Switching Engineering Report: Network Design and Security Analysis
VerifiedAdded on 2020/05/03
|23
|2840
|398
Report
AI Summary
This report provides a comprehensive investigation into switching engineering, addressing various aspects of network design and security for a creative consultancy organization. It begins with an introduction to internetwork concepts, including hubs, switches, and bridges, and then delves into the core principles of LAN switching. The report explores switching concepts, categorizing switches as connectionless or connection-oriented and distinguishing between Layer 2 and Layer 3 switches. A significant portion of the report is dedicated to network security, discussing concepts like authentication and common threats such as worms and DoS attacks. The report also examines VLAN attacks, including VLAN hopping and ARP poisoning. The report then transitions to Ethernet switching, detailing its applications, design, and the differences between Layer 2 and Layer 3 switching. The report concludes with a brief overview of wireless LAN switching, including its architecture and traffic management. The network design includes separate VLANs for different departments, connected by routers, and utilizes Cisco products. The report includes network, switch, and PC configurations, and a Cisco Packet Tracer file is likely included to demonstrate the network setup.

SWITCHING ENGINEERING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................3
Task - 1 LAN Switching Investigation........................................................................................................3
1. Internetwork Concepts.....................................................................................................................3
2. Switching Concepts.........................................................................................................................4
3. Basic Switch Configuration.............................................................................................................5
Task - 2 Design and Investigate the Switching Security..............................................................................5
1. Concepts of Network Security.........................................................................................................5
2. VLAN Attacks.................................................................................................................................6
3. Random Frame Stress Attacks.........................................................................................................6
Task - 3 Network Design for Ethernet Switching........................................................................................7
1. Ethernet Switching..........................................................................................................................7
2. Difference between Layer 2 and Layer 3 Switching........................................................................7
3. Ethernet Switching Industrial Application.......................................................................................7
4. Ethernet Switch Network Design.....................................................................................................7
Task - 4 Wireless LAN Switching Investigation.........................................................................................7
1. Wireless Switching Works...............................................................................................................7
2. WLAN switching Architecture........................................................................................................7
3. Wireless Traffics..............................................................................................................................7
4. Wireless Management and Monitoring............................................................................................7
Conclusion...................................................................................................................................................7
References...................................................................................................................................................7
2
Introduction.................................................................................................................................................3
Task - 1 LAN Switching Investigation........................................................................................................3
1. Internetwork Concepts.....................................................................................................................3
2. Switching Concepts.........................................................................................................................4
3. Basic Switch Configuration.............................................................................................................5
Task - 2 Design and Investigate the Switching Security..............................................................................5
1. Concepts of Network Security.........................................................................................................5
2. VLAN Attacks.................................................................................................................................6
3. Random Frame Stress Attacks.........................................................................................................6
Task - 3 Network Design for Ethernet Switching........................................................................................7
1. Ethernet Switching..........................................................................................................................7
2. Difference between Layer 2 and Layer 3 Switching........................................................................7
3. Ethernet Switching Industrial Application.......................................................................................7
4. Ethernet Switch Network Design.....................................................................................................7
Task - 4 Wireless LAN Switching Investigation.........................................................................................7
1. Wireless Switching Works...............................................................................................................7
2. WLAN switching Architecture........................................................................................................7
3. Wireless Traffics..............................................................................................................................7
4. Wireless Management and Monitoring............................................................................................7
Conclusion...................................................................................................................................................7
References...................................................................................................................................................7
2

Introduction
The Creative consultancy organization decided to create the network connection. The
organization has four building or department such as finance, admin, research and accounts. The
organization needs to create a separate VLAN for each building. It is also interested to create the
effective network connection for the organization. So, the network team will investigate the LAN
switching, Ethernet switching and Wireless LAN switching. The team also investigates the
network security to provide the secured network connection for organizations. The proposed
network must provide the effectiveness and scalability.
Task - 1 LAN Switching Investigation
1. Internetwork Concepts
The collection of individual networks is known as internetwork as it is connected by the
intermediate networking devices. In single large network, the internetworking uses the functions
tointerconnectother network devices. It must meet the challenges of administrating and creating
the internetwork. The internetworking has various challenges such as implementation of the
functional internetwork and it establishes the effective and efficient internetwork. It must face
the areas of connectivity, flexibility, reliability and network management. The internetworking
supports the communication between the disparate technologies. In network management, the
internetwork must be provide the centralized support and troubleshooting capabilities.
Most common internetworking devices are listed below.
Hubs
Switches
Bridges
Hubs
Hubs are used for connecting the multiple Ethernet devices. It performs functions as a
single unit. The hubs are used for controlling the media access by utilizes the carried sense
multiple access with collision detection. The hubs operates at half duplex mode.
3
The Creative consultancy organization decided to create the network connection. The
organization has four building or department such as finance, admin, research and accounts. The
organization needs to create a separate VLAN for each building. It is also interested to create the
effective network connection for the organization. So, the network team will investigate the LAN
switching, Ethernet switching and Wireless LAN switching. The team also investigates the
network security to provide the secured network connection for organizations. The proposed
network must provide the effectiveness and scalability.
Task - 1 LAN Switching Investigation
1. Internetwork Concepts
The collection of individual networks is known as internetwork as it is connected by the
intermediate networking devices. In single large network, the internetworking uses the functions
tointerconnectother network devices. It must meet the challenges of administrating and creating
the internetwork. The internetworking has various challenges such as implementation of the
functional internetwork and it establishes the effective and efficient internetwork. It must face
the areas of connectivity, flexibility, reliability and network management. The internetworking
supports the communication between the disparate technologies. In network management, the
internetwork must be provide the centralized support and troubleshooting capabilities.
Most common internetworking devices are listed below.
Hubs
Switches
Bridges
Hubs
Hubs are used for connecting the multiple Ethernet devices. It performs functions as a
single unit. The hubs are used for controlling the media access by utilizes the carried sense
multiple access with collision detection. The hubs operates at half duplex mode.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Switches
Switches are used to link the Ethernet network. The switches are connected to the
network by using the twisted pair cabling. The hubs and switches are treating the data which they
receive. Hubs do its function by sending the data through the network. The switches work by
transferring the data from one port to another port which is considered as the destination port.
The switches operate at full duplex mode.
Bridges
Bridges are used to create the connection with other bridge network by using protocols.
Bridges work at the data link layer of the OSI model. The bridges are also used to link the
various networks and it easily develops the communication between the networks. The bridges
also connects two physical LAN, Logical LAN and Local area network by using the protocols.
4
Switches are used to link the Ethernet network. The switches are connected to the
network by using the twisted pair cabling. The hubs and switches are treating the data which they
receive. Hubs do its function by sending the data through the network. The switches work by
transferring the data from one port to another port which is considered as the destination port.
The switches operate at full duplex mode.
Bridges
Bridges are used to create the connection with other bridge network by using protocols.
Bridges work at the data link layer of the OSI model. The bridges are also used to link the
various networks and it easily develops the communication between the networks. The bridges
also connects two physical LAN, Logical LAN and Local area network by using the protocols.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. Switching Concepts
The Concept of switching is used to forward the packets from one port to other ports. The
network communication systems use the number switch nodes to create the communication
between two networks. Switching is commonly divided into two main types such as Connection
less and Connection oriented switches. The Connectionless switching does not require the
previous handshaking and acknowledgements. The connection oriented switching requires the
pre-established circuit along the path between the destinations. These switches first forward the
data to the circuit after transfer is completed. Because, switching circuit saves the data for future
use.The different types of switching techniques are listed in below.
Circuit Switching
Packet Switching
Message Switching
The network switches are described as layer 2 and layer 3 switches. The layer 2 and layer
3 switches are organized to conform to the ISO seen layer model. These are discussed in below.
Layer 2 Switching
Layer 2 switches are used to learn the MAC address automatically and to create the table.
Layer 2 switch tables are used for forwarding the packets from one port to destination port. It
easily retrieves the information from the packets. It easily forwards the packets at the wire speed
of the network. It does not have impact on the network performance and band width issues.
Because it does not requires any set up and management.
Layer 3 Switching
Layer 3 switches are based on the routing information and it traditionally has the routers
function. It uses the specialized routing protocols. It easily enables the routers to learn the routes
between the network.
3. Basic Switch Configuration
The basic switch configuration is shown in below.
5
The Concept of switching is used to forward the packets from one port to other ports. The
network communication systems use the number switch nodes to create the communication
between two networks. Switching is commonly divided into two main types such as Connection
less and Connection oriented switches. The Connectionless switching does not require the
previous handshaking and acknowledgements. The connection oriented switching requires the
pre-established circuit along the path between the destinations. These switches first forward the
data to the circuit after transfer is completed. Because, switching circuit saves the data for future
use.The different types of switching techniques are listed in below.
Circuit Switching
Packet Switching
Message Switching
The network switches are described as layer 2 and layer 3 switches. The layer 2 and layer
3 switches are organized to conform to the ISO seen layer model. These are discussed in below.
Layer 2 Switching
Layer 2 switches are used to learn the MAC address automatically and to create the table.
Layer 2 switch tables are used for forwarding the packets from one port to destination port. It
easily retrieves the information from the packets. It easily forwards the packets at the wire speed
of the network. It does not have impact on the network performance and band width issues.
Because it does not requires any set up and management.
Layer 3 Switching
Layer 3 switches are based on the routing information and it traditionally has the routers
function. It uses the specialized routing protocols. It easily enables the routers to learn the routes
between the network.
3. Basic Switch Configuration
The basic switch configuration is shown in below.
5
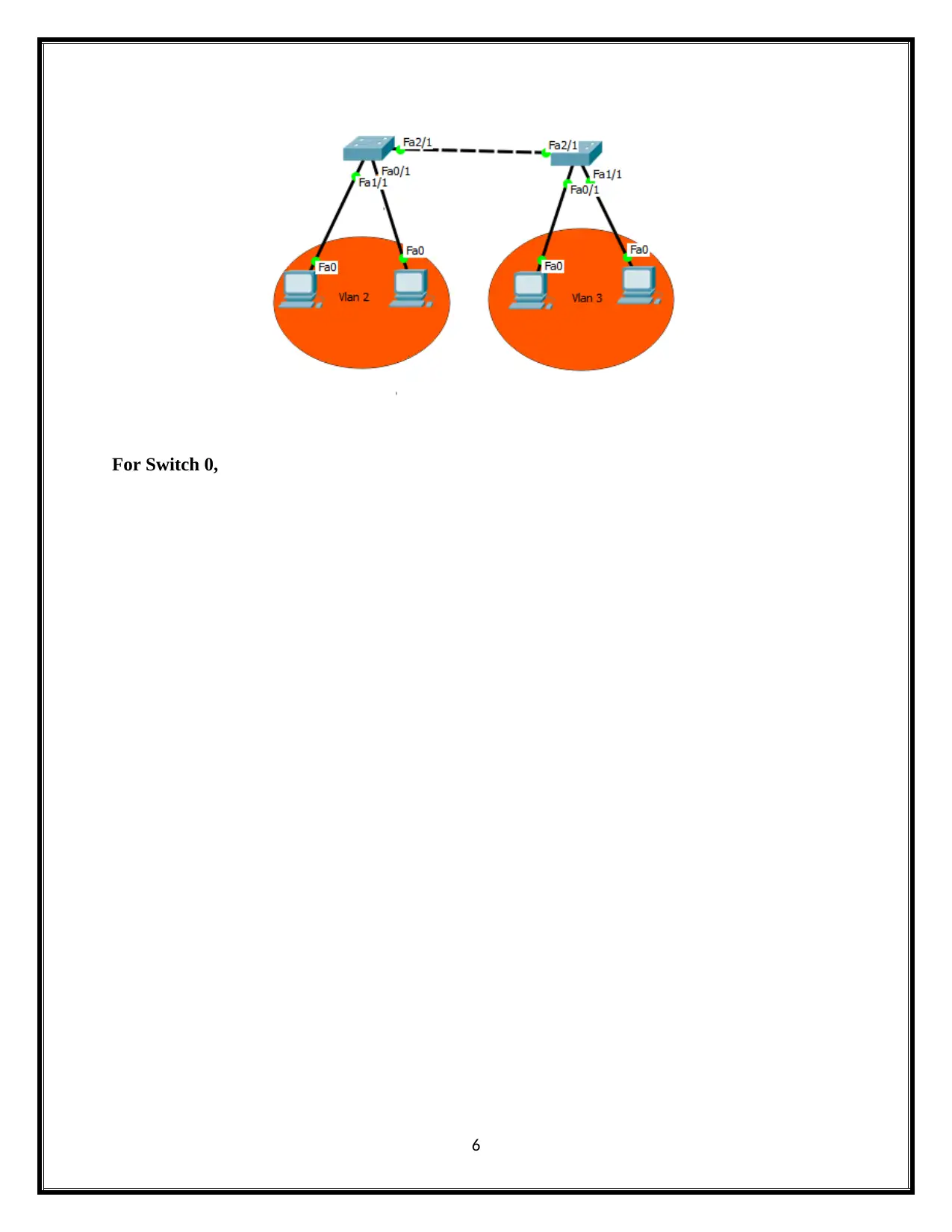
For Switch 0,
6
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
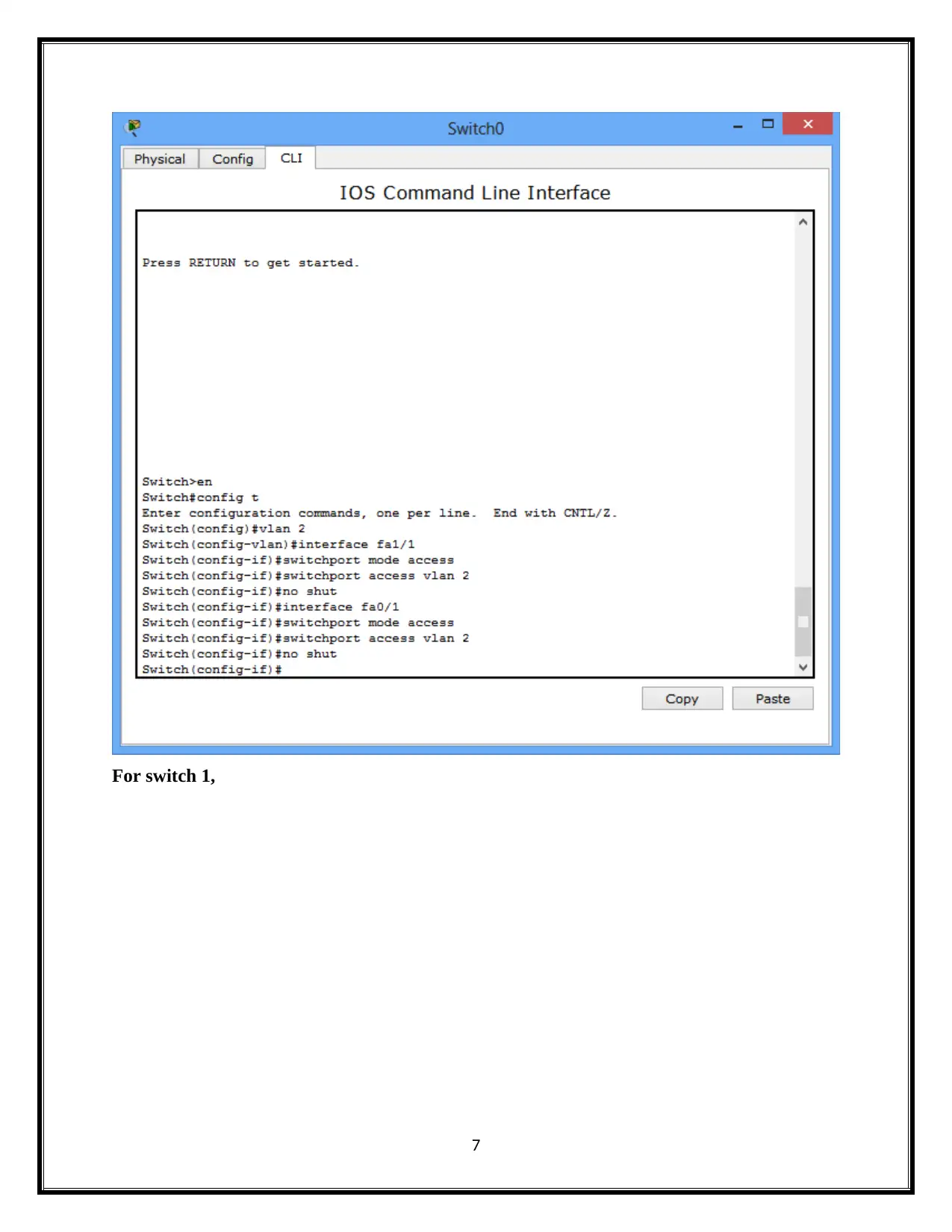
For switch 1,
7
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
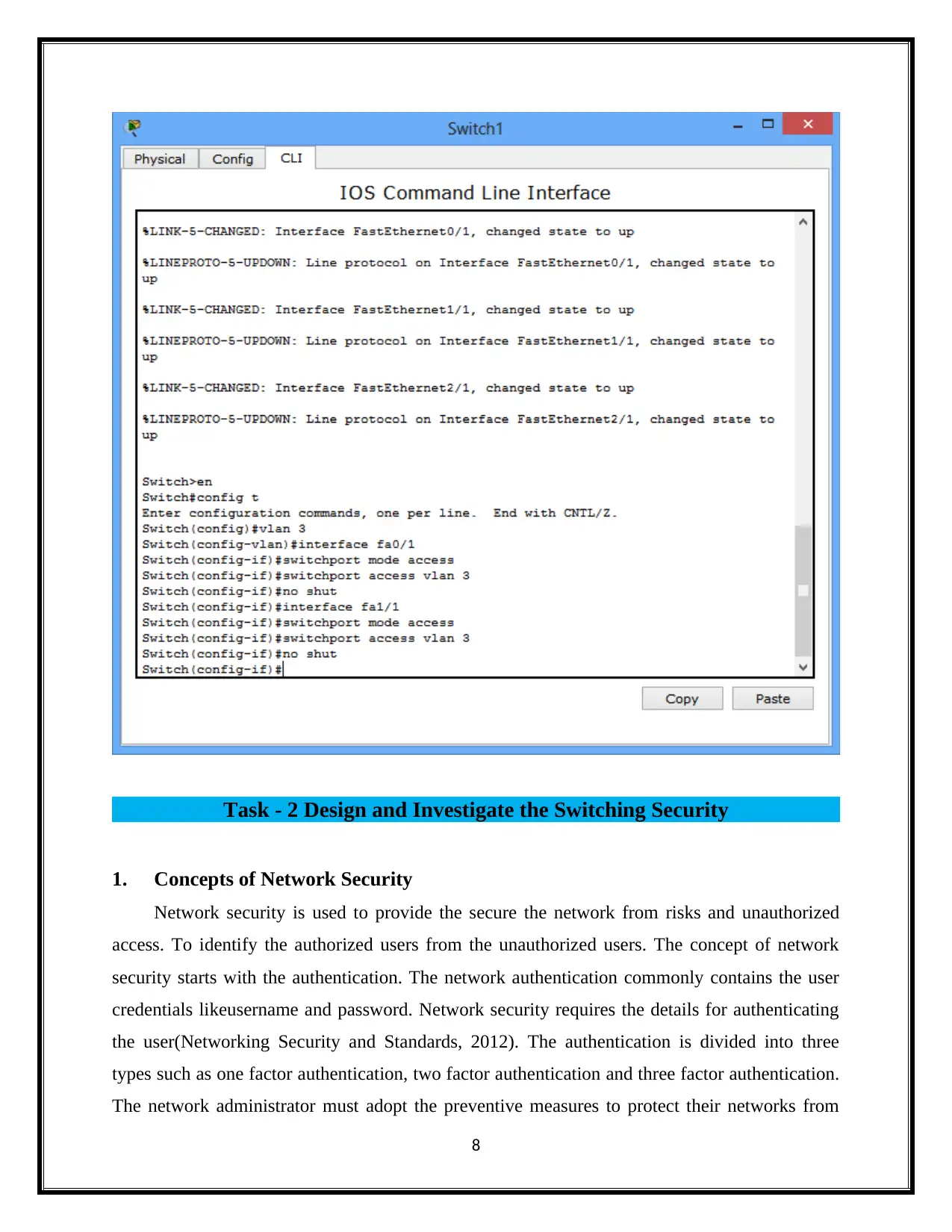
Task - 2 Design and Investigate the Switching Security
1. Concepts of Network Security
Network security is used to provide the secure the network from risks and unauthorized
access. To identify the authorized users from the unauthorized users. The concept of network
security starts with the authentication. The network authentication commonly contains the user
credentials likeusername and password. Network security requires the details for authenticating
the user(Networking Security and Standards, 2012). The authentication is divided into three
types such as one factor authentication, two factor authentication and three factor authentication.
The network administrator must adopt the preventive measures to protect their networks from
8
1. Concepts of Network Security
Network security is used to provide the secure the network from risks and unauthorized
access. To identify the authorized users from the unauthorized users. The concept of network
security starts with the authentication. The network authentication commonly contains the user
credentials likeusername and password. Network security requires the details for authenticating
the user(Networking Security and Standards, 2012). The authentication is divided into three
types such as one factor authentication, two factor authentication and three factor authentication.
The network administrator must adopt the preventive measures to protect their networks from
8

risks. The very common and easy way to protecting the user network by assigning the user name
and password.
Security threats
The security threats are Worms, Trojan horses and DoS. These are most common security
threats. These threats destroy and consume the network resources. So, the network security is
used in identifying and mitigating the potential threats, company, person and other organization.
Network security isthe elimination of the security threats by using the various network devices.
These are listed below.
Antivirus
Antimalware Software
Firewalls
Access Control
Intrusion Prevention Systems
Quality of Services
Network security is nothing but demonstrating the network metrics by using the Quality
of services routing. The quality of services is used to determine the most secured path to connect
two distant nodes that are considered as the source node and destination node of the network.
The quality of services provides three basic network metrics such as traffic filtration, encryption
and authentication.
Remote Monitoring
Remote network monitoring is used to provide overall network information to the network
administrator. The network administrator uses the information to monitor, trouble shoot and
analyze the local area network. It is used to interconnect the lines from a central site.
2. VLAN Attacks
The VLAN attacks are listed and discussed below.
VLAN hopping Attacks
The VLAN hopping is one of the methods of attacking the network resources on VLAN
networks.The VLAN hopping attacks the weakness of user VLAN. It basically attacks the host
on VLAN to gain the access to other VLAN. The VLAN hopping attacks has two types such as
double tagging and switch spoofing. The switch spoofing is the process of attacking the host
9
and password.
Security threats
The security threats are Worms, Trojan horses and DoS. These are most common security
threats. These threats destroy and consume the network resources. So, the network security is
used in identifying and mitigating the potential threats, company, person and other organization.
Network security isthe elimination of the security threats by using the various network devices.
These are listed below.
Antivirus
Antimalware Software
Firewalls
Access Control
Intrusion Prevention Systems
Quality of Services
Network security is nothing but demonstrating the network metrics by using the Quality
of services routing. The quality of services is used to determine the most secured path to connect
two distant nodes that are considered as the source node and destination node of the network.
The quality of services provides three basic network metrics such as traffic filtration, encryption
and authentication.
Remote Monitoring
Remote network monitoring is used to provide overall network information to the network
administrator. The network administrator uses the information to monitor, trouble shoot and
analyze the local area network. It is used to interconnect the lines from a central site.
2. VLAN Attacks
The VLAN attacks are listed and discussed below.
VLAN hopping Attacks
The VLAN hopping is one of the methods of attacking the network resources on VLAN
networks.The VLAN hopping attacks the weakness of user VLAN. It basically attacks the host
on VLAN to gain the access to other VLAN. The VLAN hopping attacks has two types such as
double tagging and switch spoofing. The switch spoofing is the process of attacking the host
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

which imitates a trunking switch by trunking and tagging the protocols. It creates the traffic for
multiple VLANs.The double tagging attack is attacking the host that is connected on the 802.1q
interfaces.
Address Resolution Protocol Attacks
The Address resolution attack is the use of old protocol and it is designed for a friendly
environment. It does not have the security. The ARP attacks are targeted to the fool into the
forwarding packets to a different VLAN. The ARP packet consists of forged identities and
network end notes. The ARP attacks also known as ARP poisoning.The ARP attacks also
perform the man in the middle attack. The man in the middle attack occurs when the one network
device impersonates the another network device.
VLAN Trunking Protocol Attack
The VLAN Trunking protocol attack is designed to create the life easy by automatically
gathering the VLAN information through the network. It needs to follow setup like VTP server
and switches. These are used for propagating all the VLAN information.
3. Random Frame Stress Attacks
The Random frame stress attack is a based on the brute force attack. It has various
incarnations and randomly gets varied in the various fields of a packet. It leaves the untouched
source and destination address, The Random frame stress attack is used to isolate the host at data
link layer. It prevents the isolated hosts from the malicious and unwanted traffic from the
untrustworthy devices(Kurose and Ross, n.d.).
Task - 3 Network Design for Ethernet Switching
1. Ethernet Switching
Ethernet switching is one of the easiest economical ways to upgrade the existing LAN.
The Ethernet switching concept is used to evaluate the various Ethernet switches. It includes the
switching fabric, MAC address table and data packet handling. The Ethernet switching hub is
used to provide the electronic switching like fabric. The fabric creates the dedicated virtual
connection between the ports. Each Ethernet switching has the own unique MAC address.
Address is stored in a switching hub. An Ethernet is a data transmission standard process for the
LAN networks. The Ethernet LANs are classified into wired LAN and Wireless LANs. The
10
multiple VLANs.The double tagging attack is attacking the host that is connected on the 802.1q
interfaces.
Address Resolution Protocol Attacks
The Address resolution attack is the use of old protocol and it is designed for a friendly
environment. It does not have the security. The ARP attacks are targeted to the fool into the
forwarding packets to a different VLAN. The ARP packet consists of forged identities and
network end notes. The ARP attacks also known as ARP poisoning.The ARP attacks also
perform the man in the middle attack. The man in the middle attack occurs when the one network
device impersonates the another network device.
VLAN Trunking Protocol Attack
The VLAN Trunking protocol attack is designed to create the life easy by automatically
gathering the VLAN information through the network. It needs to follow setup like VTP server
and switches. These are used for propagating all the VLAN information.
3. Random Frame Stress Attacks
The Random frame stress attack is a based on the brute force attack. It has various
incarnations and randomly gets varied in the various fields of a packet. It leaves the untouched
source and destination address, The Random frame stress attack is used to isolate the host at data
link layer. It prevents the isolated hosts from the malicious and unwanted traffic from the
untrustworthy devices(Kurose and Ross, n.d.).
Task - 3 Network Design for Ethernet Switching
1. Ethernet Switching
Ethernet switching is one of the easiest economical ways to upgrade the existing LAN.
The Ethernet switching concept is used to evaluate the various Ethernet switches. It includes the
switching fabric, MAC address table and data packet handling. The Ethernet switching hub is
used to provide the electronic switching like fabric. The fabric creates the dedicated virtual
connection between the ports. Each Ethernet switching has the own unique MAC address.
Address is stored in a switching hub. An Ethernet is a data transmission standard process for the
LAN networks. The Ethernet LANs are classified into wired LAN and Wireless LANs. The
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Ethernet Switchingis also known as IEEE 802.3 standards. The success of Ethernet process has
the features such as simplicity and maintenance, ability to adapt the new technology and it can be
installed and upgraded in less cost. The Ethernet LAN uses the following technologies like
FDDI,Token ring and ATM.Ethernet includes three categories like performance such as Fast
Ethernet (100 Mbps) and Gigabit Ethernet (1000 Mbps).
IEEE Standards
IEEE 802 –standard Ethernet
IEEE 802.1Q-VLAN tags
IEEE 802.11-wireless LAN
IEEE 802.11a-OFDM
IEEE 802.15-bluetooth
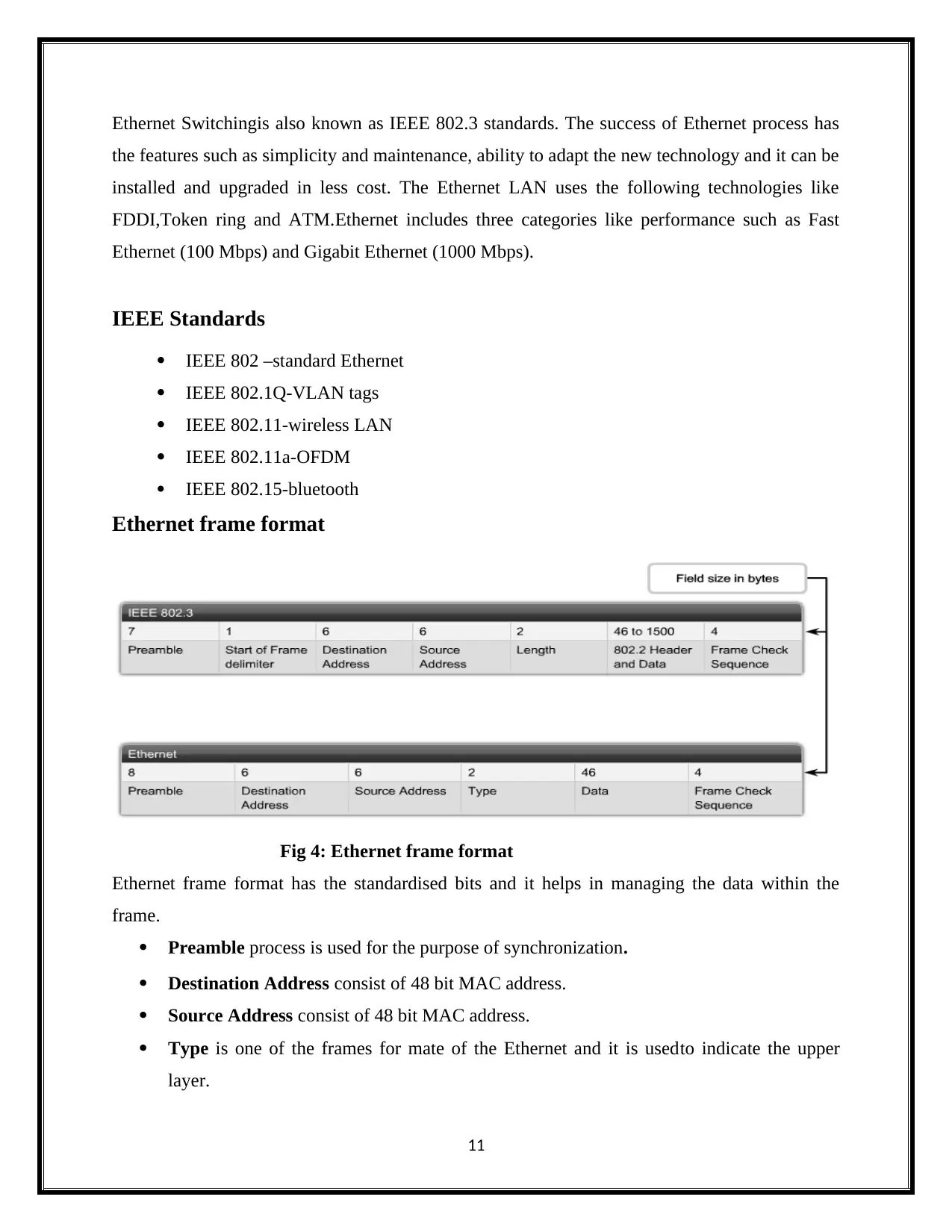
Ethernet frame format
Fig 4: Ethernet frame format
Ethernet frame format has the standardised bits and it helps in managing the data within the
frame.
Preamble process is used for the purpose of synchronization.
Destination Address consist of 48 bit MAC address.
Source Address consist of 48 bit MAC address.
Type is one of the frames for mate of the Ethernet and it is usedto indicate the upper
layer.
11
the features such as simplicity and maintenance, ability to adapt the new technology and it can be
installed and upgraded in less cost. The Ethernet LAN uses the following technologies like
FDDI,Token ring and ATM.Ethernet includes three categories like performance such as Fast
Ethernet (100 Mbps) and Gigabit Ethernet (1000 Mbps).
IEEE Standards
IEEE 802 –standard Ethernet
IEEE 802.1Q-VLAN tags
IEEE 802.11-wireless LAN
IEEE 802.11a-OFDM
IEEE 802.15-bluetooth
Ethernet frame format
Fig 4: Ethernet frame format
Ethernet frame format has the standardised bits and it helps in managing the data within the
frame.
Preamble process is used for the purpose of synchronization.
Destination Address consist of 48 bit MAC address.
Source Address consist of 48 bit MAC address.
Type is one of the frames for mate of the Ethernet and it is usedto indicate the upper
layer.
11

Data or Payload is a typical IPv4 packet.
Frame Check Sequence (FCS) used to check the damage frames.
2. Difference between Layer 2 and Layer 3 Switching
Layer 2(data link layer)
Layer 2 switches is used to decidehow the packets will move around the network. The
layer 2 Switch can be used to find the MAC address or media access control and then to send and
receive the information of the packet. The layer 3 switchesare automatically used to save the
packet and routing informationat NVRAM.
Layer 3(network layer)
Layer 3 switches use the same switching operation technology as the layer 2 switching. It
has some great advantages over the layer 2. It performs the routing by using the routers and
switches. It also performs two or more virtual LANs. It protects the unauthorised setup changes.
3. Ethernet Switching Industrial Application
The Ethernet switching is commonly used in HMI (Human Machine Interface).
Itis also useful for theindustrial Ethernet networking processes.
Ethernet switching is used for the industrial imaging and also for more industrial
application.
The switching process is used control the motor, physical security and also
programmable logic control.
It also performs testing, scientific and measurement processes.
4. Ethernet Switch Network Design
Based on the case study, The Ethernet Switching Network Design is shown in below.
12
Frame Check Sequence (FCS) used to check the damage frames.
2. Difference between Layer 2 and Layer 3 Switching
Layer 2(data link layer)
Layer 2 switches is used to decidehow the packets will move around the network. The
layer 2 Switch can be used to find the MAC address or media access control and then to send and
receive the information of the packet. The layer 3 switchesare automatically used to save the
packet and routing informationat NVRAM.
Layer 3(network layer)
Layer 3 switches use the same switching operation technology as the layer 2 switching. It
has some great advantages over the layer 2. It performs the routing by using the routers and
switches. It also performs two or more virtual LANs. It protects the unauthorised setup changes.
3. Ethernet Switching Industrial Application
The Ethernet switching is commonly used in HMI (Human Machine Interface).
Itis also useful for theindustrial Ethernet networking processes.
Ethernet switching is used for the industrial imaging and also for more industrial
application.
The switching process is used control the motor, physical security and also
programmable logic control.
It also performs testing, scientific and measurement processes.
4. Ethernet Switch Network Design
Based on the case study, The Ethernet Switching Network Design is shown in below.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





