Computer Security: System Investigation Report - CO4509, UCLAN
VerifiedAdded on 2023/02/01
|25
|3821
|87
Report
AI Summary
This report details a system security investigation conducted on a VMware virtual machine provided by Benny Vandergast Inc. The project involved identifying the IP address, usernames, and passwords of the system. The investigation focused on evaluating the security of the system, including aspects like security patches, communication issues, network service problems, password settings, and potential threats from viruses and malware. The student utilized tools such as Lynis to conduct security audits and assessments, identifying vulnerabilities and weaknesses in the system's configuration. The report outlines the methods used for the investigation, presents the results obtained from security tests, and proposes solutions for securing the system, including hardening SSH, configuring sudo, and implementing web server hardening techniques. The report aims to provide a comprehensive analysis of the system's security posture and offer practical recommendations for improvement.

University
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
1
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Project Description............................................................................................................................3
2. VM ware Image File Installation......................................................................................................3
3. Description of Investigate of the System Security............................................................................8
4. Description of the Results...............................................................................................................11
5. Proposal on how to secure the System............................................................................................22
References...........................................................................................................................................24
2
1. Project Description............................................................................................................................3
2. VM ware Image File Installation......................................................................................................3
3. Description of Investigate of the System Security............................................................................8
4. Description of the Results...............................................................................................................11
5. Proposal on how to secure the System............................................................................................22
References...........................................................................................................................................24
2

Project Description
In this Project we shall discuss about System Security and how best to utilise different
tools for minimising the threats to our Network. We shall be using the platform of VM image
files. i.e. Virtual Machines. Now, a virtual machine is a software computer that, like a
physical computer, runs an operating system and applications and is based on computer
architectures which provides functionality of a physical computer. The virtual machine is
comprised of a set of specification and configuration files and is backed by the physical
resources of a host.
VM ware Image File Installation
Many firms provide VM’s in the market based upon the Operating System in use.
Widget Inc is one such company and we shall use the VM provided by it for our Project.
What we will be doing during this whole project is that, we shall conduct various Tests and
Security checks on our System on VM platform and then, identify, understand, study and
make a Result based on our tests (Lange, 2018). Now, our concentration of these tests and
trials will be specifically for Security and Safety in general. We shall make use of particular
Safety Tools like Lynis to conduct the above mentioned Tests on the VM’s.
a. The Exercise of Testing and Assessment will cover the below topics,
b. A Planned method of Security System Inspection.
c. Tools required for this Inspection of Security.
d. Analysing the outcome of this Inspection
No we come to the part where the VM file will be installed for use (Hamid, 2017). Follow the
below steps for using the VM File on the system,
The VM File has to be downloaded on our System in use.
Start installing the VM work station once the down load has been completed.
Complete the process of installing the VM work station.
Open the VM work station as shown in the below image.
3
In this Project we shall discuss about System Security and how best to utilise different
tools for minimising the threats to our Network. We shall be using the platform of VM image
files. i.e. Virtual Machines. Now, a virtual machine is a software computer that, like a
physical computer, runs an operating system and applications and is based on computer
architectures which provides functionality of a physical computer. The virtual machine is
comprised of a set of specification and configuration files and is backed by the physical
resources of a host.
VM ware Image File Installation
Many firms provide VM’s in the market based upon the Operating System in use.
Widget Inc is one such company and we shall use the VM provided by it for our Project.
What we will be doing during this whole project is that, we shall conduct various Tests and
Security checks on our System on VM platform and then, identify, understand, study and
make a Result based on our tests (Lange, 2018). Now, our concentration of these tests and
trials will be specifically for Security and Safety in general. We shall make use of particular
Safety Tools like Lynis to conduct the above mentioned Tests on the VM’s.
a. The Exercise of Testing and Assessment will cover the below topics,
b. A Planned method of Security System Inspection.
c. Tools required for this Inspection of Security.
d. Analysing the outcome of this Inspection
No we come to the part where the VM file will be installed for use (Hamid, 2017). Follow the
below steps for using the VM File on the system,
The VM File has to be downloaded on our System in use.
Start installing the VM work station once the down load has been completed.
Complete the process of installing the VM work station.
Open the VM work station as shown in the below image.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
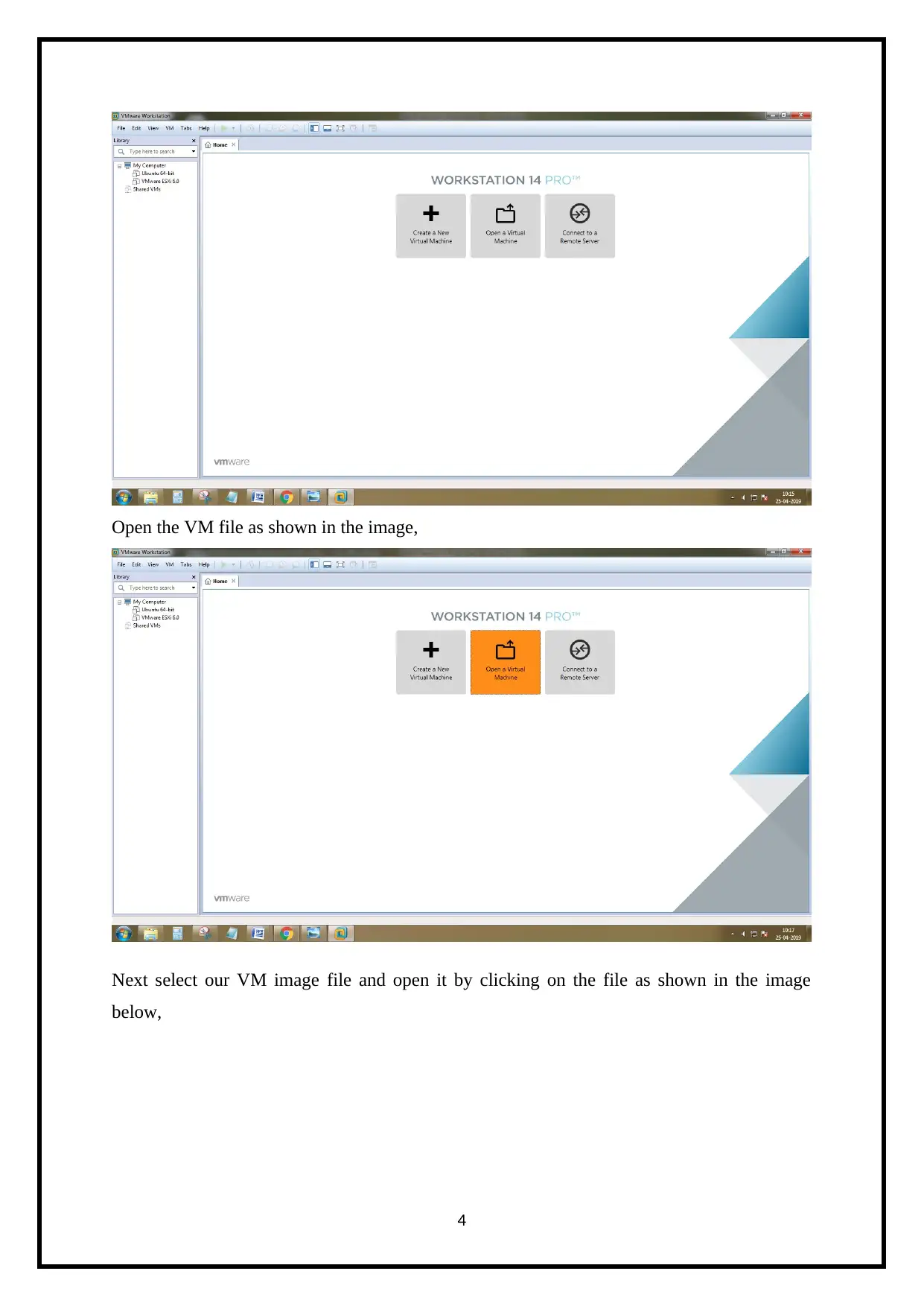
Open the VM file as shown in the image,
Next select our VM image file and open it by clicking on the file as shown in the image
below,
4
Next select our VM image file and open it by clicking on the file as shown in the image
below,
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
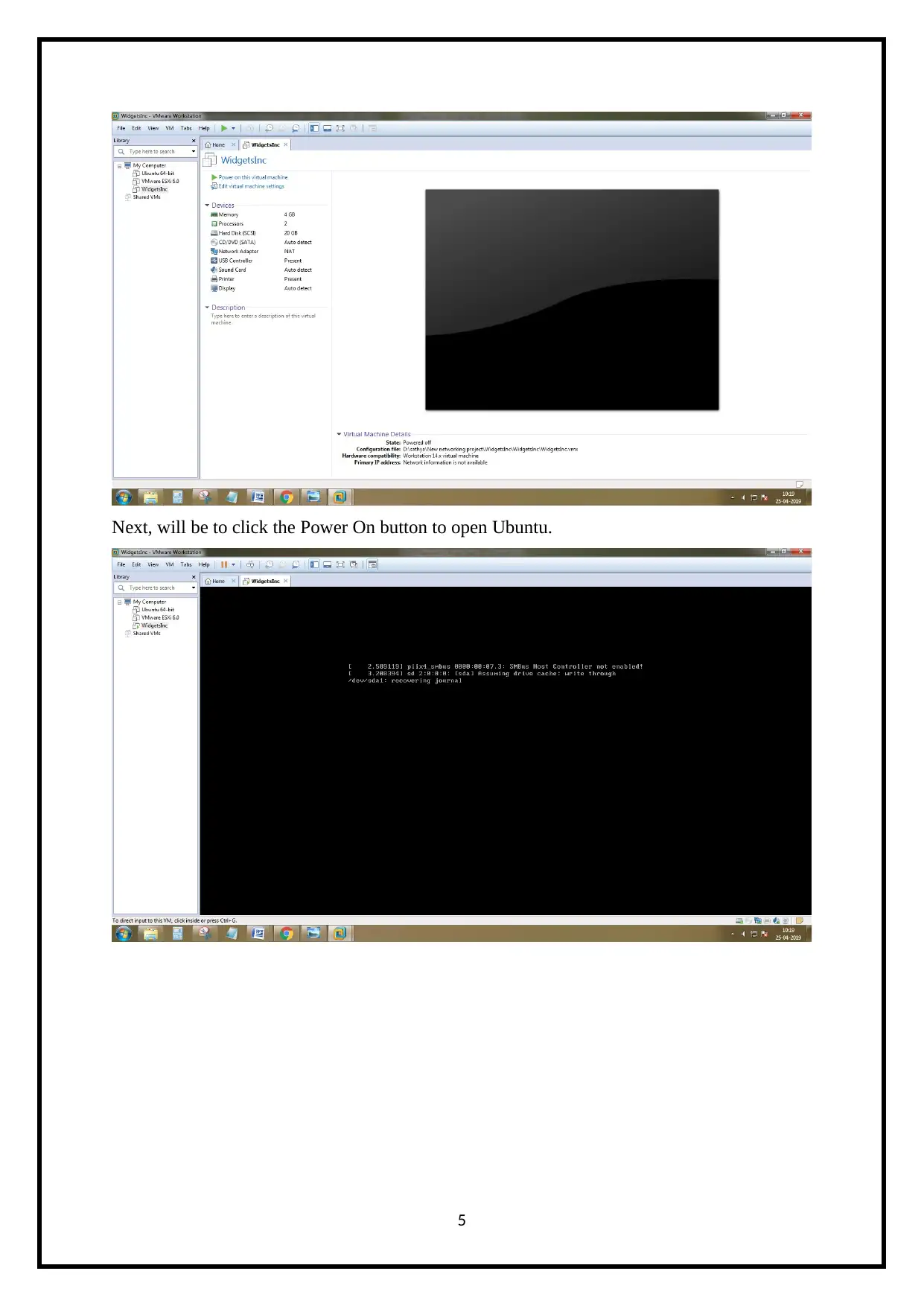
Next, will be to click the Power On button to open Ubuntu.
5
5
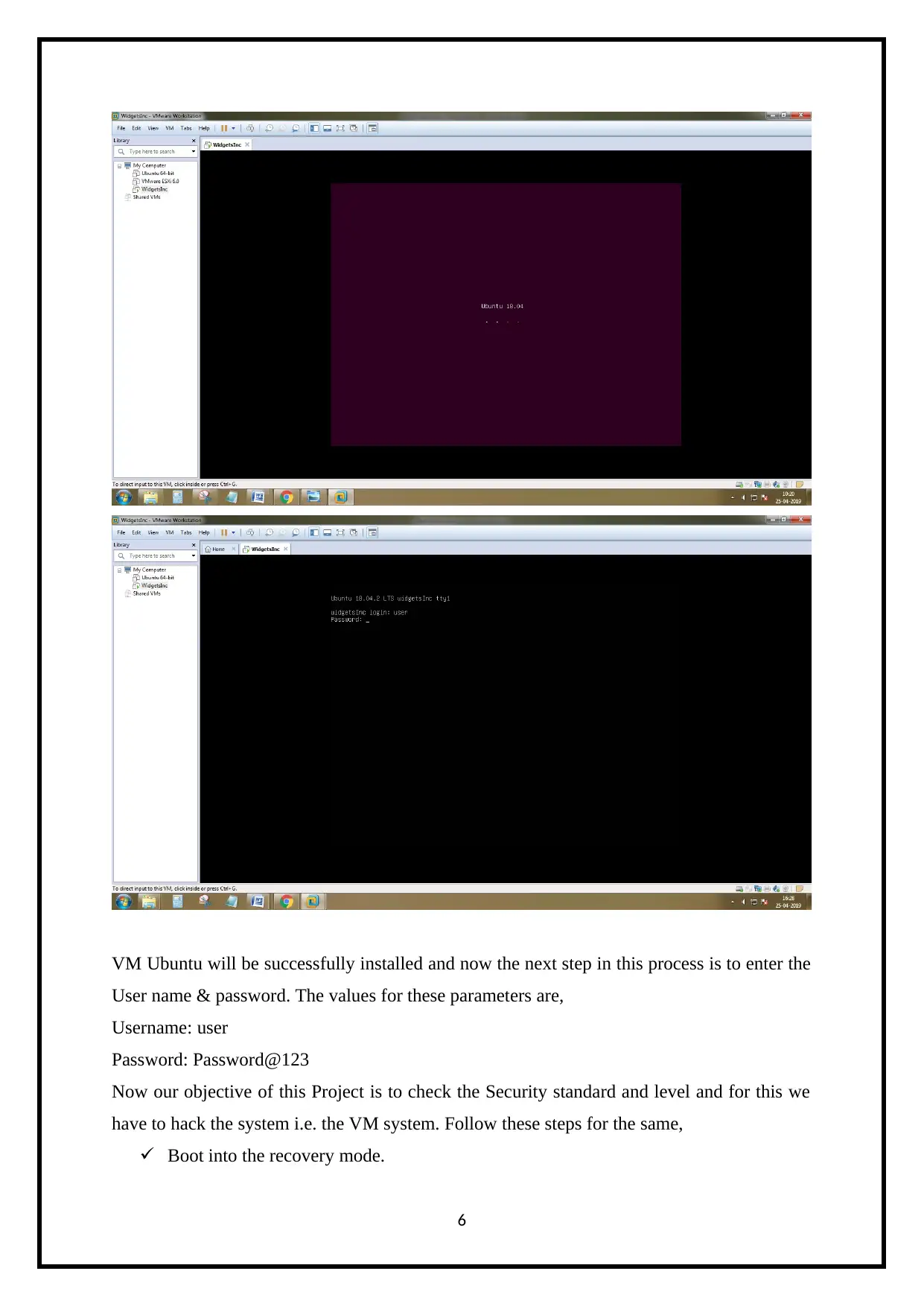
VM Ubuntu will be successfully installed and now the next step in this process is to enter the
User name & password. The values for these parameters are,
Username: user
Password: Password@123
Now our objective of this Project is to check the Security standard and level and for this we
have to hack the system i.e. the VM system. Follow these steps for the same,
Boot into the recovery mode.
6
User name & password. The values for these parameters are,
Username: user
Password: Password@123
Now our objective of this Project is to check the Security standard and level and for this we
have to hack the system i.e. the VM system. Follow these steps for the same,
Boot into the recovery mode.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
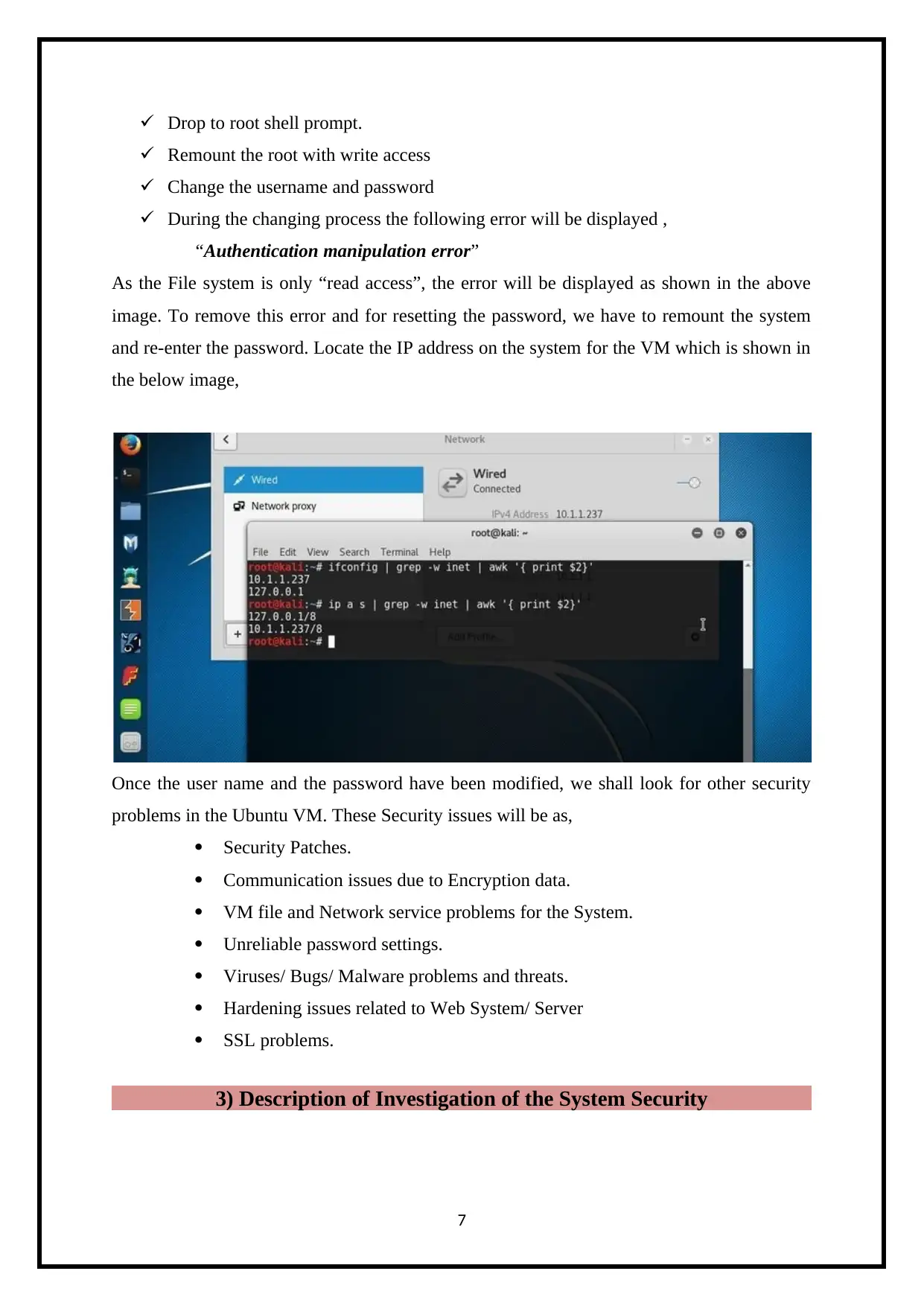
Drop to root shell prompt.
Remount the root with write access
Change the username and password
During the changing process the following error will be displayed ,
“Authentication manipulation error”
As the File system is only “read access”, the error will be displayed as shown in the above
image. To remove this error and for resetting the password, we have to remount the system
and re-enter the password. Locate the IP address on the system for the VM which is shown in
the below image,
Once the user name and the password have been modified, we shall look for other security
problems in the Ubuntu VM. These Security issues will be as,
Security Patches.
Communication issues due to Encryption data.
VM file and Network service problems for the System.
Unreliable password settings.
Viruses/ Bugs/ Malware problems and threats.
Hardening issues related to Web System/ Server
SSL problems.
3) Description of Investigation of the System Security
7
Remount the root with write access
Change the username and password
During the changing process the following error will be displayed ,
“Authentication manipulation error”
As the File system is only “read access”, the error will be displayed as shown in the above
image. To remove this error and for resetting the password, we have to remount the system
and re-enter the password. Locate the IP address on the system for the VM which is shown in
the below image,
Once the user name and the password have been modified, we shall look for other security
problems in the Ubuntu VM. These Security issues will be as,
Security Patches.
Communication issues due to Encryption data.
VM file and Network service problems for the System.
Unreliable password settings.
Viruses/ Bugs/ Malware problems and threats.
Hardening issues related to Web System/ Server
SSL problems.
3) Description of Investigation of the System Security
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Most organizations and companies these days want their information system to be managed
as safely and securely as possible. “Security Evaluation” is the right step in achieving this
goal for any organization. Security Evaluation is particularly important because of the rapidly
changing environment of the information security system or the operation system. Threats
from new viruses, bugs, malwares, and data theft make Data vulnerable and Security at all
time risk. With a “Security Evaluation” during the development process, threats can be
detected and corrected early. But also after the end of a project, a security evaluation can be
useful to know existing threats and potential vulnerabilities of your system. We shall discuss
the Security Evaluation procedure and the various tests and analyses we shall use for this.
This will not only make us understand the type and frequency of threats before and during the
evaluation process but also for the likely attacks after the process is completed. We shall use
one of the processes mentioned below for our Security Evaluation,
- Studying and getting all the information for the Design structure of the System,
Software used Authentication, Validation of the Framework and lastly the
Certification for the System in use.
- Focussing on the behavioural aspect of the system in use and understanding its
interrelation with other components/ software’s/ Stored data/ Sectors on the
System.
- Understanding the mind of a Hacker and a Potential Attacker and how they will
use a tool for entering the Server/ Framework system and be a threat to the
security (He, 2015).
Now with a specific security benchmark which has been certified and classified from
authorities, the security of our system can be inspected and analysed. An attempt to illegally
get into the system will be tried out and analysed. We shall be using our VM image file,
Ubuntu 18.04 for this Security Evaluation. (“Ubuntu” is an open source operating
system which is built upon the code base of Linux). We shall maintain the standards so as the
Security satisfies the criteria’s as laid down by international level and governed by computer
security specifications. “Encryption” is the process of encoding a message or information in
such a way that only authorized parties can access it and those who are not authorized cannot.
Encryption does not itself prevent interference, but denies the intelligible content to a would-
be interceptor. In an encryption scheme, the intended information or message, referred to
as plaintext, is encrypted using an encryption algorithm – a cipher – generating cipher
text that can be read only if decrypted.
8
as safely and securely as possible. “Security Evaluation” is the right step in achieving this
goal for any organization. Security Evaluation is particularly important because of the rapidly
changing environment of the information security system or the operation system. Threats
from new viruses, bugs, malwares, and data theft make Data vulnerable and Security at all
time risk. With a “Security Evaluation” during the development process, threats can be
detected and corrected early. But also after the end of a project, a security evaluation can be
useful to know existing threats and potential vulnerabilities of your system. We shall discuss
the Security Evaluation procedure and the various tests and analyses we shall use for this.
This will not only make us understand the type and frequency of threats before and during the
evaluation process but also for the likely attacks after the process is completed. We shall use
one of the processes mentioned below for our Security Evaluation,
- Studying and getting all the information for the Design structure of the System,
Software used Authentication, Validation of the Framework and lastly the
Certification for the System in use.
- Focussing on the behavioural aspect of the system in use and understanding its
interrelation with other components/ software’s/ Stored data/ Sectors on the
System.
- Understanding the mind of a Hacker and a Potential Attacker and how they will
use a tool for entering the Server/ Framework system and be a threat to the
security (He, 2015).
Now with a specific security benchmark which has been certified and classified from
authorities, the security of our system can be inspected and analysed. An attempt to illegally
get into the system will be tried out and analysed. We shall be using our VM image file,
Ubuntu 18.04 for this Security Evaluation. (“Ubuntu” is an open source operating
system which is built upon the code base of Linux). We shall maintain the standards so as the
Security satisfies the criteria’s as laid down by international level and governed by computer
security specifications. “Encryption” is the process of encoding a message or information in
such a way that only authorized parties can access it and those who are not authorized cannot.
Encryption does not itself prevent interference, but denies the intelligible content to a would-
be interceptor. In an encryption scheme, the intended information or message, referred to
as plaintext, is encrypted using an encryption algorithm – a cipher – generating cipher
text that can be read only if decrypted.
8

Understanding the importance of Up-Dates and Software patches is also very
important to the overall security of the System. These will reduce the exposures for attacks by
outsiders as the software and the system will be updated to the latest version.
Now the best possible way to ensure the Security of the System (Ubuntu) is by
undergoing the hardening process for the network which shall be carried out as below,
Always Up-date the System
Attackers are always looking for soft spots that can be attacked and be easy targets for
even malwares, bugs and viruses. Reduce the amount of unwanted programs,sectors and tools
which do not add any value to the overall improvement and performance of the Network.
Such type of programs, Files, Sectors and areas should be discarded and isolated from the
main Network. Scan the entire Network thoroughly for such type of bugs and corrupted areas.
Reducing the programs and sectors will also reduce the exposed area for potential attackers.
All the bugs and viruses will be quarantined every time the System is Updated and patches
used.
The following command is ways to update an Ubuntusystem:
apt-get or apt command – apt-get command or apt command is the command-line tool for
handling packages.
Turn on SELinux
SELinux provides a flexible Mandatory Access Control (MAC) system built into
the Linux kernel. Under standard Linux Discretionary Access Control (DAC), an
application or process running as a user (UID or SUID) has the user's permissions to objects
such as files, sockets, and other processes. A SELinux-hardened system will run
with SELinux in enforcing mode, meaning that the SELinux policy is in effect and things
that it doesn't want to allow won't be allowed. But when trying to debug permission
problems, it might make sense to temporarily disable SELinux. Its architecture strives to
separate enforcement of security decisions from the security policy itself, and streamlines the
amount of software involved with security policy enforcement. Limiting privilege to the
minimum required to work reduces or eliminates the ability of these programs
and daemons to cause harm if faulty or compromised. This confinement mechanism operates
independently of the traditional Linux control mechanisms.
Sudo Configuration
One of the way’s to implement security in Linux is the user management policy and
user permission and normal users are not authorized to perform any system operations.
9
important to the overall security of the System. These will reduce the exposures for attacks by
outsiders as the software and the system will be updated to the latest version.
Now the best possible way to ensure the Security of the System (Ubuntu) is by
undergoing the hardening process for the network which shall be carried out as below,
Always Up-date the System
Attackers are always looking for soft spots that can be attacked and be easy targets for
even malwares, bugs and viruses. Reduce the amount of unwanted programs,sectors and tools
which do not add any value to the overall improvement and performance of the Network.
Such type of programs, Files, Sectors and areas should be discarded and isolated from the
main Network. Scan the entire Network thoroughly for such type of bugs and corrupted areas.
Reducing the programs and sectors will also reduce the exposed area for potential attackers.
All the bugs and viruses will be quarantined every time the System is Updated and patches
used.
The following command is ways to update an Ubuntusystem:
apt-get or apt command – apt-get command or apt command is the command-line tool for
handling packages.
Turn on SELinux
SELinux provides a flexible Mandatory Access Control (MAC) system built into
the Linux kernel. Under standard Linux Discretionary Access Control (DAC), an
application or process running as a user (UID or SUID) has the user's permissions to objects
such as files, sockets, and other processes. A SELinux-hardened system will run
with SELinux in enforcing mode, meaning that the SELinux policy is in effect and things
that it doesn't want to allow won't be allowed. But when trying to debug permission
problems, it might make sense to temporarily disable SELinux. Its architecture strives to
separate enforcement of security decisions from the security policy itself, and streamlines the
amount of software involved with security policy enforcement. Limiting privilege to the
minimum required to work reduces or eliminates the ability of these programs
and daemons to cause harm if faulty or compromised. This confinement mechanism operates
independently of the traditional Linux control mechanisms.
Sudo Configuration
One of the way’s to implement security in Linux is the user management policy and
user permission and normal users are not authorized to perform any system operations.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

If a normal user needs to perform any system wide changes he needs to use either ‘su‘or
‘sudo ‘command. ‘su‘ forces you to share your root password to other users whereas
‘sudo‘makes it possible to execute system commands without root password. ‘sudo‘lets you
use your own password to execute system commands i.e., delegates system responsibility
without root password. ‘sudo‘ is a root binary setuid, which executes root commands on
behalf of authorized users and the users need to enter their own password to execute system
command followed by ‘sudo‘.
SSH Security and Server Hardening
“SSH” or Secure Shell is the popular protocol for doing system administration on
Linux systems. It runs on most systems, often with its default configuration. As this service
opens up a potential gateway into the system, it is one of the steps to hardening a Linux
system. While it is good to manually harden a system, software and the related configurations
can change over time. SSH is based on network protocol and can use to execute various
command line operations and data transfer. It is necessary to limit SSH access to specific
users as part of server hardening. Instead of using a normal password-based login, a better
way is using public key authentication. Keys are considered much safer and less prone
to brute-force attacks. Disable Password Authentication to force users using keys. It is best
practice not to log in as the root user. Use a normal user account to initiate your connection
instead, together with sudo. Direct root logins may result in bad accountability of the actions
performed by this user account. Another recommended way to reduce potential attacks and
threats is to deploy Security System Tools. “Lynis” is a well-known Security tool used in
Security Auditing, Security Management etc. It provides insights in how well systems are
hardened and what you can do, to improve your security defenses. The software is open
source and free to use. It is updated on a regular basis, to keep up with new technologies.
Lynis is the system and security auditing tool specifically for Linux Platform.
Web server hardening
Transport Layer Security (TLS) is the successor protocol to SSL (Secure Sockets
Layer). TLS is an improved version of SSL. It works in much the same way as the SSL,
using encryption to protect the transfer of data and information. The Hardening process on
the Network and the System will enhance the value and the efficiency of TLS & SSL. This
shall lead to the following factors,
Settings of Nginx:NGINX is a lightweight, high-performance web server designed
for high-traffic use cases. One of NGINX’s strongest features is the ability to efficiently
serve static content and files. All NGINX configuration files are located in the /etc/nginx/
10
‘sudo ‘command. ‘su‘ forces you to share your root password to other users whereas
‘sudo‘makes it possible to execute system commands without root password. ‘sudo‘lets you
use your own password to execute system commands i.e., delegates system responsibility
without root password. ‘sudo‘ is a root binary setuid, which executes root commands on
behalf of authorized users and the users need to enter their own password to execute system
command followed by ‘sudo‘.
SSH Security and Server Hardening
“SSH” or Secure Shell is the popular protocol for doing system administration on
Linux systems. It runs on most systems, often with its default configuration. As this service
opens up a potential gateway into the system, it is one of the steps to hardening a Linux
system. While it is good to manually harden a system, software and the related configurations
can change over time. SSH is based on network protocol and can use to execute various
command line operations and data transfer. It is necessary to limit SSH access to specific
users as part of server hardening. Instead of using a normal password-based login, a better
way is using public key authentication. Keys are considered much safer and less prone
to brute-force attacks. Disable Password Authentication to force users using keys. It is best
practice not to log in as the root user. Use a normal user account to initiate your connection
instead, together with sudo. Direct root logins may result in bad accountability of the actions
performed by this user account. Another recommended way to reduce potential attacks and
threats is to deploy Security System Tools. “Lynis” is a well-known Security tool used in
Security Auditing, Security Management etc. It provides insights in how well systems are
hardened and what you can do, to improve your security defenses. The software is open
source and free to use. It is updated on a regular basis, to keep up with new technologies.
Lynis is the system and security auditing tool specifically for Linux Platform.
Web server hardening
Transport Layer Security (TLS) is the successor protocol to SSL (Secure Sockets
Layer). TLS is an improved version of SSL. It works in much the same way as the SSL,
using encryption to protect the transfer of data and information. The Hardening process on
the Network and the System will enhance the value and the efficiency of TLS & SSL. This
shall lead to the following factors,
Settings of Nginx:NGINX is a lightweight, high-performance web server designed
for high-traffic use cases. One of NGINX’s strongest features is the ability to efficiently
serve static content and files. All NGINX configuration files are located in the /etc/nginx/
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

directory. The primary configuration file is /etc/nginx/nginx.conf. This is used for the
Hardening process and the tuning of the entire system for Hardening.
High Goal Setting: Using a proper tool like SSL which is authorized and certified
will better aid in the securing the sensitive areas of the web server. Also the Configuration of
the Server as explained above.
Description of the Results
Now for understanding the importance of Audit for Security system of the Web
Server (VM Image File), we shall be using a special tool. This is known as “Lynis”. This
software is freely available over the net; Lynis is a host-based, open-source security auditing
application that can evaluate the security profile and posture of operating systems. Lynis
won't perform any system hardening automatically but it will offer suggestions that show you
how you can go about hardening the system yourself.
Now let’s look at the process of installing the Lynis over our platform i.e. Ubuntu 18.04,
- Update the System/ Framework by the below command,
Sudo apt-get update
- Install the Lynis tool on the system by entering the below command,
Sudo apt-get install lynis
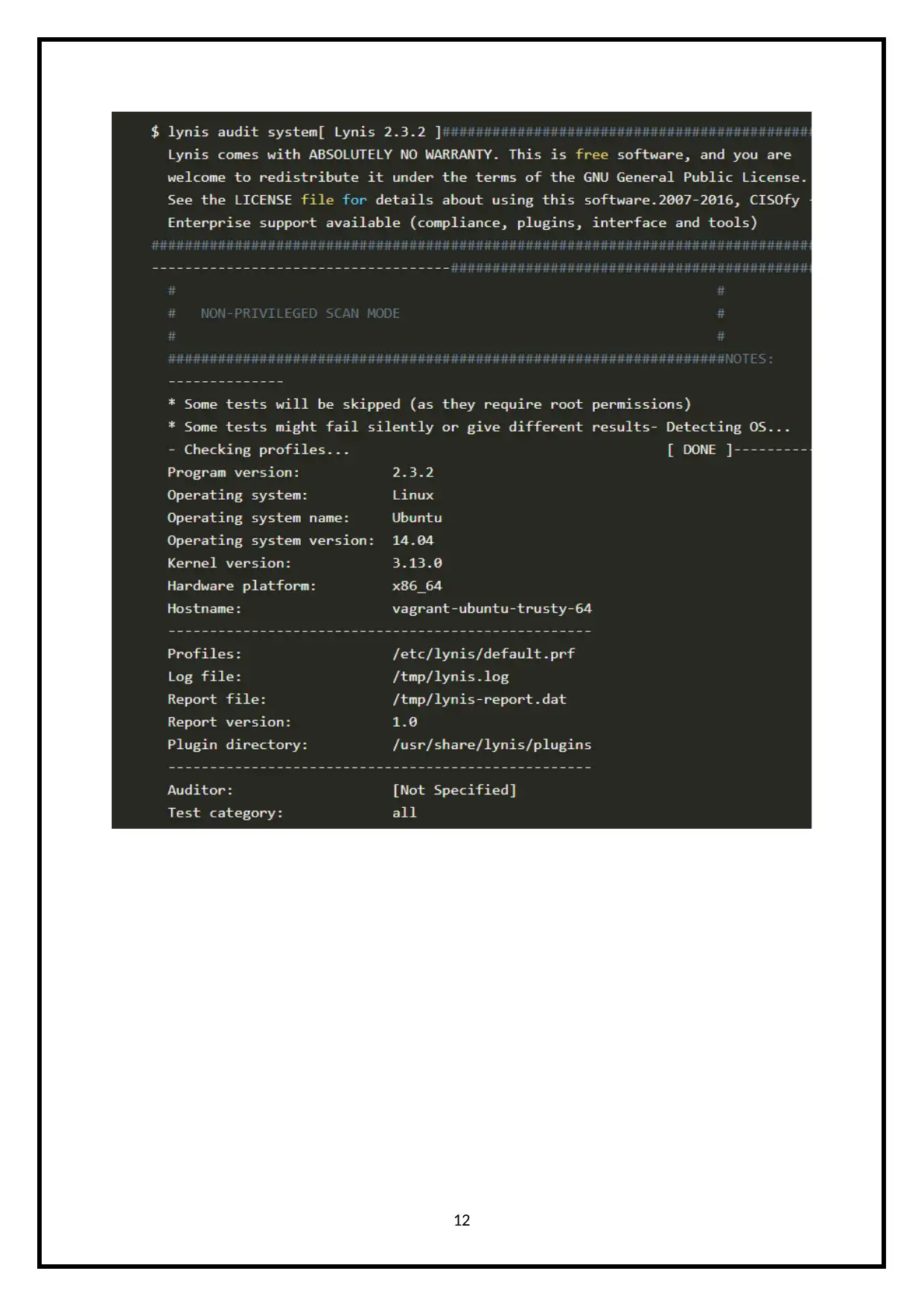
The below image shows the outcome of using the above commands,
11
Hardening process and the tuning of the entire system for Hardening.
High Goal Setting: Using a proper tool like SSL which is authorized and certified
will better aid in the securing the sensitive areas of the web server. Also the Configuration of
the Server as explained above.
Description of the Results
Now for understanding the importance of Audit for Security system of the Web
Server (VM Image File), we shall be using a special tool. This is known as “Lynis”. This
software is freely available over the net; Lynis is a host-based, open-source security auditing
application that can evaluate the security profile and posture of operating systems. Lynis
won't perform any system hardening automatically but it will offer suggestions that show you
how you can go about hardening the system yourself.
Now let’s look at the process of installing the Lynis over our platform i.e. Ubuntu 18.04,
- Update the System/ Framework by the below command,
Sudo apt-get update
- Install the Lynis tool on the system by entering the below command,
Sudo apt-get install lynis
The below image shows the outcome of using the above commands,
11
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





