Comprehensive Technical Risk Analysis Report for ABC Fitness Gym
VerifiedAdded on 2022/09/28
|11
|2777
|20
Report
AI Summary
This report provides a comprehensive technical risk analysis for ABC Fitness Gym, examining the organization's technology environment and potential vulnerabilities. The report identifies key assets, threats, vulnerabilities, and consequences, utilizing an IT control framework to assess risks related to employee information, gym equipment inventory, and member data. It also incorporates industry risk recommendations and proposes mitigation strategies, including software updates, antivirus protection, data backups, employee training, and secure infrastructure. The report further outlines protection mechanisms such as safeguards, tools, technologies, and cultural practices to enhance data security. Finally, it offers recommendations based on the principles of information systems, emphasizing confidentiality, integrity, and availability to ensure the secure and efficient operation of ABC Fitness Gym's IT systems.

Technical Risk Analysis
Name of the Student
Student ID
Name of the Subject
Subject Code
Name of the Lecturer
Author Note
Name of the Student
Student ID
Name of the Subject
Subject Code
Name of the Lecturer
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
ABC fitness gym is an organisation that has been looking forward to implement information
system within the organisation as it has been expanding ever since its establishment. Before,
the organisation did not have an information system but now the implementation of the
expansion has made many people join the company as employees and members. The
expansion has been such that the organisation has expanded its physical structure as well as
brought together the huge number of expansion in employee implementation, members and
gym equipment inventory. However, applying the information system to handle all the
business operation but also lead to several aspects of vulnerability related to the information
management of the business assets. Safeguarding business information for the smooth
operation of the business is extremely essential for every organisation. Therefore following
would be a report where the identification of all the business assets, the vulnerabilities they
have and the mitigation strategies for the entire organisation including the people within the
organisation would be described in details.
ABC fitness gym is an organisation that has been looking forward to implement information
system within the organisation as it has been expanding ever since its establishment. Before,
the organisation did not have an information system but now the implementation of the
expansion has made many people join the company as employees and members. The
expansion has been such that the organisation has expanded its physical structure as well as
brought together the huge number of expansion in employee implementation, members and
gym equipment inventory. However, applying the information system to handle all the
business operation but also lead to several aspects of vulnerability related to the information
management of the business assets. Safeguarding business information for the smooth
operation of the business is extremely essential for every organisation. Therefore following
would be a report where the identification of all the business assets, the vulnerabilities they
have and the mitigation strategies for the entire organisation including the people within the
organisation would be described in details.

Table of Contents
1. Risk assessment......................................................................................................................4
1.1 Identify key assets, threats, vulnerabilities and consequences based on IT Control
Framework.............................................................................................................................4
1.2 Existing industry risk recommendations for the project..................................................5
1.3 Mitigate the risks and impact on the organisation...........................................................6
2. Protection mechanisms...........................................................................................................7
2.1 Safe guards.......................................................................................................................7
2.2 Tools and technologies.....................................................................................................8
2.3 Culture..............................................................................................................................9
2.4 People...............................................................................................................................9
3. Recommendations..................................................................................................................9
3.1 Discuss on the principles of IS.........................................................................................9
References................................................................................................................................11
1. Risk assessment......................................................................................................................4
1.1 Identify key assets, threats, vulnerabilities and consequences based on IT Control
Framework.............................................................................................................................4
1.2 Existing industry risk recommendations for the project..................................................5
1.3 Mitigate the risks and impact on the organisation...........................................................6
2. Protection mechanisms...........................................................................................................7
2.1 Safe guards.......................................................................................................................7
2.2 Tools and technologies.....................................................................................................8
2.3 Culture..............................................................................................................................9
2.4 People...............................................................................................................................9
3. Recommendations..................................................................................................................9
3.1 Discuss on the principles of IS.........................................................................................9
References................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
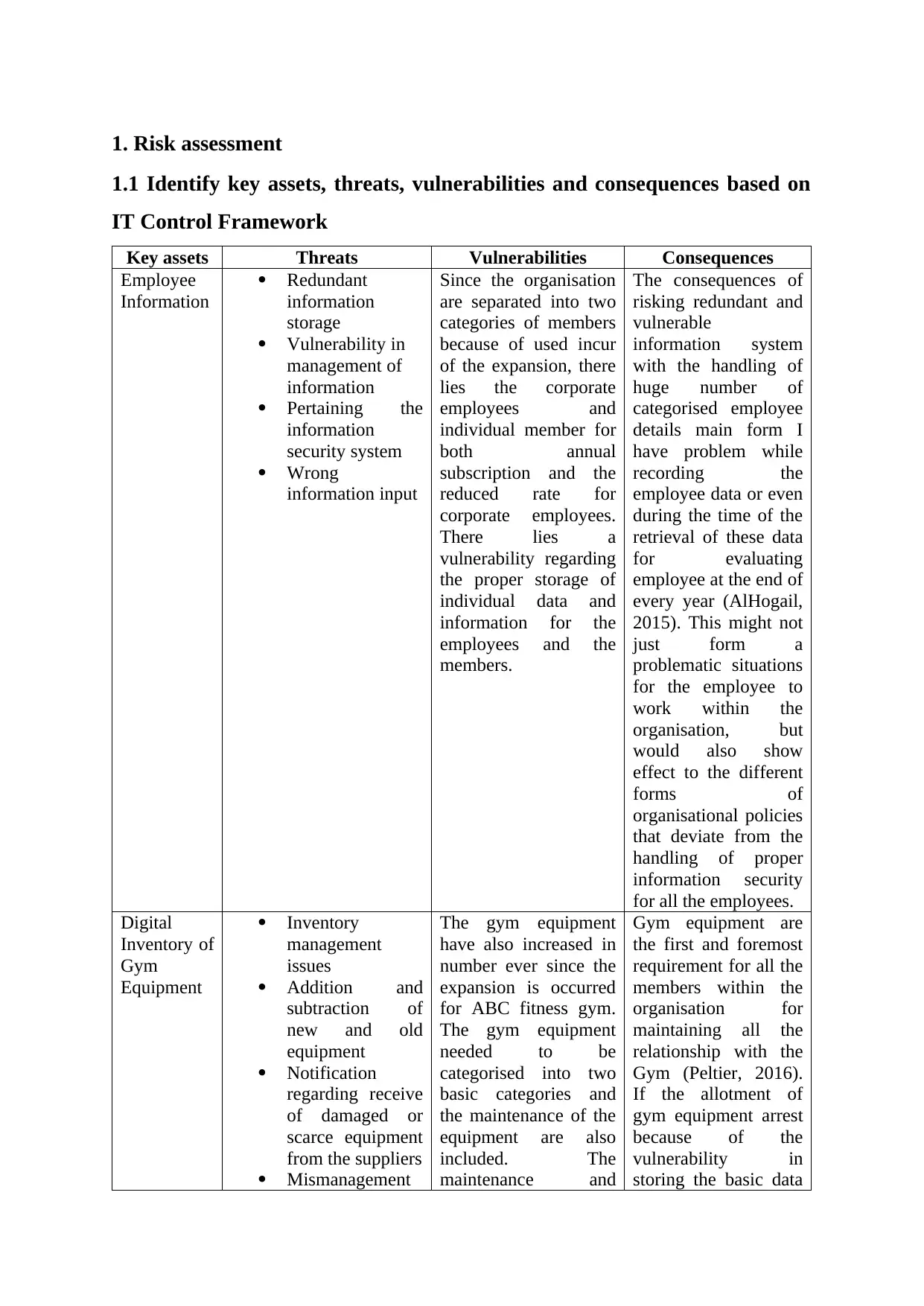
1. Risk assessment
1.1 Identify key assets, threats, vulnerabilities and consequences based on
IT Control Framework
Key assets Threats Vulnerabilities Consequences
Employee
Information
Redundant
information
storage
Vulnerability in
management of
information
Pertaining the
information
security system
Wrong
information input
Since the organisation
are separated into two
categories of members
because of used incur
of the expansion, there
lies the corporate
employees and
individual member for
both annual
subscription and the
reduced rate for
corporate employees.
There lies a
vulnerability regarding
the proper storage of
individual data and
information for the
employees and the
members.
The consequences of
risking redundant and
vulnerable
information system
with the handling of
huge number of
categorised employee
details main form I
have problem while
recording the
employee data or even
during the time of the
retrieval of these data
for evaluating
employee at the end of
every year (AlHogail,
2015). This might not
just form a
problematic situations
for the employee to
work within the
organisation, but
would also show
effect to the different
forms of
organisational policies
that deviate from the
handling of proper
information security
for all the employees.
Digital
Inventory of
Gym
Equipment
Inventory
management
issues
Addition and
subtraction of
new and old
equipment
Notification
regarding receive
of damaged or
scarce equipment
from the suppliers
Mismanagement
The gym equipment
have also increased in
number ever since the
expansion is occurred
for ABC fitness gym.
The gym equipment
needed to be
categorised into two
basic categories and
the maintenance of the
equipment are also
included. The
maintenance and
Gym equipment are
the first and foremost
requirement for all the
members within the
organisation for
maintaining all the
relationship with the
Gym (Peltier, 2016).
If the allotment of
gym equipment arrest
because of the
vulnerability in
storing the basic data
1.1 Identify key assets, threats, vulnerabilities and consequences based on
IT Control Framework
Key assets Threats Vulnerabilities Consequences
Employee
Information
Redundant
information
storage
Vulnerability in
management of
information
Pertaining the
information
security system
Wrong
information input
Since the organisation
are separated into two
categories of members
because of used incur
of the expansion, there
lies the corporate
employees and
individual member for
both annual
subscription and the
reduced rate for
corporate employees.
There lies a
vulnerability regarding
the proper storage of
individual data and
information for the
employees and the
members.
The consequences of
risking redundant and
vulnerable
information system
with the handling of
huge number of
categorised employee
details main form I
have problem while
recording the
employee data or even
during the time of the
retrieval of these data
for evaluating
employee at the end of
every year (AlHogail,
2015). This might not
just form a
problematic situations
for the employee to
work within the
organisation, but
would also show
effect to the different
forms of
organisational policies
that deviate from the
handling of proper
information security
for all the employees.
Digital
Inventory of
Gym
Equipment
Inventory
management
issues
Addition and
subtraction of
new and old
equipment
Notification
regarding receive
of damaged or
scarce equipment
from the suppliers
Mismanagement
The gym equipment
have also increased in
number ever since the
expansion is occurred
for ABC fitness gym.
The gym equipment
needed to be
categorised into two
basic categories and
the maintenance of the
equipment are also
included. The
maintenance and
Gym equipment are
the first and foremost
requirement for all the
members within the
organisation for
maintaining all the
relationship with the
Gym (Peltier, 2016).
If the allotment of
gym equipment arrest
because of the
vulnerability in
storing the basic data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
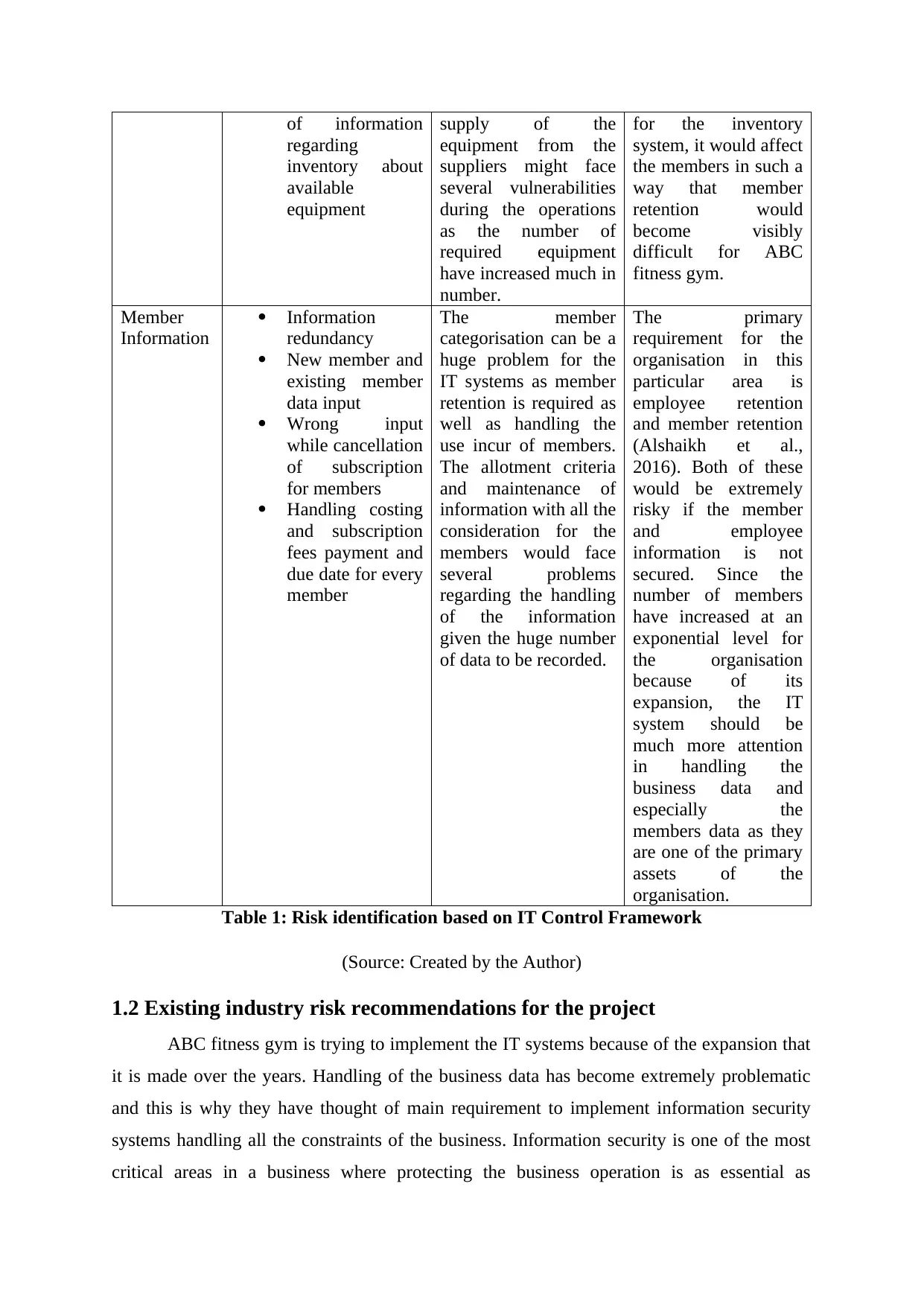
of information
regarding
inventory about
available
equipment
supply of the
equipment from the
suppliers might face
several vulnerabilities
during the operations
as the number of
required equipment
have increased much in
number.
for the inventory
system, it would affect
the members in such a
way that member
retention would
become visibly
difficult for ABC
fitness gym.
Member
Information
Information
redundancy
New member and
existing member
data input
Wrong input
while cancellation
of subscription
for members
Handling costing
and subscription
fees payment and
due date for every
member
The member
categorisation can be a
huge problem for the
IT systems as member
retention is required as
well as handling the
use incur of members.
The allotment criteria
and maintenance of
information with all the
consideration for the
members would face
several problems
regarding the handling
of the information
given the huge number
of data to be recorded.
The primary
requirement for the
organisation in this
particular area is
employee retention
and member retention
(Alshaikh et al.,
2016). Both of these
would be extremely
risky if the member
and employee
information is not
secured. Since the
number of members
have increased at an
exponential level for
the organisation
because of its
expansion, the IT
system should be
much more attention
in handling the
business data and
especially the
members data as they
are one of the primary
assets of the
organisation.
Table 1: Risk identification based on IT Control Framework
(Source: Created by the Author)
1.2 Existing industry risk recommendations for the project
ABC fitness gym is trying to implement the IT systems because of the expansion that
it is made over the years. Handling of the business data has become extremely problematic
and this is why they have thought of main requirement to implement information security
systems handling all the constraints of the business. Information security is one of the most
critical areas in a business where protecting the business operation is as essential as
regarding
inventory about
available
equipment
supply of the
equipment from the
suppliers might face
several vulnerabilities
during the operations
as the number of
required equipment
have increased much in
number.
for the inventory
system, it would affect
the members in such a
way that member
retention would
become visibly
difficult for ABC
fitness gym.
Member
Information
Information
redundancy
New member and
existing member
data input
Wrong input
while cancellation
of subscription
for members
Handling costing
and subscription
fees payment and
due date for every
member
The member
categorisation can be a
huge problem for the
IT systems as member
retention is required as
well as handling the
use incur of members.
The allotment criteria
and maintenance of
information with all the
consideration for the
members would face
several problems
regarding the handling
of the information
given the huge number
of data to be recorded.
The primary
requirement for the
organisation in this
particular area is
employee retention
and member retention
(Alshaikh et al.,
2016). Both of these
would be extremely
risky if the member
and employee
information is not
secured. Since the
number of members
have increased at an
exponential level for
the organisation
because of its
expansion, the IT
system should be
much more attention
in handling the
business data and
especially the
members data as they
are one of the primary
assets of the
organisation.
Table 1: Risk identification based on IT Control Framework
(Source: Created by the Author)
1.2 Existing industry risk recommendations for the project
ABC fitness gym is trying to implement the IT systems because of the expansion that
it is made over the years. Handling of the business data has become extremely problematic
and this is why they have thought of main requirement to implement information security
systems handling all the constraints of the business. Information security is one of the most
critical areas in a business where protecting the business operation is as essential as

implementing the system for handling the business operations. One of the primary
requirement for enabling information system within an organisation is also looking forward
to handle the information security beforehand. The ways by which information system
implementation is done without out the security for the business information is one of the
primary mistakes that organisations usually conduct (Dhillon, Syed & Pedron, 2016). The
introduction of security risk management for the ABC fitness gym is first and foremost
necessary for implementing the information system within the business process. During the
time of the risk assessment procedure, it might be time consuming for categorical identifying
all the threats and vulnerabilities for every asset included within the organisation but data
mining approach might help to establish a relationship between the threats in the world the
ability and the asset. This would help in finding out a recommendation mechanism that would
help in increasing the risk assessment accuracy with a proper strategy for providing accuracy
to the mitigation strategies as well.
1.3 Mitigate the risks and impact on the organisation
There are several ways to mitigate all the problems and the risk that might impact
ABC fitness gym because of the information security risk that might occur for both the
inventory system and the employee and member information management. The following
would be the risk mitigation strategies for the organisation:
The software should always be kept up to date that has been handling the
information system for the organisation (Soomro, Shah & Ahmed, 2016).
Updating the software is absolutely necessary as the latest versions would be
packed with the most recent security operations from the end of the vendors.
Installing anti-virus protective software is one of the most intelligent
mitigation strategies so that the cyber security risks are protected against. The
software must also be kept up to date show that the latest security patches for
the anti-virus protection software is available to provide maximum service for
identifying, safeguarding and mitigating the cyber security risks.
The critical data regarding the assets of the organisation should be backed up
so that cyber security risk and protection of data would have a system backup
strategy (Hoffmann, Kiedrowicz & Stanik, 2016). It is advisable that all the
senior leadership team of the organisation has a backup of the critical data for
the organisation.
requirement for enabling information system within an organisation is also looking forward
to handle the information security beforehand. The ways by which information system
implementation is done without out the security for the business information is one of the
primary mistakes that organisations usually conduct (Dhillon, Syed & Pedron, 2016). The
introduction of security risk management for the ABC fitness gym is first and foremost
necessary for implementing the information system within the business process. During the
time of the risk assessment procedure, it might be time consuming for categorical identifying
all the threats and vulnerabilities for every asset included within the organisation but data
mining approach might help to establish a relationship between the threats in the world the
ability and the asset. This would help in finding out a recommendation mechanism that would
help in increasing the risk assessment accuracy with a proper strategy for providing accuracy
to the mitigation strategies as well.
1.3 Mitigate the risks and impact on the organisation
There are several ways to mitigate all the problems and the risk that might impact
ABC fitness gym because of the information security risk that might occur for both the
inventory system and the employee and member information management. The following
would be the risk mitigation strategies for the organisation:
The software should always be kept up to date that has been handling the
information system for the organisation (Soomro, Shah & Ahmed, 2016).
Updating the software is absolutely necessary as the latest versions would be
packed with the most recent security operations from the end of the vendors.
Installing anti-virus protective software is one of the most intelligent
mitigation strategies so that the cyber security risks are protected against. The
software must also be kept up to date show that the latest security patches for
the anti-virus protection software is available to provide maximum service for
identifying, safeguarding and mitigating the cyber security risks.
The critical data regarding the assets of the organisation should be backed up
so that cyber security risk and protection of data would have a system backup
strategy (Hoffmann, Kiedrowicz & Stanik, 2016). It is advisable that all the
senior leadership team of the organisation has a backup of the critical data for
the organisation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security training of the employees is extremely necessary so that they might
not typically indulge into you getting to cyber phishing, ransomware attacks,
rootkits, spywares, DNS attacks and other viruses.
The infrastructure should be secured by choosing the appropriate IT
department outsourcing and suppliers so that the network traffic monitoring,
suspicious activity detection, server and application health and multi factor
authentication is implemented.
Every threat should be identified and potential risk mitigation plan at the
initial level should be initiated.
Figure 1: Risk Management and mitigation Decisions
(Source: Stewart & Jürjens, 2017)
2. Protection mechanisms
2.1 Safe guards
There are several security practices that ABC fitness gym can include within the
business so that their information system and sensitive information about the business,
including the employee and member data and information can be protected. Following would
not typically indulge into you getting to cyber phishing, ransomware attacks,
rootkits, spywares, DNS attacks and other viruses.
The infrastructure should be secured by choosing the appropriate IT
department outsourcing and suppliers so that the network traffic monitoring,
suspicious activity detection, server and application health and multi factor
authentication is implemented.
Every threat should be identified and potential risk mitigation plan at the
initial level should be initiated.
Figure 1: Risk Management and mitigation Decisions
(Source: Stewart & Jürjens, 2017)
2. Protection mechanisms
2.1 Safe guards
There are several security practices that ABC fitness gym can include within the
business so that their information system and sensitive information about the business,
including the employee and member data and information can be protected. Following would
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

be a safeguarding strategy developed for ABC fitness gym so that the necessary information
and business confidential data can be protected:
The primary practice of collecting information about the employees and the
members is what is absolutely important for ABC fitness gym to protect. More
information than the necessary data is not required and therefore the data
breach can be saved from occurring if only necessary information are saved.
The limitless of information would make it impossible for the hackers to steal
as all the information would only be saved for the utilisation of running
throughout the business on a day to day basis.
The information inventory about the gym equipment including all the devices
used for storing and transferring the information needs to be protected so that
the information would not be transferred to wrong hands. It needs to be
understood that it is extremely important to keep a track of every information
being stored at and where it is being stored at. The access to all the devices
would also need to be e kept in close proximity and should be recorded.
Access to information should also be limited so that only business executive
has the ability to access all the business information.
The physical document security is extremely important so that all the
documents must be stored in the most secured system with access only to
trusted employees (Carcary et al., 2016). The other necessary physical
documents must be disposed in the form of destructive manner
implementation such that data cannot be recovered from the physical
documents.
A business credit card should be used for pain for all the expenses and the
transactional details that are exchanged from the members to the gym or the
gym to the employees. All remuneration payment to the employees should be
done via bank payment.
Employee fraud must be guarded against so that there would be no threat from
the internal employees about the data being hacked or passed onto some
authorised hacker.
Responses to the data breaches must be planned before hand for providing the
business with maximum protection. Finding out vulnerabilities and acting
immediately through severe investigation is extremely required.
and business confidential data can be protected:
The primary practice of collecting information about the employees and the
members is what is absolutely important for ABC fitness gym to protect. More
information than the necessary data is not required and therefore the data
breach can be saved from occurring if only necessary information are saved.
The limitless of information would make it impossible for the hackers to steal
as all the information would only be saved for the utilisation of running
throughout the business on a day to day basis.
The information inventory about the gym equipment including all the devices
used for storing and transferring the information needs to be protected so that
the information would not be transferred to wrong hands. It needs to be
understood that it is extremely important to keep a track of every information
being stored at and where it is being stored at. The access to all the devices
would also need to be e kept in close proximity and should be recorded.
Access to information should also be limited so that only business executive
has the ability to access all the business information.
The physical document security is extremely important so that all the
documents must be stored in the most secured system with access only to
trusted employees (Carcary et al., 2016). The other necessary physical
documents must be disposed in the form of destructive manner
implementation such that data cannot be recovered from the physical
documents.
A business credit card should be used for pain for all the expenses and the
transactional details that are exchanged from the members to the gym or the
gym to the employees. All remuneration payment to the employees should be
done via bank payment.
Employee fraud must be guarded against so that there would be no threat from
the internal employees about the data being hacked or passed onto some
authorised hacker.
Responses to the data breaches must be planned before hand for providing the
business with maximum protection. Finding out vulnerabilities and acting
immediately through severe investigation is extremely required.

2.2 Tools and technologies
ABC fitness gym can utilise safeguarding of the business information with the
following tools as it will be absolutely e important for protecting the data and information for
the employees and the members including the gym equipment inventory:
Antivirus software programs
Hardware firewall systems
Cloud data storage systems
Email protection systems for helping the organisation fight against phishing
and spam threats
Wi-Fi encryption
Fraud prevention with the help of Card processing
Secured network access
2.3 Culture
The organisation should include the cultural guides within the organisation so that all
the activities that are performed as the day to day business operation by the employees and
the business members would eventually am and protecting the information asset for the
organisation (Safa, Von Solms & Furnell, 2016). The employee behaviour must also be train
that such a way that their activities might at to the organisational goal at protecting the
information about the business, the employee and the member data.
2.4 People
The people within the organisation that are the primary assets comprise of mostly the
employees and the members of the gym (Oppliger, 2015). These people should be trained in
such a way that the day today activities would add to the security of Information and not add
to making the system more vulnerable for hackers to get inside the information system.
3. Recommendations
3.1 Discuss on the principles of IS
Confidentiality: Confidentiality is one of the most important aspects of a
business regarding all the business information including the business,
employee and client information. ABC gym also needs to implement the
above mentioned information security systems so that confidentiality of all the
ABC fitness gym can utilise safeguarding of the business information with the
following tools as it will be absolutely e important for protecting the data and information for
the employees and the members including the gym equipment inventory:
Antivirus software programs
Hardware firewall systems
Cloud data storage systems
Email protection systems for helping the organisation fight against phishing
and spam threats
Wi-Fi encryption
Fraud prevention with the help of Card processing
Secured network access
2.3 Culture
The organisation should include the cultural guides within the organisation so that all
the activities that are performed as the day to day business operation by the employees and
the business members would eventually am and protecting the information asset for the
organisation (Safa, Von Solms & Furnell, 2016). The employee behaviour must also be train
that such a way that their activities might at to the organisational goal at protecting the
information about the business, the employee and the member data.
2.4 People
The people within the organisation that are the primary assets comprise of mostly the
employees and the members of the gym (Oppliger, 2015). These people should be trained in
such a way that the day today activities would add to the security of Information and not add
to making the system more vulnerable for hackers to get inside the information system.
3. Recommendations
3.1 Discuss on the principles of IS
Confidentiality: Confidentiality is one of the most important aspects of a
business regarding all the business information including the business,
employee and client information. ABC gym also needs to implement the
above mentioned information security systems so that confidentiality of all the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

business data including the client and employee data are stored to be kept
confidential.
Integrity: Integrity is extremely required for every business organisation
regarding the business data as redundancy for mismanagement in handling the
integrity of data would result in to wrong business and data forecasting. This
would result into to the loss of reputation for the business because of the
wrong steps taken towards the future.
Availability: The availability of information is extremely required because as
it has been mentioned above, extra information collection leads to
management issues in handling the required information. Therefore the
recommendation as me the above to reduce the collection of data only to the
necessary information to be told would make the information system be much
more flexible and available for the day to day requirements of the business
operations.
As it has been recommended as above, all these would be extremely necessary to
handle the business information that has now become huge in number because of the
expansion of ABC fitness gym. Proper maintenance of all the business data would ensure that
the business thinks about restoring the integrity, confidentiality and availability of the
information which forms the most important asset for the organisation other than the
monetary capital assets. This should ensure that the business has been thinking about
expanding its reputation for providing the best possible solution to the clients regarding
information system vulnerability.
confidential.
Integrity: Integrity is extremely required for every business organisation
regarding the business data as redundancy for mismanagement in handling the
integrity of data would result in to wrong business and data forecasting. This
would result into to the loss of reputation for the business because of the
wrong steps taken towards the future.
Availability: The availability of information is extremely required because as
it has been mentioned above, extra information collection leads to
management issues in handling the required information. Therefore the
recommendation as me the above to reduce the collection of data only to the
necessary information to be told would make the information system be much
more flexible and available for the day to day requirements of the business
operations.
As it has been recommended as above, all these would be extremely necessary to
handle the business information that has now become huge in number because of the
expansion of ABC fitness gym. Proper maintenance of all the business data would ensure that
the business thinks about restoring the integrity, confidentiality and availability of the
information which forms the most important asset for the organisation other than the
monetary capital assets. This should ensure that the business has been thinking about
expanding its reputation for providing the best possible solution to the clients regarding
information system vulnerability.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
AlHogail, A. (2015). Design and validation of information security culture
framework. Computers in Human Behavior, 49, 567-575.
Alshaikh, M., Maynard, S. B., Ahmad, A., & Chang, S. (2016). Information Security Policy:
A Management Practice Perspective. arXiv preprint arXiv:1606.00890.
Carcary, M., Renaud, K., McLaughlin, S., & O'Brien, C. (2016). A framework for
information security governance and management. It Professional, 18(2), 22-30.
Dhillon, G., Syed, R., & Pedron, C. (2016). Interpreting information security culture: An
organizational transformation case study. Computers & Security, 56, 63-69.
Hoffmann, R., Kiedrowicz, M., & Stanik, J. (2016). Risk management system as the basic
paradigm of the information security management system in an organization.
In MATEC Web of Conferences (Vol. 76, p. 04010). EDP Sciences.
Oppliger, R. (2015). Quantitative risk analysis in information security management: a modern
fairy tale. IEEE Security & Privacy, 13(6), 18-21.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. computers & security, 56, 70-82.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Stewart, H., & Jürjens, J. (2017). Information security management and the human aspect in
organizations. Information & Computer Security, 25(5), 494-534.
AlHogail, A. (2015). Design and validation of information security culture
framework. Computers in Human Behavior, 49, 567-575.
Alshaikh, M., Maynard, S. B., Ahmad, A., & Chang, S. (2016). Information Security Policy:
A Management Practice Perspective. arXiv preprint arXiv:1606.00890.
Carcary, M., Renaud, K., McLaughlin, S., & O'Brien, C. (2016). A framework for
information security governance and management. It Professional, 18(2), 22-30.
Dhillon, G., Syed, R., & Pedron, C. (2016). Interpreting information security culture: An
organizational transformation case study. Computers & Security, 56, 63-69.
Hoffmann, R., Kiedrowicz, M., & Stanik, J. (2016). Risk management system as the basic
paradigm of the information security management system in an organization.
In MATEC Web of Conferences (Vol. 76, p. 04010). EDP Sciences.
Oppliger, R. (2015). Quantitative risk analysis in information security management: a modern
fairy tale. IEEE Security & Privacy, 13(6), 18-21.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. computers & security, 56, 70-82.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Stewart, H., & Jürjens, J. (2017). Information security management and the human aspect in
organizations. Information & Computer Security, 25(5), 494-534.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



