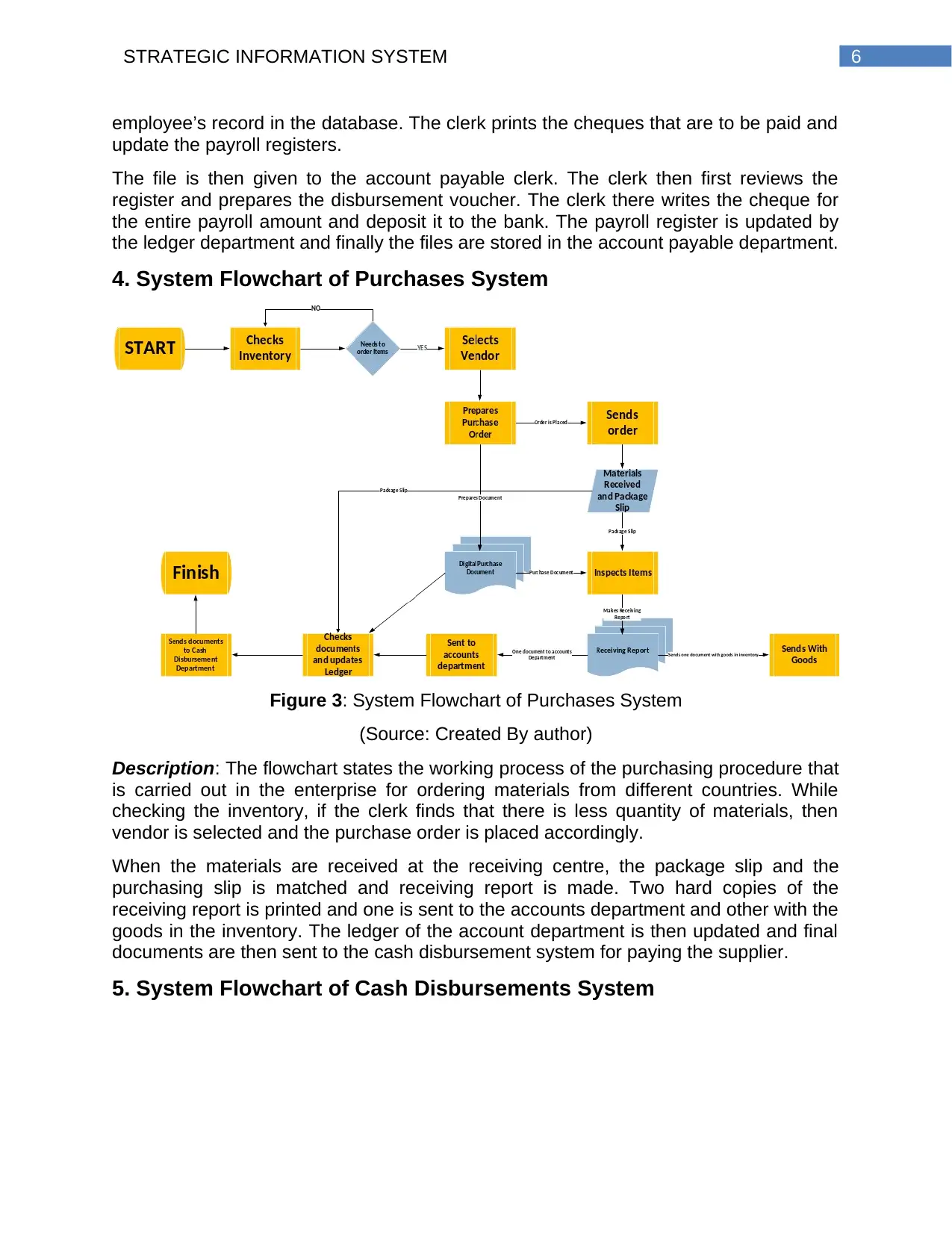
4. System Flowchart of Purchases System
Figure 3: System Flowchart of Purchases System
(Source: Created By author)
Description: The flowchart states the working process of the purchasing procedure that
is carried out in the enterprise for ordering materials from different countries. While
checking the inventory, if the clerk finds that there is less quantity of materials, then
vendor is selected and the purchase order is placed accordingly.
When the materials are received at the receiving centre, the package slip and the
purchasing slip is matched and receiving report is made. Two hard copies of the
receiving report is printed and one is sent to the accounts department and other with the
goods in the inventory. The ledger of the account department is then updated and final
documents are then sent to the cash disbursement system for paying the supplier.
5. System Flowchart of Cash Disbursements System
employee’s record in the database. The clerk prints the cheques that are to be paid and
update the payroll registers.
The file is then given to the account payable clerk. The clerk then first reviews the
register and prepares the disbursement voucher. The clerk there writes the cheque for
the entire payroll amount and deposit it to the bank. The payroll register is updated by
the ledger department and finally the files are stored in the account payable department.
4. System Flowchart of Purchases System
Figure 3: System Flowchart of Purchases System
(Source: Created By author)
Description: The flowchart states the working process of the purchasing procedure that
is carried out in the enterprise for ordering materials from different countries. While
checking the inventory, if the clerk finds that there is less quantity of materials, then
vendor is selected and the purchase order is placed accordingly.
When the materials are received at the receiving centre, the package slip and the
purchasing slip is matched and receiving report is made. Two hard copies of the
receiving report is printed and one is sent to the accounts department and other with the
goods in the inventory. The ledger of the account department is then updated and final
documents are then sent to the cash disbursement system for paying the supplier.
5. System Flowchart of Cash Disbursements System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
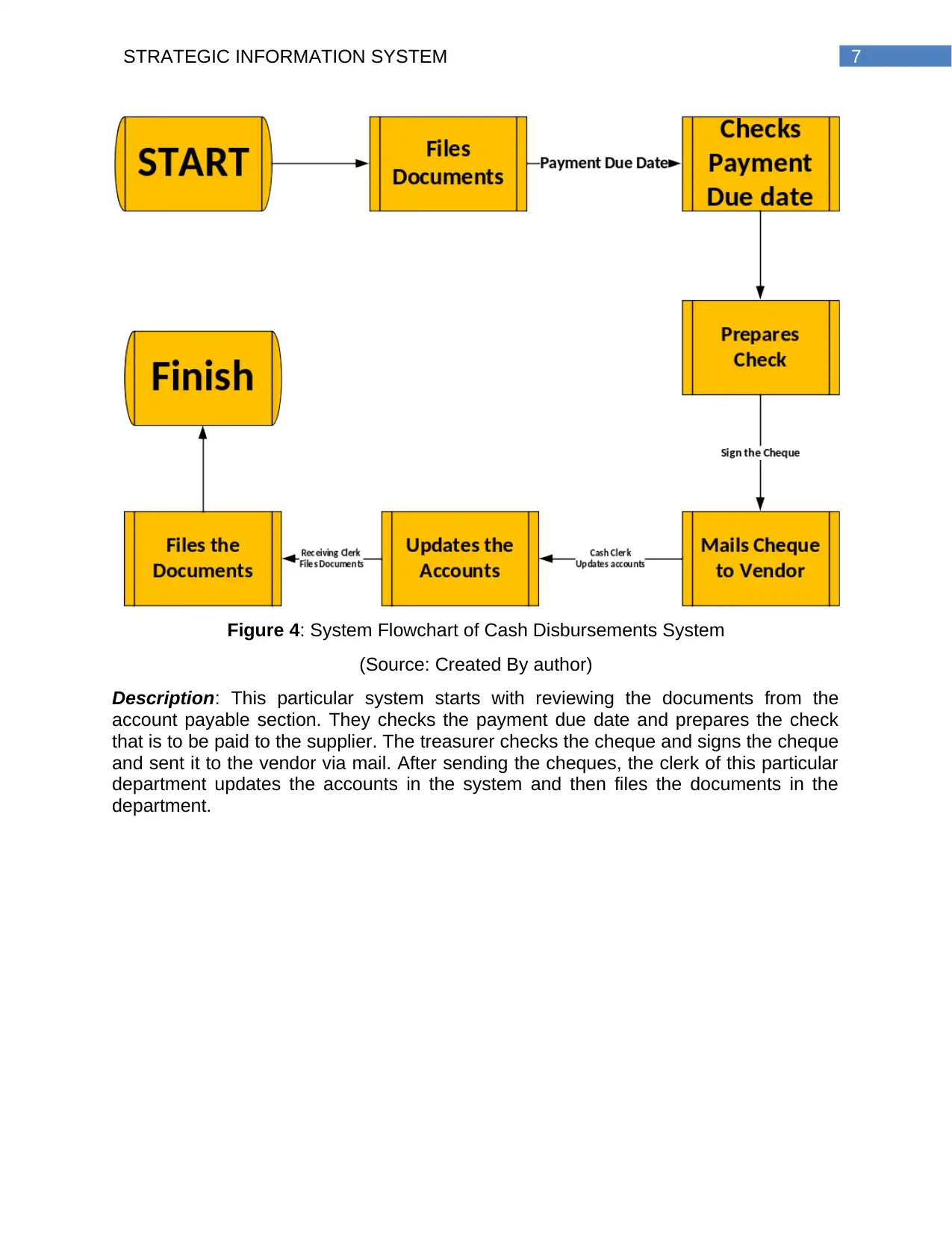
7STRATEGIC INFORMATION SYSTEM
Figure 4: System Flowchart of Cash Disbursements System
(Source: Created By author)
Description: This particular system starts with reviewing the documents from the
account payable section. They checks the payment due date and prepares the check
that is to be paid to the supplier. The treasurer checks the cheque and signs the cheque
and sent it to the vendor via mail. After sending the cheques, the clerk of this particular
department updates the accounts in the system and then files the documents in the
department.
Figure 4: System Flowchart of Cash Disbursements System
(Source: Created By author)
Description: This particular system starts with reviewing the documents from the
account payable section. They checks the payment due date and prepares the check
that is to be paid to the supplier. The treasurer checks the cheque and signs the cheque
and sent it to the vendor via mail. After sending the cheques, the clerk of this particular
department updates the accounts in the system and then files the documents in the
department.
8STRATEGIC INFORMATION SYSTEM
6. System Flowchart of Payroll System
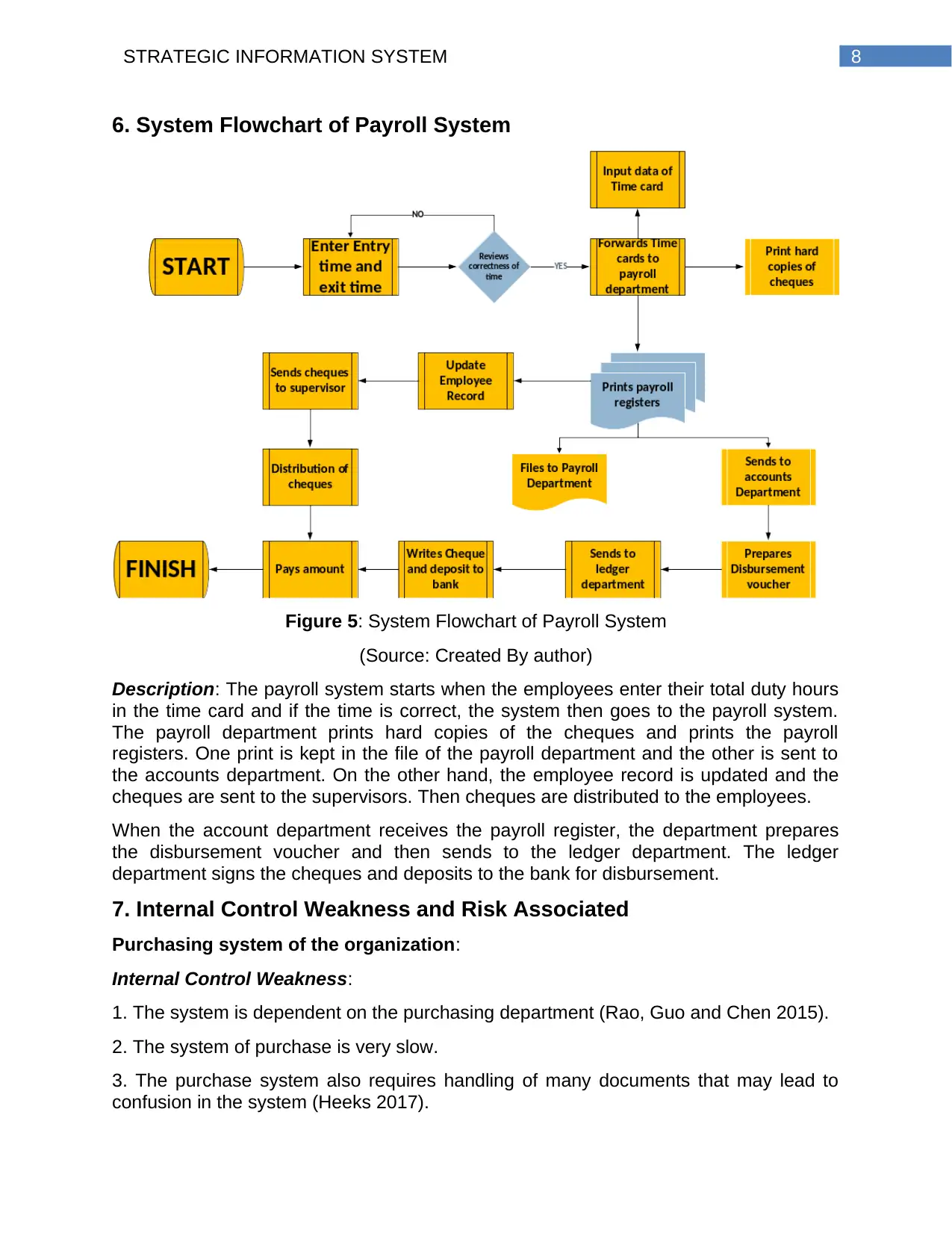
Figure 5: System Flowchart of Payroll System
(Source: Created By author)
Description: The payroll system starts when the employees enter their total duty hours
in the time card and if the time is correct, the system then goes to the payroll system.
The payroll department prints hard copies of the cheques and prints the payroll
registers. One print is kept in the file of the payroll department and the other is sent to
the accounts department. On the other hand, the employee record is updated and the
cheques are sent to the supervisors. Then cheques are distributed to the employees.
When the account department receives the payroll register, the department prepares
the disbursement voucher and then sends to the ledger department. The ledger
department signs the cheques and deposits to the bank for disbursement.
7. Internal Control Weakness and Risk Associated
Purchasing system of the organization:
Internal Control Weakness:
1. The system is dependent on the purchasing department (Rao, Guo and Chen 2015).
2. The system of purchase is very slow.
3. The purchase system also requires handling of many documents that may lead to
confusion in the system (Heeks 2017).
6. System Flowchart of Payroll System
Figure 5: System Flowchart of Payroll System
(Source: Created By author)
Description: The payroll system starts when the employees enter their total duty hours
in the time card and if the time is correct, the system then goes to the payroll system.
The payroll department prints hard copies of the cheques and prints the payroll
registers. One print is kept in the file of the payroll department and the other is sent to
the accounts department. On the other hand, the employee record is updated and the
cheques are sent to the supervisors. Then cheques are distributed to the employees.
When the account department receives the payroll register, the department prepares
the disbursement voucher and then sends to the ledger department. The ledger
department signs the cheques and deposits to the bank for disbursement.
7. Internal Control Weakness and Risk Associated
Purchasing system of the organization:
Internal Control Weakness:
1. The system is dependent on the purchasing department (Rao, Guo and Chen 2015).
2. The system of purchase is very slow.
3. The purchase system also requires handling of many documents that may lead to
confusion in the system (Heeks 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION SYSTEM
Risks Associated with the system:
1.1 Risk of making the system slow down as the process involved in the system needs
more manual labour (Thompson 2017).
2.1 Risk of conducting human error as the system mainly depends on the process done
by the clerk (Duncan and Whittington 2016).
3.1 The information or the data are uploaded on the central payroll section that might
crash anytime making the system stop for some time.
Cash Disbursement system of the organization:
Internal Control Weakness:
1. While writing the cheques, mistake may occur and mistake can also occur while
cheques are transferred from department to another (Safari et al. 2016).
2. Security breach might take place with the centralized system as the system is not
secured (Ji, Lu and Qu 2017). There might be internal password theft or hardware or
software failure.
3. There is also a risk of denial of service in the enterprise business operations.
Risks Associated with the system:
1.1 Spam, scams as well as phishing might take place as the system (Gallemore and
Labro 2015).
2.1 Security breach might take place with the centralized system as the system is not
secured. There might be internal password theft or hardware or software failure (Chen
et al. 2016).
3.1 There is also a risk of denial of service in the enterprise business operations
(Avgerou and Walsham 2017).
Payroll system of the organization:
Internal Control Weakness:
1. The employee may not be fair to enter their working hours in the system as the
system is carried out manually (Aladwan 2018).
2. Human mistakes are very common with the system as because the system deals with
human errors of dealing with the business operations.
Risks Associated with the system:
1.1 Making the system slow and have infected virus and malware in the system (Khan
and Gray 2016).
2.1 Fraud caused by the humans and the password theft is caused by the system is risk
to Bell Studio.
3.1 Risk of staff dishonesty is involved in the system (Salterio 2015).
Risks Associated with the system:
1.1 Risk of making the system slow down as the process involved in the system needs
more manual labour (Thompson 2017).
2.1 Risk of conducting human error as the system mainly depends on the process done
by the clerk (Duncan and Whittington 2016).
3.1 The information or the data are uploaded on the central payroll section that might
crash anytime making the system stop for some time.
Cash Disbursement system of the organization:
Internal Control Weakness:
1. While writing the cheques, mistake may occur and mistake can also occur while
cheques are transferred from department to another (Safari et al. 2016).
2. Security breach might take place with the centralized system as the system is not
secured (Ji, Lu and Qu 2017). There might be internal password theft or hardware or
software failure.
3. There is also a risk of denial of service in the enterprise business operations.
Risks Associated with the system:
1.1 Spam, scams as well as phishing might take place as the system (Gallemore and
Labro 2015).
2.1 Security breach might take place with the centralized system as the system is not
secured. There might be internal password theft or hardware or software failure (Chen
et al. 2016).
3.1 There is also a risk of denial of service in the enterprise business operations
(Avgerou and Walsham 2017).
Payroll system of the organization:
Internal Control Weakness:
1. The employee may not be fair to enter their working hours in the system as the
system is carried out manually (Aladwan 2018).
2. Human mistakes are very common with the system as because the system deals with
human errors of dealing with the business operations.
Risks Associated with the system:
1.1 Making the system slow and have infected virus and malware in the system (Khan
and Gray 2016).
2.1 Fraud caused by the humans and the password theft is caused by the system is risk
to Bell Studio.
3.1 Risk of staff dishonesty is involved in the system (Salterio 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION SYSTEM
8. Conclusion
The information system of the Bell Studio includes manual working procedure and
documenting working procedure. All the procedures are done mainly by the clerks of
each department. Bell Studio has transaction process, management process and the
report g process and three sub systems were chosen from the operation of the business
that included in the Bell Studio.
The system that this report mentions is the purchasing system that contains about
material ordering of Bell Studio. The other systems that are included are payroll process
of paying their employee and the cash disbursement system of paying their supplier
with the required amount for their supplies. This project details the business operations
of the system that includes the DFD (Data Flow Diagrams) of the systems and the
flowchart of the systems. As stated from the perspective of business analyst, it is the
duty to make all the procedure advanced and up to date. So, this report also states the
internal flaws that business operations of the system incurs and the risks that are
included in the system. The report above shows the internal control weakness of the
three system and their risks associated with the system.
8. Conclusion
The information system of the Bell Studio includes manual working procedure and
documenting working procedure. All the procedures are done mainly by the clerks of
each department. Bell Studio has transaction process, management process and the
report g process and three sub systems were chosen from the operation of the business
that included in the Bell Studio.
The system that this report mentions is the purchasing system that contains about
material ordering of Bell Studio. The other systems that are included are payroll process
of paying their employee and the cash disbursement system of paying their supplier
with the required amount for their supplies. This project details the business operations
of the system that includes the DFD (Data Flow Diagrams) of the systems and the
flowchart of the systems. As stated from the perspective of business analyst, it is the
duty to make all the procedure advanced and up to date. So, this report also states the
internal flaws that business operations of the system incurs and the risks that are
included in the system. The report above shows the internal control weakness of the
three system and their risks associated with the system.

11STRATEGIC INFORMATION SYSTEM
Reference
Aladwan, M., 2018. Undertaking of environmental accounting responsibility to achieve
sustainable development: evidence from Jordanian chemical and mining
companies. International Journal of Managerial and Financial Accounting, 10(1), pp.48-
64.
Avgerou, C. and Walsham, G. eds., 2017. Information technology in context: Studies
from the perspective of developing countries: Studies from the perspective of
developing countries. Routledge.
Chen, Y., Knechel, W.R., Marisetty, V.B., Truong, C. and Veeraraghavan, M., 2016.
Board independence and internal control weakness: Evidence from SOX 404
disclosures. Auditing: A Journal of Practice & Theory, 36(2), pp.45-62.
Duncan, R.A.K. and Whittington, M., 2016. Enhancing cloud security and privacy: the
power and the weakness of the audit trail. CLOUD COMPUTING 2016.
Gallemore, J. and Labro, E., 2015. The importance of the internal information
environment for tax avoidance. Journal of Accounting and Economics, 60(1), pp.149-
167.
Haislip, J.Z., Masli, A., Richardson, V.J. and Sanchez, J.M., 2015. Repairing
organizational legitimacy following information technology (IT) material weaknesses:
Executive turnover, IT expertise, and IT system upgrades. Journal of Information
Systems, 30(1), pp.41-70.
Heeks, R., 2017. Information technology, information systems and public sector
accountability. In Information Technology in Context: Studies from the Perspective of
Developing Countries (pp. 201-219). Routledge.
Ji, X.D., Lu, W. and Qu, W., 2017. Voluntary disclosure of internal control weakness and
earnings quality: Evidence from China. The International Journal of Accounting, 52(1),
pp.27-44.
Kanodia, C. and Sapra, H., 2016. A real effects perspective to accounting measurement
and disclosure: Implications and insights for future research. Journal of Accounting
Research, 54(2), pp.623-676.
Khan, T. and Gray, R., 2016. Accounting, identity, autopoiesis+ sustainability: A
comment, development and expansion on Lawrence, Botes, Collins and Roper
(2013). Meditari Accountancy Research, 24(1), pp.36-55.
Rao, Y., Guo, K.H. and Chen, Y., 2015. Information systems maturity, knowledge
sharing, and firm performance. International Journal of Accounting & Information
Management, 23(2), pp.106-127.
Safari, H., Faraji, Z. and Majidian, S., 2016. Identifying and evaluating enterprise
architecture risks using FMEA and fuzzy VIKOR. Journal of Intelligent
Manufacturing, 27(2), pp.475-486.7
Reference
Aladwan, M., 2018. Undertaking of environmental accounting responsibility to achieve
sustainable development: evidence from Jordanian chemical and mining
companies. International Journal of Managerial and Financial Accounting, 10(1), pp.48-
64.
Avgerou, C. and Walsham, G. eds., 2017. Information technology in context: Studies
from the perspective of developing countries: Studies from the perspective of
developing countries. Routledge.
Chen, Y., Knechel, W.R., Marisetty, V.B., Truong, C. and Veeraraghavan, M., 2016.
Board independence and internal control weakness: Evidence from SOX 404
disclosures. Auditing: A Journal of Practice & Theory, 36(2), pp.45-62.
Duncan, R.A.K. and Whittington, M., 2016. Enhancing cloud security and privacy: the
power and the weakness of the audit trail. CLOUD COMPUTING 2016.
Gallemore, J. and Labro, E., 2015. The importance of the internal information
environment for tax avoidance. Journal of Accounting and Economics, 60(1), pp.149-
167.
Haislip, J.Z., Masli, A., Richardson, V.J. and Sanchez, J.M., 2015. Repairing
organizational legitimacy following information technology (IT) material weaknesses:
Executive turnover, IT expertise, and IT system upgrades. Journal of Information
Systems, 30(1), pp.41-70.
Heeks, R., 2017. Information technology, information systems and public sector
accountability. In Information Technology in Context: Studies from the Perspective of
Developing Countries (pp. 201-219). Routledge.
Ji, X.D., Lu, W. and Qu, W., 2017. Voluntary disclosure of internal control weakness and
earnings quality: Evidence from China. The International Journal of Accounting, 52(1),
pp.27-44.
Kanodia, C. and Sapra, H., 2016. A real effects perspective to accounting measurement
and disclosure: Implications and insights for future research. Journal of Accounting
Research, 54(2), pp.623-676.
Khan, T. and Gray, R., 2016. Accounting, identity, autopoiesis+ sustainability: A
comment, development and expansion on Lawrence, Botes, Collins and Roper
(2013). Meditari Accountancy Research, 24(1), pp.36-55.
Rao, Y., Guo, K.H. and Chen, Y., 2015. Information systems maturity, knowledge
sharing, and firm performance. International Journal of Accounting & Information
Management, 23(2), pp.106-127.
Safari, H., Faraji, Z. and Majidian, S., 2016. Identifying and evaluating enterprise
architecture risks using FMEA and fuzzy VIKOR. Journal of Intelligent
Manufacturing, 27(2), pp.475-486.7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





