CYB-690: System Design Document for Security Architecture
VerifiedAdded on 2022/11/28
|8
|965
|350
Report
AI Summary
This system design document details the creation of a secure organizational architecture, aiming to protect sensitive information from both internal and external security threats. The report starts by outlining design goals, including data identification, storage methods, user access privileges, and authentication systems. It then provides a system overview, detailing the types of data stored (configuration, business-specific, and HRM data), the software and hardware components involved (servers, operating systems, and firewall devices), and the authentication process. The document also addresses potential risks, such as cyberattacks and privilege misuse, along with corresponding countermeasures. It covers low-level implementation aspects, including firewall device implementation and authentication using a Radius server. Finally, it touches upon the human-machine interface and concludes with a summary of the security architecture described. The report also includes references to related academic papers.

Running head: SYSTEM DESIGN DOCUMENT
System Design Document
Name of the Student
Name of the University
Author Note
System Design Document
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SYSTEM DESIGN DOCUMENT
Summary
Security has become the most important aspect of an organization. Hence it is important that
businesses ensure a secure organizational architecture to prevent themselves from becoming
exposed to external as well as internal security risks. The report talks about a design of a
secured architecture that can help typical organizations protect their sensitive information
from security risks by detailing the implementation. Thereafter the report ends with
concluding notes.
SYSTEM DESIGN DOCUMENT
Summary
Security has become the most important aspect of an organization. Hence it is important that
businesses ensure a secure organizational architecture to prevent themselves from becoming
exposed to external as well as internal security risks. The report talks about a design of a
secured architecture that can help typical organizations protect their sensitive information
from security risks by detailing the implementation. Thereafter the report ends with
concluding notes.

2
SYSTEM DESIGN DOCUMENT
Table of Contents
Introduction................................................................................................................................3
Design Document.......................................................................................................................3
Design goals...........................................................................................................................3
System Overview...................................................................................................................3
Potential risks and Countermeasures.....................................................................................4
Low Level implementation....................................................................................................5
Firewall device and perimeter network..............................................................................5
Authentication....................................................................................................................5
Human Machine Interface......................................................................................................6
Conclusion..................................................................................................................................6
References..................................................................................................................................7
SYSTEM DESIGN DOCUMENT
Table of Contents
Introduction................................................................................................................................3
Design Document.......................................................................................................................3
Design goals...........................................................................................................................3
System Overview...................................................................................................................3
Potential risks and Countermeasures.....................................................................................4
Low Level implementation....................................................................................................5
Firewall device and perimeter network..............................................................................5
Authentication....................................................................................................................5
Human Machine Interface......................................................................................................6
Conclusion..................................................................................................................................6
References..................................................................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SYSTEM DESIGN DOCUMENT
Introduction
The following report starts with design goals based on which the security architecture
of the organization is suggested (Olivier, Carlos & Florent, 2015). After that a brief overview
on the overall security architecture is discussed including the devices involved and then low
level implementation is given on security and authentication. After touching on the human
machine interface the report ends with conclusions.
Design Document
Design goals
The goals of designing the system of the organization is to identify the types of the data used
by the organization and whether they are sensitive data.
To understand the way in which such data can be stored and managed and the use of database
management systems.
To find out the types of users requiring access to the data and resources of the organization
and whether the access privileges of these users will vary.
To find out the authentication system in place to ensure right access privileges are granted to
the right class of users.
To know the security systems put in place to secure the operations within the organization
from both external and internal security risks.
System Overview
The organization stores three types of data. These are configuration and diagnostic
data, business specific data as well as HRM related data. These data are stored in the
mainframe data stores which are then managed using the DB2 RDBMS software (Zhao, &
SYSTEM DESIGN DOCUMENT
Introduction
The following report starts with design goals based on which the security architecture
of the organization is suggested (Olivier, Carlos & Florent, 2015). After that a brief overview
on the overall security architecture is discussed including the devices involved and then low
level implementation is given on security and authentication. After touching on the human
machine interface the report ends with conclusions.
Design Document
Design goals
The goals of designing the system of the organization is to identify the types of the data used
by the organization and whether they are sensitive data.
To understand the way in which such data can be stored and managed and the use of database
management systems.
To find out the types of users requiring access to the data and resources of the organization
and whether the access privileges of these users will vary.
To find out the authentication system in place to ensure right access privileges are granted to
the right class of users.
To know the security systems put in place to secure the operations within the organization
from both external and internal security risks.
System Overview
The organization stores three types of data. These are configuration and diagnostic
data, business specific data as well as HRM related data. These data are stored in the
mainframe data stores which are then managed using the DB2 RDBMS software (Zhao, &
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SYSTEM DESIGN DOCUMENT
Yu, 2017). The different servers in use are the network server, the mail server the database
server and the authentication server. All these servers have windows server 2016 installed as
the operating system, the network server has Symantec endpoint security installed for
ensuring firewall and antivirus security from the software side. The mail server has the
roundcube mail configured and setup, the database server is used to manage the databases
using IBM DB2. The authentication server dictates the access levels for the three key classes
of users – network admin, database admin, and other organizational members. The overall
system is further secured from the hardware level through the hardware firewall device
SOPHOS which excludes other users from the internal network of the company.
Potential risks and Countermeasures
Cyber attackers can intrude the company network and compromise the data and
resources. By implementing a firewall device outside the internal network, this threat can be
mitigated.
Escalation and misuse of privileges is another threat that can harm a businesses from
within the organization by their own members. By having specified roles and dedicated
responsibilities to each class of users such incidents and can be immediately identified and
addressed.
SYSTEM DESIGN DOCUMENT
Yu, 2017). The different servers in use are the network server, the mail server the database
server and the authentication server. All these servers have windows server 2016 installed as
the operating system, the network server has Symantec endpoint security installed for
ensuring firewall and antivirus security from the software side. The mail server has the
roundcube mail configured and setup, the database server is used to manage the databases
using IBM DB2. The authentication server dictates the access levels for the three key classes
of users – network admin, database admin, and other organizational members. The overall
system is further secured from the hardware level through the hardware firewall device
SOPHOS which excludes other users from the internal network of the company.
Potential risks and Countermeasures
Cyber attackers can intrude the company network and compromise the data and
resources. By implementing a firewall device outside the internal network, this threat can be
mitigated.
Escalation and misuse of privileges is another threat that can harm a businesses from
within the organization by their own members. By having specified roles and dedicated
responsibilities to each class of users such incidents and can be immediately identified and
addressed.
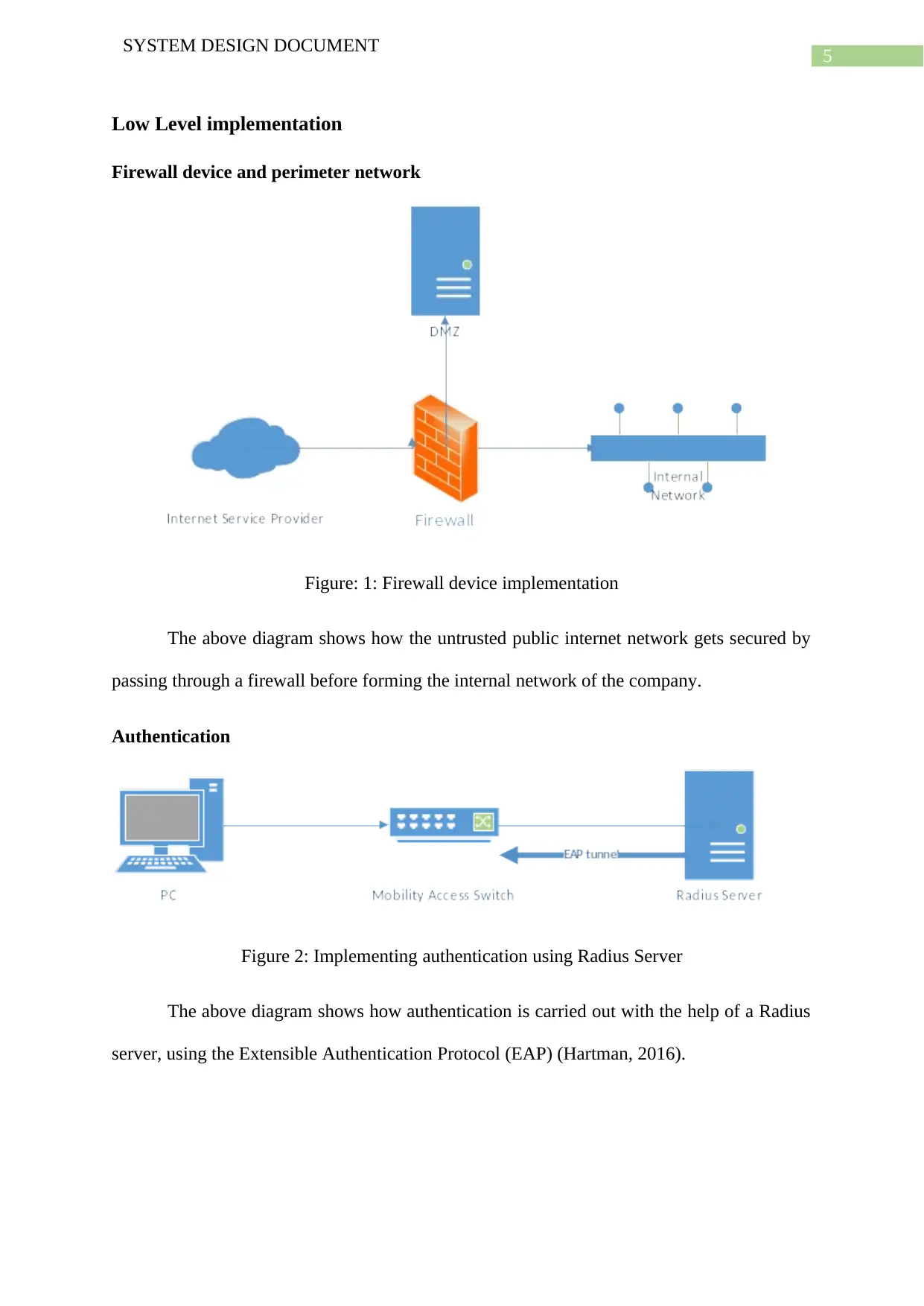
5
SYSTEM DESIGN DOCUMENT
Low Level implementation
Firewall device and perimeter network
Figure: 1: Firewall device implementation
The above diagram shows how the untrusted public internet network gets secured by
passing through a firewall before forming the internal network of the company.
Authentication
Figure 2: Implementing authentication using Radius Server
The above diagram shows how authentication is carried out with the help of a Radius
server, using the Extensible Authentication Protocol (EAP) (Hartman, 2016).
SYSTEM DESIGN DOCUMENT
Low Level implementation
Firewall device and perimeter network
Figure: 1: Firewall device implementation
The above diagram shows how the untrusted public internet network gets secured by
passing through a firewall before forming the internal network of the company.
Authentication
Figure 2: Implementing authentication using Radius Server
The above diagram shows how authentication is carried out with the help of a Radius
server, using the Extensible Authentication Protocol (EAP) (Hartman, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SYSTEM DESIGN DOCUMENT
Human Machine Interface
Here the human machine interface mostly involves knowledge of operating
computers. For most of the members of the organization the process is quite straightforward
as they do not have to think about the configuration and setting up of the systems (Martinsen,
Downey & Baturynska, 2016). For the database administrator, this gets more complex as they
not only have to get the concept of the database but also its implementation. Lastly the
network administrators are responsible for configuring and maintaining the network as well
as overlook the security and authentication mechanisms in place.
Conclusion
In conclusion the above report succeeds in describing the security architecture of the
system and is observed to provide design goals based on which the security architecture of
the organization is suggested. After that a brief overview on the overall security architecture
is discussed including the devices involved and then low level implementation is given on
security and authentication.
SYSTEM DESIGN DOCUMENT
Human Machine Interface
Here the human machine interface mostly involves knowledge of operating
computers. For most of the members of the organization the process is quite straightforward
as they do not have to think about the configuration and setting up of the systems (Martinsen,
Downey & Baturynska, 2016). For the database administrator, this gets more complex as they
not only have to get the concept of the database but also its implementation. Lastly the
network administrators are responsible for configuring and maintaining the network as well
as overlook the security and authentication mechanisms in place.
Conclusion
In conclusion the above report succeeds in describing the security architecture of the
system and is observed to provide design goals based on which the security architecture of
the organization is suggested. After that a brief overview on the overall security architecture
is discussed including the devices involved and then low level implementation is given on
security and authentication.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SYSTEM DESIGN DOCUMENT
References
Hartman, S. (2016). Larger Packets for RADIUS over TCP(No. RFC 7930).
Martinsen, K., Downey, J., & Baturynska, I. (2016). Human-machine interface for artificial
neural network based machine tool process monitoring. Procedia CIRP, 41, 933-938.
Olivier, F., Carlos, G., & Florent, N. (2015). New security architecture for IoT
network. Procedia Computer Science, 52, 1028-1033.
Zhao, K., & Yu, J. X. (2017). Graph Processing in RDBMSs. IEEE Data Eng. Bull., 40(3), 6-
17.
SYSTEM DESIGN DOCUMENT
References
Hartman, S. (2016). Larger Packets for RADIUS over TCP(No. RFC 7930).
Martinsen, K., Downey, J., & Baturynska, I. (2016). Human-machine interface for artificial
neural network based machine tool process monitoring. Procedia CIRP, 41, 933-938.
Olivier, F., Carlos, G., & Florent, N. (2015). New security architecture for IoT
network. Procedia Computer Science, 52, 1028-1033.
Zhao, K., & Yu, J. X. (2017). Graph Processing in RDBMSs. IEEE Data Eng. Bull., 40(3), 6-
17.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




