IT Networking Design Report: IPv4, IPv6, and Transition Mechanisms
VerifiedAdded on 2020/04/29
|16
|3121
|57
Report
AI Summary
This report presents a detailed analysis of IT networking design, focusing on TCP/IP protocols and their application. It begins with an introduction to TCP/IP, covering its basic characteristics and layered protocol stack design. The report then differentiates between IPv6 and IPv4, exploring their packet formats, addressing schemes, and address spaces. Transition mechanisms, including dual IP stack implementation, are discussed to facilitate the adoption of IPv6. The applied section includes project tasks examining TCP headers in IPv4 and IPv6, analyzing 6to4 and Teredo capture files, and investigating router solicitation packets. The report provides answers to specific questions related to these tasks, offering insights into the practical aspects of network design and protocol implementation. The findings highlight the importance of understanding both IPv4 and IPv6, along with the transition strategies needed for a smooth migration, ensuring efficient data transmission and network management.

Running head: IT NETWORKING DESIGNING
IT Networking Designing
Name of the Student
Name of the University
Author’s Note
IT Networking Designing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT NETWORKING DESIGNING
Table of Contents
SECTION 1 (Research)...................................................................................................................2
Introduction..................................................................................................................................2
Basic characteristics and layered protocol stack design of TCP/IP protocols.............................2
Difference between IPv6 and IPv4..............................................................................................3
Transition mechanism..................................................................................................................4
Dual IP stack implementation......................................................................................................5
Conclusion...................................................................................................................................5
SECTION 2 (Applied).....................................................................................................................6
Project Task 1 – Examination of the TCP Header in IPv4 and IPv6...........................................6
Answer to question 1...............................................................................................................6
Answer to question 2...............................................................................................................7
Project task 2 – Examination of 6to4 capture file........................................................................7
Answer to Question 1..............................................................................................................7
Answer to Question 2..............................................................................................................8
Project Task 3 – Examination of the Teredo capture file and Router Solicitation packet.........11
Answer to Question 1............................................................................................................11
Answer to Question 2............................................................................................................11
Bibliography..................................................................................................................................14
IT NETWORKING DESIGNING
Table of Contents
SECTION 1 (Research)...................................................................................................................2
Introduction..................................................................................................................................2
Basic characteristics and layered protocol stack design of TCP/IP protocols.............................2
Difference between IPv6 and IPv4..............................................................................................3
Transition mechanism..................................................................................................................4
Dual IP stack implementation......................................................................................................5
Conclusion...................................................................................................................................5
SECTION 2 (Applied).....................................................................................................................6
Project Task 1 – Examination of the TCP Header in IPv4 and IPv6...........................................6
Answer to question 1...............................................................................................................6
Answer to question 2...............................................................................................................7
Project task 2 – Examination of 6to4 capture file........................................................................7
Answer to Question 1..............................................................................................................7
Answer to Question 2..............................................................................................................8
Project Task 3 – Examination of the Teredo capture file and Router Solicitation packet.........11
Answer to Question 1............................................................................................................11
Answer to Question 2............................................................................................................11
Bibliography..................................................................................................................................14

2
IT NETWORKING DESIGNING
SECTION 1 (Research)
Introduction
For the preparation o0of the report a research is done on the TCP/IP protocols and the
rules followed in the communication network for the transmission of the data packets. Each of
the layer of the TCP/IP model is responsible for sending and receiving the data packets and
ensures that the information are delivered and the management of the data transfer for the
identification of the transmission of the data. IP addressing is important for connecting with the
hosts connected in the network.
Basic characteristics and layered protocol stack design of TCP/IP protocols
Internet protocol suite is used in the network and the TCP/IP model acts as the standard
for development of the stack or the protocol suite for the network. Different modules comprises
to form the stack and different functionality are provided by the module. The modules should be
independent of each other and high layer protocol is used for supporting the lower layer of the
protocols. The protocol stack is used as a collection of the protocols that are used in the different
layers of the TCP/IP model. The protocols are used for establishment of a connection between
the different types of devices connected in the network and mainly the five layers such as
application, transport, network, data link and physical layer. The devices that requires to use the
protocol stack are categorized into host system or end system and intermediate node or system.
Intermediate node utilizes the first three layers of the TCP/IP model for communicating with the
other devices while there are some expectation that some of the device may use all the five layers
for successful communication. The effective element that is used for processing the sending and
receiving the data that are collected in the group for becoming the layer.
IT NETWORKING DESIGNING
SECTION 1 (Research)
Introduction
For the preparation o0of the report a research is done on the TCP/IP protocols and the
rules followed in the communication network for the transmission of the data packets. Each of
the layer of the TCP/IP model is responsible for sending and receiving the data packets and
ensures that the information are delivered and the management of the data transfer for the
identification of the transmission of the data. IP addressing is important for connecting with the
hosts connected in the network.
Basic characteristics and layered protocol stack design of TCP/IP protocols
Internet protocol suite is used in the network and the TCP/IP model acts as the standard
for development of the stack or the protocol suite for the network. Different modules comprises
to form the stack and different functionality are provided by the module. The modules should be
independent of each other and high layer protocol is used for supporting the lower layer of the
protocols. The protocol stack is used as a collection of the protocols that are used in the different
layers of the TCP/IP model. The protocols are used for establishment of a connection between
the different types of devices connected in the network and mainly the five layers such as
application, transport, network, data link and physical layer. The devices that requires to use the
protocol stack are categorized into host system or end system and intermediate node or system.
Intermediate node utilizes the first three layers of the TCP/IP model for communicating with the
other devices while there are some expectation that some of the device may use all the five layers
for successful communication. The effective element that is used for processing the sending and
receiving the data that are collected in the group for becoming the layer.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
IT NETWORKING DESIGNING
Difference between IPv6 and IPv4
The main difference identified between the different versions of IP address are the
addressing scheme and the format of the packets for communicating in the network. The IP
address are combined with the TCP for connecting with the different sources and establishment
of a direct link between the hosts.
Description IPv4 IPv6
Packet Format It have an IP header
that is 20 to 60 bytes
long and an address
mask is used for the
designation of the
network using the host
connected in the
network. An address
prefix is used for the
designation of the host
portion and it is written
as /nn.
The length of the IP address is 40 bytes and
it is much simple than the IPv4 header.
Address mask is not used. The address
prefix is used for the designation of the
subnet and it is written as /nnn.
Address Space 4 bytes and 32 bits
address is used and it is
divided into different
classes such as A, B,
C, D, E. The total
16 bytes or 128 bits in length and it works
on the 64 bit architecture. The host part of
the IPv6 is derived from the Mac number of
the interface and its architecture is complex
than the IPv4. 10^28 times more than the
IT NETWORKING DESIGNING
Difference between IPv6 and IPv4
The main difference identified between the different versions of IP address are the
addressing scheme and the format of the packets for communicating in the network. The IP
address are combined with the TCP for connecting with the different sources and establishment
of a direct link between the hosts.
Description IPv4 IPv6
Packet Format It have an IP header
that is 20 to 60 bytes
long and an address
mask is used for the
designation of the
network using the host
connected in the
network. An address
prefix is used for the
designation of the host
portion and it is written
as /nn.
The length of the IP address is 40 bytes and
it is much simple than the IPv4 header.
Address mask is not used. The address
prefix is used for the designation of the
subnet and it is written as /nnn.
Address Space 4 bytes and 32 bits
address is used and it is
divided into different
classes such as A, B,
C, D, E. The total
16 bytes or 128 bits in length and it works
on the 64 bit architecture. The host part of
the IPv6 is derived from the Mac number of
the interface and its architecture is complex
than the IPv4. 10^28 times more than the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
IT NETWORKING DESIGNING
number of address
supported by the IPv4
is 4294967296
address provided by the IPv4.
Address
representation
The IPv4 address is
represented as
nnn.nnn.nnn.nnn and
nnn is less than equal
to 255. The maximum
number that can be
printed is 15.
The text form of IPv6 address is
xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx
where, x represents a 4 bit hexadecimal
digit. The o’s can be eliminated and double
colon should be used for designation of the
0 bits in the IPv6 address. E.g. :: ffff: 12:
121:41 is an IPv4 address that is mapped to
IPv6.
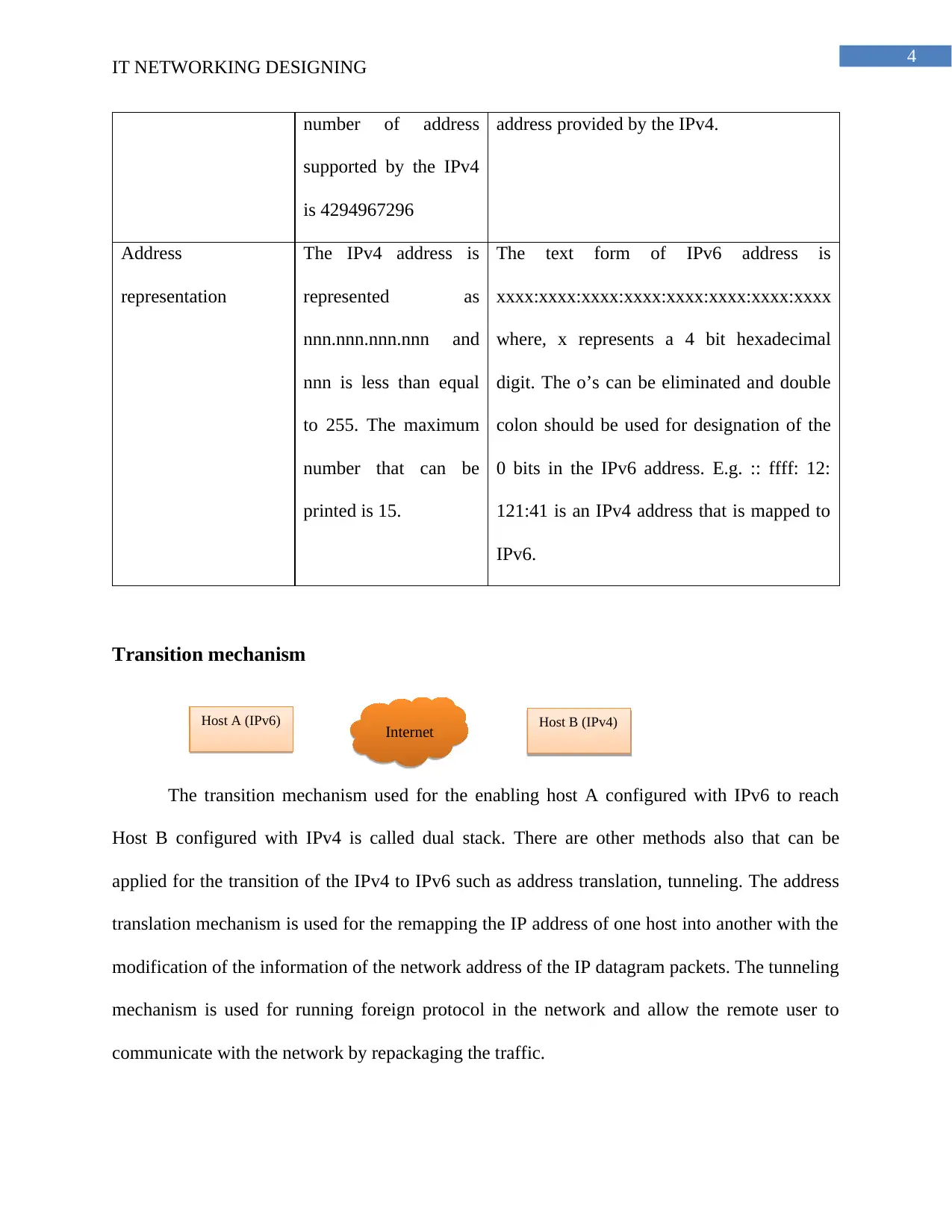
Transition mechanism
The transition mechanism used for the enabling host A configured with IPv6 to reach
Host B configured with IPv4 is called dual stack. There are other methods also that can be
applied for the transition of the IPv4 to IPv6 such as address translation, tunneling. The address
translation mechanism is used for the remapping the IP address of one host into another with the
modification of the information of the network address of the IP datagram packets. The tunneling
mechanism is used for running foreign protocol in the network and allow the remote user to
communicate with the network by repackaging the traffic.
Host A (IPv6) Internet Host B (IPv4)
IT NETWORKING DESIGNING
number of address
supported by the IPv4
is 4294967296
address provided by the IPv4.
Address
representation
The IPv4 address is
represented as
nnn.nnn.nnn.nnn and
nnn is less than equal
to 255. The maximum
number that can be
printed is 15.
The text form of IPv6 address is
xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx
where, x represents a 4 bit hexadecimal
digit. The o’s can be eliminated and double
colon should be used for designation of the
0 bits in the IPv6 address. E.g. :: ffff: 12:
121:41 is an IPv4 address that is mapped to
IPv6.
Transition mechanism
The transition mechanism used for the enabling host A configured with IPv6 to reach
Host B configured with IPv4 is called dual stack. There are other methods also that can be
applied for the transition of the IPv4 to IPv6 such as address translation, tunneling. The address
translation mechanism is used for the remapping the IP address of one host into another with the
modification of the information of the network address of the IP datagram packets. The tunneling
mechanism is used for running foreign protocol in the network and allow the remote user to
communicate with the network by repackaging the traffic.
Host A (IPv6) Internet Host B (IPv4)

5
IT NETWORKING DESIGNING
Dual IP stack implementation
For the implementation of the Dual stack mechanism the support of the nodes should be
analyzed. The nodes should support both the version of the IP and the operation should be
selected for enabling or disabling the stacks. There are three main parts of the dual stack
architecture such as the DSTM client, DSTM server and the DSTM gateway.
The client is the dual stack nodes connected in the network that request for the IPv4
address and allows the IPv6 host to communicate with the IPv4 hosts. A DSTM server is setup
for allocation of the IPv4 address with the IPv6 gateway to the nodes connected in the network.
The DSTM gateway is used for the end point tunneling and encapsulating or decapsulating the
packets tunneled in the network.
Conclusion
From the above report it can be concluded that a research is made on the TCP/IP protocol
for the evaluation of the protocols used for communicating with the nodes connected in the
network. It is important for the network administrator to identify the different approach of the
IPv6 and the dual stack mechanism should be followed for the adoption of the IPv4 and the IPv6
nodes to communicate with each other. A dual stack network environment is created and
different IP management tools are used for ensuring smooth transition in the network.
IT NETWORKING DESIGNING
Dual IP stack implementation
For the implementation of the Dual stack mechanism the support of the nodes should be
analyzed. The nodes should support both the version of the IP and the operation should be
selected for enabling or disabling the stacks. There are three main parts of the dual stack
architecture such as the DSTM client, DSTM server and the DSTM gateway.
The client is the dual stack nodes connected in the network that request for the IPv4
address and allows the IPv6 host to communicate with the IPv4 hosts. A DSTM server is setup
for allocation of the IPv4 address with the IPv6 gateway to the nodes connected in the network.
The DSTM gateway is used for the end point tunneling and encapsulating or decapsulating the
packets tunneled in the network.
Conclusion
From the above report it can be concluded that a research is made on the TCP/IP protocol
for the evaluation of the protocols used for communicating with the nodes connected in the
network. It is important for the network administrator to identify the different approach of the
IPv6 and the dual stack mechanism should be followed for the adoption of the IPv4 and the IPv6
nodes to communicate with each other. A dual stack network environment is created and
different IP management tools are used for ensuring smooth transition in the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT NETWORKING DESIGNING
SECTION 2 (Applied)
Project Task 1 – Examination of the TCP Header in IPv4 and IPv6
Answer to question 1
As every one of the fields of IPv6 headers are not the same as that of the IPv4 header, the
PT module makes an interpretation of IP/ICMP headers to make end to end correspondence
conceivable. Because of the address interpretation capacity and due to conceivable port
multiplexing, PT likewise makes fitting changes in accordance with the upper layer convention
(TCP/UDP) headers, e.g., the checksum.
The IPv4toIPv6 interpreter replaces the IPv4 header of IPv4 packet with an IPv6 header
to send it to the IPv6 have. Aside from ICMP bundles, the vehicle layer header and information
segment of the packet are left unaltered. In IPv6, way MTU revelation is required however it is
discretionary in IPv4. This infers IPv6 switches will never part a packets just the sender can do
discontinuity. Way MTU disclosure is actualized by sending an ICMP mistake message to the
packet sender expressing that the bundle is too enormous. At the point when an IPv6 switch
sends an ICMP blunder message, it will go through an interpreter, which will make an
interpretation of the ICMP mistake to a frame that the IPv4 sender can get it. For this situation an
IPv6 part header is just included if the IPv4 packet is now divided. The nearness of df hail in the
IPv4 header is the sign of Path MTU revelation.
In any case, if the IPv4 sender does not perform way MTU revelation, the interpreter
needs to guarantee that the packet does not surpass the way MTU on the IPv6 side. The
interpreter parts the IPv4 packet with the goal that it fits in a 1280 byte IPv6 bundle, since IPv6
ensures that 1280 byte packets never should be divided. Likewise, when the IPv4 sender does not
IT NETWORKING DESIGNING
SECTION 2 (Applied)
Project Task 1 – Examination of the TCP Header in IPv4 and IPv6
Answer to question 1
As every one of the fields of IPv6 headers are not the same as that of the IPv4 header, the
PT module makes an interpretation of IP/ICMP headers to make end to end correspondence
conceivable. Because of the address interpretation capacity and due to conceivable port
multiplexing, PT likewise makes fitting changes in accordance with the upper layer convention
(TCP/UDP) headers, e.g., the checksum.
The IPv4toIPv6 interpreter replaces the IPv4 header of IPv4 packet with an IPv6 header
to send it to the IPv6 have. Aside from ICMP bundles, the vehicle layer header and information
segment of the packet are left unaltered. In IPv6, way MTU revelation is required however it is
discretionary in IPv4. This infers IPv6 switches will never part a packets just the sender can do
discontinuity. Way MTU disclosure is actualized by sending an ICMP mistake message to the
packet sender expressing that the bundle is too enormous. At the point when an IPv6 switch
sends an ICMP blunder message, it will go through an interpreter, which will make an
interpretation of the ICMP mistake to a frame that the IPv4 sender can get it. For this situation an
IPv6 part header is just included if the IPv4 packet is now divided. The nearness of df hail in the
IPv4 header is the sign of Path MTU revelation.
In any case, if the IPv4 sender does not perform way MTU revelation, the interpreter
needs to guarantee that the packet does not surpass the way MTU on the IPv6 side. The
interpreter parts the IPv4 packet with the goal that it fits in a 1280 byte IPv6 bundle, since IPv6
ensures that 1280 byte packets never should be divided. Likewise, when the IPv4 sender does not
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT NETWORKING DESIGNING
perform way MTU revelation the interpreter should dependably incorporate an IPv6 section
header to demonstrate that the sender permits discontinuity.
Answer to question 2
2.1.1 The source port of the TCP is 1287 and HTTP protocol is used for the
transportation of the TCP packets.
2.1.2. The destination port number is 80 and it indicates that the connection is established
with a web server. The port 80 is used for sending and receiving web client based
communications and messages from the web server.
2.1.3. The acknowledgement number expected from the destination by the source is
985664865.
2.1.4. The length of the header is 20 bytes.
2.2.1. With the selection of the IPv6 and expansion it is found that the data have changed.
2.2.2. The data have changed because the data IPv4 address are translated into IPv6
address.
Project task 2 – Examination of 6to4 capture file
Answer to Question 1
For the translation of the IPv4 to IPv6 the 6to4 transition mechanism is applied and the
IPv4 packets are transmitted over the IPv6 network. This mechanism removes the requirement of
tunneling but this cannot be implemented permanently in the network and when it is applied on
the host connected in the network it is the responsibility of the host to encapsulate the incoming
6to4 IP packets and forward the packets to the other clients. Auto configuration is utilized for the
IT NETWORKING DESIGNING
perform way MTU revelation the interpreter should dependably incorporate an IPv6 section
header to demonstrate that the sender permits discontinuity.
Answer to question 2
2.1.1 The source port of the TCP is 1287 and HTTP protocol is used for the
transportation of the TCP packets.
2.1.2. The destination port number is 80 and it indicates that the connection is established
with a web server. The port 80 is used for sending and receiving web client based
communications and messages from the web server.
2.1.3. The acknowledgement number expected from the destination by the source is
985664865.
2.1.4. The length of the header is 20 bytes.
2.2.1. With the selection of the IPv6 and expansion it is found that the data have changed.
2.2.2. The data have changed because the data IPv4 address are translated into IPv6
address.
Project task 2 – Examination of 6to4 capture file
Answer to Question 1
For the translation of the IPv4 to IPv6 the 6to4 transition mechanism is applied and the
IPv4 packets are transmitted over the IPv6 network. This mechanism removes the requirement of
tunneling but this cannot be implemented permanently in the network and when it is applied on
the host connected in the network it is the responsibility of the host to encapsulate the incoming
6to4 IP packets and forward the packets to the other clients. Auto configuration is utilized for the

8
IT NETWORKING DESIGNING
IPv6 network and the 1st 64 bits of the IP address acts as the prefix and the 16 bits are 2002:
while the rest 32 bits are IPv4 address. The last 16 bits of the IPv6 address are the addressing the
subnets used in the same 6to4 router used for configuring the local area network.
Due to the fact the IPv6 hosts applying auto setup currently have determined the original
64 bit number portion of their address, they've to simply watch for a router advertise revealing
the initial 64 items of prefix to truly have a complete IPv6 address. A 6to4 router is used for
sending encapsulated package immediately around IPv4 if the initial 16 bits are 2002, utilizing
the next 32 bits whilst the place, or otherwise send the package to a well-known relay host,
which includes usage of indigenous IPv6. 6to4 does not help interoperation between IPv4-only
hosts and IPv6-only hosts. 6to4 is merely a transparent mechanism applied as a transport coating
between IPv6 nodes.
Answer to Question 2
2.1. The information about the IPv4 header encapsulating the IPv6 packet.
Internet Protocol Version 4, Src: 70.55.213.211, Dst: 192.88.99.1
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 80
Identification: 0x935a (37722)
Flags: 0x00
Fragment offset: 0
IT NETWORKING DESIGNING
IPv6 network and the 1st 64 bits of the IP address acts as the prefix and the 16 bits are 2002:
while the rest 32 bits are IPv4 address. The last 16 bits of the IPv6 address are the addressing the
subnets used in the same 6to4 router used for configuring the local area network.
Due to the fact the IPv6 hosts applying auto setup currently have determined the original
64 bit number portion of their address, they've to simply watch for a router advertise revealing
the initial 64 items of prefix to truly have a complete IPv6 address. A 6to4 router is used for
sending encapsulated package immediately around IPv4 if the initial 16 bits are 2002, utilizing
the next 32 bits whilst the place, or otherwise send the package to a well-known relay host,
which includes usage of indigenous IPv6. 6to4 does not help interoperation between IPv4-only
hosts and IPv6-only hosts. 6to4 is merely a transparent mechanism applied as a transport coating
between IPv6 nodes.
Answer to Question 2
2.1. The information about the IPv4 header encapsulating the IPv6 packet.
Internet Protocol Version 4, Src: 70.55.213.211, Dst: 192.88.99.1
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 80
Identification: 0x935a (37722)
Flags: 0x00
Fragment offset: 0
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT NETWORKING DESIGNING
Time to live: 128
Protocol: IPv6 (41)
Header checksum: 0x67c6 [validation disabled]
[Header checksum status: Unverified]
Source: 70.55.213.211
Destination: 192.88.99.1
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
2.2. The IPv4 addresses assigned to the source and destination fields.
Source: 70.55.213.211
Destination: 192.88.99.1
2.3. The information about the IPv6 packet that has been encapsulated.
Internet Protocol Version 6, Src: 2002:4637:d5d3::4637:d5d3, Dst: 2001:4860:0:2001::68
0110 .... = Version: 6
.... 0000 0000 .... .... .... .... .... = Traffic Class: 0x00 (DSCP: CS0, ECN: Not-ECT)
.... .... .... 0000 0000 0000 0000 0000 = Flow Label: 0x00000
Payload Length: 20
Next Header: TCP (6)
IT NETWORKING DESIGNING
Time to live: 128
Protocol: IPv6 (41)
Header checksum: 0x67c6 [validation disabled]
[Header checksum status: Unverified]
Source: 70.55.213.211
Destination: 192.88.99.1
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
2.2. The IPv4 addresses assigned to the source and destination fields.
Source: 70.55.213.211
Destination: 192.88.99.1
2.3. The information about the IPv6 packet that has been encapsulated.
Internet Protocol Version 6, Src: 2002:4637:d5d3::4637:d5d3, Dst: 2001:4860:0:2001::68
0110 .... = Version: 6
.... 0000 0000 .... .... .... .... .... = Traffic Class: 0x00 (DSCP: CS0, ECN: Not-ECT)
.... .... .... 0000 0000 0000 0000 0000 = Flow Label: 0x00000
Payload Length: 20
Next Header: TCP (6)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT NETWORKING DESIGNING
Hop Limit: 128
Source: 2002:4637:d5d3::4637:d5d3
Destination: 2001:4860:0:2001::68
[Source 6to4 Gateway IPv4: 70.55.213.211]
[Source 6to4 SLA ID: 0]
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
2.4. The IPv6 address assigned to the 6to4 source node.
Source: 2002:4637:d5d3::4637:d5d3
2.5. The IPv4 address assigned to the 6to4 gateway router servicing the 6to4 source
node.
[Source 6to4 Gateway IPv4: 70.55.213.211]
2.6. The IPv6 address assigned to the 6to4 destination node.
Destination: 2001:4860:0:2001::68
2.7. The acknowledge receipt of the packet sent by the other node in previous frame.
Acknowledgement number: 985667781
IT NETWORKING DESIGNING
Hop Limit: 128
Source: 2002:4637:d5d3::4637:d5d3
Destination: 2001:4860:0:2001::68
[Source 6to4 Gateway IPv4: 70.55.213.211]
[Source 6to4 SLA ID: 0]
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
2.4. The IPv6 address assigned to the 6to4 source node.
Source: 2002:4637:d5d3::4637:d5d3
2.5. The IPv4 address assigned to the 6to4 gateway router servicing the 6to4 source
node.
[Source 6to4 Gateway IPv4: 70.55.213.211]
2.6. The IPv6 address assigned to the 6to4 destination node.
Destination: 2001:4860:0:2001::68
2.7. The acknowledge receipt of the packet sent by the other node in previous frame.
Acknowledgement number: 985667781

11
IT NETWORKING DESIGNING
Project Task 3 – Examination of the Teredo capture file and Router Solicitation
packet
Answer to Question 1
The teredo transition technology is used for the providing full connection to the IPv6
network and teredo can operate utilizing an independent platform tunnelling protocol and
providing connectivity by the encapsulation of the IPv6 data packets with the implementation of
the IPv4 data protocol. The teredo is used for routing the datagrams for the IPv4 and teredo relay
is used receiving the data packets and un encapsulating for forwarding the data packets in the
network. It is a temporary procedure for connecting the IPv6 hosts in a network with the IPv4
host.
For pseudo tunneling of the Teredo the outgoing data packets should be unfiltered and the
replies should also be unfiltered. A typical setup should be created for creation of a stateful
functionality with the firewall and detection of the errors in the network. The outgoing network
traffic can be blocked for interfering with the teredo activity and the new methods should be
applied for mitigation of the risk of dos attacks and uncovering the teredo tunnels.
The main components of the teredo are the teredo clients, teredo servers, reredos relays
and the teredo host specific relays that are applied in the network for configuring the network
with global addressing scheme. The host specific relay is used for connecting the interface of the
different devices connected in the network. The teredo servers are also installed in the network
assisting the configuration of the address and facilitating the initial communication between the
clients.
IT NETWORKING DESIGNING
Project Task 3 – Examination of the Teredo capture file and Router Solicitation
packet
Answer to Question 1
The teredo transition technology is used for the providing full connection to the IPv6
network and teredo can operate utilizing an independent platform tunnelling protocol and
providing connectivity by the encapsulation of the IPv6 data packets with the implementation of
the IPv4 data protocol. The teredo is used for routing the datagrams for the IPv4 and teredo relay
is used receiving the data packets and un encapsulating for forwarding the data packets in the
network. It is a temporary procedure for connecting the IPv6 hosts in a network with the IPv4
host.
For pseudo tunneling of the Teredo the outgoing data packets should be unfiltered and the
replies should also be unfiltered. A typical setup should be created for creation of a stateful
functionality with the firewall and detection of the errors in the network. The outgoing network
traffic can be blocked for interfering with the teredo activity and the new methods should be
applied for mitigation of the risk of dos attacks and uncovering the teredo tunnels.
The main components of the teredo are the teredo clients, teredo servers, reredos relays
and the teredo host specific relays that are applied in the network for configuring the network
with global addressing scheme. The host specific relay is used for connecting the interface of the
different devices connected in the network. The teredo servers are also installed in the network
assisting the configuration of the address and facilitating the initial communication between the
clients.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





