TCP/IP Networking Report: M2M Solution, Analysis and Implementation
VerifiedAdded on 2020/02/24
|16
|2617
|94
Report
AI Summary
This report details the implementation of a network architecture for an M2M solution across six buildings, utilizing the TCP/IP protocol. It begins with an introduction and a table of contents, followed by an analysis of addressing solutions, including subnet calculations for each building to accommodate approximately 1200 workstations. The report then explains communication protocols, emphasizing the importance of reliable data transmission and the use of network analyzers for performance monitoring and vulnerability assessment, particularly in the context of potential attacks. The report recommends specific network analyzer tools like Wireshark and the ZVA40 vector network analyzer, outlining their benefits, usability, associated costs, and maintenance. The conclusion summarizes the key findings, emphasizing the need for both hardware and software solutions to optimize the M2M network infrastructure and ensure efficient operation. The report includes references to cited sources.

Running Head: TCP/IP NETWORKING
TCP/IP NETWORKING
[Name of the student]
[Name of the University]
TCP/IP NETWORKING
[Name of the student]
[Name of the University]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1TCP/IP NETWORKING
Table of Contents
Introduction 2
Task 1.A. Addressing solution 2
Task 1. B. Explanation 8
Task 2. A. Communication protocol & Role of network analyzers 8
Task 2. B. Network analyzer tools 11
Benefits and Usability 11
Associated costs 12
Recommendation 13
Conclusion 13
References 14
Table of Contents
Introduction 2
Task 1.A. Addressing solution 2
Task 1. B. Explanation 8
Task 2. A. Communication protocol & Role of network analyzers 8
Task 2. B. Network analyzer tools 11
Benefits and Usability 11
Associated costs 12
Recommendation 13
Conclusion 13
References 14
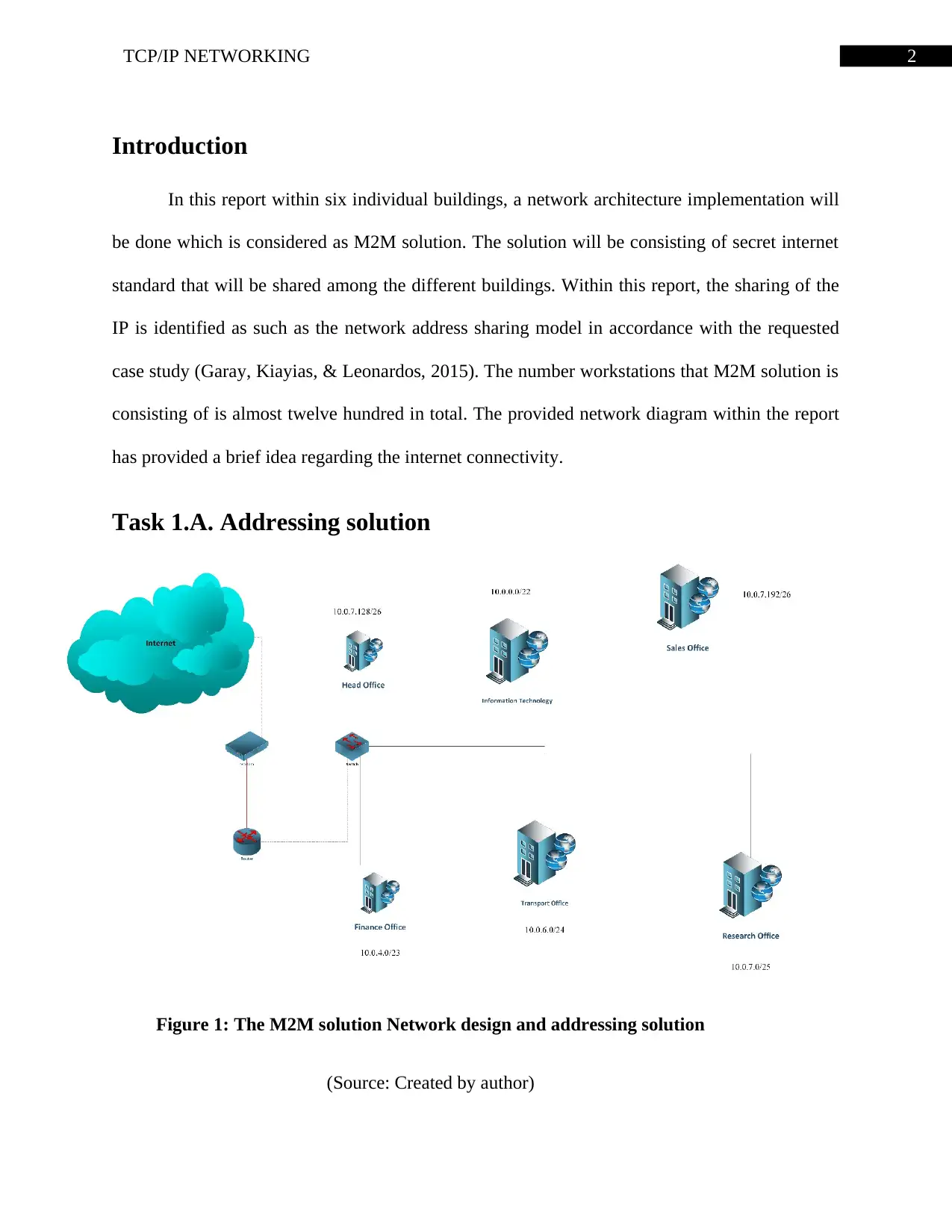
2TCP/IP NETWORKING
Introduction
In this report within six individual buildings, a network architecture implementation will
be done which is considered as M2M solution. The solution will be consisting of secret internet
standard that will be shared among the different buildings. Within this report, the sharing of the
IP is identified as such as the network address sharing model in accordance with the requested
case study (Garay, Kiayias, & Leonardos, 2015). The number workstations that M2M solution is
consisting of is almost twelve hundred in total. The provided network diagram within the report
has provided a brief idea regarding the internet connectivity.
Task 1.A. Addressing solution
Figure 1: The M2M solution Network design and addressing solution
(Source: Created by author)
Introduction
In this report within six individual buildings, a network architecture implementation will
be done which is considered as M2M solution. The solution will be consisting of secret internet
standard that will be shared among the different buildings. Within this report, the sharing of the
IP is identified as such as the network address sharing model in accordance with the requested
case study (Garay, Kiayias, & Leonardos, 2015). The number workstations that M2M solution is
consisting of is almost twelve hundred in total. The provided network diagram within the report
has provided a brief idea regarding the internet connectivity.
Task 1.A. Addressing solution
Figure 1: The M2M solution Network design and addressing solution
(Source: Created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
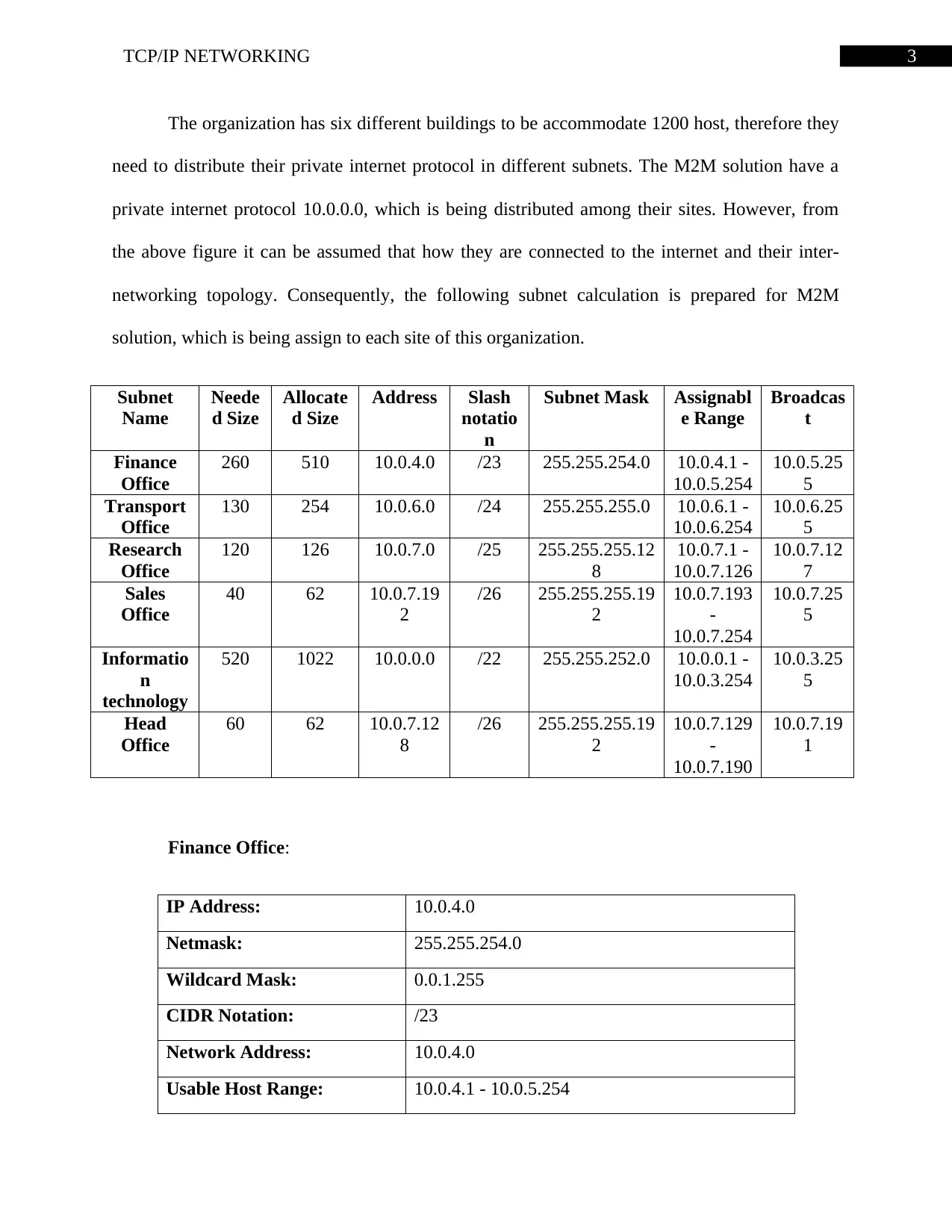
3TCP/IP NETWORKING
The organization has six different buildings to be accommodate 1200 host, therefore they
need to distribute their private internet protocol in different subnets. The M2M solution have a
private internet protocol 10.0.0.0, which is being distributed among their sites. However, from
the above figure it can be assumed that how they are connected to the internet and their inter-
networking topology. Consequently, the following subnet calculation is prepared for M2M
solution, which is being assign to each site of this organization.
Subnet
Name
Neede
d Size
Allocate
d Size
Address Slash
notatio
n
Subnet Mask Assignabl
e Range
Broadcas
t
Finance
Office
260 510 10.0.4.0 /23 255.255.254.0 10.0.4.1 -
10.0.5.254
10.0.5.25
5
Transport
Office
130 254 10.0.6.0 /24 255.255.255.0 10.0.6.1 -
10.0.6.254
10.0.6.25
5
Research
Office
120 126 10.0.7.0 /25 255.255.255.12
8
10.0.7.1 -
10.0.7.126
10.0.7.12
7
Sales
Office
40 62 10.0.7.19
2
/26 255.255.255.19
2
10.0.7.193
-
10.0.7.254
10.0.7.25
5
Informatio
n
technology
520 1022 10.0.0.0 /22 255.255.252.0 10.0.0.1 -
10.0.3.254
10.0.3.25
5
Head
Office
60 62 10.0.7.12
8
/26 255.255.255.19
2
10.0.7.129
-
10.0.7.190
10.0.7.19
1
Finance Office:
IP Address: 10.0.4.0
Netmask: 255.255.254.0
Wildcard Mask: 0.0.1.255
CIDR Notation: /23
Network Address: 10.0.4.0
Usable Host Range: 10.0.4.1 - 10.0.5.254
The organization has six different buildings to be accommodate 1200 host, therefore they
need to distribute their private internet protocol in different subnets. The M2M solution have a
private internet protocol 10.0.0.0, which is being distributed among their sites. However, from
the above figure it can be assumed that how they are connected to the internet and their inter-
networking topology. Consequently, the following subnet calculation is prepared for M2M
solution, which is being assign to each site of this organization.
Subnet
Name
Neede
d Size
Allocate
d Size
Address Slash
notatio
n
Subnet Mask Assignabl
e Range
Broadcas
t
Finance
Office
260 510 10.0.4.0 /23 255.255.254.0 10.0.4.1 -
10.0.5.254
10.0.5.25
5
Transport
Office
130 254 10.0.6.0 /24 255.255.255.0 10.0.6.1 -
10.0.6.254
10.0.6.25
5
Research
Office
120 126 10.0.7.0 /25 255.255.255.12
8
10.0.7.1 -
10.0.7.126
10.0.7.12
7
Sales
Office
40 62 10.0.7.19
2
/26 255.255.255.19
2
10.0.7.193
-
10.0.7.254
10.0.7.25
5
Informatio
n
technology
520 1022 10.0.0.0 /22 255.255.252.0 10.0.0.1 -
10.0.3.254
10.0.3.25
5
Head
Office
60 62 10.0.7.12
8
/26 255.255.255.19
2
10.0.7.129
-
10.0.7.190
10.0.7.19
1
Finance Office:
IP Address: 10.0.4.0
Netmask: 255.255.254.0
Wildcard Mask: 0.0.1.255
CIDR Notation: /23
Network Address: 10.0.4.0
Usable Host Range: 10.0.4.1 - 10.0.5.254
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4TCP/IP NETWORKING
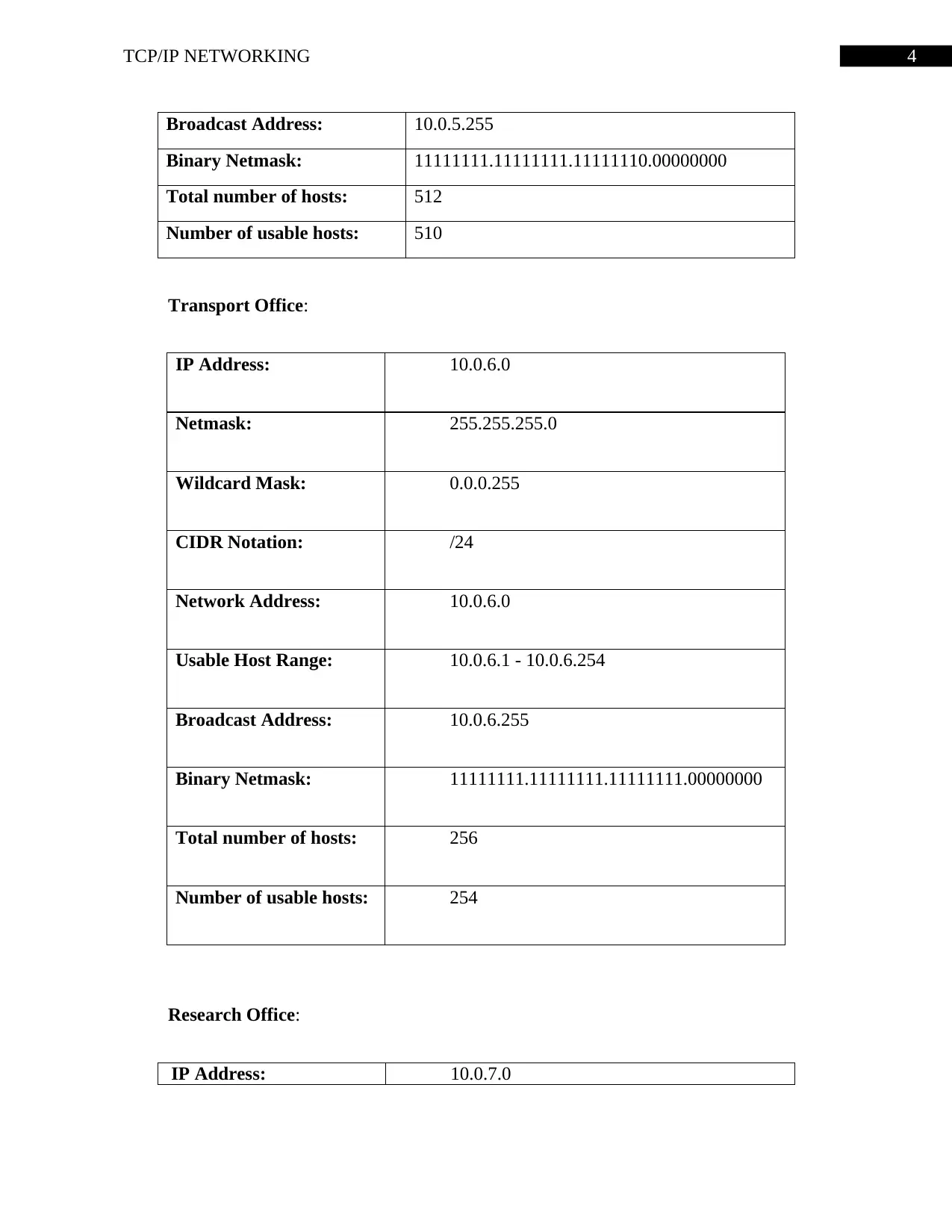
Broadcast Address: 10.0.5.255
Binary Netmask: 11111111.11111111.11111110.00000000
Total number of hosts: 512
Number of usable hosts: 510
Transport Office:
IP Address: 10.0.6.0
Netmask: 255.255.255.0
Wildcard Mask: 0.0.0.255
CIDR Notation: /24
Network Address: 10.0.6.0
Usable Host Range: 10.0.6.1 - 10.0.6.254
Broadcast Address: 10.0.6.255
Binary Netmask: 11111111.11111111.11111111.00000000
Total number of hosts: 256
Number of usable hosts: 254
Research Office:
IP Address: 10.0.7.0
Broadcast Address: 10.0.5.255
Binary Netmask: 11111111.11111111.11111110.00000000
Total number of hosts: 512
Number of usable hosts: 510
Transport Office:
IP Address: 10.0.6.0
Netmask: 255.255.255.0
Wildcard Mask: 0.0.0.255
CIDR Notation: /24
Network Address: 10.0.6.0
Usable Host Range: 10.0.6.1 - 10.0.6.254
Broadcast Address: 10.0.6.255
Binary Netmask: 11111111.11111111.11111111.00000000
Total number of hosts: 256
Number of usable hosts: 254
Research Office:
IP Address: 10.0.7.0
5TCP/IP NETWORKING
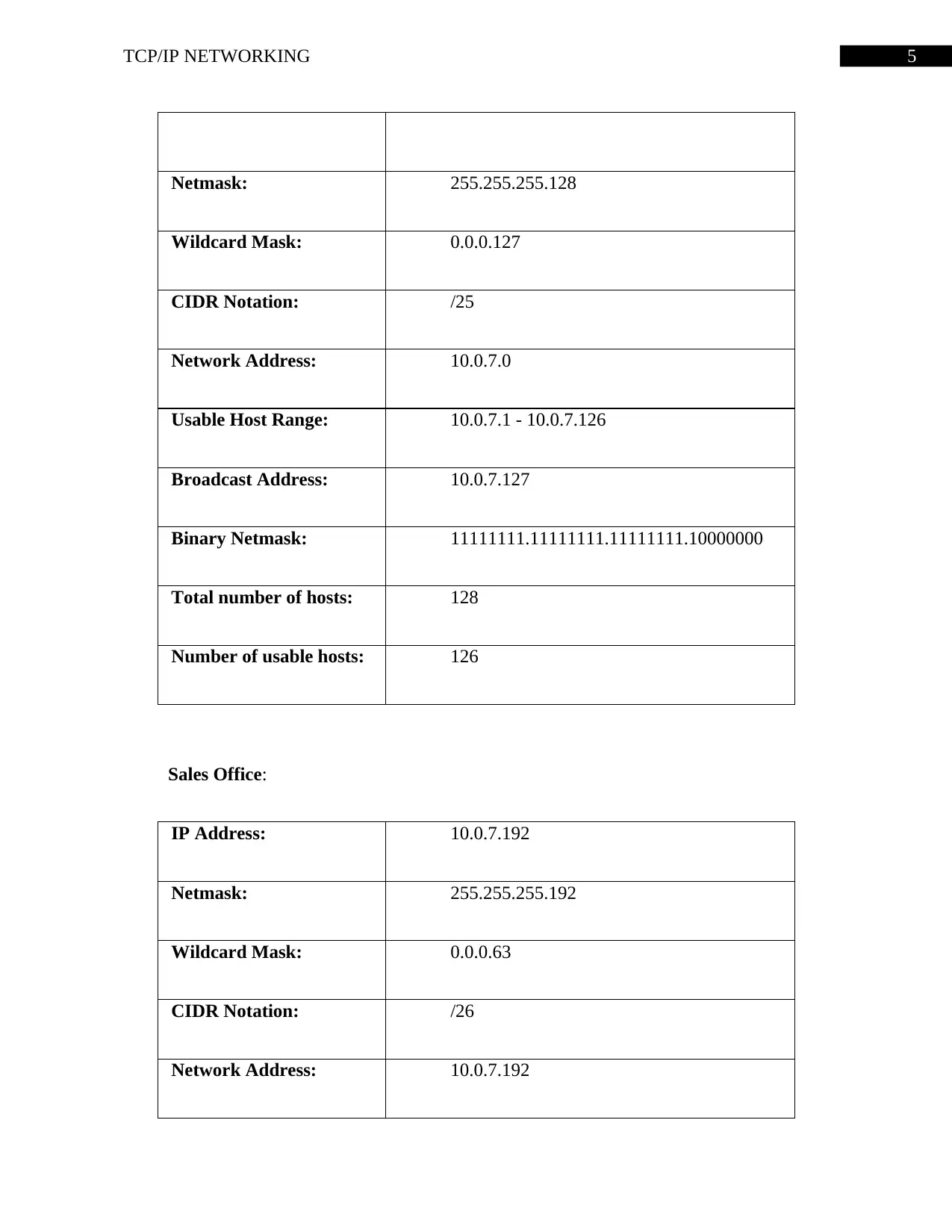
Netmask: 255.255.255.128
Wildcard Mask: 0.0.0.127
CIDR Notation: /25
Network Address: 10.0.7.0
Usable Host Range: 10.0.7.1 - 10.0.7.126
Broadcast Address: 10.0.7.127
Binary Netmask: 11111111.11111111.11111111.10000000
Total number of hosts: 128
Number of usable hosts: 126
Sales Office:
IP Address: 10.0.7.192
Netmask: 255.255.255.192
Wildcard Mask: 0.0.0.63
CIDR Notation: /26
Network Address: 10.0.7.192
Netmask: 255.255.255.128
Wildcard Mask: 0.0.0.127
CIDR Notation: /25
Network Address: 10.0.7.0
Usable Host Range: 10.0.7.1 - 10.0.7.126
Broadcast Address: 10.0.7.127
Binary Netmask: 11111111.11111111.11111111.10000000
Total number of hosts: 128
Number of usable hosts: 126
Sales Office:
IP Address: 10.0.7.192
Netmask: 255.255.255.192
Wildcard Mask: 0.0.0.63
CIDR Notation: /26
Network Address: 10.0.7.192
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6TCP/IP NETWORKING
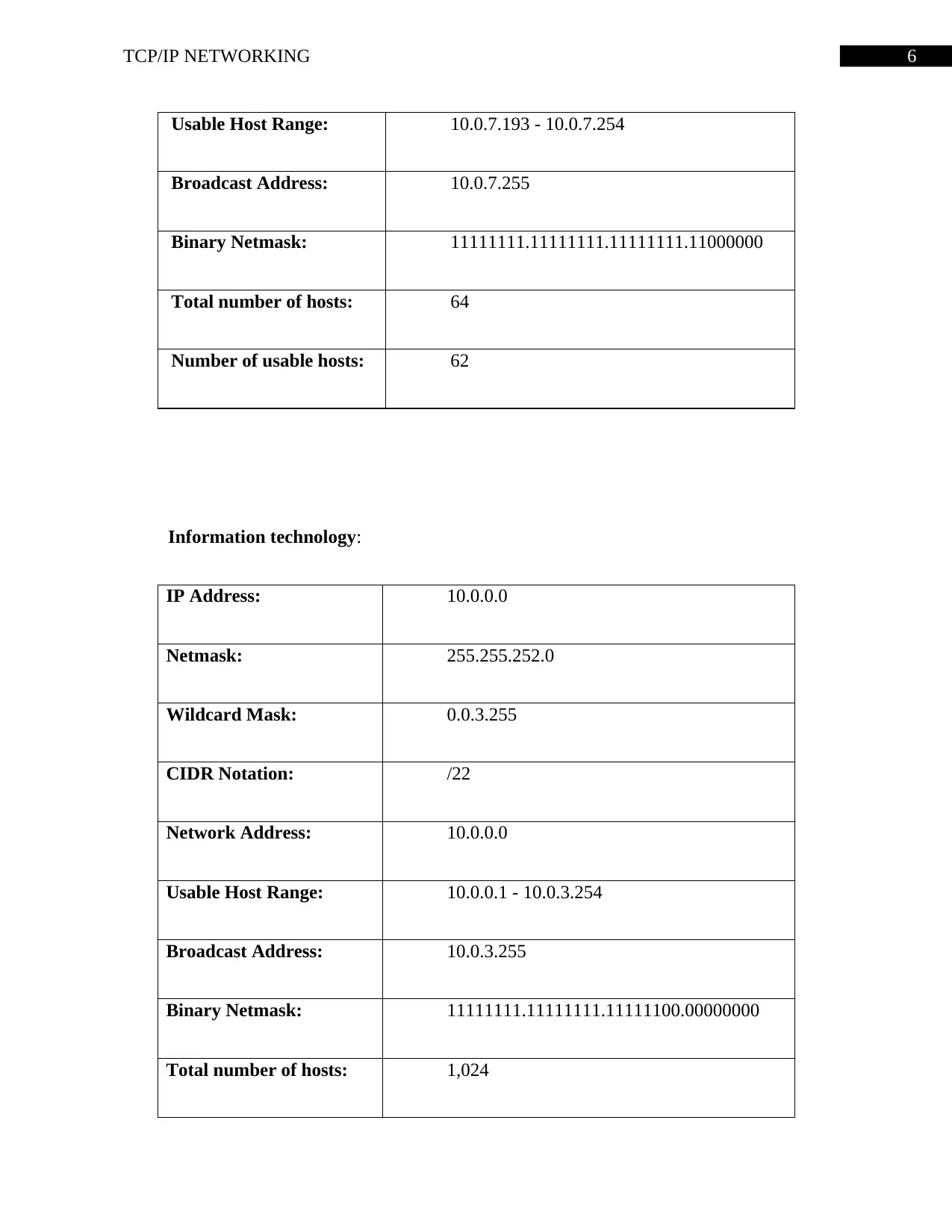
Usable Host Range: 10.0.7.193 - 10.0.7.254
Broadcast Address: 10.0.7.255
Binary Netmask: 11111111.11111111.11111111.11000000
Total number of hosts: 64
Number of usable hosts: 62
Information technology:
IP Address: 10.0.0.0
Netmask: 255.255.252.0
Wildcard Mask: 0.0.3.255
CIDR Notation: /22
Network Address: 10.0.0.0
Usable Host Range: 10.0.0.1 - 10.0.3.254
Broadcast Address: 10.0.3.255
Binary Netmask: 11111111.11111111.11111100.00000000
Total number of hosts: 1,024
Usable Host Range: 10.0.7.193 - 10.0.7.254
Broadcast Address: 10.0.7.255
Binary Netmask: 11111111.11111111.11111111.11000000
Total number of hosts: 64
Number of usable hosts: 62
Information technology:
IP Address: 10.0.0.0
Netmask: 255.255.252.0
Wildcard Mask: 0.0.3.255
CIDR Notation: /22
Network Address: 10.0.0.0
Usable Host Range: 10.0.0.1 - 10.0.3.254
Broadcast Address: 10.0.3.255
Binary Netmask: 11111111.11111111.11111100.00000000
Total number of hosts: 1,024
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7TCP/IP NETWORKING
Number of usable hosts: 1,022
Head Office:
IP Address: 10.0.7.128
Netmask: 255.255.255.192
Wildcard Mask: 0.0.0.63
CIDR Notation: /26
Network Address: 10.0.7.128
Usable Host Range: 10.0.7.129 - 10.0.7.190
Broadcast Address: 10.0.7.191
Binary Netmask: 11111111.11111111.11111111.11000000
Total number of hosts: 64
Number of usable hosts: 62
Number of usable hosts: 1,022
Head Office:
IP Address: 10.0.7.128
Netmask: 255.255.255.192
Wildcard Mask: 0.0.0.63
CIDR Notation: /26
Network Address: 10.0.7.128
Usable Host Range: 10.0.7.129 - 10.0.7.190
Broadcast Address: 10.0.7.191
Binary Netmask: 11111111.11111111.11111111.11000000
Total number of hosts: 64
Number of usable hosts: 62

8TCP/IP NETWORKING
Task 1. B. Explanation
The main challenge in accommodating 1,024 hosts in a site is broadcasting in this
network. A broadcasting is technique of sending data packet though all the host in a network, if
any network having any broadcasting issue than it might be causes a rollover. However, if any
network having more than 1,022 hosts in a network, where require hosts per site is 1,024 then it
also deal with wastages of internet protocol issue.
Task 2. A. Communication protocol & Role of network analyzers
Communication protocols are required to provide end to end reliable data transmission. A
commutation protocol can be define as a set of rule that responsible to provided secure and
reliable data transmission (Chaubey et al., 2015). The M2M solution has around 1200 has in their
six building. Consequently, they have to utilize suitable systems for network devices to
recognize and additionally make the association between each other. These protocols are
likewise in charge of arranging decides that can determine how the information acquired from
network devices and additionally sent over the system. Consequently, the communication
protocol component likewise valuable to improve the execution of the system by message
verification as well as data compression.
As per the M2M solution networking infrastructure, design directing conventions
additionally required distinguishing different switches in the system. The router is assignment
with a routing protocol for utilized as a part of the switches to deal with the pathway between
sources to destination (Garay, Kiayias & Leonardos, 2015). There are few well-known routings
protocols are BGP, EIGRP and also OSPF. Through, the M2M solution it can execute the OSPF
Task 1. B. Explanation
The main challenge in accommodating 1,024 hosts in a site is broadcasting in this
network. A broadcasting is technique of sending data packet though all the host in a network, if
any network having any broadcasting issue than it might be causes a rollover. However, if any
network having more than 1,022 hosts in a network, where require hosts per site is 1,024 then it
also deal with wastages of internet protocol issue.
Task 2. A. Communication protocol & Role of network analyzers
Communication protocols are required to provide end to end reliable data transmission. A
commutation protocol can be define as a set of rule that responsible to provided secure and
reliable data transmission (Chaubey et al., 2015). The M2M solution has around 1200 has in their
six building. Consequently, they have to utilize suitable systems for network devices to
recognize and additionally make the association between each other. These protocols are
likewise in charge of arranging decides that can determine how the information acquired from
network devices and additionally sent over the system. Consequently, the communication
protocol component likewise valuable to improve the execution of the system by message
verification as well as data compression.
As per the M2M solution networking infrastructure, design directing conventions
additionally required distinguishing different switches in the system. The router is assignment
with a routing protocol for utilized as a part of the switches to deal with the pathway between
sources to destination (Garay, Kiayias & Leonardos, 2015). There are few well-known routings
protocols are BGP, EIGRP and also OSPF. Through, the M2M solution it can execute the OSPF
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9TCP/IP NETWORKING
protocol for their association to manage private systems administration locales with a center
switch, as appeared in the above figure 1.
The network protocol analyzer can be an instrument or programming that measure the
system execution by some system parameters. Moreover, the M2M arrangement has presented
six distinct destinations that can be associated with the web, hence they need to utilize an
examination device to check vulnerability and performance as well (Namesh & Ramakrishnan,
2015).
Figure 2: ZVA40 vector network analyzer
(Source: Duchêne et al., 2017, pp-13)
The network analyzer programming likewise compresses crude information into
something that sounds good to a client, who is insufficient shrewd with network administration
protocol for their association to manage private systems administration locales with a center
switch, as appeared in the above figure 1.
The network protocol analyzer can be an instrument or programming that measure the
system execution by some system parameters. Moreover, the M2M arrangement has presented
six distinct destinations that can be associated with the web, hence they need to utilize an
examination device to check vulnerability and performance as well (Namesh & Ramakrishnan,
2015).
Figure 2: ZVA40 vector network analyzer
(Source: Duchêne et al., 2017, pp-13)
The network analyzer programming likewise compresses crude information into
something that sounds good to a client, who is insufficient shrewd with network administration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10TCP/IP NETWORKING
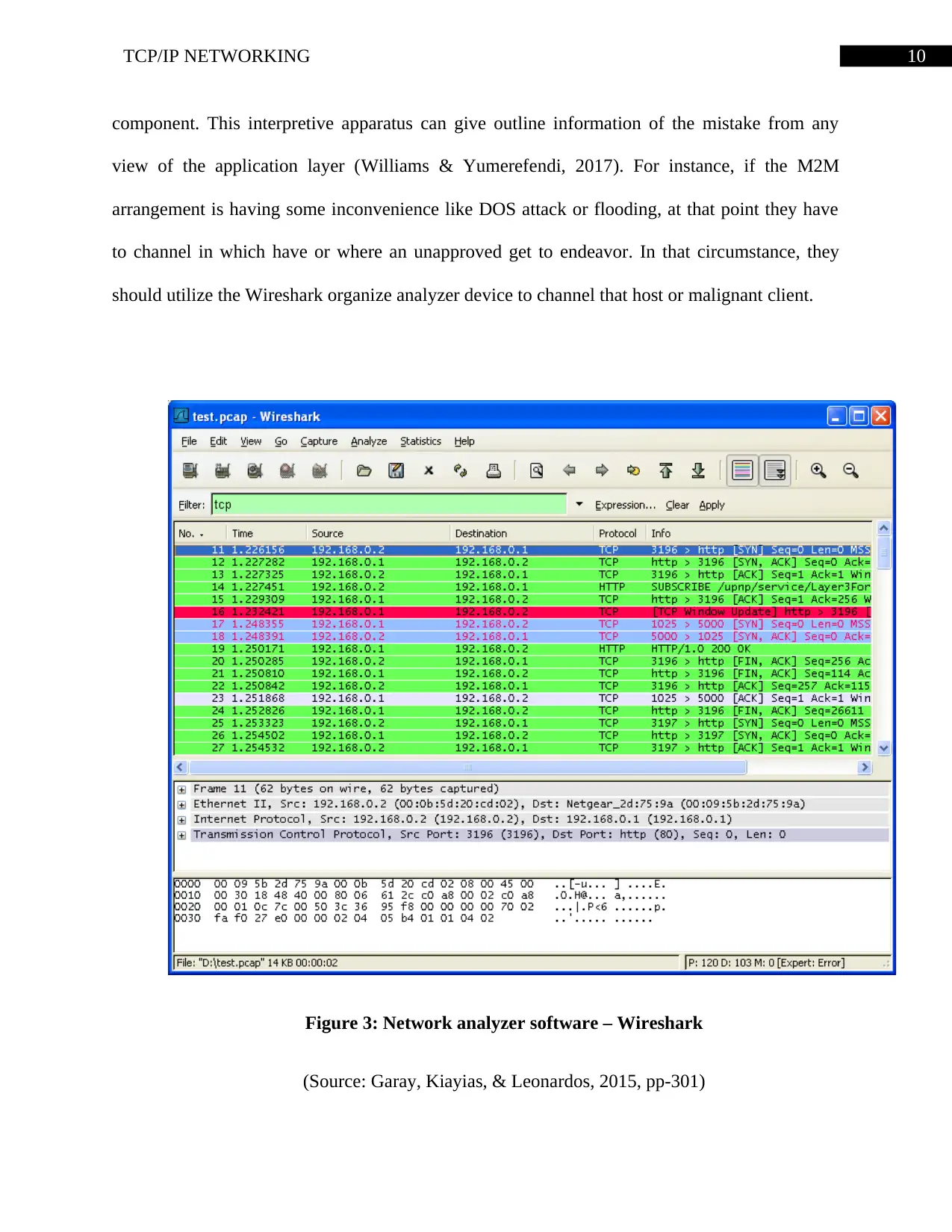
component. This interpretive apparatus can give outline information of the mistake from any
view of the application layer (Williams & Yumerefendi, 2017). For instance, if the M2M
arrangement is having some inconvenience like DOS attack or flooding, at that point they have
to channel in which have or where an unapproved get to endeavor. In that circumstance, they
should utilize the Wireshark organize analyzer device to channel that host or malignant client.
Figure 3: Network analyzer software – Wireshark
(Source: Garay, Kiayias, & Leonardos, 2015, pp-301)
component. This interpretive apparatus can give outline information of the mistake from any
view of the application layer (Williams & Yumerefendi, 2017). For instance, if the M2M
arrangement is having some inconvenience like DOS attack or flooding, at that point they have
to channel in which have or where an unapproved get to endeavor. In that circumstance, they
should utilize the Wireshark organize analyzer device to channel that host or malignant client.
Figure 3: Network analyzer software – Wireshark
(Source: Garay, Kiayias, & Leonardos, 2015, pp-301)

11TCP/IP NETWORKING
Task 2. B. Network analyzer tools
Benefits and Usability
The network analysers are used to analyse traffic all over the network of M2M solution.
There are two type of network analysers are available in the market such as a hardware device to
tracer the bandwidth, signal strength etc. as well as a software for data packets analysis.
Therefore, according to their category they have different specific functionality and features as
well (Segata et al., 2014). Consequently, a hardware device is ZVA40 vector network analyser
and Wireshark packet capturing tool is required in M2M solution to check their functionality.
A network protocol analyser like Wireshark offers many advantages that make it
engaging for regular utilize in most of the organization. The Wireshark network traffic analyser
can be utilized more than one hundred of network protocol. It can store the captured transmitted
data for offline or live examination, where the organization can filter out vital information
(Chaubey et al., 2015). It has been expected that Wireshark is very much compatible with Linux,
NetBSD, Windows, Solaris, and FreeBSD.
The hardware tool is being utilized in M2M solution is vector network analyser ZVA40
can measure the network traffic by watching a few parameters. For example, an order is a
measure of how well a coupler can isolate signals moving the diverse way (Burns et al., 2016).
Therefore, VAN is use to test the following component of M2M solution network infrastructure
Task 2. B. Network analyzer tools
Benefits and Usability
The network analysers are used to analyse traffic all over the network of M2M solution.
There are two type of network analysers are available in the market such as a hardware device to
tracer the bandwidth, signal strength etc. as well as a software for data packets analysis.
Therefore, according to their category they have different specific functionality and features as
well (Segata et al., 2014). Consequently, a hardware device is ZVA40 vector network analyser
and Wireshark packet capturing tool is required in M2M solution to check their functionality.
A network protocol analyser like Wireshark offers many advantages that make it
engaging for regular utilize in most of the organization. The Wireshark network traffic analyser
can be utilized more than one hundred of network protocol. It can store the captured transmitted
data for offline or live examination, where the organization can filter out vital information
(Chaubey et al., 2015). It has been expected that Wireshark is very much compatible with Linux,
NetBSD, Windows, Solaris, and FreeBSD.
The hardware tool is being utilized in M2M solution is vector network analyser ZVA40
can measure the network traffic by watching a few parameters. For example, an order is a
measure of how well a coupler can isolate signals moving the diverse way (Burns et al., 2016).
Therefore, VAN is use to test the following component of M2M solution network infrastructure
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





