Technical Risk Analysis Documentation: Software Development Project
VerifiedAdded on 2023/04/21
|12
|2321
|149
Report
AI Summary
This report provides a comprehensive technical risk analysis for an innovative software development project. It identifies key threats such as social engineering attacks, disclosure of critical business information, unauthorized system access, loss of user data, and accidental human errors. Each risk is assessed for its impact and likelihood, leading to a prioritized risk rating. The report details specific risk mitigation strategies, assigning responsibility for each action and outlining the expected impact on the organization. Protection mechanisms are discussed, including limiting data access, identifying sensitive data, planning security policies, enforcing strong password standards, and implementing regular data backups. A gap analysis highlights the omission of project management-related risks (time, cost, scope), underscoring the need for a more holistic risk assessment. The report concludes that mitigation is the most suitable strategy, emphasizing the importance of security policies to ensure data integrity and project success. Desklib offers a platform to explore this and similar documents.

Running head: TECHNICAL RISK ANALYSIS
Technical Risk Analysis Documentation
Student Name:
University Name:
Technical Risk Analysis Documentation
Student Name:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1TECHNICAL RISK ANALYSIS
Executive Summary
This report focuses on risk analysis and management related to a project for innovative
software development by an organization. In this report, the key threats associated with the
project has been identified that are required to be mitigated for achieving the desired
requirements. The risks have been determined from present situation of the organization
which demonstrates that the project may be compromised or fail due to lack of proper
security measures. The software development project may be affected due to IT infrastructure
existing in the organization. It has been identified that the implementation of suitable security
policies will help to ensure successful completion of the project. Apart from that, it is
recommended that the organization should monitor and keep track of the employees activities
so that the project is successful.
Executive Summary
This report focuses on risk analysis and management related to a project for innovative
software development by an organization. In this report, the key threats associated with the
project has been identified that are required to be mitigated for achieving the desired
requirements. The risks have been determined from present situation of the organization
which demonstrates that the project may be compromised or fail due to lack of proper
security measures. The software development project may be affected due to IT infrastructure
existing in the organization. It has been identified that the implementation of suitable security
policies will help to ensure successful completion of the project. Apart from that, it is
recommended that the organization should monitor and keep track of the employees activities
so that the project is successful.

2TECHNICAL RISK ANALYSIS
Table of Contents
Introduction................................................................................................................................3
Identification and discussion on key threats..............................................................................3
Assessment and evaluation of the risks......................................................................................4
Risk mitigation and impact on the organization........................................................................5
Summary of the protection mechanisms....................................................................................6
Gap analysis and rationale.........................................................................................................8
Conclusion..................................................................................................................................9
References................................................................................................................................10
Table of Contents
Introduction................................................................................................................................3
Identification and discussion on key threats..............................................................................3
Assessment and evaluation of the risks......................................................................................4
Risk mitigation and impact on the organization........................................................................5
Summary of the protection mechanisms....................................................................................6
Gap analysis and rationale.........................................................................................................8
Conclusion..................................................................................................................................9
References................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3TECHNICAL RISK ANALYSIS
Introduction
In this report, the risks associated with a project on innovative software development
by an organization has been analysed to ensure achievement of quality deliverables. The key
threats related to the project has been presented in this report. Further, mitigation strategies
for the identified risks has been presented in this report along with impact on the
organization. The risks have to be mitigated with the help of proper mitigation strategies.
Some protection mechanisms are also discussed in this report to ensure that the project is
completed following the security requirements. A gap analysis has also been carried out to
present the areas in which further analysis is required for successful completion of the
project.
Identification and discussion on key threats
The key threats that has been identified in context to the project on innovative
software development are presented as below:
Social engineering attacks – It refers to the cyber security threats that may gain access
to the system or affect data contained in the servers.
Disclosure of critical business information – It relates to exposure of vital information
about the business thus affecting the entire project (Peltier, 2016).
Unauthorized access to the system – External attackers may steal the documentation
or codes of the software being developed as most of the data is stored on servers that is
publicly available through internet.
Loss or theft of user data – The attackers or insiders may gain access to the individual
data of the employees or customers which could be used to exploit the servers of the
organization (Soomro, Shah & Ahmed, 2016).
Introduction
In this report, the risks associated with a project on innovative software development
by an organization has been analysed to ensure achievement of quality deliverables. The key
threats related to the project has been presented in this report. Further, mitigation strategies
for the identified risks has been presented in this report along with impact on the
organization. The risks have to be mitigated with the help of proper mitigation strategies.
Some protection mechanisms are also discussed in this report to ensure that the project is
completed following the security requirements. A gap analysis has also been carried out to
present the areas in which further analysis is required for successful completion of the
project.
Identification and discussion on key threats
The key threats that has been identified in context to the project on innovative
software development are presented as below:
Social engineering attacks – It refers to the cyber security threats that may gain access
to the system or affect data contained in the servers.
Disclosure of critical business information – It relates to exposure of vital information
about the business thus affecting the entire project (Peltier, 2016).
Unauthorized access to the system – External attackers may steal the documentation
or codes of the software being developed as most of the data is stored on servers that is
publicly available through internet.
Loss or theft of user data – The attackers or insiders may gain access to the individual
data of the employees or customers which could be used to exploit the servers of the
organization (Soomro, Shah & Ahmed, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4TECHNICAL RISK ANALYSIS
Accidental threats or human errors – It relates to installation of any harmful
application by the employees or mishandling of data could result into access to servers of the
organization.
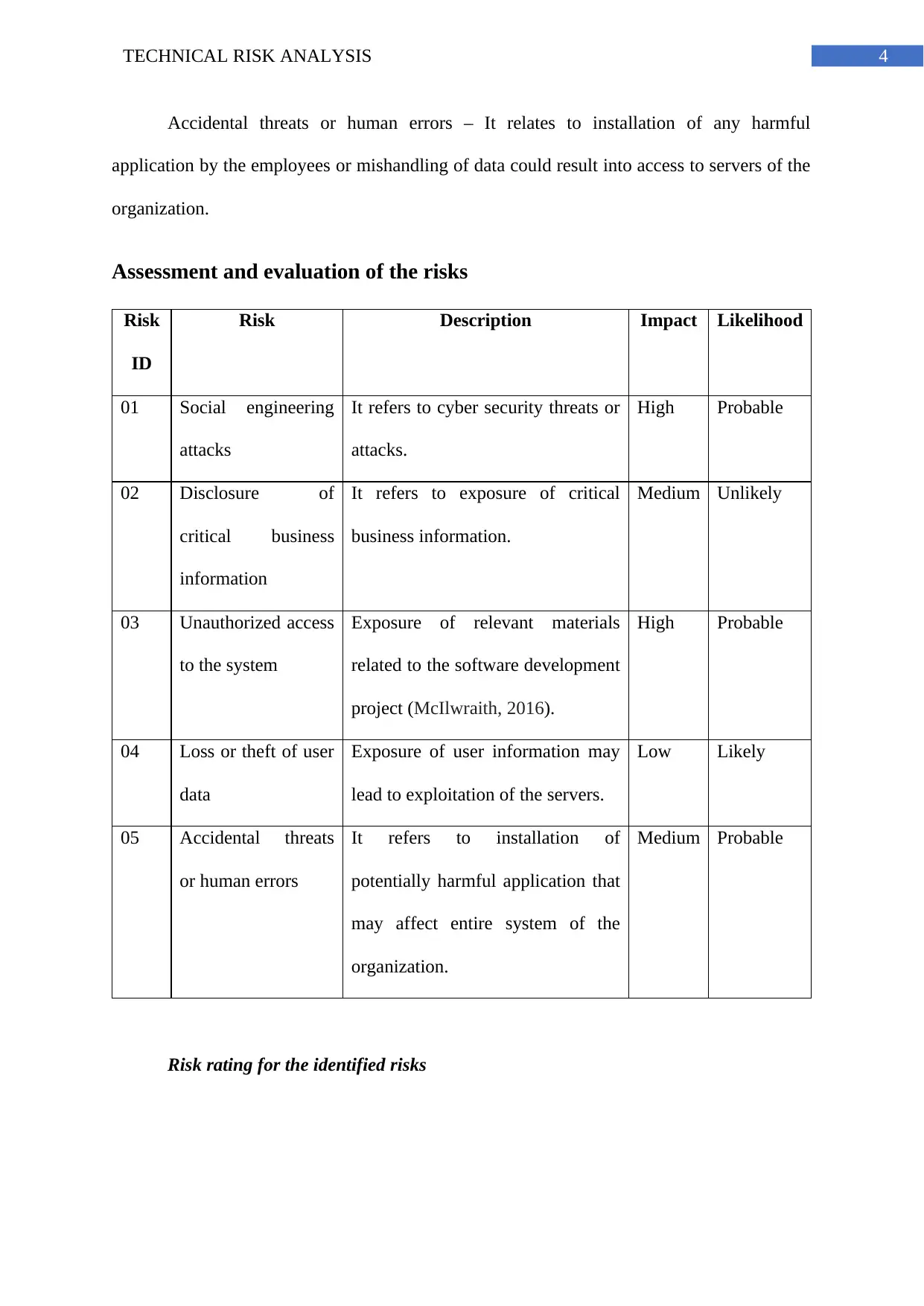
Assessment and evaluation of the risks
Risk
ID
Risk Description Impact Likelihood
01 Social engineering
attacks
It refers to cyber security threats or
attacks.
High Probable
02 Disclosure of
critical business
information
It refers to exposure of critical
business information.
Medium Unlikely
03 Unauthorized access
to the system
Exposure of relevant materials
related to the software development
project (McIlwraith, 2016).
High Probable
04 Loss or theft of user
data
Exposure of user information may
lead to exploitation of the servers.
Low Likely
05 Accidental threats
or human errors
It refers to installation of
potentially harmful application that
may affect entire system of the
organization.
Medium Probable
Risk rating for the identified risks
Accidental threats or human errors – It relates to installation of any harmful
application by the employees or mishandling of data could result into access to servers of the
organization.
Assessment and evaluation of the risks
Risk
ID
Risk Description Impact Likelihood
01 Social engineering
attacks
It refers to cyber security threats or
attacks.
High Probable
02 Disclosure of
critical business
information
It refers to exposure of critical
business information.
Medium Unlikely
03 Unauthorized access
to the system
Exposure of relevant materials
related to the software development
project (McIlwraith, 2016).
High Probable
04 Loss or theft of user
data
Exposure of user information may
lead to exploitation of the servers.
Low Likely
05 Accidental threats
or human errors
It refers to installation of
potentially harmful application that
may affect entire system of the
organization.
Medium Probable
Risk rating for the identified risks
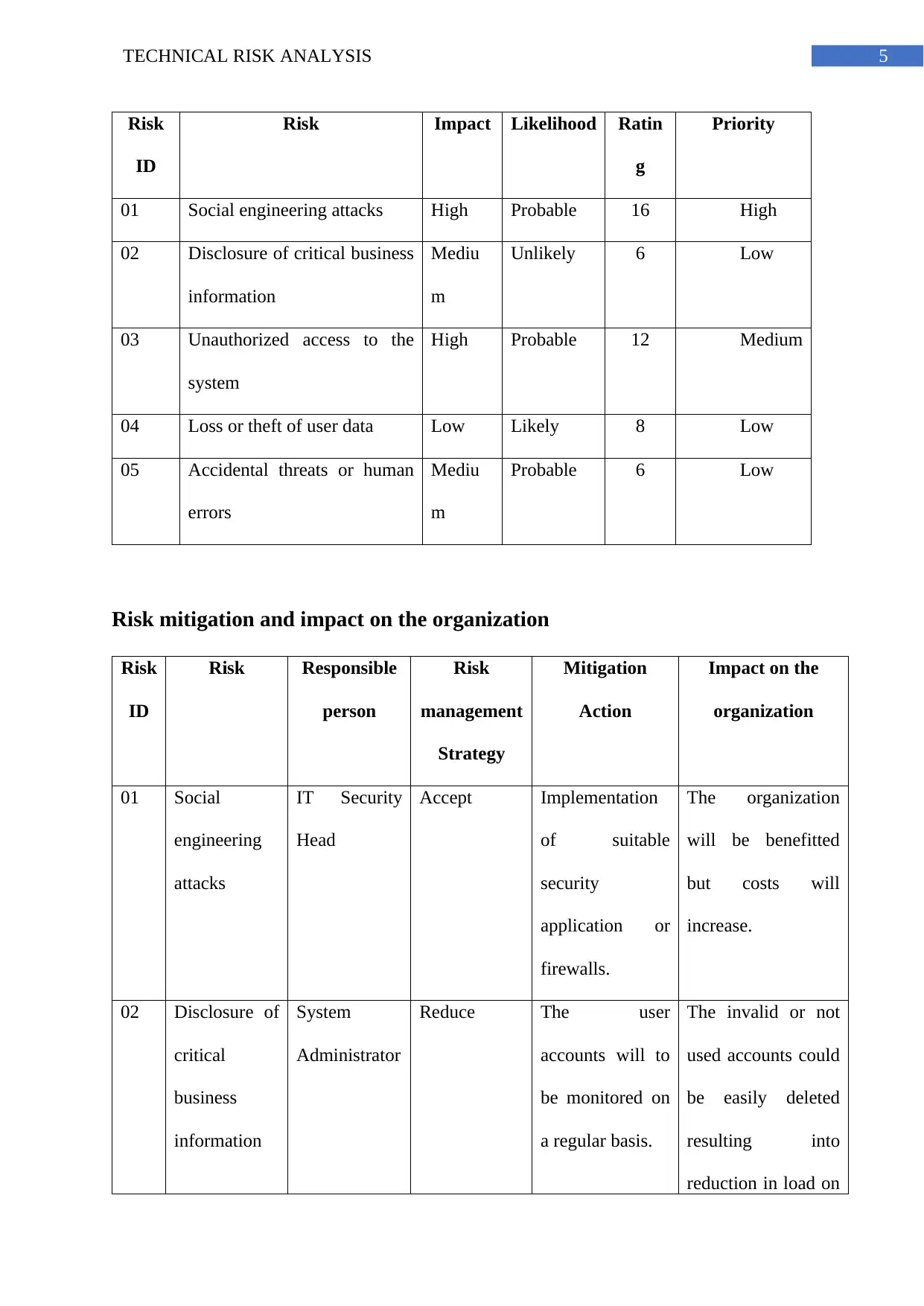
5TECHNICAL RISK ANALYSIS
Risk
ID
Risk Impact Likelihood Ratin
g
Priority
01 Social engineering attacks High Probable 16 High
02 Disclosure of critical business
information
Mediu
m
Unlikely 6 Low
03 Unauthorized access to the
system
High Probable 12 Medium
04 Loss or theft of user data Low Likely 8 Low
05 Accidental threats or human
errors
Mediu
m
Probable 6 Low
Risk mitigation and impact on the organization
Risk
ID
Risk Responsible
person
Risk
management
Strategy
Mitigation
Action
Impact on the
organization
01 Social
engineering
attacks
IT Security
Head
Accept Implementation
of suitable
security
application or
firewalls.
The organization
will be benefitted
but costs will
increase.
02 Disclosure of
critical
business
information
System
Administrator
Reduce The user
accounts will to
be monitored on
a regular basis.
The invalid or not
used accounts could
be easily deleted
resulting into
reduction in load on
Risk
ID
Risk Impact Likelihood Ratin
g
Priority
01 Social engineering attacks High Probable 16 High
02 Disclosure of critical business
information
Mediu
m
Unlikely 6 Low
03 Unauthorized access to the
system
High Probable 12 Medium
04 Loss or theft of user data Low Likely 8 Low
05 Accidental threats or human
errors
Mediu
m
Probable 6 Low
Risk mitigation and impact on the organization
Risk
ID
Risk Responsible
person
Risk
management
Strategy
Mitigation
Action
Impact on the
organization
01 Social
engineering
attacks
IT Security
Head
Accept Implementation
of suitable
security
application or
firewalls.
The organization
will be benefitted
but costs will
increase.
02 Disclosure of
critical
business
information
System
Administrator
Reduce The user
accounts will to
be monitored on
a regular basis.
The invalid or not
used accounts could
be easily deleted
resulting into
reduction in load on
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
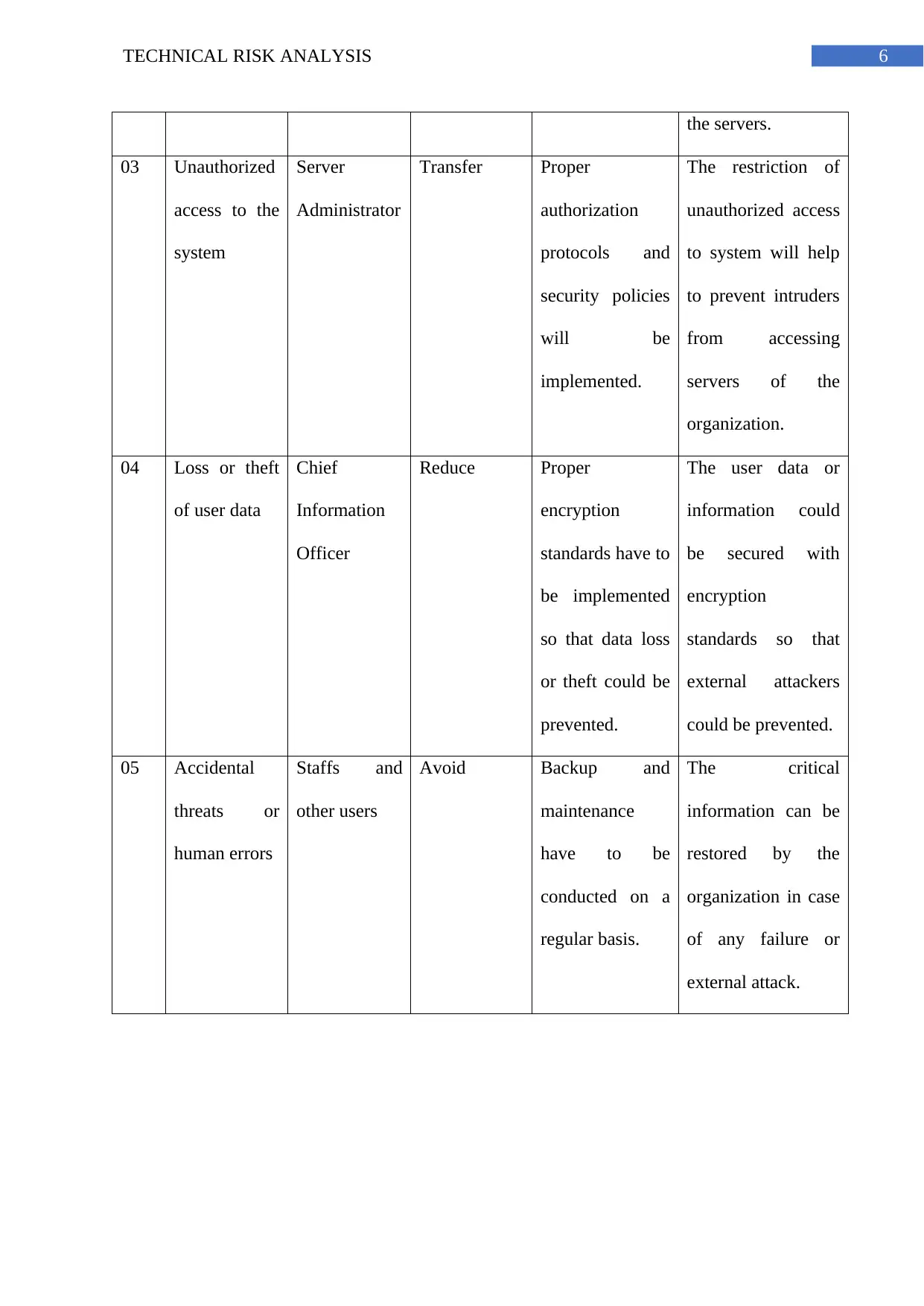
6TECHNICAL RISK ANALYSIS
the servers.
03 Unauthorized
access to the
system
Server
Administrator
Transfer Proper
authorization
protocols and
security policies
will be
implemented.
The restriction of
unauthorized access
to system will help
to prevent intruders
from accessing
servers of the
organization.
04 Loss or theft
of user data
Chief
Information
Officer
Reduce Proper
encryption
standards have to
be implemented
so that data loss
or theft could be
prevented.
The user data or
information could
be secured with
encryption
standards so that
external attackers
could be prevented.
05 Accidental
threats or
human errors
Staffs and
other users
Avoid Backup and
maintenance
have to be
conducted on a
regular basis.
The critical
information can be
restored by the
organization in case
of any failure or
external attack.
the servers.
03 Unauthorized
access to the
system
Server
Administrator
Transfer Proper
authorization
protocols and
security policies
will be
implemented.
The restriction of
unauthorized access
to system will help
to prevent intruders
from accessing
servers of the
organization.
04 Loss or theft
of user data
Chief
Information
Officer
Reduce Proper
encryption
standards have to
be implemented
so that data loss
or theft could be
prevented.
The user data or
information could
be secured with
encryption
standards so that
external attackers
could be prevented.
05 Accidental
threats or
human errors
Staffs and
other users
Avoid Backup and
maintenance
have to be
conducted on a
regular basis.
The critical
information can be
restored by the
organization in case
of any failure or
external attack.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7TECHNICAL RISK ANALYSIS
Summary of the protection mechanisms
The protection mechanisms that could be applied in the organization to ensure
integrity and confidentiality of information in context to the innovative software development
project are listed below:
Limitation to data access – Presently, most of the organizations give privileged access
to critical business information for specific people and insiders. However, in the organization
carrying out the project there is no restriction to data access and the users could access the
servers publicly anywhere through internet. The access rights of the employees have to be
divided according to the user level and their position in the organization (Layton, 2016). The
access to sensitive data for every employee in the organization may lead to data loss, theft or
hijacking entire system of the organization. Therefore, limiting the access rights will help in
effective management of their data.
Identification of sensitive data – The organization should be able to identify the data
that is important for them and the information that is critical for the business. It will help to
determine the right information so that resources could be allocated properly for protection of
the sensitive and crucial information (Safa & Von Solms, 2016). The sensitive data should be
kept secure with the help of proper authentication and authorization protocols. The security of
the business sensitive data will be ensured through strict measures and security policies.
Planning of security policy – A security plan or certain policies have to be developed
so that critical situations could be avoided. The development of a security policy will help to
address the issues with data access and management rights of the users. The policy will
comprise of the points that have to be followed and maintained during handling of data
within the organization (Burns et al., 2017). The security policy will include the do’s and
Summary of the protection mechanisms
The protection mechanisms that could be applied in the organization to ensure
integrity and confidentiality of information in context to the innovative software development
project are listed below:
Limitation to data access – Presently, most of the organizations give privileged access
to critical business information for specific people and insiders. However, in the organization
carrying out the project there is no restriction to data access and the users could access the
servers publicly anywhere through internet. The access rights of the employees have to be
divided according to the user level and their position in the organization (Layton, 2016). The
access to sensitive data for every employee in the organization may lead to data loss, theft or
hijacking entire system of the organization. Therefore, limiting the access rights will help in
effective management of their data.
Identification of sensitive data – The organization should be able to identify the data
that is important for them and the information that is critical for the business. It will help to
determine the right information so that resources could be allocated properly for protection of
the sensitive and crucial information (Safa & Von Solms, 2016). The sensitive data should be
kept secure with the help of proper authentication and authorization protocols. The security of
the business sensitive data will be ensured through strict measures and security policies.
Planning of security policy – A security plan or certain policies have to be developed
so that critical situations could be avoided. The development of a security policy will help to
address the issues with data access and management rights of the users. The policy will
comprise of the points that have to be followed and maintained during handling of data
within the organization (Burns et al., 2017). The security policy will include the do’s and

8TECHNICAL RISK ANALYSIS
don’ts for users accessing systems of the organization. The policy will also ensure that data
integrity and confidentiality is maintained within the organization.
Strong and different password standards – The business sensitive data will be locked
with the help of strong passwords or other encryption standards which could be accessed by
authorized users only (AlHogail, 2015). The different departments will be provided with
separate passwords for accessing the critical business information. Further, the individual
users of the system will have different passwords for accessing their workstation. The
organization should use unique passwords for the employees as well as administrative staffs
so that user access could be restricted according to their level of authorization. The
implementation of encryption standards will help to ensure security and confidentiality
during data transmission or transaction carried out within the organization.
Regular data backup and update – It is one of the important security measure that will
include security checks on a regular basis and backup of data regularly. It will help the
organization to prevent data loss as the data could be retrieved and restored from backup
(Sandberg, Amin & Johansson, 2015). Further, the systems being used in the organization
have to be updated on a regular basis through security applications.
It is important that cyber security risks should identified and evaluated on a regular
basis to stay updated on the recent advancements in information security threats or
vulnerabilities. The application of suitable strategies will help to maintain the data integrity
and confidentiality within the organization. The mitigation of security risks and maintenance
of security policies will help to ensure successful business growth of the organization. The
implementation of proper security measures is essential to maintain good business
relationship with the customers.
don’ts for users accessing systems of the organization. The policy will also ensure that data
integrity and confidentiality is maintained within the organization.
Strong and different password standards – The business sensitive data will be locked
with the help of strong passwords or other encryption standards which could be accessed by
authorized users only (AlHogail, 2015). The different departments will be provided with
separate passwords for accessing the critical business information. Further, the individual
users of the system will have different passwords for accessing their workstation. The
organization should use unique passwords for the employees as well as administrative staffs
so that user access could be restricted according to their level of authorization. The
implementation of encryption standards will help to ensure security and confidentiality
during data transmission or transaction carried out within the organization.
Regular data backup and update – It is one of the important security measure that will
include security checks on a regular basis and backup of data regularly. It will help the
organization to prevent data loss as the data could be retrieved and restored from backup
(Sandberg, Amin & Johansson, 2015). Further, the systems being used in the organization
have to be updated on a regular basis through security applications.
It is important that cyber security risks should identified and evaluated on a regular
basis to stay updated on the recent advancements in information security threats or
vulnerabilities. The application of suitable strategies will help to maintain the data integrity
and confidentiality within the organization. The mitigation of security risks and maintenance
of security policies will help to ensure successful business growth of the organization. The
implementation of proper security measures is essential to maintain good business
relationship with the customers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9TECHNICAL RISK ANALYSIS
Gap analysis and rationale
The major gap is that the factors related to project management has not been
considered in this risk analysis. The important aspects that may affect the project that is
Time, Cost and Scope risks has not been analysed in this report. However, it is essential that
the risks related to project management aspects should be also analysed to ensure successful
completion of the project. The risks associated with time, cost or scope of a project could
have an adverse impact on the time or budget for completing the project. Hence, it is vital
that those risks should be also identified and analysed at an early stage for successful
achievement of the desired goals and objectives from the project. The analysis of those risks
prior to execution of the project will help to implement suitable strategies for risk mitigation
and fulfilment of the desired requirements.
Conclusion
From the overall discussions carried out in this report, it can be concluded that
mitigation is the most suitable strategy for successful completion of the project. The risks
identified in this report could be mitigated with the help of proper security measures to ensure
success of the project. The risks being identified have been prioritized according to the rating
calculated from impact and likelihood. Various risk management strategies have been applied
for the different types of risks identified in context to the project. The person who will be
associated with mitigation of the identified risks has been presented in this report so that the
risks can be mitigated efficiently. Further, it is recommended that implementation of security
policies will help to ensure integrity and confidentiality of data within the organization.
Gap analysis and rationale
The major gap is that the factors related to project management has not been
considered in this risk analysis. The important aspects that may affect the project that is
Time, Cost and Scope risks has not been analysed in this report. However, it is essential that
the risks related to project management aspects should be also analysed to ensure successful
completion of the project. The risks associated with time, cost or scope of a project could
have an adverse impact on the time or budget for completing the project. Hence, it is vital
that those risks should be also identified and analysed at an early stage for successful
achievement of the desired goals and objectives from the project. The analysis of those risks
prior to execution of the project will help to implement suitable strategies for risk mitigation
and fulfilment of the desired requirements.
Conclusion
From the overall discussions carried out in this report, it can be concluded that
mitigation is the most suitable strategy for successful completion of the project. The risks
identified in this report could be mitigated with the help of proper security measures to ensure
success of the project. The risks being identified have been prioritized according to the rating
calculated from impact and likelihood. Various risk management strategies have been applied
for the different types of risks identified in context to the project. The person who will be
associated with mitigation of the identified risks has been presented in this report so that the
risks can be mitigated efficiently. Further, it is recommended that implementation of security
policies will help to ensure integrity and confidentiality of data within the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10TECHNICAL RISK ANALYSIS
References
AlHogail, A. (2015). Design and validation of information security culture
framework. Computers in Human Behavior, 49, 567-575.
Burns, A. J., Posey, C., Courtney, J. F., Roberts, T. L., & Nanayakkara, P. (2017).
Organizational information security as a complex adaptive system: insights from three
agent-based models. Information Systems Frontiers, 19(3), 509-524.
Carcary, M., Renaud, K., McLaughlin, S., & O'Brien, C. (2016). A Framework for
Information Security Governance and Management. IT Professional, 18(2), 22-30.
Da Veiga, A., & Martins, N. (2015). Improving the information security culture through
monitoring and implementation actions illustrated through a case study. Computers &
Security, 49, 162-176.
Layton, T. P. (2016). Information Security: Design, implementation, measurement, and
compliance. Auerbach Publications.
McIlwraith, A. (2016). Information security and employee behaviour: how to reduce risk
through employee education, training and awareness. Routledge.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Safa, N. S., & Von Solms, R. (2016). An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, 442-451.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. Computers & Security, 56, 70-82.
References
AlHogail, A. (2015). Design and validation of information security culture
framework. Computers in Human Behavior, 49, 567-575.
Burns, A. J., Posey, C., Courtney, J. F., Roberts, T. L., & Nanayakkara, P. (2017).
Organizational information security as a complex adaptive system: insights from three
agent-based models. Information Systems Frontiers, 19(3), 509-524.
Carcary, M., Renaud, K., McLaughlin, S., & O'Brien, C. (2016). A Framework for
Information Security Governance and Management. IT Professional, 18(2), 22-30.
Da Veiga, A., & Martins, N. (2015). Improving the information security culture through
monitoring and implementation actions illustrated through a case study. Computers &
Security, 49, 162-176.
Layton, T. P. (2016). Information Security: Design, implementation, measurement, and
compliance. Auerbach Publications.
McIlwraith, A. (2016). Information security and employee behaviour: how to reduce risk
through employee education, training and awareness. Routledge.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Safa, N. S., & Von Solms, R. (2016). An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, 442-451.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. Computers & Security, 56, 70-82.

11TECHNICAL RISK ANALYSIS
Sandberg, H., Amin, S., & Johansson, K. H. (2015). Cyberphysical security in networked
control systems: An introduction to the issue. IEEE Control Systems, 35(1), 20-23.
Singhal, A., & Ou, X. (2017). Security risk analysis of enterprise networks using probabilistic
attack graphs. In Network Security Metrics (pp. 53-73). Springer, Cham.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Sandberg, H., Amin, S., & Johansson, K. H. (2015). Cyberphysical security in networked
control systems: An introduction to the issue. IEEE Control Systems, 35(1), 20-23.
Singhal, A., & Ou, X. (2017). Security risk analysis of enterprise networks using probabilistic
attack graphs. In Network Security Metrics (pp. 53-73). Springer, Cham.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




