ISYS225 Systems Analysis and Design: Semester 2 Activities Report
VerifiedAdded on 2023/06/04
|13
|1447
|395
Report
AI Summary
This document presents a comprehensive report on fundamental concepts in Systems Analysis and Design, covering activities from week 5 to week 11 of the ISYS225 course. It includes various activities such as listing basic and supporting activities for a lemonade stall, creating context-level and level 0 Data Flow Diagrams (DFDs), and addressing questions related to HIPAA compliance in real-time glucose monitoring systems. The report also delves into object-oriented systems design, identifying objects for a car buying system and a university library system, and constructing class and communication diagrams. Furthermore, it includes activities related to class diagrams for books and related product content, and outlines deployment activities for a parcel courier service company's system. The document demonstrates a thorough understanding of systems analysis and design principles through practical examples and diagrams.

1Fundamental Concept in Systems Analysis and Design
FUNDAMENTAL CONCEPT IN SYSTEMS ANALYSIS AND DESIGN
By (Student names)
[Course Name]
[Lecture Name]
[University Name]
[City where the university is located]
[Date]
FUNDAMENTAL CONCEPT IN SYSTEMS ANALYSIS AND DESIGN
By (Student names)
[Course Name]
[Lecture Name]
[University Name]
[City where the university is located]
[Date]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2Fundamental Concept in Systems Analysis and Design
Table of Contents
Activity 5.....................................................................................................................................................3
List of basic activities taking place at lemonade stall..............................................................................3
Additional activities needed to support basic activities...........................................................................4
Grouping activities..................................................................................................................................4
Logical fashion....................................................................................................................................4
Functional areas...................................................................................................................................4
Context Level DFD.................................................................................................................................5
Identified manageable sub-processes and level 0 DFD............................................................................5
Activity 6.....................................................................................................................................................6
Question 1...............................................................................................................................................6
Question 2...............................................................................................................................................7
Question 3...............................................................................................................................................7
Question 4...............................................................................................................................................7
Question 5...............................................................................................................................................7
Activity 7.....................................................................................................................................................7
a. How object-oriented systems design can be applied........................................................................7
b. List of all the objects........................................................................................................................8
c. Two objects class diagram...............................................................................................................8
Activity 8.....................................................................................................................................................8
List of the possible objects......................................................................................................................8
Domain class diagram.............................................................................................................................9
Class diagram..........................................................................................................................................9
Communication diagram.......................................................................................................................10
Activity 9...................................................................................................................................................10
Class diagram to represent the book and its key content elements.........................................................10
Expanded class diagram to include related product content...................................................................11
Activity 10.................................................................................................................................................12
Parcel courier service company system deployment activities...............................................................12
Reference...................................................................................................................................................14
Table of Contents
Activity 5.....................................................................................................................................................3
List of basic activities taking place at lemonade stall..............................................................................3
Additional activities needed to support basic activities...........................................................................4
Grouping activities..................................................................................................................................4
Logical fashion....................................................................................................................................4
Functional areas...................................................................................................................................4
Context Level DFD.................................................................................................................................5
Identified manageable sub-processes and level 0 DFD............................................................................5
Activity 6.....................................................................................................................................................6
Question 1...............................................................................................................................................6
Question 2...............................................................................................................................................7
Question 3...............................................................................................................................................7
Question 4...............................................................................................................................................7
Question 5...............................................................................................................................................7
Activity 7.....................................................................................................................................................7
a. How object-oriented systems design can be applied........................................................................7
b. List of all the objects........................................................................................................................8
c. Two objects class diagram...............................................................................................................8
Activity 8.....................................................................................................................................................8
List of the possible objects......................................................................................................................8
Domain class diagram.............................................................................................................................9
Class diagram..........................................................................................................................................9
Communication diagram.......................................................................................................................10
Activity 9...................................................................................................................................................10
Class diagram to represent the book and its key content elements.........................................................10
Expanded class diagram to include related product content...................................................................11
Activity 10.................................................................................................................................................12
Parcel courier service company system deployment activities...............................................................12
Reference...................................................................................................................................................14
3Fundamental Concept in Systems Analysis and Design
Activity 5
List of basic activities taking place at lemonade stall
i. Customers visiting the stall
ii. Customers ordering the foods
iii. Customers ordering drinks
iv. Waiters serving the customers
v. Customers making the payments
vi. Cashiers receiving payments
Additional activities needed to support basic activities.
i. Cashiers preparing the invoices
ii. Cashiers issuing receipts to customers
Grouping activities
Logical fashion
i. Customers visiting the stall
ii. Customers ordering the foods
iii. Customers ordering drinks
iv. Waiters serving the customers
Functional areas
i. Customers making the payments
ii. Cashiers receiving payments
iii. Cashiers preparing the invoices
iv. Cashiers issuing receipts to customers
Activity 5
List of basic activities taking place at lemonade stall
i. Customers visiting the stall
ii. Customers ordering the foods
iii. Customers ordering drinks
iv. Waiters serving the customers
v. Customers making the payments
vi. Cashiers receiving payments
Additional activities needed to support basic activities.
i. Cashiers preparing the invoices
ii. Cashiers issuing receipts to customers
Grouping activities
Logical fashion
i. Customers visiting the stall
ii. Customers ordering the foods
iii. Customers ordering drinks
iv. Waiters serving the customers
Functional areas
i. Customers making the payments
ii. Cashiers receiving payments
iii. Cashiers preparing the invoices
iv. Cashiers issuing receipts to customers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4Fundamental Concept in Systems Analysis and Design
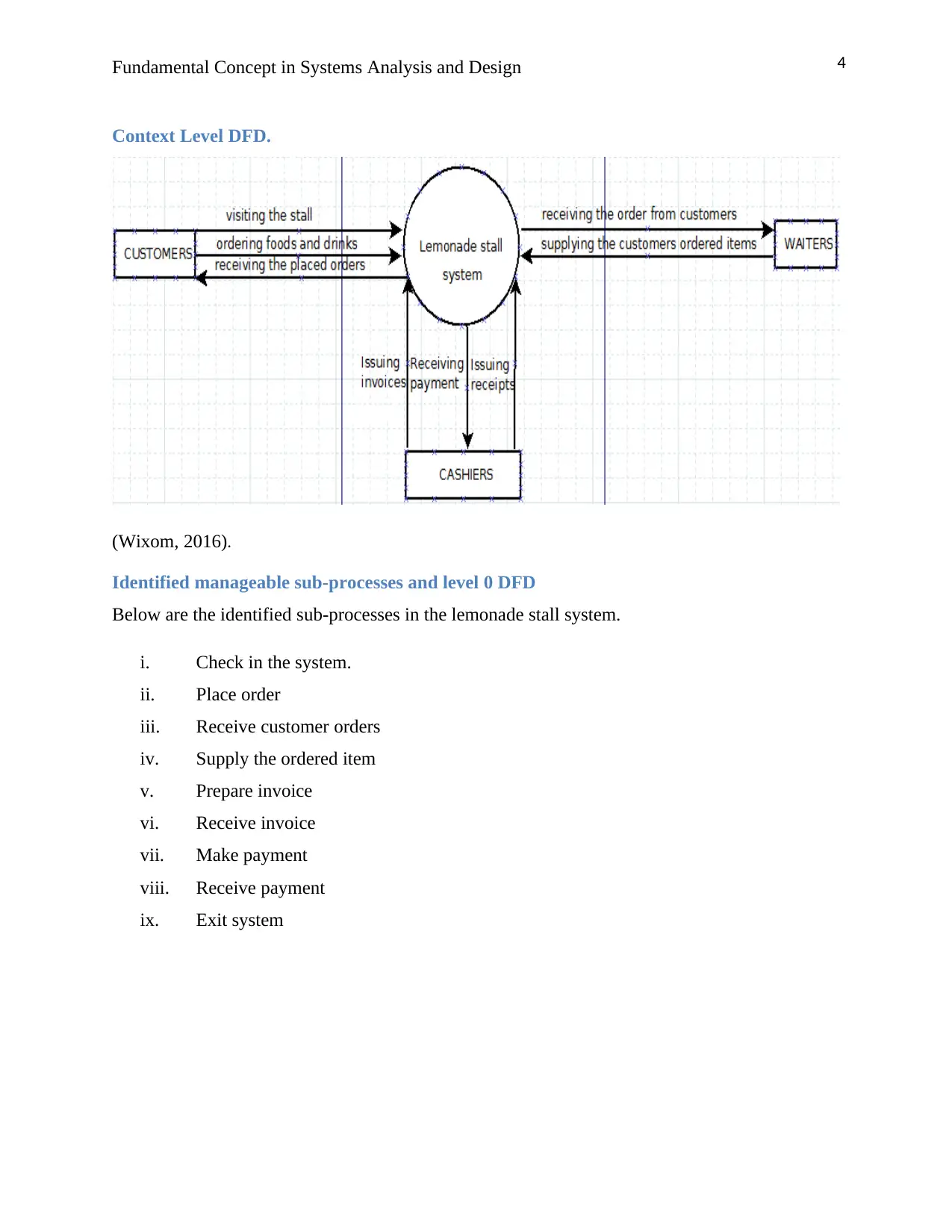
Context Level DFD.
(Wixom, 2016).
Identified manageable sub-processes and level 0 DFD
Below are the identified sub-processes in the lemonade stall system.
i. Check in the system.
ii. Place order
iii. Receive customer orders
iv. Supply the ordered item
v. Prepare invoice
vi. Receive invoice
vii. Make payment
viii. Receive payment
ix. Exit system
Context Level DFD.
(Wixom, 2016).
Identified manageable sub-processes and level 0 DFD
Below are the identified sub-processes in the lemonade stall system.
i. Check in the system.
ii. Place order
iii. Receive customer orders
iv. Supply the ordered item
v. Prepare invoice
vi. Receive invoice
vii. Make payment
viii. Receive payment
ix. Exit system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5Fundamental Concept in Systems Analysis and Design
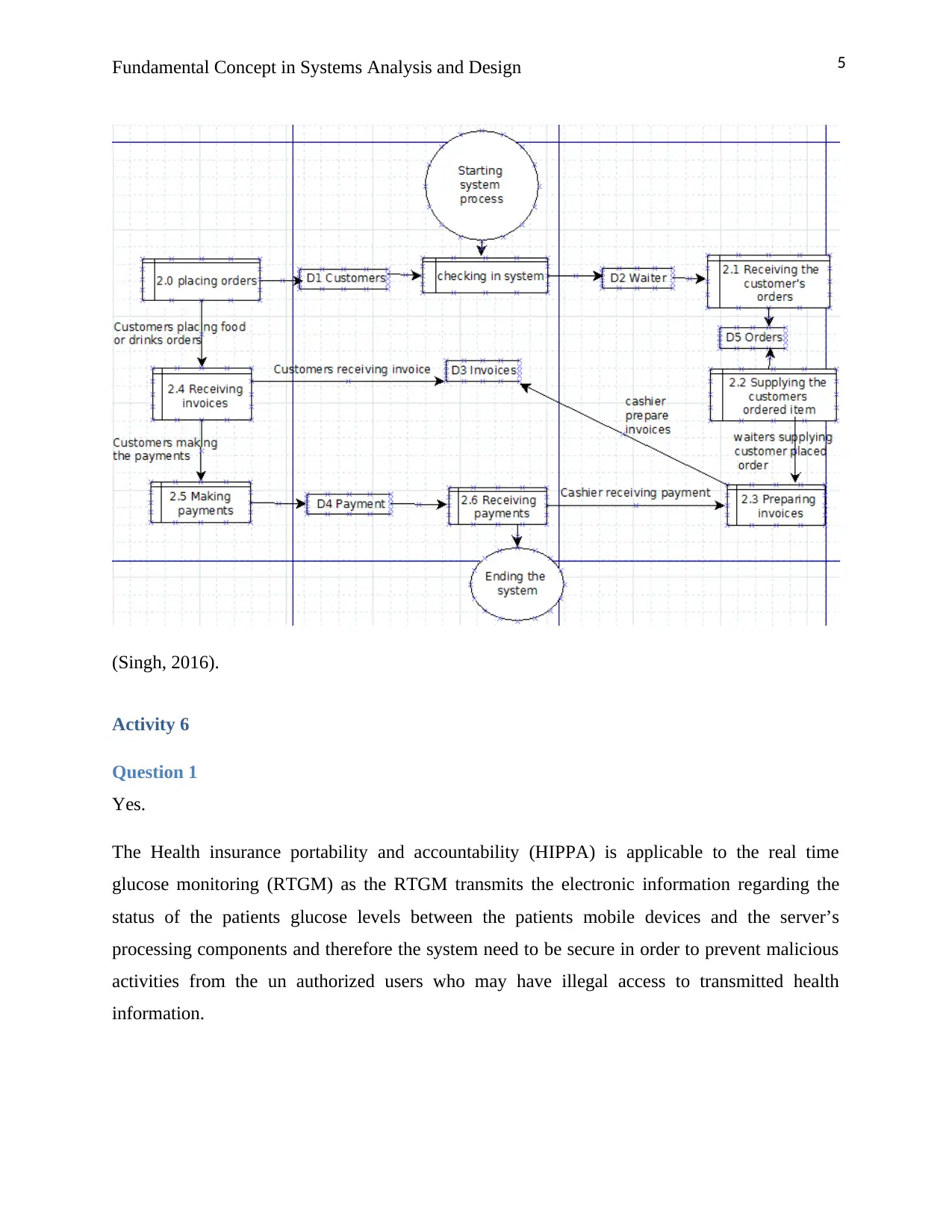
(Singh, 2016).
Activity 6
Question 1
Yes.
The Health insurance portability and accountability (HIPPA) is applicable to the real time
glucose monitoring (RTGM) as the RTGM transmits the electronic information regarding the
status of the patients glucose levels between the patients mobile devices and the server’s
processing components and therefore the system need to be secure in order to prevent malicious
activities from the un authorized users who may have illegal access to transmitted health
information.
(Singh, 2016).
Activity 6
Question 1
Yes.
The Health insurance portability and accountability (HIPPA) is applicable to the real time
glucose monitoring (RTGM) as the RTGM transmits the electronic information regarding the
status of the patients glucose levels between the patients mobile devices and the server’s
processing components and therefore the system need to be secure in order to prevent malicious
activities from the un authorized users who may have illegal access to transmitted health
information.

6Fundamental Concept in Systems Analysis and Design
Question 2
There will be data security during its transmission between the mobile devices and the server
components which will be enforced through the application of the encryption technique which
mainly encodes the information and data transmitted by hiding it from the un authorized system
and information users and thus enforcing data safety during transmission between mobile and
server components.
Question 3
The data of lost or stolen devices can be protected through setting of strong passwords and
usernames however the devices should be configured for daily back system and also to be fixed
with a track device to locate the lost or stolen device possible location.
Question 4
The health officers can access the health information from the system server using the
workstations or the mobile devices, then the health system will be recording and examining the
system access into the ePHI where the devices details and access time is recorded and if any un
recognized system is detected the operation will be terminated immediately. In case the users use
external devices they require installing them with antivirus applications to protect the malwares
and the malicious attacks (Award, 2013).
Question 5
There will be requirement of ePHI security for the signal transmission on wired or wireless
media between the work-stations devices and the server components in order to ensure that the
signals are protected through the encryption to enforce data confidentiality and limiting changes
to the servers that are managed by the third parties (Laplante, 2013).
Activity 7
a. How object-oriented systems design can be applied
The object oriented system design is applied in this system since the car buying system
development will use object oriented programming which will involve number of entities and
their respective attributes that links the various objects.
Question 2
There will be data security during its transmission between the mobile devices and the server
components which will be enforced through the application of the encryption technique which
mainly encodes the information and data transmitted by hiding it from the un authorized system
and information users and thus enforcing data safety during transmission between mobile and
server components.
Question 3
The data of lost or stolen devices can be protected through setting of strong passwords and
usernames however the devices should be configured for daily back system and also to be fixed
with a track device to locate the lost or stolen device possible location.
Question 4
The health officers can access the health information from the system server using the
workstations or the mobile devices, then the health system will be recording and examining the
system access into the ePHI where the devices details and access time is recorded and if any un
recognized system is detected the operation will be terminated immediately. In case the users use
external devices they require installing them with antivirus applications to protect the malwares
and the malicious attacks (Award, 2013).
Question 5
There will be requirement of ePHI security for the signal transmission on wired or wireless
media between the work-stations devices and the server components in order to ensure that the
signals are protected through the encryption to enforce data confidentiality and limiting changes
to the servers that are managed by the third parties (Laplante, 2013).
Activity 7
a. How object-oriented systems design can be applied
The object oriented system design is applied in this system since the car buying system
development will use object oriented programming which will involve number of entities and
their respective attributes that links the various objects.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7Fundamental Concept in Systems Analysis and Design
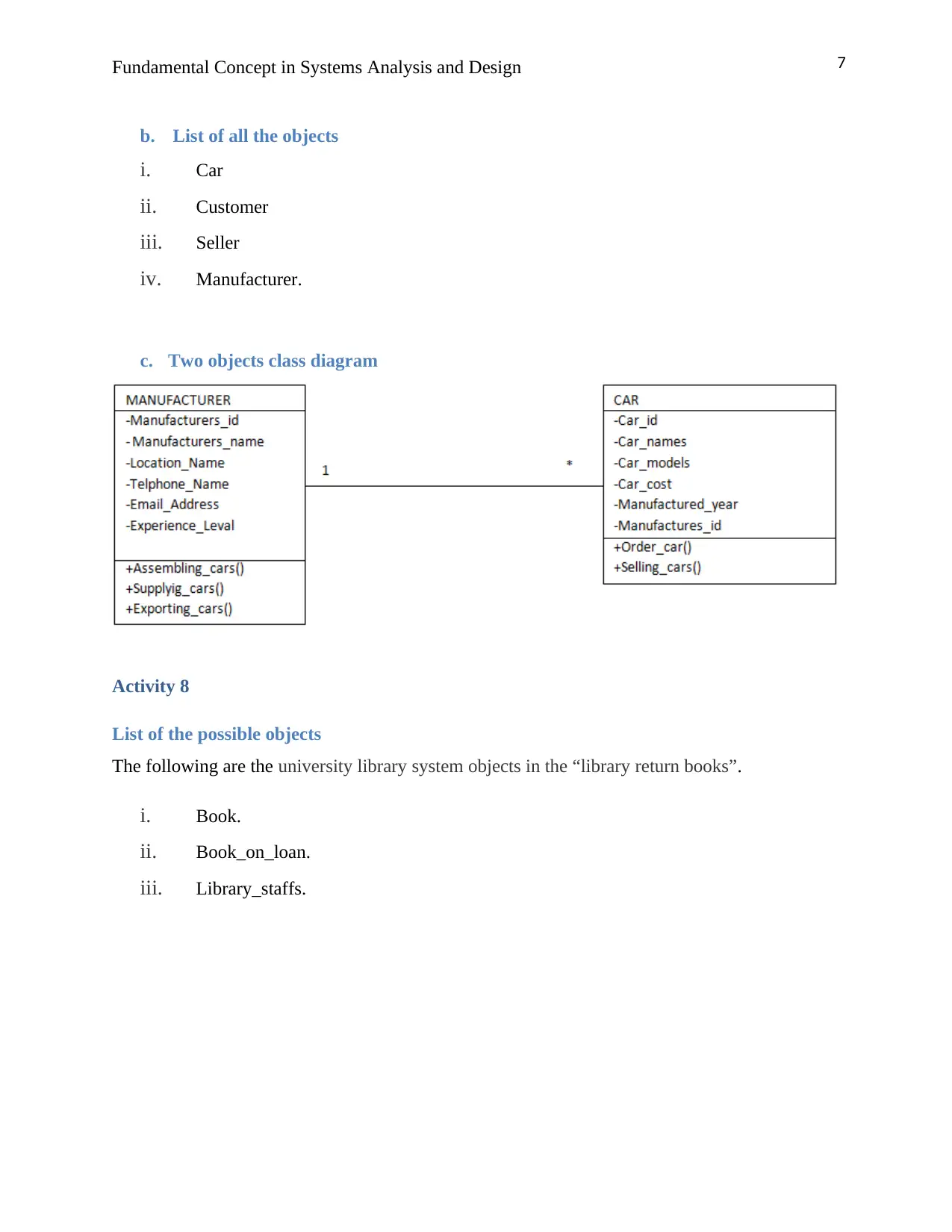
b. List of all the objects
i. Car
ii. Customer
iii. Seller
iv. Manufacturer.
c. Two objects class diagram
Activity 8
List of the possible objects
The following are the university library system objects in the “library return books”.
i. Book.
ii. Book_on_loan.
iii. Library_staffs.
b. List of all the objects
i. Car
ii. Customer
iii. Seller
iv. Manufacturer.
c. Two objects class diagram
Activity 8
List of the possible objects
The following are the university library system objects in the “library return books”.
i. Book.
ii. Book_on_loan.
iii. Library_staffs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
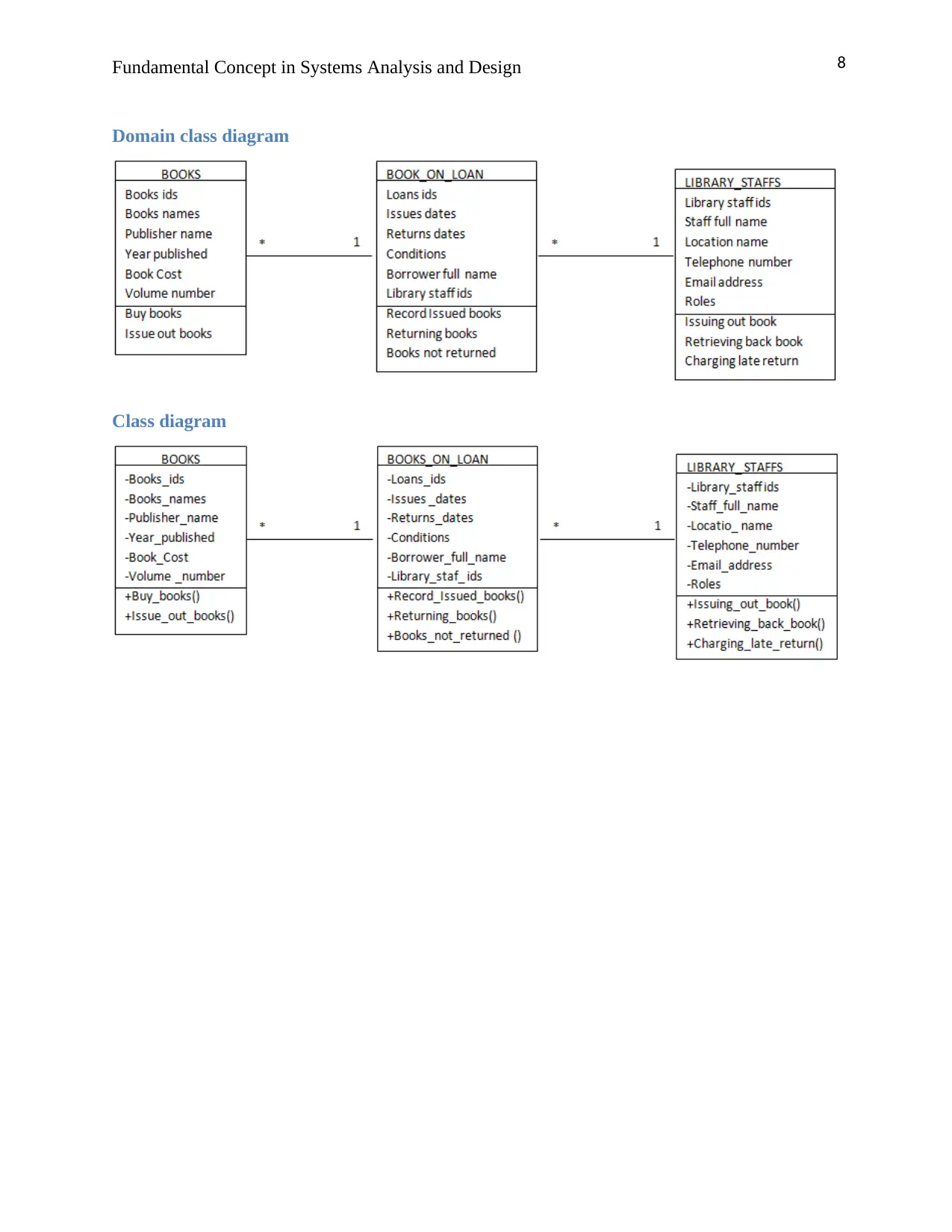
8Fundamental Concept in Systems Analysis and Design
Domain class diagram
Class diagram
Domain class diagram
Class diagram
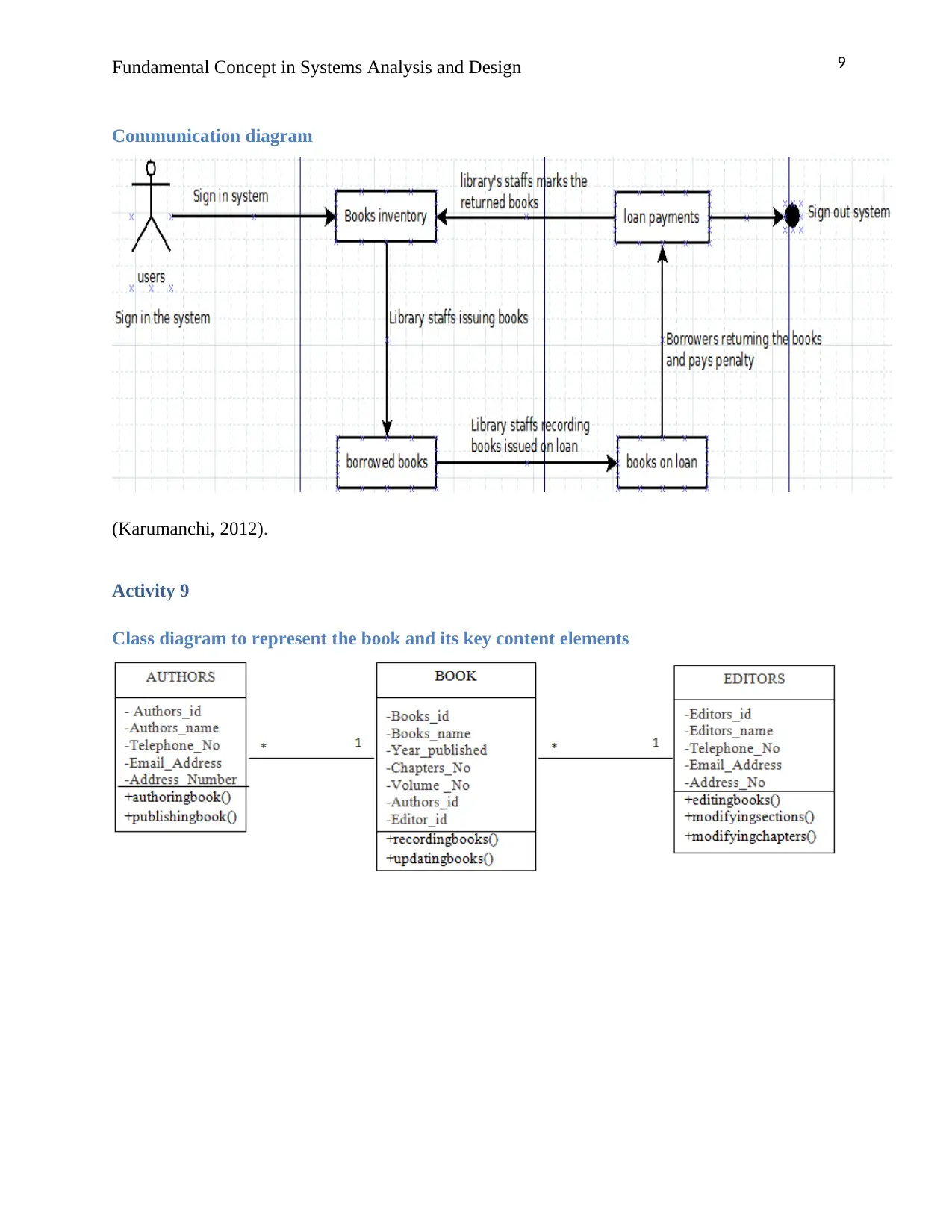
9Fundamental Concept in Systems Analysis and Design
Communication diagram
(Karumanchi, 2012).
Activity 9
Class diagram to represent the book and its key content elements
Communication diagram
(Karumanchi, 2012).
Activity 9
Class diagram to represent the book and its key content elements
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
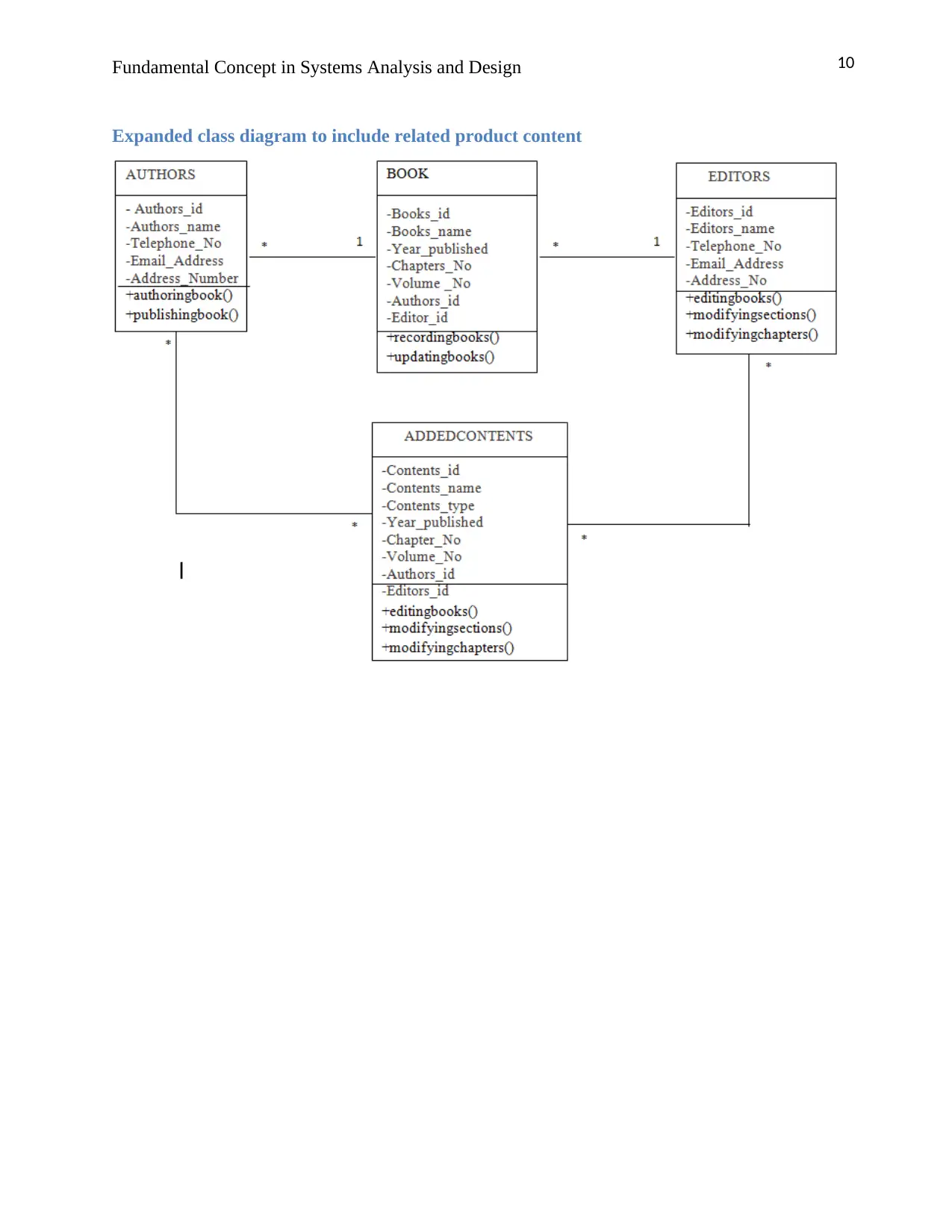
10Fundamental Concept in Systems Analysis and Design
Expanded class diagram to include related product content
Expanded class diagram to include related product content
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11Fundamental Concept in Systems Analysis and Design
Activity 10
Parcel courier service company system deployment activities
a) Training users
In order to deploy the system or account sub-system module as the first module in the
organization the development team will train the system users and the target users will be the
account team and the management members. Among the things that the team will be trained in
are the following:
i. How to securely open the computers system.
ii. How to securely start the installed sub-system.
iii. How to sign in the sub-system.
iv. How to operate the system like preparing trial balance, balance sheet among others.
The management team will be trained on the following aspects:
i. How to securely open the computers system.
ii. How to securely start the installed sub-system.
iii. How to sign in the sub-system.
iv. How to operate the system like checking the profits and amount received reports.
Therefore each system user will be having unique privileges on system access.
b) Deployment order
When the staffs and system users are fully trained by the system developers, the system modules
will be installed and configured into the computers systems where the newly installed system
will be executed parallel to the old system for a period of six weeks for the staffs to be used to
the new operations then the organization data and operations will be shifted to the new installed
system after six weeks elapses.
c) Support activities
The system will be installed in the organization and the system users will be using it and incase
of any error arising the system users will be alerting the technical team to fix the system errors
and bugs and ensure it is operating and running normally (Goyal, 2011).
Activity 10
Parcel courier service company system deployment activities
a) Training users
In order to deploy the system or account sub-system module as the first module in the
organization the development team will train the system users and the target users will be the
account team and the management members. Among the things that the team will be trained in
are the following:
i. How to securely open the computers system.
ii. How to securely start the installed sub-system.
iii. How to sign in the sub-system.
iv. How to operate the system like preparing trial balance, balance sheet among others.
The management team will be trained on the following aspects:
i. How to securely open the computers system.
ii. How to securely start the installed sub-system.
iii. How to sign in the sub-system.
iv. How to operate the system like checking the profits and amount received reports.
Therefore each system user will be having unique privileges on system access.
b) Deployment order
When the staffs and system users are fully trained by the system developers, the system modules
will be installed and configured into the computers systems where the newly installed system
will be executed parallel to the old system for a period of six weeks for the staffs to be used to
the new operations then the organization data and operations will be shifted to the new installed
system after six weeks elapses.
c) Support activities
The system will be installed in the organization and the system users will be using it and incase
of any error arising the system users will be alerting the technical team to fix the system errors
and bugs and ensure it is operating and running normally (Goyal, 2011).

12Fundamental Concept in Systems Analysis and Design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




