System Analysis and Design: Patterns, Implementation, and SDLC Role
VerifiedAdded on 2023/06/03
|9
|1946
|63
Report
AI Summary
This report provides a detailed analysis of system analysis and design principles, focusing on the application of design patterns, the implementation of controller and domain entity classes, and a reflection on the role of design processes within the Software Development Life Cycle (SDLC). It examines the use of behavioral patterns in use case analysis, illustrates the implementation of patterns through class diagrams and test harnesses, and discusses the significance of software architecture, database design, user interface design, use case realization, and detailed design within the SDLC. The report emphasizes the importance of each design process phase in creating efficient and effective eHealth information systems, highlighting the relationships between logical business behavior and the system's physical design.

Running head: SYSTEM ANALYSIS AND DESIGN
System Analysis and Design
Name of the Student
Name of the University
System Analysis and Design
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SYSTEM ANALYSIS AND DESIGN
Table of Contents
Question 1 - Reflection on Patterns...........................................................................................2
Question 2 – Pattern Implementation.........................................................................................3
Question 3 - Reflect on the role of Design Processes within the SDLC....................................4
Bibliography:..............................................................................................................................8
Table of Contents
Question 1 - Reflection on Patterns...........................................................................................2
Question 2 – Pattern Implementation.........................................................................................3
Question 3 - Reflect on the role of Design Processes within the SDLC....................................4
Bibliography:..............................................................................................................................8

2SYSTEM ANALYSIS AND DESIGN
Question 1 - Reflection on Patterns
The Use Case analyzed that has been already analyzed is categorized into the
Behavioral pattern. The other available design patterns were creation and structural.
However, as the use case has been used for determining the interaction of the users with the
system, the Behavioral pattern was the best solution. The pattern used in the use case analysis
has the characteristics named reusability, useful solution and contextual. The use case has
properly shown how the users will be efficiently interacting with the system. Moreover, the
associated interactions has been also mentioned.
The use case pattern states that the physician will get notification after the frontline
personnel mark the situation as emergency. The staff can track the patient health related data
and treatment patterns. The staff can also access the history of patient health data. This use
case pattern shows that the staff such as nurse, frontline personnel, and physicians can access
all the patient data immediately for improving the patient health care. The use case pattern
shows that each patient must be logged in before accessing the system. The login is important
as the system will store all the patient data specifically for each patient. The system cannot
identify which data is associated with which patient. The patient will get login credentials
based on the registration. The patient can also track the health data like the staff. However,
the patient health data access is restricted to his/her own data. The patient can also add
additional data. Taken as an example, the patient may want to record voice message
regarding the experience while glucose level is not normal. Configuring the application is an
additional use case pattern that has been assumed. The application will allow the user to
customize the application theme, font sizes and more.
Question 1 - Reflection on Patterns
The Use Case analyzed that has been already analyzed is categorized into the
Behavioral pattern. The other available design patterns were creation and structural.
However, as the use case has been used for determining the interaction of the users with the
system, the Behavioral pattern was the best solution. The pattern used in the use case analysis
has the characteristics named reusability, useful solution and contextual. The use case has
properly shown how the users will be efficiently interacting with the system. Moreover, the
associated interactions has been also mentioned.
The use case pattern states that the physician will get notification after the frontline
personnel mark the situation as emergency. The staff can track the patient health related data
and treatment patterns. The staff can also access the history of patient health data. This use
case pattern shows that the staff such as nurse, frontline personnel, and physicians can access
all the patient data immediately for improving the patient health care. The use case pattern
shows that each patient must be logged in before accessing the system. The login is important
as the system will store all the patient data specifically for each patient. The system cannot
identify which data is associated with which patient. The patient will get login credentials
based on the registration. The patient can also track the health data like the staff. However,
the patient health data access is restricted to his/her own data. The patient can also add
additional data. Taken as an example, the patient may want to record voice message
regarding the experience while glucose level is not normal. Configuring the application is an
additional use case pattern that has been assumed. The application will allow the user to
customize the application theme, font sizes and more.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
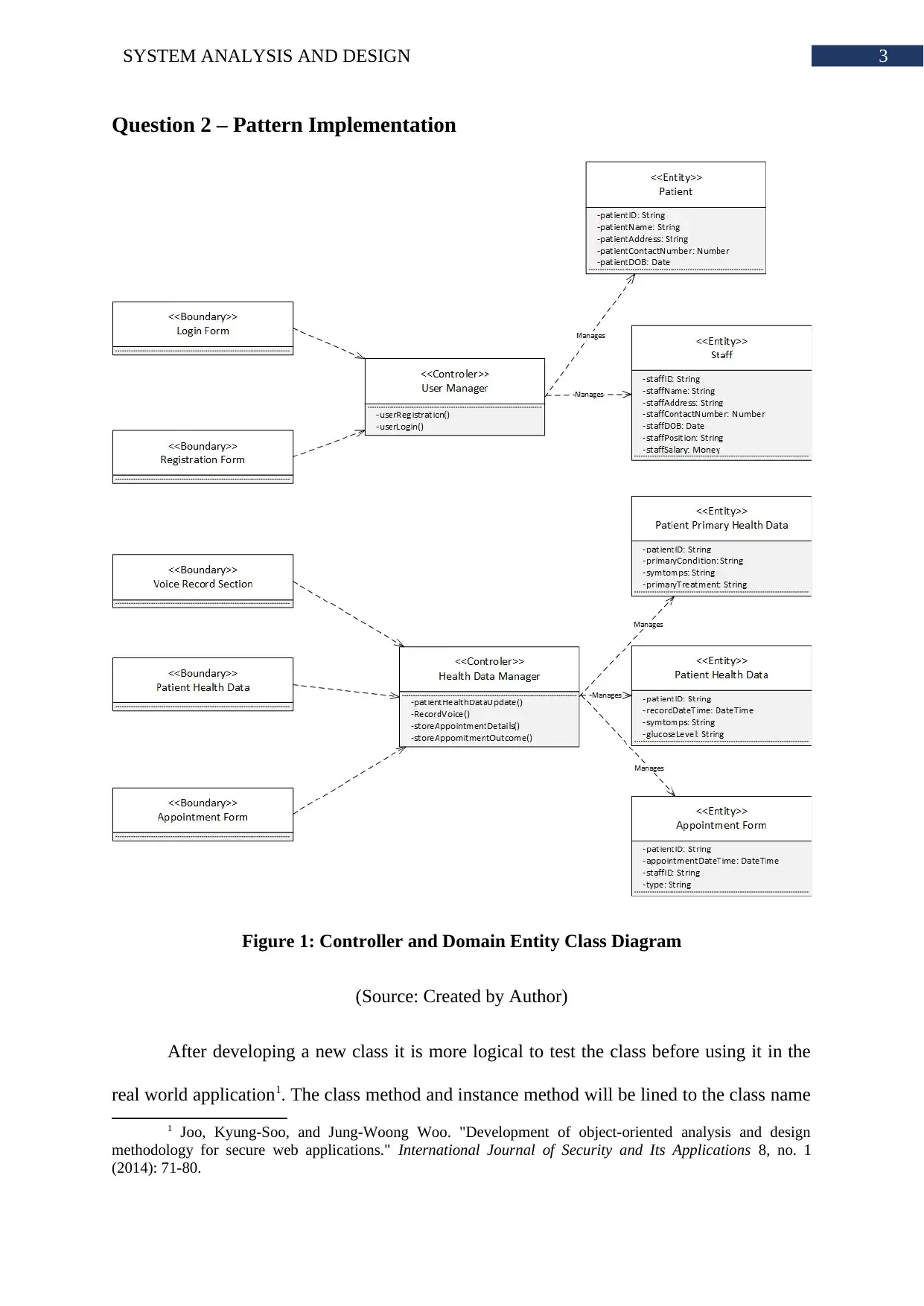
3SYSTEM ANALYSIS AND DESIGN
Question 2 – Pattern Implementation
Figure 1: Controller and Domain Entity Class Diagram
(Source: Created by Author)
After developing a new class it is more logical to test the class before using it in the
real world application1. The class method and instance method will be lined to the class name
1 Joo, Kyung-Soo, and Jung-Woong Woo. "Development of object-oriented analysis and design
methodology for secure web applications." International Journal of Security and Its Applications 8, no. 1
(2014): 71-80.
Question 2 – Pattern Implementation
Figure 1: Controller and Domain Entity Class Diagram
(Source: Created by Author)
After developing a new class it is more logical to test the class before using it in the
real world application1. The class method and instance method will be lined to the class name
1 Joo, Kyung-Soo, and Jung-Woong Woo. "Development of object-oriented analysis and design
methodology for secure web applications." International Journal of Security and Its Applications 8, no. 1
(2014): 71-80.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SYSTEM ANALYSIS AND DESIGN
and instance name respectively. The system will use the method call approach. This approach
entails that one method can be called from within another method. The method call is a
critical part of test harness.
Test Case: The staff will set an appointment for the patient. The system will check is
patient is registered. If the patient is not registered, then registration method will be called
from within the set appointment method.
The argument passing is also an important part of the harness testing. This approach
allows the objects to pass parameters into the methods. The methods and constructors are
used for argument passing. The class can implement constructor overloading so that a same
class can be used for different purposes.
Test Case: The system will define the number of arguments while registering a
patient or staff. Based on the number of parameters passed, the system will determine
whether the person is a patient or a staff.
Question 3 - Reflect on the role of Design Processes within the SDLC
Software Architecture: It is used for designing a software system and creating a
eHealth information system, the architecture is used for creating a statement identification of
the assets required for the development of the IoT healthcare system. The architectural
models are used for evaluation of the interoperability, security, efficiency, quality and asset
reusability2. The software architecture is used for the development of the framework of the
infrastructure and it helps in inclusion of the new elements in the telehealth system for
management of the hardware and the software platform. The software architecture is created
during the design phase of the software development lifecycle model and it helps in
2 Alexander, Kaitlin, and Stephen M. Easterbrook. "The software architecture of climate models: a
graphical comparison of CMIP5 and EMICAR5 configurations." Geoscientific Model Development 8, no. 4
(2015): 1221-1232.
and instance name respectively. The system will use the method call approach. This approach
entails that one method can be called from within another method. The method call is a
critical part of test harness.
Test Case: The staff will set an appointment for the patient. The system will check is
patient is registered. If the patient is not registered, then registration method will be called
from within the set appointment method.
The argument passing is also an important part of the harness testing. This approach
allows the objects to pass parameters into the methods. The methods and constructors are
used for argument passing. The class can implement constructor overloading so that a same
class can be used for different purposes.
Test Case: The system will define the number of arguments while registering a
patient or staff. Based on the number of parameters passed, the system will determine
whether the person is a patient or a staff.
Question 3 - Reflect on the role of Design Processes within the SDLC
Software Architecture: It is used for designing a software system and creating a
eHealth information system, the architecture is used for creating a statement identification of
the assets required for the development of the IoT healthcare system. The architectural
models are used for evaluation of the interoperability, security, efficiency, quality and asset
reusability2. The software architecture is used for the development of the framework of the
infrastructure and it helps in inclusion of the new elements in the telehealth system for
management of the hardware and the software platform. The software architecture is created
during the design phase of the software development lifecycle model and it helps in
2 Alexander, Kaitlin, and Stephen M. Easterbrook. "The software architecture of climate models: a
graphical comparison of CMIP5 and EMICAR5 configurations." Geoscientific Model Development 8, no. 4
(2015): 1221-1232.

5SYSTEM ANALYSIS AND DESIGN
improvement of the efficiency of the eHealth solution developed for meeting the local needs
of the patients. The software architecture is created by combining the different components
and service involved for the management of the health informatics.
Database Design: For the management of the data generated from the IoT telehealth
devices a distributed database management system should be applied. The use of big data can
be an ideal choice for the development team for data analysis and storing data generated from
multiple sources. There are different conceptual database models that can be used for the
diagnostic of the patient health condition3. The database design is created and during the
database management phase of software development lifecycle model. The database
architecture is created and the flow of information between the different components are
identified for designing the tables and store the information of the patients and the individuals
using the system. The development of the database can be separated from the software
development lifecycle model after the analysis of the requirement of the project. For the
development of the database a logical design is created that is dependent on the conceptual
data model and the constraint are identified for the data representation.
User Interface: The user interface is the communication medium between the user
and the system. The system will have different user interfaces. The patients will use the
mobile screen for communicating with the system and the staff will use computer for
interacting with the system4. The system interface design process are executed in several
parts. The first one is creating low fidelity prototypes. In this user interface design, the system
interface mockups or wireframes are created. The mockups are analyzed and suggestions are
3 Elmasri, Ramez, and Sham Navathe. Fundamentals of database systems. London: Pearson, 2016.
4 Courtney, Karen L., Judith T. Matthews, Julie M. McMillan, L. Mecca Person, Asim Smailagic, and
Daniel Siewiorek. "Usability testing of a prototype multi-user telehealth kiosk." Studies in health technology
and informatics 208 (2015): 109-113.
improvement of the efficiency of the eHealth solution developed for meeting the local needs
of the patients. The software architecture is created by combining the different components
and service involved for the management of the health informatics.
Database Design: For the management of the data generated from the IoT telehealth
devices a distributed database management system should be applied. The use of big data can
be an ideal choice for the development team for data analysis and storing data generated from
multiple sources. There are different conceptual database models that can be used for the
diagnostic of the patient health condition3. The database design is created and during the
database management phase of software development lifecycle model. The database
architecture is created and the flow of information between the different components are
identified for designing the tables and store the information of the patients and the individuals
using the system. The development of the database can be separated from the software
development lifecycle model after the analysis of the requirement of the project. For the
development of the database a logical design is created that is dependent on the conceptual
data model and the constraint are identified for the data representation.
User Interface: The user interface is the communication medium between the user
and the system. The system will have different user interfaces. The patients will use the
mobile screen for communicating with the system and the staff will use computer for
interacting with the system4. The system interface design process are executed in several
parts. The first one is creating low fidelity prototypes. In this user interface design, the system
interface mockups or wireframes are created. The mockups are analyzed and suggestions are
3 Elmasri, Ramez, and Sham Navathe. Fundamentals of database systems. London: Pearson, 2016.
4 Courtney, Karen L., Judith T. Matthews, Julie M. McMillan, L. Mecca Person, Asim Smailagic, and
Daniel Siewiorek. "Usability testing of a prototype multi-user telehealth kiosk." Studies in health technology
and informatics 208 (2015): 109-113.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SYSTEM ANALYSIS AND DESIGN
collected. Based on the output of the evaluation, the high level prototypes are created. These
high-level prototypes are the intractable user interface.
The user interfaces are created after all the design paradigms are identified. The use
case realization acts as the most important source of interface information.
Use Case Realization: The use case realization offers a construct for organizing the
entities that visualizes how the logical business behavior is supported by the system physical
design. The use case is the communication medium between the logician and physical aspect
of the system5. The main purpose of the use case realization is defining the physical design of
the system regarding classes and cooperating objects that is supports the use case. Therefore,
the use case realization, can be considered as the based on the use case modeling approach,
are consisted of various UML diagrams like class diagram and several interaction diagrams.
The use case realization is used in the designing phase of the SDLC methodology.
The designing of the system is a very crucial part of the system project as the whole code is
based on the designs. As the real reason behind the use case realization is to establish logical
communication between the real world applications, it is done in early stage of design.
Detailed Design: The detailed design phase is consisted of process flow diagrams,
activity diagrams, state-chart diagrams and many more. These designs are created based on
the input of the use case realization process output. The process flow diagram shows how the
system execute each process and how the end users and other entities of the organization
participate in the process6. The activity diagram is similar to the process flow diagram but
5 Van Rossem, Steven, Xuejun Cai, Ivano Cerrato, Per Danielsson, Felicián Németh, P. Pechenot,
István Pelle et al. "NFV service dynamicity with a DevOps approach: Insights from a use-case realization." In
IM2017, the IEEE International Symposium on Integrated Network Management, pp. 674-679. 2017.
6 Sharma, Chayanika, Sangeeta Sabharwal, and Ritu Sibal. "Applying genetic algorithm for
prioritization of test case scenarios derived from UML diagrams." arXiv preprint arXiv:1410.4838 (2014).
collected. Based on the output of the evaluation, the high level prototypes are created. These
high-level prototypes are the intractable user interface.
The user interfaces are created after all the design paradigms are identified. The use
case realization acts as the most important source of interface information.
Use Case Realization: The use case realization offers a construct for organizing the
entities that visualizes how the logical business behavior is supported by the system physical
design. The use case is the communication medium between the logician and physical aspect
of the system5. The main purpose of the use case realization is defining the physical design of
the system regarding classes and cooperating objects that is supports the use case. Therefore,
the use case realization, can be considered as the based on the use case modeling approach,
are consisted of various UML diagrams like class diagram and several interaction diagrams.
The use case realization is used in the designing phase of the SDLC methodology.
The designing of the system is a very crucial part of the system project as the whole code is
based on the designs. As the real reason behind the use case realization is to establish logical
communication between the real world applications, it is done in early stage of design.
Detailed Design: The detailed design phase is consisted of process flow diagrams,
activity diagrams, state-chart diagrams and many more. These designs are created based on
the input of the use case realization process output. The process flow diagram shows how the
system execute each process and how the end users and other entities of the organization
participate in the process6. The activity diagram is similar to the process flow diagram but
5 Van Rossem, Steven, Xuejun Cai, Ivano Cerrato, Per Danielsson, Felicián Németh, P. Pechenot,
István Pelle et al. "NFV service dynamicity with a DevOps approach: Insights from a use-case realization." In
IM2017, the IEEE International Symposium on Integrated Network Management, pp. 674-679. 2017.
6 Sharma, Chayanika, Sangeeta Sabharwal, and Ritu Sibal. "Applying genetic algorithm for
prioritization of test case scenarios derived from UML diagrams." arXiv preprint arXiv:1410.4838 (2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SYSTEM ANALYSIS AND DESIGN
actually consists of the insight of the system processes. The activity diagram shows how the
system functions would work in response to the user request.
The detailed design process is executed in the final part of the design phase. The
detailed designs and generated based on all the design and requirement of the system
determined in the project.
actually consists of the insight of the system processes. The activity diagram shows how the
system functions would work in response to the user request.
The detailed design process is executed in the final part of the design phase. The
detailed designs and generated based on all the design and requirement of the system
determined in the project.

8SYSTEM ANALYSIS AND DESIGN
Bibliography:
Alexander, Kaitlin, and Stephen M. Easterbrook. "The software architecture of climate
models: a graphical comparison of CMIP5 and EMICAR5 configurations." Geoscientific
Model Development 8, no. 4 (2015): 1221-1232.
Courtney, Karen L., Judith T. Matthews, Julie M. McMillan, L. Mecca Person, Asim
Smailagic, and Daniel Siewiorek. "Usability testing of a prototype multi-user telehealth
kiosk." Studies in health technology and informatics 208 (2015): 109-113.
Elmasri, Ramez, and Sham Navathe. Fundamentals of database systems. London: Pearson,
2016.
Joo, Kyung-Soo, and Jung-Woong Woo. "Development of object-oriented analysis and
design methodology for secure web applications." International Journal of Security and Its
Applications 8, no. 1 (2014): 71-80.
Sharma, Chayanika, Sangeeta Sabharwal, and Ritu Sibal. "Applying genetic algorithm for
prioritization of test case scenarios derived from UML diagrams." arXiv preprint
arXiv:1410.4838 (2014).
Van Rossem, Steven, Xuejun Cai, Ivano Cerrato, Per Danielsson, Felicián Németh, P.
Pechenot, István Pelle et al. "NFV service dynamicity with a DevOps approach: Insights from
a use-case realization." In IM2017, the IEEE International Symposium on Integrated Network
Management, pp. 674-679. 2017.
Bibliography:
Alexander, Kaitlin, and Stephen M. Easterbrook. "The software architecture of climate
models: a graphical comparison of CMIP5 and EMICAR5 configurations." Geoscientific
Model Development 8, no. 4 (2015): 1221-1232.
Courtney, Karen L., Judith T. Matthews, Julie M. McMillan, L. Mecca Person, Asim
Smailagic, and Daniel Siewiorek. "Usability testing of a prototype multi-user telehealth
kiosk." Studies in health technology and informatics 208 (2015): 109-113.
Elmasri, Ramez, and Sham Navathe. Fundamentals of database systems. London: Pearson,
2016.
Joo, Kyung-Soo, and Jung-Woong Woo. "Development of object-oriented analysis and
design methodology for secure web applications." International Journal of Security and Its
Applications 8, no. 1 (2014): 71-80.
Sharma, Chayanika, Sangeeta Sabharwal, and Ritu Sibal. "Applying genetic algorithm for
prioritization of test case scenarios derived from UML diagrams." arXiv preprint
arXiv:1410.4838 (2014).
Van Rossem, Steven, Xuejun Cai, Ivano Cerrato, Per Danielsson, Felicián Németh, P.
Pechenot, István Pelle et al. "NFV service dynamicity with a DevOps approach: Insights from
a use-case realization." In IM2017, the IEEE International Symposium on Integrated Network
Management, pp. 674-679. 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



