Detailed Report on System Architecture, Security, and Quality Metrics
VerifiedAdded on 2022/12/18
|7
|751
|78
Report
AI Summary
This report provides a detailed analysis of a system architecture, focusing on its design, security requirements, and non-functional aspects. It begins with an ER diagram and outlines a client-server architecture, including web server, application server, and database server components. The report emphasizes security, addressing concerns like outdated systems, firewalls, unused ports, cross-site scripting, and DDoS attacks. Non-functional requirements, such as performance, safety, and security, are also discussed. Finally, the report presents quality metrics for evaluating software, detailing characteristics like device dependency, self-containedness, robustness, and consistency. References to relevant sources are included to support the analysis.

Table of Contents
ER diagram......................................................................................................................................2
System architecture..........................................................................................................................2
Security requirements..............................................................................................................................3
Non-functional requirements...................................................................................................................4
Quality metrics.................................................................................................................................4
References........................................................................................................................................7
1
ER diagram......................................................................................................................................2
System architecture..........................................................................................................................2
Security requirements..............................................................................................................................3
Non-functional requirements...................................................................................................................4
Quality metrics.................................................................................................................................4
References........................................................................................................................................7
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
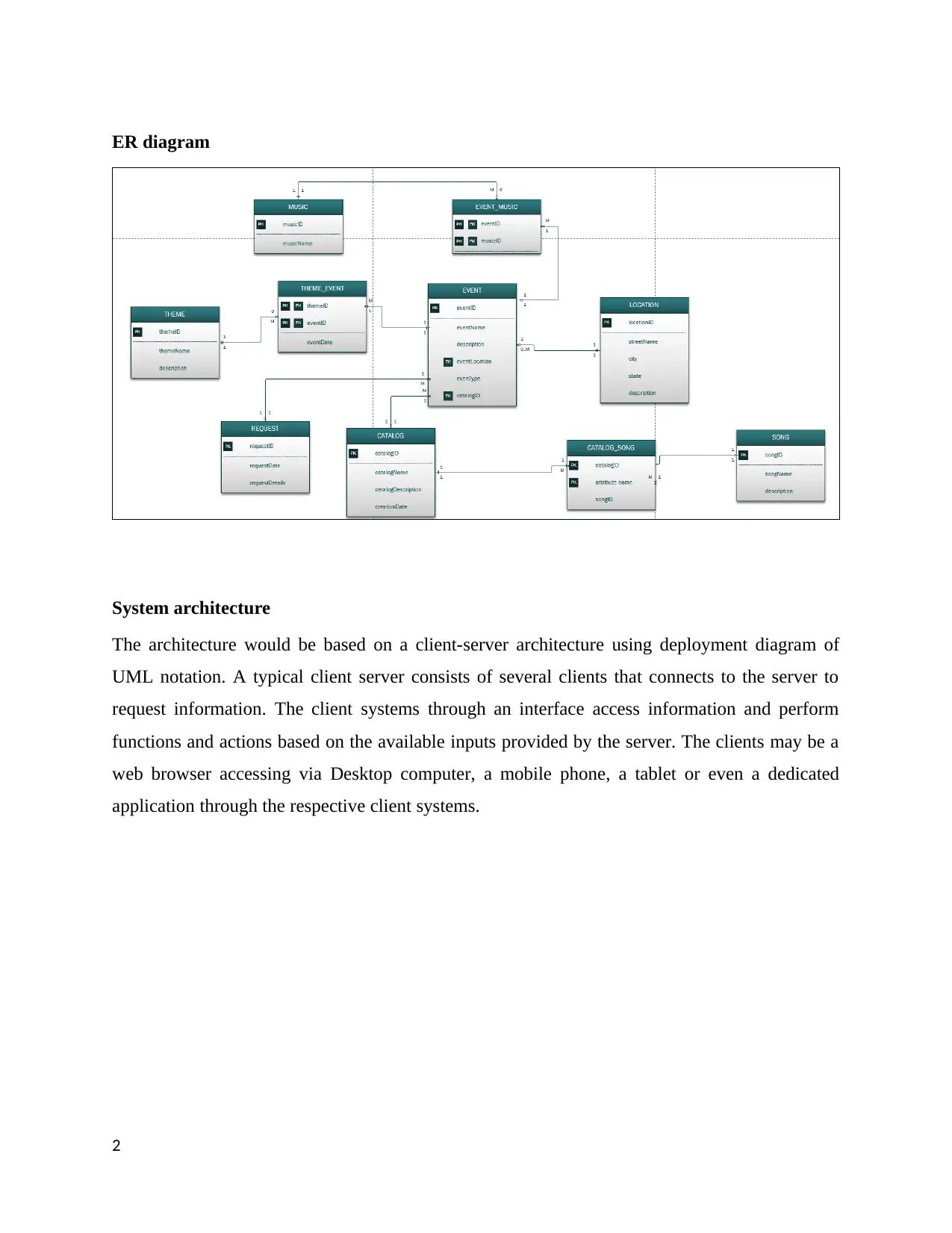
ER diagram
System architecture
The architecture would be based on a client-server architecture using deployment diagram of
UML notation. A typical client server consists of several clients that connects to the server to
request information. The client systems through an interface access information and perform
functions and actions based on the available inputs provided by the server. The clients may be a
web browser accessing via Desktop computer, a mobile phone, a tablet or even a dedicated
application through the respective client systems.
2
System architecture
The architecture would be based on a client-server architecture using deployment diagram of
UML notation. A typical client server consists of several clients that connects to the server to
request information. The client systems through an interface access information and perform
functions and actions based on the available inputs provided by the server. The clients may be a
web browser accessing via Desktop computer, a mobile phone, a tablet or even a dedicated
application through the respective client systems.
2
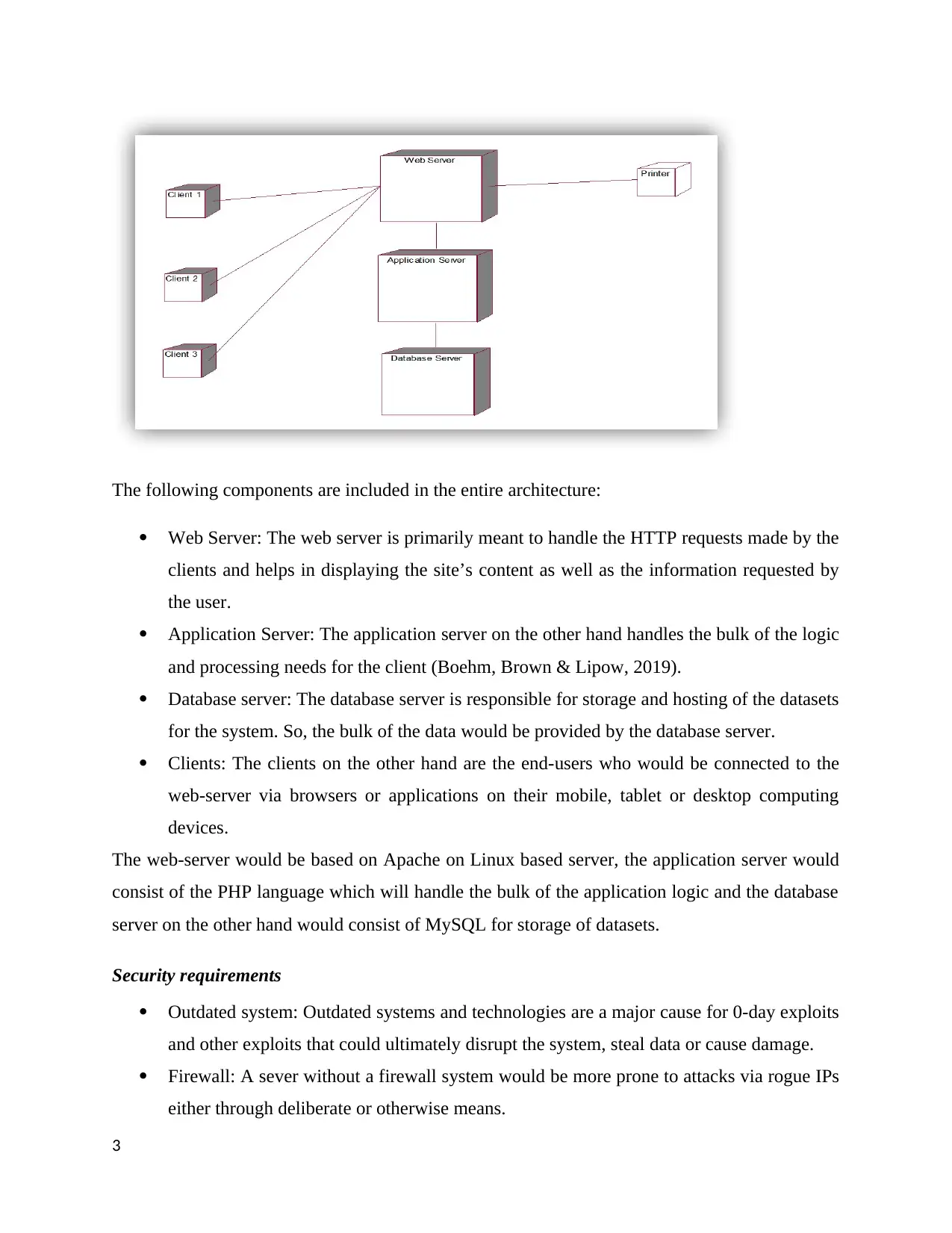
The following components are included in the entire architecture:
Web Server: The web server is primarily meant to handle the HTTP requests made by the
clients and helps in displaying the site’s content as well as the information requested by
the user.
Application Server: The application server on the other hand handles the bulk of the logic
and processing needs for the client (Boehm, Brown & Lipow, 2019).
Database server: The database server is responsible for storage and hosting of the datasets
for the system. So, the bulk of the data would be provided by the database server.
Clients: The clients on the other hand are the end-users who would be connected to the
web-server via browsers or applications on their mobile, tablet or desktop computing
devices.
The web-server would be based on Apache on Linux based server, the application server would
consist of the PHP language which will handle the bulk of the application logic and the database
server on the other hand would consist of MySQL for storage of datasets.
Security requirements
Outdated system: Outdated systems and technologies are a major cause for 0-day exploits
and other exploits that could ultimately disrupt the system, steal data or cause damage.
Firewall: A sever without a firewall system would be more prone to attacks via rogue IPs
either through deliberate or otherwise means.
3
Web Server: The web server is primarily meant to handle the HTTP requests made by the
clients and helps in displaying the site’s content as well as the information requested by
the user.
Application Server: The application server on the other hand handles the bulk of the logic
and processing needs for the client (Boehm, Brown & Lipow, 2019).
Database server: The database server is responsible for storage and hosting of the datasets
for the system. So, the bulk of the data would be provided by the database server.
Clients: The clients on the other hand are the end-users who would be connected to the
web-server via browsers or applications on their mobile, tablet or desktop computing
devices.
The web-server would be based on Apache on Linux based server, the application server would
consist of the PHP language which will handle the bulk of the application logic and the database
server on the other hand would consist of MySQL for storage of datasets.
Security requirements
Outdated system: Outdated systems and technologies are a major cause for 0-day exploits
and other exploits that could ultimately disrupt the system, steal data or cause damage.
Firewall: A sever without a firewall system would be more prone to attacks via rogue IPs
either through deliberate or otherwise means.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Unused ports: Unused ports are another major cause for concerns as hackers could find
such ports and plan an attack via those routes.
Cross-site scripting: Cross-site scripting-based attacks are those that exploit the
vulnerabilities inherent to an unprotected scripts on the website. The same can be used to
steal user data, put an immense load onto the server or corrupt the database.
DDoS: A Distributed Denial of Service Attack is a type of attack wherein the entire
website could be brought to a halt by increasing the load on the server via rogue systems
spread across the world (Dr.M. Balasundaram & K.Poongodi, 2012).
Non-functional requirements
Following are key non-functional requirements of the proposed system:
Performance requirements:
Increased customer satisfaction
Reduction in overall costs
Safety requirements
Backup recovery and business continuity
Security requirements
Account ID and password protection
Failed log-on attempts
Encryption
Auto-timeout screen blanking
Quality metrics
Quality metrics for evaluating the software quality:
Primitive
characteristi
cs
Metric
definition
Correlatio
n with
quality
Potential
advantage
s
Quantifiabilit
y
Ease level
for
automated
evaluation
developme
How
complete
is the
automate
d
4
such ports and plan an attack via those routes.
Cross-site scripting: Cross-site scripting-based attacks are those that exploit the
vulnerabilities inherent to an unprotected scripts on the website. The same can be used to
steal user data, put an immense load onto the server or corrupt the database.
DDoS: A Distributed Denial of Service Attack is a type of attack wherein the entire
website could be brought to a halt by increasing the load on the server via rogue systems
spread across the world (Dr.M. Balasundaram & K.Poongodi, 2012).
Non-functional requirements
Following are key non-functional requirements of the proposed system:
Performance requirements:
Increased customer satisfaction
Reduction in overall costs
Safety requirements
Backup recovery and business continuity
Security requirements
Account ID and password protection
Failed log-on attempts
Encryption
Auto-timeout screen blanking
Quality metrics
Quality metrics for evaluating the software quality:
Primitive
characteristi
cs
Metric
definition
Correlatio
n with
quality
Potential
advantage
s
Quantifiabilit
y
Ease level
for
automated
evaluation
developme
How
complete
is the
automate
d
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
nt evaluatio
n
Device-
dependency
Do the
functionaliti
es of the
proposed
software
independent
of the
underlying
computer for
achieving
required
objectives
such as
precision,
storage
scheme?
Self-
containednes
s
Does the
developed
software has
a facility to
for correct
positioning
of required
input or
output
devices?
Robustness Does the
proposed
5
n
Device-
dependency
Do the
functionaliti
es of the
proposed
software
independent
of the
underlying
computer for
achieving
required
objectives
such as
precision,
storage
scheme?
Self-
containednes
s
Does the
developed
software has
a facility to
for correct
positioning
of required
input or
output
devices?
Robustness Does the
proposed
5
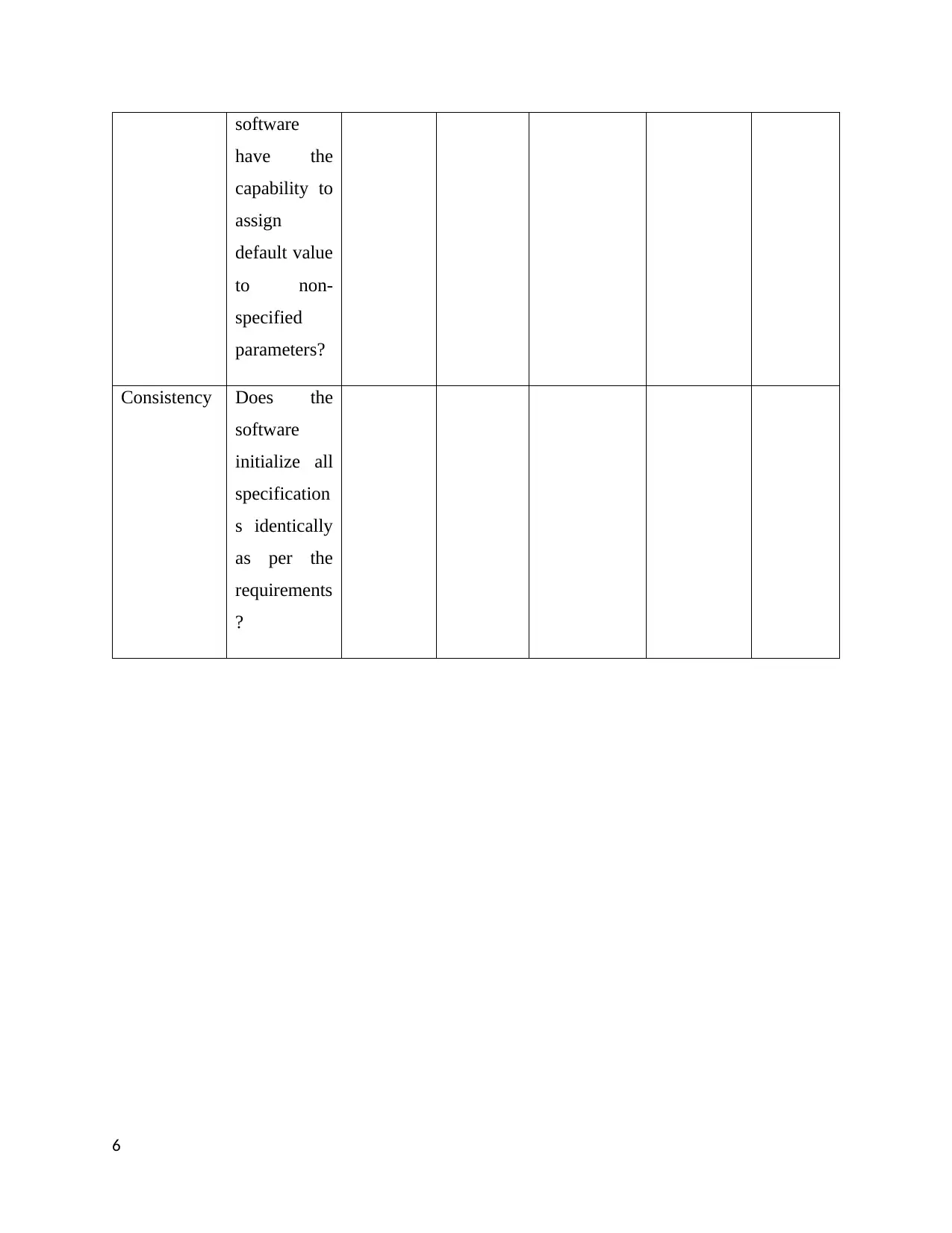
software
have the
capability to
assign
default value
to non-
specified
parameters?
Consistency Does the
software
initialize all
specification
s identically
as per the
requirements
?
6
have the
capability to
assign
default value
to non-
specified
parameters?
Consistency Does the
software
initialize all
specification
s identically
as per the
requirements
?
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Boehm, B., Brown, J., & Lipow, M. (2019). Quantitative Evaluation of Software
Quality [Ebook] (1st ed., pp. 12-14). US. Retrieved from
https://csse.usc.edu/TECHRPTS/1976/usccse76-501/usccse76-501.pdf
Dr.M. Balasundaram, D., & K.Poongodi, K. (2012). Customer Satisfaction With Internet
Banking - An Analytical Study with Special Reference to the Selected Customers in
Namakkal District. Global Journal For Research Analysis, 3(8), 18-20. doi:
10.15373/22778160/august2014/6
7
Boehm, B., Brown, J., & Lipow, M. (2019). Quantitative Evaluation of Software
Quality [Ebook] (1st ed., pp. 12-14). US. Retrieved from
https://csse.usc.edu/TECHRPTS/1976/usccse76-501/usccse76-501.pdf
Dr.M. Balasundaram, D., & K.Poongodi, K. (2012). Customer Satisfaction With Internet
Banking - An Analytical Study with Special Reference to the Selected Customers in
Namakkal District. Global Journal For Research Analysis, 3(8), 18-20. doi:
10.15373/22778160/august2014/6
7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





