Exploring Network Security through Tcpdump and Other Tools
VerifiedAdded on 2020/05/08
|25
|528
|129
AI Summary
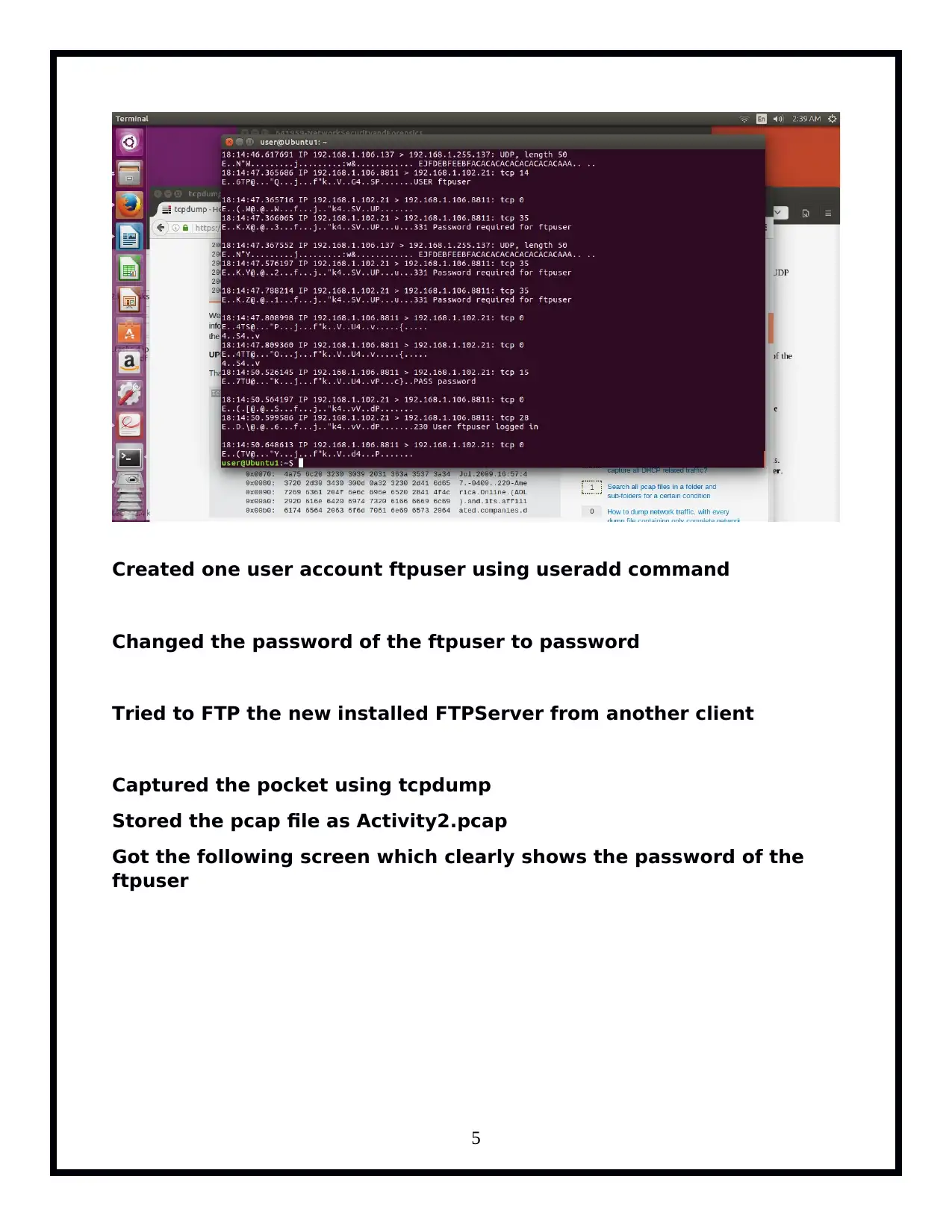
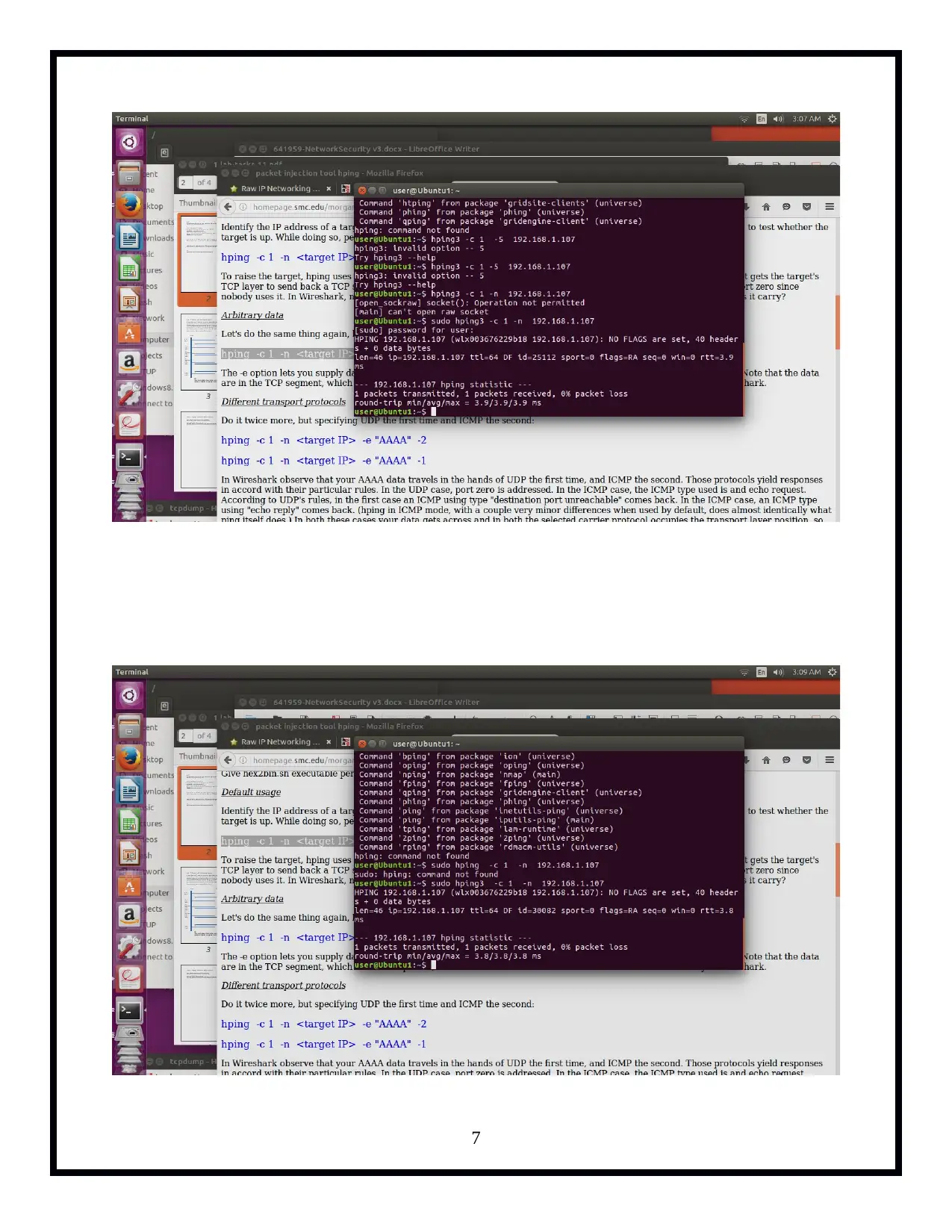
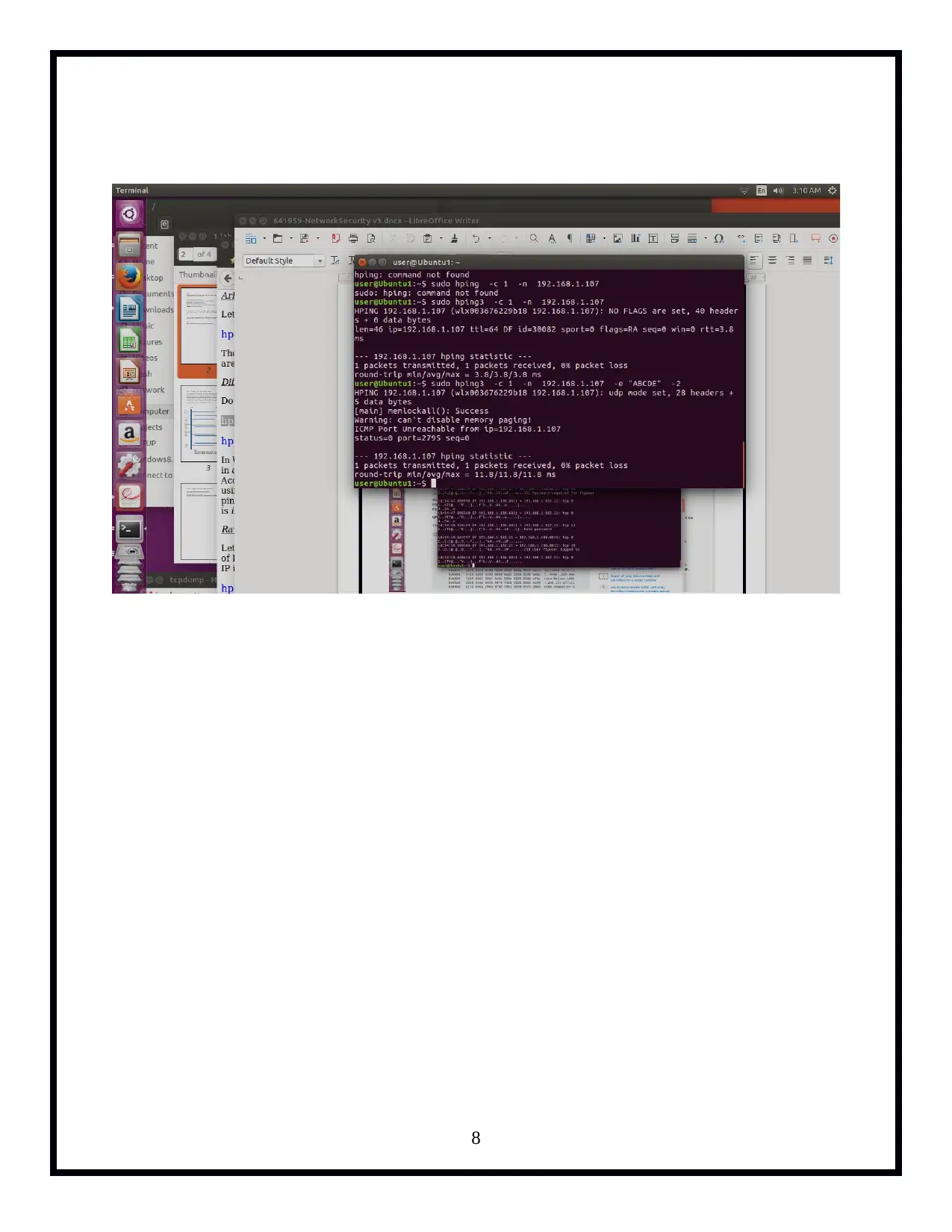
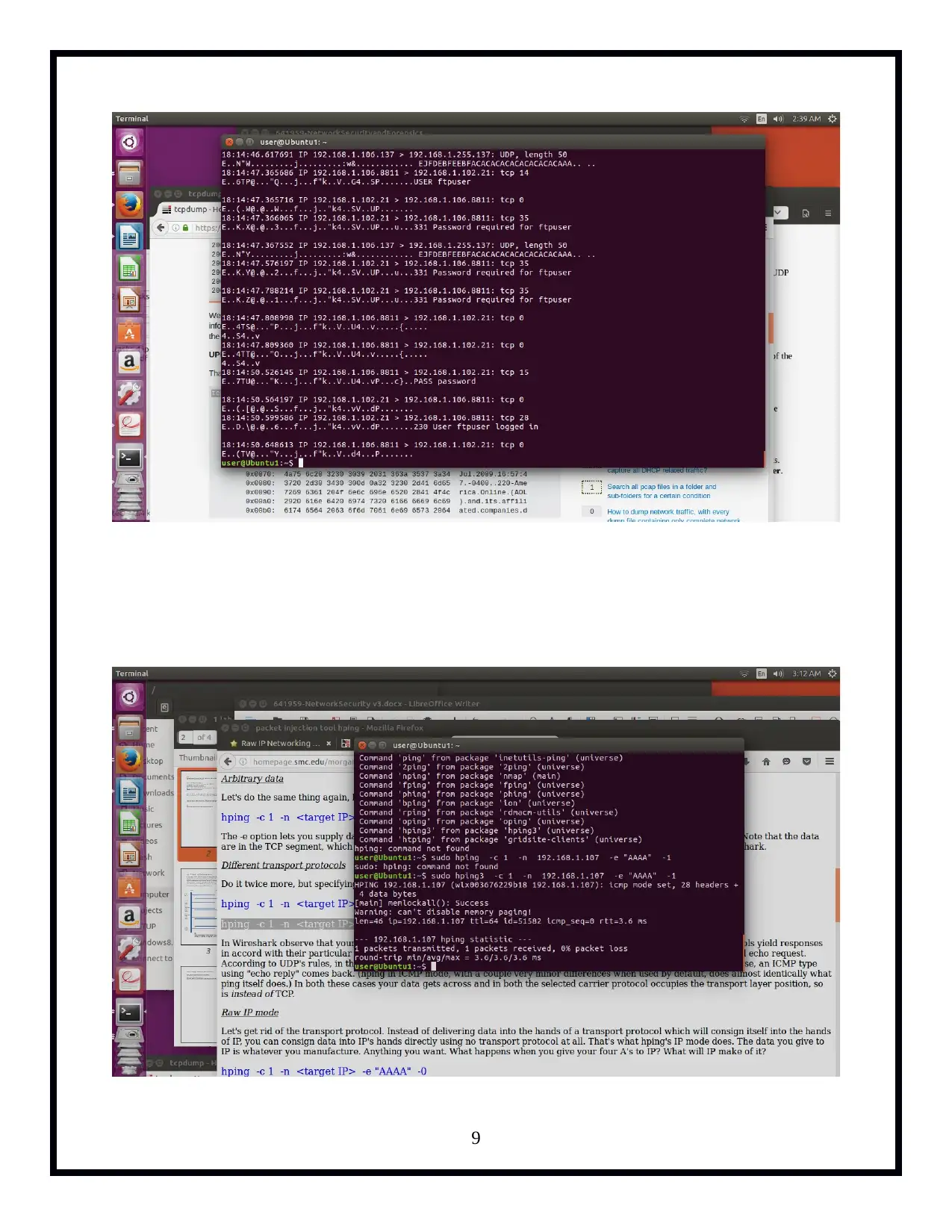
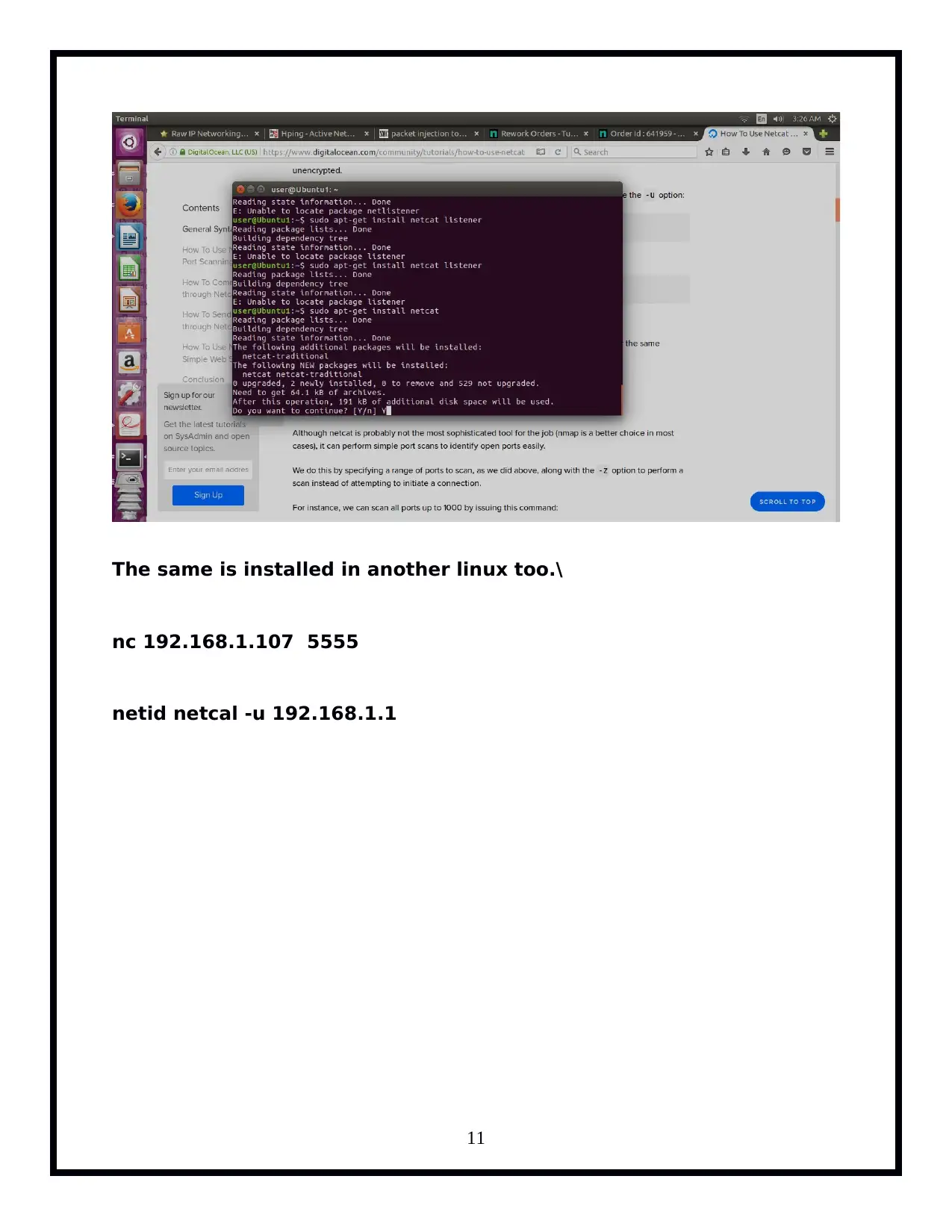
The 'Network Security and Forensics' assignment provides a practical approach for students to delve into network security mechanisms. Through the use of command-line tools like Tcpdump, Iptables, Hping3, and ProFTPd, participants explore various tasks including version checking with Tcpdump, listing interfaces, pinging loopback addresses while capturing traffic, FTP server setup and analysis, UDP and ICMP protocol manipulation, IPv4 fragmentation, IP fragment reassembly, sniffing in switched environments via ARP Cache Poisoning, TCP RST attacks on telnet and SSH connections, rate limiting, and iptables trickery. The tasks are designed to enhance understanding of network packet capturing, security vulnerabilities such as ARP spoofing and session disruption, firewall evasion techniques using fragment route tools, IP fragmentation reassembly, and defensive measures like rate limiting with Iptables.
1 out of 25



![[object Object]](/_next/static/media/star-bottom.7253800d.svg)