Comprehensive TCP/IP Networking Assessment Report for IT Solutions
VerifiedAdded on 2021/04/21
|12
|2378
|79
Report
AI Summary
This report presents a comprehensive analysis of TCP/IP networking, beginning with a comparison of the OSI and TCP/IP reference models, highlighting their respective strengths and weaknesses. It delves into the Address Resolution Protocol (ARP), explaining its function in mapping IP addresses to physical machine addresses and its significance in IPv4 networks, including discussions on ARP cache and security vulnerabilities. The report also includes practical exercises, such as subnet mask calculations using gestioip.net and subnet-calculator.com, demonstrating the configuration of IP addresses and subnetting. A significant portion of the report is dedicated to a case study for Foreshore IT solutions, detailing the design of a simple addressing solution to connect six different branches. This includes network diagrams, subnet planning, and DHCP configuration, addressing considerations for network growth and security measures like VLANs and access control lists. The report concludes with a discussion on how to reconfigure the network if the number of hosts increases. This solution is contributed by a student to be published on the website Desklib. Desklib is a platform which provides all the necessary AI based study tools for students.

Running head: TCP/IP NETWORKING
TCP/IP Networking
Assessment No
Assessment Title
Student Name & ID
Subject Name and Code
Student Email Address
TCP/IP Networking
Assessment No
Assessment Title
Student Name & ID
Subject Name and Code
Student Email Address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
TCP/IP NETWORKING
Table of Contents
Answer to Question 1: Comparison and contrast of the OSI reference model................................2
Answer to Question 2:.....................................................................................................................4
Hands on Project 2.3: calculation of the subnet mask for a required number of IPV4 subnets. .4
Hands on Project 2.5....................................................................................................................5
Answer to Question 3: Address Resolution Protocol and its Purpose.............................................6
Answer to Question 4: Case Study Task.........................................................................................7
Bibliography..................................................................................................................................12
TCP/IP NETWORKING
Table of Contents
Answer to Question 1: Comparison and contrast of the OSI reference model................................2
Answer to Question 2:.....................................................................................................................4
Hands on Project 2.3: calculation of the subnet mask for a required number of IPV4 subnets. .4
Hands on Project 2.5....................................................................................................................5
Answer to Question 3: Address Resolution Protocol and its Purpose.............................................6
Answer to Question 4: Case Study Task.........................................................................................7
Bibliography..................................................................................................................................12
2
TCP/IP NETWORKING
Answer to Question 1: Comparison and contrast of the OSI reference model
OSI Reference Model TCP/IP Networking Model
It is a generic standard independent of the
protocol that can act as a gateway for
communicating with the end users connected
in the network (Goralski, 2017).
It is dependent on the standard of protocols
using which the internet works and has a
communication protocol that is used for
connecting the hosts in the network.
The delivery of the data packets depends on
the transport layer
The delivery of the data packets is not solely
dependent on the transport layer and thus it
does not guarantees the delivery (Edwards &
Bramante, 2015). But the TCP/IP model is
more reliable than OSI reference model
The OSI reference model follows a vertical
approach
The TCP/IP model follows a horizontal
approach
In this model both the presentation layer and
the session layer is separate
In this model the presentation and the session
layer is combined to form an application
layer.
The transport layer follows connection
oriented approach
The transport layer of TCP/IP model can
connection less or connection oriented
The network layer of TCP/IP can be
connection less or connection oriented (Alani,
2014)
The network layer follows connection less
approach
TCP/IP NETWORKING
Answer to Question 1: Comparison and contrast of the OSI reference model
OSI Reference Model TCP/IP Networking Model
It is a generic standard independent of the
protocol that can act as a gateway for
communicating with the end users connected
in the network (Goralski, 2017).
It is dependent on the standard of protocols
using which the internet works and has a
communication protocol that is used for
connecting the hosts in the network.
The delivery of the data packets depends on
the transport layer
The delivery of the data packets is not solely
dependent on the transport layer and thus it
does not guarantees the delivery (Edwards &
Bramante, 2015). But the TCP/IP model is
more reliable than OSI reference model
The OSI reference model follows a vertical
approach
The TCP/IP model follows a horizontal
approach
In this model both the presentation layer and
the session layer is separate
In this model the presentation and the session
layer is combined to form an application
layer.
The transport layer follows connection
oriented approach
The transport layer of TCP/IP model can
connection less or connection oriented
The network layer of TCP/IP can be
connection less or connection oriented (Alani,
2014)
The network layer follows connection less
approach
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
TCP/IP NETWORKING
OSI model faces problem while application of
different protocols into the model
This model does not fits any network
protocols into the model
The protocols can be replaced with new if
there is a change in the technology
Replacement of the protocol is not possible
The services, protocols and the interfaces can
be distinct easily as it is independent of any
protocols
It is dependent on the protocol and the
services, interfaces and the protocols cannot
be separated (Yadav, 2015).
The OSI model consists of 7 layers The TCP/IP model has 4 layers
The TCP/IP networking model is the most useful for the development of a network
because it enables a full control of the network by specifying how the data is changed over
internet. It also increases the reliability of the network with the application of the automatic
recovery of the network if any of the network devices fails. It helps in better management of the
network by assembling the data into small packets and send over the network to reach the right
node.
TCP/IP NETWORKING
OSI model faces problem while application of
different protocols into the model
This model does not fits any network
protocols into the model
The protocols can be replaced with new if
there is a change in the technology
Replacement of the protocol is not possible
The services, protocols and the interfaces can
be distinct easily as it is independent of any
protocols
It is dependent on the protocol and the
services, interfaces and the protocols cannot
be separated (Yadav, 2015).
The OSI model consists of 7 layers The TCP/IP model has 4 layers
The TCP/IP networking model is the most useful for the development of a network
because it enables a full control of the network by specifying how the data is changed over
internet. It also increases the reliability of the network with the application of the automatic
recovery of the network if any of the network devices fails. It helps in better management of the
network by assembling the data into small packets and send over the network to reach the right
node.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
TCP/IP NETWORKING
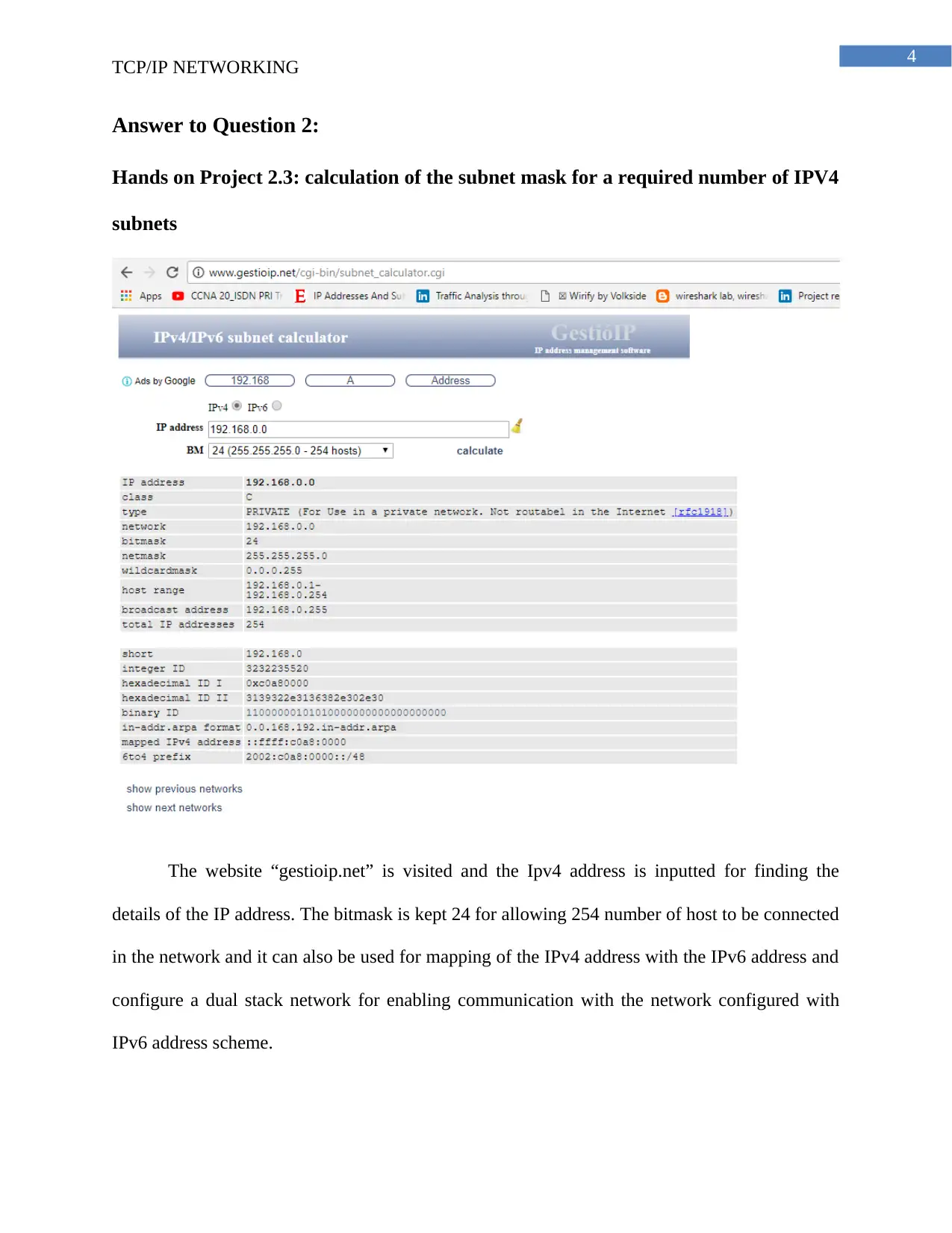
Answer to Question 2:
Hands on Project 2.3: calculation of the subnet mask for a required number of IPV4
subnets
The website “gestioip.net” is visited and the Ipv4 address is inputted for finding the
details of the IP address. The bitmask is kept 24 for allowing 254 number of host to be connected
in the network and it can also be used for mapping of the IPv4 address with the IPv6 address and
configure a dual stack network for enabling communication with the network configured with
IPv6 address scheme.
TCP/IP NETWORKING
Answer to Question 2:
Hands on Project 2.3: calculation of the subnet mask for a required number of IPV4
subnets
The website “gestioip.net” is visited and the Ipv4 address is inputted for finding the
details of the IP address. The bitmask is kept 24 for allowing 254 number of host to be connected
in the network and it can also be used for mapping of the IPv4 address with the IPv6 address and
configure a dual stack network for enabling communication with the network configured with
IPv6 address scheme.
5
TCP/IP NETWORKING
Hands on Project 2.5
Subnet calculation for the IP Address 192.168.0.1
Subnet mask Subnet bits Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
255.255.255.192 2 26 62 192.168.0.1 -
192.168.0.62
192.168.0.63
The subnet of the IP address “192.168.0.1” is calculated from the website subnet-
calculator.com and the subnet mask, subnet bits, mask bits, host per subnet, host address range
and the broadcast address is noted. The values of the subnet are changed and the change in the
rest of the vales are noted and attached in the above table.
Subnet calculation for the IP Address 10.0.0.1
Subnet bits Maximum
subnets
Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
8 256 16 65534 10.0.0.1 -
10.0.255.254
10.0.255.255
The Class A network is selected for evaluation and the mask bits is changed from
255.0.0.0 to 255.255.0.0 and available number of host per subnet is noted and it has been found
that the host per subnet decreased.
TCP/IP NETWORKING
Hands on Project 2.5
Subnet calculation for the IP Address 192.168.0.1
Subnet mask Subnet bits Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
255.255.255.192 2 26 62 192.168.0.1 -
192.168.0.62
192.168.0.63
The subnet of the IP address “192.168.0.1” is calculated from the website subnet-
calculator.com and the subnet mask, subnet bits, mask bits, host per subnet, host address range
and the broadcast address is noted. The values of the subnet are changed and the change in the
rest of the vales are noted and attached in the above table.
Subnet calculation for the IP Address 10.0.0.1
Subnet bits Maximum
subnets
Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
8 256 16 65534 10.0.0.1 -
10.0.255.254
10.0.255.255
The Class A network is selected for evaluation and the mask bits is changed from
255.0.0.0 to 255.255.0.0 and available number of host per subnet is noted and it has been found
that the host per subnet decreased.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
TCP/IP NETWORKING
More experiment is done and the class B is also selected and the IP address changed to
172.16.0.1 and the range of the first octet range becomes 128 – 198.
Answer to Question 3: Address Resolution Protocol and its Purpose
The address resolution protocol (ARP) is applied for the mapping of the IP address with
physical machine address of the computers. It uses the data link protocol for the mapping of IP
address with the hardware address. The main operation of the address resolution protocol is done
beneath the network layer as an interface of OSI and the OSI link layer. It finds its application in
an IPv4 network (Bruschi et al., 2017). The address resolution is used for finding the address of
a computer from a network. The address can be resolved utilizing the protocol where an
information is sent from the local computer to the server. The network system can be uniquely
identified by analyzing the information received from the server with the help of the address. The
procedure of address resolution is completed after receiving response from the server with the
required address at the client end.
The main purpose of the ARP cache is to maintain a correlation between the IP address
and its corresponding MAC address. The ARP cache table is populated with the resolution of the
hostname and the IP address and maintain communication between the devices connected with
the router. There are several disadvantage of the ARP cache because the hackers can access the
cache table to modify the data traffic and cause session hijacking and denial of service (Younes,
2018). Address resolution protocol is stateless because the hosts connected in the network cache
the replies of the ARP. There are different defense mechanism that can be applied for the
prevention of the ARP spoofing attacks and secure the network from unauthorized users (Yang,
2015). The application of static Arp entry, spoof detection and prevention software and
increasing the security of the operating system of the hosts can reduce the risk of ARP spoofing
TCP/IP NETWORKING
More experiment is done and the class B is also selected and the IP address changed to
172.16.0.1 and the range of the first octet range becomes 128 – 198.
Answer to Question 3: Address Resolution Protocol and its Purpose
The address resolution protocol (ARP) is applied for the mapping of the IP address with
physical machine address of the computers. It uses the data link protocol for the mapping of IP
address with the hardware address. The main operation of the address resolution protocol is done
beneath the network layer as an interface of OSI and the OSI link layer. It finds its application in
an IPv4 network (Bruschi et al., 2017). The address resolution is used for finding the address of
a computer from a network. The address can be resolved utilizing the protocol where an
information is sent from the local computer to the server. The network system can be uniquely
identified by analyzing the information received from the server with the help of the address. The
procedure of address resolution is completed after receiving response from the server with the
required address at the client end.
The main purpose of the ARP cache is to maintain a correlation between the IP address
and its corresponding MAC address. The ARP cache table is populated with the resolution of the
hostname and the IP address and maintain communication between the devices connected with
the router. There are several disadvantage of the ARP cache because the hackers can access the
cache table to modify the data traffic and cause session hijacking and denial of service (Younes,
2018). Address resolution protocol is stateless because the hosts connected in the network cache
the replies of the ARP. There are different defense mechanism that can be applied for the
prevention of the ARP spoofing attacks and secure the network from unauthorized users (Yang,
2015). The application of static Arp entry, spoof detection and prevention software and
increasing the security of the operating system of the hosts can reduce the risk of ARP spoofing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
TCP/IP NETWORKING
attacks. The redundancy in the network service can be implemented and the Arp cache can be
used for debugging the IP traffic between the hosts for communicating in the network.
Answer to Question 4: Case Study Task
Introduction
The report is prepared for Foreshore IT solutions for the development of a network
solution to connect the six different branches of the company. The prototype of the network is
designed and attached with the report. A simple network address solution is created for the
configuration of the router according to the address plan and enabling communication between
the different departments. With the calculation of the network address and the range of IP
address the security of the network can be increased and the whole network can be monitored
from a single point.
a. Detail Design of Simple Addressing Solution
TCP/IP NETWORKING
attacks. The redundancy in the network service can be implemented and the Arp cache can be
used for debugging the IP traffic between the hosts for communicating in the network.
Answer to Question 4: Case Study Task
Introduction
The report is prepared for Foreshore IT solutions for the development of a network
solution to connect the six different branches of the company. The prototype of the network is
designed and attached with the report. A simple network address solution is created for the
configuration of the router according to the address plan and enabling communication between
the different departments. With the calculation of the network address and the range of IP
address the security of the network can be increased and the whole network can be monitored
from a single point.
a. Detail Design of Simple Addressing Solution
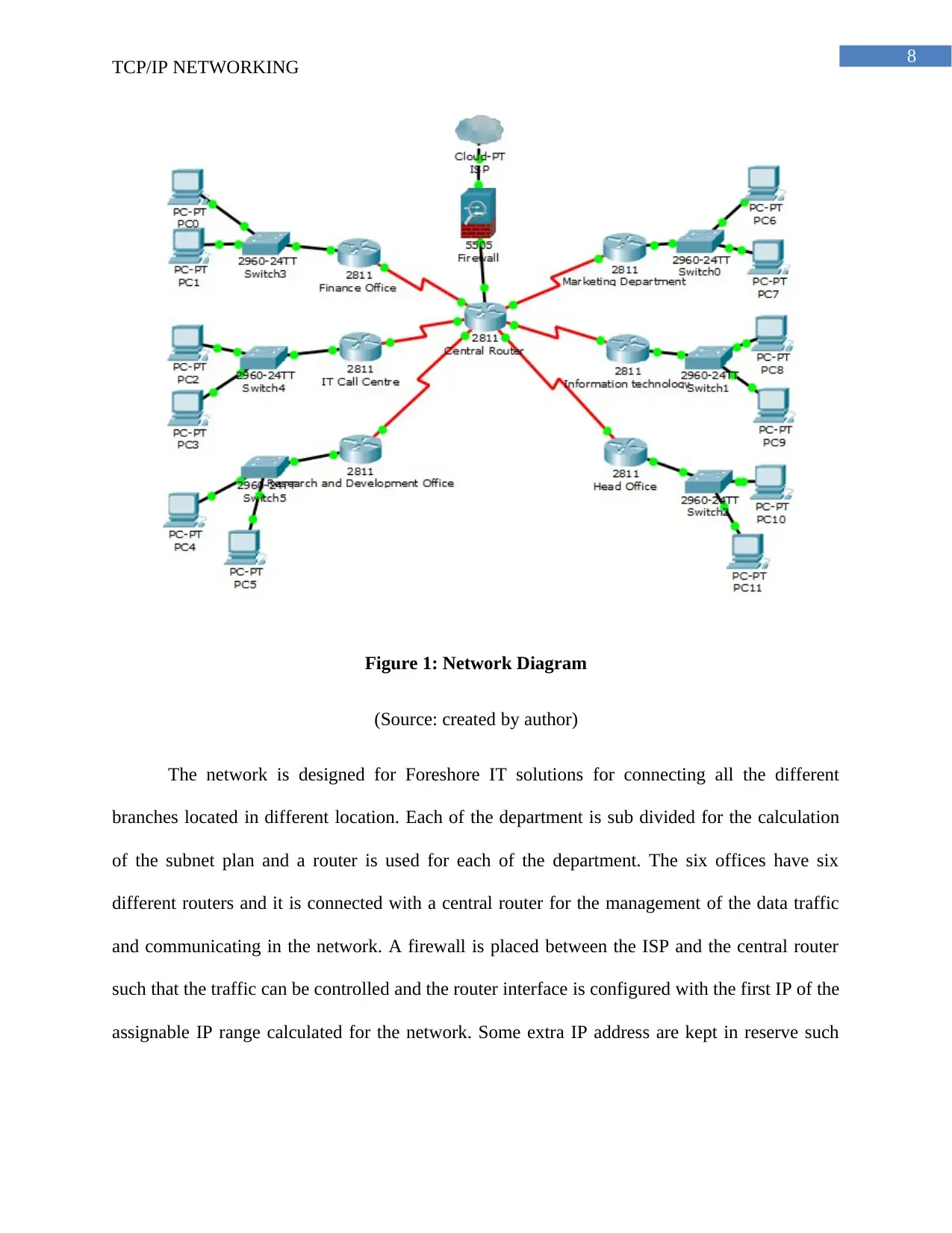
8
TCP/IP NETWORKING
Figure 1: Network Diagram
(Source: created by author)
The network is designed for Foreshore IT solutions for connecting all the different
branches located in different location. Each of the department is sub divided for the calculation
of the subnet plan and a router is used for each of the department. The six offices have six
different routers and it is connected with a central router for the management of the data traffic
and communicating in the network. A firewall is placed between the ISP and the central router
such that the traffic can be controlled and the router interface is configured with the first IP of the
assignable IP range calculated for the network. Some extra IP address are kept in reserve such
TCP/IP NETWORKING
Figure 1: Network Diagram
(Source: created by author)
The network is designed for Foreshore IT solutions for connecting all the different
branches located in different location. Each of the department is sub divided for the calculation
of the subnet plan and a router is used for each of the department. The six offices have six
different routers and it is connected with a central router for the management of the data traffic
and communicating in the network. A firewall is placed between the ISP and the central router
such that the traffic can be controlled and the router interface is configured with the first IP of the
assignable IP range calculated for the network. Some extra IP address are kept in reserve such
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
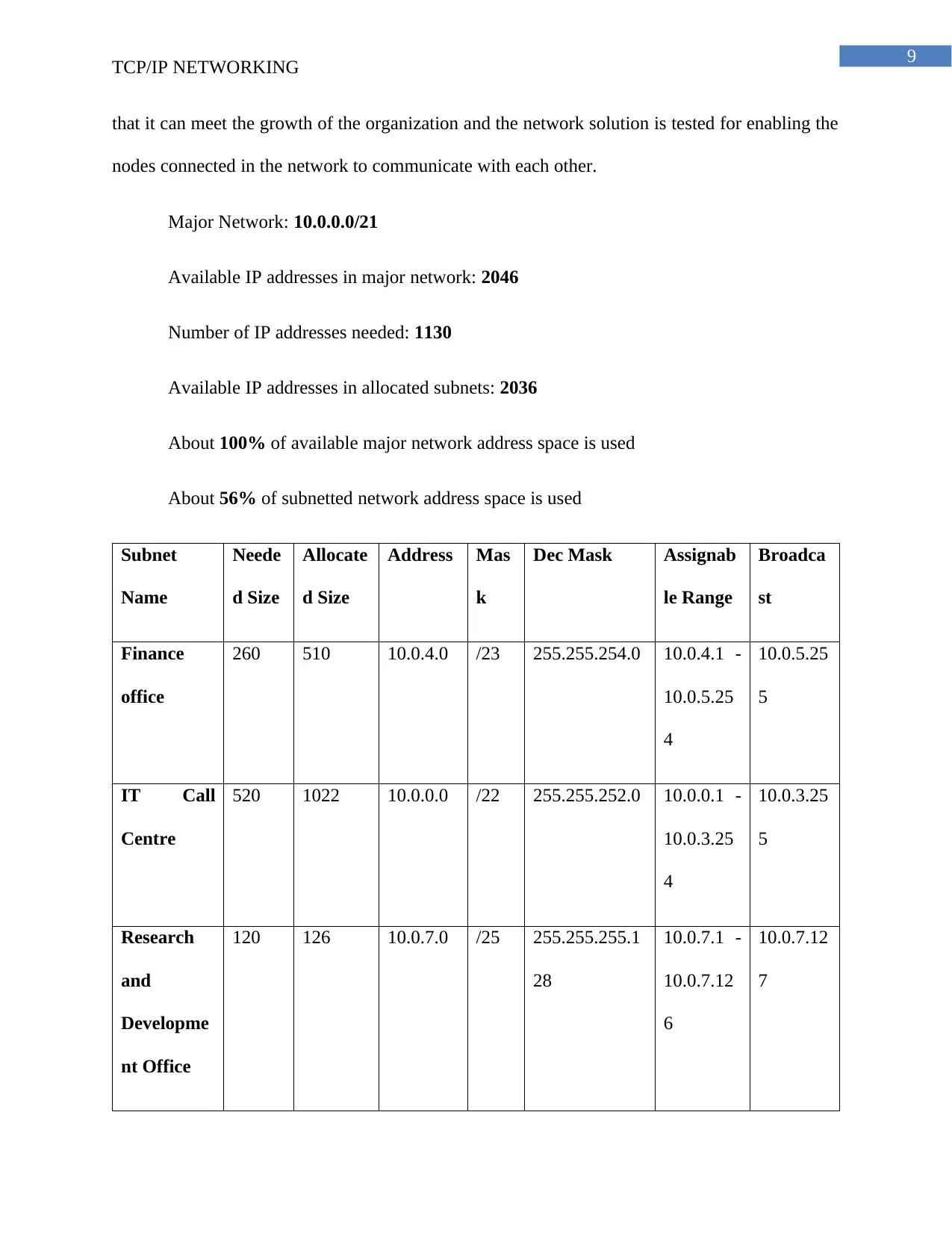
9
TCP/IP NETWORKING
that it can meet the growth of the organization and the network solution is tested for enabling the
nodes connected in the network to communicate with each other.
Major Network: 10.0.0.0/21
Available IP addresses in major network: 2046
Number of IP addresses needed: 1130
Available IP addresses in allocated subnets: 2036
About 100% of available major network address space is used
About 56% of subnetted network address space is used
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignab
le Range
Broadca
st
Finance
office
260 510 10.0.4.0 /23 255.255.254.0 10.0.4.1 -
10.0.5.25
4
10.0.5.25
5
IT Call
Centre
520 1022 10.0.0.0 /22 255.255.252.0 10.0.0.1 -
10.0.3.25
4
10.0.3.25
5
Research
and
Developme
nt Office
120 126 10.0.7.0 /25 255.255.255.1
28
10.0.7.1 -
10.0.7.12
6
10.0.7.12
7
TCP/IP NETWORKING
that it can meet the growth of the organization and the network solution is tested for enabling the
nodes connected in the network to communicate with each other.
Major Network: 10.0.0.0/21
Available IP addresses in major network: 2046
Number of IP addresses needed: 1130
Available IP addresses in allocated subnets: 2036
About 100% of available major network address space is used
About 56% of subnetted network address space is used
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignab
le Range
Broadca
st
Finance
office
260 510 10.0.4.0 /23 255.255.254.0 10.0.4.1 -
10.0.5.25
4
10.0.5.25
5
IT Call
Centre
520 1022 10.0.0.0 /22 255.255.252.0 10.0.0.1 -
10.0.3.25
4
10.0.3.25
5
Research
and
Developme
nt Office
120 126 10.0.7.0 /25 255.255.255.1
28
10.0.7.1 -
10.0.7.12
6
10.0.7.12
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
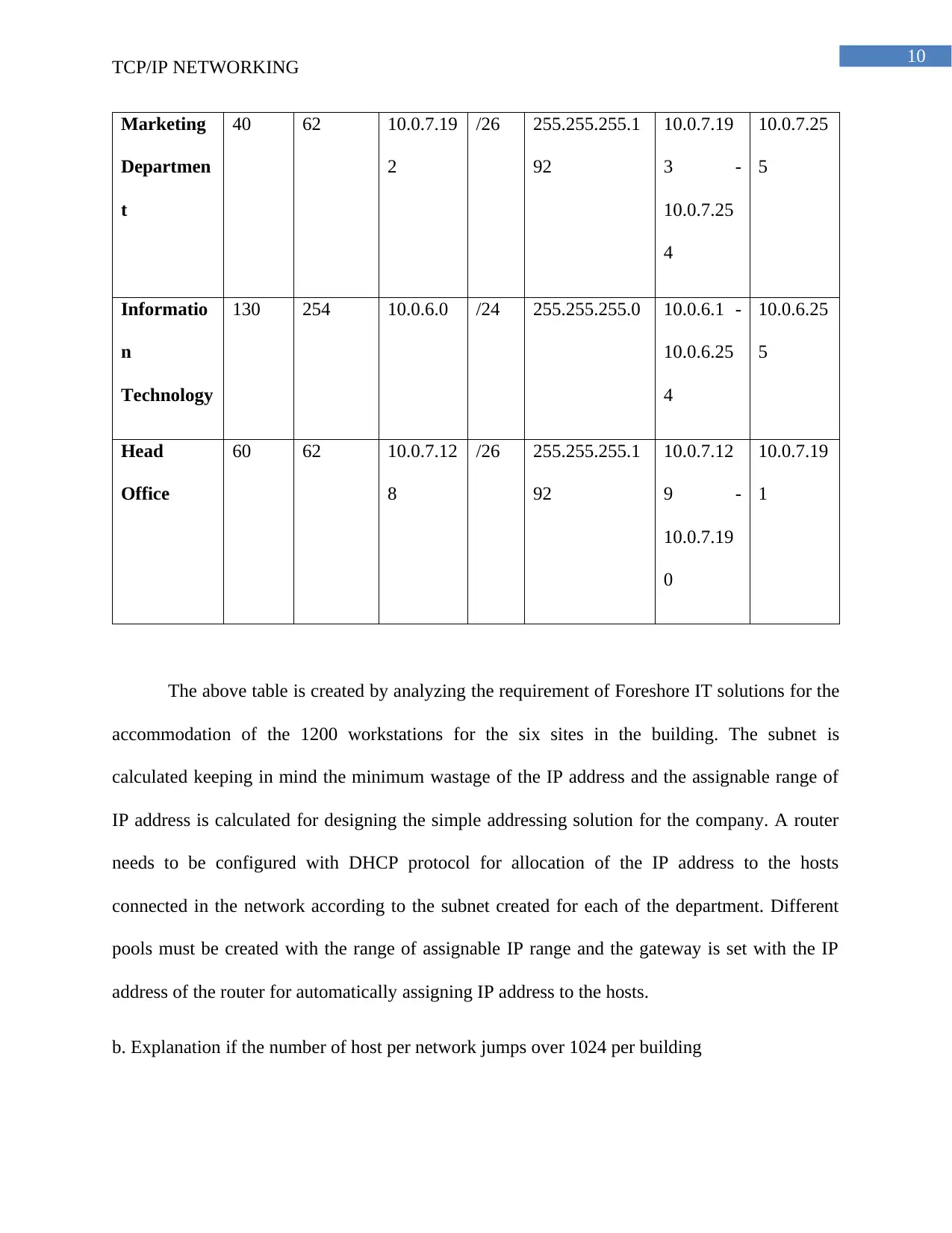
10
TCP/IP NETWORKING
Marketing
Departmen
t
40 62 10.0.7.19
2
/26 255.255.255.1
92
10.0.7.19
3 -
10.0.7.25
4
10.0.7.25
5
Informatio
n
Technology
130 254 10.0.6.0 /24 255.255.255.0 10.0.6.1 -
10.0.6.25
4
10.0.6.25
5
Head
Office
60 62 10.0.7.12
8
/26 255.255.255.1
92
10.0.7.12
9 -
10.0.7.19
0
10.0.7.19
1
The above table is created by analyzing the requirement of Foreshore IT solutions for the
accommodation of the 1200 workstations for the six sites in the building. The subnet is
calculated keeping in mind the minimum wastage of the IP address and the assignable range of
IP address is calculated for designing the simple addressing solution for the company. A router
needs to be configured with DHCP protocol for allocation of the IP address to the hosts
connected in the network according to the subnet created for each of the department. Different
pools must be created with the range of assignable IP range and the gateway is set with the IP
address of the router for automatically assigning IP address to the hosts.
b. Explanation if the number of host per network jumps over 1024 per building
TCP/IP NETWORKING
Marketing
Departmen
t
40 62 10.0.7.19
2
/26 255.255.255.1
92
10.0.7.19
3 -
10.0.7.25
4
10.0.7.25
5
Informatio
n
Technology
130 254 10.0.6.0 /24 255.255.255.0 10.0.6.1 -
10.0.6.25
4
10.0.6.25
5
Head
Office
60 62 10.0.7.12
8
/26 255.255.255.1
92
10.0.7.12
9 -
10.0.7.19
0
10.0.7.19
1
The above table is created by analyzing the requirement of Foreshore IT solutions for the
accommodation of the 1200 workstations for the six sites in the building. The subnet is
calculated keeping in mind the minimum wastage of the IP address and the assignable range of
IP address is calculated for designing the simple addressing solution for the company. A router
needs to be configured with DHCP protocol for allocation of the IP address to the hosts
connected in the network according to the subnet created for each of the department. Different
pools must be created with the range of assignable IP range and the gateway is set with the IP
address of the router for automatically assigning IP address to the hosts.
b. Explanation if the number of host per network jumps over 1024 per building

11
TCP/IP NETWORKING
If there is a sudden increase in the number of hosts in the network the network
configuration needs to be reconfigured without implementation of the extra network device in
the network. The subnet must be calculated and the router should be configured according to the
new subnet calculation for the accommodation of the new hosts in the network. The gateway
interface of the routers should be used for DHCP configuration and the range of the IP address
for each of the subnet. The multiple subnet is created for the isolation of each of the departments
and controlling the departments. The subnet mask is calculated with the application of the host
formula and the subnet mask needs to be re calculated if the host per building increases to 1024.
For the calculation of the new subnet mask VLSM and CIDR notation is used. For connecting
each of the department the central router is configured with VLAN configuration such that each
of the department is assigned with the range of IP address. It increases the security of the
network by isolating the hosts. The routers can also be configured with access control list for
blocking a range of Ip address to access the organizational resources.
Conclusion
The report concludes that with the development of the simple addressing solution for the
network designed for Foreshore IT solutions the effort of the network administrator can be
decreased. It helps in configuring the routers with the DHCP protocol according to the address
plan. Some extra number of address are kept in reserve for the accommodation of the
organizational growth. If case of sudden increase of the host to1204 for each of the department
the whole address plan needs to be reconfigured with the application of the new address plan.
TCP/IP NETWORKING
If there is a sudden increase in the number of hosts in the network the network
configuration needs to be reconfigured without implementation of the extra network device in
the network. The subnet must be calculated and the router should be configured according to the
new subnet calculation for the accommodation of the new hosts in the network. The gateway
interface of the routers should be used for DHCP configuration and the range of the IP address
for each of the subnet. The multiple subnet is created for the isolation of each of the departments
and controlling the departments. The subnet mask is calculated with the application of the host
formula and the subnet mask needs to be re calculated if the host per building increases to 1024.
For the calculation of the new subnet mask VLSM and CIDR notation is used. For connecting
each of the department the central router is configured with VLAN configuration such that each
of the department is assigned with the range of IP address. It increases the security of the
network by isolating the hosts. The routers can also be configured with access control list for
blocking a range of Ip address to access the organizational resources.
Conclusion
The report concludes that with the development of the simple addressing solution for the
network designed for Foreshore IT solutions the effort of the network administrator can be
decreased. It helps in configuring the routers with the DHCP protocol according to the address
plan. Some extra number of address are kept in reserve for the accommodation of the
organizational growth. If case of sudden increase of the host to1204 for each of the department
the whole address plan needs to be reconfigured with the application of the new address plan.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




