Technology and Identity Theft: Legal Ramifications and Solutions
VerifiedAdded on 2023/06/14
|14
|3598
|144
Essay
AI Summary
This essay addresses the pervasive issue of identity theft in the digital age, highlighting the story of an individual, Ann Krebs, who fell victim to this crime despite taking precautions. It underscores the emotional and financial devastation caused by identity theft and emphasizes the need for effective preventative measures. The proposal aims to enlighten the government and marketplace on methods to eradicate identity theft, referencing credible sources and legal regulations like FACTA. It analyzes the problem, discussing how easily personal information can be accessed and exploited through techniques like phishing and pharming. Furthermore, the essay proposes solutions such as the Institution of the Unique Coding System (UCS) and the creation of specialized task forces to combat identity theft, referencing successful initiatives like California's approach and President Obama's BuySecure Initiative. The essay concludes by stressing the importance of data protection and the need for collaborative efforts between government, businesses, and consumers to mitigate the risks of identity theft.

Running head: TECHNOLOGY AND IDENTITY THEFT
1
Technology and Identity Theft
Kimberlee Mullins
DeVryUniversity
1
Technology and Identity Theft
Kimberlee Mullins
DeVryUniversity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IDENTITY THEFT 2
Technology and Identity Theft
Ann Krebs exhibited great caution when using the Internet as she was determined to
ensure that her private information on the Internet was safe. Ann still fell victim of the now
rampant crime of identity theft despite her caution. The thief mysteriously managed to access
both her credit report and history. Upon sharing her case with the company that had given the
credit card to the hacker, she decided to take the necessary steps to ensure that a similar case
does not occur to her in future. She first checked with all the credit bureaus and was shocked to
learn that her credit report information had been altered. Upon attempting multiple times, Ann
was able to access her credit report and was once again shocked to discover that the thief stole
her identity six months ago.After having been issued with an FTC affidavit, a report of the credit
card, a report from the police, and freezing credit with the three bureaus, Ann was able to have
the thief apprehended. According to Ann, the Government and the Congress are equally to blame
for the incident as they do not follow the proper guidelines, and also, do not give the victim clear
directions on how to clear the issue. This, and other similar incidents, goes a long way towards
pointing out how identity theft victims’ data can be accessed and used despite the level of
caution exhibited. Additionally, Ann narrates how the whole process drains one emotionally and
also time consuming.
Incidents similar to Ann’s reaffirms that an Identity theft case can be devastating not only
because it significantly impacts one’s financial stability, but also because it “kills” ones
emotional stability. This story has helped many people with similar cases exhibit great courage
when dealing with their identity theft situation.
The aim of this proposal entitled Identity Theft is to, therefore, enlighten the government
and the marketplace on the multiple methods of successfully eradicating identity theft and
Technology and Identity Theft
Ann Krebs exhibited great caution when using the Internet as she was determined to
ensure that her private information on the Internet was safe. Ann still fell victim of the now
rampant crime of identity theft despite her caution. The thief mysteriously managed to access
both her credit report and history. Upon sharing her case with the company that had given the
credit card to the hacker, she decided to take the necessary steps to ensure that a similar case
does not occur to her in future. She first checked with all the credit bureaus and was shocked to
learn that her credit report information had been altered. Upon attempting multiple times, Ann
was able to access her credit report and was once again shocked to discover that the thief stole
her identity six months ago.After having been issued with an FTC affidavit, a report of the credit
card, a report from the police, and freezing credit with the three bureaus, Ann was able to have
the thief apprehended. According to Ann, the Government and the Congress are equally to blame
for the incident as they do not follow the proper guidelines, and also, do not give the victim clear
directions on how to clear the issue. This, and other similar incidents, goes a long way towards
pointing out how identity theft victims’ data can be accessed and used despite the level of
caution exhibited. Additionally, Ann narrates how the whole process drains one emotionally and
also time consuming.
Incidents similar to Ann’s reaffirms that an Identity theft case can be devastating not only
because it significantly impacts one’s financial stability, but also because it “kills” ones
emotional stability. This story has helped many people with similar cases exhibit great courage
when dealing with their identity theft situation.
The aim of this proposal entitled Identity Theft is to, therefore, enlighten the government
and the marketplace on the multiple methods of successfully eradicating identity theft and

IDENTITY THEFT 3
present a great deal of information regarding how such incidents affects one’s credit as well as
life. Rosenstein and Fine (2016) point out that, “Identity theft/thieves can result in a devastating
impact on one’s finances and emotional stability” (Rosenstein and Fine, 2016). Despite the fact
that I am pursuing my undergraduate studies, I feel that the Identity Theft topic is of great
importance because I was a victim of the same some years ago. As a consequence, I am greatly
motivated and overwhelmed by the topic. In this proposal, I will review multiple credible sources
that will enable me establish my credibility. To establish my credibility, I will borrow the
concepts presented by Rosenstein and Fine (2016), Linnhoff and Langenderfer (2004), and The
Federal Trade Commission (2016), who are famous for the Identity Theft topic.
Identity theft can be classified as a major cause of social, emotional, and financial strain
in the consumers and marketplace. Some of the approaches that can be adopted to combat this
trend include the Congress strictly adhering to the regulations as stipulated by FACTA and close
monitoring as well. According to these regulations, the Congress, in collaboration with the
Department of Justice and the FTC, should ensure the safety of both off-line and online
information that is sensitive.
Problem Analysis
A simple search of multiple names through Google reveals that many people share
names nationwide. With this in mind, we cannot say that just by using someone else’s name will
make you be labelled an identity thief. As a consequence of this factor, identity thieves can now
easily steal passwords and user log-ins for various Websites; this means that the thieves can hack
many websites and eventually notice that the profits escalated massively as compared to when a
present a great deal of information regarding how such incidents affects one’s credit as well as
life. Rosenstein and Fine (2016) point out that, “Identity theft/thieves can result in a devastating
impact on one’s finances and emotional stability” (Rosenstein and Fine, 2016). Despite the fact
that I am pursuing my undergraduate studies, I feel that the Identity Theft topic is of great
importance because I was a victim of the same some years ago. As a consequence, I am greatly
motivated and overwhelmed by the topic. In this proposal, I will review multiple credible sources
that will enable me establish my credibility. To establish my credibility, I will borrow the
concepts presented by Rosenstein and Fine (2016), Linnhoff and Langenderfer (2004), and The
Federal Trade Commission (2016), who are famous for the Identity Theft topic.
Identity theft can be classified as a major cause of social, emotional, and financial strain
in the consumers and marketplace. Some of the approaches that can be adopted to combat this
trend include the Congress strictly adhering to the regulations as stipulated by FACTA and close
monitoring as well. According to these regulations, the Congress, in collaboration with the
Department of Justice and the FTC, should ensure the safety of both off-line and online
information that is sensitive.
Problem Analysis
A simple search of multiple names through Google reveals that many people share
names nationwide. With this in mind, we cannot say that just by using someone else’s name will
make you be labelled an identity thief. As a consequence of this factor, identity thieves can now
easily steal passwords and user log-ins for various Websites; this means that the thieves can hack
many websites and eventually notice that the profits escalated massively as compared to when a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IDENTITY THEFT 4
single Web site’s data was captured.
For the better part of human history, the identity of a person was known by a few. Pharming,
identity theft, and phishing before the massive usage of computers, identity theft was executed
mainly by use of mail for anonymity purposes as personal transactions often made it compulsory
to use a photo ID, such as an I.D. card or a driver’s license. The crucial aspect in identity theft is
that the crime or criminal intent needs to be evident. For an identity theft to be acknowledged,
there was to be more than simply utilizing another person’s name. It needs the presence of
sensitive data that that is sufficient to access another person’s personal information. In a scenario
where a user follows a link in the email, one occurrence out of the two possible ones will
materialize: the user will either be taken to a replica website and in a scenario wherethe personal
information of the user is required, it will used; secondly, the technological choice of the user is
accessed by a virus that will either work to create a path for the thieves to gather sensitive data,
or which is applied as a tool to infect cellphones, computers, and other technologies.
single Web site’s data was captured.
For the better part of human history, the identity of a person was known by a few. Pharming,
identity theft, and phishing before the massive usage of computers, identity theft was executed
mainly by use of mail for anonymity purposes as personal transactions often made it compulsory
to use a photo ID, such as an I.D. card or a driver’s license. The crucial aspect in identity theft is
that the crime or criminal intent needs to be evident. For an identity theft to be acknowledged,
there was to be more than simply utilizing another person’s name. It needs the presence of
sensitive data that that is sufficient to access another person’s personal information. In a scenario
where a user follows a link in the email, one occurrence out of the two possible ones will
materialize: the user will either be taken to a replica website and in a scenario wherethe personal
information of the user is required, it will used; secondly, the technological choice of the user is
accessed by a virus that will either work to create a path for the thieves to gather sensitive data,
or which is applied as a tool to infect cellphones, computers, and other technologies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IDENTITY THEFT 5
Transactions which are conducted online bear the highest degree of anonymity provided
the user can provide accurate information, which is enough to prove identity. Pharming can be
viewed as a more modern method that either downloads or installs a program on the computer of
the user. This takes place when the user enters a particular series of websites and instead of
accessing the original site, a “clone” site is created. Another type of pharming is key logging.
What happens is that the user makes keystrokes, and in turn, a malicious software logs after each
keystroke. The phishing technique has also been noted to be one of the primary methods used to
steal identities(Oorschot&Stubblebine, 2005). For instance, if a person rents a space using names
which are not similar to those in the birth certificate, and pays the agreed rent on time, such a
case cannot be ruled out as an identity theft.
Due to the complications of the daily life, a person’s identity also became more
complicated. For instance, a person can be involved in relationships with financial institutions,
the government, and other corporations. Due to these multiple relationships, a person might no
longer be personally known to those he/she is having a relationship with. Pharming and Phishing
are two well-known methods which are utilized by identity thieves to access consumers’
information. However, the individuals behind these sort of attacks have lived in
sophisticationand the e-mails now perfectly match with the institutions they are impersonating.
Valuable information, including the names of the maiden mothers, driver’s license numbers, and
credit card numbers are frequently used so that the identity thieves can trick others into believing
that they are the individuals they are mimicking.As seen in the previous section, phishing and
pharming are some of the schemes that are used to obtain personal data from the Internet.
Additionally, a great deal of transactions involving identity theft are conducted through the
Transactions which are conducted online bear the highest degree of anonymity provided
the user can provide accurate information, which is enough to prove identity. Pharming can be
viewed as a more modern method that either downloads or installs a program on the computer of
the user. This takes place when the user enters a particular series of websites and instead of
accessing the original site, a “clone” site is created. Another type of pharming is key logging.
What happens is that the user makes keystrokes, and in turn, a malicious software logs after each
keystroke. The phishing technique has also been noted to be one of the primary methods used to
steal identities(Oorschot&Stubblebine, 2005). For instance, if a person rents a space using names
which are not similar to those in the birth certificate, and pays the agreed rent on time, such a
case cannot be ruled out as an identity theft.
Due to the complications of the daily life, a person’s identity also became more
complicated. For instance, a person can be involved in relationships with financial institutions,
the government, and other corporations. Due to these multiple relationships, a person might no
longer be personally known to those he/she is having a relationship with. Pharming and Phishing
are two well-known methods which are utilized by identity thieves to access consumers’
information. However, the individuals behind these sort of attacks have lived in
sophisticationand the e-mails now perfectly match with the institutions they are impersonating.
Valuable information, including the names of the maiden mothers, driver’s license numbers, and
credit card numbers are frequently used so that the identity thieves can trick others into believing
that they are the individuals they are mimicking.As seen in the previous section, phishing and
pharming are some of the schemes that are used to obtain personal data from the Internet.
Additionally, a great deal of transactions involving identity theft are conducted through the
IDENTITY THEFT 6
Internet, including online shopping and banking, and as a consequence, identity thieves can
easily utilize the information they stole.
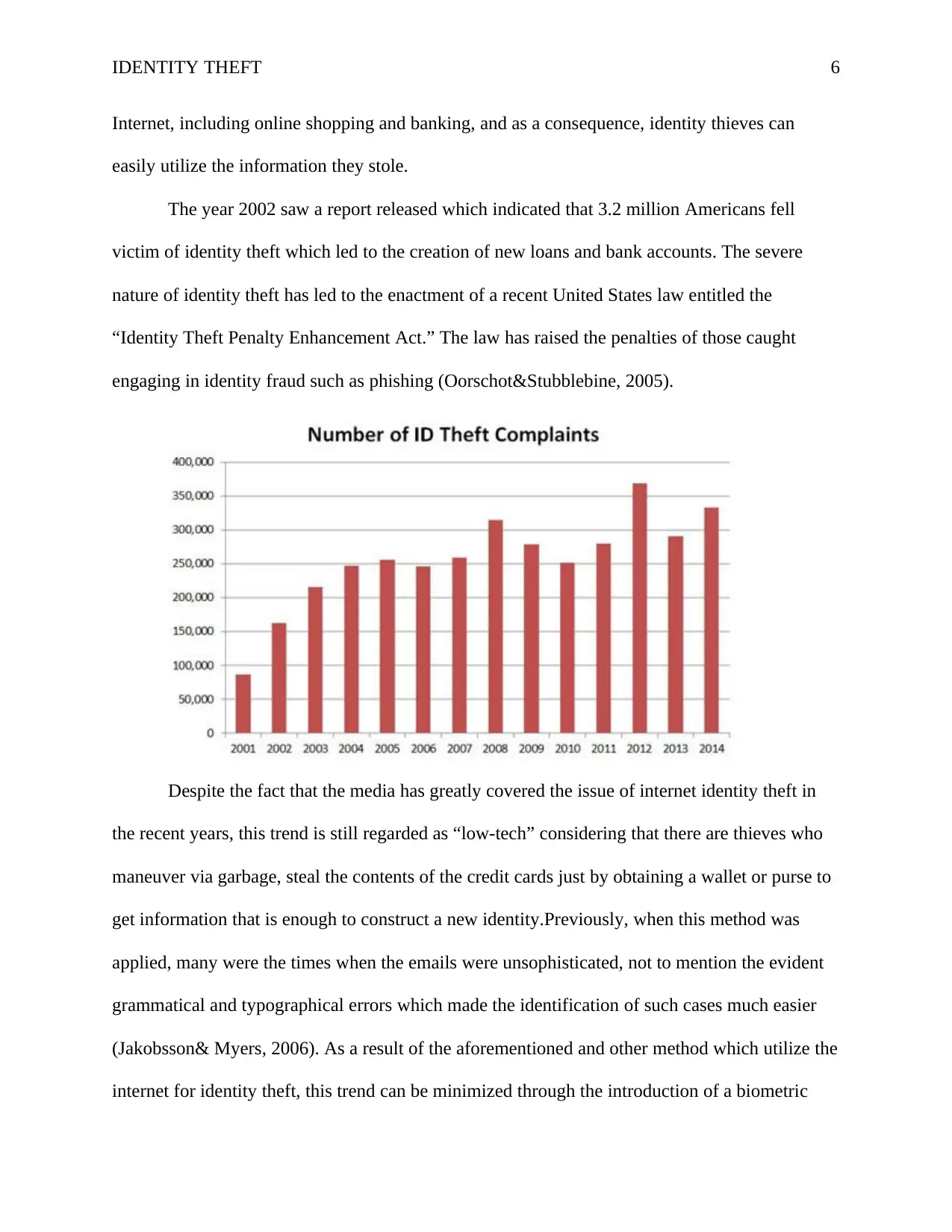
The year 2002 saw a report released which indicated that 3.2 million Americans fell
victim of identity theft which led to the creation of new loans and bank accounts. The severe
nature of identity theft has led to the enactment of a recent United States law entitled the
“Identity Theft Penalty Enhancement Act.” The law has raised the penalties of those caught
engaging in identity fraud such as phishing (Oorschot&Stubblebine, 2005).
Despite the fact that the media has greatly covered the issue of internet identity theft in
the recent years, this trend is still regarded as “low-tech” considering that there are thieves who
maneuver via garbage, steal the contents of the credit cards just by obtaining a wallet or purse to
get information that is enough to construct a new identity.Previously, when this method was
applied, many were the times when the emails were unsophisticated, not to mention the evident
grammatical and typographical errors which made the identification of such cases much easier
(Jakobsson& Myers, 2006). As a result of the aforementioned and other method which utilize the
internet for identity theft, this trend can be minimized through the introduction of a biometric
Internet, including online shopping and banking, and as a consequence, identity thieves can
easily utilize the information they stole.
The year 2002 saw a report released which indicated that 3.2 million Americans fell
victim of identity theft which led to the creation of new loans and bank accounts. The severe
nature of identity theft has led to the enactment of a recent United States law entitled the
“Identity Theft Penalty Enhancement Act.” The law has raised the penalties of those caught
engaging in identity fraud such as phishing (Oorschot&Stubblebine, 2005).
Despite the fact that the media has greatly covered the issue of internet identity theft in
the recent years, this trend is still regarded as “low-tech” considering that there are thieves who
maneuver via garbage, steal the contents of the credit cards just by obtaining a wallet or purse to
get information that is enough to construct a new identity.Previously, when this method was
applied, many were the times when the emails were unsophisticated, not to mention the evident
grammatical and typographical errors which made the identification of such cases much easier
(Jakobsson& Myers, 2006). As a result of the aforementioned and other method which utilize the
internet for identity theft, this trend can be minimized through the introduction of a biometric
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IDENTITY THEFT 7
system. Additionally, this trend can be eradicated appropriately through the formulation of a
force or another special unit focusing on the elimination of the problem (Rosenstein & Fine,
2016).
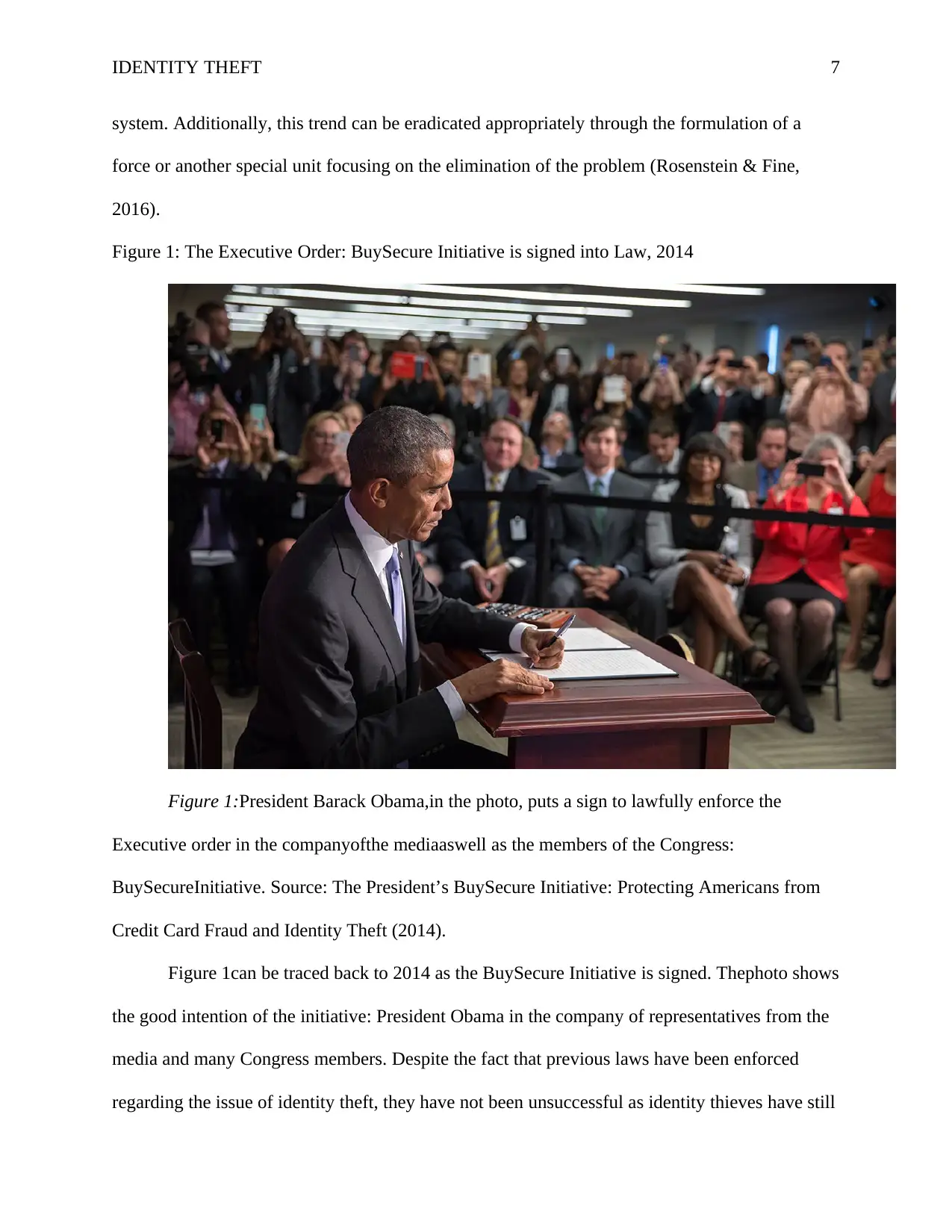
Figure 1: The Executive Order: BuySecure Initiative is signed into Law, 2014
Figure 1:President Barack Obama,in the photo, puts a sign to lawfully enforce the
Executive order in the companyofthe mediaaswell as the members of the Congress:
BuySecureInitiative. Source: The President’s BuySecure Initiative: Protecting Americans from
Credit Card Fraud and Identity Theft (2014).
Figure 1can be traced back to 2014 as the BuySecure Initiative is signed. Thephoto shows
the good intention of the initiative: President Obama in the company of representatives from the
media and many Congress members. Despite the fact that previous laws have been enforced
regarding the issue of identity theft, they have not been unsuccessful as identity thieves have still
system. Additionally, this trend can be eradicated appropriately through the formulation of a
force or another special unit focusing on the elimination of the problem (Rosenstein & Fine,
2016).
Figure 1: The Executive Order: BuySecure Initiative is signed into Law, 2014
Figure 1:President Barack Obama,in the photo, puts a sign to lawfully enforce the
Executive order in the companyofthe mediaaswell as the members of the Congress:
BuySecureInitiative. Source: The President’s BuySecure Initiative: Protecting Americans from
Credit Card Fraud and Identity Theft (2014).
Figure 1can be traced back to 2014 as the BuySecure Initiative is signed. Thephoto shows
the good intention of the initiative: President Obama in the company of representatives from the
media and many Congress members. Despite the fact that previous laws have been enforced
regarding the issue of identity theft, they have not been unsuccessful as identity thieves have still
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IDENTITY THEFT 8
managed to hack systems. However, the passing of the new bill will make it more challenging
for the thieves to access information.
Solution
One of the solutions that can be fruitful in eradicating this menace is the
Institution of the Unique Coding System (UCS), which will create and issue a card. The card will
have a chip, and in addition to this, certain letters and numbers will be issued to every person and
this will enable theverification for credit accounts, utilities, and employment. As opposed to
issuing Social Security Numbers, duplication of the UCS will be impossible considering that the
person need to have the card only for the purposes of verification including searching for
employment, applying for credit or verifying identity. In the event where an EMV machine is
unavailable, the combination of the letter and number may be applied in combination with taking
security verification questions randomly.
Notably, the new system is a wise method of eliminating the crisis as it will render the
process of hacking into a company’s or individual’s personal information more difficult.
Additionally, UCS is composed of an isolated device which is possessed by the “owner” that can
lock instantly in the event where the card is misplaced and creates and issues quarterly reports
regarding to the credit to every persons’ issued card that can only be viewed in particular
regions, as opposed to the Social Security Administration which gives sufficient room for
stealing and duplication of their numbers.
Multiple strategies have been put in place by the Federal Enforcement officials to identify
the identity thieves and eliminate the annoying trend through the creation of special groups that
particularly focus on combating the menace. An Assistant U.S. Attorney institutes the special
institutions and makes a prompt follow up to ensure that the groups convene and generate a
managed to hack systems. However, the passing of the new bill will make it more challenging
for the thieves to access information.
Solution
One of the solutions that can be fruitful in eradicating this menace is the
Institution of the Unique Coding System (UCS), which will create and issue a card. The card will
have a chip, and in addition to this, certain letters and numbers will be issued to every person and
this will enable theverification for credit accounts, utilities, and employment. As opposed to
issuing Social Security Numbers, duplication of the UCS will be impossible considering that the
person need to have the card only for the purposes of verification including searching for
employment, applying for credit or verifying identity. In the event where an EMV machine is
unavailable, the combination of the letter and number may be applied in combination with taking
security verification questions randomly.
Notably, the new system is a wise method of eliminating the crisis as it will render the
process of hacking into a company’s or individual’s personal information more difficult.
Additionally, UCS is composed of an isolated device which is possessed by the “owner” that can
lock instantly in the event where the card is misplaced and creates and issues quarterly reports
regarding to the credit to every persons’ issued card that can only be viewed in particular
regions, as opposed to the Social Security Administration which gives sufficient room for
stealing and duplication of their numbers.
Multiple strategies have been put in place by the Federal Enforcement officials to identify
the identity thieves and eliminate the annoying trend through the creation of special groups that
particularly focus on combating the menace. An Assistant U.S. Attorney institutes the special
institutions and makes a prompt follow up to ensure that the groups convene and generate a

IDENTITY THEFT 9
solution to the matters in hand.Looking at California, for instance, this concept registered
tremendous success following the proposition of the idea by Governor Schwarzenegger
(Schwarzenegger, 2005).
The congress, the market, as well as the Social Security Administration, has created great
strain in identity theft control. In a scenario where there is an excellent addressing of the matters
regarding massive issuance and use of Social Security numbers and keeping data safe, pin-
pointing the identity thief would be as easy. However, a resolution to the problem may be found
in the near future as President Obama made it compulsory for his board of executives to initiate
step by step submissions with important and genuine data to the Training Alliance's Internet
Fraud Alert System and the National Cyber-Forensics and resources relating to the menace to the
FTC (Pres. Obama & EPIC, 2014). In addition, the issuance of quarterly credit statements would
minimize the problem as the consumers would know the contents of their credit cards four times
annually.
Four steps must be conducted to make the UCS operational fully. First, I will fund the
system and the experts in technology and identity theft will come in to design the system. As a
consequence of the adoption of an improved and modern technical system, EMV system experts,
web designers, card specialist, and a special team of experts in the field of identity theft will be
recruited to get the UNCS running. The next step will involve testing of the system randomly by
government officials and consumers, of which I will conduct the first test in collaboration with
the two experts to test the EMV system.Testing the system with individuals who are selected at
random will help in the identification of areas that need modification before approval by the
Congress, Federal Enforcement officials, and other branches of the government. Two crucial
phases in the whole process entail convincing the individuals who are randomly selected to
solution to the matters in hand.Looking at California, for instance, this concept registered
tremendous success following the proposition of the idea by Governor Schwarzenegger
(Schwarzenegger, 2005).
The congress, the market, as well as the Social Security Administration, has created great
strain in identity theft control. In a scenario where there is an excellent addressing of the matters
regarding massive issuance and use of Social Security numbers and keeping data safe, pin-
pointing the identity thief would be as easy. However, a resolution to the problem may be found
in the near future as President Obama made it compulsory for his board of executives to initiate
step by step submissions with important and genuine data to the Training Alliance's Internet
Fraud Alert System and the National Cyber-Forensics and resources relating to the menace to the
FTC (Pres. Obama & EPIC, 2014). In addition, the issuance of quarterly credit statements would
minimize the problem as the consumers would know the contents of their credit cards four times
annually.
Four steps must be conducted to make the UCS operational fully. First, I will fund the
system and the experts in technology and identity theft will come in to design the system. As a
consequence of the adoption of an improved and modern technical system, EMV system experts,
web designers, card specialist, and a special team of experts in the field of identity theft will be
recruited to get the UNCS running. The next step will involve testing of the system randomly by
government officials and consumers, of which I will conduct the first test in collaboration with
the two experts to test the EMV system.Testing the system with individuals who are selected at
random will help in the identification of areas that need modification before approval by the
Congress, Federal Enforcement officials, and other branches of the government. Two crucial
phases in the whole process entail convincing the individuals who are randomly selected to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IDENTITY THEFT 10
submit their personal information to be used in the creation of a card (a sample one) and to put
forward submissions on a daily basis regarding the manner in which the system will be
instrumental in the eradication of identity theft. Following the execution of all the required
modifications and approval of the same but the officials, executive will send emailsin masses
briefing the consumers on the launch date, and in addition to that, send personal emails giving
instructions on where consumers can collect their cards. Upon the issuance of the card to the
individual, it will be compulsory for the owner to sign for the card for record keeping purposes.
In a case where the owner misplaces the card and it is possible to compare the signatures if a
person had used the card prior to the “owner’s” deactivation of the card. But, in case identity
theft is still witnessed under the watch of the new system, consumers should be granted enough
time to solve the issue and should as well be exempted from any charges associated with the
correction.
Certainly, this plan will be instrumental in the eradication of identity theft considering
that the system will be impossible to hack and steal government official and consumer personal
information. Additionally, deactivation of the card will be possible once the consumers note that
their card is lost. Besides the opportunity to deactivate the card, the relevant officials will get a
notification upon the deactivation. In response, someone will make a call to the card holder and
prompt him/her to answer several security questions, upon which the issuance of a new card will
follow.
Benefits
The given alternative will establish a feeling of safety to the officials of the government
as well as all consumers. Prior to the UNCS taking effect, the necessary funds must be availed.
The funds will be raised through conducting fundraising campaigns to create an awareness of the
submit their personal information to be used in the creation of a card (a sample one) and to put
forward submissions on a daily basis regarding the manner in which the system will be
instrumental in the eradication of identity theft. Following the execution of all the required
modifications and approval of the same but the officials, executive will send emailsin masses
briefing the consumers on the launch date, and in addition to that, send personal emails giving
instructions on where consumers can collect their cards. Upon the issuance of the card to the
individual, it will be compulsory for the owner to sign for the card for record keeping purposes.
In a case where the owner misplaces the card and it is possible to compare the signatures if a
person had used the card prior to the “owner’s” deactivation of the card. But, in case identity
theft is still witnessed under the watch of the new system, consumers should be granted enough
time to solve the issue and should as well be exempted from any charges associated with the
correction.
Certainly, this plan will be instrumental in the eradication of identity theft considering
that the system will be impossible to hack and steal government official and consumer personal
information. Additionally, deactivation of the card will be possible once the consumers note that
their card is lost. Besides the opportunity to deactivate the card, the relevant officials will get a
notification upon the deactivation. In response, someone will make a call to the card holder and
prompt him/her to answer several security questions, upon which the issuance of a new card will
follow.
Benefits
The given alternative will establish a feeling of safety to the officials of the government
as well as all consumers. Prior to the UNCS taking effect, the necessary funds must be availed.
The funds will be raised through conducting fundraising campaigns to create an awareness of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IDENTITY THEFT 11
draining impacts of identity theft. In addition to the funds and the system experts, a reader card
of the EMV, along with an installed chip and many technological documents will essential to
kick start the project. One of the remarkable benefits of the proposed system is its ability to
generate and issue reports pertaining to the credit cards four times per year.
The plan will be a great time and energy saver. Additionally, the plan will help the
Congress, consumers and S.S.A reduce unnecessary spending as the odds of experiencing
identity theft will be minimized. The current system of testing costs $ 7.3 billion per year. As a
result of the expensive nature of the initial biometric system of verification, UNCS came in
handy in replacing the initial system. The cost difference between the biometric and the UNCS
adds up to $ 4.2 billion dollars per year, thus the UNCS can be said to be a more cost efficient as
it totals up to $ 3.1 billion each year.
Year 1 Year 5 Year 10
0
1
2
3
4
5
6
7
8
Cost of Current Testing
System (in billions of
dollars)
Cost of Proposed Testing
System (in billions of
dollars)
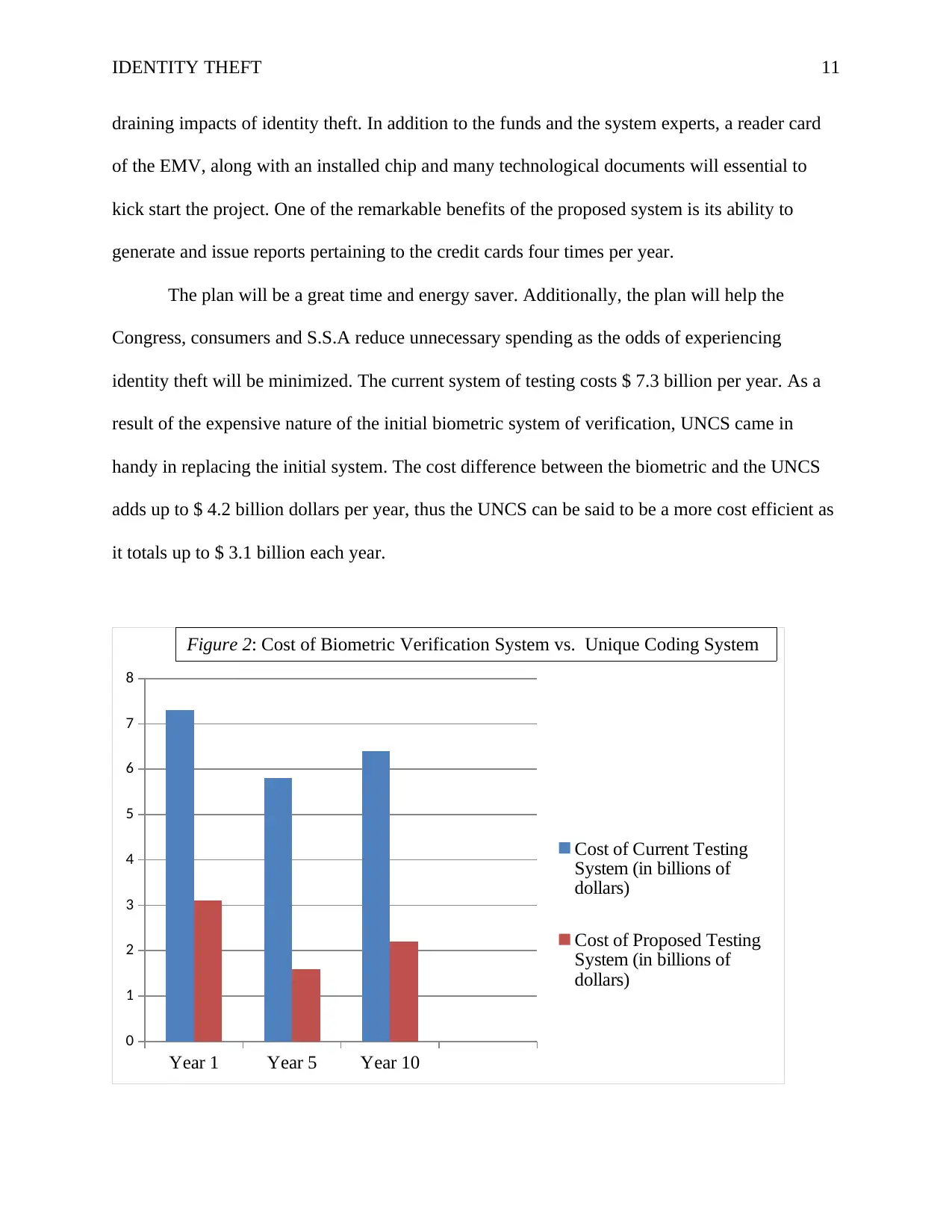
Figure 2: Cost of Biometric Verification System vs. Unique Coding System
draining impacts of identity theft. In addition to the funds and the system experts, a reader card
of the EMV, along with an installed chip and many technological documents will essential to
kick start the project. One of the remarkable benefits of the proposed system is its ability to
generate and issue reports pertaining to the credit cards four times per year.
The plan will be a great time and energy saver. Additionally, the plan will help the
Congress, consumers and S.S.A reduce unnecessary spending as the odds of experiencing
identity theft will be minimized. The current system of testing costs $ 7.3 billion per year. As a
result of the expensive nature of the initial biometric system of verification, UNCS came in
handy in replacing the initial system. The cost difference between the biometric and the UNCS
adds up to $ 4.2 billion dollars per year, thus the UNCS can be said to be a more cost efficient as
it totals up to $ 3.1 billion each year.
Year 1 Year 5 Year 10
0
1
2
3
4
5
6
7
8
Cost of Current Testing
System (in billions of
dollars)
Cost of Proposed Testing
System (in billions of
dollars)
Figure 2: Cost of Biometric Verification System vs. Unique Coding System

IDENTITY THEFT 12
Figure 2: The figure above indicates the biometric verification system cost. A shown, the figures
are in billions of dollars. The part in blue shows the program’s first year, and then 5 and 10 years
later. The red part shows the UCS in a similar organization of 3 years: 1, 5, and 10.From the
figure, it is evident that the implementation of UNCs will, in the short and long term, save
billions of dollars.
Conclusion
To conclude, technology can be used to eradicate identity theft. Under enforcement of
cybercrimes and E-commerce has increased the odds of Internet identity theft occurring. Lack of
information and forensic challenges are some of the contributors to the under enforcement. In the
case where the suspect falls under another jurisdiction, the local enforcement bodies should be
engaged. (Swire, 2009). Conversely, the concept is that Congress needs to be accountable, and
not the hacker, in cases where the FACTA is under enforced as well as not dealing with the issue
of massive distribution of Social Security numbers. (Linnhoff&Langenderfer, 2004).
Additionally, in a scenario where the Congress fails to give a resolution to identity theft,
financial and social disasters will follow. In addition, UNCS will be instrumental in time saving
as there will be issuance of reports four times in a year, not to mention the effectiveness of the
system. The biometric system is costly and cannot be compared to the new system in terms of
cost effectiveness.
Figure 2: The figure above indicates the biometric verification system cost. A shown, the figures
are in billions of dollars. The part in blue shows the program’s first year, and then 5 and 10 years
later. The red part shows the UCS in a similar organization of 3 years: 1, 5, and 10.From the
figure, it is evident that the implementation of UNCs will, in the short and long term, save
billions of dollars.
Conclusion
To conclude, technology can be used to eradicate identity theft. Under enforcement of
cybercrimes and E-commerce has increased the odds of Internet identity theft occurring. Lack of
information and forensic challenges are some of the contributors to the under enforcement. In the
case where the suspect falls under another jurisdiction, the local enforcement bodies should be
engaged. (Swire, 2009). Conversely, the concept is that Congress needs to be accountable, and
not the hacker, in cases where the FACTA is under enforced as well as not dealing with the issue
of massive distribution of Social Security numbers. (Linnhoff&Langenderfer, 2004).
Additionally, in a scenario where the Congress fails to give a resolution to identity theft,
financial and social disasters will follow. In addition, UNCS will be instrumental in time saving
as there will be issuance of reports four times in a year, not to mention the effectiveness of the
system. The biometric system is costly and cannot be compared to the new system in terms of
cost effectiveness.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.