Information System Security and Risk Management Comprehensive Report
VerifiedAdded on 2023/06/05
|15
|3898
|364
Report
AI Summary
This report provides a comprehensive analysis of information system security and risk management, focusing on various threats and mitigation strategies within an Amazon AWS environment. It delves into the mechanics of ransomware attacks, tools for defense, and vulnerabilities in network routers and switches. The report also addresses ensuring the availability and reliability of web services, maintaining staff email confidentiality and integrity, and tackling security issues related to webmail and web servers. Furthermore, it explores the impact of human factors on security, the use of log records for analysis, and the application of audit logs. The report concludes by highlighting five key tools for framework protection, offering a holistic view of information system security and risk management practices.

Running head: INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
Information System Security and Risk Management
Name of the Student
Name of the University
Author Note
Information System Security and Risk Management
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
Table of Contents
1. Introduction:...............................................................................................................2
2. Ransomware Malware:...............................................................................................3
2.1 Working Mechanism:...........................................................................................3
2.2 Tools to tackle ransomware attack:......................................................................3
3. Network routers and switches threats:.......................................................................4
5. Ensuring confidentiality and integrity of staff email:................................................5
6. Threats, malware and security issues of the webmail and web server:......................5
7. Improving the availability of the email server:..........................................................6
8. Human factors impact and organizational issues:......................................................8
9. Use of Log records:....................................................................................................9
10. Usage of audit log records:...................................................................................10
11. 5 tools used for protecting the framework:............................................................10
Conclusion:..................................................................................................................11
References:...................................................................................................................12
Table of Contents
1. Introduction:...............................................................................................................2
2. Ransomware Malware:...............................................................................................3
2.1 Working Mechanism:...........................................................................................3
2.2 Tools to tackle ransomware attack:......................................................................3
3. Network routers and switches threats:.......................................................................4
5. Ensuring confidentiality and integrity of staff email:................................................5
6. Threats, malware and security issues of the webmail and web server:......................5
7. Improving the availability of the email server:..........................................................6
8. Human factors impact and organizational issues:......................................................8
9. Use of Log records:....................................................................................................9
10. Usage of audit log records:...................................................................................10
11. 5 tools used for protecting the framework:............................................................10
Conclusion:..................................................................................................................11
References:...................................................................................................................12

2INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
1. Introduction:
The ransomware is a typical malicious software which is used by the hackers to get
the access to the victim's computer or similar type of devices. The ransomware actually
blocks the users from accessing their own computer system (Kharraz et al., 2015). To release
the important data stored in the system the hacker wants a ransom or a payment from the
victim. This is not also sure that the attacker will give the data access to the victim after the
payment. This malicious software generally comes in the form of an email from an unknown
source which actually pretends to be a trusted source. The main aim of this report is to
discuss various types of ransomware attacks and how the working mechanism of the
ransomware attack. With the mechanism, this report will also discuss three tools to tackle the
ransomware attack in the Amazon aws services. With the ransomware attack, the devices of
the network are highly vulnerable in the Amazon web services. This report will also discuss
how these devices are vulnerable to attacks.
Further, this report will also discuss how the Amazon web services can ensure the
availability and reliability of the web services. With that, the email confidentiality and
integrity of the organization will also be evaluated. The security issues and malware related
problems of the webmail server will be discussed. To improve the availability of the web
server, two approaches will be discussed. Evaluating these parts risk management
recommendation will be discussed to reduce the risks of the employees in the Amazon web
services organization. The log reports also have a big role in the security aspects. How this
logs can be used for analysing the web server problems will be evaluated. Also, the
importance of the audit log report will be discussed. Lastly, five types of network security
devices will be discussed how these devices can help to reduce the risks and threats.
1. Introduction:
The ransomware is a typical malicious software which is used by the hackers to get
the access to the victim's computer or similar type of devices. The ransomware actually
blocks the users from accessing their own computer system (Kharraz et al., 2015). To release
the important data stored in the system the hacker wants a ransom or a payment from the
victim. This is not also sure that the attacker will give the data access to the victim after the
payment. This malicious software generally comes in the form of an email from an unknown
source which actually pretends to be a trusted source. The main aim of this report is to
discuss various types of ransomware attacks and how the working mechanism of the
ransomware attack. With the mechanism, this report will also discuss three tools to tackle the
ransomware attack in the Amazon aws services. With the ransomware attack, the devices of
the network are highly vulnerable in the Amazon web services. This report will also discuss
how these devices are vulnerable to attacks.
Further, this report will also discuss how the Amazon web services can ensure the
availability and reliability of the web services. With that, the email confidentiality and
integrity of the organization will also be evaluated. The security issues and malware related
problems of the webmail server will be discussed. To improve the availability of the web
server, two approaches will be discussed. Evaluating these parts risk management
recommendation will be discussed to reduce the risks of the employees in the Amazon web
services organization. The log reports also have a big role in the security aspects. How this
logs can be used for analysing the web server problems will be evaluated. Also, the
importance of the audit log report will be discussed. Lastly, five types of network security
devices will be discussed how these devices can help to reduce the risks and threats.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
2. Ransomware Malware:
The ransomware is a typical harmful software which is capable of locking the files
without the administrative permissions, and this files only can be accessed by a key for which
the attacker wants a payment form the victim.
2.1 Working Mechanism:
When the user or the owner of the computer downloads the ransomware file as an
email attachment and opens the file, the malicious codes start to execute. This execution
process encrypts the important personal files stored in the local storage (Maurya et al., 2018).
2.2 Tools to tackle ransomware attack:
The three best tools to tackle the ransomware attack are the:
Kaspersky anti-ransomware tool: This tool runs in the background of the operating
system and observes the activity of the network traffic. Whenever anything found
suspicious or behaving like the ransomware it blocked immediately (McNeil, Frey &
Embrechts, 2015).
McAfee Ransomware Interceptor: The McAfee ransomware inspector can detect
various types of ransomware attacks including the latest WannaCry malware. Though
the McAfee ransomware inspector can raise false detections in some cases it still one
of the best tools to tackle the ransomware attack.
Avast anti-ransomware tools: It is not necessary that all the ransomware will work
in the same way. For certain cases decryption is needed and the process of decryption
can be different for different types of ransomware.
2. Ransomware Malware:
The ransomware is a typical harmful software which is capable of locking the files
without the administrative permissions, and this files only can be accessed by a key for which
the attacker wants a payment form the victim.
2.1 Working Mechanism:
When the user or the owner of the computer downloads the ransomware file as an
email attachment and opens the file, the malicious codes start to execute. This execution
process encrypts the important personal files stored in the local storage (Maurya et al., 2018).
2.2 Tools to tackle ransomware attack:
The three best tools to tackle the ransomware attack are the:
Kaspersky anti-ransomware tool: This tool runs in the background of the operating
system and observes the activity of the network traffic. Whenever anything found
suspicious or behaving like the ransomware it blocked immediately (McNeil, Frey &
Embrechts, 2015).
McAfee Ransomware Interceptor: The McAfee ransomware inspector can detect
various types of ransomware attacks including the latest WannaCry malware. Though
the McAfee ransomware inspector can raise false detections in some cases it still one
of the best tools to tackle the ransomware attack.
Avast anti-ransomware tools: It is not necessary that all the ransomware will work
in the same way. For certain cases decryption is needed and the process of decryption
can be different for different types of ransomware.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
3. Network routers and switches threats:
The main work of the network routers and switches are passing the data packets
through and out in a network. As this routers and switches work on simple passing devices,
this becomes the main attraction of the hackers to exploit the vulnerabilities.
The routers and the switches can be hacked easily by the backtrack method which is
used for finding vulnerabilities in a network system such as weaknesses and passwords. This
tool was developed by the Cisco for the auditing purpose, but this tool is often used by the
attackers to find vulnerabilities. By finding the vulnerabilities in a network device, the
attacker can use the confidential information of the network for various illegal work which is
abusing the internal data (Woods & Hollnagel, 2017).
Another type of threats related to the network routers is the session hijacking. This
type of attack occurs when the attacker successfully inserts the false IP packets which can
cause massive destruction to the system. 4. Ensuring the availability and reliability of web
service:
High availability and reliability of the web server are required for the Amazon web
service for satisfying the customers. An unsatisfied customer can lead to loss of the business.
The availability and reliability of the web server can be increased by improving the
architecture of the design, code optimization and by analysing the points of failures and by
solving the failure points.
To achieve high availability of the web service components of particular layers can be
enhanced. For the case of the Presentation layer dynamic content caching solution and using
the built-in features of the UI, technology can help to increase the availability of the web
service (Verborgh et al., 2014).
3. Network routers and switches threats:
The main work of the network routers and switches are passing the data packets
through and out in a network. As this routers and switches work on simple passing devices,
this becomes the main attraction of the hackers to exploit the vulnerabilities.
The routers and the switches can be hacked easily by the backtrack method which is
used for finding vulnerabilities in a network system such as weaknesses and passwords. This
tool was developed by the Cisco for the auditing purpose, but this tool is often used by the
attackers to find vulnerabilities. By finding the vulnerabilities in a network device, the
attacker can use the confidential information of the network for various illegal work which is
abusing the internal data (Woods & Hollnagel, 2017).
Another type of threats related to the network routers is the session hijacking. This
type of attack occurs when the attacker successfully inserts the false IP packets which can
cause massive destruction to the system. 4. Ensuring the availability and reliability of web
service:
High availability and reliability of the web server are required for the Amazon web
service for satisfying the customers. An unsatisfied customer can lead to loss of the business.
The availability and reliability of the web server can be increased by improving the
architecture of the design, code optimization and by analysing the points of failures and by
solving the failure points.
To achieve high availability of the web service components of particular layers can be
enhanced. For the case of the Presentation layer dynamic content caching solution and using
the built-in features of the UI, technology can help to increase the availability of the web
service (Verborgh et al., 2014).

5INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
Like the availability enhancement of the web service, the enhancement of the web
service reliability is also required to satisfy the customers. This reliability can be achieved by
a guaranteed delivery which ensures that a sent request will be received by the receiver.
Duplication elimination is another technique to gain high reliability of web service. In this
case, it is ensured that no duplicate message will be sent over the web service. Lastly, the
message ordering ensures the sequence of the message remains intact.
5. Ensuring confidentiality and integrity of staff email:
Confidential communications are very much required in all the organization including
this organization also to maintain the privacy. As the main way of communication in this type
of organization is email it needs to ensure that the emails are confidential and follows the data
integrity principle (Hopkin, 2018).
To ensure the confidentiality of the email ensuring the usability is one of the best
ways. It is a key solution for sending a secure e-mail. With that to ensure more confidentiality
of the email the traffic of the email need to be protected over the whole organization. This
can be achieved by following a same policy throughout the organization. Maintaining the
data integrity is also a vital part for the organization. To ensure the data integrity encryption
of the email can be used. For the encryption, the digital signature is a very good solution. It
can help to intact the original data sent by the sender. In this case, the hashing technique is
used which sign the overall document digitally. Any change made to the document will
invalid the hash. Thus it can ensure the integrity of the email (Wong & Brooks, 2015).
6. Threats, malware and security issues of the webmail and web server:
The threats which are experienced by the webmail is the lack of securement where
only one digital certificate is used, improper policies of using external webmail, corporate
content filter bypassing. Also, this type of webmail uses insecure data transmission, and the
Like the availability enhancement of the web service, the enhancement of the web
service reliability is also required to satisfy the customers. This reliability can be achieved by
a guaranteed delivery which ensures that a sent request will be received by the receiver.
Duplication elimination is another technique to gain high reliability of web service. In this
case, it is ensured that no duplicate message will be sent over the web service. Lastly, the
message ordering ensures the sequence of the message remains intact.
5. Ensuring confidentiality and integrity of staff email:
Confidential communications are very much required in all the organization including
this organization also to maintain the privacy. As the main way of communication in this type
of organization is email it needs to ensure that the emails are confidential and follows the data
integrity principle (Hopkin, 2018).
To ensure the confidentiality of the email ensuring the usability is one of the best
ways. It is a key solution for sending a secure e-mail. With that to ensure more confidentiality
of the email the traffic of the email need to be protected over the whole organization. This
can be achieved by following a same policy throughout the organization. Maintaining the
data integrity is also a vital part for the organization. To ensure the data integrity encryption
of the email can be used. For the encryption, the digital signature is a very good solution. It
can help to intact the original data sent by the sender. In this case, the hashing technique is
used which sign the overall document digitally. Any change made to the document will
invalid the hash. Thus it can ensure the integrity of the email (Wong & Brooks, 2015).
6. Threats, malware and security issues of the webmail and web server:
The threats which are experienced by the webmail is the lack of securement where
only one digital certificate is used, improper policies of using external webmail, corporate
content filter bypassing. Also, this type of webmail uses insecure data transmission, and the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
human error is also there for which the threats arise. In the case of web server threats, there
are brute force attacks, Denial of Service, SQL injection and unpatched software (Safa, Von
Solms & Furnell, 2016).
The malware related to the webmail services are the phishing attacks, ransomware
attacks which gained so much attention in the recent years. In the phishing technique, a fake
webpage is presented to the victim and when the victim login through this webpage the
attacker capture the login credentials of the victim (Nazareth & Choi, 2015). In the case of
web server malware, this can be virus, Trojans, spyware, bots, worms which can harm the
web server by running some malicious codes.
The main security issues with the webmail are the lack of encryption. Many webmail
servers simply do not provide any encryption service to the email which is sent. This leads to
a vulnerability by which the attackers can easily intervene in the messaging system. In the
case of the web server, the general security issues are the data integrity and privacy in which
the data is altered and can be seen by the attackers which stored in a server. Also, the
common gateway interface script is another security issue related to the web server which
exploits the information of the hosts (Kiedrowicz & Stanik, 2015).
7. Improving the availability of the email server:
The approaches to improve the availability of the email server is a proper backup
system and a recovery plan.
Using a backup plan can periodically backup the data stored in an email server, and
this data can be restored whenever the data is needed. Also, if any mishap happened with the
server mechanism, then this backup data can be used in the new hardware which can greatly
increase the availability of the email data to the users (Fennelly, 2016).
human error is also there for which the threats arise. In the case of web server threats, there
are brute force attacks, Denial of Service, SQL injection and unpatched software (Safa, Von
Solms & Furnell, 2016).
The malware related to the webmail services are the phishing attacks, ransomware
attacks which gained so much attention in the recent years. In the phishing technique, a fake
webpage is presented to the victim and when the victim login through this webpage the
attacker capture the login credentials of the victim (Nazareth & Choi, 2015). In the case of
web server malware, this can be virus, Trojans, spyware, bots, worms which can harm the
web server by running some malicious codes.
The main security issues with the webmail are the lack of encryption. Many webmail
servers simply do not provide any encryption service to the email which is sent. This leads to
a vulnerability by which the attackers can easily intervene in the messaging system. In the
case of the web server, the general security issues are the data integrity and privacy in which
the data is altered and can be seen by the attackers which stored in a server. Also, the
common gateway interface script is another security issue related to the web server which
exploits the information of the hosts (Kiedrowicz & Stanik, 2015).
7. Improving the availability of the email server:
The approaches to improve the availability of the email server is a proper backup
system and a recovery plan.
Using a backup plan can periodically backup the data stored in an email server, and
this data can be restored whenever the data is needed. Also, if any mishap happened with the
server mechanism, then this backup data can be used in the new hardware which can greatly
increase the availability of the email data to the users (Fennelly, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
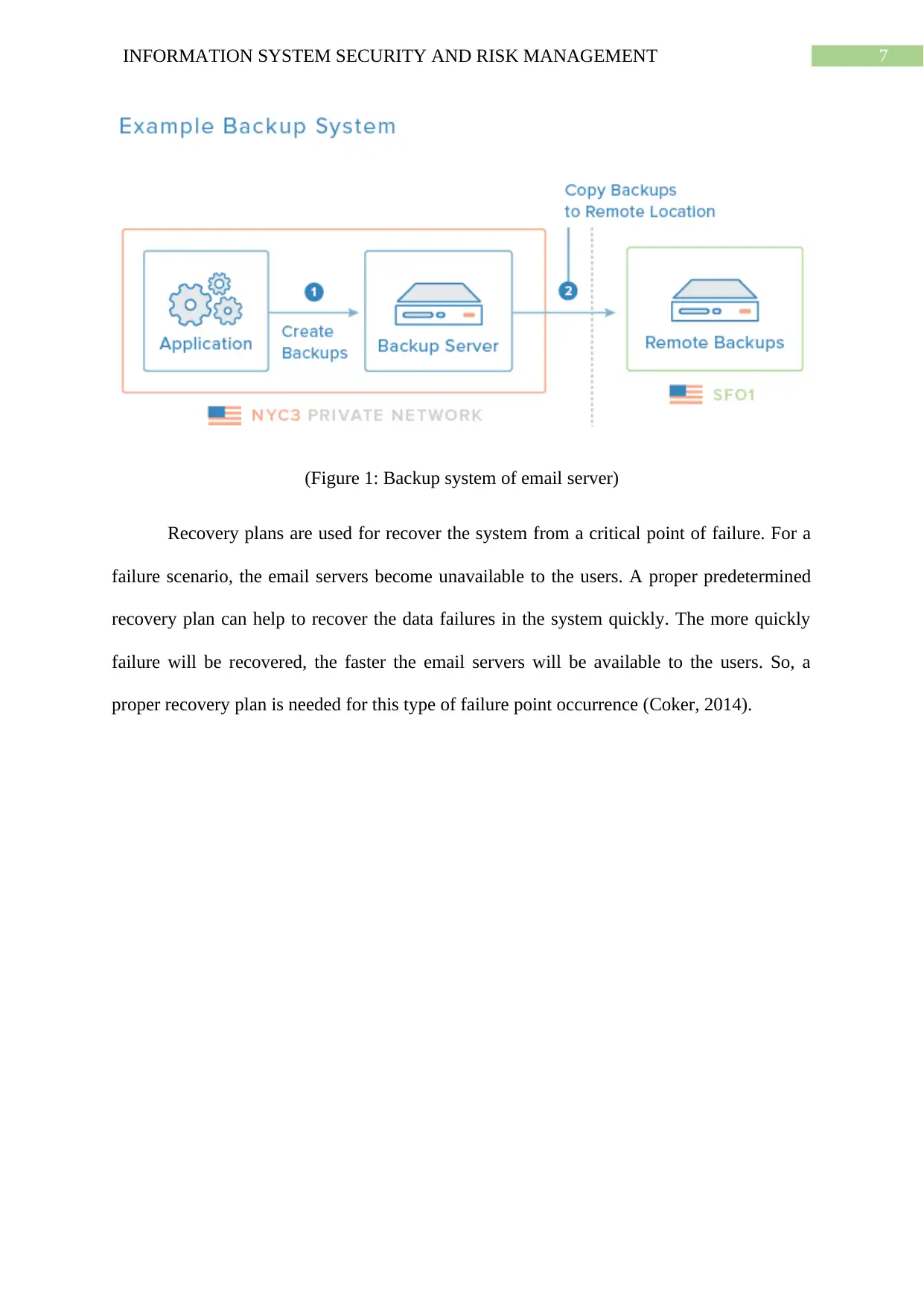
7INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
(Figure 1: Backup system of email server)
Recovery plans are used for recover the system from a critical point of failure. For a
failure scenario, the email servers become unavailable to the users. A proper predetermined
recovery plan can help to recover the data failures in the system quickly. The more quickly
failure will be recovered, the faster the email servers will be available to the users. So, a
proper recovery plan is needed for this type of failure point occurrence (Coker, 2014).
(Figure 1: Backup system of email server)
Recovery plans are used for recover the system from a critical point of failure. For a
failure scenario, the email servers become unavailable to the users. A proper predetermined
recovery plan can help to recover the data failures in the system quickly. The more quickly
failure will be recovered, the faster the email servers will be available to the users. So, a
proper recovery plan is needed for this type of failure point occurrence (Coker, 2014).

8INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
(Figure 2: Recovery plan of an email server)
8. Human factors impact and organizational issues:
The main impact of the human factors in the case of information system related
security is the lack of motivation, lack of awareness, belief, behaviour and the improper use
of technology. The lack of motivation occurs when the security related issues not shared with
the employees of the organization. In the case of lack of awareness, it occurs when the
common knowledge of the attacks and vulnerabilities is not known to the employees of the
organization. The belief of the employees plays an important role in the case of security
related issues of the organization. If any employee believes that the extra tight security is not
required for the communication, then they may face various types of security flaws (Eriksson,
2017). The behaviour also plays a huge role in this case. If an employee holds some risky
behaviour towards the organization, then they may cause of the security issues in the
(Figure 2: Recovery plan of an email server)
8. Human factors impact and organizational issues:
The main impact of the human factors in the case of information system related
security is the lack of motivation, lack of awareness, belief, behaviour and the improper use
of technology. The lack of motivation occurs when the security related issues not shared with
the employees of the organization. In the case of lack of awareness, it occurs when the
common knowledge of the attacks and vulnerabilities is not known to the employees of the
organization. The belief of the employees plays an important role in the case of security
related issues of the organization. If any employee believes that the extra tight security is not
required for the communication, then they may face various types of security flaws (Eriksson,
2017). The behaviour also plays a huge role in this case. If an employee holds some risky
behaviour towards the organization, then they may cause of the security issues in the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
organization. Improper use of the provided technologies can also become a problem for the
organization.
To manage this types of risks, some sort of recommendation can be given, and they are
discussed below.
Log files are an important file which holds the information about the activity of the
users. So the data integrity of these log files is required. By evaluating the log file
information risks can be managed.
Unauthorised access should be detected to reduce the risks.
The security system needs to be evaluated periodically to determine any major flaws.
This can help to detect risk occurrence (Peltier, 2016).
9. Use of Log records:
The log record is a file which includes the activity related information of a system.
This log analysis was done to reduce various types of risks related to the system. In most of
the cases, this type of log file is generated by the operating system or by some type of
network equipment. This log file is generally stored in the log collector of the internal hard
drive of the system. This log file can provide valuable information about the system to
determine the security, access and the problems related to the server system. A day to day
analysis of log files can help to avoid and reduce the different type of risks associated with
the organization (Aven, 2016).
This log files can be used for determining the root of the problems which the
organization is facing. This log files can be used for increasing the awareness about the
security. Also, it can give the details about the failed process and where this failure is
occurring. The log analysis report can help in the case of trend determination. With that, it
can help to improve the search facilities which can improve the monitoring system of the
organization. Improper use of the provided technologies can also become a problem for the
organization.
To manage this types of risks, some sort of recommendation can be given, and they are
discussed below.
Log files are an important file which holds the information about the activity of the
users. So the data integrity of these log files is required. By evaluating the log file
information risks can be managed.
Unauthorised access should be detected to reduce the risks.
The security system needs to be evaluated periodically to determine any major flaws.
This can help to detect risk occurrence (Peltier, 2016).
9. Use of Log records:
The log record is a file which includes the activity related information of a system.
This log analysis was done to reduce various types of risks related to the system. In most of
the cases, this type of log file is generated by the operating system or by some type of
network equipment. This log file is generally stored in the log collector of the internal hard
drive of the system. This log file can provide valuable information about the system to
determine the security, access and the problems related to the server system. A day to day
analysis of log files can help to avoid and reduce the different type of risks associated with
the organization (Aven, 2016).
This log files can be used for determining the root of the problems which the
organization is facing. This log files can be used for increasing the awareness about the
security. Also, it can give the details about the failed process and where this failure is
occurring. The log analysis report can help in the case of trend determination. With that, it
can help to improve the search facilities which can improve the monitoring system of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
organization. Another main advantage of the log file is that it can be used for dynamic data
streaming (Xu & Swanson, 2016) .
10. Usage of audit log records:
The major usage of audit log records are as follows: -
Accountability: with the help of the log data the organization can identify the data
that are required for the completion of the entire project. These data that are generated
during the accountability checking helps in providing proper training to the unserved
parts of the project (Rittinghouse & Ransome, 2016)
Reconstruction: this processing helps in understanding the basic terminologies that
are required for completion of the project. This leads to the fact that the data
management that is performed with the help of the audit logging in the platform of e-
mail and messaging, the data processing will be performed in a better and more
accurate way
11. 5 tools used for protecting the framework:
5 tools that are required for mitigating the risks that are present in the functioning of the
webmails, as well as the emails, are as follows:
Secure Socket Layer protocol (SSL): In case of implementing the Secure Socket
Layer protocol (SSL), the major advantage that the platform enjoys is the processing
of the data management and this is the sole reason that the data management includes
the functioning of the Secure Socket Layer protocol (SSL) for keeping the database
secured and this also helps in protecting the database of the organization that has been
implementing the framework (Karagiannis et al., 2015).
organization. Another main advantage of the log file is that it can be used for dynamic data
streaming (Xu & Swanson, 2016) .
10. Usage of audit log records:
The major usage of audit log records are as follows: -
Accountability: with the help of the log data the organization can identify the data
that are required for the completion of the entire project. These data that are generated
during the accountability checking helps in providing proper training to the unserved
parts of the project (Rittinghouse & Ransome, 2016)
Reconstruction: this processing helps in understanding the basic terminologies that
are required for completion of the project. This leads to the fact that the data
management that is performed with the help of the audit logging in the platform of e-
mail and messaging, the data processing will be performed in a better and more
accurate way
11. 5 tools used for protecting the framework:
5 tools that are required for mitigating the risks that are present in the functioning of the
webmails, as well as the emails, are as follows:
Secure Socket Layer protocol (SSL): In case of implementing the Secure Socket
Layer protocol (SSL), the major advantage that the platform enjoys is the processing
of the data management and this is the sole reason that the data management includes
the functioning of the Secure Socket Layer protocol (SSL) for keeping the database
secured and this also helps in protecting the database of the organization that has been
implementing the framework (Karagiannis et al., 2015).

11INFORMATION SYSTEM SECURITY AND RISK MANAGEMENT
Multi-factor authentication: After implementation of the Multi-factor
authentication, the major factor that affects the processing of the data management is
that the imposters who want to gain access to the data centre gets stopped and the data
that is present in the database is protected by the methodology (DeAngelo & Stulz,
2015)
Malware detection: After implementation of the malware implementation process,
the major advantage that is enjoyed by the organization is that it protects the data
framework form the malicious attacks of the malware
Site monitoring: Site monitoring helps in understanding the importance of
monitoring of the project for better and efficient completion of the project.
Daily or weekly backups: Daily and weekly backup help in keeping storage of the
data on a weekly basis, leading to the fact that the entire data is protected.
Conclusion:
From the above report, it can be concluded that when the user downloads the file in
the email attachment and runs it, the software takes over the whole administrative system of
the computer and denies the user from the access of the internal data of the computer. With
the encryption, this also shuffles the contents of the files and make it unable to read. To
decrypt this files again a key is required for which the attacker wants payment from the
victim. This tool support 21 decryption method for data decryption also it provides an
additional decryption wizard. The attacker successfully inserts the false IP packets in the
network devices by the IP spoofing technique, alterations and by using prediction of
sequenced numbers. Also, the management of the organisation needs the aware the staffs of
the risks of the email communication which will help the staffs in avoiding the common
mistakes. The backup data also give the opportunity to roll back the data in some previous
condition because of unwanted modification of data which is causing unavailability of the
Multi-factor authentication: After implementation of the Multi-factor
authentication, the major factor that affects the processing of the data management is
that the imposters who want to gain access to the data centre gets stopped and the data
that is present in the database is protected by the methodology (DeAngelo & Stulz,
2015)
Malware detection: After implementation of the malware implementation process,
the major advantage that is enjoyed by the organization is that it protects the data
framework form the malicious attacks of the malware
Site monitoring: Site monitoring helps in understanding the importance of
monitoring of the project for better and efficient completion of the project.
Daily or weekly backups: Daily and weekly backup help in keeping storage of the
data on a weekly basis, leading to the fact that the entire data is protected.
Conclusion:
From the above report, it can be concluded that when the user downloads the file in
the email attachment and runs it, the software takes over the whole administrative system of
the computer and denies the user from the access of the internal data of the computer. With
the encryption, this also shuffles the contents of the files and make it unable to read. To
decrypt this files again a key is required for which the attacker wants payment from the
victim. This tool support 21 decryption method for data decryption also it provides an
additional decryption wizard. The attacker successfully inserts the false IP packets in the
network devices by the IP spoofing technique, alterations and by using prediction of
sequenced numbers. Also, the management of the organisation needs the aware the staffs of
the risks of the email communication which will help the staffs in avoiding the common
mistakes. The backup data also give the opportunity to roll back the data in some previous
condition because of unwanted modification of data which is causing unavailability of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


