Detailed Wireless Network Report for Sydney Education Group, ICT40115
VerifiedAdded on 2022/10/17
|20
|4787
|213
Report
AI Summary
This report details the design and implementation of a wireless local area network (WLAN) for the Sydney Education Group (SEG) Brisbane campus. The report begins by outlining the business requirements, including the need for secure network access, data sharing, and adherence to industry standards. It then details the data gathering techniques used, such as surveys and stakeholder meetings, to define the network requirements. The report covers hardware and software configuration, including the selection of desktops, routers, wireless access points, and a NAS device, along with associated costs. A network diagram and three-layer hierarchical topology are presented, along with an IP addressing scheme and protocols. The report also addresses security threats and testing, and includes a backup plan. Finally, the report concludes with recommendations and references, along with meeting minutes.
T-1.8.1
Details of Assessment
Term and Year Time allowed N/A
Assessment No 1 of 2 Assessment Weighting 60%
Assessment Type Report Writing
Due Date Week-4 Room George St
Details of Subject
Qualification ICT40115 Certificate IV in Information Technology
Subject Name Wireless Network
Details of Unit(s) of competency
Unit Code (s) and
Names
ICTICT401 Determine and confirm client business requirements
ICTNWK405 Build a small wireless local area network
ICTSAS307 Install, configure and secure a small office or home office network
ICTNWK410 Install hardware to a network
Details of Student
Student Name
College Student ID
Student Declaration: I declare that the work submitted is my
own and has not been copied or plagiarised from any person or
source. I acknowledge that I understand the requirements to
complete the assessment tasks. I am also aware of my right to
appeal. The feedback session schedule and reassessment
procedure were explained to me.
Student’s
Signature: ____________________
Date: _____/_____/_________
Details of Assessor
Assessor’s Name
Assessment Outcome
Assessment
Result Competent Not Yet Competent Marks /60
Feedback to Student
Progressive feedback to students, identifying gaps in competency and comments on positive improvements:
______________________________________________________________________________________
______________________________________________________________________________________
______________________________________________________________________________________
______________________________________________________________________________________
______________________________________________________________________________________
____________________________________________________________________
Assessor Declaration: I declare that I have conducted a
fair, valid, reliable and flexible assessment with this
student.
Student attended the feedback session.
Student did not attend the feedback session.
Assessor’s
Signature: ___________________
Date: _____/_____/________
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 1
Details of Assessment
Term and Year Time allowed N/A
Assessment No 1 of 2 Assessment Weighting 60%
Assessment Type Report Writing
Due Date Week-4 Room George St
Details of Subject
Qualification ICT40115 Certificate IV in Information Technology
Subject Name Wireless Network
Details of Unit(s) of competency
Unit Code (s) and
Names
ICTICT401 Determine and confirm client business requirements
ICTNWK405 Build a small wireless local area network
ICTSAS307 Install, configure and secure a small office or home office network
ICTNWK410 Install hardware to a network
Details of Student
Student Name
College Student ID
Student Declaration: I declare that the work submitted is my
own and has not been copied or plagiarised from any person or
source. I acknowledge that I understand the requirements to
complete the assessment tasks. I am also aware of my right to
appeal. The feedback session schedule and reassessment
procedure were explained to me.
Student’s
Signature: ____________________
Date: _____/_____/_________
Details of Assessor
Assessor’s Name
Assessment Outcome
Assessment
Result Competent Not Yet Competent Marks /60
Feedback to Student
Progressive feedback to students, identifying gaps in competency and comments on positive improvements:
______________________________________________________________________________________
______________________________________________________________________________________
______________________________________________________________________________________
______________________________________________________________________________________
______________________________________________________________________________________
____________________________________________________________________
Assessor Declaration: I declare that I have conducted a
fair, valid, reliable and flexible assessment with this
student.
Student attended the feedback session.
Student did not attend the feedback session.
Assessor’s
Signature: ___________________
Date: _____/_____/________
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

T-1.8.1
Purpose of the assessment
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 2
Purpose of the assessment
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 2
T-1.8.1
The purpose of this assessment is to assess the student in the following
outcomes:
Competent
(C)
Not yet
Competent
(NYC)
ICTICT401 Determine and confirm client business requirements
1. Determine context of business need or problem
1.1 Establish the business problem to be investigated, including determining
system boundaries, scope and the development methodology to be used
1.2 Use chosen information gathering method to identify clients of the system
and problems they encounter
1.3 Analyse physical requirements and identify changes required to implement
new systems
1.4 Record client responses
1.5 Submit documentation to client for final approval or sign-off
2. Gather information
2.1 Use chosen information gathering method to identify clients of the system
and problems they encounter
2.2 Record client responses
2.3 Analyse gathered information to identify new system requirements and
establish problem specifications
2.4 Document system requirements and problems
2.5 Analyse physical requirements and identify changes required to implement
new systems
3. Confirm system specifications
3.1 Check documentation to ensure it meets client business needs
3.2 Submit documentation to the client for verification of accuracy and approval
3.3 Make changes to the documentation as necessary and indicated by the
client
3.4 Submit documentation to client for final approval or sign-off
ICTSAS307 Install, configure and secure a small office or home office network
1. Confirm client requirements and identify relevant network equipment
1.1 Identify and clarify client requirements for the small office home office
network
1.2 Identify most suitable network design to meet client requirements
1.3 Develop and document network design
1.4 Identify most suitable network technologies, devices and protocols and
network cables and connectors to meet network design
1.5 Review available network technologies, devices and protocols and
determine the most appropriate to meet client requirements
1.6 Source vendors and service suppliers to obtain specifications, availability
and cost of identified components
1.7 Ensure client sign-off for proposed network design and associated
components
2. Install and configure hardware and software
2.1 Develop installation plans with prioritised tasks and contingency
arrangements for installation of components with minimum disruption to client
2.2 Liaise with appropriate person to obtain approval for plans, including
security clearance and timing
2.3 Confirm and review supplier documentation that network cables and
connectors have been installed according to industry standards, client
requirements and building requirements
ICTNWK410 Install hardware to a network
1. Determine network hardware requirements
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 3
The purpose of this assessment is to assess the student in the following
outcomes:
Competent
(C)
Not yet
Competent
(NYC)
ICTICT401 Determine and confirm client business requirements
1. Determine context of business need or problem
1.1 Establish the business problem to be investigated, including determining
system boundaries, scope and the development methodology to be used
1.2 Use chosen information gathering method to identify clients of the system
and problems they encounter
1.3 Analyse physical requirements and identify changes required to implement
new systems
1.4 Record client responses
1.5 Submit documentation to client for final approval or sign-off
2. Gather information
2.1 Use chosen information gathering method to identify clients of the system
and problems they encounter
2.2 Record client responses
2.3 Analyse gathered information to identify new system requirements and
establish problem specifications
2.4 Document system requirements and problems
2.5 Analyse physical requirements and identify changes required to implement
new systems
3. Confirm system specifications
3.1 Check documentation to ensure it meets client business needs
3.2 Submit documentation to the client for verification of accuracy and approval
3.3 Make changes to the documentation as necessary and indicated by the
client
3.4 Submit documentation to client for final approval or sign-off
ICTSAS307 Install, configure and secure a small office or home office network
1. Confirm client requirements and identify relevant network equipment
1.1 Identify and clarify client requirements for the small office home office
network
1.2 Identify most suitable network design to meet client requirements
1.3 Develop and document network design
1.4 Identify most suitable network technologies, devices and protocols and
network cables and connectors to meet network design
1.5 Review available network technologies, devices and protocols and
determine the most appropriate to meet client requirements
1.6 Source vendors and service suppliers to obtain specifications, availability
and cost of identified components
1.7 Ensure client sign-off for proposed network design and associated
components
2. Install and configure hardware and software
2.1 Develop installation plans with prioritised tasks and contingency
arrangements for installation of components with minimum disruption to client
2.2 Liaise with appropriate person to obtain approval for plans, including
security clearance and timing
2.3 Confirm and review supplier documentation that network cables and
connectors have been installed according to industry standards, client
requirements and building requirements
ICTNWK410 Install hardware to a network
1. Determine network hardware requirements
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
T-1.8.1
1.1 Assess client network hardware and cabling requirements, considering
compatibility with existing application software and operating system
1.2 Analyse requirements against local area network (LAN), wide area network
(WAN), wireless networks, and mobile equipment access design limitations
and organisational guidelines
1.3 Evaluate client requirements according to organisational guidelines,
corporate purchasing procedures, licensing
2. Obtain network hardware
2.1 Contact vendors and obtain technical specifications
2.2 Evaluate or test hardware according to client requirements and
organisational guidelines
2.3 Document recommendations and provide copies to appropriate person
2.4 Determine and document licensing requirements and security issues
2.5 Acquire hardware according to recommendations and organisational
procedures
2.6 Organise cabling infrastructure where required
ICTNWK405 Build a small wireless local area network
1. Confirm client and equipment requirements
1.1 Identify, clarify and organise client requirements according to network
needs and organisational requirements
1.2 Ensure an appropriate person has given the authority for wireless network
access
1.3 Evaluate requirements along with business needs, and translate into
technical requirements
1.4 Identify components to be installed in order to meet the technical
requirements
1.5 Select position for access point, based on user requirements and
environmental conditions
1.6 Arrange for preliminary work to be carried out to meet cabling and power
requirements
Assessment/evidence gathering conditions
Each assessment component is recorded as either Competent (C) or Not Yet Competent (NYC). A student can
only achieve competence when all assessment components listed under “Purpose of the assessment” section
are recorded as competent. Your trainer will give you feedback after the completion of each assessment. A
student who is assessed as NYC (Not Yet Competent) is eligible for re-assessment.
Resources required for this assessment
Computer with relevant software applications and access to internet
Weekly eLearning notes relevant to the tasks/questions
Instructions for Students
Please read the following instructions carefully
This assessment has to be completed In class At home
The assessment is to be completed according to the instructions given by your assessor.
Feedback on each task will be provided to enable you to determine how your work could be improved. You
will be provided with feedback on your work within two weeks of the assessment due date. All other
feedback will be provided by the end of the term.
Should you not answer the questions correctly, you will be given feedback on the results and your gaps in
knowledge. You will be given another opportunity to demonstrate your knowledge and skills to be deemed
competent for this unit of competency.
If you are not sure about any aspect of this assessment, please ask for clarification from your assessor.
Please refer to the College re-assessment for more information (Student handbook).
Assessment Task 1- Project Activity Report (60%)
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 4
1.1 Assess client network hardware and cabling requirements, considering
compatibility with existing application software and operating system
1.2 Analyse requirements against local area network (LAN), wide area network
(WAN), wireless networks, and mobile equipment access design limitations
and organisational guidelines
1.3 Evaluate client requirements according to organisational guidelines,
corporate purchasing procedures, licensing
2. Obtain network hardware
2.1 Contact vendors and obtain technical specifications
2.2 Evaluate or test hardware according to client requirements and
organisational guidelines
2.3 Document recommendations and provide copies to appropriate person
2.4 Determine and document licensing requirements and security issues
2.5 Acquire hardware according to recommendations and organisational
procedures
2.6 Organise cabling infrastructure where required
ICTNWK405 Build a small wireless local area network
1. Confirm client and equipment requirements
1.1 Identify, clarify and organise client requirements according to network
needs and organisational requirements
1.2 Ensure an appropriate person has given the authority for wireless network
access
1.3 Evaluate requirements along with business needs, and translate into
technical requirements
1.4 Identify components to be installed in order to meet the technical
requirements
1.5 Select position for access point, based on user requirements and
environmental conditions
1.6 Arrange for preliminary work to be carried out to meet cabling and power
requirements
Assessment/evidence gathering conditions
Each assessment component is recorded as either Competent (C) or Not Yet Competent (NYC). A student can
only achieve competence when all assessment components listed under “Purpose of the assessment” section
are recorded as competent. Your trainer will give you feedback after the completion of each assessment. A
student who is assessed as NYC (Not Yet Competent) is eligible for re-assessment.
Resources required for this assessment
Computer with relevant software applications and access to internet
Weekly eLearning notes relevant to the tasks/questions
Instructions for Students
Please read the following instructions carefully
This assessment has to be completed In class At home
The assessment is to be completed according to the instructions given by your assessor.
Feedback on each task will be provided to enable you to determine how your work could be improved. You
will be provided with feedback on your work within two weeks of the assessment due date. All other
feedback will be provided by the end of the term.
Should you not answer the questions correctly, you will be given feedback on the results and your gaps in
knowledge. You will be given another opportunity to demonstrate your knowledge and skills to be deemed
competent for this unit of competency.
If you are not sure about any aspect of this assessment, please ask for clarification from your assessor.
Please refer to the College re-assessment for more information (Student handbook).
Assessment Task 1- Project Activity Report (60%)
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
T-1.8.1
In this assessment task, you are required to gather, determine and confirm client requirement and
review available network technologies, devices and protocols to build WLAN (Wireless Local Area
Network) for small office or home office network by choosing appropriate hardware and software in
accordance to business and technical requirements including installation plan, network design and
security.
Introduction:
Sydney Education Group (SEG) is a growing educational provider. It has been operating since
2010. Its main business is to provide vocational training and education for international students. With
further growth in business, SEG has decided to open new office in Brisbane.
Business Details:
The business is owned and managed by John Carter. He is the CEO of the company. There are
altogether 10 full-time for Brisbane Campus.
Brisbane campus comprises of 2 departments and 10 staff; Marketing and Admissions. Andre Shaw is
office manager and is responsible for operations, budgeting and approval for Brisbane site. Tracy
Johnson and Angela Sharma are head of Marketing and Admissions department respectively. They
both have 3 staff members in their departments. Tracy is responsible for marketing materials,
approving contents in the website for Brisbane and organising course information. Angela looks after
compliance, student’s documents and policy and procedure.
Below is the organisational chart for Brisbane campus.
The budget SEG have for IT infrastructure is $30,000 in order to purchase physical, network hardware
and software. With these hardware and software are you are require to set up IT infrastructure and
network connectivity in Brisbane campus.
Challenges:
SEG has contracted Complete IT Solutions (CIS) (Managed Services) to complete this project. You
are working as a Network Administrator in CIS. Andre has requested CIS to investigate and prepare a
recommendation report that satisfies all the Hardware, Software, and Infrastructure requirements for
SEG.
Furthermore, after meeting with Andre, Johnson and Angela, following information were collected.
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 5
Andre Shaw
Office Manager
Tracy Johnson
Marketing
officers X 3
Angela
Sharma
Admissions
Officers X 3
Receptionist
In this assessment task, you are required to gather, determine and confirm client requirement and
review available network technologies, devices and protocols to build WLAN (Wireless Local Area
Network) for small office or home office network by choosing appropriate hardware and software in
accordance to business and technical requirements including installation plan, network design and
security.
Introduction:
Sydney Education Group (SEG) is a growing educational provider. It has been operating since
2010. Its main business is to provide vocational training and education for international students. With
further growth in business, SEG has decided to open new office in Brisbane.
Business Details:
The business is owned and managed by John Carter. He is the CEO of the company. There are
altogether 10 full-time for Brisbane Campus.
Brisbane campus comprises of 2 departments and 10 staff; Marketing and Admissions. Andre Shaw is
office manager and is responsible for operations, budgeting and approval for Brisbane site. Tracy
Johnson and Angela Sharma are head of Marketing and Admissions department respectively. They
both have 3 staff members in their departments. Tracy is responsible for marketing materials,
approving contents in the website for Brisbane and organising course information. Angela looks after
compliance, student’s documents and policy and procedure.
Below is the organisational chart for Brisbane campus.
The budget SEG have for IT infrastructure is $30,000 in order to purchase physical, network hardware
and software. With these hardware and software are you are require to set up IT infrastructure and
network connectivity in Brisbane campus.
Challenges:
SEG has contracted Complete IT Solutions (CIS) (Managed Services) to complete this project. You
are working as a Network Administrator in CIS. Andre has requested CIS to investigate and prepare a
recommendation report that satisfies all the Hardware, Software, and Infrastructure requirements for
SEG.
Furthermore, after meeting with Andre, Johnson and Angela, following information were collected.
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 5
Andre Shaw
Office Manager
Tracy Johnson
Marketing
officers X 3
Angela
Sharma
Admissions
Officers X 3
Receptionist
T-1.8.1
Each staff member will have complete desktop, access to
printer, wireless and NAS
Staff should be able to use the network securely.
Data in Network Access Storage (NAS) should be able to share between all staff.
Hardware and software should be of industry standards.
Router and WAP must be regularly monitored and backed up.
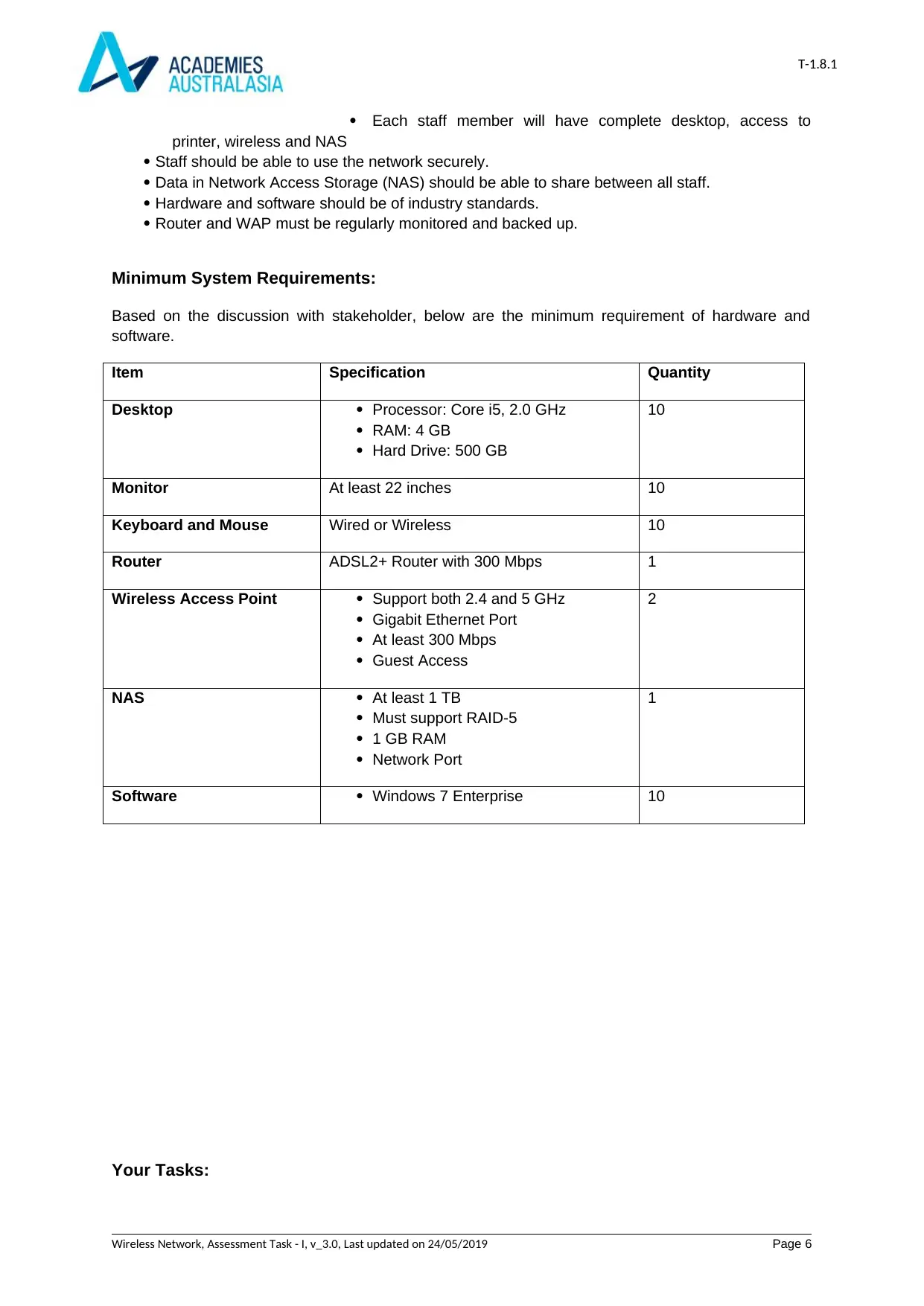
Minimum System Requirements:
Based on the discussion with stakeholder, below are the minimum requirement of hardware and
software.
Item Specification Quantity
Desktop Processor: Core i5, 2.0 GHz
RAM: 4 GB
Hard Drive: 500 GB
10
Monitor At least 22 inches 10
Keyboard and Mouse Wired or Wireless 10
Router ADSL2+ Router with 300 Mbps 1
Wireless Access Point Support both 2.4 and 5 GHz
Gigabit Ethernet Port
At least 300 Mbps
Guest Access
2
NAS At least 1 TB
Must support RAID-5
1 GB RAM
Network Port
1
Software Windows 7 Enterprise 10
Your Tasks:
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 6
Each staff member will have complete desktop, access to
printer, wireless and NAS
Staff should be able to use the network securely.
Data in Network Access Storage (NAS) should be able to share between all staff.
Hardware and software should be of industry standards.
Router and WAP must be regularly monitored and backed up.
Minimum System Requirements:
Based on the discussion with stakeholder, below are the minimum requirement of hardware and
software.
Item Specification Quantity
Desktop Processor: Core i5, 2.0 GHz
RAM: 4 GB
Hard Drive: 500 GB
10
Monitor At least 22 inches 10
Keyboard and Mouse Wired or Wireless 10
Router ADSL2+ Router with 300 Mbps 1
Wireless Access Point Support both 2.4 and 5 GHz
Gigabit Ethernet Port
At least 300 Mbps
Guest Access
2
NAS At least 1 TB
Must support RAID-5
1 GB RAM
Network Port
1
Software Windows 7 Enterprise 10
Your Tasks:
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

T-1.8.1
Report Writing
Research and prepare a report for Sydney Education Group.
To satisfy the business requirements for SEG,
You report must contain:
Cover page
Table of Contents (Refer to sample Table of Content)
Number all pages at the bottom centre of the page
Include your course, name and student number as a header at the top of each page. Use 1.5
line spacing (other guides may prefer double spacing)
Use the Times New Roman font at either 11pt or 12pt size
Either have a line space between paragraphs or indent the first line of each Paragraph.
Marking Guide for Trainer:
Marking List Marks out of
60
Introduction /3
Data Gathering techniques /4
Network Requirement /5
Hardware and software configuration /5
Hardware and software Cost /4
Network Diagram – (should include Router/WAP, clients, and printers) /5
Topology /5
Configuration /10
Security Threat Detection and Testing /5
Backup plan /4
Sign off Form /3
Conclusions /2
Reference /2
Meeting Minutes /3
TOTAL /60
TABLE OF CONTENTS
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 7
Report Writing
Research and prepare a report for Sydney Education Group.
To satisfy the business requirements for SEG,
You report must contain:
Cover page
Table of Contents (Refer to sample Table of Content)
Number all pages at the bottom centre of the page
Include your course, name and student number as a header at the top of each page. Use 1.5
line spacing (other guides may prefer double spacing)
Use the Times New Roman font at either 11pt or 12pt size
Either have a line space between paragraphs or indent the first line of each Paragraph.
Marking Guide for Trainer:
Marking List Marks out of
60
Introduction /3
Data Gathering techniques /4
Network Requirement /5
Hardware and software configuration /5
Hardware and software Cost /4
Network Diagram – (should include Router/WAP, clients, and printers) /5
Topology /5
Configuration /10
Security Threat Detection and Testing /5
Backup plan /4
Sign off Form /3
Conclusions /2
Reference /2
Meeting Minutes /3
TOTAL /60
TABLE OF CONTENTS
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

T-1.8.1
Introduction:..........................................................................................................................................8
Data Gathering Techniques:..................................................................................................................8
Network Requirement:..........................................................................................................................9
Hardware and Software Configuration:...............................................................................................10
Hardware and Software Cost:..............................................................................................................12
Network Diagram – (Should include Router/WAP, Clients, and Printers)............................................12
Topology:.............................................................................................................................................13
Configuration:......................................................................................................................................13
IP Addressing scheme.........................................................................................................13
Suitable protocols to be used with the capabilities and features,...................................13
Internet (WAN) connection to be used...............................................................................13
Security Threat Detection and Testing:...............................................................................................13
Backup Plan:........................................................................................................................................14
Sign off Form:......................................................................................................................................15
Conclusions:.........................................................................................................................................15
References:..........................................................................................................................................16
Appendix-1..........................................................................................................................................17
Minutes of interview – Sydney Education Group..................................................................17
Appendix-2..........................................................................................................................................18
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 8
Introduction:..........................................................................................................................................8
Data Gathering Techniques:..................................................................................................................8
Network Requirement:..........................................................................................................................9
Hardware and Software Configuration:...............................................................................................10
Hardware and Software Cost:..............................................................................................................12
Network Diagram – (Should include Router/WAP, Clients, and Printers)............................................12
Topology:.............................................................................................................................................13
Configuration:......................................................................................................................................13
IP Addressing scheme.........................................................................................................13
Suitable protocols to be used with the capabilities and features,...................................13
Internet (WAN) connection to be used...............................................................................13
Security Threat Detection and Testing:...............................................................................................13
Backup Plan:........................................................................................................................................14
Sign off Form:......................................................................................................................................15
Conclusions:.........................................................................................................................................15
References:..........................................................................................................................................16
Appendix-1..........................................................................................................................................17
Minutes of interview – Sydney Education Group..................................................................17
Appendix-2..........................................................................................................................................18
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 8

T-1.8.1
Introduction:
The report is prepared for Sydney Education Group (SEG) for the development of a network solution
and connect its new office in Brisbane with the existing network infrastructure. An analysis is made on
the current needs of the network and identify the hardware and software needed for the development
of the network infrastructure. Different data gathering techniques are applied for finding the
requirement such as survey, brainstorming and stakeholder meetings for collecting the requirement
and set up the IT infrastructure following the budget and time constraints. Different hardware and
software are compared with each other based on its functionality and configuration that is needed to
meeting the needs of the organization [8]. The minimum configuration that is required is needed to be
analysed and an analysis is made on the cost of the hardware and software for the preparation of the
budget and complete the project within the allocated budget. A network diagram is prepared based on
the departments and number of users using the network and three layer hierarchical network topology
is selected such that the redundancy is increased. AN IP addressing plan is created based on the
number of hosts needed to be assigned with an IP address for configuration of the DHCP scope and
allocating IP to each of the devices connected in the network. An analysis is made on the security
threats acting on the network and testing is needed to be done that that the vulnerability of the
network is eliminated. A backup plan is created for the network such that no data is lost using the
network and the network can be configured with the previous working state in case of any error or
disaster.
Data Gathering Techniques:
The following are the two data gathering techniques discussed below:
Establishment of the project goals and objectives – In the early stage of the project the goals
and objectives is needed to be clearly stated such that it can be used as a guide to take future
decision. Stakeholder interviews can be used for reviewing the document and realizing that
the project would help in improving the business process.
Use of Questionnaires and brainstorming - Different types of question such as observational
question, reflective question, interpretative and decisional questions are needed to be
included in the questionnaires for performing the brainstorming and analyse the requirement
of the project [6]. It can also be used for performing a survey and documenting the
requirement.
The following are the sample questions that can be used for collecting the requirements:
What does the network remind you of?
What would we do differently for the development of the network?
What do we need to start, stop, or continue doing?
The answers of the questions helps in analysing the current needs of the users and develop the
network according to it. The current network problems can also be identified and it helps in
eliminating the problem for the new network.
The problems faced by the users can be documented such that it can be used for analysing the
risk and vulnerability and increase the efficiency of the new network solution.
For analysing the physical requirement as estimation is needed to be made for the number of
users and service that are needed to be enabled. For the implementation of the VOIP service a
service provider is needed to be selected providing both the data and VoIP service and the
routers are needed to be configured with QoS such that the user faces no lag in voice calls and
the channels of voice calls are free from collision and no data packets are lost in the network [4].
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 9
Introduction:
The report is prepared for Sydney Education Group (SEG) for the development of a network solution
and connect its new office in Brisbane with the existing network infrastructure. An analysis is made on
the current needs of the network and identify the hardware and software needed for the development
of the network infrastructure. Different data gathering techniques are applied for finding the
requirement such as survey, brainstorming and stakeholder meetings for collecting the requirement
and set up the IT infrastructure following the budget and time constraints. Different hardware and
software are compared with each other based on its functionality and configuration that is needed to
meeting the needs of the organization [8]. The minimum configuration that is required is needed to be
analysed and an analysis is made on the cost of the hardware and software for the preparation of the
budget and complete the project within the allocated budget. A network diagram is prepared based on
the departments and number of users using the network and three layer hierarchical network topology
is selected such that the redundancy is increased. AN IP addressing plan is created based on the
number of hosts needed to be assigned with an IP address for configuration of the DHCP scope and
allocating IP to each of the devices connected in the network. An analysis is made on the security
threats acting on the network and testing is needed to be done that that the vulnerability of the
network is eliminated. A backup plan is created for the network such that no data is lost using the
network and the network can be configured with the previous working state in case of any error or
disaster.
Data Gathering Techniques:
The following are the two data gathering techniques discussed below:
Establishment of the project goals and objectives – In the early stage of the project the goals
and objectives is needed to be clearly stated such that it can be used as a guide to take future
decision. Stakeholder interviews can be used for reviewing the document and realizing that
the project would help in improving the business process.
Use of Questionnaires and brainstorming - Different types of question such as observational
question, reflective question, interpretative and decisional questions are needed to be
included in the questionnaires for performing the brainstorming and analyse the requirement
of the project [6]. It can also be used for performing a survey and documenting the
requirement.
The following are the sample questions that can be used for collecting the requirements:
What does the network remind you of?
What would we do differently for the development of the network?
What do we need to start, stop, or continue doing?
The answers of the questions helps in analysing the current needs of the users and develop the
network according to it. The current network problems can also be identified and it helps in
eliminating the problem for the new network.
The problems faced by the users can be documented such that it can be used for analysing the
risk and vulnerability and increase the efficiency of the new network solution.
For analysing the physical requirement as estimation is needed to be made for the number of
users and service that are needed to be enabled. For the implementation of the VOIP service a
service provider is needed to be selected providing both the data and VoIP service and the
routers are needed to be configured with QoS such that the user faces no lag in voice calls and
the channels of voice calls are free from collision and no data packets are lost in the network [4].
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
T-1.8.1
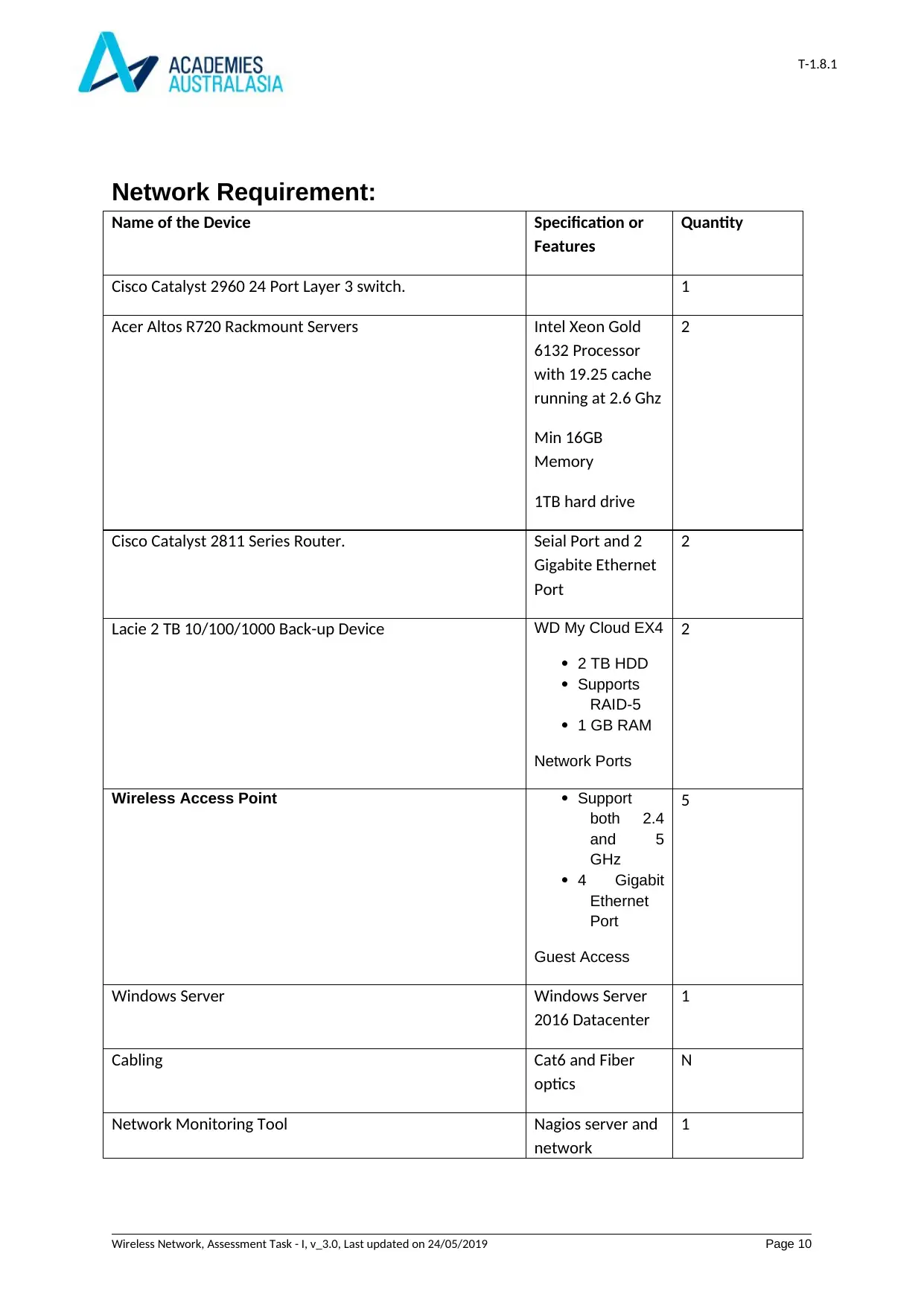
Network Requirement:
Name of the Device Specification or
Features
Quantity
Cisco Catalyst 2960 24 Port Layer 3 switch. 1
Acer Altos R720 Rackmount Servers Intel Xeon Gold
6132 Processor
with 19.25 cache
running at 2.6 Ghz
Min 16GB
Memory
1TB hard drive
2
Cisco Catalyst 2811 Series Router. Seial Port and 2
Gigabite Ethernet
Port
2
Lacie 2 TB 10/100/1000 Back-up Device WD My Cloud EX4
2 TB HDD
Supports
RAID-5
1 GB RAM
Network Ports
2
Wireless Access Point Support
both 2.4
and 5
GHz
4 Gigabit
Ethernet
Port
Guest Access
5
Windows Server Windows Server
2016 Datacenter
1
Cabling Cat6 and Fiber
optics
N
Network Monitoring Tool Nagios server and
network
1
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 10
Network Requirement:
Name of the Device Specification or
Features
Quantity
Cisco Catalyst 2960 24 Port Layer 3 switch. 1
Acer Altos R720 Rackmount Servers Intel Xeon Gold
6132 Processor
with 19.25 cache
running at 2.6 Ghz
Min 16GB
Memory
1TB hard drive
2
Cisco Catalyst 2811 Series Router. Seial Port and 2
Gigabite Ethernet
Port
2
Lacie 2 TB 10/100/1000 Back-up Device WD My Cloud EX4
2 TB HDD
Supports
RAID-5
1 GB RAM
Network Ports
2
Wireless Access Point Support
both 2.4
and 5
GHz
4 Gigabit
Ethernet
Port
Guest Access
5
Windows Server Windows Server
2016 Datacenter
1
Cabling Cat6 and Fiber
optics
N
Network Monitoring Tool Nagios server and
network
1
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
T-1.8.1
monitoring
Virus Protection McAfee Antivirus
2019
1
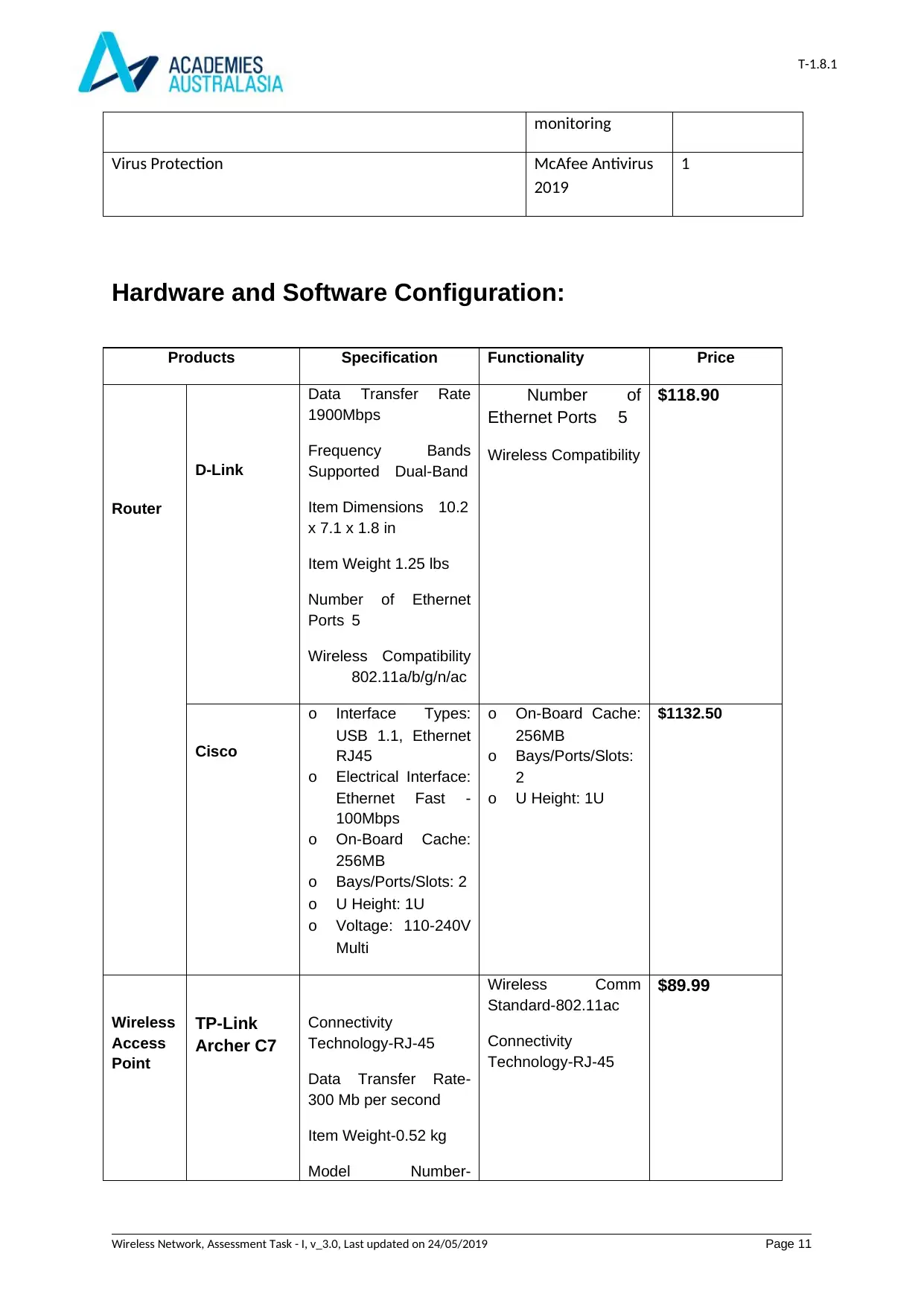
Hardware and Software Configuration:
Products Specification Functionality Price
Router
D-Link
Data Transfer Rate
1900Mbps
Frequency Bands
Supported Dual-Band
Item Dimensions 10.2
x 7.1 x 1.8 in
Item Weight 1.25 lbs
Number of Ethernet
Ports 5
Wireless Compatibility
802.11a/b/g/n/ac
Number of
Ethernet Ports 5
Wireless Compatibility
$118.90
Cisco
o Interface Types:
USB 1.1, Ethernet
RJ45
o Electrical Interface:
Ethernet Fast -
100Mbps
o On-Board Cache:
256MB
o Bays/Ports/Slots: 2
o U Height: 1U
o Voltage: 110-240V
Multi
o On-Board Cache:
256MB
o Bays/Ports/Slots:
2
o U Height: 1U
$1132.50
Wireless
Access
Point
TP-Link
Archer C7
Connectivity
Technology-RJ-45
Data Transfer Rate-
300 Mb per second
Item Weight-0.52 kg
Model Number-
Wireless Comm
Standard-802.11ac
Connectivity
Technology-RJ-45
$89.99
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 11
monitoring
Virus Protection McAfee Antivirus
2019
1
Hardware and Software Configuration:
Products Specification Functionality Price
Router
D-Link
Data Transfer Rate
1900Mbps
Frequency Bands
Supported Dual-Band
Item Dimensions 10.2
x 7.1 x 1.8 in
Item Weight 1.25 lbs
Number of Ethernet
Ports 5
Wireless Compatibility
802.11a/b/g/n/ac
Number of
Ethernet Ports 5
Wireless Compatibility
$118.90
Cisco
o Interface Types:
USB 1.1, Ethernet
RJ45
o Electrical Interface:
Ethernet Fast -
100Mbps
o On-Board Cache:
256MB
o Bays/Ports/Slots: 2
o U Height: 1U
o Voltage: 110-240V
Multi
o On-Board Cache:
256MB
o Bays/Ports/Slots:
2
o U Height: 1U
$1132.50
Wireless
Access
Point
TP-Link
Archer C7
Connectivity
Technology-RJ-45
Data Transfer Rate-
300 Mb per second
Item Weight-0.52 kg
Model Number-
Wireless Comm
Standard-802.11ac
Connectivity
Technology-RJ-45
$89.99
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 11
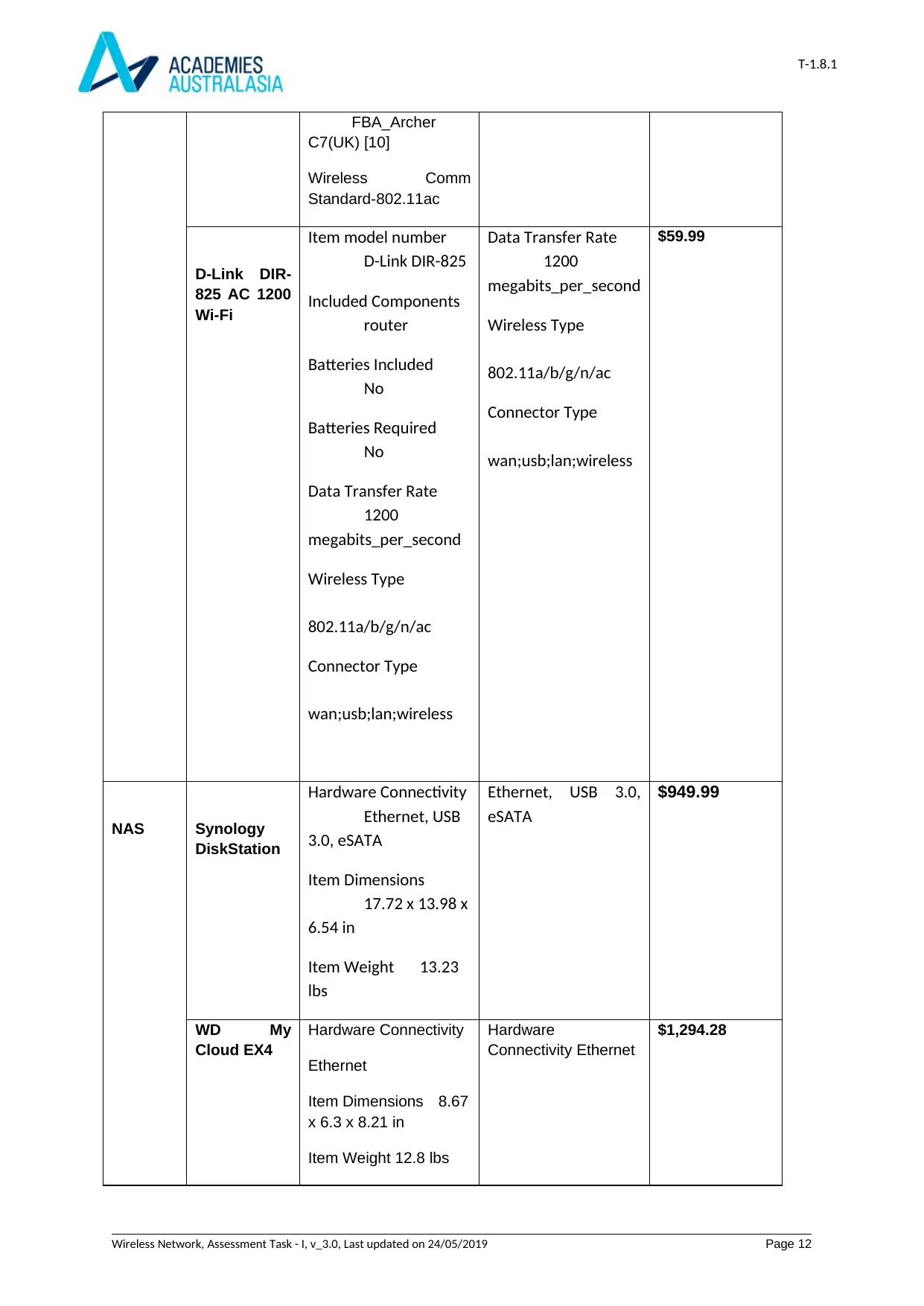
T-1.8.1
FBA_Archer
C7(UK) [10]
Wireless Comm
Standard-802.11ac
D-Link DIR-
825 AC 1200
Wi-Fi
Item model number
D-Link DIR-825
Included Components
router
Batteries Included
No
Batteries Required
No
Data Transfer Rate
1200
megabits_per_second
Wireless Type
802.11a/b/g/n/ac
Connector Type
wan;usb;lan;wireless
Data Transfer Rate
1200
megabits_per_second
Wireless Type
802.11a/b/g/n/ac
Connector Type
wan;usb;lan;wireless
$59.99
NAS Synology
DiskStation
Hardware Connectivity
Ethernet, USB
3.0, eSATA
Item Dimensions
17.72 x 13.98 x
6.54 in
Item Weight 13.23
lbs
Ethernet, USB 3.0,
eSATA
$949.99
WD My
Cloud EX4
Hardware Connectivity
Ethernet
Item Dimensions 8.67
x 6.3 x 8.21 in
Item Weight 12.8 lbs
Hardware
Connectivity Ethernet
$1,294.28
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 12
FBA_Archer
C7(UK) [10]
Wireless Comm
Standard-802.11ac
D-Link DIR-
825 AC 1200
Wi-Fi
Item model number
D-Link DIR-825
Included Components
router
Batteries Included
No
Batteries Required
No
Data Transfer Rate
1200
megabits_per_second
Wireless Type
802.11a/b/g/n/ac
Connector Type
wan;usb;lan;wireless
Data Transfer Rate
1200
megabits_per_second
Wireless Type
802.11a/b/g/n/ac
Connector Type
wan;usb;lan;wireless
$59.99
NAS Synology
DiskStation
Hardware Connectivity
Ethernet, USB
3.0, eSATA
Item Dimensions
17.72 x 13.98 x
6.54 in
Item Weight 13.23
lbs
Ethernet, USB 3.0,
eSATA
$949.99
WD My
Cloud EX4
Hardware Connectivity
Ethernet
Item Dimensions 8.67
x 6.3 x 8.21 in
Item Weight 12.8 lbs
Hardware
Connectivity Ethernet
$1,294.28
Wireless Network, Assessment Task - I, v_3.0, Last updated on 24/05/2019 Page 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




