ITNET202A - Stuxnet Analysis: Enterprise Security & Risk Assessment
VerifiedAdded on 2023/06/12
|15
|2730
|224
Report
AI Summary
This report provides an in-depth analysis of the Stuxnet worm, a sophisticated cyber weapon that targeted industrial control systems, particularly those used in Iran's nuclear program. The report details Stuxnet's functionalities, including its infection methods, reconnaissance techniques, and sabotage mechanisms, emphasizing its impact on access control, identity, cryptography, and network security. It incorporates a qualitative risk analysis, examining the threats posed by Stuxnet, such as system failure, delayed advancement, and information loss. Furthermore, the report explores the application of enterprise security architecture frameworks like SABSA and TOGAF to prevent similar attacks, highlighting the importance of cohesiveness, coherence, and structured security measures. Finally, it considers the legality of Stuxnet under international law, referencing UN Charter articles and the principles of non-intervention and self-defense.

Running head: STUXNET
STUXNET
Name of the Student
Name of the University
Author note
STUXNET
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
STUXNET
Table of Contents
Introduction......................................................................................................................................2
Qualitative risk analysis...................................................................................................................4
Enterprise Security Architecture......................................................................................................6
The regulations................................................................................................................................9
Conclusion.......................................................................................................................................9
Reference:......................................................................................................................................11
STUXNET
Table of Contents
Introduction......................................................................................................................................2
Qualitative risk analysis...................................................................................................................4
Enterprise Security Architecture......................................................................................................6
The regulations................................................................................................................................9
Conclusion.......................................................................................................................................9
Reference:......................................................................................................................................11

2
STUXNET
Introduction
From the innovation of first computer-associated industrial control system devices, the
concern around the hardware and software vulnerabilities and potential security risk associate
with the devices are overwhelming. Stuxnet is a type of computer worm which infect industrial
control systems that are mainly utilized in infrastructure supporting facilities such as gas lines,
water treatment facility and power plants. This worms effects can be found in various region all
over the world, mostly in Iran, India and Indonesia. The Stuxnet warm first discovered in 2010
by security firm in a Belarus (Iasiello, 2014). The malware was designed to attack a particular
type of ICS specialty which is a nuclear plants for power or uranium enrichment. This warm has
the capability to spread through an air-gapped network by a removal disk such a thumb drives.
Industrial control systems are generally operated by assembly code on programmable logic
controllers. They are designed to work without any internet connection. To gain access over
PlCs, third parties must conduct reconnaissance(Gellman & Nakashima, 2013). However, every
PLC is designed differently, for integrates any PLC system attacker first needs ICS’s schematics.
This Schematics can also be stolen from inside by utilizing an early version of Stuxnet. Each
component of Stuxnet was implemented for specific reason and for the final goal of potentially
sabotage for the final goal of potentially sabotage for the final goal of potentially sabotaging the
ICS. Attackers create a mirror environment of the ICS hardware such as DLCs to test their code.
For infect the target ICS, removal disks are used to directly by some unknown third party such as
contractor who perhaps has the access over ICS. When Stuxnet infected in a system its spread in
search of field all over the organization. When stuxnet has the access over the target computer
it’s modify the PLC code which sabotage the whole system. The massive piece of malware
secretly mapped and monitored Iran’s computer networks, sending back a steady stream of
STUXNET
Introduction
From the innovation of first computer-associated industrial control system devices, the
concern around the hardware and software vulnerabilities and potential security risk associate
with the devices are overwhelming. Stuxnet is a type of computer worm which infect industrial
control systems that are mainly utilized in infrastructure supporting facilities such as gas lines,
water treatment facility and power plants. This worms effects can be found in various region all
over the world, mostly in Iran, India and Indonesia. The Stuxnet warm first discovered in 2010
by security firm in a Belarus (Iasiello, 2014). The malware was designed to attack a particular
type of ICS specialty which is a nuclear plants for power or uranium enrichment. This warm has
the capability to spread through an air-gapped network by a removal disk such a thumb drives.
Industrial control systems are generally operated by assembly code on programmable logic
controllers. They are designed to work without any internet connection. To gain access over
PlCs, third parties must conduct reconnaissance(Gellman & Nakashima, 2013). However, every
PLC is designed differently, for integrates any PLC system attacker first needs ICS’s schematics.
This Schematics can also be stolen from inside by utilizing an early version of Stuxnet. Each
component of Stuxnet was implemented for specific reason and for the final goal of potentially
sabotage for the final goal of potentially sabotage for the final goal of potentially sabotaging the
ICS. Attackers create a mirror environment of the ICS hardware such as DLCs to test their code.
For infect the target ICS, removal disks are used to directly by some unknown third party such as
contractor who perhaps has the access over ICS. When Stuxnet infected in a system its spread in
search of field all over the organization. When stuxnet has the access over the target computer
it’s modify the PLC code which sabotage the whole system. The massive piece of malware
secretly mapped and monitored Iran’s computer networks, sending back a steady stream of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
STUXNET
intelligence to prepare for a cyber-warfare campaign, according to the officials. The effort,
involving the National Security Agency, the CIA and Israel’s military, has included the use of
destructive software such as the Stuxnet virus to cause malfunctions in Iran’s nuclear enrichment
equipment (Singer, 2015). This malicious malware attacks in three phases. Firstly, it infect the
windows networks and system and make multiple replicate of itself. Then it search for out
Siemens Step7 software, which is also Windows-based and used to program industrial control
systems that operate equipment, such as centrifuges. Finally, it compromised the programmable
logic controllers.
1. Infection
Stuxnet infect system via an USB
device and proceeds to infect all
machines running Microsoft
Windows. By brandishing a digital
certificate that seems to show that it
comes from a reliable company, the
worm is able to evade automated-
detection systems.
2. Search
Stuxnet then checks whether a
given machine is part of the
targeted industrial control system
made by seimens. Such systems are
deployed in Iran to run high-speed
centrifuges that help to enrich
nuclear fuel.
3. Update
If the system is not a
target. Stuxnet is
unable to do any
damage. It will try to
access the internet to
download a more
recent version of itself.
STUXNET
intelligence to prepare for a cyber-warfare campaign, according to the officials. The effort,
involving the National Security Agency, the CIA and Israel’s military, has included the use of
destructive software such as the Stuxnet virus to cause malfunctions in Iran’s nuclear enrichment
equipment (Singer, 2015). This malicious malware attacks in three phases. Firstly, it infect the
windows networks and system and make multiple replicate of itself. Then it search for out
Siemens Step7 software, which is also Windows-based and used to program industrial control
systems that operate equipment, such as centrifuges. Finally, it compromised the programmable
logic controllers.
1. Infection
Stuxnet infect system via an USB
device and proceeds to infect all
machines running Microsoft
Windows. By brandishing a digital
certificate that seems to show that it
comes from a reliable company, the
worm is able to evade automated-
detection systems.
2. Search
Stuxnet then checks whether a
given machine is part of the
targeted industrial control system
made by seimens. Such systems are
deployed in Iran to run high-speed
centrifuges that help to enrich
nuclear fuel.
3. Update
If the system is not a
target. Stuxnet is
unable to do any
damage. It will try to
access the internet to
download a more
recent version of itself.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
STUXNET
Qualitative risk analysis
The approach of qualitative risk analysis is applied to study in-depth of the collect
data that would help to understand the event and the risk associate with the attack.
According to some new research by cyber security firm, the Stuxnet was built to inflated
target uranium enrichment equipment utilized to fuel Tehran’s controversial nuclear
Program. At begging stage, it changes the revolution speed in a grammatical manner
from 1410 Hz to 2 Hz and then 1046 Hz. That effects the systems functionality by
modifying the output frequency and sabotages the automation system. Apparently meant
to damage centrifuges at a uranium enrichment facility in Iran, Stuxnet now illustrates the
potential complexities and dangers of cyberwar (Watkins, 2014). Iran is developing
nuclear weapon from 1970 and since then there are multiple reports have accused that
Iran is trying to develop an advance and productive mass destruction weapons. However,
4. Compromise
The malware then
compromises the target
system logic controllers,
exploiting “zero day”
vulnerabilities software
weakness that have not been
identified by security
experts.
5. Control
In the startup, stuxnet spies
on the operations of the
targeted system. Then it uses
the information it has
gathered to take control of
the centrifuges, making them
spin themselves to failure.
6. Deceive and Destroy
Meanwhile, it delivers false
feedback to outside
controllers, ensuring that
authorities would not know
about vulnerabilities until it
is too late.
STUXNET
Qualitative risk analysis
The approach of qualitative risk analysis is applied to study in-depth of the collect
data that would help to understand the event and the risk associate with the attack.
According to some new research by cyber security firm, the Stuxnet was built to inflated
target uranium enrichment equipment utilized to fuel Tehran’s controversial nuclear
Program. At begging stage, it changes the revolution speed in a grammatical manner
from 1410 Hz to 2 Hz and then 1046 Hz. That effects the systems functionality by
modifying the output frequency and sabotages the automation system. Apparently meant
to damage centrifuges at a uranium enrichment facility in Iran, Stuxnet now illustrates the
potential complexities and dangers of cyberwar (Watkins, 2014). Iran is developing
nuclear weapon from 1970 and since then there are multiple reports have accused that
Iran is trying to develop an advance and productive mass destruction weapons. However,
4. Compromise
The malware then
compromises the target
system logic controllers,
exploiting “zero day”
vulnerabilities software
weakness that have not been
identified by security
experts.
5. Control
In the startup, stuxnet spies
on the operations of the
targeted system. Then it uses
the information it has
gathered to take control of
the centrifuges, making them
spin themselves to failure.
6. Deceive and Destroy
Meanwhile, it delivers false
feedback to outside
controllers, ensuring that
authorities would not know
about vulnerabilities until it
is too late.
5
STUXNET
there is no solid evidence THAT Iran is associate with this activities. Many countries
tried to uncover the truth by pressuring their authorities. On the other hand, Iran claims
that they are following the arms control agreements and justified each new discovery by
refereeing to the developing of a peaceful nation. The suspicions against Iran nuclear
weapon program is gradually increasing. The nuclear program has been exposed by
several destructive and advanced attempt such as Stuxnet (Guitton& Korzak, 2013). It
was designed to attacks a certain target software which is responsible for regulate the
speed of centrifuges in the enrichment program. The cyber worm infect the software
system command the equipment to speed in a destructive manner that destroys the
centrifuges. The main aim of the Stuxnet was not to destroy the nuclear program rather it
was designed to delay the program. So international community can have some time to
make pressure on Iran through negotiations and sanctions. The idea was to force them
reconstruct the damage facility rather than proceed to the advance progression of the
weapons.
Threats Description
T1 The worm affect the centrifuges such corrupt associate system with a
destructive speed that could lead to system failure.
T2 The progression of the advancement is delayed.
T3 The corrupted system needs to reconstruct as needs more time and cost
investment.
T4 The system hide the actual results of Stuxnet operations.
T5 Possibility of losing secret information.
STUXNET
there is no solid evidence THAT Iran is associate with this activities. Many countries
tried to uncover the truth by pressuring their authorities. On the other hand, Iran claims
that they are following the arms control agreements and justified each new discovery by
refereeing to the developing of a peaceful nation. The suspicions against Iran nuclear
weapon program is gradually increasing. The nuclear program has been exposed by
several destructive and advanced attempt such as Stuxnet (Guitton& Korzak, 2013). It
was designed to attacks a certain target software which is responsible for regulate the
speed of centrifuges in the enrichment program. The cyber worm infect the software
system command the equipment to speed in a destructive manner that destroys the
centrifuges. The main aim of the Stuxnet was not to destroy the nuclear program rather it
was designed to delay the program. So international community can have some time to
make pressure on Iran through negotiations and sanctions. The idea was to force them
reconstruct the damage facility rather than proceed to the advance progression of the
weapons.
Threats Description
T1 The worm affect the centrifuges such corrupt associate system with a
destructive speed that could lead to system failure.
T2 The progression of the advancement is delayed.
T3 The corrupted system needs to reconstruct as needs more time and cost
investment.
T4 The system hide the actual results of Stuxnet operations.
T5 Possibility of losing secret information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
STUXNET
STUXNET
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
STUXNET
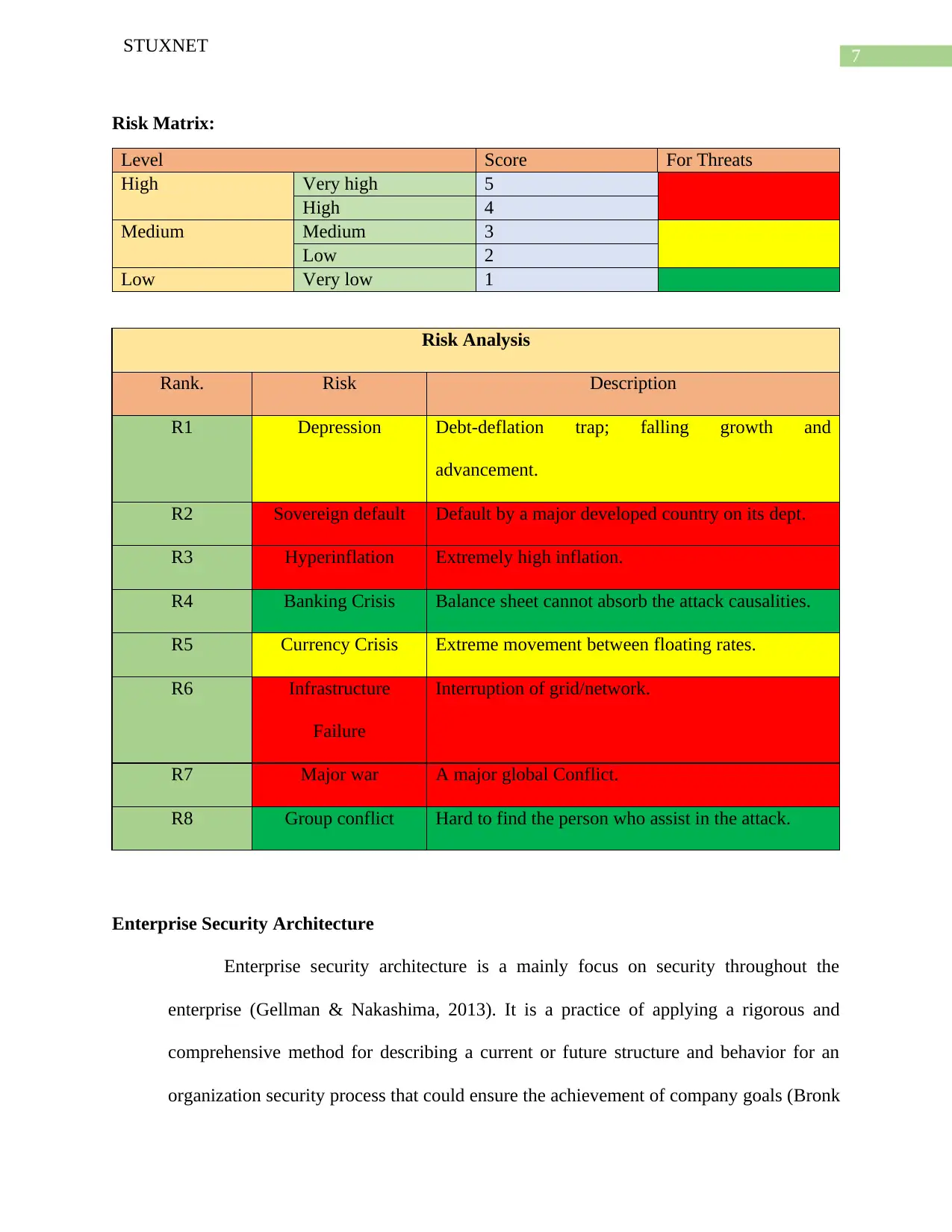
Risk Matrix:
Level Score For Threats
High Very high 5
High 4
Medium Medium 3
Low 2
Low Very low 1
Risk Analysis
Rank. Risk Description
R1 Depression Debt-deflation trap; falling growth and
advancement.
R2 Sovereign default Default by a major developed country on its dept.
R3 Hyperinflation Extremely high inflation.
R4 Banking Crisis Balance sheet cannot absorb the attack causalities.
R5 Currency Crisis Extreme movement between floating rates.
R6 Infrastructure
Failure
Interruption of grid/network.
R7 Major war A major global Conflict.
R8 Group conflict Hard to find the person who assist in the attack.
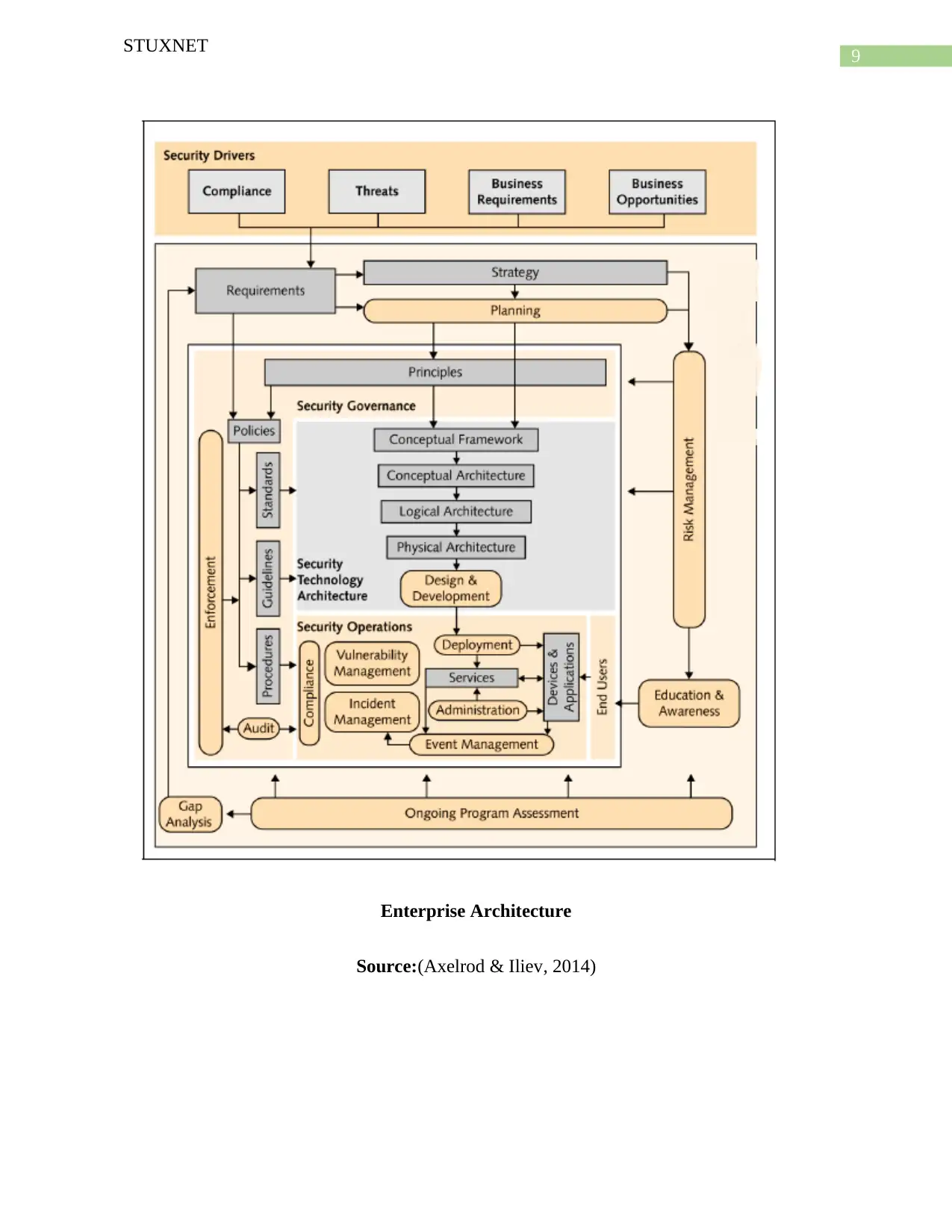
Enterprise Security Architecture
Enterprise security architecture is a mainly focus on security throughout the
enterprise (Gellman & Nakashima, 2013). It is a practice of applying a rigorous and
comprehensive method for describing a current or future structure and behavior for an
organization security process that could ensure the achievement of company goals (Bronk
STUXNET
Risk Matrix:
Level Score For Threats
High Very high 5
High 4
Medium Medium 3
Low 2
Low Very low 1
Risk Analysis
Rank. Risk Description
R1 Depression Debt-deflation trap; falling growth and
advancement.
R2 Sovereign default Default by a major developed country on its dept.
R3 Hyperinflation Extremely high inflation.
R4 Banking Crisis Balance sheet cannot absorb the attack causalities.
R5 Currency Crisis Extreme movement between floating rates.
R6 Infrastructure
Failure
Interruption of grid/network.
R7 Major war A major global Conflict.
R8 Group conflict Hard to find the person who assist in the attack.
Enterprise Security Architecture
Enterprise security architecture is a mainly focus on security throughout the
enterprise (Gellman & Nakashima, 2013). It is a practice of applying a rigorous and
comprehensive method for describing a current or future structure and behavior for an
organization security process that could ensure the achievement of company goals (Bronk

8
STUXNET
& Tikk-Ringas, 2013). It broadly relates with the security practice of business
optimization as it address the business security architecture. It has been become a
common practice among all the organization in order to achieve companies’ goals and
maintain the productivity or services.
In the case of Iran nuclear asset it can be useful to prevent attack such as Stuxnet which is
specially designed to infracted the target system. Enterprise security architecture framework such
as SABSA, TOGAF, or C4ISTAR framework can help the Iranian prevent attacks (Gellman &
Nakashima, 2013). The practice is involved in developing an architecture security framework to
describe the current security framework and align them according to the program changes. There
are certain advantages can be gain by utilizing this framework that are follows:
Deliver cohesiveness, coherence and structure.
It aligns the enterprise activities with the security.
Establish a common framework for information security within the enterprise.
This framework provides clear identification of business process and the performance
and how these are executed in the real time. It also evaluates the risks posture of the
enterprise and check the capability of the current architecture system that is associate
with the security of the organization (Bronk & Tikk-Ringas, 2013). the architecture
process are flows down into the discrete information technology component such as
organization activities, charts and process flows including the organization cycle, timing
and periods.
STUXNET
& Tikk-Ringas, 2013). It broadly relates with the security practice of business
optimization as it address the business security architecture. It has been become a
common practice among all the organization in order to achieve companies’ goals and
maintain the productivity or services.
In the case of Iran nuclear asset it can be useful to prevent attack such as Stuxnet which is
specially designed to infracted the target system. Enterprise security architecture framework such
as SABSA, TOGAF, or C4ISTAR framework can help the Iranian prevent attacks (Gellman &
Nakashima, 2013). The practice is involved in developing an architecture security framework to
describe the current security framework and align them according to the program changes. There
are certain advantages can be gain by utilizing this framework that are follows:
Deliver cohesiveness, coherence and structure.
It aligns the enterprise activities with the security.
Establish a common framework for information security within the enterprise.
This framework provides clear identification of business process and the performance
and how these are executed in the real time. It also evaluates the risks posture of the
enterprise and check the capability of the current architecture system that is associate
with the security of the organization (Bronk & Tikk-Ringas, 2013). the architecture
process are flows down into the discrete information technology component such as
organization activities, charts and process flows including the organization cycle, timing
and periods.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
STUXNET
Enterprise Architecture
Source:(Axelrod & Iliev, 2014)
STUXNET
Enterprise Architecture
Source:(Axelrod & Iliev, 2014)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
STUXNET
The regulations
UN Charter Article 2(4) and UN Charter Article 51 are set by the UN Security Council to
determine any existence of any threat that could breach the peace. The main objectives of this
article is to maintain peace by preventing war (Bronk & Tikk-Ringas, 2013). UN was
constructed mainly because the destruction of World War 2. Nowadays, this charters are still
active. According to the article 51 “Nothing in the present Charter shall impair the inherent right
of individual or collective self-defense if an armed attack occurs against a Member of the United
Nations, until the Security Council has taken measures necessary to maintain international peace
and security (Axelrod & Iliev, 2014). Measures taken by Members in the exercise of this right of
self-defense shall be immediately reported to the Security Council and shall not in any way
affect the authority and responsibility of the Security Council under the present Charter to take at
any time such action as it deems necessary in order to maintain or restore international peace and
security.” After evaluating UN charter the illegality of Stuxnet can be determined. Whether
Stuxnet is a violation of these two principles depends on whether it can be qualified as a use of
‘armed force. Stuxnet would be illegal even if it were established that Iran is in breach of the
NPT. If however Stuxnet is not considered a use of force, it would be a breach of the principle of
non-intervention, unless it amounts to a lawful countermeasure against Iran’s alleged breach of
its non-proliferation obligations (Bambauer, 2013).
Conclusion
Stuxnet is a type of computer worm which infect industrial control systems that
are mainly utilized in infrastructure supporting facilities such as gas lines, water
treatment facility and power plants. This worms effects can be found in various region all
over the world, mostly in Iran, India and Indonesia. The Stuxnet warm first discovered in
STUXNET
The regulations
UN Charter Article 2(4) and UN Charter Article 51 are set by the UN Security Council to
determine any existence of any threat that could breach the peace. The main objectives of this
article is to maintain peace by preventing war (Bronk & Tikk-Ringas, 2013). UN was
constructed mainly because the destruction of World War 2. Nowadays, this charters are still
active. According to the article 51 “Nothing in the present Charter shall impair the inherent right
of individual or collective self-defense if an armed attack occurs against a Member of the United
Nations, until the Security Council has taken measures necessary to maintain international peace
and security (Axelrod & Iliev, 2014). Measures taken by Members in the exercise of this right of
self-defense shall be immediately reported to the Security Council and shall not in any way
affect the authority and responsibility of the Security Council under the present Charter to take at
any time such action as it deems necessary in order to maintain or restore international peace and
security.” After evaluating UN charter the illegality of Stuxnet can be determined. Whether
Stuxnet is a violation of these two principles depends on whether it can be qualified as a use of
‘armed force. Stuxnet would be illegal even if it were established that Iran is in breach of the
NPT. If however Stuxnet is not considered a use of force, it would be a breach of the principle of
non-intervention, unless it amounts to a lawful countermeasure against Iran’s alleged breach of
its non-proliferation obligations (Bambauer, 2013).
Conclusion
Stuxnet is a type of computer worm which infect industrial control systems that
are mainly utilized in infrastructure supporting facilities such as gas lines, water
treatment facility and power plants. This worms effects can be found in various region all
over the world, mostly in Iran, India and Indonesia. The Stuxnet warm first discovered in

11
STUXNET
2010 by security firm in a Belarus. The malware was designed to attack a particular type
of ICS specialty which is a nuclear plants for power or uranium enrichment. This warm
has the capability to spread through an air-gapped network by a removal disk such a
thumb drives. Industrial control systems are generally operated by assembly code on
programmable logic controllers. They are designed to work without any internet
connection. To gain access over PlCs, third parties must conduct reconnaissance.
However, every PLC is designed differently, for integrates any PLC system attacker first
needs ICS’s schematics. This Schematics can also be stolen from inside by utilizing an
early version of Stuxnet. Each component of Stuxnet was implemented for specific
reason and for the final goal of potentially sabotage for the final goal of potentially
sabotage for the final goal of potentially sabotaging the ICS. Security Council has taken
measures necessary to maintain international peace and security (Axelrod & Iliev, 2014).
Measures taken by Members in the exercise of this right of self-defense shall be
immediately reported to the Security Council and shall not in any way affect the authority
and responsibility of the Security Council under the present Charter to take at any time
such action as it deems necessary in order to maintain or restore international peace and
security.” After evaluating UN charter the illegality of Stuxnet can be determined.
Whether Stuxnet is a violation of these two principles depends on whether it can be
qualified as a use of ‘armed force. Stuxnet would be illegal even if it were established
that Iran is in breach of the NPT.
STUXNET
2010 by security firm in a Belarus. The malware was designed to attack a particular type
of ICS specialty which is a nuclear plants for power or uranium enrichment. This warm
has the capability to spread through an air-gapped network by a removal disk such a
thumb drives. Industrial control systems are generally operated by assembly code on
programmable logic controllers. They are designed to work without any internet
connection. To gain access over PlCs, third parties must conduct reconnaissance.
However, every PLC is designed differently, for integrates any PLC system attacker first
needs ICS’s schematics. This Schematics can also be stolen from inside by utilizing an
early version of Stuxnet. Each component of Stuxnet was implemented for specific
reason and for the final goal of potentially sabotage for the final goal of potentially
sabotage for the final goal of potentially sabotaging the ICS. Security Council has taken
measures necessary to maintain international peace and security (Axelrod & Iliev, 2014).
Measures taken by Members in the exercise of this right of self-defense shall be
immediately reported to the Security Council and shall not in any way affect the authority
and responsibility of the Security Council under the present Charter to take at any time
such action as it deems necessary in order to maintain or restore international peace and
security.” After evaluating UN charter the illegality of Stuxnet can be determined.
Whether Stuxnet is a violation of these two principles depends on whether it can be
qualified as a use of ‘armed force. Stuxnet would be illegal even if it were established
that Iran is in breach of the NPT.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



