System Security: WebGoat, Kali, BackTrack VM and Network Scanning
VerifiedAdded on 2020/01/07
|13
|999
|347
Practical Assignment
AI Summary
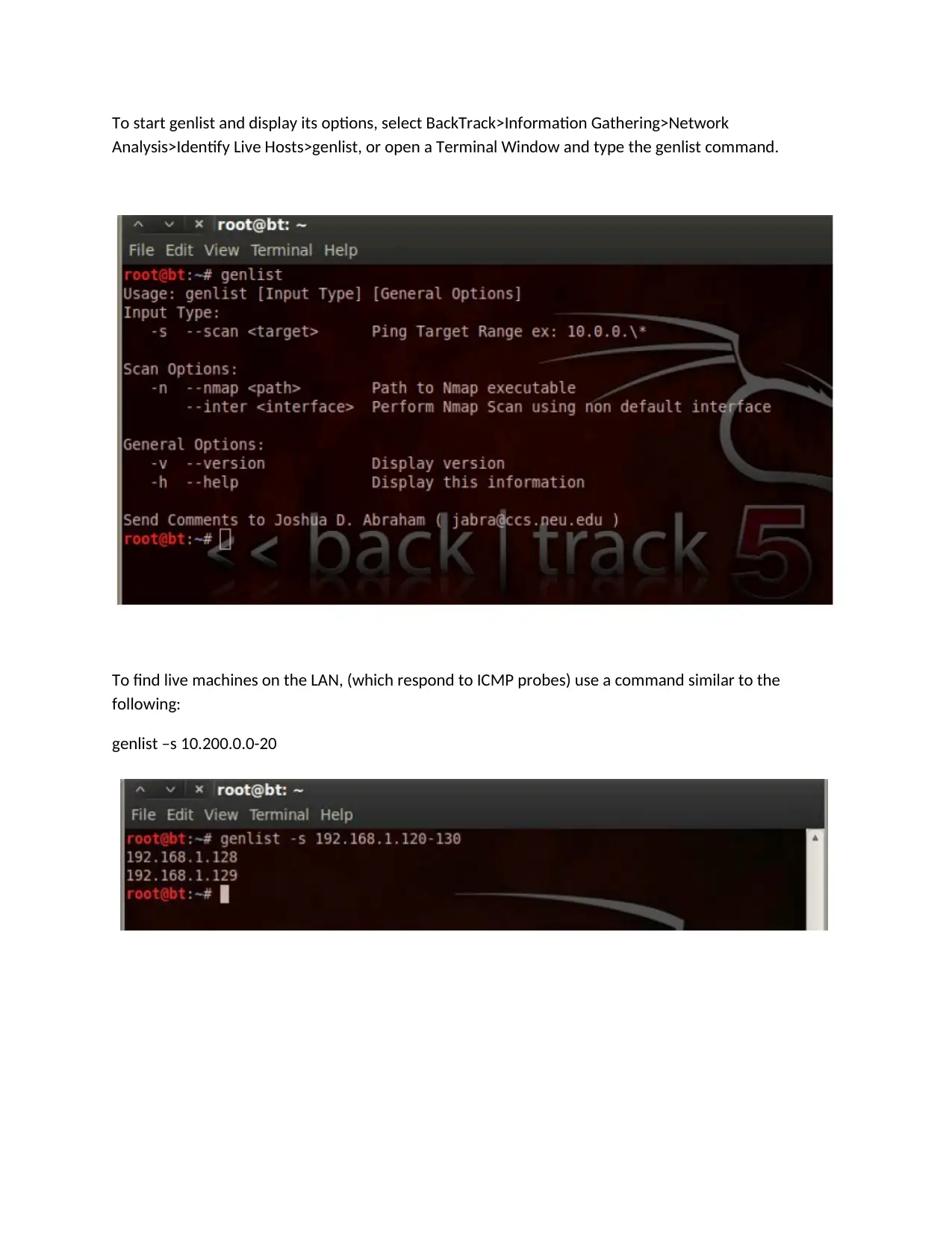
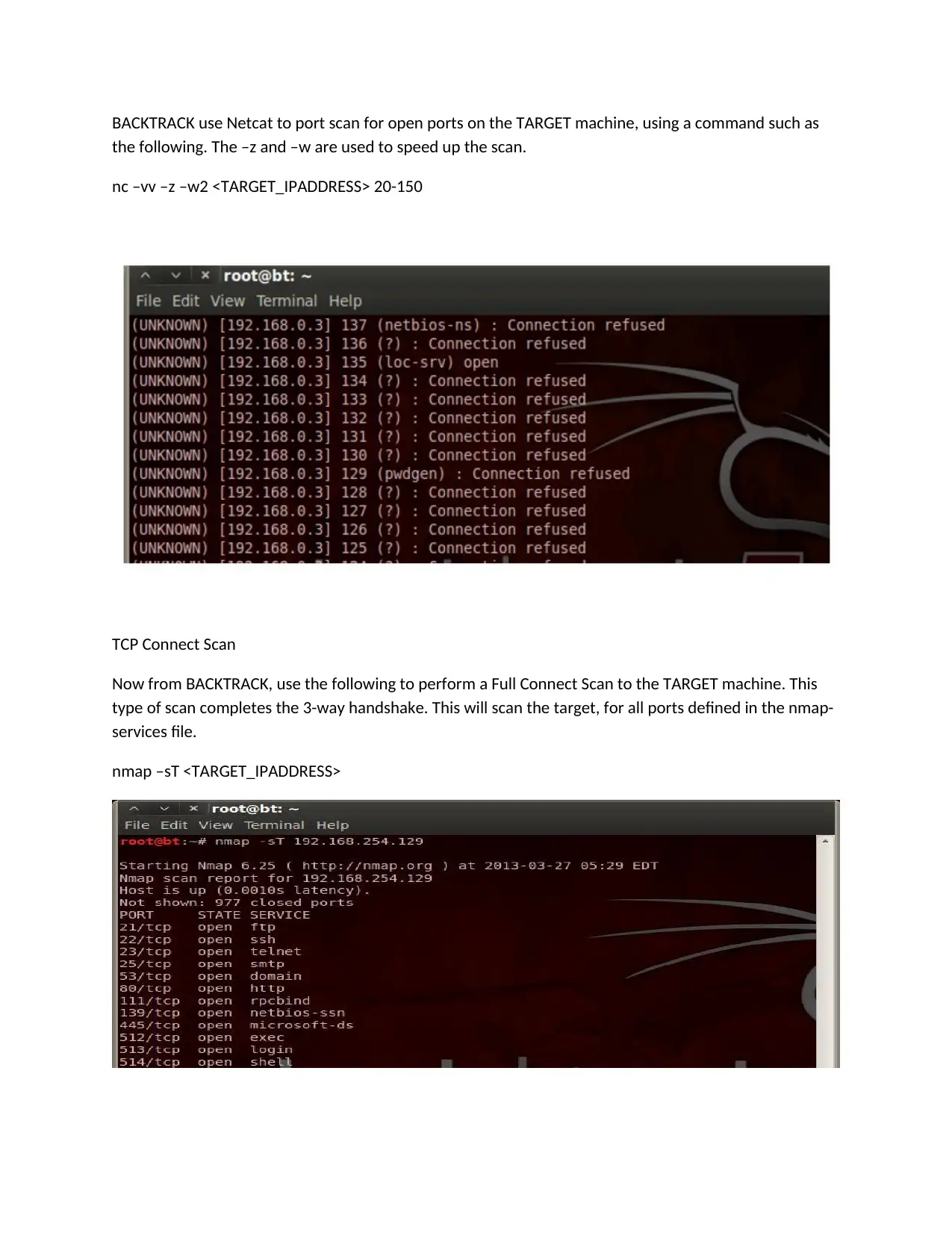
This assignment details the setup and use of WebGoat on a Kali Linux virtual machine, alongside the utilization of a BackTrack VM for security testing. Part A focuses on installing and configuring WebGoat, a deliberately vulnerable web application, and explores common web application vulnerabilities like parameter tampering, insecure storage, injection flaws (including SQL injection), cross-site scripting (XSS), and insecure communication. The assignment provides instructions for exploiting XSS vulnerabilities by injecting malicious scripts and understanding the concepts of Stored XSS and CSRF attacks. Part B shifts to a BackTrack environment, guiding the user through network scanning techniques using Nmap and Netcat to identify live hosts and open ports on a target machine. The assignment emphasizes the practical application of these tools to perform connect scans and assess the target's network security posture. References to external resources for CUDA programming and security concepts are also provided.
1 out of 13



![[object Object]](/_next/static/media/star-bottom.7253800d.svg)