Information Security Case Study: Deep Dive into the Target Data Breach
VerifiedAdded on 2023/04/10
|9
|1388
|70
Case Study
AI Summary
This assignment is a comprehensive case study analyzing the 2013 Target data breach. It begins with an introduction to the breach, detailing the use of BlackPOS malware and the compromise of millions of credit card and personal records. A concept map diagrams the threats, security operations, and governance aspects related to the breach. The study then examines the CIA triad (Confidentiality, Integrity, and Availability) and its relevance to the security failures. It explores the protections that were in place, including Windows-based systems and signature-based antivirus, and discusses the impact of cybercrime laws. The analysis concludes by assessing the effectiveness of Target's security measures and emphasizing the need for continuous improvements to address evolving cyber threats. The paper also touches on the ethical and legal implications of the breach, highlighting the failure of existing regulations to prevent the attack and the subsequent damage to Target's reputation.

Running head: INFORMATION SECURITY CASE STUDY
Information Security Case Study
Name of the Student
Name of the University
Author Note:
Information Security Case Study
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY CASE STUDY
Table of Contents
1. Introduction..................................................................................................................................2
2.1 Describe the target breach.....................................................................................................2
2.2 Identify the threats target using concept map diagram..........................................................2
2.3 CIA........................................................................................................................................2
2.4 Relation to the security breach..............................................................................................3
2.5 Protections were in place.......................................................................................................3
3. Conclusion...................................................................................................................................4
4. Reference.....................................................................................................................................6
Table of Contents
1. Introduction..................................................................................................................................2
2.1 Describe the target breach.....................................................................................................2
2.2 Identify the threats target using concept map diagram..........................................................2
2.3 CIA........................................................................................................................................2
2.4 Relation to the security breach..............................................................................................3
2.5 Protections were in place.......................................................................................................3
3. Conclusion...................................................................................................................................4
4. Reference.....................................................................................................................................6

2INFORMATION SECURITY CASE STUDY
1. Introduction
The foremost determination of this paper is to focus on the threat associated which
occurred in Target Corporation’s Network in the year 2013. The advantages, disadvantages,
threats and vulnerabilities in various IT environments. A concept map diagram will be presented
in this paper considering its security threat. The CIA triad will be discussed in this paper and
how it is related to the security breach will be also presented in this paperi. The mitigation plan
for the risks will be stated in the paper considering their effectivenessii. The legal and the ethical
issue associated with this security breach will be also discussed in a detailed manner in this
paper.
2.1 Describe the target breach
This security breach is one of the most devastating among all the major data breaches of
recent times. The cyber criminals used a malware called BlackPOS and about 40 million credit
and debit card holders lost their data in this attack. The attack also compromised the data of 70
million people. The name of the consumer of the organization, their credit and debit card
numbers, expiration dates of the cards, CVV were all compromised due to the attack. Huge
amount of money was compromised due to this attackiii. There were a lot of expenses after this
security attack, which is huge concern for this organization.
1. Introduction
The foremost determination of this paper is to focus on the threat associated which
occurred in Target Corporation’s Network in the year 2013. The advantages, disadvantages,
threats and vulnerabilities in various IT environments. A concept map diagram will be presented
in this paper considering its security threat. The CIA triad will be discussed in this paper and
how it is related to the security breach will be also presented in this paperi. The mitigation plan
for the risks will be stated in the paper considering their effectivenessii. The legal and the ethical
issue associated with this security breach will be also discussed in a detailed manner in this
paper.
2.1 Describe the target breach
This security breach is one of the most devastating among all the major data breaches of
recent times. The cyber criminals used a malware called BlackPOS and about 40 million credit
and debit card holders lost their data in this attack. The attack also compromised the data of 70
million people. The name of the consumer of the organization, their credit and debit card
numbers, expiration dates of the cards, CVV were all compromised due to the attack. Huge
amount of money was compromised due to this attackiii. There were a lot of expenses after this
security attack, which is huge concern for this organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3INFORMATION SECURITY CASE STUDY
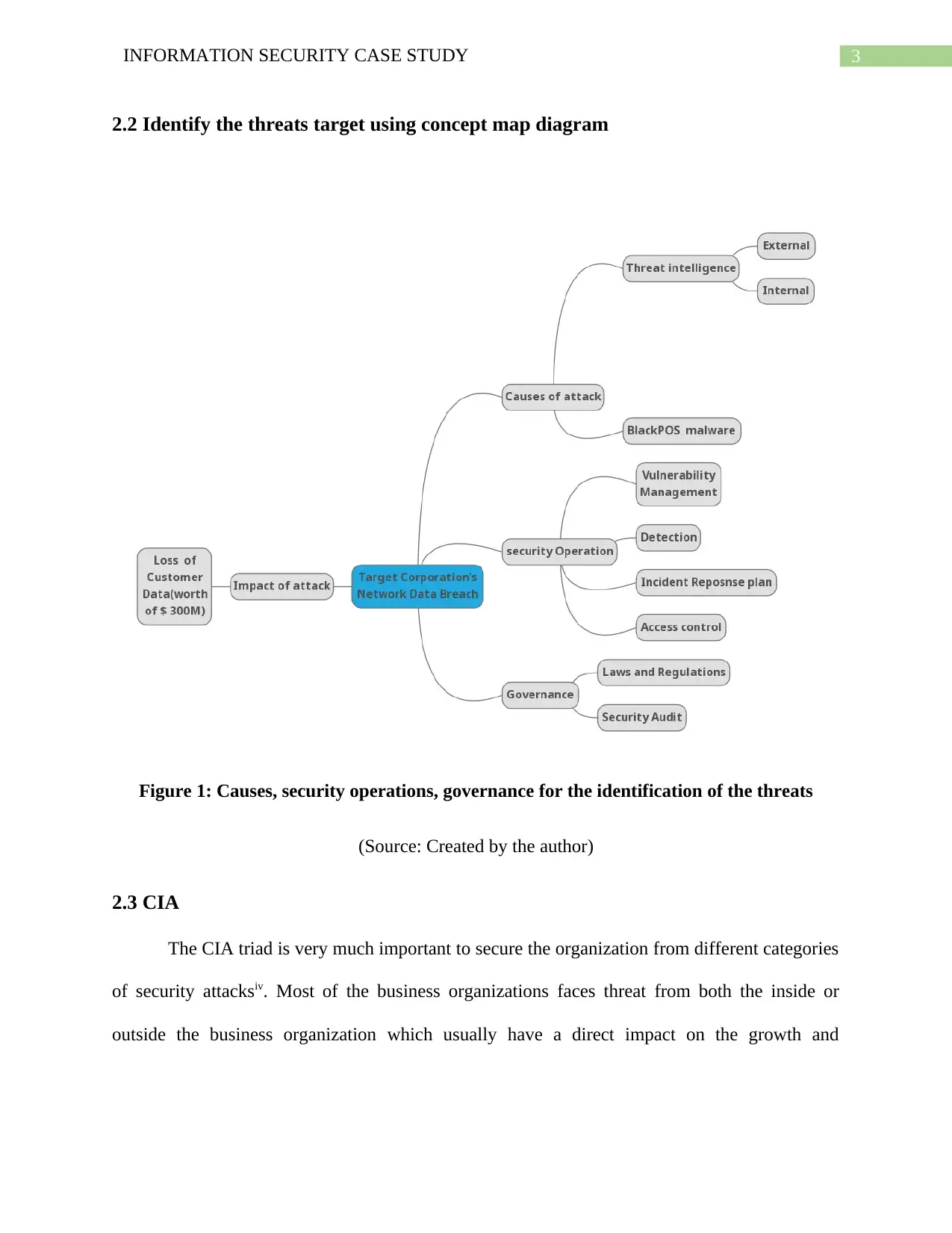
2.2 Identify the threats target using concept map diagram
Figure 1: Causes, security operations, governance for the identification of the threats
(Source: Created by the author)
2.3 CIA
The CIA triad is very much important to secure the organization from different categories
of security attacksiv. Most of the business organizations faces threat from both the inside or
outside the business organization which usually have a direct impact on the growth and
2.2 Identify the threats target using concept map diagram
Figure 1: Causes, security operations, governance for the identification of the threats
(Source: Created by the author)
2.3 CIA
The CIA triad is very much important to secure the organization from different categories
of security attacksiv. Most of the business organizations faces threat from both the inside or
outside the business organization which usually have a direct impact on the growth and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY CASE STUDY
productivity of the organization. The description of each of the categories of CIA are as
followings:
Confidentiality: The confidentiality is a set of rules which is very much important for
limit the access to information.
Integrity: The trust worthiness of the information and the accuracy of the data can be
managed using Integrityv.
Availability: The availability of the information must be from a reliable source, any
kinds of unauthorized access can have a huge impact on the efficiency and productivity of the
organization as important data are transported from one unit of the organization to another.
2.4 Relation to the security breach
The compromise of the Fazio Mechanical Services was compromised using the Citadel
Trojan may fall into the category of the compromising the confidentiality of the services. The
security systems which were used in this organization were compromised heavily which is a very
serious concern and falls under the category of the confidentiality. The cybercriminal got access
to the network of the organization is a significant concern for the organization as well. The
confidentiality of their private network was breached when the malware had their effect on the
PoS terminals. The data which are moved out of the target network are hampered the
confidentiality of the datavi. The data which are stolen from the network made the data available
to the consumers of this organization where the availability of the data is breached.
2.5 Protections were in place
Windows based operating systems were used in the working environment of this
organization. The internal servers which were supposed to protect the private network were
productivity of the organization. The description of each of the categories of CIA are as
followings:
Confidentiality: The confidentiality is a set of rules which is very much important for
limit the access to information.
Integrity: The trust worthiness of the information and the accuracy of the data can be
managed using Integrityv.
Availability: The availability of the information must be from a reliable source, any
kinds of unauthorized access can have a huge impact on the efficiency and productivity of the
organization as important data are transported from one unit of the organization to another.
2.4 Relation to the security breach
The compromise of the Fazio Mechanical Services was compromised using the Citadel
Trojan may fall into the category of the compromising the confidentiality of the services. The
security systems which were used in this organization were compromised heavily which is a very
serious concern and falls under the category of the confidentiality. The cybercriminal got access
to the network of the organization is a significant concern for the organization as well. The
confidentiality of their private network was breached when the malware had their effect on the
PoS terminals. The data which are moved out of the target network are hampered the
confidentiality of the datavi. The data which are stolen from the network made the data available
to the consumers of this organization where the availability of the data is breached.
2.5 Protections were in place
Windows based operating systems were used in the working environment of this
organization. The internal servers which were supposed to protect the private network were

5INFORMATION SECURITY CASE STUDY
compromised by the cyber criminals. Signature based antivirus detections were used by this
organization in order to protect the organizational assets was itself. Multiphase data exfiltration
schemes are used by this organization to protect the infiltrations. There are different categories of
cybercrime law and regulations which protects the business organizations from the cyber security
attacks such as the federal Computer Fraud and Abuse Act (CFAA). The department of Justice
Computer Crimes and the Intellectual Property Division.
The protections that were on place both positively and negatively had an impact on
Target Corporation Network. The laws, rules and regulations are very much important to secure
the organizational assets but at the same time these protocols and rules gave the cyber criminals
the access to the private network. Professional code of conduct was breached the moments their
database was under threat. The protection was enough from the point of view of the internal
stakeholders of the organization but the advancements of the cyber criminals was more way head
that the existing network security of this organization. The security and the privacy of the
business data was very poorly compromised. In spite of the every protocols and rules, the
business reputation of this organization was badly compromisedvii. The cyber rules and
regulations failed miserably when trying to protect the data from the cyber criminals. However it
can be said that the security measures taken by this organization was only able to protect the
network up to a certain levelviii. Advancements and modifications are very much important in the
security plan of this organization so that the can deal with more powerful threats.
3. Conclusion
The paper concludes the security breach which happened in the year when the
networking security of Target Corporation network was compromised by a very powerful attack
by a group of cyber criminals. The description of the impact of the security attack can be
compromised by the cyber criminals. Signature based antivirus detections were used by this
organization in order to protect the organizational assets was itself. Multiphase data exfiltration
schemes are used by this organization to protect the infiltrations. There are different categories of
cybercrime law and regulations which protects the business organizations from the cyber security
attacks such as the federal Computer Fraud and Abuse Act (CFAA). The department of Justice
Computer Crimes and the Intellectual Property Division.
The protections that were on place both positively and negatively had an impact on
Target Corporation Network. The laws, rules and regulations are very much important to secure
the organizational assets but at the same time these protocols and rules gave the cyber criminals
the access to the private network. Professional code of conduct was breached the moments their
database was under threat. The protection was enough from the point of view of the internal
stakeholders of the organization but the advancements of the cyber criminals was more way head
that the existing network security of this organization. The security and the privacy of the
business data was very poorly compromised. In spite of the every protocols and rules, the
business reputation of this organization was badly compromisedvii. The cyber rules and
regulations failed miserably when trying to protect the data from the cyber criminals. However it
can be said that the security measures taken by this organization was only able to protect the
network up to a certain levelviii. Advancements and modifications are very much important in the
security plan of this organization so that the can deal with more powerful threats.
3. Conclusion
The paper concludes the security breach which happened in the year when the
networking security of Target Corporation network was compromised by a very powerful attack
by a group of cyber criminals. The description of the impact of the security attack can be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY CASE STUDY
concluded from the paper, along with that importance of the CIA triad has been explained well in
the paper. The effectiveness of the existing security policy followed by this organization can be
also determined from this paper as well. Thus the paper can be very much beneficial for
maintaining the networking security in business organizations.
concluded from the paper, along with that importance of the CIA triad has been explained well in
the paper. The effectiveness of the existing security policy followed by this organization can be
also determined from this paper as well. Thus the paper can be very much beneficial for
maintaining the networking security in business organizations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY CASE STUDY
4. Reference:
Bellia, P. L. (2016). A Code-Based Approach to Unauthorized Access Under the Computer
Fraud and Abuse Act. Geo. Wash. L. Rev., 84, 1442.
Ellsworth, J. L., Porter, B. W., Suver, C. A., & Newcombe, C. R. (2016). U.S. Patent No.
9,240,954. Washington, DC: U.S. Patent and Trademark Office.
Ettema, T., & Xie, H. (2016). U.S. Patent No. 9,495,188. Washington, DC: U.S. Patent and
Trademark Office.
Griffin, T. E., McDaniel, A. R., Razavi, R., & Westrup, S. (2016). U.S. Patent Application No.
14/594,590.
Mayer, J. (2016). The Narrow Interpretation of the Computer Fraud and Abuse Act: A User
Guide for Applying United States v. Nosal. Geo. Wash. L. Rev., 84, 1644.
Richardson, D. R., Marshall, B. E., Sivasubramanian, S., & Saraf, T. (2016). U.S. Patent No.
9,251,112. Washington, DC: U.S. Patent and Trademark Office.
Whitehouse, S. (2016). Hacking into the Computer Fraud and Abuse Act: The CFAA at 30. Geo.
Wash. L. Rev., 84, 1437-1438.
Williams, B. (2018). Preventing Unintended Internet Discrimination: An Analysis of the
Computer Fraud and Abuse Act for Algorithmic Racial Steering. U. Ill. L. Rev., 847.
4. Reference:
Bellia, P. L. (2016). A Code-Based Approach to Unauthorized Access Under the Computer
Fraud and Abuse Act. Geo. Wash. L. Rev., 84, 1442.
Ellsworth, J. L., Porter, B. W., Suver, C. A., & Newcombe, C. R. (2016). U.S. Patent No.
9,240,954. Washington, DC: U.S. Patent and Trademark Office.
Ettema, T., & Xie, H. (2016). U.S. Patent No. 9,495,188. Washington, DC: U.S. Patent and
Trademark Office.
Griffin, T. E., McDaniel, A. R., Razavi, R., & Westrup, S. (2016). U.S. Patent Application No.
14/594,590.
Mayer, J. (2016). The Narrow Interpretation of the Computer Fraud and Abuse Act: A User
Guide for Applying United States v. Nosal. Geo. Wash. L. Rev., 84, 1644.
Richardson, D. R., Marshall, B. E., Sivasubramanian, S., & Saraf, T. (2016). U.S. Patent No.
9,251,112. Washington, DC: U.S. Patent and Trademark Office.
Whitehouse, S. (2016). Hacking into the Computer Fraud and Abuse Act: The CFAA at 30. Geo.
Wash. L. Rev., 84, 1437-1438.
Williams, B. (2018). Preventing Unintended Internet Discrimination: An Analysis of the
Computer Fraud and Abuse Act for Algorithmic Racial Steering. U. Ill. L. Rev., 847.

i Richardson, D. R., Marshall, B. E., Sivasubramanian, S., & Saraf, T. (2016). U.S. Patent No.
9,251,112. Washington, DC: U.S. Patent and Trademark Office.
ii Mayer, J. (2016). The Narrow Interpretation of the Computer Fraud and Abuse Act: A User Guide for
Applying United States v. Nosal. Geo. Wash. L. Rev., 84, 1644.
iii Whitehouse, S. (2016). Hacking into the Computer Fraud and Abuse Act: The CFAA at 30. Geo.
Wash. L. Rev., 84, 1437-1438.
iv Williams, B. (2018). Preventing Unintended Internet Discrimination: An Analysis of the Computer
Fraud and Abuse Act for Algorithmic Racial Steering. U. Ill. L. Rev., 847.
v Griffin, T. E., McDaniel, A. R., Razavi, R., & Westrup, S. (2016). U.S. Patent Application No.
14/594,590.
vi Ettema, T., & Xie, H. (2016). U.S. Patent No. 9,495,188. Washington, DC: U.S. Patent and
Trademark Office.
vii Ellsworth, J. L., Porter, B. W., Suver, C. A., & Newcombe, C. R. (2016). U.S. Patent No. 9,240,954.
Washington, DC: U.S. Patent and Trademark Office.
viii Bellia, P. L. (2016). A Code-Based Approach to Unauthorized Access Under the Computer Fraud
and Abuse Act. Geo. Wash. L. Rev., 84, 1442.
9,251,112. Washington, DC: U.S. Patent and Trademark Office.
ii Mayer, J. (2016). The Narrow Interpretation of the Computer Fraud and Abuse Act: A User Guide for
Applying United States v. Nosal. Geo. Wash. L. Rev., 84, 1644.
iii Whitehouse, S. (2016). Hacking into the Computer Fraud and Abuse Act: The CFAA at 30. Geo.
Wash. L. Rev., 84, 1437-1438.
iv Williams, B. (2018). Preventing Unintended Internet Discrimination: An Analysis of the Computer
Fraud and Abuse Act for Algorithmic Racial Steering. U. Ill. L. Rev., 847.
v Griffin, T. E., McDaniel, A. R., Razavi, R., & Westrup, S. (2016). U.S. Patent Application No.
14/594,590.
vi Ettema, T., & Xie, H. (2016). U.S. Patent No. 9,495,188. Washington, DC: U.S. Patent and
Trademark Office.
vii Ellsworth, J. L., Porter, B. W., Suver, C. A., & Newcombe, C. R. (2016). U.S. Patent No. 9,240,954.
Washington, DC: U.S. Patent and Trademark Office.
viii Bellia, P. L. (2016). A Code-Based Approach to Unauthorized Access Under the Computer Fraud
and Abuse Act. Geo. Wash. L. Rev., 84, 1442.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





