System Analysis and Design: Security Issues & Biometric Analysis
VerifiedAdded on 2023/06/14
|7
|1398
|142
Homework Assignment
AI Summary
This assignment delves into key concepts of system analysis and design, focusing on security, biometrics, and cryptography. It addresses the CIA trait (Confidentiality, Integrity, Availability) in the context of ATM security, including PIN protection and data backup strategies. The assignment uses permutation and combination to analyze security vulnerabilities, such as broken ATM keys, and discusses the limitations and challenges of biometric systems, including privacy concerns, potential for false rejections, and accuracy issues. It also examines the implications of false negatives in biometric authentication and provides a cryptographic analysis using substitution and Caesar ciphers. The document emphasizes the importance of multi-factor biometrics to mitigate risks and enhance security in system design.

Running head: SYSTEM ANALYSIS AND DESIGN
SYSTEM ANALYSIS AND DESIGN
Name of the Student
Name of the University
Author Note
SYSTEM ANALYSIS AND DESIGN
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2SYSTEM ANALYSIS AND DESIGN
Table of Contents
Question 1..................................................................................................................................3
Question 2..................................................................................................................................3
Question 3..................................................................................................................................3
Question 4..................................................................................................................................4
Question 5..................................................................................................................................5
References..................................................................................................................................6
Table of Contents
Question 1..................................................................................................................................3
Question 2..................................................................................................................................3
Question 3..................................................................................................................................3
Question 4..................................................................................................................................4
Question 5..................................................................................................................................5
References..................................................................................................................................6

3SYSTEM ANALYSIS AND DESIGN
Question 1
The concept of integrity, confidentiality and availability can be considered as CIA
trait, which is nothing but a model which is implemented for the purpose of guiding the
information security within any form of organization. In this case it can be stated that the
concept of the confidentiality is the privacy aspect I the ATM machine. The PIN number are
designed for the purpose of security so that any type of authorized person do not have the
access to the account of the user. Safeguarding the data from any type of intrusion can be
considered one of the most vital aspects in such cases. In order to achieve the security of the
data there always should be a backup plan, which can be implemented if there is any type of
problem relating to fire or natural disaster (Fernandez & Alexander, 2016).
Question 2
The ATM machine consist of many keys, which have specific operation related to it.
In this case, a thief has entered and broken some of the keys in the machine. In this case, we
would be using the aspect of permutation and combination in order to get the answer.
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
Therefore, it can be stated here that total number of possibility outcome in a particular
situation would be 120. On the other hand, it can be mentioned that the security aspect of the
ATM does allow only three tries to every user to enter their PIN and after the third PIN the
card would be blocked automatically. So taking this into consideration the number of try that
the theft can make is three. This is due to the factor that after the third card he would not be
able to make the next try (Farooq et al., 2015).
Question 3
The main reason behind the reluctant use of the biometric machine are as follows:
Question 1
The concept of integrity, confidentiality and availability can be considered as CIA
trait, which is nothing but a model which is implemented for the purpose of guiding the
information security within any form of organization. In this case it can be stated that the
concept of the confidentiality is the privacy aspect I the ATM machine. The PIN number are
designed for the purpose of security so that any type of authorized person do not have the
access to the account of the user. Safeguarding the data from any type of intrusion can be
considered one of the most vital aspects in such cases. In order to achieve the security of the
data there always should be a backup plan, which can be implemented if there is any type of
problem relating to fire or natural disaster (Fernandez & Alexander, 2016).
Question 2
The ATM machine consist of many keys, which have specific operation related to it.
In this case, a thief has entered and broken some of the keys in the machine. In this case, we
would be using the aspect of permutation and combination in order to get the answer.
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
Therefore, it can be stated here that total number of possibility outcome in a particular
situation would be 120. On the other hand, it can be mentioned that the security aspect of the
ATM does allow only three tries to every user to enter their PIN and after the third PIN the
card would be blocked automatically. So taking this into consideration the number of try that
the theft can make is three. This is due to the factor that after the third card he would not be
able to make the next try (Farooq et al., 2015).
Question 3
The main reason behind the reluctant use of the biometric machine are as follows:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4SYSTEM ANALYSIS AND DESIGN
Privacy is one of the factor, which play a vital role in this aspect. It is seen majorly that
there are different type of privacy issue, which are formed in the different type of
technology, which are used in daily life. If somehow the server of the biometric is
breached it can result in a big problem which cannot be resolved very easily.
Any kind of error may lead to false rejection. The main concept which is applied to the
aspect of the biometric is that the personal detail of the person would be stored in the
database ones the person tries to access it, the data from the database would be accessed.
If the user were located in the database, the person would be allowed or else rejected. In
some cases due to false functionality the user who have the information in the database
are rejected and they cannot access
Lack of accuracy can also be a problem in such type of system. The concept in such a
case is the false identity. It can be seen sometimes that a person with the false identity of
another person would be granted entry. This may result in different types of illegal
activity.
The risk factors, which are stated above, can be removed with the use of multifactor
biometric. The concept is beneficial in a way that help the actual user to be identified quite
easily and help the system to make to wise decision (Choi et al., 2016)
Question 4
The false negative thing in the concept of the biometric is that if the system rejects the
identity of a particular person. It can be a problem due to the aspect of authentication, which
is applied to the concept. Depending on the incident, there can be different types of illegal
activities, which are performed. In most of the cases, the people using the identity of another
person usually involve in different type of unethical activities. When the biometric system is
Privacy is one of the factor, which play a vital role in this aspect. It is seen majorly that
there are different type of privacy issue, which are formed in the different type of
technology, which are used in daily life. If somehow the server of the biometric is
breached it can result in a big problem which cannot be resolved very easily.
Any kind of error may lead to false rejection. The main concept which is applied to the
aspect of the biometric is that the personal detail of the person would be stored in the
database ones the person tries to access it, the data from the database would be accessed.
If the user were located in the database, the person would be allowed or else rejected. In
some cases due to false functionality the user who have the information in the database
are rejected and they cannot access
Lack of accuracy can also be a problem in such type of system. The concept in such a
case is the false identity. It can be seen sometimes that a person with the false identity of
another person would be granted entry. This may result in different types of illegal
activity.
The risk factors, which are stated above, can be removed with the use of multifactor
biometric. The concept is beneficial in a way that help the actual user to be identified quite
easily and help the system to make to wise decision (Choi et al., 2016)
Question 4
The false negative thing in the concept of the biometric is that if the system rejects the
identity of a particular person. It can be a problem due to the aspect of authentication, which
is applied to the concept. Depending on the incident, there can be different types of illegal
activities, which are performed. In most of the cases, the people using the identity of another
person usually involve in different type of unethical activities. When the biometric system is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5SYSTEM ANALYSIS AND DESIGN
implemented in, the organizational level and it lead to problem it can shut down the overall
infrastructure of the organization.
Question 5
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
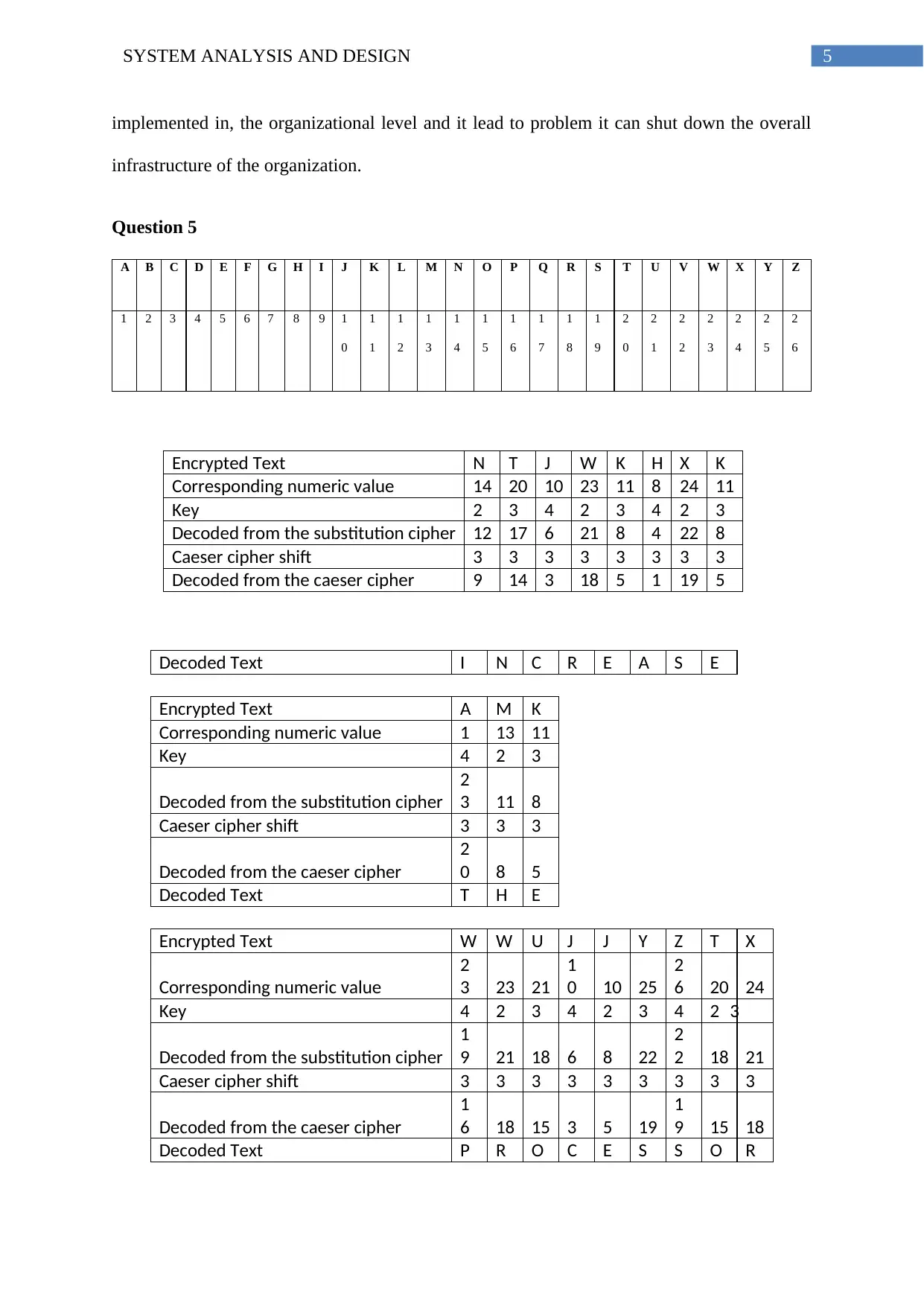
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
implemented in, the organizational level and it lead to problem it can shut down the overall
infrastructure of the organization.
Question 5
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
6SYSTEM ANALYSIS AND DESIGN
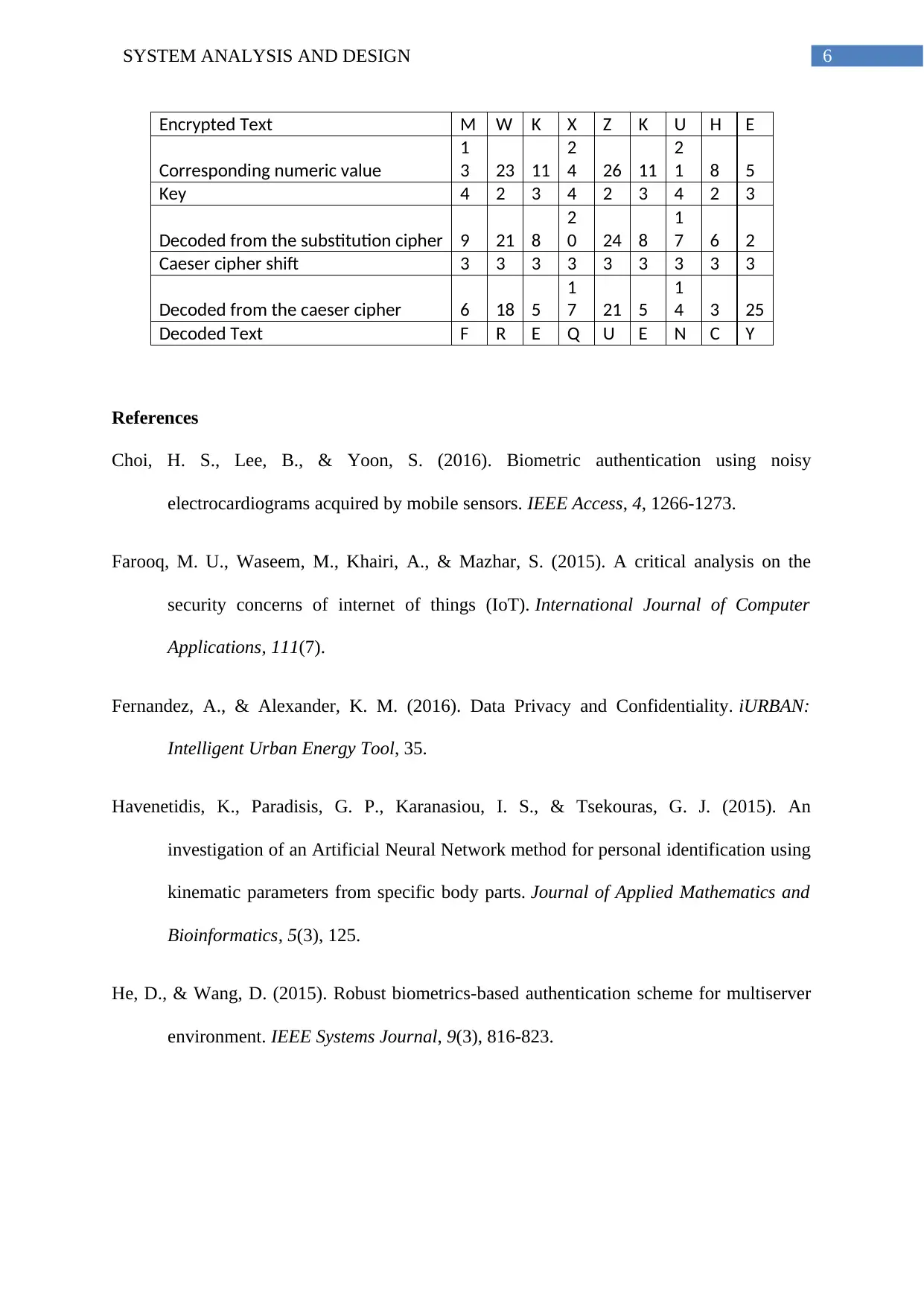
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
References
Choi, H. S., Lee, B., & Yoon, S. (2016). Biometric authentication using noisy
electrocardiograms acquired by mobile sensors. IEEE Access, 4, 1266-1273.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
Fernandez, A., & Alexander, K. M. (2016). Data Privacy and Confidentiality. iURBAN:
Intelligent Urban Energy Tool, 35.
Havenetidis, K., Paradisis, G. P., Karanasiou, I. S., & Tsekouras, G. J. (2015). An
investigation of an Artificial Neural Network method for personal identification using
kinematic parameters from specific body parts. Journal of Applied Mathematics and
Bioinformatics, 5(3), 125.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
References
Choi, H. S., Lee, B., & Yoon, S. (2016). Biometric authentication using noisy
electrocardiograms acquired by mobile sensors. IEEE Access, 4, 1266-1273.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
Fernandez, A., & Alexander, K. M. (2016). Data Privacy and Confidentiality. iURBAN:
Intelligent Urban Energy Tool, 35.
Havenetidis, K., Paradisis, G. P., Karanasiou, I. S., & Tsekouras, G. J. (2015). An
investigation of an Artificial Neural Network method for personal identification using
kinematic parameters from specific body parts. Journal of Applied Mathematics and
Bioinformatics, 5(3), 125.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7SYSTEM ANALYSIS AND DESIGN
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




