Logical Design and Cloud Services for Xero Sydney Branch Network
VerifiedAdded on 2021/01/02
|16
|3076
|159
Report
AI Summary
This report provides a comprehensive analysis of the network infrastructure designed for Xero's Sydney branch. It begins with an introduction to the importance of IT infrastructure in modern businesses, specifically focusing on the Xero company. The main body of the report details the geographical scope of the network, which includes a mix of LAN and CAN architectures to connect 240 computer systems across an 8-floor building. It then presents a three-layered hierarchical model (core, distribution, and access layers) for the network's logical design, identifying the key network devices, including servers, routers, switches, and firewalls. The report also explains the IP addressing and subnet masking configurations used. Furthermore, it discusses two cloud service providers, Amazon Web Services (AWS) and Google Cloud Platform, evaluating their services for email and web hosting, and justifying their suitability for Xero's needs. The report also covers virtualization techniques and dynamic scaling supported by cloud computing. Overall, this report provides insights into building an effective and efficient IT infrastructure for Xero's Sydney branch, supporting its operational needs with scalability and security.

Proposal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
1. Geographical scope of the network developed within Xero company established in Sydney 1
2. Logical design for the Sydney branch which is based on three layered architecture. Also
identify the network devices and server used in development of the networking infrastructure 2
3. Identify the IP addresses with the subnet masks used for network configuration...................3
4. Discuss about the two organisations that provides cloud services for hosting the email and
wed services of company . Justify the answer explaining the level of services each company
provide that suits..........................................................................................................................3
5. Discuss about the technique of using the virtualisation service in supporting and
implementing the cloud platform.................................................................................................6
6. Dynamic scaling which is supported by cloud computing......................................................7
CONCLUSION................................................................................................................................7
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
1. Geographical scope of the network developed within Xero company established in Sydney 1
2. Logical design for the Sydney branch which is based on three layered architecture. Also
identify the network devices and server used in development of the networking infrastructure 2
3. Identify the IP addresses with the subnet masks used for network configuration...................3
4. Discuss about the two organisations that provides cloud services for hosting the email and
wed services of company . Justify the answer explaining the level of services each company
provide that suits..........................................................................................................................3
5. Discuss about the technique of using the virtualisation service in supporting and
implementing the cloud platform.................................................................................................6
6. Dynamic scaling which is supported by cloud computing......................................................7
CONCLUSION................................................................................................................................7

INTRODUCTION
In today's modernised world, Technology have transformed the human creative world
into the automatised world. IT infrastructure within the industry one of the important aspect
nowadays, which helps in improving the productivity and efficiency of the business. This report
will be based on the networking infrastructure of the Xero company which is going to develop its
new branch within Sydney. This report will assist the organization in developing a effective IT
infrastructure for the company in order to improve the overall performance. This study will
provide logical design of the networking infrastructure within the Xero company which is newly
established in Australia.
Furthermore, it will create a complete knowledge about the service provider which fulfils
various data manipulation requirements of the users. This document also helps in determining the
geographical range of network design which supports the communication and interaction within
the systems situated within 8 floor building. Moreover, It will also help in identifying the IP
addresses and subnet masking in order to configure the systems within the industry. Various
virtualisation techniques are also identified here along with the dynamic scaling which is
supported by cloud computing.
MAIN BODY
1. Geographical scope of the network developed within Xero company established in Sydney
Geographical scope of networking can be termed as a range within which the computer
systems can interact with each other in order to meet the specific goal of the Xero company
Sydney branch. The scope of the network is referred to its geographical size. A network can
range in size from just a few computers to the thousands of computers linked together for the
main purpose of interconnectivity (Dijkhuizen Ham,2018). Networking is generally classified
under different types of categories such as LAN, MAN, CAN, WAN etc.
Sydney branch of the Xero company wants to establish a interconnectivity between 240
computer systems which are placed in the building of 8 floor. In order to connect the computer
devices with each other which can be further connected to the main server which controls all the
information of the company. Sydney branch of Xero organization uses mix architecture that is
LAN (Local area Network) and CAN (Campus area network) for providing the interconnectivity
within the 8 floored building. According to the given diagram, the network is divided into four
Local Area Network which connects the compute systems of the Two floors together in order to
1
In today's modernised world, Technology have transformed the human creative world
into the automatised world. IT infrastructure within the industry one of the important aspect
nowadays, which helps in improving the productivity and efficiency of the business. This report
will be based on the networking infrastructure of the Xero company which is going to develop its
new branch within Sydney. This report will assist the organization in developing a effective IT
infrastructure for the company in order to improve the overall performance. This study will
provide logical design of the networking infrastructure within the Xero company which is newly
established in Australia.
Furthermore, it will create a complete knowledge about the service provider which fulfils
various data manipulation requirements of the users. This document also helps in determining the
geographical range of network design which supports the communication and interaction within
the systems situated within 8 floor building. Moreover, It will also help in identifying the IP
addresses and subnet masking in order to configure the systems within the industry. Various
virtualisation techniques are also identified here along with the dynamic scaling which is
supported by cloud computing.
MAIN BODY
1. Geographical scope of the network developed within Xero company established in Sydney
Geographical scope of networking can be termed as a range within which the computer
systems can interact with each other in order to meet the specific goal of the Xero company
Sydney branch. The scope of the network is referred to its geographical size. A network can
range in size from just a few computers to the thousands of computers linked together for the
main purpose of interconnectivity (Dijkhuizen Ham,2018). Networking is generally classified
under different types of categories such as LAN, MAN, CAN, WAN etc.
Sydney branch of the Xero company wants to establish a interconnectivity between 240
computer systems which are placed in the building of 8 floor. In order to connect the computer
devices with each other which can be further connected to the main server which controls all the
information of the company. Sydney branch of Xero organization uses mix architecture that is
LAN (Local area Network) and CAN (Campus area network) for providing the interconnectivity
within the 8 floored building. According to the given diagram, the network is divided into four
Local Area Network which connects the compute systems of the Two floors together in order to
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
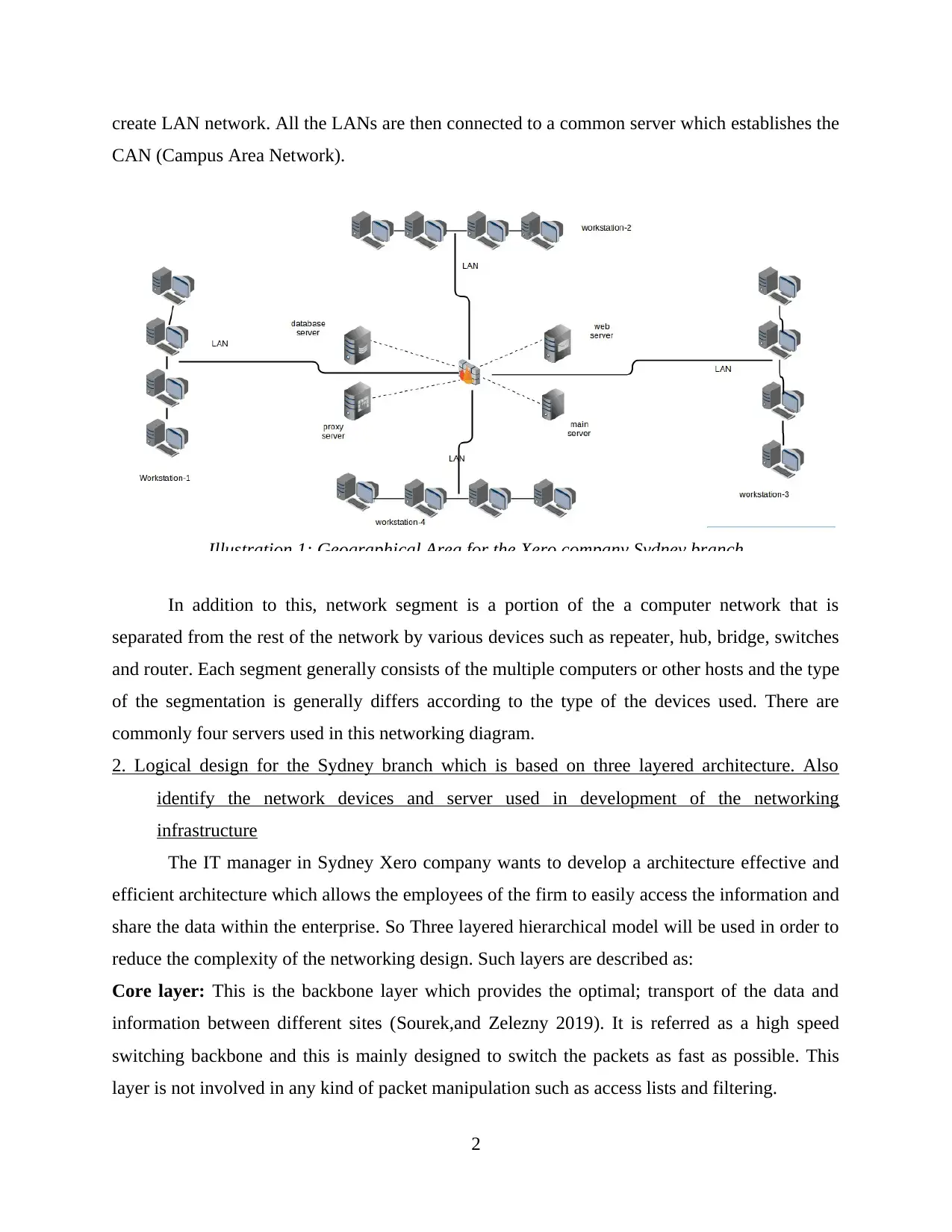
create LAN network. All the LANs are then connected to a common server which establishes the
CAN (Campus Area Network).
In addition to this, network segment is a portion of the a computer network that is
separated from the rest of the network by various devices such as repeater, hub, bridge, switches
and router. Each segment generally consists of the multiple computers or other hosts and the type
of the segmentation is generally differs according to the type of the devices used. There are
commonly four servers used in this networking diagram.
2. Logical design for the Sydney branch which is based on three layered architecture. Also
identify the network devices and server used in development of the networking
infrastructure
The IT manager in Sydney Xero company wants to develop a architecture effective and
efficient architecture which allows the employees of the firm to easily access the information and
share the data within the enterprise. So Three layered hierarchical model will be used in order to
reduce the complexity of the networking design. Such layers are described as:
Core layer: This is the backbone layer which provides the optimal; transport of the data and
information between different sites (Sourek,and Zelezny 2019). It is referred as a high speed
switching backbone and this is mainly designed to switch the packets as fast as possible. This
layer is not involved in any kind of packet manipulation such as access lists and filtering.
2
Illustration 1: Geographical Area for the Xero company Sydney branch
CAN (Campus Area Network).
In addition to this, network segment is a portion of the a computer network that is
separated from the rest of the network by various devices such as repeater, hub, bridge, switches
and router. Each segment generally consists of the multiple computers or other hosts and the type
of the segmentation is generally differs according to the type of the devices used. There are
commonly four servers used in this networking diagram.
2. Logical design for the Sydney branch which is based on three layered architecture. Also
identify the network devices and server used in development of the networking
infrastructure
The IT manager in Sydney Xero company wants to develop a architecture effective and
efficient architecture which allows the employees of the firm to easily access the information and
share the data within the enterprise. So Three layered hierarchical model will be used in order to
reduce the complexity of the networking design. Such layers are described as:
Core layer: This is the backbone layer which provides the optimal; transport of the data and
information between different sites (Sourek,and Zelezny 2019). It is referred as a high speed
switching backbone and this is mainly designed to switch the packets as fast as possible. This
layer is not involved in any kind of packet manipulation such as access lists and filtering.
2
Illustration 1: Geographical Area for the Xero company Sydney branch
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Distributed layer: This is demarcation point between the access and core layer which helps in
differentiating the access and core layer. This layer is mainly aimed at providing the bpoudary
definition which may involve in packet manipulation.
Access layer: This can be considered as a point at which local end users are allowed to interrupt
into the entwork. This layer is involved in providing the remote sites access to corporate network
via internet.
Required networking device used in designing the network for Xero Sydney branch are
Computer systems, printers, four different types of servers and one centralised server. Along
with this routers, switches and hub are also used for the proper transmission of the data from
source to the appropriate destination along with the secured way. However, IT manager of the
company has also used the Firewall for the security purpose which restricts the authorisation of
the users in gaining access to the confidential data. Although, there are many servers used in this
network such as Dynamic Host control protocol, file server, print server, Domain name server
etc in order top control the file printing actions.
3
Illustration 2: Logical Diagram interface for the networking
differentiating the access and core layer. This layer is mainly aimed at providing the bpoudary
definition which may involve in packet manipulation.
Access layer: This can be considered as a point at which local end users are allowed to interrupt
into the entwork. This layer is involved in providing the remote sites access to corporate network
via internet.
Required networking device used in designing the network for Xero Sydney branch are
Computer systems, printers, four different types of servers and one centralised server. Along
with this routers, switches and hub are also used for the proper transmission of the data from
source to the appropriate destination along with the secured way. However, IT manager of the
company has also used the Firewall for the security purpose which restricts the authorisation of
the users in gaining access to the confidential data. Although, there are many servers used in this
network such as Dynamic Host control protocol, file server, print server, Domain name server
etc in order top control the file printing actions.
3
Illustration 2: Logical Diagram interface for the networking
3. Identify the IP addresses with the subnet masks used for network configuration
IP addresses is a dotted decimal notation which is 4 sets of numbers separated space.
Each set generally represents the 8-bit number ranging from 0-255 (Liand et.al., 2019). This is
the main aspect fo configuring the network server for a web site. It is a logical numeric address
assigned to every single computer, printer, Ethernet, router, switch or device based on TCP/IP
network.
Subnetting is the process of dividing the large network of Xero Sydney branch into
smaller sub-networks (Subnets). IP address helps in identifying the subnets which is more
efficient practice as it creates smaller broadcast and generates less traffic.
Address class Number of
network bits
Number of Host
bits
Subnet mask CIDR Notation
C 24 8 255.255.255.0 /24
C 25 7 255.255.255.240 /25
C 28 4 255.255.255.240 /28
C 30 2 255.255.255.252 /30
4. Discuss about the two organisations that provides cloud services for hosting the email and wed
services of company . Justify the answer explaining the level of services each company
provide that suits.
Cloud services are the important part of network development which made available to
the users on the demand by using internet from the cloud computing service provider. It always
opposed to being provide from the XERO firm on premises servers. Cloud services are covered
the wide range of important resources that service provider delivers to the customer. The usage
of service has become associated with the common cloud offering facilities such as Software as a
service and platform as a service (Bennett, Ward and Robertson, 2018). Web services and
hosting are necessary concept that support the entire infrastructure to maintain and control the
data in proper manner.
Amazon web service:
Amazon web service is the fastest and protected platform of cloud service which offered
different type of infrastructure facilities such as computing power, database storage, networking
etc. This type of service provide the host in the static websites. In this way, user can easily build
4
IP addresses is a dotted decimal notation which is 4 sets of numbers separated space.
Each set generally represents the 8-bit number ranging from 0-255 (Liand et.al., 2019). This is
the main aspect fo configuring the network server for a web site. It is a logical numeric address
assigned to every single computer, printer, Ethernet, router, switch or device based on TCP/IP
network.
Subnetting is the process of dividing the large network of Xero Sydney branch into
smaller sub-networks (Subnets). IP address helps in identifying the subnets which is more
efficient practice as it creates smaller broadcast and generates less traffic.
Address class Number of
network bits
Number of Host
bits
Subnet mask CIDR Notation
C 24 8 255.255.255.0 /24
C 25 7 255.255.255.240 /25
C 28 4 255.255.255.240 /28
C 30 2 255.255.255.252 /30
4. Discuss about the two organisations that provides cloud services for hosting the email and wed
services of company . Justify the answer explaining the level of services each company
provide that suits.
Cloud services are the important part of network development which made available to
the users on the demand by using internet from the cloud computing service provider. It always
opposed to being provide from the XERO firm on premises servers. Cloud services are covered
the wide range of important resources that service provider delivers to the customer. The usage
of service has become associated with the common cloud offering facilities such as Software as a
service and platform as a service (Bennett, Ward and Robertson, 2018). Web services and
hosting are necessary concept that support the entire infrastructure to maintain and control the
data in proper manner.
Amazon web service:
Amazon web service is the fastest and protected platform of cloud service which offered
different type of infrastructure facilities such as computing power, database storage, networking
etc. This type of service provide the host in the static websites. In this way, user can easily build
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the complicated application that are trustworthy, flexible and scalable. Amazon web service
started to offer the various type of service in marketplace. It is also known as cloud computing
service. It doesn't required any plan for server and other Information techniques infrastructure
which takes up time advance (Kumar and Kushwaha, 2018). Instead, this service is increasing
the demand in marketplace. In marketplace, The Amazon EC2 container service enables the
customer to work with the docker container on the AWS platform. Developer can use this service
for the server less functions that automatically run the code for applications and services.
Data Management-
Amazon web service has provided to manage the database service through the Amazon
relational database which includes the different type of options such as MySQL, SQL server and
Oracle etc. this system has high performance database Amazon Aurora that offers the facilities to
manage the DBMS.
Networking-
Amazon circuital cloud provide an administrator to control or manage the overall virtual
network that easily isolated the sections of AWS cloud. It is automatically provisions the new
resources within the VPC for extra protection. The professional has established a connection
from on premises data centre into the Amazon direct cloud. It help to balance the traffic of
network by using AWS balancing tools such as network load balancer and application load
balancer.
Security and governance-
This service has provided a wide range of service regarding cloud security which include
the identity and management access. It allows the admin to define or easily manage the user
access through resources. An administration has created a user directory with the cloud directory
and connect cloud resources for an existing active drive within the AWS services.
Google cloud platform services:
Google cloud platform is a type of cloud service for the purpose of hosting that should
integrate with the storage used by the developer and enterprises for the managing the live data.
This type of service available in market at various flexible payment plan which based on the pay
as you go. Google cloud platform services can easily access by the developer, administrator and
other professional over the internet. They provide different type of services such as storage, big
data, machine learning and internet of things.
5
started to offer the various type of service in marketplace. It is also known as cloud computing
service. It doesn't required any plan for server and other Information techniques infrastructure
which takes up time advance (Kumar and Kushwaha, 2018). Instead, this service is increasing
the demand in marketplace. In marketplace, The Amazon EC2 container service enables the
customer to work with the docker container on the AWS platform. Developer can use this service
for the server less functions that automatically run the code for applications and services.
Data Management-
Amazon web service has provided to manage the database service through the Amazon
relational database which includes the different type of options such as MySQL, SQL server and
Oracle etc. this system has high performance database Amazon Aurora that offers the facilities to
manage the DBMS.
Networking-
Amazon circuital cloud provide an administrator to control or manage the overall virtual
network that easily isolated the sections of AWS cloud. It is automatically provisions the new
resources within the VPC for extra protection. The professional has established a connection
from on premises data centre into the Amazon direct cloud. It help to balance the traffic of
network by using AWS balancing tools such as network load balancer and application load
balancer.
Security and governance-
This service has provided a wide range of service regarding cloud security which include
the identity and management access. It allows the admin to define or easily manage the user
access through resources. An administration has created a user directory with the cloud directory
and connect cloud resources for an existing active drive within the AWS services.
Google cloud platform services:
Google cloud platform is a type of cloud service for the purpose of hosting that should
integrate with the storage used by the developer and enterprises for the managing the live data.
This type of service available in market at various flexible payment plan which based on the pay
as you go. Google cloud platform services can easily access by the developer, administrator and
other professional over the internet. They provide different type of services such as storage, big
data, machine learning and internet of things.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Artificial intelligence-
For instances, Good cloud service offers the machine learning engine that help to manage
the service. It also enables users to build strong learning model to handle different type of
operations and functions. This service is evolving, change and introduce on the demand of user
as well as high competitive pressure.
Big data processing-
Big data service is mainly included the data processing, analytics such as big query which
made against the multi terabyte data data sets. It intend to process for analytics, extract and load
for real time computational projects. It hosting the online service to secure their information
through the cloud computing.
5. Discuss about the technique of using the virtualisation service in supporting and implementing
the cloud platform
Virtualisation is basically type of process that create virtual version which included the
computer hardware computer network and storage devices etc. virtualisation is playing important
role in cloud for creating of virtual server, devices, infrastructure and other resources. It has
ability to run different type of operating system at same hardware (Mondesire and et.al., 2019).
It can be divided into different type of virtualisation technique that support the cloud services in
proper manner.
Network virtualisation-
It is a type of method that combine with the available resources in the network system by
separated in the available bandwidth into the multiple channels. It can be assigned to the
particular sever at real time operations. This technology help to manage the complexity of
network system in proper manner.
Storage Virtualising-
this technique is provided the facility to user for managing the space of hardware system
from the several interconnected storage device into the single storage device (Prakash, 2019).
This type of storage technique basically used for the storage area networks. It also manipulating
in the cloud mostly useful for backup, recovering and archiving etc.
Server Virtualisation-
6
For instances, Good cloud service offers the machine learning engine that help to manage
the service. It also enables users to build strong learning model to handle different type of
operations and functions. This service is evolving, change and introduce on the demand of user
as well as high competitive pressure.
Big data processing-
Big data service is mainly included the data processing, analytics such as big query which
made against the multi terabyte data data sets. It intend to process for analytics, extract and load
for real time computational projects. It hosting the online service to secure their information
through the cloud computing.
5. Discuss about the technique of using the virtualisation service in supporting and implementing
the cloud platform
Virtualisation is basically type of process that create virtual version which included the
computer hardware computer network and storage devices etc. virtualisation is playing important
role in cloud for creating of virtual server, devices, infrastructure and other resources. It has
ability to run different type of operating system at same hardware (Mondesire and et.al., 2019).
It can be divided into different type of virtualisation technique that support the cloud services in
proper manner.
Network virtualisation-
It is a type of method that combine with the available resources in the network system by
separated in the available bandwidth into the multiple channels. It can be assigned to the
particular sever at real time operations. This technology help to manage the complexity of
network system in proper manner.
Storage Virtualising-
this technique is provided the facility to user for managing the space of hardware system
from the several interconnected storage device into the single storage device (Prakash, 2019).
This type of storage technique basically used for the storage area networks. It also manipulating
in the cloud mostly useful for backup, recovering and archiving etc.
Server Virtualisation-
6

This technique is based on the physical servers which simulates server by changing their
processor, identify and operating system. In this way, user continuously managing the complex
server resources and make lot of resources required for sharing or utilising.
Data Virtualisation-
This type of cloud computing virtualisation technique is mainly abstracting the technical
details which usually used the data management of performance and location. It is important
technique that help for XERO Firm to manage and store their data in an appropriate manner.
Desktop Virtualisation-
This type of technique enables to emulate a load of workstation than the server. It allows
for user to access the desktop through remotely (Sun and et.al., 2018). Each and Every work
stations are necessary running in the data centre server which access to both more secure and
portable. This type of technique is using to control the overall functionality of desktop system in
proper manner.
Application Virtualisation-
The application virtualisation is a type of software in cloud computing abstract of the
application layer which separated it from the other operating system (Suratno and et.al., 2018). It
is the best ways to determine that application can run in the form of encapsulated with out being
independent. It is providing the level of isolation and application created for the operating system
which are completely run from different operating system in proper ways.
6. Dynamic scaling which is supported by cloud computing.
Cloud computing is a powerful tool which enables the user to access the resource on
demand in Which dynamic scaling helps in creating the virtualised storage for the users.
Dynamic scaling of web applications in a virtualised cloud environment helps in providing the
ability to grow or shrink the infrastructure resource dynamically as needed to adopt workload
changes in an autocratic manner (Abrarand et.al., 2018). It also maximises the uses of resources.
It enables the users for Pay-per-use or pay-as-you-grow services.
CONCLUSION
As per discussion, it concluded that cloud computing is modern technology that help for
storage the data through devices. It is based on the networking infrastructure of the Xero which
is going to develop its new branch within Sydney. It also discuss about the organization in
developing a effective IT infrastructure to improve the overall performance. It summarised that
7
processor, identify and operating system. In this way, user continuously managing the complex
server resources and make lot of resources required for sharing or utilising.
Data Virtualisation-
This type of cloud computing virtualisation technique is mainly abstracting the technical
details which usually used the data management of performance and location. It is important
technique that help for XERO Firm to manage and store their data in an appropriate manner.
Desktop Virtualisation-
This type of technique enables to emulate a load of workstation than the server. It allows
for user to access the desktop through remotely (Sun and et.al., 2018). Each and Every work
stations are necessary running in the data centre server which access to both more secure and
portable. This type of technique is using to control the overall functionality of desktop system in
proper manner.
Application Virtualisation-
The application virtualisation is a type of software in cloud computing abstract of the
application layer which separated it from the other operating system (Suratno and et.al., 2018). It
is the best ways to determine that application can run in the form of encapsulated with out being
independent. It is providing the level of isolation and application created for the operating system
which are completely run from different operating system in proper ways.
6. Dynamic scaling which is supported by cloud computing.
Cloud computing is a powerful tool which enables the user to access the resource on
demand in Which dynamic scaling helps in creating the virtualised storage for the users.
Dynamic scaling of web applications in a virtualised cloud environment helps in providing the
ability to grow or shrink the infrastructure resource dynamically as needed to adopt workload
changes in an autocratic manner (Abrarand et.al., 2018). It also maximises the uses of resources.
It enables the users for Pay-per-use or pay-as-you-grow services.
CONCLUSION
As per discussion, it concluded that cloud computing is modern technology that help for
storage the data through devices. It is based on the networking infrastructure of the Xero which
is going to develop its new branch within Sydney. It also discuss about the organization in
developing a effective IT infrastructure to improve the overall performance. It summarised that
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the logical design of the networking infrastructure within the Xero company which is newly
established in Australia. Furthermore, this report is also describing the geographical range of
network design which supports the communication and interaction within the systems situated
within 8 floor building. It is determine the IP addresses and subnet masking in order to configure
the systems within the industry.
8
established in Australia. Furthermore, this report is also describing the geographical range of
network design which supports the communication and interaction within the systems situated
within 8 floor building. It is determine the IP addresses and subnet masking in order to configure
the systems within the industry.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and Journals
Bennett, K.W., Ward, D.W. and Robertson, J., 2018, May. Cloud-based security architecture
supporting Army Research Laboratory's collaborative research environments. In
Ground/Air Multisensor Interoperability, Integration, and Networking for Persistent ISR
IX (Vol. 10635, p. 106350G). International Society for Optics and Photonics.
Kumar, S. and Kushwaha, A.S., 2018, August. Virtualization Backbone of Cloud Computing-
Analysis. In 2018 4th International Conference on Computing Sciences (ICCS) (pp. 35-
39). IEEE.
Mondesire, S.C. and et.al., 2019. Combining virtualization and containerization to support
interactive games and simulations on the cloud. Simulation Modelling Practice and
Theory, 93, pp.233-244.
Prakash, S., 2019. Role of Virtualization Techniques in Cloud Computing Environment. In
Advances in Computer Communication and Computational Sciences (pp. 439-450).
Springer, Singapore.
Sun, J. and et.al., 2018, March. The Research for Virtualization Network Security on Cloud
Computing. In 2018 2nd International Conference on Artificial Intelligence:
Technologies and Applications (ICAITA 2018). Atlantis Press.
Suratno, B. and et.al., 2018, July. A method for operationalizing service-dominant business
models into conceptual process models. In International Symposium on Business
Modeling and Software Design (pp. 133-148). Springer, Cham.
Dijkhuizen, N.V. and Ham, J.V.D., 2018. A Survey of Network Traffic Anonymisation
Techniques and Implementations. ACM Computing Surveys (CSUR). 51(3). p.52.
Sourek, G. and Zelezny, F., 2019. Efficient Extraction of Network Event Types from NetFlows.
Security and Communication Networks. 2019.
Li, Z. and et.al., 2019. A Quantitative and Comparative Study of Network-Level Efficiency for
Cloud Storage Services. ACM Transactions on Modeling and Performance Evaluation of
Computing Systems (TOMPECS). 4(1). p.3.
Abrar, M. and et.al., 2018, February. Real time smart grid load management by integrated and
secured communication. In 2018 International Conference on Innovative Trends in
Computer Engineering (ITCE) (pp. 253-257). IEEE.
9
Books and Journals
Bennett, K.W., Ward, D.W. and Robertson, J., 2018, May. Cloud-based security architecture
supporting Army Research Laboratory's collaborative research environments. In
Ground/Air Multisensor Interoperability, Integration, and Networking for Persistent ISR
IX (Vol. 10635, p. 106350G). International Society for Optics and Photonics.
Kumar, S. and Kushwaha, A.S., 2018, August. Virtualization Backbone of Cloud Computing-
Analysis. In 2018 4th International Conference on Computing Sciences (ICCS) (pp. 35-
39). IEEE.
Mondesire, S.C. and et.al., 2019. Combining virtualization and containerization to support
interactive games and simulations on the cloud. Simulation Modelling Practice and
Theory, 93, pp.233-244.
Prakash, S., 2019. Role of Virtualization Techniques in Cloud Computing Environment. In
Advances in Computer Communication and Computational Sciences (pp. 439-450).
Springer, Singapore.
Sun, J. and et.al., 2018, March. The Research for Virtualization Network Security on Cloud
Computing. In 2018 2nd International Conference on Artificial Intelligence:
Technologies and Applications (ICAITA 2018). Atlantis Press.
Suratno, B. and et.al., 2018, July. A method for operationalizing service-dominant business
models into conceptual process models. In International Symposium on Business
Modeling and Software Design (pp. 133-148). Springer, Cham.
Dijkhuizen, N.V. and Ham, J.V.D., 2018. A Survey of Network Traffic Anonymisation
Techniques and Implementations. ACM Computing Surveys (CSUR). 51(3). p.52.
Sourek, G. and Zelezny, F., 2019. Efficient Extraction of Network Event Types from NetFlows.
Security and Communication Networks. 2019.
Li, Z. and et.al., 2019. A Quantitative and Comparative Study of Network-Level Efficiency for
Cloud Storage Services. ACM Transactions on Modeling and Performance Evaluation of
Computing Systems (TOMPECS). 4(1). p.3.
Abrar, M. and et.al., 2018, February. Real time smart grid load management by integrated and
secured communication. In 2018 International Conference on Innovative Trends in
Computer Engineering (ITCE) (pp. 253-257). IEEE.
9

10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





