Assignment on Subnetting and IP Addressing - Internet Technologies
VerifiedAdded on 2022/08/26
|10
|1726
|27
Homework Assignment
AI Summary
This document presents a comprehensive solution to an assignment focused on subnetting and IP addressing within the context of Internet technologies. The assignment covers several key areas, including subnet classification and network address allocation, considering scenarios with varying numbers of hosts. It delves into IPv6 addressing, comparing global unicast, unique local, and link-local addresses with IPv4 counterparts, and discusses the role and purpose of NAT in IPv4 networks. Furthermore, the solution provides a comparative analysis of link-state and distance-vector routing protocols, evaluating their advantages and disadvantages. The assignment also assesses the efficiency of a given system and explores TCP communication, detailing sequence numbers, port numbers, and acknowledgement numbers in different segments. The document includes a bibliography of relevant sources.

Running head: SUBNETTING AND IP ADDRESSING
Subnetting and IP Addressing
Name of the Student
Name of the University
Author Note
Subnetting and IP Addressing
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SUBNETTING AND IP ADDRESSING
Table of Contents
Question 1: Subnet Classification..............................................................................................2
1.1 Network addresses for subnets of the figure....................................................................2
1.2 Subnet addresses when number of hosts between subnets A-D is 21..............................2
1.3 Network prefix advertised by R1 to public Internet.........................................................3
Question 2: IP Addressing.........................................................................................................3
2.1 Global unicast, unique local and link local IPv6 addresses and comparison with IPv4. .3
2.2 NAT and purpose of utilization with IPv4.......................................................................4
Question 3: Comparison of Link state and Distance vector routing protocols at network layer
with their advantages and disadvantages...................................................................................5
Link State Routing Protocols.................................................................................................5
Distance Vector Routing Protocols........................................................................................5
Question 4: Evaluating efficiency of system.............................................................................6
Question 5: TCP Communication..............................................................................................7
5.1 Provide sequence number, source port number and destination port number of second
segment between hosts A and B.............................................................................................7
5.2 Provide acknowledgement number, source port number and destination port number in
first arriving segment.............................................................................................................7
5.3 Provide acknowledgement number when second segment arrives first...........................7
Bibliography...............................................................................................................................8
Table of Contents
Question 1: Subnet Classification..............................................................................................2
1.1 Network addresses for subnets of the figure....................................................................2
1.2 Subnet addresses when number of hosts between subnets A-D is 21..............................2
1.3 Network prefix advertised by R1 to public Internet.........................................................3
Question 2: IP Addressing.........................................................................................................3
2.1 Global unicast, unique local and link local IPv6 addresses and comparison with IPv4. .3
2.2 NAT and purpose of utilization with IPv4.......................................................................4
Question 3: Comparison of Link state and Distance vector routing protocols at network layer
with their advantages and disadvantages...................................................................................5
Link State Routing Protocols.................................................................................................5
Distance Vector Routing Protocols........................................................................................5
Question 4: Evaluating efficiency of system.............................................................................6
Question 5: TCP Communication..............................................................................................7
5.1 Provide sequence number, source port number and destination port number of second
segment between hosts A and B.............................................................................................7
5.2 Provide acknowledgement number, source port number and destination port number in
first arriving segment.............................................................................................................7
5.3 Provide acknowledgement number when second segment arrives first...........................7
Bibliography...............................................................................................................................8
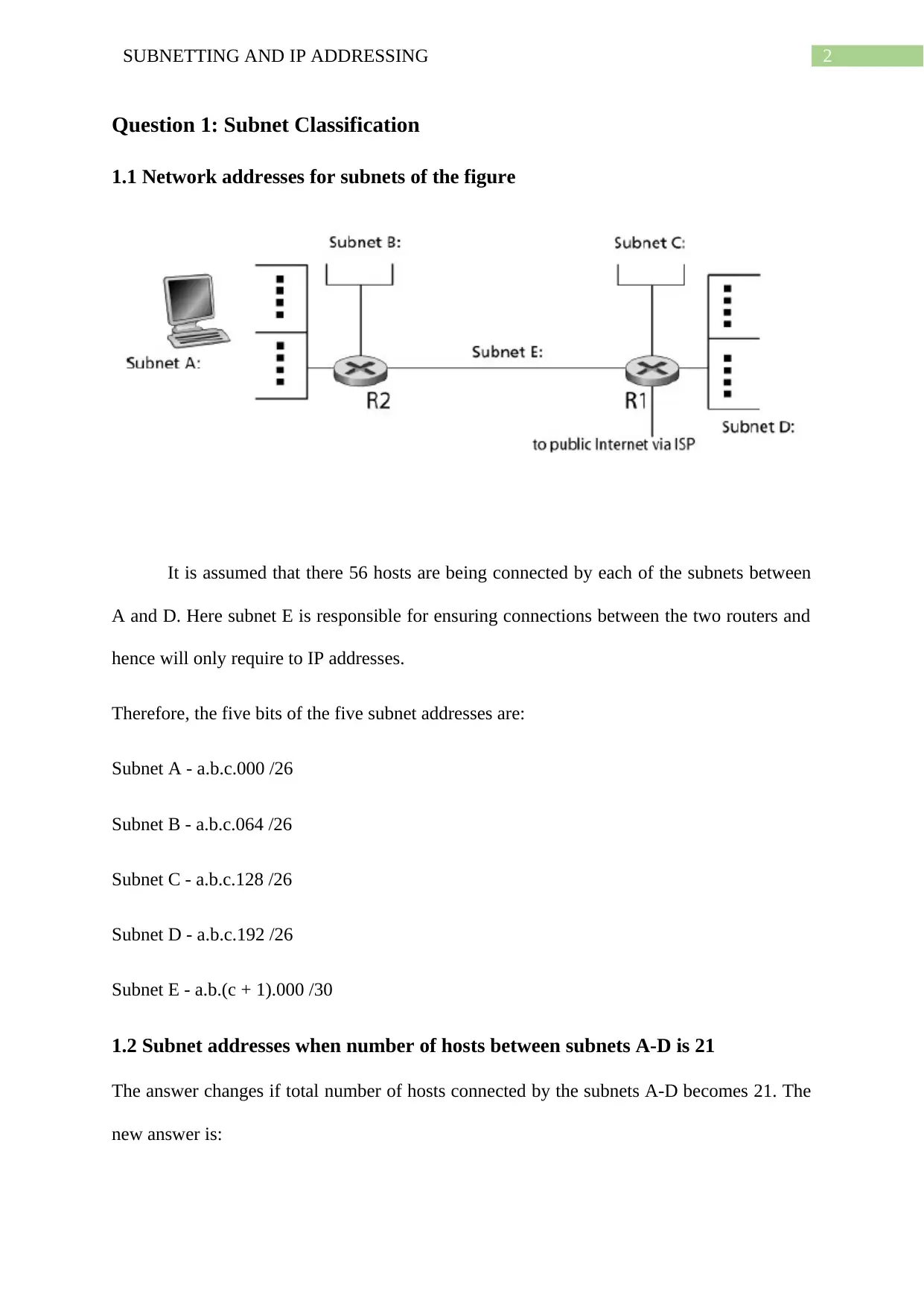
2SUBNETTING AND IP ADDRESSING
Question 1: Subnet Classification
1.1 Network addresses for subnets of the figure
It is assumed that there 56 hosts are being connected by each of the subnets between
A and D. Here subnet E is responsible for ensuring connections between the two routers and
hence will only require to IP addresses.
Therefore, the five bits of the five subnet addresses are:
Subnet A - a.b.c.000 /26
Subnet B - a.b.c.064 /26
Subnet C - a.b.c.128 /26
Subnet D - a.b.c.192 /26
Subnet E - a.b.(c + 1).000 /30
1.2 Subnet addresses when number of hosts between subnets A-D is 21
The answer changes if total number of hosts connected by the subnets A-D becomes 21. The
new answer is:
Question 1: Subnet Classification
1.1 Network addresses for subnets of the figure
It is assumed that there 56 hosts are being connected by each of the subnets between
A and D. Here subnet E is responsible for ensuring connections between the two routers and
hence will only require to IP addresses.
Therefore, the five bits of the five subnet addresses are:
Subnet A - a.b.c.000 /26
Subnet B - a.b.c.064 /26
Subnet C - a.b.c.128 /26
Subnet D - a.b.c.192 /26
Subnet E - a.b.(c + 1).000 /30
1.2 Subnet addresses when number of hosts between subnets A-D is 21
The answer changes if total number of hosts connected by the subnets A-D becomes 21. The
new answer is:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SUBNETTING AND IP ADDRESSING
Subnet A - a.b.c.00 /26
Subnet B - a.b.c.08 /26
Subnet C - a.b.c.16 /26
Subnet D - a.b.c.24 /26
Subnet E - a.b.c.32 /30
1.3 Network prefix advertised by R1 to public Internet
The network prefix advertised by the router R1 to public internet when subnets A-D
each have 56 hosts needs to be a.b.c.0 /23 or a prefix with a higher available address space.
When the total required connections to hosts change to 21 for subnets A-D the network prefix
to be advertised by the router R1 to public internet needs to be a.b.c.0 /23 or prefixes that
offer higher available address space for allocation.
Question 2: IP Addressing
2.1 Global unicast, unique local and link local IPv6 addresses and comparison
with IPv4
The IPv6 global unicast addresses are used for identifying a particular interface in a
given node (Hossain et al., 2016). IPv6 Unicast addresses can identify only one node in the
networks and are used in one to one communication.
The IPv6 unique local addresses get used in the networks of large corporations at
various sites. These addresses have been defined in IETF RFC 4193 and gets reserved within
the range - FC00::/7. The range FC00::/7 implies that the unique local addresses start with 7
bits having a bit pattern 1111 110L.
Subnet A - a.b.c.00 /26
Subnet B - a.b.c.08 /26
Subnet C - a.b.c.16 /26
Subnet D - a.b.c.24 /26
Subnet E - a.b.c.32 /30
1.3 Network prefix advertised by R1 to public Internet
The network prefix advertised by the router R1 to public internet when subnets A-D
each have 56 hosts needs to be a.b.c.0 /23 or a prefix with a higher available address space.
When the total required connections to hosts change to 21 for subnets A-D the network prefix
to be advertised by the router R1 to public internet needs to be a.b.c.0 /23 or prefixes that
offer higher available address space for allocation.
Question 2: IP Addressing
2.1 Global unicast, unique local and link local IPv6 addresses and comparison
with IPv4
The IPv6 global unicast addresses are used for identifying a particular interface in a
given node (Hossain et al., 2016). IPv6 Unicast addresses can identify only one node in the
networks and are used in one to one communication.
The IPv6 unique local addresses get used in the networks of large corporations at
various sites. These addresses have been defined in IETF RFC 4193 and gets reserved within
the range - FC00::/7. The range FC00::/7 implies that the unique local addresses start with 7
bits having a bit pattern 1111 110L.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SUBNETTING AND IP ADDRESSING
Link local IPv6 addresses are those IPv6 addresses which start as FE in hexadecimals.
It is not possible to route these link local addresses to public networks and are only limited to
local networks. These addresses are auto-configured that is they are automatically generated
when the devices are plugged (Bahnasse et al., 2019). Comparison of IPv6 addressing with
IPv4 is given below.
IPv4 IPv6
Contains 32 bit address space. Contains an address space of 128 bits.
Header length is measured to be 20 bytes. Header length is measured at 40 bytes.
There are 12 header fields. There are only 8 header fields.
The header section of every address is 4. The header section of every address is 8.
Network security based on IPsec is optional. Network security based on IPsec is
mandatoy.
2.2 NAT and purpose of utilization with IPv4
There are several uses of NAT, though it is mainly used in conserving the public IPv4
addresses. This is done by permitting the networks in using private IPv4 addresses in the
internal network and translating them to public addresses when accessing the outside
networks.
Since NAT provides translation of public addresses to private addresses, it is possible
for in the internet to make efficient use of the IPv4 address spaces otherwise the address
space would have been exhausted a long time ago.
Link local IPv6 addresses are those IPv6 addresses which start as FE in hexadecimals.
It is not possible to route these link local addresses to public networks and are only limited to
local networks. These addresses are auto-configured that is they are automatically generated
when the devices are plugged (Bahnasse et al., 2019). Comparison of IPv6 addressing with
IPv4 is given below.
IPv4 IPv6
Contains 32 bit address space. Contains an address space of 128 bits.
Header length is measured to be 20 bytes. Header length is measured at 40 bytes.
There are 12 header fields. There are only 8 header fields.
The header section of every address is 4. The header section of every address is 8.
Network security based on IPsec is optional. Network security based on IPsec is
mandatoy.
2.2 NAT and purpose of utilization with IPv4
There are several uses of NAT, though it is mainly used in conserving the public IPv4
addresses. This is done by permitting the networks in using private IPv4 addresses in the
internal network and translating them to public addresses when accessing the outside
networks.
Since NAT provides translation of public addresses to private addresses, it is possible
for in the internet to make efficient use of the IPv4 address spaces otherwise the address
space would have been exhausted a long time ago.
5SUBNETTING AND IP ADDRESSING
Question 3: Comparison of Link state and Distance vector routing
protocols at network layer with their advantages and disadvantages
Link State Routing Protocols
Link state routing protocols ensure that complete road of the network gets maintained
in each router which runs a link state routing protocol. Link state routing always make
attempts in maintaining the full network topology while also making updates with every
change in network. While doing so each of the routers individually calculate the shortest path
to reach the destination networks with Shortest Path First (SPF) algorithms like the Dijkstra’s
algorithm (Yi & Parrein, 2017). The benefits and drawbacks are given below.
Advantages Disadvantages
Link state protocols evaluate cost metrics in
determining shortest paths.
Require more processing and memory
resources than distance vector protocols.
Each router stores complete picture of the
network.
They need administrators who have
thorough understanding of such protocols.
Link-state protocols support CIDR and
VLSM.
Initially networks re flooded with LSAs in
the discovery process and can hamper data
transmission.
Database size of the link state routing can be
minimized with careful and efficient
network design.
Strictly requires hierarchical network design
for smaller network segmentations thereby
reducing the size of topology tables.
Distance Vector Routing Protocols
Distance vector protocols refer to the simplest routing protocols that use distance and
direction or vector for finding paths to the destination (Daggitt & Griffin, 2018). Here,
Question 3: Comparison of Link state and Distance vector routing
protocols at network layer with their advantages and disadvantages
Link State Routing Protocols
Link state routing protocols ensure that complete road of the network gets maintained
in each router which runs a link state routing protocol. Link state routing always make
attempts in maintaining the full network topology while also making updates with every
change in network. While doing so each of the routers individually calculate the shortest path
to reach the destination networks with Shortest Path First (SPF) algorithms like the Dijkstra’s
algorithm (Yi & Parrein, 2017). The benefits and drawbacks are given below.
Advantages Disadvantages
Link state protocols evaluate cost metrics in
determining shortest paths.
Require more processing and memory
resources than distance vector protocols.
Each router stores complete picture of the
network.
They need administrators who have
thorough understanding of such protocols.
Link-state protocols support CIDR and
VLSM.
Initially networks re flooded with LSAs in
the discovery process and can hamper data
transmission.
Database size of the link state routing can be
minimized with careful and efficient
network design.
Strictly requires hierarchical network design
for smaller network segmentations thereby
reducing the size of topology tables.
Distance Vector Routing Protocols
Distance vector protocols refer to the simplest routing protocols that use distance and
direction or vector for finding paths to the destination (Daggitt & Griffin, 2018). Here,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SUBNETTING AND IP ADDRESSING
routers running a distance vector routing protocol informs the neighbours regarding the
periodic changes to the network topology by means of limited broadcasts and destination IP
address as 255.255.255.255. These protocols make use of the Bellman-Ford algorithm to find
the optimal paths. The advantages and disadvantages are:
Advantages Disadvantages
Stable and time tested routing method. Susceptible to routing loops.
Comparatively easier to implement and
manage.
Takes longer time to reach destination
compared to other routing methods.
Minimal bandwidth impact for usual LAN
networks.
Bandwidth requirements increase
significantly for WAN and complex LAN
environments.
Needs the least hardware and processing
resources compared to other routing
methods.
Routers need to recalculate the routing
tables prior to forwarding the changes.
Question 4: Evaluating efficiency of system
Message length = 120 byte
15-byte header at 4 layers (5, 4, 3 and 2)
Therefore header size in four layers = (15 * 4) = 60 bytes
Total efficiency = 120/(120 + 60) * 100 = 66.67%
routers running a distance vector routing protocol informs the neighbours regarding the
periodic changes to the network topology by means of limited broadcasts and destination IP
address as 255.255.255.255. These protocols make use of the Bellman-Ford algorithm to find
the optimal paths. The advantages and disadvantages are:
Advantages Disadvantages
Stable and time tested routing method. Susceptible to routing loops.
Comparatively easier to implement and
manage.
Takes longer time to reach destination
compared to other routing methods.
Minimal bandwidth impact for usual LAN
networks.
Bandwidth requirements increase
significantly for WAN and complex LAN
environments.
Needs the least hardware and processing
resources compared to other routing
methods.
Routers need to recalculate the routing
tables prior to forwarding the changes.
Question 4: Evaluating efficiency of system
Message length = 120 byte
15-byte header at 4 layers (5, 4, 3 and 2)
Therefore header size in four layers = (15 * 4) = 60 bytes
Total efficiency = 120/(120 + 60) * 100 = 66.67%
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SUBNETTING AND IP ADDRESSING
Question 5: TCP Communication
5.1 Provide sequence number, source port number and destination port number
of second segment between hosts A and B.
Sequence number (second segment) = first segment sequence number + destination port
number
= 105 + 80
= 185
So, sequence number = 185
Source port number = 500
Destination port number = 80
5.2 Provide acknowledgement number, source port number and destination port
number in first arriving segment.
Acknowledgement number = 186
Source port number = 80
Destination port number= 500
5.3 Provide acknowledgement number when second segment arrives first
Acknowledgement number = 106
Question 5: TCP Communication
5.1 Provide sequence number, source port number and destination port number
of second segment between hosts A and B.
Sequence number (second segment) = first segment sequence number + destination port
number
= 105 + 80
= 185
So, sequence number = 185
Source port number = 500
Destination port number = 80
5.2 Provide acknowledgement number, source port number and destination port
number in first arriving segment.
Acknowledgement number = 186
Source port number = 80
Destination port number= 500
5.3 Provide acknowledgement number when second segment arrives first
Acknowledgement number = 106

8SUBNETTING AND IP ADDRESSING
Bibliography
Bahnasse, A., Bensalah, F., Louhab, F. E., Khiat, A., Khiat, Y., & Talea, M. (2019).
Automation of network simulation: concepts related to IPv4 and IPv6
convergence. Procedia Computer Science, 155, 456-461.
https://doi.org/10.1016/j.procs.2019.08.063
Daggitt, M. L., & Griffin, T. G. (2018, September). Rate of convergence of increasing path-
vector routing protocols. In 2018 IEEE 26th International Conference on Network
Protocols (ICNP) (pp. 335-345). IEEE. https://doi.org/10.1109/ICNP.2018.00049
Grailet, J. F., Tarissan, F., & Donnet, B. (2016). TreeNET: Discovering and connecting
subnets. In 8th International Workshop on Traffic Monitoring and Analysis (TMA).
Available at https://orbi.uliege.be/bitstream/2268/194693/1/paper.pdf
Hossain, M. A., Printder, D., Jahan, S., & Hussain, M. (2016). Performance analysis of three
transition mechanisms between IPv6 network and IPv4 network: dual stack tunneling
and translation. International Journal of Computer, 20(1), 217-228. Available at
https://www.researchgate.net/publication/302468792
Lehman, V., Hoque, A. M., Yu, Y., Wang, L., Zhang, B., & Zhang, L. (2016). A secure link
state routing protocol for NDN. Tech. Rep. NDN-0037. Available at http://named-
data.net/wp-content/uploads/2016/01/ndn-0037-1-nlsr.pdf
Rula, J. P., Bustamante, F. E., & Steiner, M. (2017, November). Cell spotting: studying the
role of cellular networks in the internet. In Proceedings of the 2017 Internet
Measurement Conference (pp. 191-204). ACM.
https://doi.org/10.1145/3131365.3131402
Bibliography
Bahnasse, A., Bensalah, F., Louhab, F. E., Khiat, A., Khiat, Y., & Talea, M. (2019).
Automation of network simulation: concepts related to IPv4 and IPv6
convergence. Procedia Computer Science, 155, 456-461.
https://doi.org/10.1016/j.procs.2019.08.063
Daggitt, M. L., & Griffin, T. G. (2018, September). Rate of convergence of increasing path-
vector routing protocols. In 2018 IEEE 26th International Conference on Network
Protocols (ICNP) (pp. 335-345). IEEE. https://doi.org/10.1109/ICNP.2018.00049
Grailet, J. F., Tarissan, F., & Donnet, B. (2016). TreeNET: Discovering and connecting
subnets. In 8th International Workshop on Traffic Monitoring and Analysis (TMA).
Available at https://orbi.uliege.be/bitstream/2268/194693/1/paper.pdf
Hossain, M. A., Printder, D., Jahan, S., & Hussain, M. (2016). Performance analysis of three
transition mechanisms between IPv6 network and IPv4 network: dual stack tunneling
and translation. International Journal of Computer, 20(1), 217-228. Available at
https://www.researchgate.net/publication/302468792
Lehman, V., Hoque, A. M., Yu, Y., Wang, L., Zhang, B., & Zhang, L. (2016). A secure link
state routing protocol for NDN. Tech. Rep. NDN-0037. Available at http://named-
data.net/wp-content/uploads/2016/01/ndn-0037-1-nlsr.pdf
Rula, J. P., Bustamante, F. E., & Steiner, M. (2017, November). Cell spotting: studying the
role of cellular networks in the internet. In Proceedings of the 2017 Internet
Measurement Conference (pp. 191-204). ACM.
https://doi.org/10.1145/3131365.3131402
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SUBNETTING AND IP ADDRESSING
Swidan, A., Abdelghany, H. B., Saifan, R., & Zilic, Z. (2016). Mobility and direction aware
ad-hoc on demand distance vector routing protocol. Procedia Computer Science, 94,
49-56. https://doi.org/10.1016/j.procs.2016.08.011
Yi, J., & Parrein, B. (2017). Multipath Extension for the Optimized Link State Routing
Protocol Version 2 (OLSRv2). Available at https://hal.archives-ouvertes.fr/hal-
01705335/document
Swidan, A., Abdelghany, H. B., Saifan, R., & Zilic, Z. (2016). Mobility and direction aware
ad-hoc on demand distance vector routing protocol. Procedia Computer Science, 94,
49-56. https://doi.org/10.1016/j.procs.2016.08.011
Yi, J., & Parrein, B. (2017). Multipath Extension for the Optimized Link State Routing
Protocol Version 2 (OLSRv2). Available at https://hal.archives-ouvertes.fr/hal-
01705335/document
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





