TCP/IP Networking Report: Addressing, Protocols, and Analysis Tools
VerifiedAdded on 2020/02/24
|13
|2383
|426
Report
AI Summary
This report presents a comprehensive analysis of TCP/IP networking, beginning with the design of a simple addressing solution using a mesh topology and VLSM for efficient IP allocation across six office buildings. The report details the IP addressing scheme for each office, including subnet masks, usable IP ranges, and CIDR notations. Furthermore, it delves into the explanation of network protocols and compares communication networks, emphasizing the role of network analyzers in traffic analysis, network discovery, and troubleshooting. The report evaluates currently available network analyzer tools, focusing on the OptiView Protocol Expert, discussing its benefits, associated costs, and ease of usability. It also provides a cost analysis and recommends the OptiView Protocol Expert for its efficiency and ease of use. The report concludes by recommending the implementation of the OptiView Protocol Expert to enhance the network solution's efficiency and reduce errors, along with the selection of the expert version to support future wireless network additions. The report also includes a detailed bibliography of relevant sources.

Running head: TCP/IP NETWORKING
TCP/IP Networking
Name of the Student
Name of the University
Author’s Note
TCP/IP Networking
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
TCP/IP NETWORKING
Table of Contents
TASK 1................................................................................................................................2
a. Design of the simple addressing solution....................................................................2
b. Explanation of the design............................................................................................6
TASK 2................................................................................................................................6
a. Explanation of the protocol and comparing communication network and role of
network analyzer..........................................................................................................................6
b. Analysis of currently available network analyzer tools...............................................7
i. Benefits, associated costs, Ease of usability.............................................................7
ii. Recommendation.....................................................................................................9
Bibliography......................................................................................................................10
TCP/IP NETWORKING
Table of Contents
TASK 1................................................................................................................................2
a. Design of the simple addressing solution....................................................................2
b. Explanation of the design............................................................................................6
TASK 2................................................................................................................................6
a. Explanation of the protocol and comparing communication network and role of
network analyzer..........................................................................................................................6
b. Analysis of currently available network analyzer tools...............................................7
i. Benefits, associated costs, Ease of usability.............................................................7
ii. Recommendation.....................................................................................................9
Bibliography......................................................................................................................10
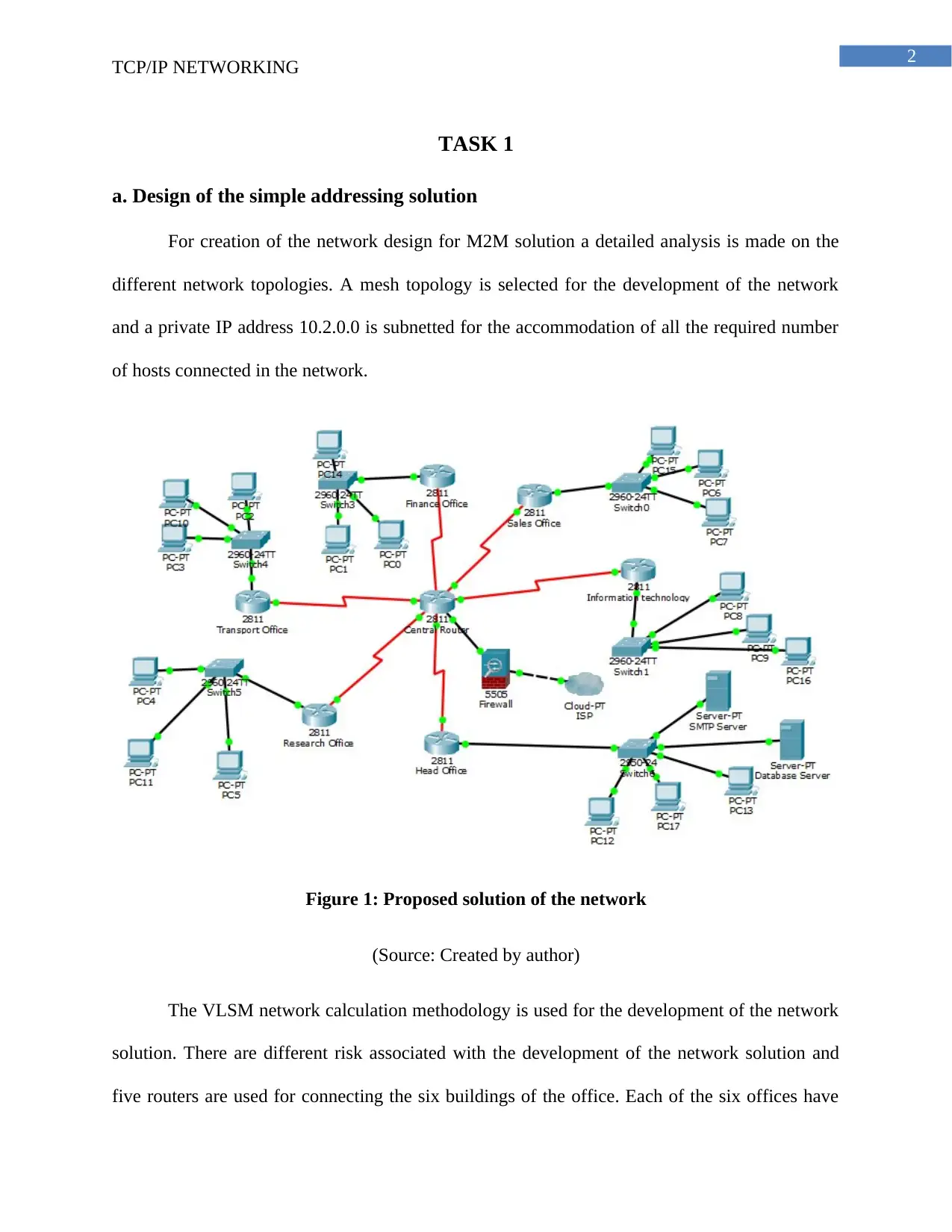
2
TCP/IP NETWORKING
TASK 1
a. Design of the simple addressing solution
For creation of the network design for M2M solution a detailed analysis is made on the
different network topologies. A mesh topology is selected for the development of the network
and a private IP address 10.2.0.0 is subnetted for the accommodation of all the required number
of hosts connected in the network.
Figure 1: Proposed solution of the network
(Source: Created by author)
The VLSM network calculation methodology is used for the development of the network
solution. There are different risk associated with the development of the network solution and
five routers are used for connecting the six buildings of the office. Each of the six offices have
TCP/IP NETWORKING
TASK 1
a. Design of the simple addressing solution
For creation of the network design for M2M solution a detailed analysis is made on the
different network topologies. A mesh topology is selected for the development of the network
and a private IP address 10.2.0.0 is subnetted for the accommodation of all the required number
of hosts connected in the network.
Figure 1: Proposed solution of the network
(Source: Created by author)
The VLSM network calculation methodology is used for the development of the network
solution. There are different risk associated with the development of the network solution and
five routers are used for connecting the six buildings of the office. Each of the six offices have
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
TCP/IP NETWORKING
separate router and a switch is connected with the router for interconnecting the nodes and the
workstations installed at the office. The router is required to be configured with proper
networking protocols for communicating with the hosts connected with the other router in the
network.
Finance Office:
IP Address: 10.2.1.1
Network Address: 10.2.1.1
Usable Host IP Range: 10.2.1.1 - 10.2.1.254
Broadcast Address: 10.2.1.255
Total Number of
Hosts:
512
A number of Usable
Hosts:
510
Subnet Mask: 255.255.254.0
Wildcard Mask: 0.0.1.255
Binary Subnet Mask: 11111111.11111111.1111111 0.00000000
IP Class: A
CIDR Notation: /23
IP Type: Private
Transport Office:
IP Address: 10.2.2.0
Network Address: 10.2.2.0
Usable Host IP Range: 10.2.2.1 - 10.2.2.254
Broadcast Address: 10.2.2.255
Total Number of
Hosts:
256
A number of Usable
Hosts:
254
Subnet Mask: 255.255.255.0
Wildcard Mask: 0.0.0.255
Binary Subnet Mask: 11111111.11111111.11111111.00000000
TCP/IP NETWORKING
separate router and a switch is connected with the router for interconnecting the nodes and the
workstations installed at the office. The router is required to be configured with proper
networking protocols for communicating with the hosts connected with the other router in the
network.
Finance Office:
IP Address: 10.2.1.1
Network Address: 10.2.1.1
Usable Host IP Range: 10.2.1.1 - 10.2.1.254
Broadcast Address: 10.2.1.255
Total Number of
Hosts:
512
A number of Usable
Hosts:
510
Subnet Mask: 255.255.254.0
Wildcard Mask: 0.0.1.255
Binary Subnet Mask: 11111111.11111111.1111111 0.00000000
IP Class: A
CIDR Notation: /23
IP Type: Private
Transport Office:
IP Address: 10.2.2.0
Network Address: 10.2.2.0
Usable Host IP Range: 10.2.2.1 - 10.2.2.254
Broadcast Address: 10.2.2.255
Total Number of
Hosts:
256
A number of Usable
Hosts:
254
Subnet Mask: 255.255.255.0
Wildcard Mask: 0.0.0.255
Binary Subnet Mask: 11111111.11111111.11111111.00000000
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
TCP/IP NETWORKING
IP Class: C
CIDR Notation: /24
IP Type: Private
Research Office:
IP Address: 10.2.3.0
Network Address: 10.2.3.0
Usable Host IP Range: 10.2.3.1 - 10.2.3.126
Broadcast Address: 10.2.3.127
Total Number of
Hosts:
128
A number of Usable
Hosts:
126
Subnet Mask: 255.255.255.128
Wildcard Mask: 0.0.0.127
Binary Subnet Mask: 11111111.11111111.11111111.10000000
IP Class: C
CIDR Notation: /25
IP Type: Private
Sales Office:
IP Address: 10.2.3.128
Network Address: 10.2.3.128
Usable Host IP Range: 10.2.3.129 - 10.2.3.190
Broadcast Address: 10.2.3.191
Total Number of Hosts: 64
A number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
TCP/IP NETWORKING
IP Class: C
CIDR Notation: /24
IP Type: Private
Research Office:
IP Address: 10.2.3.0
Network Address: 10.2.3.0
Usable Host IP Range: 10.2.3.1 - 10.2.3.126
Broadcast Address: 10.2.3.127
Total Number of
Hosts:
128
A number of Usable
Hosts:
126
Subnet Mask: 255.255.255.128
Wildcard Mask: 0.0.0.127
Binary Subnet Mask: 11111111.11111111.11111111.10000000
IP Class: C
CIDR Notation: /25
IP Type: Private
Sales Office:
IP Address: 10.2.3.128
Network Address: 10.2.3.128
Usable Host IP Range: 10.2.3.129 - 10.2.3.190
Broadcast Address: 10.2.3.191
Total Number of Hosts: 64
A number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private

5
TCP/IP NETWORKING
TCP/IP NETWORKING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
TCP/IP NETWORKING
Information technology:
IP Address: 10.2.3.192
Network Address: 10.2.3.192
Usable Host IP Range: 10.2.0.1 - 10.2.3.254
Broadcast Address: 10.2.3.255
Total Number of Hosts: 1,024
A number of Usable Hosts: 1,022
Subnet Mask: 255.255.252.0
Wildcard Mask: 0.0.3.255
Binary Subnet Mask: 11111111.11111111.11111100.00000000
IP Class: B
CIDR Notation: /22
IP Type: Private
Head Office:
IP Address: 10.2.4.0
Network Address: 10.2.4.0
Usable Host IP Range: 10.2.4.1 - 10.2.4.62
Broadcast Address: 10.2.4.63
Total Number of Hosts: 64
A number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
A firewall is installed in the network for restricting the intruders to gain the access of the
network resources. Two servers are installed in the network for increasing the efficiency of the
network communication and reduce the risk of virus and Trojan from external emails. The server
is configured with SMTP protocol and a database server is installed for increasing the efficiency
of the network and store the useful information for management of the network solution. The
TCP/IP NETWORKING
Information technology:
IP Address: 10.2.3.192
Network Address: 10.2.3.192
Usable Host IP Range: 10.2.0.1 - 10.2.3.254
Broadcast Address: 10.2.3.255
Total Number of Hosts: 1,024
A number of Usable Hosts: 1,022
Subnet Mask: 255.255.252.0
Wildcard Mask: 0.0.3.255
Binary Subnet Mask: 11111111.11111111.11111100.00000000
IP Class: B
CIDR Notation: /22
IP Type: Private
Head Office:
IP Address: 10.2.4.0
Network Address: 10.2.4.0
Usable Host IP Range: 10.2.4.1 - 10.2.4.62
Broadcast Address: 10.2.4.63
Total Number of Hosts: 64
A number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
A firewall is installed in the network for restricting the intruders to gain the access of the
network resources. Two servers are installed in the network for increasing the efficiency of the
network communication and reduce the risk of virus and Trojan from external emails. The server
is configured with SMTP protocol and a database server is installed for increasing the efficiency
of the network and store the useful information for management of the network solution. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
TCP/IP NETWORKING
hosts are required to be assigned with a static IP address within the range for communicating
with the other hosts.
b. Explanation of the design
If there is a sudden increase in the number of hosts in the network per subnet the network
administrator needs to recalculate the subnets or add new routers for accommodating the hosts.
The addition of a new router in the network would be helpful because it would not disturb the
current network solution and help to accommodate the hosts without affect the current network
solution. For accommodation of the host without adding extra cost the addressing scheme is
required to be changes and the subnet mask is required to be recalculated. The calculation of the
new subnet mask and the assignable range of the IP address is listed below.
Head Office 10.0.20.0 /22 255.255.252.0 10.0.20.1 - 10.0.23.254
Finance Office 10.0.0.0 /22 255.255.252.0 10.0.0.1 - 10.0.3.254
Transport Office 10.0.4.0 /22 255.255.252.0 10.0.4.1 - 10.0.7.254
Research Office 10.0.8.0 /22 255.255.252.0 10.0.8.1 - 10.0.11.254
Sales Office 10.0.12.0 /22 255.255.252.0 10.0.12.1 - 10.0.15.254
Information Technology 10.0.16.0 /22 255.255.252.0 10.0.16.1 - 10.0.19.254
TASK 2
a. Explanation of the protocol and comparing communication network and role of
network analyzer
There are different network protocol analyzer available and can be used for identification
of the flow of the data in the network. The hosts connected in the network is required to be
TCP/IP NETWORKING
hosts are required to be assigned with a static IP address within the range for communicating
with the other hosts.
b. Explanation of the design
If there is a sudden increase in the number of hosts in the network per subnet the network
administrator needs to recalculate the subnets or add new routers for accommodating the hosts.
The addition of a new router in the network would be helpful because it would not disturb the
current network solution and help to accommodate the hosts without affect the current network
solution. For accommodation of the host without adding extra cost the addressing scheme is
required to be changes and the subnet mask is required to be recalculated. The calculation of the
new subnet mask and the assignable range of the IP address is listed below.
Head Office 10.0.20.0 /22 255.255.252.0 10.0.20.1 - 10.0.23.254
Finance Office 10.0.0.0 /22 255.255.252.0 10.0.0.1 - 10.0.3.254
Transport Office 10.0.4.0 /22 255.255.252.0 10.0.4.1 - 10.0.7.254
Research Office 10.0.8.0 /22 255.255.252.0 10.0.8.1 - 10.0.11.254
Sales Office 10.0.12.0 /22 255.255.252.0 10.0.12.1 - 10.0.15.254
Information Technology 10.0.16.0 /22 255.255.252.0 10.0.16.1 - 10.0.19.254
TASK 2
a. Explanation of the protocol and comparing communication network and role of
network analyzer
There are different network protocol analyzer available and can be used for identification
of the flow of the data in the network. The hosts connected in the network is required to be

8
TCP/IP NETWORKING
analyzed and it can also be used for network discovery and troubleshooting the network
(Severance, 2013). The loss of data, timeouts and retries made in the network is required to be
controlled for increasing the efficiency in the network and the loss of the data packets in the
network is also required to be managed for minimizing the congestion and avoiding generation
of extra packets in the network.
For the preparation of the network design for M2M solution a private address 10.2.0.0 is
used and implementation of the Netasyst Network Analyzer can help in analysis of the traffic in
the network. There are two version of the network protocol analyzer such as standard and expert
and each of the version have three option that can be choosen according to the requirement of the
network. The price of the product varies according to the options selected. There are different
software that can also be used for analysis of the traffic such as wireshark, nmap, etc. and these
are available free of cost (Kulkarni & Agrawal, 2014). The network protocol analyzer are
installed for gathering proof from the network in case of an attack and it can also be used for
finding errors and flaws in the system and secure the vulnerable point for increasing the
efficiency of the network. The configuration of the router can and the mac address can also be
gathered and documented for handling the emergency condition in the network.
b. Analysis of currently available network analyzer tools
i. Benefits, associated costs, Ease of usability
Benefits-
The implementation of the hardware protocol analyzer helps in analysis and monitoring
the current network infrastructure. The OptiView Protocol Expert is selected for implementation
in the proposed network solution because it have different options available and the price of the
TCP/IP NETWORKING
analyzed and it can also be used for network discovery and troubleshooting the network
(Severance, 2013). The loss of data, timeouts and retries made in the network is required to be
controlled for increasing the efficiency in the network and the loss of the data packets in the
network is also required to be managed for minimizing the congestion and avoiding generation
of extra packets in the network.
For the preparation of the network design for M2M solution a private address 10.2.0.0 is
used and implementation of the Netasyst Network Analyzer can help in analysis of the traffic in
the network. There are two version of the network protocol analyzer such as standard and expert
and each of the version have three option that can be choosen according to the requirement of the
network. The price of the product varies according to the options selected. There are different
software that can also be used for analysis of the traffic such as wireshark, nmap, etc. and these
are available free of cost (Kulkarni & Agrawal, 2014). The network protocol analyzer are
installed for gathering proof from the network in case of an attack and it can also be used for
finding errors and flaws in the system and secure the vulnerable point for increasing the
efficiency of the network. The configuration of the router can and the mac address can also be
gathered and documented for handling the emergency condition in the network.
b. Analysis of currently available network analyzer tools
i. Benefits, associated costs, Ease of usability
Benefits-
The implementation of the hardware protocol analyzer helps in analysis and monitoring
the current network infrastructure. The OptiView Protocol Expert is selected for implementation
in the proposed network solution because it have different options available and the price of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
TCP/IP NETWORKING
solution is reasonable. The packets captured using the OptiView Protocol Expert can be decoded
and the traffic in the network can be monitored at a real time. Alarm can be set in different stages
of the analysis such a notification can be triggered if any abnormality is noticed in the current
framework of the network. The OptiView Protocol Expert have the option to decode 250
protocols or more. Moreover it have the support for VoIP and the graphical user interface can be
easily used for analysis of the current status of the network. The error statistics and network
details can be stored it can run in advanced discovery mode to find the device connected in the
network.
Associated Cost-
OptiView Protocol Expert
SL
No.
Product Cost Man
Power
1 OptiView™
Series III
Integrated Network Analyzer
$ $3195 to
$3500
6
2 NMap Free 6
Total $ 3500 12
Cost of OptiView Protocol Expert Installation & Maintenance
SL No. Expertise Cost
1 Network Administration $500.00
2 Network Installation $550.00
3 Network Device Monitor $280.00
4 Network Monitor $300.00
5 Administrator $600.00
6 Maintenance Staff $120.00
Total $2350.00
Cost of Wireshark Maintenance
SL No. Expertise Cost
1 Network Administration Build Finance $170.00
2 Network Administration Build Transport $170.00
3 Network Administration Build Research $170.00
TCP/IP NETWORKING
solution is reasonable. The packets captured using the OptiView Protocol Expert can be decoded
and the traffic in the network can be monitored at a real time. Alarm can be set in different stages
of the analysis such a notification can be triggered if any abnormality is noticed in the current
framework of the network. The OptiView Protocol Expert have the option to decode 250
protocols or more. Moreover it have the support for VoIP and the graphical user interface can be
easily used for analysis of the current status of the network. The error statistics and network
details can be stored it can run in advanced discovery mode to find the device connected in the
network.
Associated Cost-
OptiView Protocol Expert
SL
No.
Product Cost Man
Power
1 OptiView™
Series III
Integrated Network Analyzer
$ $3195 to
$3500
6
2 NMap Free 6
Total $ 3500 12
Cost of OptiView Protocol Expert Installation & Maintenance
SL No. Expertise Cost
1 Network Administration $500.00
2 Network Installation $550.00
3 Network Device Monitor $280.00
4 Network Monitor $300.00
5 Administrator $600.00
6 Maintenance Staff $120.00
Total $2350.00
Cost of Wireshark Maintenance
SL No. Expertise Cost
1 Network Administration Build Finance $170.00
2 Network Administration Build Transport $170.00
3 Network Administration Build Research $170.00
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
TCP/IP NETWORKING
4 Network Administration Build Sales $170.00
5 Network Administration Build Information $170.00
6 Network Administration Build Head $170.00
Total $1020.00
Grand Total Cost $6870.00
Ease of usability-
The GUI of OptiView Protocol Expert is simple and it provides visibility in the network
and thus makes the network clear. It can also be used for managing and validating the changes in
the network framework and solve the performance issues in the network. The traffic can be
analyzed with the click of a button and helps the network administrator to monitor the network at
a real time. The statistics of the device connected in the network can also be fetched on a click
and helps in analysis of the VLAN and switch route connected in the network. An account is
created for the network administrator for
ii. Recommendation
It is recommended that with the six offices are required to be interconnected for
communicating with each other. Different subnets is required to be created for different network
and each of the communication is required to be performed via the network firewall installed in
the network. It is recommended that the use of OptiView Protocol Expert would increase the
efficiency of the network solution and reduce the error in the network. It have less maintenance
cost and easy to use by the network administrator. The expert version of OptiView Protocol
Expert is required to be selected for getting all the support and manage the wireless network that
can be added in future for managing the wireless device connected in the network.
TCP/IP NETWORKING
4 Network Administration Build Sales $170.00
5 Network Administration Build Information $170.00
6 Network Administration Build Head $170.00
Total $1020.00
Grand Total Cost $6870.00
Ease of usability-
The GUI of OptiView Protocol Expert is simple and it provides visibility in the network
and thus makes the network clear. It can also be used for managing and validating the changes in
the network framework and solve the performance issues in the network. The traffic can be
analyzed with the click of a button and helps the network administrator to monitor the network at
a real time. The statistics of the device connected in the network can also be fetched on a click
and helps in analysis of the VLAN and switch route connected in the network. An account is
created for the network administrator for
ii. Recommendation
It is recommended that with the six offices are required to be interconnected for
communicating with each other. Different subnets is required to be created for different network
and each of the communication is required to be performed via the network firewall installed in
the network. It is recommended that the use of OptiView Protocol Expert would increase the
efficiency of the network solution and reduce the error in the network. It have less maintenance
cost and easy to use by the network administrator. The expert version of OptiView Protocol
Expert is required to be selected for getting all the support and manage the wireless network that
can be added in future for managing the wireless device connected in the network.

11
TCP/IP NETWORKING
Bibliography
Alexander, G., & Crandall, J. R. (2015, April). Off-path round trip time measurement via TCP/IP
side channels. In Computer Communications (INFOCOM), 2015 IEEE Conference on
(pp. 1589-1597). IEEE.
Bauer, G., Bawej, T., Behrens, U., Branson, J., Chaze, O., Cittolin, S., ... & Dupont, A. (2014).
10 Gbps TCP/IP streams from the FPGA for high energy physics. In Journal of Physics:
Conference Series (Vol. 513, No. 1, p. 012042). IOP Publishing.
Clavel, F., Savary, E., Angays, P., & Vieux-Melchior, A. (2015). Integration of a new standard:
A network simulator of IEC 61850 architectures for electrical substations. IEEE Industry
Applications Magazine, 21(1), 41-48.
Goralski, W. (2017). The Illustrated network: How TCP/IP works in a modern network. Morgan
Kaufmann.
Kulkarni, S., & Agrawal, P. (2014). Introduction. In Analysis of TCP Performance in Data
Center Networks (pp. 1-15). Springer New York.
Patinge, S., Suryawanshi, Y., & Kakde, S. (2013, December). Design of ARM based data
acquisition & control using GSM & TCP/IP network. In Computational Intelligence and
Computing Research (ICCIC), 2013 IEEE International Conference on (pp. 1-4). IEEE.
Severance, C. (2013). Van Jacobson: content-centric networking. Computer, 46(1), 11-13.
Shang, W., Yu, Y., Droms, R., & Zhang, L. (2016). Challenges in IoT networking via TCP/IP
architecture. NDN Project, Tech. Rep. NDN-0038.
TCP/IP NETWORKING
Bibliography
Alexander, G., & Crandall, J. R. (2015, April). Off-path round trip time measurement via TCP/IP
side channels. In Computer Communications (INFOCOM), 2015 IEEE Conference on
(pp. 1589-1597). IEEE.
Bauer, G., Bawej, T., Behrens, U., Branson, J., Chaze, O., Cittolin, S., ... & Dupont, A. (2014).
10 Gbps TCP/IP streams from the FPGA for high energy physics. In Journal of Physics:
Conference Series (Vol. 513, No. 1, p. 012042). IOP Publishing.
Clavel, F., Savary, E., Angays, P., & Vieux-Melchior, A. (2015). Integration of a new standard:
A network simulator of IEC 61850 architectures for electrical substations. IEEE Industry
Applications Magazine, 21(1), 41-48.
Goralski, W. (2017). The Illustrated network: How TCP/IP works in a modern network. Morgan
Kaufmann.
Kulkarni, S., & Agrawal, P. (2014). Introduction. In Analysis of TCP Performance in Data
Center Networks (pp. 1-15). Springer New York.
Patinge, S., Suryawanshi, Y., & Kakde, S. (2013, December). Design of ARM based data
acquisition & control using GSM & TCP/IP network. In Computational Intelligence and
Computing Research (ICCIC), 2013 IEEE International Conference on (pp. 1-4). IEEE.
Severance, C. (2013). Van Jacobson: content-centric networking. Computer, 46(1), 11-13.
Shang, W., Yu, Y., Droms, R., & Zhang, L. (2016). Challenges in IoT networking via TCP/IP
architecture. NDN Project, Tech. Rep. NDN-0038.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





