System Administration: Linux vs Windows, Server Roles & Directory
VerifiedAdded on 2023/05/27
|9
|1379
|138
Report
AI Summary
This report provides a detailed comparison of Linux and Windows operating systems within the context of system administration for Rogue Construction Company. It outlines the key differences in file systems, permissions, and security practices between the two platforms, emphasizing the importance of data security measures such as role-based access control and data recovery strategies. The report also details the proposed server infrastructure for the company, including application, web, database, email, and DHCP/DNS servers, specifying their roles, locations, and system requirements. Furthermore, it discusses the implementation of directory services using Active Directory, highlighting its benefits for centralized security and resource management, with a proposed deployment across the main office and construction site. The document includes updated network diagrams and references to support the analysis and recommendations. Desklib offers a wide array of study resources, including past papers and solved assignments, to aid students in their learning journey.

WEEK 2: SYSTEM ADMINISTRATION
(Student’s Name)
(Professor’s name)
(Course)
(Date)
(Student’s Name)
(Professor’s name)
(Course)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
In week one, as a network manager, I was able to set up Rouge Construction company a
network infrastructure. In addition to this, I was able to choose the best storage option for the
organization where I settled for cloud-based and network attached. Also in week one through a
diagram, I was able to deploy a hierarchical model for the construction Company. In this week,
this paper will give an overview of Linux and windows operating system. Second, the paper will
be updating the existing corporate infrastructure diagram which include server roles where I will
provide an updated labelled diagram. Third, this paper will highlight on directory services where
I will show how the organization need to go about installing the appropriate directory services
and how it would be deployed.
Part A
Linux vs. Windows
Linux file systems are a little bit different than permissions in Microsoft. The file system
in Linux what computer scientists refer to as POSIX standard; this means that every directory
and file is owned by both a group and a user i.e. each and every user is has a primary group
membership; where file created by every user the user who created is automatically given that
ownership. Second, in linux every file has an information node (inode) which store information
about that file which includes even the last modified file, ownership, file size, permissions, and
data block location. Lastly, there are three types of permissions in linux which are group owner
permission, everyone on the Linux system permissions, and owner permission. Windows OS on
the other hand takes its permissions to the extreme where every file can have permissions
assigned to it for any number of groups and any number of users. NTFS permission is the
common type of permission used in windows.
In week one, as a network manager, I was able to set up Rouge Construction company a
network infrastructure. In addition to this, I was able to choose the best storage option for the
organization where I settled for cloud-based and network attached. Also in week one through a
diagram, I was able to deploy a hierarchical model for the construction Company. In this week,
this paper will give an overview of Linux and windows operating system. Second, the paper will
be updating the existing corporate infrastructure diagram which include server roles where I will
provide an updated labelled diagram. Third, this paper will highlight on directory services where
I will show how the organization need to go about installing the appropriate directory services
and how it would be deployed.
Part A
Linux vs. Windows
Linux file systems are a little bit different than permissions in Microsoft. The file system
in Linux what computer scientists refer to as POSIX standard; this means that every directory
and file is owned by both a group and a user i.e. each and every user is has a primary group
membership; where file created by every user the user who created is automatically given that
ownership. Second, in linux every file has an information node (inode) which store information
about that file which includes even the last modified file, ownership, file size, permissions, and
data block location. Lastly, there are three types of permissions in linux which are group owner
permission, everyone on the Linux system permissions, and owner permission. Windows OS on
the other hand takes its permissions to the extreme where every file can have permissions
assigned to it for any number of groups and any number of users. NTFS permission is the
common type of permission used in windows.

Permissions exists in two ways inherited permissions and explicit permissions. Inherited
permissions are those permissions which are given to an object as it is a child of a parent while
explicit permission are permission which is set by default when an object is created by the user
action. Those permissions which are inherited from near relatives usually take precedence over
permissions which are inherited from distant predecessors.
NTFS permission in windows are used to manage folders and files which are stored in
NTFS file systems. Share permissions in windows determine the permissions which are set for a
certain folder when one shares the folder while NTFS determine the actions that users take for a
certain file or folder both locally and on the organization network. This permissions still apply
when access files from Linux to windows but when using windows to access Linux permissions
will apply where there are three types of permissions i.e. read, write and execute. Data security is
paramount and as the network manager need to have the best practices to secure data. First, it is
very important to grant access to groups, applications and users at a certain scope. In here, one
need to use RBAC predefined roles. Second, it is very important to control want users or clients
have to access to which is done via management plane and data plane interfaces. Lastly, it is very
important to ensure that one can recover a deletion of key vaults or key vault objects (Neira,
2018).
If the construction company employees and the company clients are honest then we do
not need to secure the organization system. To achieve this the organization need to conduct
sensitization workshop to everyone. Lastly, it is not possible to have a system which runs
exclusively on workstations and server; this is because users find it best to use windows at their
end since it is very easy to use.
permissions are those permissions which are given to an object as it is a child of a parent while
explicit permission are permission which is set by default when an object is created by the user
action. Those permissions which are inherited from near relatives usually take precedence over
permissions which are inherited from distant predecessors.
NTFS permission in windows are used to manage folders and files which are stored in
NTFS file systems. Share permissions in windows determine the permissions which are set for a
certain folder when one shares the folder while NTFS determine the actions that users take for a
certain file or folder both locally and on the organization network. This permissions still apply
when access files from Linux to windows but when using windows to access Linux permissions
will apply where there are three types of permissions i.e. read, write and execute. Data security is
paramount and as the network manager need to have the best practices to secure data. First, it is
very important to grant access to groups, applications and users at a certain scope. In here, one
need to use RBAC predefined roles. Second, it is very important to control want users or clients
have to access to which is done via management plane and data plane interfaces. Lastly, it is very
important to ensure that one can recover a deletion of key vaults or key vault objects (Neira,
2018).
If the construction company employees and the company clients are honest then we do
not need to secure the organization system. To achieve this the organization need to conduct
sensitization workshop to everyone. Lastly, it is not possible to have a system which runs
exclusively on workstations and server; this is because users find it best to use windows at their
end since it is very easy to use.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Part B
Corporate Proposal II: Server Roles
The number of servers which were proposed for Rogue Construction Company were three i.e.
the email server, database server, and a web server. For this week one addition server is needed
that is the application server. Table one below summarizes the location each server and where
the server need to be located.
Name of the server Server Role
(Purpose)
Location of the
server
System
requirements
Application Server The major purpose of
the application server
is to offer support to
the web server, it also
host applications used
by the organization
Construction site Windows server 2016
OS, 8 GB RAM, and
a hard disk space of
250GB. This type of
operating is
manageable even
with basic knowledge
of IT. Requires no
manpower to
manageable
(Carvalho, 2013)
Web Server Process web pages
for someone. The
server also offers that
communication
between the client
Rogue company
main office
Linux OS, with a
RAM of 12 GB and
1TB system drive.
With Linux, it offers
more advanced
Corporate Proposal II: Server Roles
The number of servers which were proposed for Rogue Construction Company were three i.e.
the email server, database server, and a web server. For this week one addition server is needed
that is the application server. Table one below summarizes the location each server and where
the server need to be located.
Name of the server Server Role
(Purpose)
Location of the
server
System
requirements
Application Server The major purpose of
the application server
is to offer support to
the web server, it also
host applications used
by the organization
Construction site Windows server 2016
OS, 8 GB RAM, and
a hard disk space of
250GB. This type of
operating is
manageable even
with basic knowledge
of IT. Requires no
manpower to
manageable
(Carvalho, 2013)
Web Server Process web pages
for someone. The
server also offers that
communication
between the client
Rogue company
main office
Linux OS, with a
RAM of 12 GB and
1TB system drive.
With Linux, it offers
more advanced
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
and the server
computer using the
HTTP protocol
security features than
windows Operating
System
Database server The server is used to
perform tasks such as
data analysis, storage
of the organization
data and
manipulation of data
The main office of
the organization
Linux operating
system with a RAM
of 8GB and hard disk
of 1TB. Linux server
offers the best
security features as
compared to windows
E-mail server With the server
manage organization
emails from clients
and emails from
employees
The main office Windows server
2016; this is because
it is very easy to
create an SMTP
service on windows
server 2016 (Ferrill,
2015)
DHCP server With a DHCP server
the organization user
computers are able to
extract their
configurations from
the server
The organization
main site
Windows server 2016
which offers
advanced features
such as network
enhancements
DNS server Rogue company is Main site Linux operating
computer using the
HTTP protocol
security features than
windows Operating
System
Database server The server is used to
perform tasks such as
data analysis, storage
of the organization
data and
manipulation of data
The main office of
the organization
Linux operating
system with a RAM
of 8GB and hard disk
of 1TB. Linux server
offers the best
security features as
compared to windows
E-mail server With the server
manage organization
emails from clients
and emails from
employees
The main office Windows server
2016; this is because
it is very easy to
create an SMTP
service on windows
server 2016 (Ferrill,
2015)
DHCP server With a DHCP server
the organization user
computers are able to
extract their
configurations from
the server
The organization
main site
Windows server 2016
which offers
advanced features
such as network
enhancements
DNS server Rogue company is Main site Linux operating

able to store the
organization IP
addresses i.e. the
organization website
and its corresponding
host names
system; this type of
OS is more secure
that windows OS
An updated diagram for rogue construction is as shown by figure one
Part C
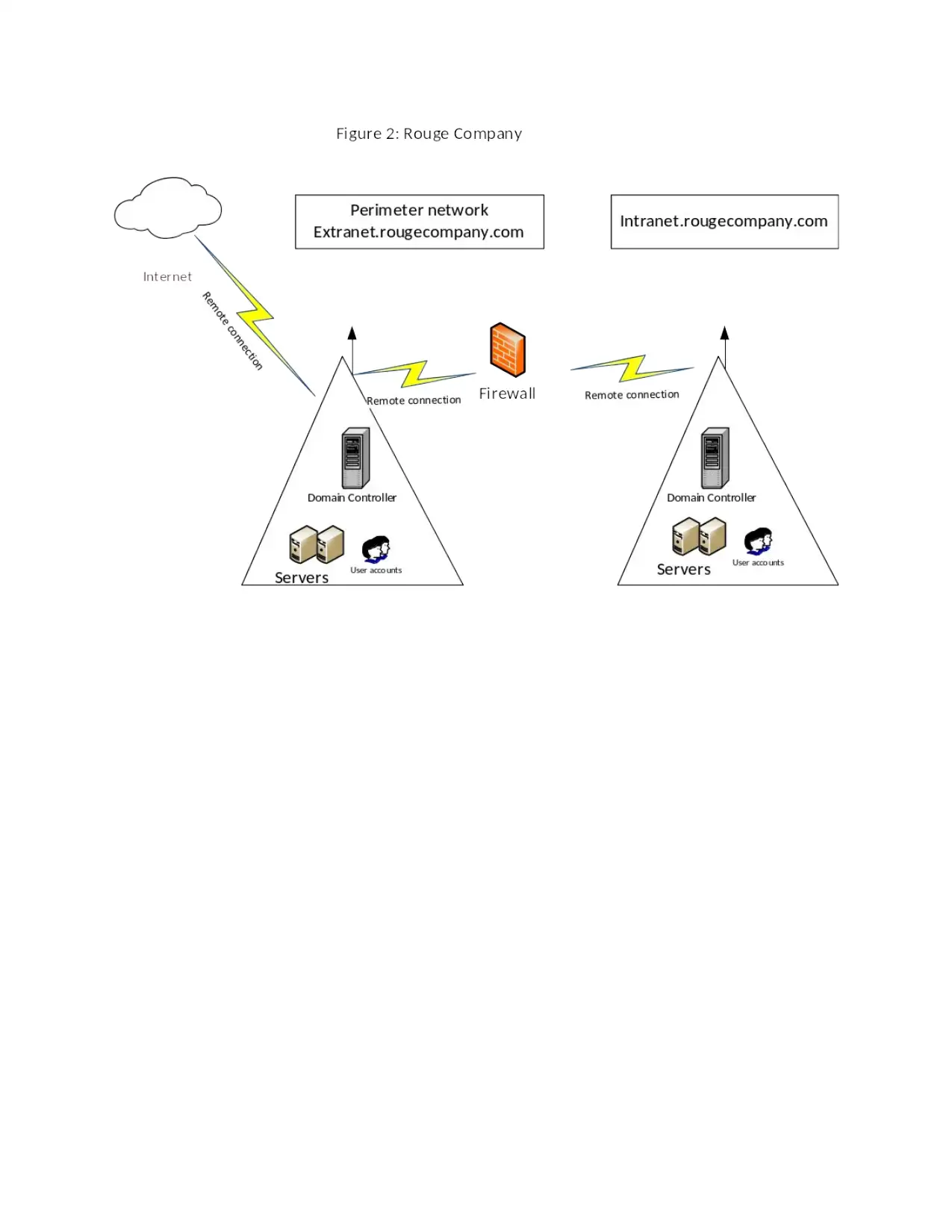
Directory Services
When planning for installation of directory services, as a network manager one need to
first understand all the features available for the windows server. One of the reasons so to why
Rouge Construction company to install directory services is; the directory services offers a
distributed security and also it provides what server administrators refer to as publishing
framework. With Active directory, Rouge Company will be able to manage the organization
application, network resources, and users. In addition, as a network manager I will be able to
install all the windows server in a parallel manner (Dauti, 2017).
For this case as a network manager this paper will go for two domain controllers where
one would be located at the main office and the other one at the construction site. Figure two
below shows how the active directory would be deployed
organization IP
addresses i.e. the
organization website
and its corresponding
host names
system; this type of
OS is more secure
that windows OS
An updated diagram for rogue construction is as shown by figure one
Part C
Directory Services
When planning for installation of directory services, as a network manager one need to
first understand all the features available for the windows server. One of the reasons so to why
Rouge Construction company to install directory services is; the directory services offers a
distributed security and also it provides what server administrators refer to as publishing
framework. With Active directory, Rouge Company will be able to manage the organization
application, network resources, and users. In addition, as a network manager I will be able to
install all the windows server in a parallel manner (Dauti, 2017).
For this case as a network manager this paper will go for two domain controllers where
one would be located at the main office and the other one at the construction site. Figure two
below shows how the active directory would be deployed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
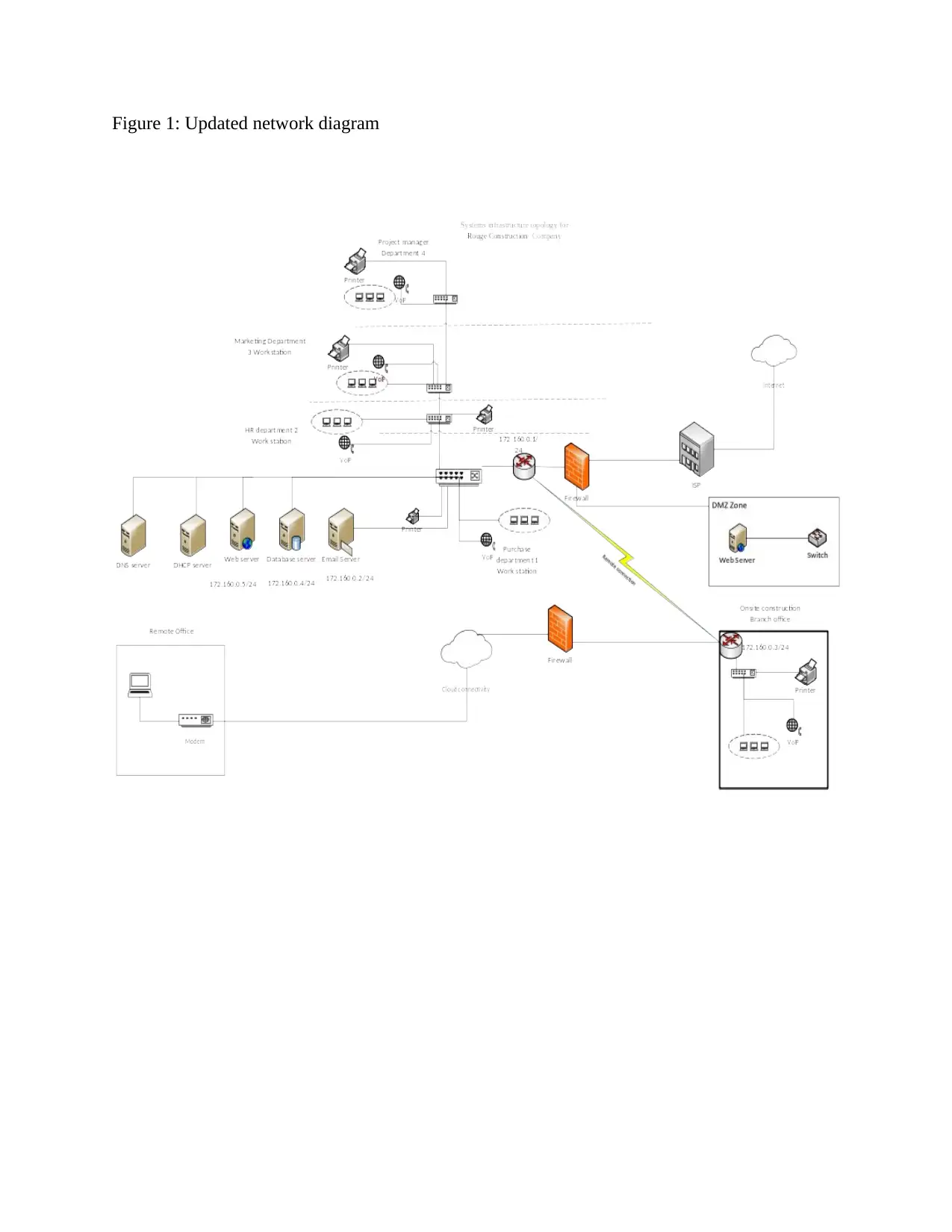
Figure 1: Updated network diagram

References
Carvalho, L. (2013). Windows Server 2012 Hyper-V cookbook : over 50 simple but incredibly
effective recipes for mastering the administration of Windows Server 2012 Hyper-V.
Birmingham: Packt Pub.
Dauti, B. (2017). Windows Server 2016 administration fundamentals : deploy, set up, and
deliver network services with Windows Server while preparing for the MTA 98-365 exam
and pass it with ease. Birmingham: Packt Publishing.
Ferrill, P. (2015, October 29). The best new features in Windows Server 2016. Retrieved from
ComputerWorld: https://www.computerworld.com/article/2998888/virtualization/the-
best-new-features-in-windows-server-2016.html
Neira, B. (2018, September 19th). Azure Data Security and Encryption Best Practices. Retrieved
from Microsoft Azure: https://docs.microsoft.com/en-us/azure/security/azure-security-
data-encryption-best-practices
Carvalho, L. (2013). Windows Server 2012 Hyper-V cookbook : over 50 simple but incredibly
effective recipes for mastering the administration of Windows Server 2012 Hyper-V.
Birmingham: Packt Pub.
Dauti, B. (2017). Windows Server 2016 administration fundamentals : deploy, set up, and
deliver network services with Windows Server while preparing for the MTA 98-365 exam
and pass it with ease. Birmingham: Packt Publishing.
Ferrill, P. (2015, October 29). The best new features in Windows Server 2016. Retrieved from
ComputerWorld: https://www.computerworld.com/article/2998888/virtualization/the-
best-new-features-in-windows-server-2016.html
Neira, B. (2018, September 19th). Azure Data Security and Encryption Best Practices. Retrieved
from Microsoft Azure: https://docs.microsoft.com/en-us/azure/security/azure-security-
data-encryption-best-practices
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





