School of Technology HND SWE: Switching Engineering Report
VerifiedAdded on 2023/01/09
|19
|4666
|64
Report
AI Summary
This report provides a detailed analysis of switching engineering concepts. It begins with an introduction to switching and internetworking, including the devices used, and then delves into the evaluation of switching, covering its working principles and advantages, such as cut-through and store-and-forward methods, along with switch configuration basics. The report then explores network security concepts, including firewall protection, VPNs, and the importance of security threads, authentication methods, and intrusion detection systems. It also investigates different types of VLAN attacks, such as VLAN hopping and ARP attacks, and random frame-stress attacks. Furthermore, the report examines Ethernet switching, its origins, and standardization, followed by a contrast of multilayer switching and an evaluation of industrial applications. Finally, the report concludes with an overview of wireless LAN switching, including how it works, its architecture, and the evaluation of wireless traffic, management, and monitoring.
Switching Engineering
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


Introduction
Switching is defined as a process that is liable for forwarding packets that are received
from one port and then transmitted to other which leads to destination. In case, when information
comes on port then it refers to ingress and when vice verse takes place i.e. data leaves port it is
defined as egress. Basically, it denotes medium via which information is routed to their final
destination (Baun, 2019). To understand this concept college in London is taken into
consideration who are looking forward to implement VLAN like pilot testing and they possess
different departments with definite number of employees. This report will furnish certain aspects
associated with LAN switching, design of switching security and concepts related with Ethernet
switching along with network design. Furthermore, wireless LAN switching will also be
investigated.
Task 1
1. Analysis of internetworking along with devices used.
The computer network comprises of distinct computers which are connected together by
utilisation of networking devices (like hubs, switch, etc.) for carrying out interaction where each
node is configured with identical protocol (TCP). When network interacts with each other that
have compatible or same communication procedures is referred to as internetworking. This can
be only attained in case same protocols are being utilised by devices connected within the
network. This is executed by usage of devices like hubs switches or routers. They possess ability
for connecting distinct networks as well as make sure that bug free communication takes place.
They acts as a backbone. The devices are specified below: Hub: It is liable for providing dedicated physical connection for each device that aids
within minimising possibilities of failure of one system that will lead to lose connectivity
in all computers. This works in physical layer which means that information is in form of
electrical signals or bits (Dickerson, 2019). Bridge: It is liable for connecting two different physical network segments. It is liable
for keeping track of MAC addresses present on network attached with their interfaces.
Bridge filters Ethernet frame through which it remains on only local side.
1
Switching is defined as a process that is liable for forwarding packets that are received
from one port and then transmitted to other which leads to destination. In case, when information
comes on port then it refers to ingress and when vice verse takes place i.e. data leaves port it is
defined as egress. Basically, it denotes medium via which information is routed to their final
destination (Baun, 2019). To understand this concept college in London is taken into
consideration who are looking forward to implement VLAN like pilot testing and they possess
different departments with definite number of employees. This report will furnish certain aspects
associated with LAN switching, design of switching security and concepts related with Ethernet
switching along with network design. Furthermore, wireless LAN switching will also be
investigated.
Task 1
1. Analysis of internetworking along with devices used.
The computer network comprises of distinct computers which are connected together by
utilisation of networking devices (like hubs, switch, etc.) for carrying out interaction where each
node is configured with identical protocol (TCP). When network interacts with each other that
have compatible or same communication procedures is referred to as internetworking. This can
be only attained in case same protocols are being utilised by devices connected within the
network. This is executed by usage of devices like hubs switches or routers. They possess ability
for connecting distinct networks as well as make sure that bug free communication takes place.
They acts as a backbone. The devices are specified below: Hub: It is liable for providing dedicated physical connection for each device that aids
within minimising possibilities of failure of one system that will lead to lose connectivity
in all computers. This works in physical layer which means that information is in form of
electrical signals or bits (Dickerson, 2019). Bridge: It is liable for connecting two different physical network segments. It is liable
for keeping track of MAC addresses present on network attached with their interfaces.
Bridge filters Ethernet frame through which it remains on only local side.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Switch: This implies multiport bridge that have buffer as well as designed in such a
manner that efficiency and performance can be enhanced. It is layer 2 device and can
conduct error checking before any data is sent.
2. Evaluation of concept of switching.
Switching denotes process associated with forwarding packets that comes from one port
to the destination.
Working of switch: When host delivers any frame to host then source host will be stored
in address table of MAC address switch. It (switch) is responsible for storing addresses of source
within the table. When switch is initialised then it do not contain any kind of information related
with host or its address (Hui, Vasseur and Hong, 2018). In case host frame is sent then MAC
address will be stored on table but if destination information is not present then switch will send
frame to all hosts present within the network (Introduction and Working of Switches in
Networking, 2020). As soon as response is attained, its address will be stored in table. Each time
this process takes place, switch will create a table. When all port numbers and addresses are
attained then switch will deliver frame to only hosts rather than to all all present within the
network. The advantages of switch are specified below:
Cut-through: When frames are received then initial 6 bytes will be checked. After this
LAN switch will be checking their destination MAC address within switching table and will
identify outgoing interface port as well as will be sent to destination. The error checking will not
be carried out here and frames will be sent as it is to receiving switches.
Store & forward: The switch will wait for entire frame before sending it and once it is
attained then switch will store entire frame in memory buffer. Furthermore, bugs will be checked
before making any decisions related with forwarding it. Cyclic redundancy check utilise
mathematical formula depending on bits within the frame. This is liable for ensuring high levels
of bug-free network traffic.
Fragment free switching: This is being applied to improvise restrictions related with cut-
through switching and will discard frames that are smaller than 64 bytes for minimising late
collisions within data transmission (Jacob and et. al, 2019).
3. Illustrate basics of switch configuration.
The steps that will be utilised for configuration of switch are specified below:
Step 1: Connect to device using console
2
manner that efficiency and performance can be enhanced. It is layer 2 device and can
conduct error checking before any data is sent.
2. Evaluation of concept of switching.
Switching denotes process associated with forwarding packets that comes from one port
to the destination.
Working of switch: When host delivers any frame to host then source host will be stored
in address table of MAC address switch. It (switch) is responsible for storing addresses of source
within the table. When switch is initialised then it do not contain any kind of information related
with host or its address (Hui, Vasseur and Hong, 2018). In case host frame is sent then MAC
address will be stored on table but if destination information is not present then switch will send
frame to all hosts present within the network (Introduction and Working of Switches in
Networking, 2020). As soon as response is attained, its address will be stored in table. Each time
this process takes place, switch will create a table. When all port numbers and addresses are
attained then switch will deliver frame to only hosts rather than to all all present within the
network. The advantages of switch are specified below:
Cut-through: When frames are received then initial 6 bytes will be checked. After this
LAN switch will be checking their destination MAC address within switching table and will
identify outgoing interface port as well as will be sent to destination. The error checking will not
be carried out here and frames will be sent as it is to receiving switches.
Store & forward: The switch will wait for entire frame before sending it and once it is
attained then switch will store entire frame in memory buffer. Furthermore, bugs will be checked
before making any decisions related with forwarding it. Cyclic redundancy check utilise
mathematical formula depending on bits within the frame. This is liable for ensuring high levels
of bug-free network traffic.
Fragment free switching: This is being applied to improvise restrictions related with cut-
through switching and will discard frames that are smaller than 64 bytes for minimising late
collisions within data transmission (Jacob and et. al, 2019).
3. Illustrate basics of switch configuration.
The steps that will be utilised for configuration of switch are specified below:
Step 1: Connect to device using console
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Through usage of software like Putty, connect with console of switch. Command prompt
will illustrate: Switch> write enable and enter. This will provide privilege EXEC mode i.e.
Switch#. Now go in global configuration mode:
Switch# configure terminal
Switch(config)#
Step 2: Set hostname
Switch(config)#hostname access-switch1
access-switch1(config)#
Step 3: Configure password
access-switch1(config)# enable secret password
Step 4: Configure password for Console access & Telnet
It will enable to lockdown all the access line by making use of password. This can be
done by following commands.
#line vty 0 15
#password strongtelpass
#login
#exit
#line console 0
#password strongconslepass
#login
#exit
Step 5: Define IP addresses which are allowed for access to switch via Telnet
#ip access-list standard TELNET.ACCESS
#permit 10.1.1.100
#permit 10.1.1.101
#exit
#line vty 0 15
3
will illustrate: Switch> write enable and enter. This will provide privilege EXEC mode i.e.
Switch#. Now go in global configuration mode:
Switch# configure terminal
Switch(config)#
Step 2: Set hostname
Switch(config)#hostname access-switch1
access-switch1(config)#
Step 3: Configure password
access-switch1(config)# enable secret password
Step 4: Configure password for Console access & Telnet
It will enable to lockdown all the access line by making use of password. This can be
done by following commands.
#line vty 0 15
#password strongtelpass
#login
#exit
#line console 0
#password strongconslepass
#login
#exit
Step 5: Define IP addresses which are allowed for access to switch via Telnet
#ip access-list standard TELNET.ACCESS
#permit 10.1.1.100
#permit 10.1.1.101
#exit
#line vty 0 15
3

#access-class TELNET-ACCESS in
#exit
Step 6: Assigning IP address to switch for management
By default Vlan 1 is assigned to management IP
#interface vlan 1
#ip address 10.1.1.200 255.255.255.0
#exit
Step 7: Assigning default gateway to switch
access-switch1(config)#ip default-gateway 10.1.1.254
Step 8: Disable not required ports on switch
This is done for enhancing security. Suppose that switch have 48-ports and from 22 to 48
ports are not needed.
#interface range fe 0/22-48
#shutdown
#exit
Step 9: Configure layer 2 VLAN & assigning ports
#vlan 2
#name DOCTOR
#exit
#vlan 3
#name NURSES
#exit
Now assign physical ports for each virtual LAN. In this case, Ports 1-2 are assigned with
VLAN2 along with VLAN3 with ports 3-4.
#interface range fe 0/1-2
#switchport mode access
4
#exit
Step 6: Assigning IP address to switch for management
By default Vlan 1 is assigned to management IP
#interface vlan 1
#ip address 10.1.1.200 255.255.255.0
#exit
Step 7: Assigning default gateway to switch
access-switch1(config)#ip default-gateway 10.1.1.254
Step 8: Disable not required ports on switch
This is done for enhancing security. Suppose that switch have 48-ports and from 22 to 48
ports are not needed.
#interface range fe 0/22-48
#shutdown
#exit
Step 9: Configure layer 2 VLAN & assigning ports
#vlan 2
#name DOCTOR
#exit
#vlan 3
#name NURSES
#exit
Now assign physical ports for each virtual LAN. In this case, Ports 1-2 are assigned with
VLAN2 along with VLAN3 with ports 3-4.
#interface range fe 0/1-2
#switchport mode access
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

#switchport mode access vlan 2
#exit
#interface range fe 0/3-4
#switchport mode access
#switchport mode access vlan 3
#exit
Step 10: Configure speed of port and half duplex settings
#configure console
#speed 100
#half duplex
#exit
To verify the duplex along with speed on fast Ethernet:
#show interface fastethernet 0/18
Step 11: Save configuration
#exit
#wr
Task 2
1. Analyse network security concepts
The process associated with taking up preventive measures for protecting underlying
networking infrastructure from any unauthorised access, malfunction, modification, misuse,
destruction or inadequate disclosure is referred to as network security (Leite, Hoji and Junior,
2018). For securing a network, certain aspects have been specified beneath:
Firewall protection: This acts like a barrier among untrusted external and trusted internal
network. Admins are liable for configuring set of defined rules which permits or blocks traffic on
the networking. For an instance, NGFW (Forcepoint's Next Generation Firewall) renders central
and seamless managed control for network traffic.
5
#exit
#interface range fe 0/3-4
#switchport mode access
#switchport mode access vlan 3
#exit
Step 10: Configure speed of port and half duplex settings
#configure console
#speed 100
#half duplex
#exit
To verify the duplex along with speed on fast Ethernet:
#show interface fastethernet 0/18
Step 11: Save configuration
#exit
#wr
Task 2
1. Analyse network security concepts
The process associated with taking up preventive measures for protecting underlying
networking infrastructure from any unauthorised access, malfunction, modification, misuse,
destruction or inadequate disclosure is referred to as network security (Leite, Hoji and Junior,
2018). For securing a network, certain aspects have been specified beneath:
Firewall protection: This acts like a barrier among untrusted external and trusted internal
network. Admins are liable for configuring set of defined rules which permits or blocks traffic on
the networking. For an instance, NGFW (Forcepoint's Next Generation Firewall) renders central
and seamless managed control for network traffic.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Virtual private network: It is liable for creating connections with network from other
site. For an instance, employees who are working from home will connect with network of firm
via VPN. Data among two points will be encrypted and users have to authenticate through which
communication between network and device can be created.
Antivirus & antimalware software: This will aid firms from certain malicious software
that comprises of trojans, viruses, worms and ransomware. Each file is scanned when they enter
within the network.
The aspects associated with network are specified beneath:
Security threads:This illustrates probable dangers which lead to creation of impact on
smooth working of PC. They can be harmful trojan malware or any adware. This leads to
corruption of data, loss or any kind of physical damage to infrastructure (Ma and et. al, 2019). In
context of security, authentication methods must be utilised from preventing individuals along
with this intrusion detection systems can be utilised for handling issues related with denial of
service attack.
QoS: Quality of services implies set of technologies which work on network that is liable
to guarantee their ability to execute high-priority applications along with traffic under restricted
network capacity. QoS technologies are liable for accomplishment by rendering differentiated
handling along with capacity allocation for peculiar flow within network traffic.
Monitoring: It is a critical process in which all the networking components such as
firewalls, Vms, servers, routers, etc. are monitored for performance and fault that are
continuously evaluated for maintaining as well as optimisation of their availability.
Remote monitoring: The standard specification that is liable for facilitating monitoring
of operational activities of network via usage of remote devices like probes. It enables carrying
out detailed monitoring related with network statistics related with Ethernet networks (Mikac and
Horvatić, 2019). This aids to monitor network traffic via remote Ethernet segment from central
location on network for detecting problem like excessive collisions, dropped packets and traffic
congestion.
2. Study distinct kind of VLAN attacks
There are different attacks that are made on VLAN, they are illustrated beneath:
6
site. For an instance, employees who are working from home will connect with network of firm
via VPN. Data among two points will be encrypted and users have to authenticate through which
communication between network and device can be created.
Antivirus & antimalware software: This will aid firms from certain malicious software
that comprises of trojans, viruses, worms and ransomware. Each file is scanned when they enter
within the network.
The aspects associated with network are specified beneath:
Security threads:This illustrates probable dangers which lead to creation of impact on
smooth working of PC. They can be harmful trojan malware or any adware. This leads to
corruption of data, loss or any kind of physical damage to infrastructure (Ma and et. al, 2019). In
context of security, authentication methods must be utilised from preventing individuals along
with this intrusion detection systems can be utilised for handling issues related with denial of
service attack.
QoS: Quality of services implies set of technologies which work on network that is liable
to guarantee their ability to execute high-priority applications along with traffic under restricted
network capacity. QoS technologies are liable for accomplishment by rendering differentiated
handling along with capacity allocation for peculiar flow within network traffic.
Monitoring: It is a critical process in which all the networking components such as
firewalls, Vms, servers, routers, etc. are monitored for performance and fault that are
continuously evaluated for maintaining as well as optimisation of their availability.
Remote monitoring: The standard specification that is liable for facilitating monitoring
of operational activities of network via usage of remote devices like probes. It enables carrying
out detailed monitoring related with network statistics related with Ethernet networks (Mikac and
Horvatić, 2019). This aids to monitor network traffic via remote Ethernet segment from central
location on network for detecting problem like excessive collisions, dropped packets and traffic
congestion.
2. Study distinct kind of VLAN attacks
There are different attacks that are made on VLAN, they are illustrated beneath:
6

VLAN Hopping Attacks: This kind of exploit enable attackers for bypassing any layer 2
restrictions that are built for dividing hosts. In this case, attacker is connected with access port
for gaining access to network traffic via other VLAN's.
ARP Attacks: It was designed for friendly environment and there was no security built on
function. In this case, attacker can pretend that there MAC address is related with IP address
within the network (Minei and Marques, 2019). There is no way for verification if identities and
anyone can intent to be someone else for having access to information.
Trunking protocol attack: It is vulnerable for probable denial of service attacks on the
network. In this case attacker can trigger issue through sending special crafted VTP packet for a
switch configured like a trunk port.
MAC/CAM attack: The information like MAC address is stored on physical port and
related parameters. The CAM tables comprises of fixed size which makes them prone to distinct
attacks such as buffer overflow attack. They are vulnerable to a potential denial of service an
attack. An attacker can potentially trigger this issue by sending a specially crafted VTP packet-
stress attacks
3. Assess random frame-stress attacks.
This takes place at layer 2 and here, ample of packets are generated randomly that
comprises of different fields in each packet that leaves only source as well as destination address
untouched. Such kind of attack must fail but bugs do not take place this leads to unexpected
access for other VLAN or might also lead to denial of service attacks. This may also include
brute force attack which are carried out on distinct fields. Within such kind of brute force attack
source along with destination address are constant (Mirza and Cosan, 2018). They are being
conducted for testing switch ability when abnormalities are encountered within input &
calculations. But random frame-stress attack can be avoided in case of Private PVLAN or VLAN
is utilised for separating host from having unwanted inputs. They are used for isolating hosts at
Layer 2 then protecting hosts from malicious or unwanted traffic from any kind of untrustworthy
devices.
7
restrictions that are built for dividing hosts. In this case, attacker is connected with access port
for gaining access to network traffic via other VLAN's.
ARP Attacks: It was designed for friendly environment and there was no security built on
function. In this case, attacker can pretend that there MAC address is related with IP address
within the network (Minei and Marques, 2019). There is no way for verification if identities and
anyone can intent to be someone else for having access to information.
Trunking protocol attack: It is vulnerable for probable denial of service attacks on the
network. In this case attacker can trigger issue through sending special crafted VTP packet for a
switch configured like a trunk port.
MAC/CAM attack: The information like MAC address is stored on physical port and
related parameters. The CAM tables comprises of fixed size which makes them prone to distinct
attacks such as buffer overflow attack. They are vulnerable to a potential denial of service an
attack. An attacker can potentially trigger this issue by sending a specially crafted VTP packet-
stress attacks
3. Assess random frame-stress attacks.
This takes place at layer 2 and here, ample of packets are generated randomly that
comprises of different fields in each packet that leaves only source as well as destination address
untouched. Such kind of attack must fail but bugs do not take place this leads to unexpected
access for other VLAN or might also lead to denial of service attacks. This may also include
brute force attack which are carried out on distinct fields. Within such kind of brute force attack
source along with destination address are constant (Mirza and Cosan, 2018). They are being
conducted for testing switch ability when abnormalities are encountered within input &
calculations. But random frame-stress attack can be avoided in case of Private PVLAN or VLAN
is utilised for separating host from having unwanted inputs. They are used for isolating hosts at
Layer 2 then protecting hosts from malicious or unwanted traffic from any kind of untrustworthy
devices.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 3
1. Assess Ethernet switching
The common form of switch which is a networking device that is utilised in Ethernet for
connecting distinct Ethernet devices is referred to as Ethernet switch.
Origin of Ethernet: It was developed in 1970s but network system were utilised
internally by Xerox. In 1980's Ethernet was developed within standardized products. It was not
used for decades but various manufacturing firms started to develop Ethernet related products.
IEEE 802.3 is utilised at present times.
1st Ethernet: The Ethernet network systems was invented to interconnect enhanced
computer workstations which makes it probable for sending data from one to another high-speed
laser printers (Mishra, Dehuri and Panigrahi, 2019). This is was invented at XEROX PARC that
also had GUI and is named Xerox Alto. The first high-speed LAN technology was brought in for
linking everything together.
Ethernet Standardisation: The Ethernet standards are being written as well as
maintained via IEEE (Institute of Electrical & Electronic Engineers). They are liable for
developing and maintaining huge number of standards that are related with electrical &
electronics industries. The most popular is Wi-Fi that is standardised like IEEE 802.11. There are
around 1100 active standards.
3com Ethernet: They are liable for rendering cost efficacious layer 2 10/100 &
10/100/1000 switching for LAN which do not require any management capabilities. It is line of
Ethernet IEEE 802.3 network cards for MCA, ISA, PCMCIA and EISA computer buses.
Star LAN: It was first Ethernet IEEE 802.3 standards over twisted pair cable. This was
standardised by standards of association in 1986 like a 1BASE5 version.
10 BASE-T: It implies Ethernet standards that are liable for transmitting 10 Mbps over
telephone wire (i.e. twisted wire pairs). This implies a shared media LAN that is utilised with
hub where each node shares 10 Mbps when utilised with switch.
Ethernet Switching: This is liable to connect devices together via a packet switching for
receiving, processing and forwarding information from one source to destination (Newman,
2018).
Fast & Gigabit Ethernet: Fast Ethernet is used for carrying traffic with speed of 10Mbps
and this was introduced within the market as IEEE 802.3u standard in 1995. Gigabit Ethernet is
8
1. Assess Ethernet switching
The common form of switch which is a networking device that is utilised in Ethernet for
connecting distinct Ethernet devices is referred to as Ethernet switch.
Origin of Ethernet: It was developed in 1970s but network system were utilised
internally by Xerox. In 1980's Ethernet was developed within standardized products. It was not
used for decades but various manufacturing firms started to develop Ethernet related products.
IEEE 802.3 is utilised at present times.
1st Ethernet: The Ethernet network systems was invented to interconnect enhanced
computer workstations which makes it probable for sending data from one to another high-speed
laser printers (Mishra, Dehuri and Panigrahi, 2019). This is was invented at XEROX PARC that
also had GUI and is named Xerox Alto. The first high-speed LAN technology was brought in for
linking everything together.
Ethernet Standardisation: The Ethernet standards are being written as well as
maintained via IEEE (Institute of Electrical & Electronic Engineers). They are liable for
developing and maintaining huge number of standards that are related with electrical &
electronics industries. The most popular is Wi-Fi that is standardised like IEEE 802.11. There are
around 1100 active standards.
3com Ethernet: They are liable for rendering cost efficacious layer 2 10/100 &
10/100/1000 switching for LAN which do not require any management capabilities. It is line of
Ethernet IEEE 802.3 network cards for MCA, ISA, PCMCIA and EISA computer buses.
Star LAN: It was first Ethernet IEEE 802.3 standards over twisted pair cable. This was
standardised by standards of association in 1986 like a 1BASE5 version.
10 BASE-T: It implies Ethernet standards that are liable for transmitting 10 Mbps over
telephone wire (i.e. twisted wire pairs). This implies a shared media LAN that is utilised with
hub where each node shares 10 Mbps when utilised with switch.
Ethernet Switching: This is liable to connect devices together via a packet switching for
receiving, processing and forwarding information from one source to destination (Newman,
2018).
Fast & Gigabit Ethernet: Fast Ethernet is used for carrying traffic with speed of 10Mbps
and this was introduced within the market as IEEE 802.3u standard in 1995. Gigabit Ethernet is
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
responsible for offering 1000Mbps computing networking. This makes use of frame format
803.2 and can also execute on full & half duplex modes.
2. Contrast layer 2 & layer 3 switching.
It is specified below:
Basis for difference Layer 2 Switch Layer 3 Switch
Switching vs. Routing Switching is carried out by
identification & maintenance of
MAC addresses table.
It is specialized device which is
designed to route data packets via
IP addresses. Here, routing is done.
Functionalities This has restricted tendency to
switch packets from one to other
port. Routing cannot be done (Shi,
Islam and Miao, 2020).
It can be used for routing along
with switching. Layer 3 switching
enables devices to carry out
communication outside network.
MAC vs. IP address It renders hardware-based methods
for communication. ARP is used
for discovering and identification
MAC address of other connected
devices.
IP address is used for carrying out
routing in VLANs (Virtual local
area network).
Speed &
performance
Packets are rerouted to destination
from source port.
Switches takes time in checking
data packets before identification
of probable route for directing data
packets to destination port.
3. Evaluate industrial applications associated with Ethernet switching.
These aspects are illustrated below:
Spanning Tree Protocol (STP): This implies network protocol which is designed for
prevention of layer 2 loops and this denotes standardised like a IEEE 802.D protocol. It is used
by industries as this blocks some ports present on switches that have redundant links for
preventing broadcast storms for ensuring loop-free topology (Singh and Pamula, 2018).
9
803.2 and can also execute on full & half duplex modes.
2. Contrast layer 2 & layer 3 switching.
It is specified below:
Basis for difference Layer 2 Switch Layer 3 Switch
Switching vs. Routing Switching is carried out by
identification & maintenance of
MAC addresses table.
It is specialized device which is
designed to route data packets via
IP addresses. Here, routing is done.
Functionalities This has restricted tendency to
switch packets from one to other
port. Routing cannot be done (Shi,
Islam and Miao, 2020).
It can be used for routing along
with switching. Layer 3 switching
enables devices to carry out
communication outside network.
MAC vs. IP address It renders hardware-based methods
for communication. ARP is used
for discovering and identification
MAC address of other connected
devices.
IP address is used for carrying out
routing in VLANs (Virtual local
area network).
Speed &
performance
Packets are rerouted to destination
from source port.
Switches takes time in checking
data packets before identification
of probable route for directing data
packets to destination port.
3. Evaluate industrial applications associated with Ethernet switching.
These aspects are illustrated below:
Spanning Tree Protocol (STP): This implies network protocol which is designed for
prevention of layer 2 loops and this denotes standardised like a IEEE 802.D protocol. It is used
by industries as this blocks some ports present on switches that have redundant links for
preventing broadcast storms for ensuring loop-free topology (Singh and Pamula, 2018).
9
VLAN Trunking Protocol (VTP): This implies Cisco proprietary protocol that is utilised
by Cisco switches for exchanging VLAN information. VTP enables firms to synchronise VLAN
information with switches in VTP domain.
Virtual local area network (VLAN): It denotes set of end stations along with switch ports
which connects them. The physical need is that end station and port with which this is connected
must belong to similar VLAN.
Simplified network management protocol (SNMP): It is used for managing, monitoring
and configuring switches over a network via a administrators. This is responsible for executing a
method to manage network devices from centralised system thereby, in case of any issue NA will
be notified.
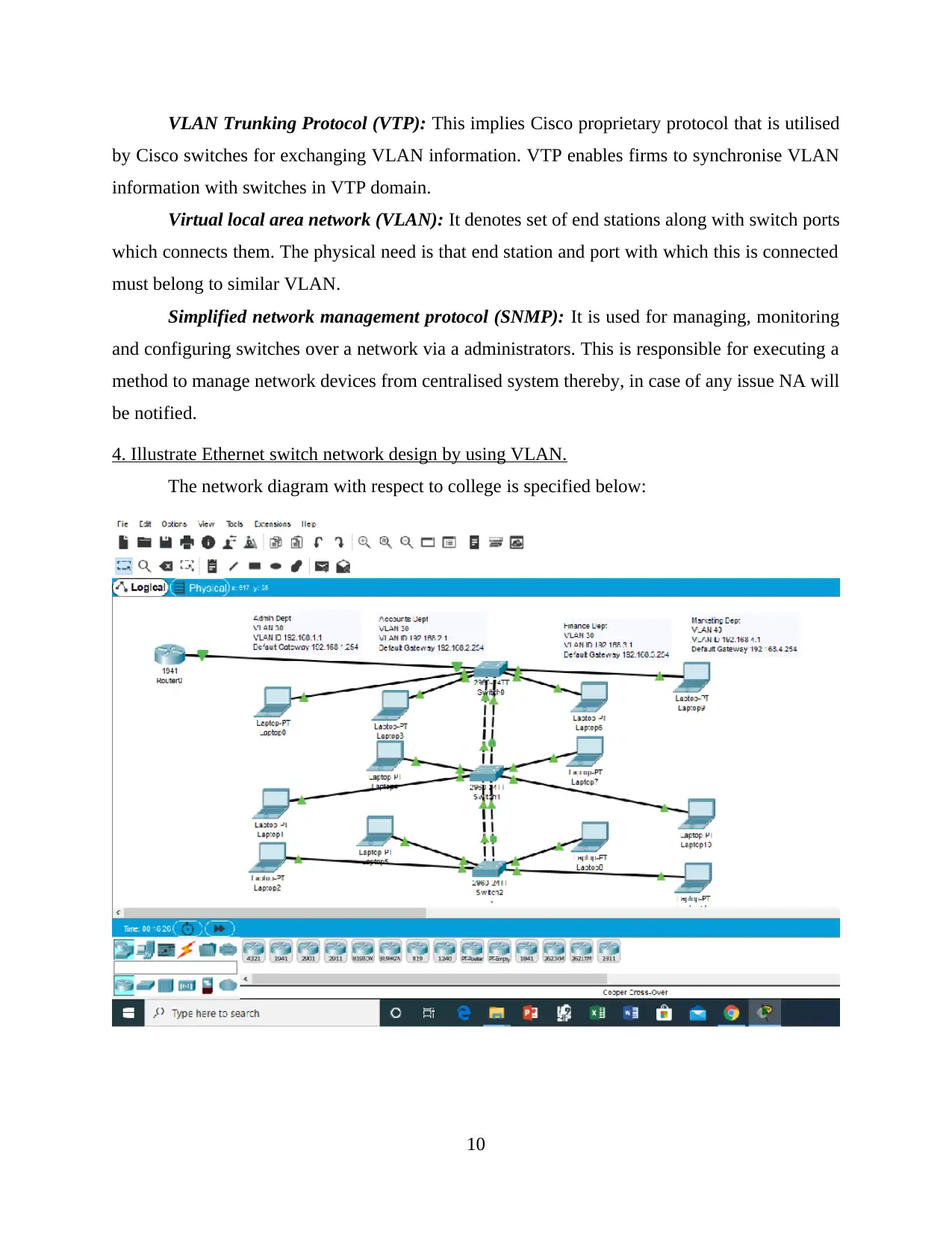
4. Illustrate Ethernet switch network design by using VLAN.
The network diagram with respect to college is specified below:
10
by Cisco switches for exchanging VLAN information. VTP enables firms to synchronise VLAN
information with switches in VTP domain.
Virtual local area network (VLAN): It denotes set of end stations along with switch ports
which connects them. The physical need is that end station and port with which this is connected
must belong to similar VLAN.
Simplified network management protocol (SNMP): It is used for managing, monitoring
and configuring switches over a network via a administrators. This is responsible for executing a
method to manage network devices from centralised system thereby, in case of any issue NA will
be notified.
4. Illustrate Ethernet switch network design by using VLAN.
The network diagram with respect to college is specified below:
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





