Information Security Management and Mitigation for Woolworths Limited
VerifiedAdded on 2020/03/04
|16
|2959
|55
Report
AI Summary
This report provides a detailed analysis of the strategic information security of Woolworths Limited. It begins by highlighting the importance of information security within the organization, emphasizing its role in protecting sensitive data and ensuring operational efficiency. The report then delves into the principles of information security management, discussing key aspects such as planning, policies, protection, leadership, and project implementation. An overview of Woolworths Limited's information security model, including the role of the Chief Information Security Officer (CISO), is provided. The report examines the legal and ethical considerations relevant to improving the management system, including contingency planning, risk management, and decision-making processes. Enterprise security policies, covering technical and end-user aspects, are also explored. Furthermore, the report identifies specific information security issues faced by Woolworths Limited, such as social and cyber crimes, DDOS attacks, and malware. Mitigation strategies, including the installation of antivirus software, encryption, and authentication measures, are discussed. Finally, the report outlines information security management policies developed for Woolworths Limited, including security education, training, and awareness programs. The conclusion emphasizes the importance of information security management for business efficiency and organizational outcomes, summarizing key findings and suggesting areas for improvement.

Running head: STRATEGIC INFORMATION SECURITY
Strategic Information Security: Woolworths Limited
Name of the student:
Student number:
Strategic Information Security: Woolworths Limited
Name of the student:
Student number:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION SECURITY
Abstract
This report reflects the importance of implementing the information system security in
Woolworths Limited. The challenges associated to Woolworths Limited’s Information Security
(IS) and their mitigate approaches are also elaborated inn this report. It has been found that, a
robust security system that covers the physical security, cyber security and communication
security is used by Woolworths Limited. However still the company is facing major level of
security issues in order to mitigate those issues the company has formulated a complete
contingency measures containing the incident response plan. The core components such as
confidentiality, integrity, availability etc are elaborated in this report.
Abstract
This report reflects the importance of implementing the information system security in
Woolworths Limited. The challenges associated to Woolworths Limited’s Information Security
(IS) and their mitigate approaches are also elaborated inn this report. It has been found that, a
robust security system that covers the physical security, cyber security and communication
security is used by Woolworths Limited. However still the company is facing major level of
security issues in order to mitigate those issues the company has formulated a complete
contingency measures containing the incident response plan. The core components such as
confidentiality, integrity, availability etc are elaborated in this report.

2STRATEGIC INFORMATION SECURITY
Table of Contents
Introduction......................................................................................................................................4
1. Role of information security in Woolworths Limited.................................................................5
1.1 Principles of information security management....................................................................5
1.2 Information security model of Woolworths Limited.............................................................6
3. Laws and ethical consideration needed for improving the management system of Woolworths
Limited.............................................................................................................................................7
3.1 Contingency plan...................................................................................................................7
3.2 Role of decision making in Woolworths Limited..................................................................8
4. Enterprise security policies..........................................................................................................9
5. Information security issues..........................................................................................................9
5.1 Information security issues associated to Woolworths Limited..........................................10
5.2 Strategic information security issue mitigation planning for Woolworths..........................10
6. Information security management policies developed for Woolworths Limited......................10
Conclusion.....................................................................................................................................11
Recommendations..........................................................................................................................12
References......................................................................................................................................14
Table of Contents
Introduction......................................................................................................................................4
1. Role of information security in Woolworths Limited.................................................................5
1.1 Principles of information security management....................................................................5
1.2 Information security model of Woolworths Limited.............................................................6
3. Laws and ethical consideration needed for improving the management system of Woolworths
Limited.............................................................................................................................................7
3.1 Contingency plan...................................................................................................................7
3.2 Role of decision making in Woolworths Limited..................................................................8
4. Enterprise security policies..........................................................................................................9
5. Information security issues..........................................................................................................9
5.1 Information security issues associated to Woolworths Limited..........................................10
5.2 Strategic information security issue mitigation planning for Woolworths..........................10
6. Information security management policies developed for Woolworths Limited......................10
Conclusion.....................................................................................................................................11
Recommendations..........................................................................................................................12
References......................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3STRATEGIC INFORMATION SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4STRATEGIC INFORMATION SECURITY
Introduction
This report depicts the importance of Information Security (IS) in different Small to
Medium Enterprise (SME) to secure their organizational confidential data. The numbers of
consumers are increasing day by day in Woolworths Limited, thus the data management is
becoming complex. In order to minimize the complexity most of the business organizations have
implemented information system in terms of ERP and SCM in their organizations (Rose,
Hawryszkiewycz and Kang 2015). Similarly, Woolworths Limited has also implemented ERP
Information System for improving their data management application. With the help of the ERP
Information System the data regarding the employees and the consumers can be managed in a
much better way. Due to distinct features of the SMEs, the information Security management for
the SMEs is also different.
The challenges associated to Information Security are represented in this report and at the
same time for mitigating the issues different issues combat strategies are also elaborated in this
report. The role of information security in Woolworths Limited and the principles of Information
Security management are also illustrated in this report. Apart from this, the laws and ethical
aspects those are considered in the company are also elaborated. Though, different issue
mitigation strategies are elaborated in this report but still certain recommendations are also
required to be incorporated to manage the information security system in Woolworths Limited.
Introduction
This report depicts the importance of Information Security (IS) in different Small to
Medium Enterprise (SME) to secure their organizational confidential data. The numbers of
consumers are increasing day by day in Woolworths Limited, thus the data management is
becoming complex. In order to minimize the complexity most of the business organizations have
implemented information system in terms of ERP and SCM in their organizations (Rose,
Hawryszkiewycz and Kang 2015). Similarly, Woolworths Limited has also implemented ERP
Information System for improving their data management application. With the help of the ERP
Information System the data regarding the employees and the consumers can be managed in a
much better way. Due to distinct features of the SMEs, the information Security management for
the SMEs is also different.
The challenges associated to Information Security are represented in this report and at the
same time for mitigating the issues different issues combat strategies are also elaborated in this
report. The role of information security in Woolworths Limited and the principles of Information
Security management are also illustrated in this report. Apart from this, the laws and ethical
aspects those are considered in the company are also elaborated. Though, different issue
mitigation strategies are elaborated in this report but still certain recommendations are also
required to be incorporated to manage the information security system in Woolworths Limited.
5STRATEGIC INFORMATION SECURITY
1. Role of information security in Woolworths Limited
1.1 Principles of information security management
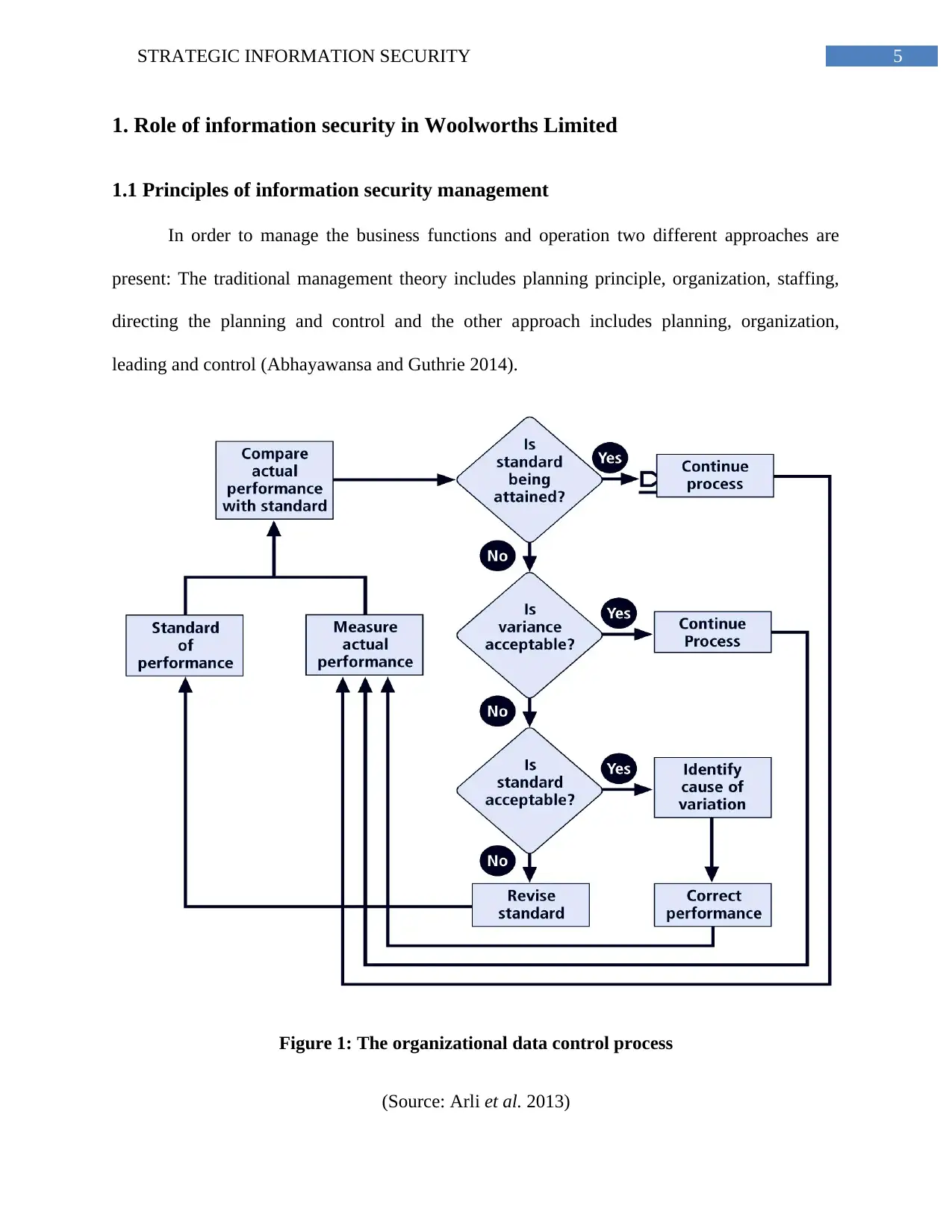
In order to manage the business functions and operation two different approaches are
present: The traditional management theory includes planning principle, organization, staffing,
directing the planning and control and the other approach includes planning, organization,
leading and control (Abhayawansa and Guthrie 2014).
Figure 1: The organizational data control process
(Source: Arli et al. 2013)
1. Role of information security in Woolworths Limited
1.1 Principles of information security management
In order to manage the business functions and operation two different approaches are
present: The traditional management theory includes planning principle, organization, staffing,
directing the planning and control and the other approach includes planning, organization,
leading and control (Abhayawansa and Guthrie 2014).
Figure 1: The organizational data control process
(Source: Arli et al. 2013)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6STRATEGIC INFORMATION SECURITY
Plan: Planning is referred to as the initial phase for Information Security Management
that helps to develop, create and implement different strategies, for the business organization
(Scott and Walker 2017). In this phase the business analysts are allowed to develop strategic
planning, tactical planning and operational planning as well.
Policies: With the help of accurate policies and practices the business organization will
be able to undertake the necessary actions those are helpful to gain measurable success from the
competitive market (Das Nair and Dube 2017). The management policies are dedicated to
structure all the required resources properly to accomplish the organizational preliminarily
determined goals.
Protection: In order to maintain the organizational security it is necessary to adopt
proper protection practices in terms of encryption, firewall and authentication.
Leadership: In order to lead the business towards measurable success it is necessary to
encourage the employees who are working for the company (Mertens et al. 2016). Leaders help
to motivate the employees by encouraging them throughout. Thus, the HRM of Woolworths
Limited is required to develop the project under the guidance of the leaders only.
Projects: In order to implement any strategic planning the company is required to form
project under the guidance of the professionals. It will help the organization to develop the
security model as well.
1.2 Information security model of Woolworths Limited
Woolworths Limited is the very first organization that hired CISO. The chief information
security officer of the company is responsible to put all the efforts to boost up the infosec
credential of the company (Bailey 2017). Though, in previous days the business operations are
Plan: Planning is referred to as the initial phase for Information Security Management
that helps to develop, create and implement different strategies, for the business organization
(Scott and Walker 2017). In this phase the business analysts are allowed to develop strategic
planning, tactical planning and operational planning as well.
Policies: With the help of accurate policies and practices the business organization will
be able to undertake the necessary actions those are helpful to gain measurable success from the
competitive market (Das Nair and Dube 2017). The management policies are dedicated to
structure all the required resources properly to accomplish the organizational preliminarily
determined goals.
Protection: In order to maintain the organizational security it is necessary to adopt
proper protection practices in terms of encryption, firewall and authentication.
Leadership: In order to lead the business towards measurable success it is necessary to
encourage the employees who are working for the company (Mertens et al. 2016). Leaders help
to motivate the employees by encouraging them throughout. Thus, the HRM of Woolworths
Limited is required to develop the project under the guidance of the leaders only.
Projects: In order to implement any strategic planning the company is required to form
project under the guidance of the professionals. It will help the organization to develop the
security model as well.
1.2 Information security model of Woolworths Limited
Woolworths Limited is the very first organization that hired CISO. The chief information
security officer of the company is responsible to put all the efforts to boost up the infosec
credential of the company (Bailey 2017). Though, in previous days the business operations are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7STRATEGIC INFORMATION SECURITY
managed by the Information Security Manager but currently the Chief Information Security
Officer (CISO) is hired to develop the risk management policies for Woolworths limited. CISO
helps to direct the business operation towards massive success by ensuring the business
objectives in a secured ad commercial manner. The threats associated to the cyber crime could be
mitigated completely through the help of information security, strategic planning and
administrative level operations (Frederick Rose, Hawryszkiewycz and Kang 2014). Both the
strategic planning and the administrative operations are managed by the information security
model developed by Woolworths Limited.
3. Laws and ethical consideration needed for improving the management
system of Woolworths Limited
3.1 Contingency plan
After analyzing the current status of Woolworths Limited it has been found, that the
company fails to adopt all the security aspects therefore in order to mitigate the issues it is
necessary to make proper contingency planning (Sah et al. 2014). The steps those have been
undertaken by Woolworths Limited are as follows:
In order identify the material risks of the company, appropriate risk management
planning are required to be adopted (Akbar and Ahsan 2014). It helps to reduce the material
business risks from the core management system of the business organization.
The administrative adequacy and the unit risk management plans should be incorporated
for developing the financial statement and accounting policies of Woolworth Limited.
managed by the Information Security Manager but currently the Chief Information Security
Officer (CISO) is hired to develop the risk management policies for Woolworths limited. CISO
helps to direct the business operation towards massive success by ensuring the business
objectives in a secured ad commercial manner. The threats associated to the cyber crime could be
mitigated completely through the help of information security, strategic planning and
administrative level operations (Frederick Rose, Hawryszkiewycz and Kang 2014). Both the
strategic planning and the administrative operations are managed by the information security
model developed by Woolworths Limited.
3. Laws and ethical consideration needed for improving the management
system of Woolworths Limited
3.1 Contingency plan
After analyzing the current status of Woolworths Limited it has been found, that the
company fails to adopt all the security aspects therefore in order to mitigate the issues it is
necessary to make proper contingency planning (Sah et al. 2014). The steps those have been
undertaken by Woolworths Limited are as follows:
In order identify the material risks of the company, appropriate risk management
planning are required to be adopted (Akbar and Ahsan 2014). It helps to reduce the material
business risks from the core management system of the business organization.
The administrative adequacy and the unit risk management plans should be incorporated
for developing the financial statement and accounting policies of Woolworth Limited.

8STRATEGIC INFORMATION SECURITY
The company should monitor the effectiveness of the policies and practices such as law,
regulation and accounting those are related to the compliances (vom Brocke et al. 2014).
The standards those are affecting the operation of the business organization that impact
the key changes are required to be monitored by the management authority of the business
organization.
Apart from this a continuous business improvement plan is required to be incorporated to
combat the security related issues of Woolworths Limited.
3.2 Role of decision making in Woolworths Limited
In order to grab more number of consumers from the competitive market it is necessary
for Woolworths Limited to develop proper mission, vision and strategy. The main aim of the
company is to gain measurable revenue from the competitive market through serving quality
products and services as well for the consumers (Ploesser 2013). The goal of the company is to
increase their brand value throughout Australia and to give proper security to the data server of
the company. Appropriate decision making is very much helpful for any business organization. It
helps to build store led customer culture and customer builds team. It helps to generate
sustainable sales in food. The business portfolio could be empowered through delivering
different range of strategies to the stakeholders (Atapattu and Sedera 2014). In order to serve
system excellence for the consumer’s end to end process is required to be implemented by the
management authority of Woolworths Limited.
The company should monitor the effectiveness of the policies and practices such as law,
regulation and accounting those are related to the compliances (vom Brocke et al. 2014).
The standards those are affecting the operation of the business organization that impact
the key changes are required to be monitored by the management authority of the business
organization.
Apart from this a continuous business improvement plan is required to be incorporated to
combat the security related issues of Woolworths Limited.
3.2 Role of decision making in Woolworths Limited
In order to grab more number of consumers from the competitive market it is necessary
for Woolworths Limited to develop proper mission, vision and strategy. The main aim of the
company is to gain measurable revenue from the competitive market through serving quality
products and services as well for the consumers (Ploesser 2013). The goal of the company is to
increase their brand value throughout Australia and to give proper security to the data server of
the company. Appropriate decision making is very much helpful for any business organization. It
helps to build store led customer culture and customer builds team. It helps to generate
sustainable sales in food. The business portfolio could be empowered through delivering
different range of strategies to the stakeholders (Atapattu and Sedera 2014). In order to serve
system excellence for the consumer’s end to end process is required to be implemented by the
management authority of Woolworths Limited.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION SECURITY
Figure 2: Focused strategy of Woolworths Limited
(Source: Recker and Rosemann 2015, pp-35)
4. Enterprise security policies
Enterprise security policy helps to handle the demand for mobile access within the
organizational network. The structures of security policy developed for Woolworth limited are
very much beneficial consumers and business perspectives (Malsbender et al. 2013). The
security policies developed for Woolworths Limited are as follows:
Technical policy: With the help of technical policies the responsibilities of security staffs
could be defined easily. Each and every forms of electric communication, remote communication
network policies could be served with the help of technical policies.
Figure 2: Focused strategy of Woolworths Limited
(Source: Recker and Rosemann 2015, pp-35)
4. Enterprise security policies
Enterprise security policy helps to handle the demand for mobile access within the
organizational network. The structures of security policy developed for Woolworth limited are
very much beneficial consumers and business perspectives (Malsbender et al. 2013). The
security policies developed for Woolworths Limited are as follows:
Technical policy: With the help of technical policies the responsibilities of security staffs
could be defined easily. Each and every forms of electric communication, remote communication
network policies could be served with the help of technical policies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION SECURITY
End user policy: The technical terms related to Woolworths Limited could be properly
served with the end user policy (Mertens et al. 2016). It helps to deliver the effective outcome
and structured revenue to the business organization.
Tying the policies together: All the policies should have to be collaborated together to
meet the requirement of the consumers by serving quality products to the consumers.
5. Information security issues
5.1 Information security issues associated to Woolworths Limited
Different Information Security issues are identified for Woolworths Limited and those
are as follows:
1. Social and cyber crime
2. DDOS attack
3. Malware explosion
4. External threats
5.2 Strategic information security issue mitigation planning for Woolworths
Installation of antivirus for securing the company application software: In order to keep
the Information System secured from their external attackers it is necessary for Woolworths
Limited to use proper antivirus software so that only the authenticated users could be able to
access information from the server. The external attackers will not be able to attack the storage
with virus and malware. The company required to connect their devices with up to date antivirus
software. The antivirus is required to be active all time and on a regular basis that is needed to be
configured in an organized manner. The downloaded files and all the removable media should be
End user policy: The technical terms related to Woolworths Limited could be properly
served with the end user policy (Mertens et al. 2016). It helps to deliver the effective outcome
and structured revenue to the business organization.
Tying the policies together: All the policies should have to be collaborated together to
meet the requirement of the consumers by serving quality products to the consumers.
5. Information security issues
5.1 Information security issues associated to Woolworths Limited
Different Information Security issues are identified for Woolworths Limited and those
are as follows:
1. Social and cyber crime
2. DDOS attack
3. Malware explosion
4. External threats
5.2 Strategic information security issue mitigation planning for Woolworths
Installation of antivirus for securing the company application software: In order to keep
the Information System secured from their external attackers it is necessary for Woolworths
Limited to use proper antivirus software so that only the authenticated users could be able to
access information from the server. The external attackers will not be able to attack the storage
with virus and malware. The company required to connect their devices with up to date antivirus
software. The antivirus is required to be active all time and on a regular basis that is needed to be
configured in an organized manner. The downloaded files and all the removable media should be

11STRATEGIC INFORMATION SECURITY
scanned automatically with the help of the software. Woolworths Limited should contact to the
help desk department regarding the security. The mitigation strategies are as follows:
Encryption: Encryption technology is required to be adopted by the business
organization to keep the information safe from the external attackers (Scott and Walker 2017).
Additionally, during the money transaction and online payment processing period the
transmission channel is also required to be encrypted properly with keys.
Authentication: With the help of authentication only the authorized users will be able to
access data from the server and none of the unauthenticated users will be able to access
information.
6. Information security management policies developed for Woolworths
Limited
Security education: Proper security education classes are required to be arranged by the
management authority to let the employees much about the digitized security policies.
Security training: Training and development programs should be arranged by the
management authority to improve the existing security of the company (Recker and Rosemann
2015).
Security awareness: Security awareness should be implemented to get structured
revenue from the competitive marketplace.
scanned automatically with the help of the software. Woolworths Limited should contact to the
help desk department regarding the security. The mitigation strategies are as follows:
Encryption: Encryption technology is required to be adopted by the business
organization to keep the information safe from the external attackers (Scott and Walker 2017).
Additionally, during the money transaction and online payment processing period the
transmission channel is also required to be encrypted properly with keys.
Authentication: With the help of authentication only the authorized users will be able to
access data from the server and none of the unauthenticated users will be able to access
information.
6. Information security management policies developed for Woolworths
Limited
Security education: Proper security education classes are required to be arranged by the
management authority to let the employees much about the digitized security policies.
Security training: Training and development programs should be arranged by the
management authority to improve the existing security of the company (Recker and Rosemann
2015).
Security awareness: Security awareness should be implemented to get structured
revenue from the competitive marketplace.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





