Arden University: Technology in Organizations Report (COM0006NFBNM)
VerifiedAdded on 2022/12/07
|12
|3844
|383
Report
AI Summary
This report examines the role of technology in modern organizations, focusing on big data applications, IT security, and telecommunications. It begins with an introduction highlighting technology's importance for information management, record-keeping, and operational efficiency. The report includes a case study on Big Data's implementation at Arden University, exploring its benefits such as targeted student scholarships, personalized curriculum development, and operational cost savings. It also delves into IT security and data privacy measures, detailing the importance of firewalls, intrusion detection systems, and the provisions of GDPR. Furthermore, the report discusses cellular networks, their components, benefits to businesses, and concludes with an overview of spreadsheet applications. The report provides a comprehensive analysis of technology's impact on organizational practices and strategies.

Technology In Organisation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION...........................................................................................................................1
Question 1: Case study and questions.............................................................................................1
Big Data and its role in Arden University...................................................................................1
Key benefits to Arden University gets after adopting Big Data..................................................3
Question 2 – Security and Privacy...................................................................................................4
Explain the IT security and data privacy measures that an organisation must implement along
with provisions of GDPR.............................................................................................................4
Question 3 Telecommunication and spreadsheets...........................................................................6
A) Describe a cellular network, its principle components and how it works.........................6
B) Explain the benefits of a cellular network to a business....................................................7
C) Spreadsheet.............................................................................................................................8
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10
INTRODUCTION...........................................................................................................................1
Question 1: Case study and questions.............................................................................................1
Big Data and its role in Arden University...................................................................................1
Key benefits to Arden University gets after adopting Big Data..................................................3
Question 2 – Security and Privacy...................................................................................................4
Explain the IT security and data privacy measures that an organisation must implement along
with provisions of GDPR.............................................................................................................4
Question 3 Telecommunication and spreadsheets...........................................................................6
A) Describe a cellular network, its principle components and how it works.........................6
B) Explain the benefits of a cellular network to a business....................................................7
C) Spreadsheet.............................................................................................................................8
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10

INTRODUCTION
Technology is essential for entity as this assists them to keep information, maintain records,
smoothening functioning of practices, secure data and others. Moreover, there are various
technologies adapted through firms in order to manage information as well as executing
activities also. The topics which are going to be discussed in this report are explaination of big
data and their roles into Arden University, main advantages firm like Arden university obtain
after adapting big data. Moreover, IT seciruty and data privacy measures that entity should
implement are also explained. Apart from this, description about cellular network, their principle
elements, how this performs, and benefits of cellular network to business are also discussed in
this report.
Question 1: Case study and questions
Big Data and its role in Arden University.
Data is undertaken as set of characters, symbols or numbers which may be stored as well
as conveyedas e-sihnals and recorded uponoptical, magnetic or mechanical media through
computer. Moreover, this is also the huge accoumulation of information which develops
exponential overtime goes on. In addition to this, it is a huge as well as difficult information
collection that no traditional data processing system and may be effectively store or processed.
In addition to this, continuous information is same as big data, but this is much larger to putting
other manner, big data is undertaken as a range of structured, semi- structured as well as
unstructured information from firm which may nbe minded for understanding as well as utilised
into advanced analytica projects such as machine learning as well as anticipative modelling.
Benefits of Big data
Regulates efffectuaal task of firm: Big data allows firms for becoming much consumer centric.
Historical as well as real time infromaation may be utilised for measuring customer desires,
aassistsing usiness for updating as well as refining its its marketing campaaignes and become
much attentive to clients expectation and requirements. In context to to respective firm,
managers consider utilisation of big data in order to regulate operative affairs of entities.
Additionally, it aids to regulate effectual task being generated within firm as well as alos
contributes their valuable contribution towards effectual productivity of firm as whole.
1
Technology is essential for entity as this assists them to keep information, maintain records,
smoothening functioning of practices, secure data and others. Moreover, there are various
technologies adapted through firms in order to manage information as well as executing
activities also. The topics which are going to be discussed in this report are explaination of big
data and their roles into Arden University, main advantages firm like Arden university obtain
after adapting big data. Moreover, IT seciruty and data privacy measures that entity should
implement are also explained. Apart from this, description about cellular network, their principle
elements, how this performs, and benefits of cellular network to business are also discussed in
this report.
Question 1: Case study and questions
Big Data and its role in Arden University.
Data is undertaken as set of characters, symbols or numbers which may be stored as well
as conveyedas e-sihnals and recorded uponoptical, magnetic or mechanical media through
computer. Moreover, this is also the huge accoumulation of information which develops
exponential overtime goes on. In addition to this, it is a huge as well as difficult information
collection that no traditional data processing system and may be effectively store or processed.
In addition to this, continuous information is same as big data, but this is much larger to putting
other manner, big data is undertaken as a range of structured, semi- structured as well as
unstructured information from firm which may nbe minded for understanding as well as utilised
into advanced analytica projects such as machine learning as well as anticipative modelling.
Benefits of Big data
Regulates efffectuaal task of firm: Big data allows firms for becoming much consumer centric.
Historical as well as real time infromaation may be utilised for measuring customer desires,
aassistsing usiness for updating as well as refining its its marketing campaaignes and become
much attentive to clients expectation and requirements. In context to to respective firm,
managers consider utilisation of big data in order to regulate operative affairs of entities.
Additionally, it aids to regulate effectual task being generated within firm as well as alos
contributes their valuable contribution towards effectual productivity of firm as whole.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Other industry: Big data is utilised through health researchers aas well as doctors for categorising
dieases risk fators as well as determining diseases and disorders into specific patients. Along
with this, the data derived from e-health records (EHRS), social media, internet and other
sources provides real time data uppn inflections disease risk as well as outbreaks to health care
facilities as well as government agencies.
Role of big data in Arden University
Target student scholarship: Arden University would recognise effective students through
providing them a test for tht it should score amount of point that would be undertaken for
scholarship. In addition to this, bidg data can be also utilised through firms for evaluating a
student’s last performance, respect to school or college they attended. In addition to this, these
methods can aids enterprise to recognise students who are much likely for sticking around into
school or college. Additionally, for institutions’ scho;airship funds, respective solution would
have higher return on investment.
Looking attention to those students who requireds the most: After the information have been
expandly evauated, this may be utilised for detrmining students who would required much
attention at the time of regular school tasks, like homework in comparision to others who would
unquestionable progressed into its carees of academics. Additionally, these activities, however,
rise of ethical questions related to either accumulating respective form of information upon
students infringes upon its privacy while also allowing students to be assisted into various
manners.
Reasess curriculum: Whole information accumulated as well a stored would aaids firm develops
aapersonalised programmes for every student. Moreover, big data also enables for specialisation
when university or college have 10,000 of students. In aaddition to this, belended learning tht
relates online as well as offline learning, is what university aare seeking for while performing
into particular market area.
Organising customised programmes for students: For arranging customised programmes outside
or inside university, big data may prove to be effectual techniques. Moreover, this has their vital
role into organising efficacious session in context with several university sessions that are
arranged through institute themself. In addition to this, it shortens ways for administration as
well as obviates dduplication of potential being generated during courses.
2
dieases risk fators as well as determining diseases and disorders into specific patients. Along
with this, the data derived from e-health records (EHRS), social media, internet and other
sources provides real time data uppn inflections disease risk as well as outbreaks to health care
facilities as well as government agencies.
Role of big data in Arden University
Target student scholarship: Arden University would recognise effective students through
providing them a test for tht it should score amount of point that would be undertaken for
scholarship. In addition to this, bidg data can be also utilised through firms for evaluating a
student’s last performance, respect to school or college they attended. In addition to this, these
methods can aids enterprise to recognise students who are much likely for sticking around into
school or college. Additionally, for institutions’ scho;airship funds, respective solution would
have higher return on investment.
Looking attention to those students who requireds the most: After the information have been
expandly evauated, this may be utilised for detrmining students who would required much
attention at the time of regular school tasks, like homework in comparision to others who would
unquestionable progressed into its carees of academics. Additionally, these activities, however,
rise of ethical questions related to either accumulating respective form of information upon
students infringes upon its privacy while also allowing students to be assisted into various
manners.
Reasess curriculum: Whole information accumulated as well a stored would aaids firm develops
aapersonalised programmes for every student. Moreover, big data also enables for specialisation
when university or college have 10,000 of students. In aaddition to this, belended learning tht
relates online as well as offline learning, is what university aare seeking for while performing
into particular market area.
Organising customised programmes for students: For arranging customised programmes outside
or inside university, big data may prove to be effectual techniques. Moreover, this has their vital
role into organising efficacious session in context with several university sessions that are
arranged through institute themself. In addition to this, it shortens ways for administration as
well as obviates dduplication of potential being generated during courses.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Save upon operations: Firms might also utilise data analytical for minimising energy uses aas
well as save amount. Firm smay develops performance models that utilise real time information
form metres, actuators, sensors. In addition to this models may aids with energy that tilise
observing, anticipating, ansuring as well as optimising. It may also determine developing which
are underperforming as well as identify that is causing the in effectiveness.
Key benefits to Arden University gets after adopting Big Data.
Arden university uses the massive records of their databases to optimise operations, provide
higher customer service, create customised marketing campaigns centered on precise consumer
alternatives, and, ultimately, boom sales. agencies who use big records have a capability
competitive gain over folks that do not because of the truth, if the records are used efficaciously,
they may make smarter and additional informed company selections. as an example, large
records can provide organizations with valuable customer statistics that can be used to decorate
advertising and marketing campaigns and techniques to be able to increase purchaser pride and
conversion quotes.
the following are some of the benefits that a delegated university receives because of the
use of big records:
solutions to difficult conditions: the usage of big facts evaluation, college coordinators
are able to carry out a ramification of difficult obligations inside the business enterprise the
usage of smooth strategies(Del Vecchio and et. al., 2018). diverse hard conditions for the college
even as associated with any jail trouble or reward with regulation. As such at the same time as
the university is ordered to show their operational operating statistics, large data can show to
very beneficial to the agency.
to be had: looking through a wall-to-wall association of file shelves is inconvenient and
time-consuming. thinking about big information is based totally on a technological tool to way,
keep, and manipulate statistics, it is a lousy lot less complex to find out what is required within
the period in-between of time and is a lot much less hard to get right of entry to even as in
assessment to another method of storing records.
Saves price of operations: It proves to be a price-powerful approach for lowering
instructional institute fees. maintaining big records processing technique that every one statistics
and facts is recorded using scientific tools, making sure that it can live on indefinitely.
3
well as save amount. Firm smay develops performance models that utilise real time information
form metres, actuators, sensors. In addition to this models may aids with energy that tilise
observing, anticipating, ansuring as well as optimising. It may also determine developing which
are underperforming as well as identify that is causing the in effectiveness.
Key benefits to Arden University gets after adopting Big Data.
Arden university uses the massive records of their databases to optimise operations, provide
higher customer service, create customised marketing campaigns centered on precise consumer
alternatives, and, ultimately, boom sales. agencies who use big records have a capability
competitive gain over folks that do not because of the truth, if the records are used efficaciously,
they may make smarter and additional informed company selections. as an example, large
records can provide organizations with valuable customer statistics that can be used to decorate
advertising and marketing campaigns and techniques to be able to increase purchaser pride and
conversion quotes.
the following are some of the benefits that a delegated university receives because of the
use of big records:
solutions to difficult conditions: the usage of big facts evaluation, college coordinators
are able to carry out a ramification of difficult obligations inside the business enterprise the
usage of smooth strategies(Del Vecchio and et. al., 2018). diverse hard conditions for the college
even as associated with any jail trouble or reward with regulation. As such at the same time as
the university is ordered to show their operational operating statistics, large data can show to
very beneficial to the agency.
to be had: looking through a wall-to-wall association of file shelves is inconvenient and
time-consuming. thinking about big information is based totally on a technological tool to way,
keep, and manipulate statistics, it is a lousy lot less complex to find out what is required within
the period in-between of time and is a lot much less hard to get right of entry to even as in
assessment to another method of storing records.
Saves price of operations: It proves to be a price-powerful approach for lowering
instructional institute fees. maintaining big records processing technique that every one statistics
and facts is recorded using scientific tools, making sure that it can live on indefinitely.
3

conventional statistics storage strategies, in conjunction with storing books or copies, however,
are high-priced and time-consuming.
short technique: big information is described as the quick transmission of records that
may be transferred and accessed at any time(Ju, Liu, and Feng, 2018). It operates on a technical
diploma in that a person can run a are seeking a challenge in the gadget and locate the record or
facts they need in five-6 clicks, that could be a time-saving approach.
Question 2 – Security and Privacy
Explain the IT security and data privacy measures that an organisation must implement along
with provisions of GDPR.
Information technology safety is one of the crucial elements in an enterprise and is one of
the important precedences as well. Within the gift time period, businesses face many problems
alongside cyber assaults it is elevating suddenly and have an impact on businesses. It's far large
for an employer industrial employer business enterprise to utilize IT protection and records
privacy measures that allow you to protect records. The records privacy and IT protection
functions that an employer wants to execute are as follows:
Firewalls: so you can defend the community, firewalls are an essential initiative to take into
account thru the manner of an organization as manipulates the overall internet web page site
visitors coming and leaving the corporation. In addition to this, a firewall is largely a community
safety device that video display gadgets outgoing and incoming community traffic any after this
it determines whether or not or not or not to permit similarly to dam particular internet net page
traffic primarily based completely at the set of safety suggestions(Lee and Huh, 2019). There are
superb types of firewalls which may be the proxy firewall, next-technology firewall, stateful
inspection firewall, unified threat manage firewall, and plenty of greater. It's far analyzed that a
firewall plays like a traffic tool and shield entry element for which IP deal with is crucial as it is
analyzed a supply much like Postal deal with suggests wherein a person stay. Moreover, it's far
analyzed that stateful inspection firewall is one of the effective and comfy firewalls as its choice
indulges after layers 3 and 4 that relaxed in formation extra nicely.
Intrusion detection machine: it's far undertaken as a tracking tool that locates suspicious hobby
and creates indicators at the identical time as well detected. Together with this, the protection
operation center and incident responders can check out the reason based totally mostly on
4
are high-priced and time-consuming.
short technique: big information is described as the quick transmission of records that
may be transferred and accessed at any time(Ju, Liu, and Feng, 2018). It operates on a technical
diploma in that a person can run a are seeking a challenge in the gadget and locate the record or
facts they need in five-6 clicks, that could be a time-saving approach.
Question 2 – Security and Privacy
Explain the IT security and data privacy measures that an organisation must implement along
with provisions of GDPR.
Information technology safety is one of the crucial elements in an enterprise and is one of
the important precedences as well. Within the gift time period, businesses face many problems
alongside cyber assaults it is elevating suddenly and have an impact on businesses. It's far large
for an employer industrial employer business enterprise to utilize IT protection and records
privacy measures that allow you to protect records. The records privacy and IT protection
functions that an employer wants to execute are as follows:
Firewalls: so you can defend the community, firewalls are an essential initiative to take into
account thru the manner of an organization as manipulates the overall internet web page site
visitors coming and leaving the corporation. In addition to this, a firewall is largely a community
safety device that video display gadgets outgoing and incoming community traffic any after this
it determines whether or not or not or not to permit similarly to dam particular internet net page
traffic primarily based completely at the set of safety suggestions(Lee and Huh, 2019). There are
superb types of firewalls which may be the proxy firewall, next-technology firewall, stateful
inspection firewall, unified threat manage firewall, and plenty of greater. It's far analyzed that a
firewall plays like a traffic tool and shield entry element for which IP deal with is crucial as it is
analyzed a supply much like Postal deal with suggests wherein a person stay. Moreover, it's far
analyzed that stateful inspection firewall is one of the effective and comfy firewalls as its choice
indulges after layers 3 and 4 that relaxed in formation extra nicely.
Intrusion detection machine: it's far undertaken as a tracking tool that locates suspicious hobby
and creates indicators at the identical time as well detected. Together with this, the protection
operation center and incident responders can check out the reason based totally mostly on
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

symptoms and then take appropriate measures for declining the quantity of chance. It is analyzed
that intrusion detection device is mainly designed to extend indoors diverse environment and is
like cyber safety answers that may either be host-based definitely or network-based totally.
Moreover, IDS is also a pay interest nice tool which reviews and monitors web page web site site
visitors to an administrator but cannot take powerful movements for stopping measures that
make the most device(Kreiling and et. Al., 2020). Furthermore, it simplest required to come
across threats and is positioned out of the band at the community which means that it is not the
actual communique route of some of the receiver and sender information.
Other than the above IT protection features, there are numerous unique measures which an
enterprise company can position into effect in conjunction with updating snug cell phones,
educate personnel about data protection, and robust password and so on.
Key Provision of GDPR
preferred records safety regulation act overhauls information protection crook framework
internal Europe and is derived into effect on 2018. Similarly to this, GDPR law is supposed to
offer human beings manipulation over their information as now groups are amassing greater non-
public records. The critical issue provisions of GDPR is given beneath:
more Territorial impact: it is said that desired statistics safety regulation has a more territorial
effect. It especially applies to the processing of private statistics via an EU business enterprise
organization even though of whether or not or now not or now not or no longer the device take
vicinity. It way that corporations who adopt servers outside the ECU may additionally moreover
fail in the scope of this regulation.
Statistics protection offer: numerous entities appointed a statistics safety officer which can be
public authorities, groups that engaged on a massive scale(Sinha and Sengupta, 2020). Agency of
precise training of private data or statistics concerning criminal offenses or convictions. The
precept position of records protection officer is to propose companies on its responsibility and to
show compliance with GDPR.
Consent: The want round consent was bolstered thru famous records protection law because that
organization intends to rely upon consent for the lawful manner of personal records. Further to
this, to be a valid lawful foundation for processing information, consent ought to be freely given,
unambiguous, knowledgeable, and lots of extras. It is analyzed that human beings moreover have
the right or authority to withdraw consent at any vicinity of time.
5
that intrusion detection device is mainly designed to extend indoors diverse environment and is
like cyber safety answers that may either be host-based definitely or network-based totally.
Moreover, IDS is also a pay interest nice tool which reviews and monitors web page web site site
visitors to an administrator but cannot take powerful movements for stopping measures that
make the most device(Kreiling and et. Al., 2020). Furthermore, it simplest required to come
across threats and is positioned out of the band at the community which means that it is not the
actual communique route of some of the receiver and sender information.
Other than the above IT protection features, there are numerous unique measures which an
enterprise company can position into effect in conjunction with updating snug cell phones,
educate personnel about data protection, and robust password and so on.
Key Provision of GDPR
preferred records safety regulation act overhauls information protection crook framework
internal Europe and is derived into effect on 2018. Similarly to this, GDPR law is supposed to
offer human beings manipulation over their information as now groups are amassing greater non-
public records. The critical issue provisions of GDPR is given beneath:
more Territorial impact: it is said that desired statistics safety regulation has a more territorial
effect. It especially applies to the processing of private statistics via an EU business enterprise
organization even though of whether or not or now not or now not or no longer the device take
vicinity. It way that corporations who adopt servers outside the ECU may additionally moreover
fail in the scope of this regulation.
Statistics protection offer: numerous entities appointed a statistics safety officer which can be
public authorities, groups that engaged on a massive scale(Sinha and Sengupta, 2020). Agency of
precise training of private data or statistics concerning criminal offenses or convictions. The
precept position of records protection officer is to propose companies on its responsibility and to
show compliance with GDPR.
Consent: The want round consent was bolstered thru famous records protection law because that
organization intends to rely upon consent for the lawful manner of personal records. Further to
this, to be a valid lawful foundation for processing information, consent ought to be freely given,
unambiguous, knowledgeable, and lots of extras. It is analyzed that human beings moreover have
the right or authority to withdraw consent at any vicinity of time.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Decorate right for people: its miles analyzed that beneath GDPR, human beings have the proper
to access their non-public statistics, a proper to have personal information erased several times, a
right to the item to records processing, a proper to regulate inaccuracies internal non-public facts
and lots of greater. Instead, at the identical time as ab man or woman has the proper not to be a
hassle to profiling which does no longer check in which the processing is authorized through
member nation law or by way of EU law.
Aside from this, there also are distinct key provisions of GDPR that is obliging agencies to
be clearer about how they use non-public information, increase consequences, a new
responsibility for processors records safety via format and default, ability to rent a lead
supervisory authority, and hundreds of more.
Question 3 Telecommunication and spreadsheets
A) Describe a cellular network, its principle components and how it works.
A cellular network is defined as a radio community allocated Overland thru mobile wherein each
cellular embodies a specific place referred to as a base station. In addition to this, it's also
referred to as a cell network that may be a verbal exchange network and right proper right here
within the final hyperlink is wireless. It is said that once some of those cells joined collectively
offer radio insurance on a huge area. It allows transceivers which encompass cell telephones,
drugs, laptops with cell broadband, modems, pagers to speak with each specific and glued
transceivers further to phones anywhere in the network. Moreover, the cell network offers
subscribers complex dispositions over answers which include decline interference, small battery
strength usage, large geographical region, beautify capability, and so forth(Rajan and Dhir,
2020). The components of cell network collectively with how they paintings are stated under:
precept network of cellular community and the manner it clearly works
cell device: It is essentially a physical smartphone that is capable of the characteristic of the
cellular network. Together with this, it's miles determined that older telephones operated in a
single brand and the contemporary-day phones are a quad-band capable, twin band on the triple-
band as nicely. Furthermore, each mobile phone is in some different manner determined thru the
worldwide cell tool identification. It is analyzed that thru, it could be commonly decided through
extracting the battery of cellular phone in addition to via studying the panel properly.
Mobile period and capability: its miles stated that cellular period suggests huge sort of cells to be
had to cover geographical location and the capability to be had to clients. At the component of
6
to access their non-public statistics, a proper to have personal information erased several times, a
right to the item to records processing, a proper to regulate inaccuracies internal non-public facts
and lots of greater. Instead, at the identical time as ab man or woman has the proper not to be a
hassle to profiling which does no longer check in which the processing is authorized through
member nation law or by way of EU law.
Aside from this, there also are distinct key provisions of GDPR that is obliging agencies to
be clearer about how they use non-public information, increase consequences, a new
responsibility for processors records safety via format and default, ability to rent a lead
supervisory authority, and hundreds of more.
Question 3 Telecommunication and spreadsheets
A) Describe a cellular network, its principle components and how it works.
A cellular network is defined as a radio community allocated Overland thru mobile wherein each
cellular embodies a specific place referred to as a base station. In addition to this, it's also
referred to as a cell network that may be a verbal exchange network and right proper right here
within the final hyperlink is wireless. It is said that once some of those cells joined collectively
offer radio insurance on a huge area. It allows transceivers which encompass cell telephones,
drugs, laptops with cell broadband, modems, pagers to speak with each specific and glued
transceivers further to phones anywhere in the network. Moreover, the cell network offers
subscribers complex dispositions over answers which include decline interference, small battery
strength usage, large geographical region, beautify capability, and so forth(Rajan and Dhir,
2020). The components of cell network collectively with how they paintings are stated under:
precept network of cellular community and the manner it clearly works
cell device: It is essentially a physical smartphone that is capable of the characteristic of the
cellular network. Together with this, it's miles determined that older telephones operated in a
single brand and the contemporary-day phones are a quad-band capable, twin band on the triple-
band as nicely. Furthermore, each mobile phone is in some different manner determined thru the
worldwide cell tool identification. It is analyzed that thru, it could be commonly decided through
extracting the battery of cellular phone in addition to via studying the panel properly.
Mobile period and capability: its miles stated that cellular period suggests huge sort of cells to be
had to cover geographical location and the capability to be had to clients. At the component of
6

this, capability inner cellular is constrained with the useful resource of manner of to be had
bandwidth and operational necessities. Moreover, it is decided that the network operator has to
period cells for managing predicted website online site visitors nicely.
Base station controller: It handles allocation of strength, radio channels and signs dimension,
frequency handover, and distribution from one base station to some other. In addition to this, it
reduced the style of connections to the mobile switching center that similarly allow for better
functionality connection.
Base transceiver station: It is largely an antenna this is an installation at the pinnacle of the
tower. Along facet this, base transceiver station is cell telephone get entry to the problem and is
chargeable for carrying out the verbal exchange among cell community and call(Galushkin,
2018). Furthermore, it is analyzed that it handles encryption, speech modulation, speech
encoding, and so forth. The base transceiver station is assigned a mobile identification which
denotes a particular place location and gives detail of the cell.
Cellular switching center: it's far undertaken as the final issue of cell network that handles
referred to as routing, name center, clean switching function and plenty of more. Similarly to
this, it handles interface controller handoffs and additionally coordinates with one of the typical
cellular switching facilities properly. Moreover, it is analyzed that the cell switching center
handles a unique base station controller which acts as an interface amongst switching centers.
B) Explain the benefits of a cellular network to a business.
There are numerous advantages received through enterprise entity even as the usage of the
cellular network and is given under:
massive vicinity of network: it's far said that cellular net paintings reach those components that
are nearly impossible for group participants. For example, if an agency consists of a wi-fi
communique in constructing then it's far available to get related to the rest of worldwide from
balcony, rooftop and so forth.
Increase mobility: it is analyzed that every business corporation is associated with the
productiveness of personnel stay on at the administrative center. Further to this, even as an
organization accepts wireless connection then the body of workers individuals get actual-time
facts. Aside from this, if a business enterprise has a traditional network at the workplace then it is
not making sure to grow a chaotic workspace.
7
bandwidth and operational necessities. Moreover, it is decided that the network operator has to
period cells for managing predicted website online site visitors nicely.
Base station controller: It handles allocation of strength, radio channels and signs dimension,
frequency handover, and distribution from one base station to some other. In addition to this, it
reduced the style of connections to the mobile switching center that similarly allow for better
functionality connection.
Base transceiver station: It is largely an antenna this is an installation at the pinnacle of the
tower. Along facet this, base transceiver station is cell telephone get entry to the problem and is
chargeable for carrying out the verbal exchange among cell community and call(Galushkin,
2018). Furthermore, it is analyzed that it handles encryption, speech modulation, speech
encoding, and so forth. The base transceiver station is assigned a mobile identification which
denotes a particular place location and gives detail of the cell.
Cellular switching center: it's far undertaken as the final issue of cell network that handles
referred to as routing, name center, clean switching function and plenty of more. Similarly to
this, it handles interface controller handoffs and additionally coordinates with one of the typical
cellular switching facilities properly. Moreover, it is analyzed that the cell switching center
handles a unique base station controller which acts as an interface amongst switching centers.
B) Explain the benefits of a cellular network to a business.
There are numerous advantages received through enterprise entity even as the usage of the
cellular network and is given under:
massive vicinity of network: it's far said that cellular net paintings reach those components that
are nearly impossible for group participants. For example, if an agency consists of a wi-fi
communique in constructing then it's far available to get related to the rest of worldwide from
balcony, rooftop and so forth.
Increase mobility: it is analyzed that every business corporation is associated with the
productiveness of personnel stay on at the administrative center. Further to this, even as an
organization accepts wireless connection then the body of workers individuals get actual-time
facts. Aside from this, if a business enterprise has a traditional network at the workplace then it is
not making sure to grow a chaotic workspace.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
High flexibility: If an employer alters the network in destiny, it is reachable and easy to govern
thru a fire connection(Preece, 2020). But if a business organization corporation has a cable
connection at the artwork location, it can without issues undo the whole approach which arises
fees and excessive time as well.
Decline possession fee: it is determined that if an agency has a look at the wi-fi community with
traditional shoppers then it's miles easily capable of creating a demarcation among costs upward
push up. On the side of this, it's miles analyzed that wi-fi connection has excessive sturdiness
compared to conventional network Which in flip help in declining possession price in a powerful
manner.
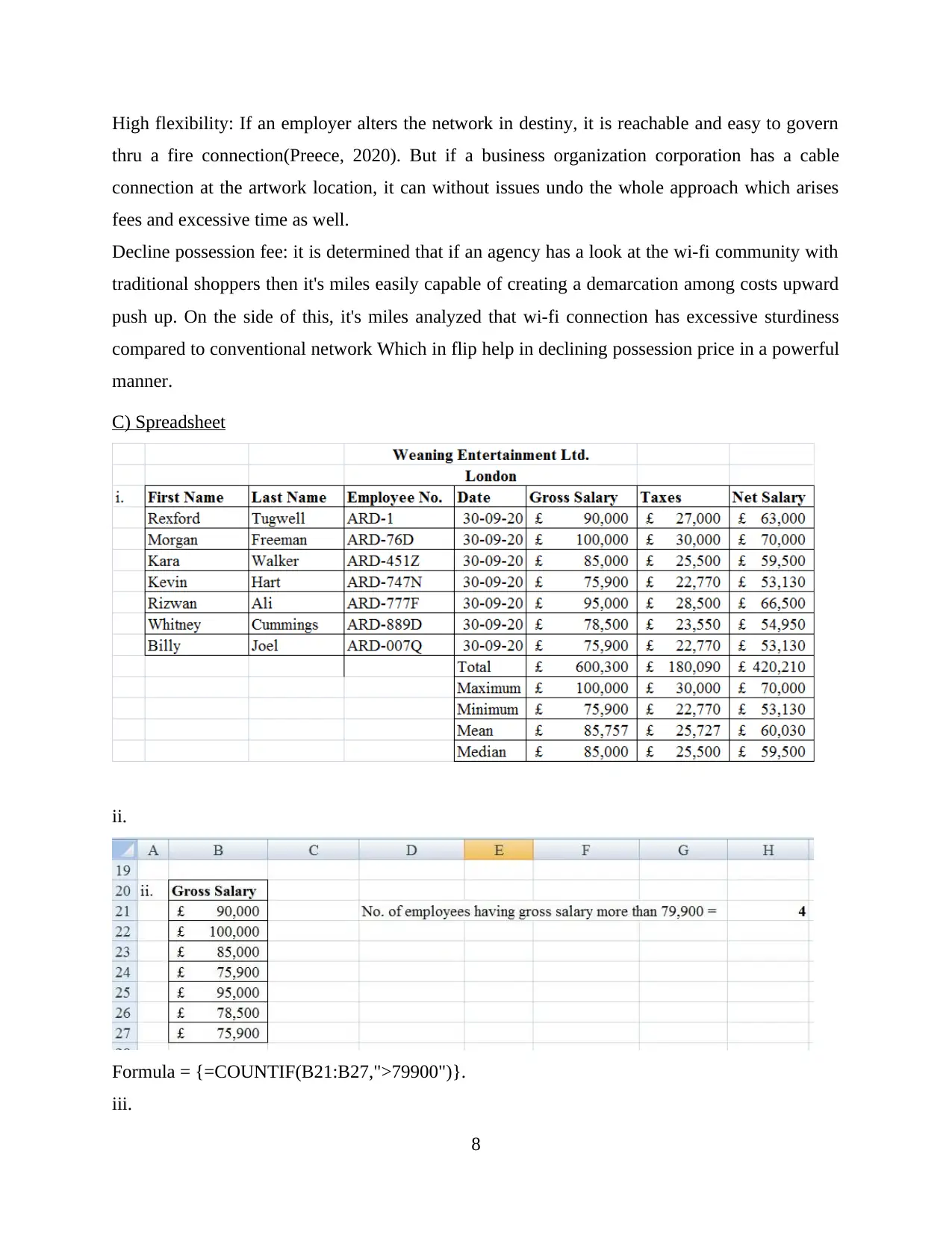
C) Spreadsheet
ii.
Formula = {=COUNTIF(B21:B27,">79900")}.
iii.
8
thru a fire connection(Preece, 2020). But if a business organization corporation has a cable
connection at the artwork location, it can without issues undo the whole approach which arises
fees and excessive time as well.
Decline possession fee: it is determined that if an agency has a look at the wi-fi community with
traditional shoppers then it's miles easily capable of creating a demarcation among costs upward
push up. On the side of this, it's miles analyzed that wi-fi connection has excessive sturdiness
compared to conventional network Which in flip help in declining possession price in a powerful
manner.
C) Spreadsheet
ii.
Formula = {=COUNTIF(B21:B27,">79900")}.
iii.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
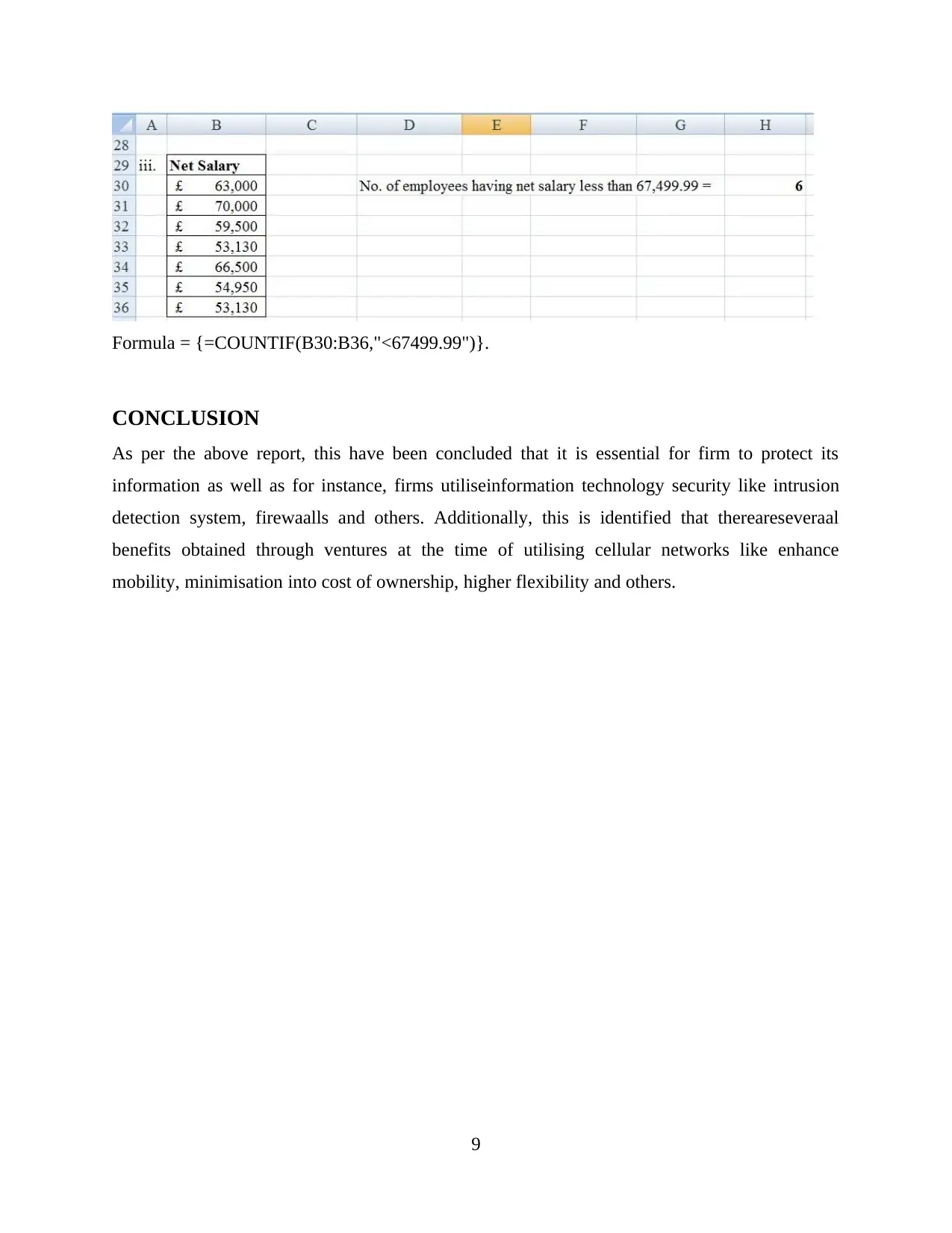
Formula = {=COUNTIF(B30:B36,"<67499.99")}.
CONCLUSION
As per the above report, this have been concluded that it is essential for firm to protect its
information as well as for instance, firms utiliseinformation technology security like intrusion
detection system, firewaalls and others. Additionally, this is identified that thereareseveraal
benefits obtained through ventures at the time of utilising cellular networks like enhance
mobility, minimisation into cost of ownership, higher flexibility and others.
9
CONCLUSION
As per the above report, this have been concluded that it is essential for firm to protect its
information as well as for instance, firms utiliseinformation technology security like intrusion
detection system, firewaalls and others. Additionally, this is identified that thereareseveraal
benefits obtained through ventures at the time of utilising cellular networks like enhance
mobility, minimisation into cost of ownership, higher flexibility and others.
9

REFERENCES
Books and Journal
Antoni, D., Jie, F. and Abareshi, A., 2020. Critical factors in information technology capability
for enhancing firm's environmental performance: case of Indonesian ICT
sector. International Journal of Agile Systems and Management, 13(2), pp.159-181.
Dastane, O., 2020. The impact of technology adoption on organizational productivity. Journal of
Industrial Distribution & Business, 11(4), pp.7-18.
Di Vaio, A. and Varriale, L., 2020. Blockchain technology in supply chain management for
sustainable performance: Evidence from the airport industry. International Journal of
Information Management, 52, p.102014.
Ghobakhloo, M., 2020. Determinants of information and digital technology implementation for
smart manufacturing. International Journal of Production Research, 58(8), pp.2384-2405.
Khalil, S. and Belitski, M., 2020. Dynamic capabilities for firm performance under the
information technology governance framework. European Business Review.
Kumar, A., 2020. Information technology industry. Journal of Management Science, Operations
& Strategies (e ISSN 2456-9305), 1(1), pp.12-15.
Long, E., 2020. Gendered narratives Relating to Women in The Information Technology
Department of a South African Organisation. Journal of International Women's
Studies, 21(6), pp.153-169.
Njock, P.G.A. and et. al., 2020. Evaluation of soil liquefaction using AI technology
incorporating a coupled ENN/t-SNE model. Soil Dynamics and Earthquake
Engineering, 130, p.105988.
Perera, S., and et. al., 2020. Blockchain technology: Is it hype or real in the construction
industry?. Journal of Industrial Information Integration, 17, p.100125.
Son, H., Chung, Y. and Yoon, S., 2020. How can university technology holding companies
bridge the Valley of Death? Evidence from Korea. Technovation, p.102158.
Vázquez-Cano, E., and et. al., 2020. Incidence of a non-sustainability use of technology on
students’ reading performance in Pisa. Sustainability, 12(2), p.749.
Wagire, A.A., and et. al., 2020. Development of maturity model for assessing the
implementation of Industry 4.0: learning from theory and practice. Production Planning
& Control, pp.1-20.
10
Books and Journal
Antoni, D., Jie, F. and Abareshi, A., 2020. Critical factors in information technology capability
for enhancing firm's environmental performance: case of Indonesian ICT
sector. International Journal of Agile Systems and Management, 13(2), pp.159-181.
Dastane, O., 2020. The impact of technology adoption on organizational productivity. Journal of
Industrial Distribution & Business, 11(4), pp.7-18.
Di Vaio, A. and Varriale, L., 2020. Blockchain technology in supply chain management for
sustainable performance: Evidence from the airport industry. International Journal of
Information Management, 52, p.102014.
Ghobakhloo, M., 2020. Determinants of information and digital technology implementation for
smart manufacturing. International Journal of Production Research, 58(8), pp.2384-2405.
Khalil, S. and Belitski, M., 2020. Dynamic capabilities for firm performance under the
information technology governance framework. European Business Review.
Kumar, A., 2020. Information technology industry. Journal of Management Science, Operations
& Strategies (e ISSN 2456-9305), 1(1), pp.12-15.
Long, E., 2020. Gendered narratives Relating to Women in The Information Technology
Department of a South African Organisation. Journal of International Women's
Studies, 21(6), pp.153-169.
Njock, P.G.A. and et. al., 2020. Evaluation of soil liquefaction using AI technology
incorporating a coupled ENN/t-SNE model. Soil Dynamics and Earthquake
Engineering, 130, p.105988.
Perera, S., and et. al., 2020. Blockchain technology: Is it hype or real in the construction
industry?. Journal of Industrial Information Integration, 17, p.100125.
Son, H., Chung, Y. and Yoon, S., 2020. How can university technology holding companies
bridge the Valley of Death? Evidence from Korea. Technovation, p.102158.
Vázquez-Cano, E., and et. al., 2020. Incidence of a non-sustainability use of technology on
students’ reading performance in Pisa. Sustainability, 12(2), p.749.
Wagire, A.A., and et. al., 2020. Development of maturity model for assessing the
implementation of Industry 4.0: learning from theory and practice. Production Planning
& Control, pp.1-20.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





