System Security Report: Firewall, IDS, Honeypots, and System Security
VerifiedAdded on 2022/10/04
|11
|2346
|20
Report
AI Summary
This report provides a comprehensive overview of system security, focusing on firewalls, intrusion detection systems (IDS), and honeypots. It begins with an executive summary highlighting the key topics covered, including the improvement of real-time system security through integrated systems like IPS, firewalls, and honeypots. The report delves into the development history of IDS and honeypots, contrasting their functionalities and discussing their components with diagrams. It explores the challenges companies face in meeting security requirements, detailing methods for data logging, intrusion prevention, and detection. Tools like Snort, Splunk, and various honeypot solutions are examined for their roles in enhancing system security. The report concludes with an understanding of network security using intrusion prevention systems, firewalls, and intrusion detection systems. It also includes a detailed bibliography of the cited sources.

Running head: SYSTEM SECURITY
SYSTEM SECURITY
Name of the Student
Name of the University
Author Note
SYSTEM SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SYSTEM SECURITY
Executive Summary
The report deals with the firewall and the intrusion detection system that are used for the
security of the internet. The report focuses on the improvement of the real time system
security of a system that is integrated with the assistance of intrusion detection system, IPS,
firewall and honey pot. The report discusses about the development history of intrusion
detection system and honey pot. Lastly, the report focuses on the differences between firewall
and intrusion detection system and the diagrams of the components of firewall and intrusion
detection system. The report concludes with an understanding of the network security using
the intrusion prevention system, firewall and the intrusion detection system.
Executive Summary
The report deals with the firewall and the intrusion detection system that are used for the
security of the internet. The report focuses on the improvement of the real time system
security of a system that is integrated with the assistance of intrusion detection system, IPS,
firewall and honey pot. The report discusses about the development history of intrusion
detection system and honey pot. Lastly, the report focuses on the differences between firewall
and intrusion detection system and the diagrams of the components of firewall and intrusion
detection system. The report concludes with an understanding of the network security using
the intrusion prevention system, firewall and the intrusion detection system.

2SYSTEM SECURITY
Table of Contents
Introduction................................................................................................................................3
Discussions.................................................................................................................................3
Improvement of System Security...........................................................................................3
Development history of IDS and Honey pot..........................................................................5
Difference between IDS and Firewall....................................................................................6
Conclusion..................................................................................................................................8
Bibliography...............................................................................................................................9
Table of Contents
Introduction................................................................................................................................3
Discussions.................................................................................................................................3
Improvement of System Security...........................................................................................3
Development history of IDS and Honey pot..........................................................................5
Difference between IDS and Firewall....................................................................................6
Conclusion..................................................................................................................................8
Bibliography...............................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SYSTEM SECURITY
Introduction
Security system is a system of hardware that prevents the intrusion that is
unauthorized into premises and then reports the attempts. A software system that is similar
and that prevents the entry that is unauthorized. There are different types of security systems
that are used such as the monitored systems, unmonitored systems, electric current home
alarm and the wireless alarm systems. The report deals with the firewall and intrusion
detection system that are used for the security of the internet. The report focuses on the
improvement of the real time system security of a system that is integrated with the assistance
of intrusion prevention system, Intrusion Detection System, firewall and honey pot. The
report discusses about the development history of intrusion detection system and honey pot.
Lastly, the report focuses on the contrast between the firewall and intrusion detection system
and the diagrams of the components of firewall and intrusion detection system.
Discussions
Improvement of System Security
The challenges for the companies in this era are to meet the requirements of security.
The methods for logging data, prevention of intrusions and detection of the intrusions have
been evolving for years. The integrated system has been established by considering the
requirement analysis of the framework of engineering, implementation, design and testing.
For the Intrusion prevention system tool that is open source known as snort is arranged in a
mode that is inline, so the sensors that are present captures the packets and then drops them in
case of any of the activity that is suspicious is seen. The signatures for the detection and the
prevention systems help the intrusion prevention system to alert the administrator and then
dropping the packets. The logging of the packets that are dropped is done using the software.
Introduction
Security system is a system of hardware that prevents the intrusion that is
unauthorized into premises and then reports the attempts. A software system that is similar
and that prevents the entry that is unauthorized. There are different types of security systems
that are used such as the monitored systems, unmonitored systems, electric current home
alarm and the wireless alarm systems. The report deals with the firewall and intrusion
detection system that are used for the security of the internet. The report focuses on the
improvement of the real time system security of a system that is integrated with the assistance
of intrusion prevention system, Intrusion Detection System, firewall and honey pot. The
report discusses about the development history of intrusion detection system and honey pot.
Lastly, the report focuses on the contrast between the firewall and intrusion detection system
and the diagrams of the components of firewall and intrusion detection system.
Discussions
Improvement of System Security
The challenges for the companies in this era are to meet the requirements of security.
The methods for logging data, prevention of intrusions and detection of the intrusions have
been evolving for years. The integrated system has been established by considering the
requirement analysis of the framework of engineering, implementation, design and testing.
For the Intrusion prevention system tool that is open source known as snort is arranged in a
mode that is inline, so the sensors that are present captures the packets and then drops them in
case of any of the activity that is suspicious is seen. The signatures for the detection and the
prevention systems help the intrusion prevention system to alert the administrator and then
dropping the packets. The logging of the packets that are dropped is done using the software.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SYSTEM SECURITY
known as Splunk. In the procedure, it provides for the cost that is effective, customizable and
alternate solutions that are scalable to the companies.
Honey pots can improve the real time system security. It is a system on the network
that acts as a decoy and then lures the hackers that are potential. The honey pot does not
contain any data or information that is live, but they can sometimes contain information’s that
are false. A honey pot should always prevent the hackers from accessing the areas that are
protected of the network.
Firewalls can also be used to improve the real time security of the system. Firewall
refers to a device of a network that blocks some kind of the traffic of the network thus
forming a barrier between a network that is trusted and a network that is untrusted. The
firewall is analogous to the firewall that is physical in a sense that the security of firewall
attempts to block the attacks of the computer that has the probability of spreading.
The firewall tools that are used for the real time system security are Algosec, FireMon
and Tufin. The tools that are used for intrusion detection system is Snort and Suricata. The
tools that are used for the intrusion prevention system are security onion and WinPatrol. The
tools that are used for system security using honey pot are Cowrie and Dionaea.
known as Splunk. In the procedure, it provides for the cost that is effective, customizable and
alternate solutions that are scalable to the companies.
Honey pots can improve the real time system security. It is a system on the network
that acts as a decoy and then lures the hackers that are potential. The honey pot does not
contain any data or information that is live, but they can sometimes contain information’s that
are false. A honey pot should always prevent the hackers from accessing the areas that are
protected of the network.
Firewalls can also be used to improve the real time security of the system. Firewall
refers to a device of a network that blocks some kind of the traffic of the network thus
forming a barrier between a network that is trusted and a network that is untrusted. The
firewall is analogous to the firewall that is physical in a sense that the security of firewall
attempts to block the attacks of the computer that has the probability of spreading.
The firewall tools that are used for the real time system security are Algosec, FireMon
and Tufin. The tools that are used for intrusion detection system is Snort and Suricata. The
tools that are used for the intrusion prevention system are security onion and WinPatrol. The
tools that are used for system security using honey pot are Cowrie and Dionaea.

5SYSTEM SECURITY
Development history of IDS and Honey pot
The journey of intrusion detection system started thirty years ago when the network
entry of the businesses spawned a challenge that is new that is the requirement for the entry
of the user and monitoring of user. The detection system of intrusion was initially made in
the US Air Force in the year 1980 by James P Anderson, a settler in the security of
information and a member of the Defence Science Board Task Force on the security of the
computer at the Air Force base of US.
During the late 1980’s the enterprises that use networks that are shared started using
the intrusion detections system. However, the intrusion detection system had some problems.
The problem was that the system could only alert the enterprises on the problems that are
known and that are categorized as threats on the list that is signature.
In the year 1990, the technology of the intrusion detection system was improved that
addressed increasing and sophistication numbers of the attacks of the network. This method
was known as the detection of anomaly. The anomaly detection depended on identifying the
patterns of behaviours on the network and gave alerts for any abnormality that is identified.
The nature of the networks that is inconsistent through the years 1990 and in early
200’s resulted is false positives that are high in number. Many of the administrators thought
that the detection system of intrusion was not reliable.
The metaphor of a bear that is attracted to and stealing of honey is very common in
many traditions all over the world. A common Slavic word for the bear is medved that is
honeyeater. The earliest techniques of honey pot are described in Clifford Still’s 1989 book
that is known as The Cuckoo’s Egg. In the year 2017, the police of Netherlands used the
methods of honey pot in order to track down the users of the Hansa market of darknet. Most
of the honey pots that are present are installed with the firewalls. The firewalls and the honey
Development history of IDS and Honey pot
The journey of intrusion detection system started thirty years ago when the network
entry of the businesses spawned a challenge that is new that is the requirement for the entry
of the user and monitoring of user. The detection system of intrusion was initially made in
the US Air Force in the year 1980 by James P Anderson, a settler in the security of
information and a member of the Defence Science Board Task Force on the security of the
computer at the Air Force base of US.
During the late 1980’s the enterprises that use networks that are shared started using
the intrusion detections system. However, the intrusion detection system had some problems.
The problem was that the system could only alert the enterprises on the problems that are
known and that are categorized as threats on the list that is signature.
In the year 1990, the technology of the intrusion detection system was improved that
addressed increasing and sophistication numbers of the attacks of the network. This method
was known as the detection of anomaly. The anomaly detection depended on identifying the
patterns of behaviours on the network and gave alerts for any abnormality that is identified.
The nature of the networks that is inconsistent through the years 1990 and in early
200’s resulted is false positives that are high in number. Many of the administrators thought
that the detection system of intrusion was not reliable.
The metaphor of a bear that is attracted to and stealing of honey is very common in
many traditions all over the world. A common Slavic word for the bear is medved that is
honeyeater. The earliest techniques of honey pot are described in Clifford Still’s 1989 book
that is known as The Cuckoo’s Egg. In the year 2017, the police of Netherlands used the
methods of honey pot in order to track down the users of the Hansa market of darknet. Most
of the honey pots that are present are installed with the firewalls. The firewalls and the honey
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SYSTEM SECURITY
pots work is a direction that is reverse to each other as the honey pots allow the traffic of the
network to come in but it blocks the traffic that is outgoing. Most of the honey pots that are
installed in the firewalls of a network and the honey pots are used to track and monitor the
hackers. The honey pots are a tool that is unique in order to learn about the strategies of the
hackers. In the language of computer, a honeypot is a security of computer mechanism set in
order to deflect, detect or counteract attempts at the use of systems of information that are
unauthorized. A honeypot includes data that is likely to appear to be a part that is legitimate
of the site, but actually it is monitored or isolated and it seems to consist of information or
some resources of value to the attackers who are blocked. This is related to sting operations
of police that is called as baiting a suspect.
Difference between IDS and Firewall
A firewall is a software or a hardware that works in a domain that is networked in
order to block the entry that is unauthorized while permitting the communications that are
authorized. A firewall is a software or a device that stands in between the network and the
internet that is local. It filters the traffic that can be harmful.
A detection system of intrusion is a device of a hardware or a software that is installed
on the host or the network in order to report and detect the attempts of intrusion to the
network.
The firewall can be personnel for security at the gate and a device of detection system
of intrusion is a security camera that is placed after the gate. A firewall can be used to block
the connections while an intrusion system cannot block the connection. An intrusion
detection system notifies any attempts of intrusion to the administrator of security.
Nevertheless, an intrusion prevention and detections system can block the connections if the
detection system finds the connection that it is an attempt of intrusion.
pots work is a direction that is reverse to each other as the honey pots allow the traffic of the
network to come in but it blocks the traffic that is outgoing. Most of the honey pots that are
installed in the firewalls of a network and the honey pots are used to track and monitor the
hackers. The honey pots are a tool that is unique in order to learn about the strategies of the
hackers. In the language of computer, a honeypot is a security of computer mechanism set in
order to deflect, detect or counteract attempts at the use of systems of information that are
unauthorized. A honeypot includes data that is likely to appear to be a part that is legitimate
of the site, but actually it is monitored or isolated and it seems to consist of information or
some resources of value to the attackers who are blocked. This is related to sting operations
of police that is called as baiting a suspect.
Difference between IDS and Firewall
A firewall is a software or a hardware that works in a domain that is networked in
order to block the entry that is unauthorized while permitting the communications that are
authorized. A firewall is a software or a device that stands in between the network and the
internet that is local. It filters the traffic that can be harmful.
A detection system of intrusion is a device of a hardware or a software that is installed
on the host or the network in order to report and detect the attempts of intrusion to the
network.
The firewall can be personnel for security at the gate and a device of detection system
of intrusion is a security camera that is placed after the gate. A firewall can be used to block
the connections while an intrusion system cannot block the connection. An intrusion
detection system notifies any attempts of intrusion to the administrator of security.
Nevertheless, an intrusion prevention and detections system can block the connections if the
detection system finds the connection that it is an attempt of intrusion.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
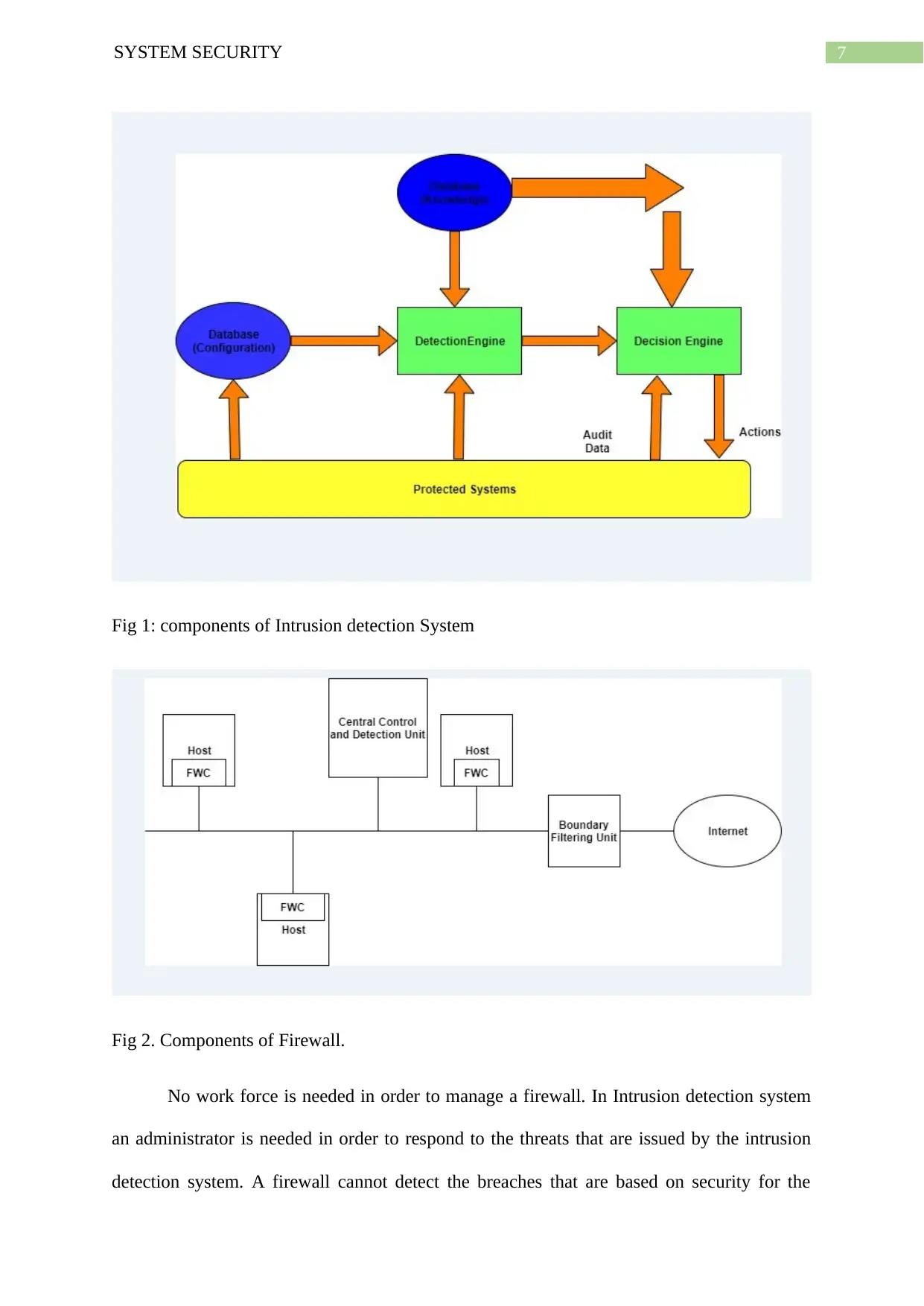
7SYSTEM SECURITY
Fig 1: components of Intrusion detection System
Fig 2. Components of Firewall.
No work force is needed in order to manage a firewall. In Intrusion detection system
an administrator is needed in order to respond to the threats that are issued by the intrusion
detection system. A firewall cannot detect the breaches that are based on security for the
Fig 1: components of Intrusion detection System
Fig 2. Components of Firewall.
No work force is needed in order to manage a firewall. In Intrusion detection system
an administrator is needed in order to respond to the threats that are issued by the intrusion
detection system. A firewall cannot detect the breaches that are based on security for the

8SYSTEM SECURITY
traffic that does not pass through the network. A detection system of intrusion has the
capability of the internal security by the collection of information from various systems and
the resources of network and examining the symptoms of the problems of security.
A firewall is a software or hardware that works in an environment that is networked in
order to block entry of the users that are unauthorized while giving access to the
communications that are authorized. A firewall can block connections while an intrusion
detection system cannot block a connection. The detection systems of intrusion are the
security cameras. A detection system of intrusion monitors the traffic of the network and then
spots the pattern of activity. It alerts the user if it comes to the conclusion that the network is
in some kind of attack.
Conclusion
The report concludes with an understanding of the network security using the
intrusion prevention system, firewall and the intrusion detection system. These are softwares
or hardwares that are used for the security of the internet in a shared network. The report
deals with the detection system of intrusion and firewall that are used for the security of the
internet. The report focuses on the improvement of the real time system security of a system
that is integrated with the assistance of detection system of intrusion, intrusion prevention
system, and firewall and honey pot. The report discusses about the development history of
honey pot and detection system of intrusion. Lastly, the report focuses on the differences
between the detection system of intrusion and firewall and the diagrams of the components of
the firewall and detection system of intrusion.
traffic that does not pass through the network. A detection system of intrusion has the
capability of the internal security by the collection of information from various systems and
the resources of network and examining the symptoms of the problems of security.
A firewall is a software or hardware that works in an environment that is networked in
order to block entry of the users that are unauthorized while giving access to the
communications that are authorized. A firewall can block connections while an intrusion
detection system cannot block a connection. The detection systems of intrusion are the
security cameras. A detection system of intrusion monitors the traffic of the network and then
spots the pattern of activity. It alerts the user if it comes to the conclusion that the network is
in some kind of attack.
Conclusion
The report concludes with an understanding of the network security using the
intrusion prevention system, firewall and the intrusion detection system. These are softwares
or hardwares that are used for the security of the internet in a shared network. The report
deals with the detection system of intrusion and firewall that are used for the security of the
internet. The report focuses on the improvement of the real time system security of a system
that is integrated with the assistance of detection system of intrusion, intrusion prevention
system, and firewall and honey pot. The report discusses about the development history of
honey pot and detection system of intrusion. Lastly, the report focuses on the differences
between the detection system of intrusion and firewall and the diagrams of the components of
the firewall and detection system of intrusion.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SYSTEM SECURITY
Bibliography
Chen, H., Cho, J.H. and Xu, S., 2018, April. Quantifying the security effectiveness of
firewalls and DMZs. In Proceedings of the 5th Annual Symposium and Bootcamp on Hot
Topics in the Science of Security (p. 9). ACM.
Fiessler, A., Lorenz, C., Hager, S. and Scheuermann, B., 2018, October. FireFlow-High
Performance Hybrid SDN-Firewalls with OpenFlow. In 2018 IEEE 43rd Conference on
Local Computer Networks (LCN) (pp. 267-270). IEEE.
Gajewski, M., Batalla, J.M., Mastorakis, G. and Mavromoustakis, C.X., 2017. A distributed
IDS architecture model for Smart Home systems. Cluster Computing, pp.1-11.
Gont, F. and Baker, F., 2016. On Firewalls in Network Security. draft-gont-opsawg-firewalls-
analysis-02 (work in progress).
Kuznetsov, A.A., Smirnov, A.A., Danilenko, D.A. and Berezovsky, A., 2015. The statistical
analysis of a network traffic for the intrusion detection and prevention
systems. Telecommunications and Radio Engineering, 74(1).
Liu-Rong, Z.H.A.O., Mei, S.E. and Zhong, W.J., 2015. AN ECONOMIC ANALYSIS OF
THE INTERACTION BETWEEN FIREWALL, IDS AND VULNERABILITY
SCAN. Economic Computation & Economic Cybernetics Studies & Research, 49(4).
McCaughey, R.J., 2017. Deception using an SSH honeypot. Naval Postgraduate School
Monterey United States.
Milenkoski, A., Vieira, M., Kounev, S., Avritzer, A. and Payne, B.D., 2015. Evaluating
computer intrusion detection systems: A survey of common practices. ACM Computing
Surveys (CSUR), 48(1), p.12.
Bibliography
Chen, H., Cho, J.H. and Xu, S., 2018, April. Quantifying the security effectiveness of
firewalls and DMZs. In Proceedings of the 5th Annual Symposium and Bootcamp on Hot
Topics in the Science of Security (p. 9). ACM.
Fiessler, A., Lorenz, C., Hager, S. and Scheuermann, B., 2018, October. FireFlow-High
Performance Hybrid SDN-Firewalls with OpenFlow. In 2018 IEEE 43rd Conference on
Local Computer Networks (LCN) (pp. 267-270). IEEE.
Gajewski, M., Batalla, J.M., Mastorakis, G. and Mavromoustakis, C.X., 2017. A distributed
IDS architecture model for Smart Home systems. Cluster Computing, pp.1-11.
Gont, F. and Baker, F., 2016. On Firewalls in Network Security. draft-gont-opsawg-firewalls-
analysis-02 (work in progress).
Kuznetsov, A.A., Smirnov, A.A., Danilenko, D.A. and Berezovsky, A., 2015. The statistical
analysis of a network traffic for the intrusion detection and prevention
systems. Telecommunications and Radio Engineering, 74(1).
Liu-Rong, Z.H.A.O., Mei, S.E. and Zhong, W.J., 2015. AN ECONOMIC ANALYSIS OF
THE INTERACTION BETWEEN FIREWALL, IDS AND VULNERABILITY
SCAN. Economic Computation & Economic Cybernetics Studies & Research, 49(4).
McCaughey, R.J., 2017. Deception using an SSH honeypot. Naval Postgraduate School
Monterey United States.
Milenkoski, A., Vieira, M., Kounev, S., Avritzer, A. and Payne, B.D., 2015. Evaluating
computer intrusion detection systems: A survey of common practices. ACM Computing
Surveys (CSUR), 48(1), p.12.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SYSTEM SECURITY
Mironov, I. and Stephens-Davidowitz, N., 2015, April. Cryptographic reverse firewalls.
In Annual International Conference on the Theory and Applications of Cryptographic
Techniques (pp. 657-686). Springer, Berlin, Heidelberg.
Pandya, S.S., 2015. Active Defence System for Network Security─ Honeypot. Advances in
Computer Science and Information Technology (ACSIT), 2(4), pp.383-386.
Potluri, S. and Diedrich, C., 2016, June. High Performance Intrusion Detection and
Prevention Systems: A Survey. In ECCWS2016-Proceedings fo the 15th European
Conference on Cyber Warfare and Security (p. 260). Academic Conferences and publishing
limited.
Snapp, S.R., Brentano, J., Dias, G., Goan, T.L., Heberlein, L.T., Ho, C.L. and Levitt, K.N.,
2017. DIDS (distributed intrusion detection system)-motivation, architecture, and an early
prototype.
Yost, J.R., 2015. The March of IDES: Early History of Intrusion-Detection Expert
Systems. IEEE Annals of the History of Computing, 38(4), pp.42-54.
Mironov, I. and Stephens-Davidowitz, N., 2015, April. Cryptographic reverse firewalls.
In Annual International Conference on the Theory and Applications of Cryptographic
Techniques (pp. 657-686). Springer, Berlin, Heidelberg.
Pandya, S.S., 2015. Active Defence System for Network Security─ Honeypot. Advances in
Computer Science and Information Technology (ACSIT), 2(4), pp.383-386.
Potluri, S. and Diedrich, C., 2016, June. High Performance Intrusion Detection and
Prevention Systems: A Survey. In ECCWS2016-Proceedings fo the 15th European
Conference on Cyber Warfare and Security (p. 260). Academic Conferences and publishing
limited.
Snapp, S.R., Brentano, J., Dias, G., Goan, T.L., Heberlein, L.T., Ho, C.L. and Levitt, K.N.,
2017. DIDS (distributed intrusion detection system)-motivation, architecture, and an early
prototype.
Yost, J.R., 2015. The March of IDES: Early History of Intrusion-Detection Expert
Systems. IEEE Annals of the History of Computing, 38(4), pp.42-54.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




