Commonwealth Bank of Australia: Strategic Information Systems Report
VerifiedAdded on 2023/06/07
|20
|5493
|486
Report
AI Summary
This report provides a comprehensive analysis of the strategic information systems employed by the Commonwealth Bank of Australia (CBA). It begins with a brief overview of CBA, its critical success factors, and primary objectives, followed by an examination of the information necessary to achieve these goals and a mission statement for the client business. The report includes a formal organizational chart and a detailed analysis of CBA's current IT systems, identifying specific control weaknesses, particularly in mobile banking security. A new, improved system is proposed, highlighting the primary features such as biometric authentication and integration of PLS with HLS standards and upgrade the mainframe systems to a UNIX and DB2, along with the relevance of advanced technologies. The report also addresses technological platforms, potential security risks, and accounting controls for the new banking system, concluding with a summary of findings and recommendations.

Running head: STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
Strategic Information Systems of Commonwealth Bank of Australia
Name of the Student
Name of the University
Author’s note
Strategic Information Systems of Commonwealth Bank of Australia
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
Table of Contents
1. Introduction..................................................................................................................................2
1.1 A Brief Introduction of Commonwealth Bank of Australia..................................................2
1.2 Critical Success Factors and Primary Objectives of CBA.....................................................2
1.3 Information helpful for achieving the Objectives..................................................................3
1.4 Mission Statement for the Client Business............................................................................3
2. Formal Organizational Chart of Commonwealth Bank of Australia...........................................4
3. A Brief Analysis of Commonwealth Bank of Australia..............................................................4
3.1 The Current System of Commonwealth Bank of Australia...................................................4
3.2 Identification of Specific Control Weaknesses within Commonwealth Bank of Australia. .5
4. New Improved System for the Commonwealth Bank of Australia.............................................7
4.1 Primary Features of New Improved System..........................................................................7
4.2 Relevance of the New Advanced Technologies....................................................................9
5. Other Kinds of Requirements....................................................................................................10
5.1 Technological Platforms for the System..............................................................................10
5.2 Potential Security Risks for the Banking Sector of CBA....................................................11
5.3 Accounting Controls over the New Banking System..........................................................12
6. Conclusion.................................................................................................................................13
7. References..................................................................................................................................14
Table of Contents
1. Introduction..................................................................................................................................2
1.1 A Brief Introduction of Commonwealth Bank of Australia..................................................2
1.2 Critical Success Factors and Primary Objectives of CBA.....................................................2
1.3 Information helpful for achieving the Objectives..................................................................3
1.4 Mission Statement for the Client Business............................................................................3
2. Formal Organizational Chart of Commonwealth Bank of Australia...........................................4
3. A Brief Analysis of Commonwealth Bank of Australia..............................................................4
3.1 The Current System of Commonwealth Bank of Australia...................................................4
3.2 Identification of Specific Control Weaknesses within Commonwealth Bank of Australia. .5
4. New Improved System for the Commonwealth Bank of Australia.............................................7
4.1 Primary Features of New Improved System..........................................................................7
4.2 Relevance of the New Advanced Technologies....................................................................9
5. Other Kinds of Requirements....................................................................................................10
5.1 Technological Platforms for the System..............................................................................10
5.2 Potential Security Risks for the Banking Sector of CBA....................................................11
5.3 Accounting Controls over the New Banking System..........................................................12
6. Conclusion.................................................................................................................................13
7. References..................................................................................................................................14

2STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
1. Introduction
1.1 A Brief Introduction of Commonwealth Bank of Australia
Information Technology (IT) has become a major factor of success for any organisation
in the world. This report is based on the various kinds of changes based on IT, which are being
made in the Commonwealth Bank of Australia (CBA). The CBA is considered as one of the
largest retail sector bank based in Australia. The banking sector is one of the largest and hence
dominates the sector of retail deposits and home loans. The bank also has a strong base of
business franchise in the segments of the retail market (Schlagwein, Thorogood and Willcocks
2014).
1.2 Critical Success Factors and Primary Objectives of CBA
The CBA has majorly acquired the major status of a popular financial icon that has been
evident with their huge success based on their success stories in the past. They have hence
continued in the path of financial success and various kinds of innovation in the technology
based on customer-centric (Osei-Kyei and Chan 2015). CBA is regarded as one of the largest
repositories within the banking sector and hence has been widely accepted by the people of
Australia. Hence the wide community of people hold ha high level of expectation from the
institution.
Some of the critical factors of success for the CBA are:
1. Passionate form of leadership in the world market.
2. Rewards and Recognition that would be linked with the services and outcomes based
on sales.
1. Introduction
1.1 A Brief Introduction of Commonwealth Bank of Australia
Information Technology (IT) has become a major factor of success for any organisation
in the world. This report is based on the various kinds of changes based on IT, which are being
made in the Commonwealth Bank of Australia (CBA). The CBA is considered as one of the
largest retail sector bank based in Australia. The banking sector is one of the largest and hence
dominates the sector of retail deposits and home loans. The bank also has a strong base of
business franchise in the segments of the retail market (Schlagwein, Thorogood and Willcocks
2014).
1.2 Critical Success Factors and Primary Objectives of CBA
The CBA has majorly acquired the major status of a popular financial icon that has been
evident with their huge success based on their success stories in the past. They have hence
continued in the path of financial success and various kinds of innovation in the technology
based on customer-centric (Osei-Kyei and Chan 2015). CBA is regarded as one of the largest
repositories within the banking sector and hence has been widely accepted by the people of
Australia. Hence the wide community of people hold ha high level of expectation from the
institution.
Some of the critical factors of success for the CBA are:
1. Passionate form of leadership in the world market.
2. Rewards and Recognition that would be linked with the services and outcomes based
on sales.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
3. High level of training of employees and mastery of the entire process of the
organization.
4. Clear form of expectations and effective measures of follow-up of the issues (Chileshe
and John Kikwasi 2014).
The primary form of objectives of the CBA are:
1. Retaining of lowest form of structure of cost.
2. Expanding of customer share with the help of direct and online form of leadership.
3. Implementation of best forms of management of people and resources.
4. Providing of more kinds of financial services and meeting the expectations of the
customer (Worthington 2016).
1.3 Information helpful for achieving the Objectives
The CBA would require to maintain a high form of competitive structure of cost that
would be meaningful for the growth of the customer base for a greater form of advantage. The
use of internet based products and various kinds of services would be the major reason for the
growth of the business. There is a high level of competitive pressure in the market from new
kinds of entrants. Many of the strategic initiatives would be primarily focused on ensuring
quality and hence they have retained the advantage of low unit of the structure of cost (Willcocks
and Reynolds 2015).
1.4 Mission Statement for the Client Business
A mission statement for the client business based within the context of CBA is – To
provide high level of services to the customer and meet the requirements of the business.
3. High level of training of employees and mastery of the entire process of the
organization.
4. Clear form of expectations and effective measures of follow-up of the issues (Chileshe
and John Kikwasi 2014).
The primary form of objectives of the CBA are:
1. Retaining of lowest form of structure of cost.
2. Expanding of customer share with the help of direct and online form of leadership.
3. Implementation of best forms of management of people and resources.
4. Providing of more kinds of financial services and meeting the expectations of the
customer (Worthington 2016).
1.3 Information helpful for achieving the Objectives
The CBA would require to maintain a high form of competitive structure of cost that
would be meaningful for the growth of the customer base for a greater form of advantage. The
use of internet based products and various kinds of services would be the major reason for the
growth of the business. There is a high level of competitive pressure in the market from new
kinds of entrants. Many of the strategic initiatives would be primarily focused on ensuring
quality and hence they have retained the advantage of low unit of the structure of cost (Willcocks
and Reynolds 2015).
1.4 Mission Statement for the Client Business
A mission statement for the client business based within the context of CBA is – To
provide high level of services to the customer and meet the requirements of the business.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
2. Formal Organizational Chart of Commonwealth Bank of Australia
(Fig 1: Organizational Chart of Commonwealth Bank of Australia)
3. A Brief Analysis of Commonwealth Bank of Australia
3.1 The Current System of Commonwealth Bank of Australia
The CBA is a public based company and is listed within the Australian Securities
Exchange. It is one of the largest form of multinational bank within Australia and they have their
subsidiaries in United Kingdom, USA, Asia, Fiji and New Zealand. The bank is able to offer
several forms of financial based services to different kinds of owners of business and various
personal clients (Fenna 2013). The structure of the organization of CBA is integrated in a vertical
manner and is thus able to operate in the form of a network based structure. The primary form of
vision of the organization is to become one of the finest form of organizations based on financial
services as they excel in high form of customer service and huge level of strategy (Murray et al.
2014). These forms of strategies are highly evaluated for recognizing various kinds of significant
opportunities within the business objectives in order to develop much value for their people,
stakeholders and customers.
With the rise in the technological aspects, the CBA has integrated Information
Technology (IT) systems within the organizational prospects. The bank has integrated various
2. Formal Organizational Chart of Commonwealth Bank of Australia
(Fig 1: Organizational Chart of Commonwealth Bank of Australia)
3. A Brief Analysis of Commonwealth Bank of Australia
3.1 The Current System of Commonwealth Bank of Australia
The CBA is a public based company and is listed within the Australian Securities
Exchange. It is one of the largest form of multinational bank within Australia and they have their
subsidiaries in United Kingdom, USA, Asia, Fiji and New Zealand. The bank is able to offer
several forms of financial based services to different kinds of owners of business and various
personal clients (Fenna 2013). The structure of the organization of CBA is integrated in a vertical
manner and is thus able to operate in the form of a network based structure. The primary form of
vision of the organization is to become one of the finest form of organizations based on financial
services as they excel in high form of customer service and huge level of strategy (Murray et al.
2014). These forms of strategies are highly evaluated for recognizing various kinds of significant
opportunities within the business objectives in order to develop much value for their people,
stakeholders and customers.
With the rise in the technological aspects, the CBA has integrated Information
Technology (IT) systems within the organizational prospects. The bank has integrated various

5STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
kinds of IT related services in their daily operations as they are extremely cautious about the
services provided to the customers (Oliveira et al. 2014). The CBA could be widely regarded as
one of the advanced forms of banks, which are highly advanced in the aspects of technology.
They have adopted huge technical changes within their systems, which are highly updated and
are able to provide higher forms of customer service. They update their technical services and
products on a daily basis. One of the most successful implementation of technology that have
been made by the CBA include the implementation of the mobile banking systems for their
customers (Abawajy 2014). This would be a major help for the organization and the customers as
they would be able to access the website of the organization from their personal mobile devices.
According to Mr. Whitely, who is the executive general manager of the CBA it has been
declared the mobile banking systems of the CBA could be regarded one of the secure form of
access methods as compared to the computer based banking systems (Kenway 2018). With the
help of the mobile banking systems, the banking sector would be able to easily track a person
who would be making use of mobile systems. The mobile devices make use of SIM for the
purpose of connecting with the bank. The present forms of the mobile version of banking within
the web browser would be able to protect the customers from any kind of hacking systems.
Hence it would add a high level of security for the customers whenever they would be availing
the banking services from the CBA (Smith 2018).
3.2 Identification of Specific Control Weaknesses within Commonwealth Bank of Australia
With the rise of the mobile banking systems, the CBA would have to maintain the high
form of security within the devices. Meeting the standards of authentication is one of the major
problem, which is faced by the CBA. The banking systems of CBA follows some form of
mechanisms based on the concerns of security within the mobile banking sector (Buckby,
kinds of IT related services in their daily operations as they are extremely cautious about the
services provided to the customers (Oliveira et al. 2014). The CBA could be widely regarded as
one of the advanced forms of banks, which are highly advanced in the aspects of technology.
They have adopted huge technical changes within their systems, which are highly updated and
are able to provide higher forms of customer service. They update their technical services and
products on a daily basis. One of the most successful implementation of technology that have
been made by the CBA include the implementation of the mobile banking systems for their
customers (Abawajy 2014). This would be a major help for the organization and the customers as
they would be able to access the website of the organization from their personal mobile devices.
According to Mr. Whitely, who is the executive general manager of the CBA it has been
declared the mobile banking systems of the CBA could be regarded one of the secure form of
access methods as compared to the computer based banking systems (Kenway 2018). With the
help of the mobile banking systems, the banking sector would be able to easily track a person
who would be making use of mobile systems. The mobile devices make use of SIM for the
purpose of connecting with the bank. The present forms of the mobile version of banking within
the web browser would be able to protect the customers from any kind of hacking systems.
Hence it would add a high level of security for the customers whenever they would be availing
the banking services from the CBA (Smith 2018).
3.2 Identification of Specific Control Weaknesses within Commonwealth Bank of Australia
With the rise of the mobile banking systems, the CBA would have to maintain the high
form of security within the devices. Meeting the standards of authentication is one of the major
problem, which is faced by the CBA. The banking systems of CBA follows some form of
mechanisms based on the concerns of security within the mobile banking sector (Buckby,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
Gallery and Ma 2015). A customer who would like to avail the technology of mobile banking
due to the huge purpose of mobility with which they would access the banking systems in any
form of situation. With the help of the mobile banking systems provided by the CBA, the
customers would be able to transfer money from one banking account to another in a user-
friendly environment. They could also be able to check the current status of their account. There
are some customers who would not wish to avail these kinds of high form of services due to a
short level of trust on the banking (Salim, Arjomandi and Seufert 2016).
In the recent times, there have been major cases of forgery and hacks within the banking
systems, which has led to lowering of trust in the mobile based banking forms. These customers
are not ready to adopt such kinds of banking systems as it would bring inconvenience on the part
of the users with the assumption that they would not be able to prevent any kinds of direct or
indirect forms of attacks on the systems. The mechanism of security that are mainly adopted by
the CBA mainly face different kinds of security issues such as being attacked by many kinds of
unauthorized users. This is mainly regarded as the highest form of priority in the aspects of
security (Brown and Davis 2015).
Another form of weakness that is faced by the CBA is that the banks mainly outsource
their facilities from third party architecture. They mainly handle the customer service of mobile
banking systems with the help of a third party service provider (Florina, Ludovica and Leonica
2013). They are thus responsible for secure form of transactions and management of the systems.
This form of method is also responsible for mitigating the authentication issues. There is no such
form of trust in the security of the data of the accounts of the customers that would include the
details of the bank account, addresses of the customers, which would be managed by the third
party service provider. Hence the customer would not be able to feel the security of sharing their
Gallery and Ma 2015). A customer who would like to avail the technology of mobile banking
due to the huge purpose of mobility with which they would access the banking systems in any
form of situation. With the help of the mobile banking systems provided by the CBA, the
customers would be able to transfer money from one banking account to another in a user-
friendly environment. They could also be able to check the current status of their account. There
are some customers who would not wish to avail these kinds of high form of services due to a
short level of trust on the banking (Salim, Arjomandi and Seufert 2016).
In the recent times, there have been major cases of forgery and hacks within the banking
systems, which has led to lowering of trust in the mobile based banking forms. These customers
are not ready to adopt such kinds of banking systems as it would bring inconvenience on the part
of the users with the assumption that they would not be able to prevent any kinds of direct or
indirect forms of attacks on the systems. The mechanism of security that are mainly adopted by
the CBA mainly face different kinds of security issues such as being attacked by many kinds of
unauthorized users. This is mainly regarded as the highest form of priority in the aspects of
security (Brown and Davis 2015).
Another form of weakness that is faced by the CBA is that the banks mainly outsource
their facilities from third party architecture. They mainly handle the customer service of mobile
banking systems with the help of a third party service provider (Florina, Ludovica and Leonica
2013). They are thus responsible for secure form of transactions and management of the systems.
This form of method is also responsible for mitigating the authentication issues. There is no such
form of trust in the security of the data of the accounts of the customers that would include the
details of the bank account, addresses of the customers, which would be managed by the third
party service provider. Hence the customer would not be able to feel the security of sharing their
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
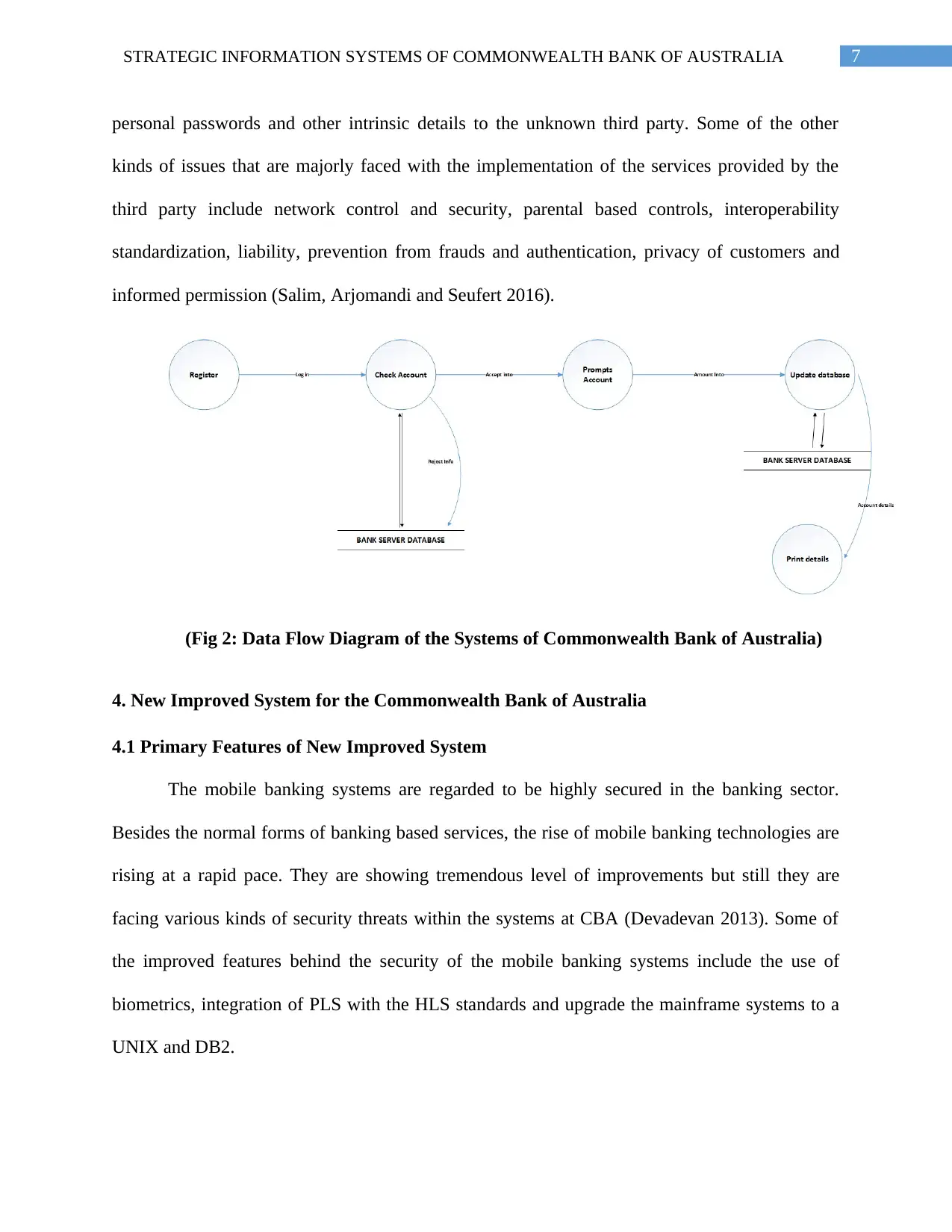
7STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
personal passwords and other intrinsic details to the unknown third party. Some of the other
kinds of issues that are majorly faced with the implementation of the services provided by the
third party include network control and security, parental based controls, interoperability
standardization, liability, prevention from frauds and authentication, privacy of customers and
informed permission (Salim, Arjomandi and Seufert 2016).
(Fig 2: Data Flow Diagram of the Systems of Commonwealth Bank of Australia)
4. New Improved System for the Commonwealth Bank of Australia
4.1 Primary Features of New Improved System
The mobile banking systems are regarded to be highly secured in the banking sector.
Besides the normal forms of banking based services, the rise of mobile banking technologies are
rising at a rapid pace. They are showing tremendous level of improvements but still they are
facing various kinds of security threats within the systems at CBA (Devadevan 2013). Some of
the improved features behind the security of the mobile banking systems include the use of
biometrics, integration of PLS with the HLS standards and upgrade the mainframe systems to a
UNIX and DB2.
personal passwords and other intrinsic details to the unknown third party. Some of the other
kinds of issues that are majorly faced with the implementation of the services provided by the
third party include network control and security, parental based controls, interoperability
standardization, liability, prevention from frauds and authentication, privacy of customers and
informed permission (Salim, Arjomandi and Seufert 2016).
(Fig 2: Data Flow Diagram of the Systems of Commonwealth Bank of Australia)
4. New Improved System for the Commonwealth Bank of Australia
4.1 Primary Features of New Improved System
The mobile banking systems are regarded to be highly secured in the banking sector.
Besides the normal forms of banking based services, the rise of mobile banking technologies are
rising at a rapid pace. They are showing tremendous level of improvements but still they are
facing various kinds of security threats within the systems at CBA (Devadevan 2013). Some of
the improved features behind the security of the mobile banking systems include the use of
biometrics, integration of PLS with the HLS standards and upgrade the mainframe systems to a
UNIX and DB2.

8STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
With the help of providing of biometric method for the security of the devices, the CBA
would be able to adopt extreme levels of trusts with the mobile banking systems. This would be
able to ensure the trust within the systems of mobile banking (Lovelock and Patterson 2015). The
method of adoption of biometrics within the mobile banking systems would be able to identify
the physical behavior of any individual. The use of biometric method would be a useful method
as the biometric details of a person are unique for every person. Hence it is extremely impossible
for copying, sharing or forgetting of the passwords. This is due to the reason as each individual
has their own personal identity. The use of biometric mechanism would be extremely important
as it helps in the improvement of the levels of security within the banking systems of CBA
(Bajada and Trayler 2015). There are various kinds of mechanisms for biometric recognition
based on the methods of authentication. Each of the biological features of persons vary from one
another. Hence, it could be suggestible that the biometric feature of authentication would be very
much useful for authenticating the user. Some of the other features based on biometric
authentication that could be included within the banking systems of CBA include hand based
recognition, face recognition, fingerprint recognition and voice recognition. Various forms of
research in the field of fingerprint recognition technology are being developed and newer kinds
of sensors are being developed.
The integration of PLS with HLS systems would also prove to be beneficial for the
security of the systems. The user interface of the PLS is mainly operated on a non-supportable
platform. In this kind of systems, the bank would normally have to enter the data based on the
applications on the internet into the systems based on PLS for the purpose of producing the
documentation of loan. Hence, in order to reduce the costs, optimize the level of functionality
and improve the level of functionality, the CBA should be able to integrate these systems within
With the help of providing of biometric method for the security of the devices, the CBA
would be able to adopt extreme levels of trusts with the mobile banking systems. This would be
able to ensure the trust within the systems of mobile banking (Lovelock and Patterson 2015). The
method of adoption of biometrics within the mobile banking systems would be able to identify
the physical behavior of any individual. The use of biometric method would be a useful method
as the biometric details of a person are unique for every person. Hence it is extremely impossible
for copying, sharing or forgetting of the passwords. This is due to the reason as each individual
has their own personal identity. The use of biometric mechanism would be extremely important
as it helps in the improvement of the levels of security within the banking systems of CBA
(Bajada and Trayler 2015). There are various kinds of mechanisms for biometric recognition
based on the methods of authentication. Each of the biological features of persons vary from one
another. Hence, it could be suggestible that the biometric feature of authentication would be very
much useful for authenticating the user. Some of the other features based on biometric
authentication that could be included within the banking systems of CBA include hand based
recognition, face recognition, fingerprint recognition and voice recognition. Various forms of
research in the field of fingerprint recognition technology are being developed and newer kinds
of sensors are being developed.
The integration of PLS with HLS systems would also prove to be beneficial for the
security of the systems. The user interface of the PLS is mainly operated on a non-supportable
platform. In this kind of systems, the bank would normally have to enter the data based on the
applications on the internet into the systems based on PLS for the purpose of producing the
documentation of loan. Hence, in order to reduce the costs, optimize the level of functionality
and improve the level of functionality, the CBA should be able to integrate these systems within
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
their sector. With the integration of these systems within their sector, the CBA would be highly
successful for exceling their levels of customer services with the help of their IT service
providers. The infrastructure of IT within the CBA have a major history of success (Van
Oosterzee, Dale and Preece 2014). Hence they would be able to implement much better forms of
systems in order to provide better forms of customer service. The implementation of these forms
of systems within the IT infrastructure would be helpful for making faster forms of decisions,
funding, differentiation between greater form of products and thus reaping higher forms of
approval rates.
The CBA has a higher form of IT based infrastructure based on IT systems. With the help
of their IT partners, the CBA should upgrade their old mainframe systems that were based on the
older versions of Windows OS to a much higher level based on DB2 and UNIX systems. With
the upgrade of the systems to a completely different mainframe systems, it would be extremely
vital for the IT systems and mobile banking sector to stay protected from several kinds of risks
within the systems. The CBA would also be able to increase the level of efficiency within the
organisation and also would be able to reduce the costs (Bott and Milkau 2014). The CBA
systems should also implement automation systems within their organisation for the purpose of
increasing the security levels, monitor over their existing IT systems, and enable higher speeds of
processing that would be able to offer higher forms of speeds within the accessibility of the
systems.
4.2 Relevance of the New Advanced Technologies
The implementation of the newer forms of systems could be classified under the EDI
(Electronic Data Interchange). This systems is an electronic form of interchange based on the
information related to a business organization. This system allow the IT systems of CBA for the
their sector. With the integration of these systems within their sector, the CBA would be highly
successful for exceling their levels of customer services with the help of their IT service
providers. The infrastructure of IT within the CBA have a major history of success (Van
Oosterzee, Dale and Preece 2014). Hence they would be able to implement much better forms of
systems in order to provide better forms of customer service. The implementation of these forms
of systems within the IT infrastructure would be helpful for making faster forms of decisions,
funding, differentiation between greater form of products and thus reaping higher forms of
approval rates.
The CBA has a higher form of IT based infrastructure based on IT systems. With the help
of their IT partners, the CBA should upgrade their old mainframe systems that were based on the
older versions of Windows OS to a much higher level based on DB2 and UNIX systems. With
the upgrade of the systems to a completely different mainframe systems, it would be extremely
vital for the IT systems and mobile banking sector to stay protected from several kinds of risks
within the systems. The CBA would also be able to increase the level of efficiency within the
organisation and also would be able to reduce the costs (Bott and Milkau 2014). The CBA
systems should also implement automation systems within their organisation for the purpose of
increasing the security levels, monitor over their existing IT systems, and enable higher speeds of
processing that would be able to offer higher forms of speeds within the accessibility of the
systems.
4.2 Relevance of the New Advanced Technologies
The implementation of the newer forms of systems could be classified under the EDI
(Electronic Data Interchange). This systems is an electronic form of interchange based on the
information related to a business organization. This system allow the IT systems of CBA for the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
processing of information using a standardized format. With the help of this process, the
company would be able to send vital information to some other company in an electronic format.
With the help of the EDI systems, the CBA banking systems would be able to reduce the risks of
losing of sensitive information. This is due to the reason that with the effect of EDI systems, the
data would be transferred to another sector in an electronic, secured format and a fast format.
The use of EDI systems within the banking systems of CBA would be able to help the banking
sector to avoid various kinds of data losses during the process of transit as the transmissions
could be easily tracked and would be monitored in real time scenarios (Jain, Keneley and
Thomson 2015).
The use of EDI systems within the latest design of the new information systems within
the banking sector would be very much useful for supporting the efficiency within the workflow,
streamlining of the various processes related to the transfer of documents, saving of a
considerable amount of time, reduction of errors and also bringing in accuracy of improving of
documents, which would enable the faster forms of business related transactions. The process of
EDI is also much more cost-effective. Hence, the integration of the EDI systems within the new
implemented systems of the banking sector of CBA (Mocker, Weill and Woerner 2014).
processing of information using a standardized format. With the help of this process, the
company would be able to send vital information to some other company in an electronic format.
With the help of the EDI systems, the CBA banking systems would be able to reduce the risks of
losing of sensitive information. This is due to the reason that with the effect of EDI systems, the
data would be transferred to another sector in an electronic, secured format and a fast format.
The use of EDI systems within the banking systems of CBA would be able to help the banking
sector to avoid various kinds of data losses during the process of transit as the transmissions
could be easily tracked and would be monitored in real time scenarios (Jain, Keneley and
Thomson 2015).
The use of EDI systems within the latest design of the new information systems within
the banking sector would be very much useful for supporting the efficiency within the workflow,
streamlining of the various processes related to the transfer of documents, saving of a
considerable amount of time, reduction of errors and also bringing in accuracy of improving of
documents, which would enable the faster forms of business related transactions. The process of
EDI is also much more cost-effective. Hence, the integration of the EDI systems within the new
implemented systems of the banking sector of CBA (Mocker, Weill and Woerner 2014).
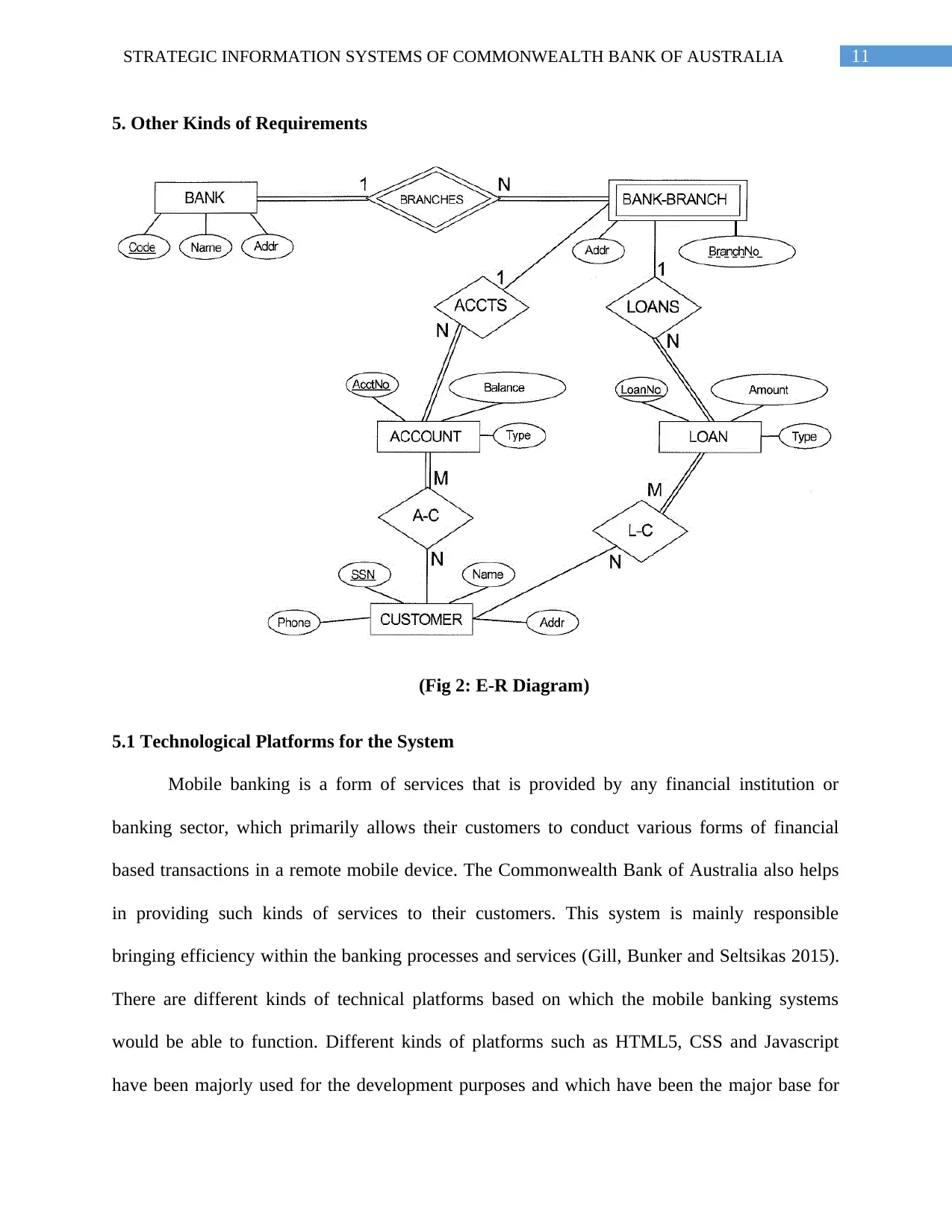
11STRATEGIC INFORMATION SYSTEMS OF COMMONWEALTH BANK OF AUSTRALIA
5. Other Kinds of Requirements
(Fig 2: E-R Diagram)
5.1 Technological Platforms for the System
Mobile banking is a form of services that is provided by any financial institution or
banking sector, which primarily allows their customers to conduct various forms of financial
based transactions in a remote mobile device. The Commonwealth Bank of Australia also helps
in providing such kinds of services to their customers. This system is mainly responsible
bringing efficiency within the banking processes and services (Gill, Bunker and Seltsikas 2015).
There are different kinds of technical platforms based on which the mobile banking systems
would be able to function. Different kinds of platforms such as HTML5, CSS and Javascript
have been majorly used for the development purposes and which have been the major base for
5. Other Kinds of Requirements
(Fig 2: E-R Diagram)
5.1 Technological Platforms for the System
Mobile banking is a form of services that is provided by any financial institution or
banking sector, which primarily allows their customers to conduct various forms of financial
based transactions in a remote mobile device. The Commonwealth Bank of Australia also helps
in providing such kinds of services to their customers. This system is mainly responsible
bringing efficiency within the banking processes and services (Gill, Bunker and Seltsikas 2015).
There are different kinds of technical platforms based on which the mobile banking systems
would be able to function. Different kinds of platforms such as HTML5, CSS and Javascript
have been majorly used for the development purposes and which have been the major base for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



