System Analysis and Design Report: Odd Jobs Limited, ICT700
VerifiedAdded on 2023/06/03
|14
|2966
|304
Report
AI Summary
This document presents a comprehensive system analysis and design report for Odd Jobs Limited, focusing on the implementation of a mobile application. The report begins with an essay and memo, discussing adaptive methodologies, including Scrum and Extreme Programming, and recommending Scrum as the most suitable approach. The memo outlines requirement gathering techniques like brainstorming, interviews, questionnaires, and JAD sessions. The second part of the report includes modeling and diagramming, featuring an event table, a domain model class diagram, a design class diagram, and a use case diagram with corresponding use case descriptions. The analysis provides a detailed overview of system design considerations, data modeling, and user interaction, offering valuable insights into the development process. The assignment is a response to an assignment brief that requested an in-depth look at system analysis and design in the context of a business application.

Running head: SYSTEM ANALYSIS AND DESIGN
System Analysis and Design
Name of the Student
Name of the University
Author’s note
System Analysis and Design
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SYSTEM ANALYSIS AND DESIGN
Table of Contents
Part A: Essay and Memo............................................................................................................2
1.1 Report...............................................................................................................................2
1.1.1 Adaptive Methodology:............................................................................................2
1.1.2 Scrum:.......................................................................................................................3
1.1.3 Extreme Programming:.............................................................................................4
1.1.4 Recommendation:.....................................................................................................5
1.2 Memo...............................................................................................................................5
Part B: Modelling and Diagramming.........................................................................................7
Question 3: Event Table:.......................................................................................................7
Question 4: Domain Model Class Diagram...........................................................................8
Question 5: Design Class Diagram........................................................................................8
Question 6: Use Case Diagram..............................................................................................9
Question 7: Use Case Description..........................................................................................9
Bibliography:............................................................................................................................11
Table of Contents
Part A: Essay and Memo............................................................................................................2
1.1 Report...............................................................................................................................2
1.1.1 Adaptive Methodology:............................................................................................2
1.1.2 Scrum:.......................................................................................................................3
1.1.3 Extreme Programming:.............................................................................................4
1.1.4 Recommendation:.....................................................................................................5
1.2 Memo...............................................................................................................................5
Part B: Modelling and Diagramming.........................................................................................7
Question 3: Event Table:.......................................................................................................7
Question 4: Domain Model Class Diagram...........................................................................8
Question 5: Design Class Diagram........................................................................................8
Question 6: Use Case Diagram..............................................................................................9
Question 7: Use Case Description..........................................................................................9
Bibliography:............................................................................................................................11

2SYSTEM ANALYSIS AND DESIGN
Part A: Essay and Memo
1.1 Report
The Odd Jobs Limited is the organization that offers spontaneous labour to other
organizations. The organizations has head quartered in Sydney. Odd Jobs Limited is looking
forward to implement the mobile application into the business. The mobile application will be
connected to database for storing and retrieving data. The application collect details like
name, address, contact details, last job and more. The internal application will maintain and
track the data flow to and fro customer. The staff license number and a scanned copy of the
license will be stored in the system. The expenses and payment will be stored in the system.
1.1.1 Adaptive Methodology:
The adaptive methodology is the process of collecting requirements while the project
development process is running. As the name suggests, the adaptive methodology means
adapting the project tasks according to the new requirements. There are various methods that
are under the adaptive SDLC method (Chauhan, Rana and Sharma 2017). In the agile
methodology, there is no specific requirements collection process at the beginning of the
adaptive methodology. The requirements are collected in the form of feedback from the end
users.
Advantages: This methodology provides enhance user satisfaction through providing
the final product prototypes from the beginning stages of the project management phases. The
end users of the proposed system along with the system interaction are focused upon from the
beginning so that system behaviour can be considered as significant part of the system
(Chowdhur et al. 2018). The communication between the partisans, project manager, system
analyst and project team allows the team members to collect extract user requirements. The
owner of the project receives functioning prototypes frequently. The main communication
Part A: Essay and Memo
1.1 Report
The Odd Jobs Limited is the organization that offers spontaneous labour to other
organizations. The organizations has head quartered in Sydney. Odd Jobs Limited is looking
forward to implement the mobile application into the business. The mobile application will be
connected to database for storing and retrieving data. The application collect details like
name, address, contact details, last job and more. The internal application will maintain and
track the data flow to and fro customer. The staff license number and a scanned copy of the
license will be stored in the system. The expenses and payment will be stored in the system.
1.1.1 Adaptive Methodology:
The adaptive methodology is the process of collecting requirements while the project
development process is running. As the name suggests, the adaptive methodology means
adapting the project tasks according to the new requirements. There are various methods that
are under the adaptive SDLC method (Chauhan, Rana and Sharma 2017). In the agile
methodology, there is no specific requirements collection process at the beginning of the
adaptive methodology. The requirements are collected in the form of feedback from the end
users.
Advantages: This methodology provides enhance user satisfaction through providing
the final product prototypes from the beginning stages of the project management phases. The
end users of the proposed system along with the system interaction are focused upon from the
beginning so that system behaviour can be considered as significant part of the system
(Chowdhur et al. 2018). The communication between the partisans, project manager, system
analyst and project team allows the team members to collect extract user requirements. The
owner of the project receives functioning prototypes frequently. The main communication
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SYSTEM ANALYSIS AND DESIGN
approach is face to face interviews and observation. This allows the system analyst to gather
more relevant and accurate information regarding user and business requirements. All the
technical activities like coding, designing and testing are continuously monitored (Dora and
Dubey 2015). The biggest advantage of the agile methodology is that it can handle scope
creep. The scope creep is the situation where new copes occur during the project lifecycle.
Disadvantages: Through the use of the adaptive methodology it is not always possible
acquiring exact information on the project complexity, requirements and size. The initial
stages of the project are not vital for the project manager (Chowdhur et al. 2018). The project
does not focus on the documentation part and thus result into lack of information on how the
project. The project is extremely dependent on the feedback from the end users. This can
create issues if the feedbacks are not authentic or project goal oriented.
1.1.2 Scrum:
The SCRUM is a part of agile project management methodology which is used for
software development projects. In an average, the SCRUM method tries to deliver a
functioning prototype to the customer within two to four weeks. The SCRUM has made the
agile manifesto term popular (Matharu et al. 2015). The agile manifesto term describes how
to make end products more effective in an efficient way. Most of the software projects has
used the SCRUM approach for delivering high quality tasks in lesser time. The scrum has
product backlog, sprint planning, sprint, scrum monitoring, sprint complete and review. In the
product backlog the OJL will decide which works to be done (Mousaei and Gandomani
2018). OJL will also prioritize their work. The product backlog details are used for creating
the project backlog.
Advantages: The main advantage of scrum is that this approach provide better
perceptibility and transparency to the project activities in comparison with the other adaptive
approach is face to face interviews and observation. This allows the system analyst to gather
more relevant and accurate information regarding user and business requirements. All the
technical activities like coding, designing and testing are continuously monitored (Dora and
Dubey 2015). The biggest advantage of the agile methodology is that it can handle scope
creep. The scope creep is the situation where new copes occur during the project lifecycle.
Disadvantages: Through the use of the adaptive methodology it is not always possible
acquiring exact information on the project complexity, requirements and size. The initial
stages of the project are not vital for the project manager (Chowdhur et al. 2018). The project
does not focus on the documentation part and thus result into lack of information on how the
project. The project is extremely dependent on the feedback from the end users. This can
create issues if the feedbacks are not authentic or project goal oriented.
1.1.2 Scrum:
The SCRUM is a part of agile project management methodology which is used for
software development projects. In an average, the SCRUM method tries to deliver a
functioning prototype to the customer within two to four weeks. The SCRUM has made the
agile manifesto term popular (Matharu et al. 2015). The agile manifesto term describes how
to make end products more effective in an efficient way. Most of the software projects has
used the SCRUM approach for delivering high quality tasks in lesser time. The scrum has
product backlog, sprint planning, sprint, scrum monitoring, sprint complete and review. In the
product backlog the OJL will decide which works to be done (Mousaei and Gandomani
2018). OJL will also prioritize their work. The product backlog details are used for creating
the project backlog.
Advantages: The main advantage of scrum is that this approach provide better
perceptibility and transparency to the project activities in comparison with the other adaptive
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SYSTEM ANALYSIS AND DESIGN
agile project management methods. The team accountability is greatly improved due to
unique features of the SCRUM method. The SLC approach allows the organization to
change the scope of the project is essential and entertains new requirements. The project
issues are recognized quickly due to presence of daily meetings (Burman 2015). The early
identified issues become easily to resolve. The project process handling and over objective
management is done through some efficient ways thus leading to quicker delivery of end
product in a cheaper cost. The OJL will be able to make the most of scrum as it is highly
related to technology/programming.
Disadvantage: The scrum method may handle scope creep. However, in big and
complex projects extensive amount of scope creep will surely result into project failure. The
scrum master will not be able to calculate the approximate time and capital required to
complete the project if OJL does not define the tasks properly in product backlog (Mousaei
and Gandomani 2018). The team members ate scrum project are not at all committed to their
work. The extensive amount of scope creep can be the cause of it. The project may never be
completed due to this reason.
1.1.3 Extreme Programming:
According to some of the project managers and organizations, the extreme
programming is one of the most useful development methods in the software development
terminology (Tabassum et al. 2017). The extreme programming have five values like
communication, simplicity, feedback, courage and respect.
Advantages: The extreme programming has ability to enhance the employee retention
and satisfaction. The continuous testing at the development stage makes the system project
progress quicker (Hameed 2016). The processes in the extreme programming is accountable.
The XP create very simple codes to make the progress faster.
agile project management methods. The team accountability is greatly improved due to
unique features of the SCRUM method. The SLC approach allows the organization to
change the scope of the project is essential and entertains new requirements. The project
issues are recognized quickly due to presence of daily meetings (Burman 2015). The early
identified issues become easily to resolve. The project process handling and over objective
management is done through some efficient ways thus leading to quicker delivery of end
product in a cheaper cost. The OJL will be able to make the most of scrum as it is highly
related to technology/programming.
Disadvantage: The scrum method may handle scope creep. However, in big and
complex projects extensive amount of scope creep will surely result into project failure. The
scrum master will not be able to calculate the approximate time and capital required to
complete the project if OJL does not define the tasks properly in product backlog (Mousaei
and Gandomani 2018). The team members ate scrum project are not at all committed to their
work. The extensive amount of scope creep can be the cause of it. The project may never be
completed due to this reason.
1.1.3 Extreme Programming:
According to some of the project managers and organizations, the extreme
programming is one of the most useful development methods in the software development
terminology (Tabassum et al. 2017). The extreme programming have five values like
communication, simplicity, feedback, courage and respect.
Advantages: The extreme programming has ability to enhance the employee retention
and satisfaction. The continuous testing at the development stage makes the system project
progress quicker (Hameed 2016). The processes in the extreme programming is accountable.
The XP create very simple codes to make the progress faster.

5SYSTEM ANALYSIS AND DESIGN
Disadvantage: The extreme programing is a relatively tough from other software
practices. The developers and programmers have to continuously work hard for making the
codes simple enough (Chowdhury et al. 2018). The continuous testing phase result in
frequent changes in the code. The developed end product is more code centric rather than
design centric.
1.1.4 Recommendation:
From the above description of the software development models, it can be said each
methodology has its advantage and disadvantage. However, the scrum seems more suitable
for OJL system development project. The organization and its stakeholder needs a user
centric application in least possible time. The cost of the project must be reasonable. The
scrum seems to meet the requirement of OJL as it can deliver a design centric final product in
a budget friendly approach.
1.2 Memo
Memo
To: Owner Colin Grey
From: << Student >>,
Date: 01-10-18
Sub: System Requirement Collection Method for Proposed Internal System Project.
There are different requirement gathering methods that are present and used by the
different companies in today’s world, mainly for software management operations. Some
of the important aspects of the requirement gathering techniques are Brainstorming. It is
utilized in requirements elicitation of the requirements to collect innovative ideas from
groups of people, focus groups that mainly aims to improve or develop the group of
individuals who need training and development in a particular field of work, interviewing
candidates as well as keeping them under observation and other techniques. One on one
Disadvantage: The extreme programing is a relatively tough from other software
practices. The developers and programmers have to continuously work hard for making the
codes simple enough (Chowdhury et al. 2018). The continuous testing phase result in
frequent changes in the code. The developed end product is more code centric rather than
design centric.
1.1.4 Recommendation:
From the above description of the software development models, it can be said each
methodology has its advantage and disadvantage. However, the scrum seems more suitable
for OJL system development project. The organization and its stakeholder needs a user
centric application in least possible time. The cost of the project must be reasonable. The
scrum seems to meet the requirement of OJL as it can deliver a design centric final product in
a budget friendly approach.
1.2 Memo
Memo
To: Owner Colin Grey
From: << Student >>,
Date: 01-10-18
Sub: System Requirement Collection Method for Proposed Internal System Project.
There are different requirement gathering methods that are present and used by the
different companies in today’s world, mainly for software management operations. Some
of the important aspects of the requirement gathering techniques are Brainstorming. It is
utilized in requirements elicitation of the requirements to collect innovative ideas from
groups of people, focus groups that mainly aims to improve or develop the group of
individuals who need training and development in a particular field of work, interviewing
candidates as well as keeping them under observation and other techniques. One on one
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SYSTEM ANALYSIS AND DESIGN
interviews plays a vital role in gathering information. The analyst, who will be taking the
interview, should be well versed with the technologies and should ask open ended as well
as closed ended questions to the interviewee in order to have an in-depth knowledge about
the candidature of the candidate. He should also seek permission from the interviewee in
case a recorder will be used in the course of the interview. Group inter views are similar to
one on one interviews and it involves more than one interviewee. It helps in giving a more
varied perspective and knowledge from the different candidates but the major drawback is
that it is extremely time consuming. Questionnaires and surveys also play an important role
in gathering information. The questions should be related to the project; the candidates are
taken for and therefore should be precise in nature. The questionnaire should not be very
long to ensure that all users are able to complete them in time an d also focus on general
open ended perspectives like how, when, who, why and what of the incidences. Existing
documents can also be analyzed in order to have a knowledge on the background of the
project and understand what research has already been done in the past and what were the
shortcomings from the earlier studies, which can be addressed now. Any issues in the
applications, which were earlier not identified or rectified by software developers, should
be rectified now. Joint Application design (JAD) as well as AJAD (Automatic joint
application design) are again important requirement gathering techniques. JAD includes the
working of a JAD sessions leader such as users, sponsors, scribes as well as managers and
other staff member. Managers can provide an in depth insight into the different crucial
aspects of the organization. AJAD works in the same way as JAD only difference being
that it is an automated process and computers do all the functions. Prototyping is another
iterative feature wherein the analyst can directly plug in himself and show the required
outputs to the user directly. It requires the users to complete the work on time.
Odd jobs limited wants to make a complete analysis of the business functioning of
interviews plays a vital role in gathering information. The analyst, who will be taking the
interview, should be well versed with the technologies and should ask open ended as well
as closed ended questions to the interviewee in order to have an in-depth knowledge about
the candidature of the candidate. He should also seek permission from the interviewee in
case a recorder will be used in the course of the interview. Group inter views are similar to
one on one interviews and it involves more than one interviewee. It helps in giving a more
varied perspective and knowledge from the different candidates but the major drawback is
that it is extremely time consuming. Questionnaires and surveys also play an important role
in gathering information. The questions should be related to the project; the candidates are
taken for and therefore should be precise in nature. The questionnaire should not be very
long to ensure that all users are able to complete them in time an d also focus on general
open ended perspectives like how, when, who, why and what of the incidences. Existing
documents can also be analyzed in order to have a knowledge on the background of the
project and understand what research has already been done in the past and what were the
shortcomings from the earlier studies, which can be addressed now. Any issues in the
applications, which were earlier not identified or rectified by software developers, should
be rectified now. Joint Application design (JAD) as well as AJAD (Automatic joint
application design) are again important requirement gathering techniques. JAD includes the
working of a JAD sessions leader such as users, sponsors, scribes as well as managers and
other staff member. Managers can provide an in depth insight into the different crucial
aspects of the organization. AJAD works in the same way as JAD only difference being
that it is an automated process and computers do all the functions. Prototyping is another
iterative feature wherein the analyst can directly plug in himself and show the required
outputs to the user directly. It requires the users to complete the work on time.
Odd jobs limited wants to make a complete analysis of the business functioning of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SYSTEM ANALYSIS AND DESIGN
their origination and they employees needs to drive a number of vehicles, which are owned
by OJL. Few of the above-discussed techniques of requirement gathering will be used for
this. Questionnaires will be distributed among the employees of OJL regarding the
different technical specifications of the vehicles to know how well educated the employees
are about the vehicles they are about to drive. In addition, a JAD session will be held
wherein, Tom Smith wants to generate an overall company report every month, on the
working and all the customers of the company have to record their name, address, and
email as well as business number for a complete and detailed analysis. He also wants some
information to be maintained such as date of the job, contracting staff an d the amount
spent for it and the technique to be used in JAD, in which all the results will be collated
and a common decision be taken. Prototyping will also be used by Gary Tal lent and Colin
Gray in order to fetch the required information.
Part B: Modelling and Diagramming
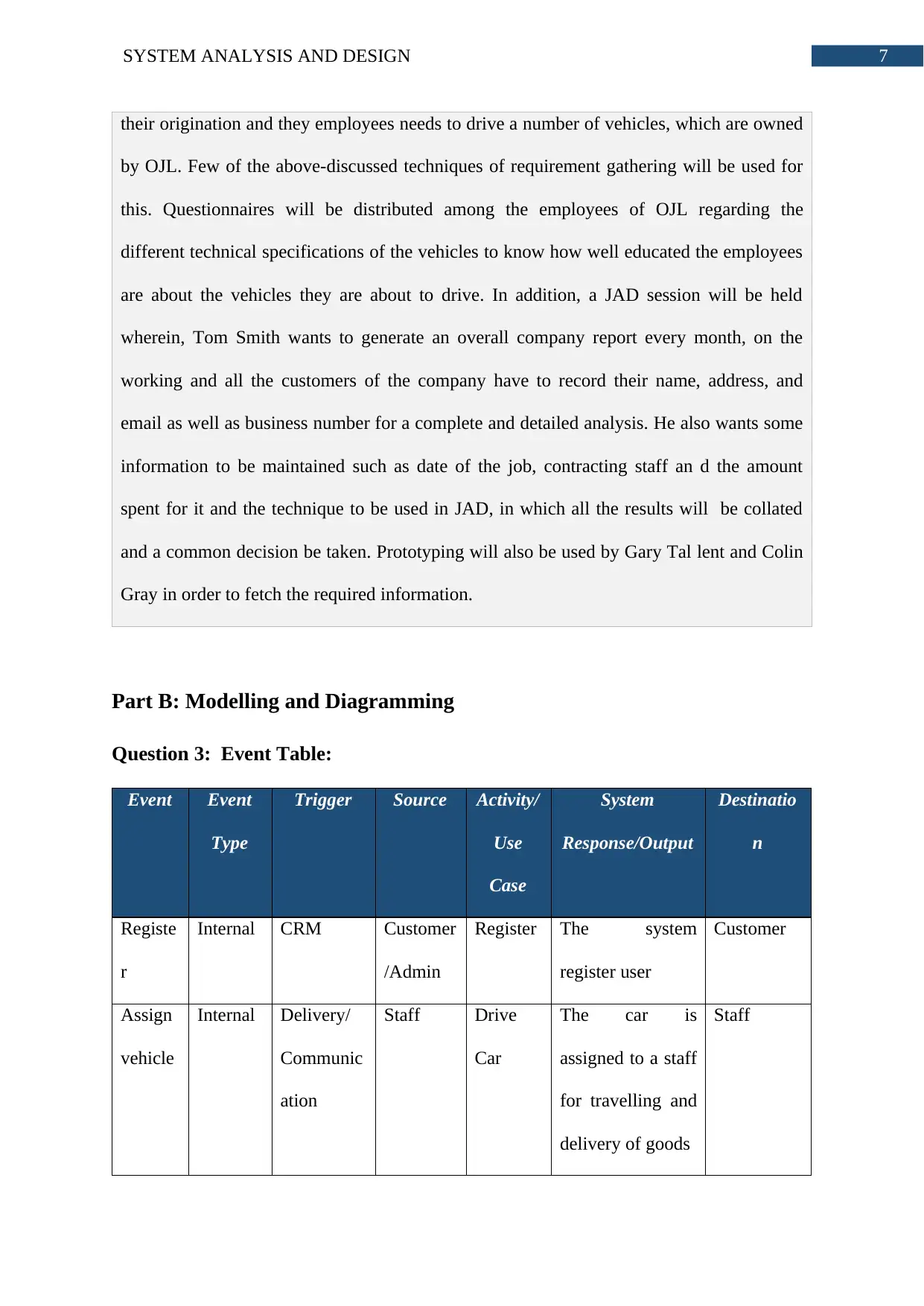
Question 3: Event Table:
Event Event
Type
Trigger Source Activity/
Use
Case
System
Response/Output
Destinatio
n
Registe
r
Internal CRM Customer
/Admin
Register The system
register user
Customer
Assign
vehicle
Internal Delivery/
Communic
ation
Staff Drive
Car
The car is
assigned to a staff
for travelling and
delivery of goods
Staff
their origination and they employees needs to drive a number of vehicles, which are owned
by OJL. Few of the above-discussed techniques of requirement gathering will be used for
this. Questionnaires will be distributed among the employees of OJL regarding the
different technical specifications of the vehicles to know how well educated the employees
are about the vehicles they are about to drive. In addition, a JAD session will be held
wherein, Tom Smith wants to generate an overall company report every month, on the
working and all the customers of the company have to record their name, address, and
email as well as business number for a complete and detailed analysis. He also wants some
information to be maintained such as date of the job, contracting staff an d the amount
spent for it and the technique to be used in JAD, in which all the results will be collated
and a common decision be taken. Prototyping will also be used by Gary Tal lent and Colin
Gray in order to fetch the required information.
Part B: Modelling and Diagramming
Question 3: Event Table:
Event Event
Type
Trigger Source Activity/
Use
Case
System
Response/Output
Destinatio
n
Registe
r
Internal CRM Customer
/Admin
Register The system
register user
Customer
Assign
vehicle
Internal Delivery/
Communic
ation
Staff Drive
Car
The car is
assigned to a staff
for travelling and
delivery of goods
Staff
8SYSTEM ANALYSIS AND DESIGN
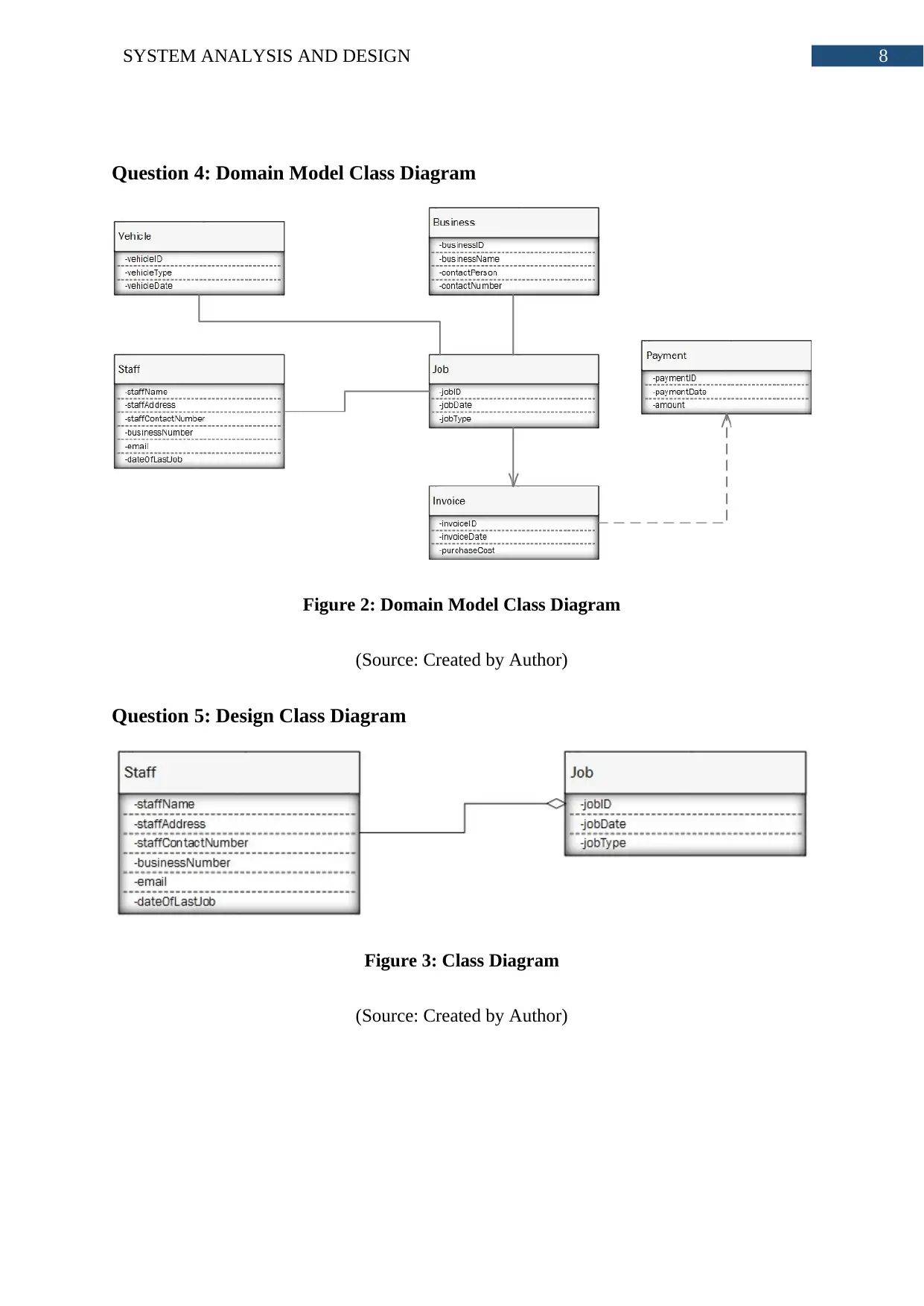
Question 4: Domain Model Class Diagram
Figure 2: Domain Model Class Diagram
(Source: Created by Author)
Question 5: Design Class Diagram
Figure 3: Class Diagram
(Source: Created by Author)
Question 4: Domain Model Class Diagram
Figure 2: Domain Model Class Diagram
(Source: Created by Author)
Question 5: Design Class Diagram
Figure 3: Class Diagram
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9SYSTEM ANALYSIS AND DESIGN
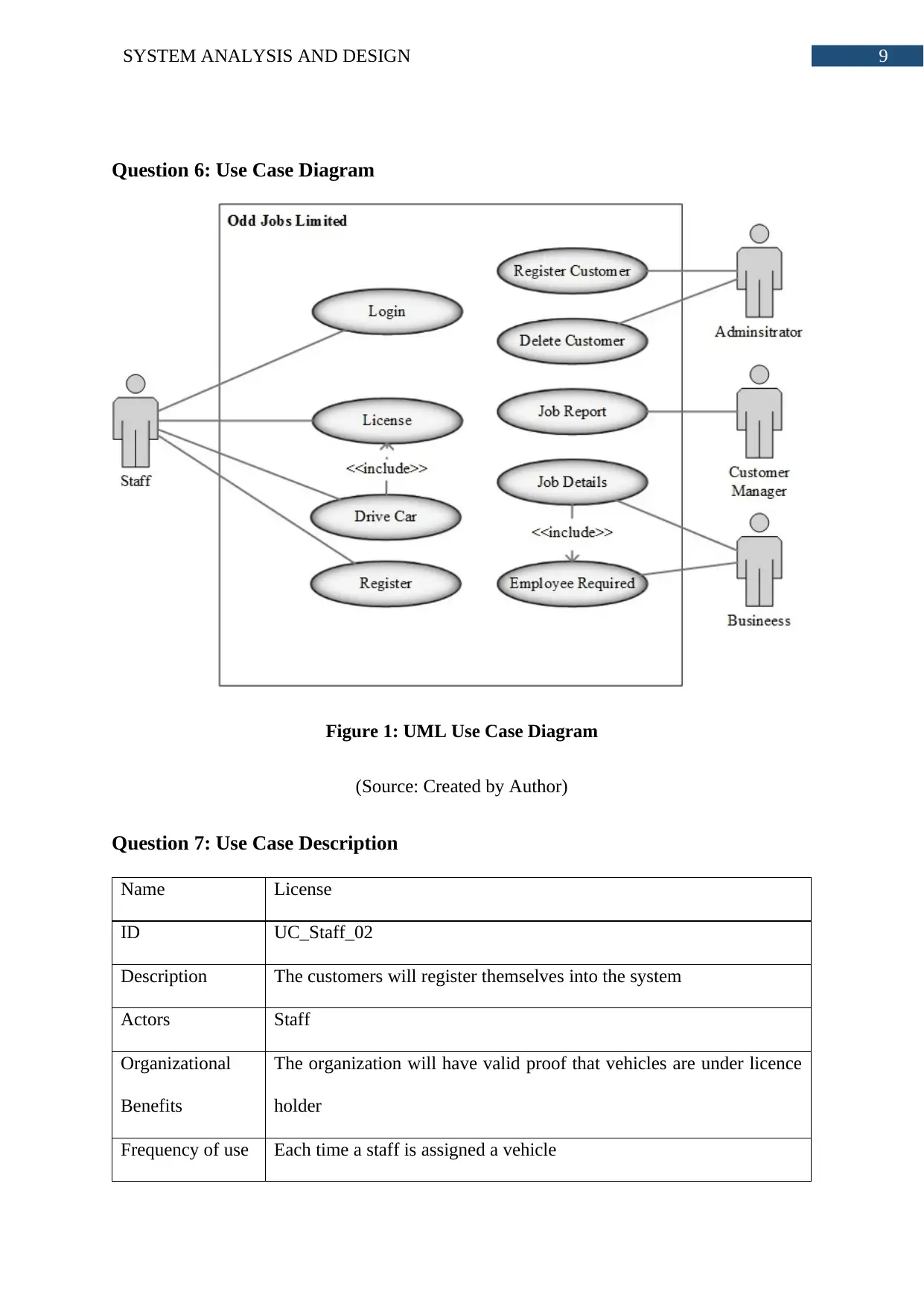
Question 6: Use Case Diagram
Figure 1: UML Use Case Diagram
(Source: Created by Author)
Question 7: Use Case Description
Name License
ID UC_Staff_02
Description The customers will register themselves into the system
Actors Staff
Organizational
Benefits
The organization will have valid proof that vehicles are under licence
holder
Frequency of use Each time a staff is assigned a vehicle
Question 6: Use Case Diagram
Figure 1: UML Use Case Diagram
(Source: Created by Author)
Question 7: Use Case Description
Name License
ID UC_Staff_02
Description The customers will register themselves into the system
Actors Staff
Organizational
Benefits
The organization will have valid proof that vehicles are under licence
holder
Frequency of use Each time a staff is assigned a vehicle
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10SYSTEM ANALYSIS AND DESIGN
Triggers Assigning vehicle to customer specific period of time
Preconditions At least a single vehicle must be available
Postconditions That vehicle cannot be assigned to any other staff for assigned period
Main Course 1. The customer enter the licence number for the first time the licence
is registered
2. The customer upload the scanned copy of the licence each time
vehicle is assigned
Exceptions EX1: The staff licence if expired
1. OJL will assign a driver to that staff
Triggers Assigning vehicle to customer specific period of time
Preconditions At least a single vehicle must be available
Postconditions That vehicle cannot be assigned to any other staff for assigned period
Main Course 1. The customer enter the licence number for the first time the licence
is registered
2. The customer upload the scanned copy of the licence each time
vehicle is assigned
Exceptions EX1: The staff licence if expired
1. OJL will assign a driver to that staff

11SYSTEM ANALYSIS AND DESIGN
Bibliography:
Burman, E., 2015. Agile in action: Hybrid methodologies in practice.
Chauhan, B.D., Rana, A. and Sharma, N.K., 2017, September. Impact of development
methodology on cost & risk for development projects. In 2017 6th International Conference
on Reliability, Infocom Technologies and Optimization (Trends and Future Directions)
(ICRITO) (pp. 267-272). IEEE.
Chowdhury, A.Z.M., Bhowmik, A., Hasan, H. and Rahim, M.S., 2018. Analysis of the
Veracities of Industry Used Software Development Life Cycle Methodologies. arXiv
preprint arXiv:1805.08631.
Chowdhury, A.Z.M., Bhowmik, A., Hasan, H. and Rahim, M.S., 2018. Analysis of the
Veracities of Industry Used Software Development Life Cycle Methodologies. arXiv
preprint arXiv:1805.08631.
Cunha, A., Garis, A. and Riesco, D., 2015. Translating between Alloy specifications and
UML class diagrams annotated with OCL. Software & Systems Modeling, 14(1), pp.5-25.
Dora, S.K. and Dubey, P., 2015. Software Development Life Cycle (SDLC) Analytical
Comparison and Survey on Traditional and Agile Methodology. National Monthly Referred
Journal of Research Science and Technology, 2(8).
Gold, B. and Vassell, C., 2015, November. Using risk management to balance agile methods:
A study of the Scrum process. In Knowledge-Based Engineering and Innovation (KBEI),
2015 2nd International Conference on (pp. 49-54). IEEE.
Hameed, A., 2016. Software Development Lifecycle for Extreme Programming.
International Journal of Information Technology and Electrical Engineering, 5(1).
Bibliography:
Burman, E., 2015. Agile in action: Hybrid methodologies in practice.
Chauhan, B.D., Rana, A. and Sharma, N.K., 2017, September. Impact of development
methodology on cost & risk for development projects. In 2017 6th International Conference
on Reliability, Infocom Technologies and Optimization (Trends and Future Directions)
(ICRITO) (pp. 267-272). IEEE.
Chowdhury, A.Z.M., Bhowmik, A., Hasan, H. and Rahim, M.S., 2018. Analysis of the
Veracities of Industry Used Software Development Life Cycle Methodologies. arXiv
preprint arXiv:1805.08631.
Chowdhury, A.Z.M., Bhowmik, A., Hasan, H. and Rahim, M.S., 2018. Analysis of the
Veracities of Industry Used Software Development Life Cycle Methodologies. arXiv
preprint arXiv:1805.08631.
Cunha, A., Garis, A. and Riesco, D., 2015. Translating between Alloy specifications and
UML class diagrams annotated with OCL. Software & Systems Modeling, 14(1), pp.5-25.
Dora, S.K. and Dubey, P., 2015. Software Development Life Cycle (SDLC) Analytical
Comparison and Survey on Traditional and Agile Methodology. National Monthly Referred
Journal of Research Science and Technology, 2(8).
Gold, B. and Vassell, C., 2015, November. Using risk management to balance agile methods:
A study of the Scrum process. In Knowledge-Based Engineering and Innovation (KBEI),
2015 2nd International Conference on (pp. 49-54). IEEE.
Hameed, A., 2016. Software Development Lifecycle for Extreme Programming.
International Journal of Information Technology and Electrical Engineering, 5(1).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




