Wibble Ltd. System Security: Analysis, Design and Implementation
VerifiedAdded on 2021/12/13
|15
|3514
|193
Report
AI Summary
This report provides a detailed analysis of system security for Wibble Ltd., addressing key aspects such as network design, threat analysis, and countermeasure evaluation. The report identifies vulnerabilities in the current network framework, emphasizing the need for firewall configuration and access control lists. It explores various security threats, including active and passive attacks, insider threats, and distributed attacks, and proposes countermeasures like intrusion detection and prevention systems, secure routing protocols, and the implementation of security profiles. The report also covers cryptography approaches and emphasizes the importance of monitoring and logging for maintaining a robust security posture. The report offers valuable insights into designing, implementing, and evaluating efficient security systems, providing a comprehensive guide for enhancing the security of Wibble Ltd.'s digital assets.

Running head: SYSTEM SECURITY
350CT System Security
Name of the Student
Name of the University
Author’s Note
350CT System Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SYSTEM SECURITY
Table of Contents
Introduction................................................................................................................................2
Design, implement, evaluate and maintain efficient security systems.......................................2
Analysis of the possible security threat......................................................................................4
Evaluation of the suitable countermeasures for networked systems..........................................6
Approaches to cryptography......................................................................................................9
Conclusion................................................................................................................................11
References................................................................................................................................12
SYSTEM SECURITY
Table of Contents
Introduction................................................................................................................................2
Design, implement, evaluate and maintain efficient security systems.......................................2
Analysis of the possible security threat......................................................................................4
Evaluation of the suitable countermeasures for networked systems..........................................6
Approaches to cryptography......................................................................................................9
Conclusion................................................................................................................................11
References................................................................................................................................12
2
SYSTEM SECURITY
Introduction
The report is prepared for the development of a system security system for Wibble
Ltd. and protecting the valuable digital assets after the analysis of the security threats. The
risk associated with the network of the organization is evaluated and the security system that
can be implemented for mitigation of the threat are identified for the development of the
security solution. The business framework is analysed for proposing the suitable
countermeasure and develop the network system. The different approaches of cryptography
that can be applied for the management of the security threat is analysed for its application
and minimize the security risk acting on the organization.
Design, implement, evaluate and maintain efficient security systems
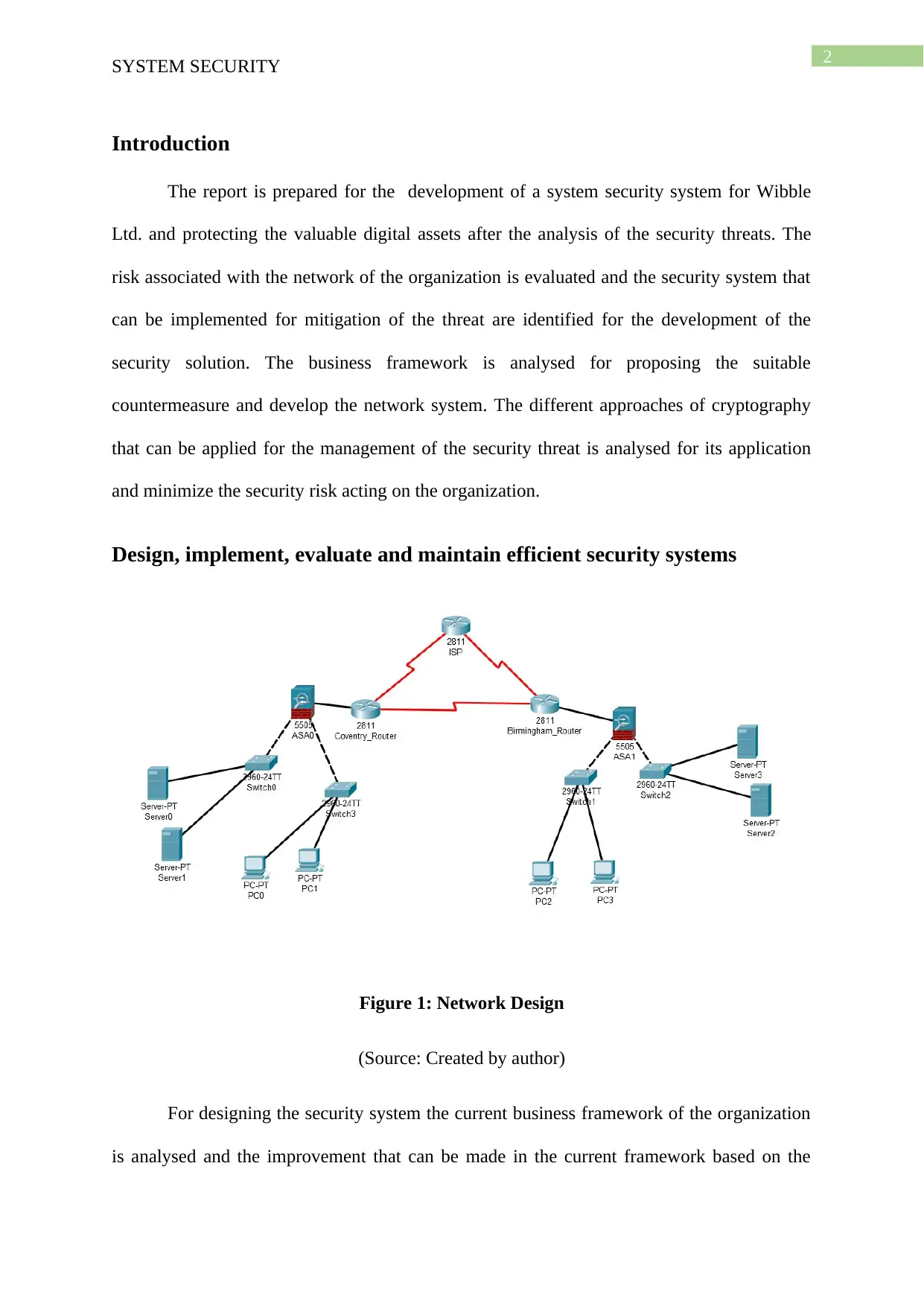
Figure 1: Network Design
(Source: Created by author)
For designing the security system the current business framework of the organization
is analysed and the improvement that can be made in the current framework based on the
SYSTEM SECURITY
Introduction
The report is prepared for the development of a system security system for Wibble
Ltd. and protecting the valuable digital assets after the analysis of the security threats. The
risk associated with the network of the organization is evaluated and the security system that
can be implemented for mitigation of the threat are identified for the development of the
security solution. The business framework is analysed for proposing the suitable
countermeasure and develop the network system. The different approaches of cryptography
that can be applied for the management of the security threat is analysed for its application
and minimize the security risk acting on the organization.
Design, implement, evaluate and maintain efficient security systems
Figure 1: Network Design
(Source: Created by author)
For designing the security system the current business framework of the organization
is analysed and the improvement that can be made in the current framework based on the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SYSTEM SECURITY
security perspective is proposed to the board of directors of Wibble Ltd. The main flaws in
the current architecture identified is the firewall configuration that is needed to be
implemented for increasing the security of hosts and the network device installed in the
internal network. The business rules of the organization is needed to be analysed for the
development of the access control list and restrict the unknown users to access the internal
resources.
For designing the security systems the people, process and the technology should be
organized and the key elements of the business is needed to be identified. The current threats
and vulnerabilities acting on the system is also needed to be evaluated for the development of
the security strategy and developing specific security policy and control for the management
of the operation of the people connected with the network (Izhar et al. 2017). The payroll
system is needed to be secured for the management of the transaction between the user and
the business should be secured such that no information is leaked. The VPN and the security
appliance should be compatible with the other network device and a penetration testing
should be done on the current system for the management of the vulnerability and eliminating
the threat associated with the system (Van Tilborg and Jajodia 2014). The error logs should
be maintained and the network traffic should be monitored for the management of the source
of data traffic and eliminate the disk of distributed denial of service attacks.
The implementation of the intrusion detection system would help to increase the
security of the network by mitigating the risks of external attacks and blocking the new
threats. For the implementation of the intrusion detection system a security policy should be
developed and the system detects the violation of the policy. If it is found that the security
policy is violated the user kicks the user violated the policy and generates an alert for the
security personnel (Trappe 2015). There are some drawbacks of the system that is the threats
that are no defines in the security policy cannot be detected and for this the intrusion
SYSTEM SECURITY
security perspective is proposed to the board of directors of Wibble Ltd. The main flaws in
the current architecture identified is the firewall configuration that is needed to be
implemented for increasing the security of hosts and the network device installed in the
internal network. The business rules of the organization is needed to be analysed for the
development of the access control list and restrict the unknown users to access the internal
resources.
For designing the security systems the people, process and the technology should be
organized and the key elements of the business is needed to be identified. The current threats
and vulnerabilities acting on the system is also needed to be evaluated for the development of
the security strategy and developing specific security policy and control for the management
of the operation of the people connected with the network (Izhar et al. 2017). The payroll
system is needed to be secured for the management of the transaction between the user and
the business should be secured such that no information is leaked. The VPN and the security
appliance should be compatible with the other network device and a penetration testing
should be done on the current system for the management of the vulnerability and eliminating
the threat associated with the system (Van Tilborg and Jajodia 2014). The error logs should
be maintained and the network traffic should be monitored for the management of the source
of data traffic and eliminate the disk of distributed denial of service attacks.
The implementation of the intrusion detection system would help to increase the
security of the network by mitigating the risks of external attacks and blocking the new
threats. For the implementation of the intrusion detection system a security policy should be
developed and the system detects the violation of the policy. If it is found that the security
policy is violated the user kicks the user violated the policy and generates an alert for the
security personnel (Trappe 2015). There are some drawbacks of the system that is the threats
that are no defines in the security policy cannot be detected and for this the intrusion
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SYSTEM SECURITY
prevention system is needed to be combined with the intrusion detection system for the
prevention of the malicious users to access the resources of the network.
The intrusion prevention system can be used for the inspection of the incoming data
traffic in the network and detect the malicious request. The traffic filtering and web
application firewall solutions are used for enforcement of the security and the malicious data
packets are dropped and the malicious IP address are blocked such that they cannot access the
internal resources of the network (Conklin et al. 2015). A pre existing database is used for the
recognition of the signatures and it is programmable for detecting the type of attack by
analysing the anomality and behaviour of the traffic. There are scope of customization of the
IPS configuration that can be used for eliminating the hidden threat maintain the security of
the organizational network.
Analysis of the possible security threat
There are several security risk acting on the current network framework of the
organization and the lack of the network security plan makes the data vulnerable to different
types of attacks and security breaches. The attack can be active or passive where active
means the alteration of the data and passive means monitoring the information (White, Fisch
and Pooch 2017). In most of the cases the data are sent to the receiver in plain text format and
it can be intercepted by the attacker for accessing the information.
In the passive attacks the attacker utilizes the information gathered from the system
without affecting the resources. Network eavesdropping and monitoring the transmission of
data are the two types of passive attacks and it is a difficult task to detect the passive attacks
as no alteration is made on the data and the receiver or the sender is unaware that any third
party is accessing their information (Kumar 2015). This types of attack can be prevented with
SYSTEM SECURITY
prevention system is needed to be combined with the intrusion detection system for the
prevention of the malicious users to access the resources of the network.
The intrusion prevention system can be used for the inspection of the incoming data
traffic in the network and detect the malicious request. The traffic filtering and web
application firewall solutions are used for enforcement of the security and the malicious data
packets are dropped and the malicious IP address are blocked such that they cannot access the
internal resources of the network (Conklin et al. 2015). A pre existing database is used for the
recognition of the signatures and it is programmable for detecting the type of attack by
analysing the anomality and behaviour of the traffic. There are scope of customization of the
IPS configuration that can be used for eliminating the hidden threat maintain the security of
the organizational network.
Analysis of the possible security threat
There are several security risk acting on the current network framework of the
organization and the lack of the network security plan makes the data vulnerable to different
types of attacks and security breaches. The attack can be active or passive where active
means the alteration of the data and passive means monitoring the information (White, Fisch
and Pooch 2017). In most of the cases the data are sent to the receiver in plain text format and
it can be intercepted by the attacker for accessing the information.
In the passive attacks the attacker utilizes the information gathered from the system
without affecting the resources. Network eavesdropping and monitoring the transmission of
data are the two types of passive attacks and it is a difficult task to detect the passive attacks
as no alteration is made on the data and the receiver or the sender is unaware that any third
party is accessing their information (Kumar 2015). This types of attack can be prevented with

5
SYSTEM SECURITY
the implementation of encryption technology and it causes the prevention of the access of the
information.
The active attack causes alteration an modification of stream of data packets and it
can be divided into three types such as:
Masquerade – In this type of attacker creates an entity that pretends as a different
one. The sequence of authentication re captured by the attacker and replayed again and again
at the time of the valid authorization sequence and gaining extra privilege by inter-
personating the entity who has the extra privilege.
Replay – The data stream are captured passively and retransmitting it subsequently
creates an unauthorized access by the third party user.
Modification of message – The legitimate message is intercepted and some part is
modified for creating an unauthorized effect for that message transmission.
There are other types of attack such as distributed attack that are used by the attacker
for creating a backdoor in the network and using an adversary code or trojan virus that are
distributed with the other users and different companies using the organizations network. The
malicious codes are used for gaining the access of the information and creating a backdoor
for functioning later (Dogra and Kohli 2016). The insider attack are caused from an inside
employee who is authorized to use the network and the user may or may not be malicious.
The insider employee performing an attack on the network have an advantage because they
do not have the need breach the authentication system and is familiar with the current
network architecture and the policy and procedures. The organization may have less focus on
protecting the resources from the internal threats and the focus is given on protecting the
network from the outside agents and thus there may be less security against the insider agents
(Pathan 2016). Thus it is recommended that the network monitoring tool should be used for
SYSTEM SECURITY
the implementation of encryption technology and it causes the prevention of the access of the
information.
The active attack causes alteration an modification of stream of data packets and it
can be divided into three types such as:
Masquerade – In this type of attacker creates an entity that pretends as a different
one. The sequence of authentication re captured by the attacker and replayed again and again
at the time of the valid authorization sequence and gaining extra privilege by inter-
personating the entity who has the extra privilege.
Replay – The data stream are captured passively and retransmitting it subsequently
creates an unauthorized access by the third party user.
Modification of message – The legitimate message is intercepted and some part is
modified for creating an unauthorized effect for that message transmission.
There are other types of attack such as distributed attack that are used by the attacker
for creating a backdoor in the network and using an adversary code or trojan virus that are
distributed with the other users and different companies using the organizations network. The
malicious codes are used for gaining the access of the information and creating a backdoor
for functioning later (Dogra and Kohli 2016). The insider attack are caused from an inside
employee who is authorized to use the network and the user may or may not be malicious.
The insider employee performing an attack on the network have an advantage because they
do not have the need breach the authentication system and is familiar with the current
network architecture and the policy and procedures. The organization may have less focus on
protecting the resources from the internal threats and the focus is given on protecting the
network from the outside agents and thus there may be less security against the insider agents
(Pathan 2016). Thus it is recommended that the network monitoring tool should be used for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SYSTEM SECURITY
the identification of the flow of data packets in different sources in the network and track the
activity of the user for securing the network framework.
The installation of the network monitoring tool would also help to mitigate the risk of
phishing attack, buffer overflow and exploit attacks. In the hijacking attack the attacker can
take over the session of a normal user and the server disconnect the other user from
communicating with the server (Joshi and Karkade 2015). The normal user can accidentally
send private information to the server that can be accessed by the hacker.
Evaluation of the suitable countermeasures for networked systems
For increasing the security of the network infrastructure the hardware device used for
communication should be configured with the secured routing protocols. WAP protocol can
be implemented for the identification of the fake nodes and adoption of preventive measures
against the nodes such that it does not reappears during the discovery phase. The protocol
monitors the neighbour node and warmhole route detection methodology for the source node
on the route selected for communication (Wang et al. 2015). There are no extra requirement
of hardware for the implementation of the protocol but it has a major disadvantage i.e. it
cannot be used for detection of other types of attacks and has high overhead.
For the development of the countermeasure an analysis should be done on the
technical aspects and the countermeasure is developed based on the following phases.
Identification of assets
In this phase the assets should be identified and secured from different types of
attacks. It users or application directly accessing the resources should be identified and
documented. The resources indirectly managed or accessed should also be identified for its
impact on the business and reputation of the business.
SYSTEM SECURITY
the identification of the flow of data packets in different sources in the network and track the
activity of the user for securing the network framework.
The installation of the network monitoring tool would also help to mitigate the risk of
phishing attack, buffer overflow and exploit attacks. In the hijacking attack the attacker can
take over the session of a normal user and the server disconnect the other user from
communicating with the server (Joshi and Karkade 2015). The normal user can accidentally
send private information to the server that can be accessed by the hacker.
Evaluation of the suitable countermeasures for networked systems
For increasing the security of the network infrastructure the hardware device used for
communication should be configured with the secured routing protocols. WAP protocol can
be implemented for the identification of the fake nodes and adoption of preventive measures
against the nodes such that it does not reappears during the discovery phase. The protocol
monitors the neighbour node and warmhole route detection methodology for the source node
on the route selected for communication (Wang et al. 2015). There are no extra requirement
of hardware for the implementation of the protocol but it has a major disadvantage i.e. it
cannot be used for detection of other types of attacks and has high overhead.
For the development of the countermeasure an analysis should be done on the
technical aspects and the countermeasure is developed based on the following phases.
Identification of assets
In this phase the assets should be identified and secured from different types of
attacks. It users or application directly accessing the resources should be identified and
documented. The resources indirectly managed or accessed should also be identified for its
impact on the business and reputation of the business.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SYSTEM SECURITY
Defining the security Objectives
The confidentiality level, availability and the integrity is related with the security
objectives and protection of the valuable information from the malicious users. The security
objectives should be defined the relevant type of information should be categorized under the
group of confidentiality, integrity and availability (Scherzer and Scherzer 2013). The
objectives are mainly derived based on the security breach and its impact level for protecting
the valuable information.
Creating an overview of the architecture
The functionality of the application should be identified and documented with the
other relevant information such as the architecture information, configuration details for
physical deployment and the other subsystems.
Creation of a profile for the web application
A security profile should be created and the server should be configured with active
directory configuration for the management of the user activity. The implementation of
authorization, authentication and access control helps in mitigation of the internal threats and
tracking the flow of data in the organizational network (Neuhaeuser and D'Angelo 2013). The
user should be restricted to change any configuration or install third party application in their
system because it can make the system vulnerable and allow the intruder to access the
network using the system. The management of the user account is important and thus groups
are created in the active directory and the users are categorized and added in the group
depending upon their roles and services required.
Identification of the threats
SYSTEM SECURITY
Defining the security Objectives
The confidentiality level, availability and the integrity is related with the security
objectives and protection of the valuable information from the malicious users. The security
objectives should be defined the relevant type of information should be categorized under the
group of confidentiality, integrity and availability (Scherzer and Scherzer 2013). The
objectives are mainly derived based on the security breach and its impact level for protecting
the valuable information.
Creating an overview of the architecture
The functionality of the application should be identified and documented with the
other relevant information such as the architecture information, configuration details for
physical deployment and the other subsystems.
Creation of a profile for the web application
A security profile should be created and the server should be configured with active
directory configuration for the management of the user activity. The implementation of
authorization, authentication and access control helps in mitigation of the internal threats and
tracking the flow of data in the organizational network (Neuhaeuser and D'Angelo 2013). The
user should be restricted to change any configuration or install third party application in their
system because it can make the system vulnerable and allow the intruder to access the
network using the system. The management of the user account is important and thus groups
are created in the active directory and the users are categorized and added in the group
depending upon their roles and services required.
Identification of the threats
8
SYSTEM SECURITY
A threat profile should be created for the identification of the path of attack and
categorizing them for meeting the objectives. The threats action on the network should be
categorized and it should be defined for adoption of the appropriate countermeasures. Th
following table is created for categorizing the threat and defining it.
Category Definition
Spoofing To access the username and password
information or any other authentication or
identification illegally for authenticating
with an information system
Tampering Unauthorized access and modification of
data in the database or between the two
clients sending and receiving data packets in
the network.
Repudiation It defines the user ability for denying the
actions or transaction performed by him.
Disclosure of information Exposure of the private data unwantedly
Denial of service In this process the system or an application
is made unavailable for the intended group
of users
Privilege elevation It is an internal threat and occurs when an
user with limited privilege uses the identity
of a user with more privilege for accessing
information or services for comprising the
entire system.
Rating the threats
SYSTEM SECURITY
A threat profile should be created for the identification of the path of attack and
categorizing them for meeting the objectives. The threats action on the network should be
categorized and it should be defined for adoption of the appropriate countermeasures. Th
following table is created for categorizing the threat and defining it.
Category Definition
Spoofing To access the username and password
information or any other authentication or
identification illegally for authenticating
with an information system
Tampering Unauthorized access and modification of
data in the database or between the two
clients sending and receiving data packets in
the network.
Repudiation It defines the user ability for denying the
actions or transaction performed by him.
Disclosure of information Exposure of the private data unwantedly
Denial of service In this process the system or an application
is made unavailable for the intended group
of users
Privilege elevation It is an internal threat and occurs when an
user with limited privilege uses the identity
of a user with more privilege for accessing
information or services for comprising the
entire system.
Rating the threats
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
SYSTEM SECURITY
The threats acting on the system should be rated according to their level of severity
and their impact on the business process. There are different factors that should be considered
for rating a threat such as attack likelihood, estimation of its potential impact on the sensitive
information, existing vulnerability, etc (Mahalingam et al. 2014). The risk should be rated
based on their damage potential and its adverse effect on the security of valuable assets.
Countermeasures
There are different control measures that can eb applied for increasing the security of
the networked system such as adoption of security control and techniques for the prevention
of exploitation of the unknown vulnerabilities acting on the system. The technical goals and
the organizational goals can be encompassed to form the counter measure. Security software
development methodology can be implemented for the development of the online web store
and the security guidelines should be followed for the development of the system. The
application of the threat modelling process and configuring the server with active directory
can also help in management of the internal and external threat acting on the network.
Approaches to cryptography
Cryptography is used for converting the ordinary text into unintelligible text using
different algorithm and keys. In this methodology data is stored and transmitted in particular
form such that the intended user can only read the data. In this process the data is protected
from theft or alteration and it also finds its application in authenticating the user. The
application of the cryptography helps in increasing the confidentiality, integrity, non-
repudiation and authentication of the user and secures the network from the external threats
(Kaur and Singh 2014). The cryptography finds its application in different types of
applications and services like computer password, e commerce transaction, banking
SYSTEM SECURITY
The threats acting on the system should be rated according to their level of severity
and their impact on the business process. There are different factors that should be considered
for rating a threat such as attack likelihood, estimation of its potential impact on the sensitive
information, existing vulnerability, etc (Mahalingam et al. 2014). The risk should be rated
based on their damage potential and its adverse effect on the security of valuable assets.
Countermeasures
There are different control measures that can eb applied for increasing the security of
the networked system such as adoption of security control and techniques for the prevention
of exploitation of the unknown vulnerabilities acting on the system. The technical goals and
the organizational goals can be encompassed to form the counter measure. Security software
development methodology can be implemented for the development of the online web store
and the security guidelines should be followed for the development of the system. The
application of the threat modelling process and configuring the server with active directory
can also help in management of the internal and external threat acting on the network.
Approaches to cryptography
Cryptography is used for converting the ordinary text into unintelligible text using
different algorithm and keys. In this methodology data is stored and transmitted in particular
form such that the intended user can only read the data. In this process the data is protected
from theft or alteration and it also finds its application in authenticating the user. The
application of the cryptography helps in increasing the confidentiality, integrity, non-
repudiation and authentication of the user and secures the network from the external threats
(Kaur and Singh 2014). The cryptography finds its application in different types of
applications and services like computer password, e commerce transaction, banking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
SYSTEM SECURITY
application, etc. There are different types of cryptographic techniques that are used in
different fields of communication and are described below:
Secret-key cryptography – In this mechanism the sender and the receiver uses a single
key. The key is used by the sender to encrypt the plain text into cipher text and send it
to the receiver whereas the receiver uses the key for decrypting the cipher text into
plain text and recover the message.
Public-key cryptography – In this mechanism two keys are used i.e. public key and
private key. The public key is distributed to the receiver after pairing it with the
private key and the private key (Bezukladnikov, Dadenkov and Kon 2016). For
performing the encryption of the file or message the public key is used and for the
decryption the private key is used. It can be applied in the network framework for the
transmission of files and information between the head office and the branches such
that the information does not gets intercepted and used for illegal activity.
Digital Signatures – It is a mathematical technique that is used for the validation of
the integrity and authenticity of the message, digital document or software. It is
equivalent with the stamped or handwritten signature and is more secure for solving
problems related with impersonating and solving problems related with
communication (Asrani, Koul and Khot 2016). With the implementation of the digital
signature the origin of the file can be identified along with other information such as
identity of the sender and status of the document.
Digital Certificates – It is an attachment that is used for the security purpose and used
for the verification of the identity of the user sending the message. The digital
certificate contains the public key and other information needed for the identification
of the user (Manjusha and Ramachandran 2015). It is used for adding more security
SYSTEM SECURITY
application, etc. There are different types of cryptographic techniques that are used in
different fields of communication and are described below:
Secret-key cryptography – In this mechanism the sender and the receiver uses a single
key. The key is used by the sender to encrypt the plain text into cipher text and send it
to the receiver whereas the receiver uses the key for decrypting the cipher text into
plain text and recover the message.
Public-key cryptography – In this mechanism two keys are used i.e. public key and
private key. The public key is distributed to the receiver after pairing it with the
private key and the private key (Bezukladnikov, Dadenkov and Kon 2016). For
performing the encryption of the file or message the public key is used and for the
decryption the private key is used. It can be applied in the network framework for the
transmission of files and information between the head office and the branches such
that the information does not gets intercepted and used for illegal activity.
Digital Signatures – It is a mathematical technique that is used for the validation of
the integrity and authenticity of the message, digital document or software. It is
equivalent with the stamped or handwritten signature and is more secure for solving
problems related with impersonating and solving problems related with
communication (Asrani, Koul and Khot 2016). With the implementation of the digital
signature the origin of the file can be identified along with other information such as
identity of the sender and status of the document.
Digital Certificates – It is an attachment that is used for the security purpose and used
for the verification of the identity of the user sending the message. The digital
certificate contains the public key and other information needed for the identification
of the user (Manjusha and Ramachandran 2015). It is used for adding more security

11
SYSTEM SECURITY
for the public key cryptography and mitigate the risk associated with transferring of
sensitive information in the network.
Authentications – It is used for providing access control to the user by checking the
identity of the user. The authentication works by matching the credentials of the
authorized user using the data residing in the authentication server.
Conclusion
From the above report it can be concluded that with the development of the secure
network framework the organization would be benefitted for securing the organizational
information. The different security mechanism that is used for securing the network
framework is analysed and documented in the report. An analysis is done on the threats and
vulnerability acting on the system for the selection of the security mechanism and secure the
network from the malicious agents. The vulnerability acting on the system should also be
categorized after performing a security analysis and a penetration testing should be done for
finding the flaws in the system and secure it from the external users.
SYSTEM SECURITY
for the public key cryptography and mitigate the risk associated with transferring of
sensitive information in the network.
Authentications – It is used for providing access control to the user by checking the
identity of the user. The authentication works by matching the credentials of the
authorized user using the data residing in the authentication server.
Conclusion
From the above report it can be concluded that with the development of the secure
network framework the organization would be benefitted for securing the organizational
information. The different security mechanism that is used for securing the network
framework is analysed and documented in the report. An analysis is done on the threats and
vulnerability acting on the system for the selection of the security mechanism and secure the
network from the malicious agents. The vulnerability acting on the system should also be
categorized after performing a security analysis and a penetration testing should be done for
finding the flaws in the system and secure it from the external users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





