Technology in Organisations: Big Data, Security, and Telecom
VerifiedAdded on 2022/12/05
|13
|3456
|498
Report
AI Summary
This report examines the role of technology within organizations, focusing on big data, security, and telecommunications. It discusses the characteristics and benefits of big data, particularly within the context of Arden University, highlighting its application in departments like registration and IT. The report then delves into security and privacy concerns, emphasizing the importance of GDPR compliance and IT security measures such as data encryption, firewalls, and secure browsers. Finally, it explores cellular networks, their components, and advantages, along with the use of spreadsheets for data calculation, providing specific examples using Excel formulas to analyze employee salary data. This comprehensive analysis provides valuable insights into the multifaceted role of technology in modern organizations.

Technology in
Organisation
Organisation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
TASK 1 – Case Study & Questions.................................................................................................1
Big Data and role....................................................................................................................1
Benefits of big data.................................................................................................................2
TASK 2 – Security and Privacy.......................................................................................................3
GDPR and data and IT security and privacy..........................................................................3
TASK 3 – Telecommunication and spreadsheets............................................................................4
Cellular networks and Components........................................................................................4
advantages of Cellular Network.............................................................................................5
Data calculation using Spreadsheet........................................................................................6
Calculate the following using excel formula and spreadsheet...............................................7
Formulas:..............................................................................................................................7
Calculate the number of employees with a gross salary more than £79900.00.....................9
Calculate the number of employees with a Net salary less than £67499.99........................10
References:.....................................................................................................................................11
Books and Journals...............................................................................................................11
TASK 1 – Case Study & Questions.................................................................................................1
Big Data and role....................................................................................................................1
Benefits of big data.................................................................................................................2
TASK 2 – Security and Privacy.......................................................................................................3
GDPR and data and IT security and privacy..........................................................................3
TASK 3 – Telecommunication and spreadsheets............................................................................4
Cellular networks and Components........................................................................................4
advantages of Cellular Network.............................................................................................5
Data calculation using Spreadsheet........................................................................................6
Calculate the following using excel formula and spreadsheet...............................................7
Formulas:..............................................................................................................................7
Calculate the number of employees with a gross salary more than £79900.00.....................9
Calculate the number of employees with a Net salary less than £67499.99........................10
References:.....................................................................................................................................11
Books and Journals...............................................................................................................11

TASK 1 – Case Study & Questions
Big Data and role
Data can be in the form of a quantity character symbol by which computer perform various
operations which may be stored or transmitted in the form of electromagnetic signals. A term big
was added with the data which transformed into a new concept known as a big data that is the
collection of huge volume data which is growing exponentially with the time (Wiggins and et.
al., 2020) . The big letters are so large in volume and are so complex that the traditional methods
of managing the data and not able to store a process them efficiently due to its huge size. Big
data is the most common word these days which basically means the information in the large
size. Big data is the set of data in the high magnitude. The best method to describe the big data is
using six V’s that are discussed below:
Volume: The main characteristic of the big data is its size and sheet volume. Volume is
defines the relationship between the size and the processing capacity of the big data. The
volume of the data keeps on changing as the data collection continues to add rapidly.
Variety: the variety represents the broad range of variety of data that is been stored and is
required to be processed and analysed. Variety means the heterogeneous sources and the
nature of data can be structured or unstructured. For example in the organisation the data
is in the form of emails, photos, videos, text messages, spreadsheets, PDF, audio etc. it
defines the variety of data.
Velocity: The velocity defines the speed to generate the data. Velocity refers how fast a
data can be generated and processed in order to meet the potential in the data. The
outstanding velocity helps in continuous and massive flow of data.
Value: The value of data defines what worth a big data can provide when it is processed
and analysed. Data is of no use until and unless it is turned into the value data which can
be utilised to get the benefits (Trewin, 2020).
Veracity: The veracity is the term that defines the quality and the origin of the data which
helps in considering how questionable impair information is being gathered. Hence, the
basically veracity is the trustworthiness of the data.
1
Big Data and role
Data can be in the form of a quantity character symbol by which computer perform various
operations which may be stored or transmitted in the form of electromagnetic signals. A term big
was added with the data which transformed into a new concept known as a big data that is the
collection of huge volume data which is growing exponentially with the time (Wiggins and et.
al., 2020) . The big letters are so large in volume and are so complex that the traditional methods
of managing the data and not able to store a process them efficiently due to its huge size. Big
data is the most common word these days which basically means the information in the large
size. Big data is the set of data in the high magnitude. The best method to describe the big data is
using six V’s that are discussed below:
Volume: The main characteristic of the big data is its size and sheet volume. Volume is
defines the relationship between the size and the processing capacity of the big data. The
volume of the data keeps on changing as the data collection continues to add rapidly.
Variety: the variety represents the broad range of variety of data that is been stored and is
required to be processed and analysed. Variety means the heterogeneous sources and the
nature of data can be structured or unstructured. For example in the organisation the data
is in the form of emails, photos, videos, text messages, spreadsheets, PDF, audio etc. it
defines the variety of data.
Velocity: The velocity defines the speed to generate the data. Velocity refers how fast a
data can be generated and processed in order to meet the potential in the data. The
outstanding velocity helps in continuous and massive flow of data.
Value: The value of data defines what worth a big data can provide when it is processed
and analysed. Data is of no use until and unless it is turned into the value data which can
be utilised to get the benefits (Trewin, 2020).
Veracity: The veracity is the term that defines the quality and the origin of the data which
helps in considering how questionable impair information is being gathered. Hence, the
basically veracity is the trustworthiness of the data.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Variability: Variability is it term that refers to the changes in the formation of data in a
particular period of a time. In simple words the constantly changing of big data in order
to change its meaning is one of the characteristic of the big data.
After, analysing the above V's of the big data it is critically evaluated that the role of big data
in the Arden University is within the two departments the first is registration or reception
department and second in IT department.
There is large amount of data of students and teachers in the Arden University that is
required to be maintained stored and analysed at the various situations for which the term big
data is utilised by the reception department in order to store the large volume and variety of
the data.
The IT department of Arden University have a large volume of data related to the software is
installed number of computers and other input and output devices that are data begin size to
be maintained by the traditional method therefore there is a big role of big data in storing,
analysing and processing of the data information’s of the IT department (Kayikci and et. al.,
2020).
Benefits of big data
The implementation of the adoption of big data processing in the ordinary University
provides the university with the various benefits which helps in improving the operational
efficiency as well as creating the outside intelligence then that helps in making the decisions
within the university regarding the student’s growth and opportunities (Rinta-Möykky, 2020).
Some of the benefits that Arden University will gain by adopting big data are discuss below:
Big Data in University can target the students for the scholarship that can provide the worth to
the university. Many students those are not financially active and require the scholarship in order
to complete their education and higher education for which many universities provide
scholarship by conducting some test by which students can prove their worth. For this University
can utilise the concept of big data to identify potential students and their performance in the test
who can fully utilise the benefits of scholarship and contribute their hard work for the betterment
of the Arden University.
Arden University can use the big data in order to identify the institutional problems as well as to
identify the possibilities for the positive change among the university that will help in more
student retention and targeting the specific amount of students that can provide the worth and
2
particular period of a time. In simple words the constantly changing of big data in order
to change its meaning is one of the characteristic of the big data.
After, analysing the above V's of the big data it is critically evaluated that the role of big data
in the Arden University is within the two departments the first is registration or reception
department and second in IT department.
There is large amount of data of students and teachers in the Arden University that is
required to be maintained stored and analysed at the various situations for which the term big
data is utilised by the reception department in order to store the large volume and variety of
the data.
The IT department of Arden University have a large volume of data related to the software is
installed number of computers and other input and output devices that are data begin size to
be maintained by the traditional method therefore there is a big role of big data in storing,
analysing and processing of the data information’s of the IT department (Kayikci and et. al.,
2020).
Benefits of big data
The implementation of the adoption of big data processing in the ordinary University
provides the university with the various benefits which helps in improving the operational
efficiency as well as creating the outside intelligence then that helps in making the decisions
within the university regarding the student’s growth and opportunities (Rinta-Möykky, 2020).
Some of the benefits that Arden University will gain by adopting big data are discuss below:
Big Data in University can target the students for the scholarship that can provide the worth to
the university. Many students those are not financially active and require the scholarship in order
to complete their education and higher education for which many universities provide
scholarship by conducting some test by which students can prove their worth. For this University
can utilise the concept of big data to identify potential students and their performance in the test
who can fully utilise the benefits of scholarship and contribute their hard work for the betterment
of the Arden University.
Arden University can use the big data in order to identify the institutional problems as well as to
identify the possibilities for the positive change among the university that will help in more
student retention and targeting the specific amount of students that can provide the worth and
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

good image for the development of the institution. Adoption of big data stores large amount of
previous data into the software easily without any load which solve the problem of enrolment
decline in the higher education of the Arden University therefore by using the big data the
organisation can determine the factors that are leading to the decrement of enrolment and when,
where and how (Lopes, Guarda and Oliveira, 2020).
Adoption of big data in the departments of the Arden University help in easy accessible of data
of files from various cabinets as earlier it was very Messy and time consuming process to access
the file from the various departments. Due to infrastructure to store the data very small therefore
department used to have the different data storing space in order to access some file the person is
required to go to particular place but with big data the person can easily access the file from any
location without any barrier to growth and understanding. Some of the some of the other benefits
that a big data can provide in Arden University are updating the grading systems, reframing
course materials, customised learning programs etc.
TASK 2 – Security and Privacy
GDPR and data and IT security and privacy
All the Business organisations are now dealing with the large volumes of data related to
personal or the financial data. And with the digitalization among the organisation there is
continuous receiving and transmitting of data through the digital mediums and also collecting
storing and creating the data over the digital and online mediums. The concept of big data and
the emergence of technology in storing and sharing of data within the organisation have
increased the threat of malware activities that are highly risking the loss and stealing of the data
within the organisations (Taylor and Whitton, 2020). Therefore, it has become very essential for
the organisations to implement it security and protection measures in the organisation order to
protect the confidentiality, integrity and availability of the personnel data, data related to the
clients and financial data. The primary aim of IT security is to protect the confidentiality and
integrity of the computer systems and the data stored and processed within it from the malicious
practices. There are many data security technologies of different shapes and forms that are
utilised to protect the data from the external sources and also helps the organisation in
safeguarding the data from inside too. Some of the IT security and data privacy measures that an
organisation must implement are discussed below:
3
previous data into the software easily without any load which solve the problem of enrolment
decline in the higher education of the Arden University therefore by using the big data the
organisation can determine the factors that are leading to the decrement of enrolment and when,
where and how (Lopes, Guarda and Oliveira, 2020).
Adoption of big data in the departments of the Arden University help in easy accessible of data
of files from various cabinets as earlier it was very Messy and time consuming process to access
the file from the various departments. Due to infrastructure to store the data very small therefore
department used to have the different data storing space in order to access some file the person is
required to go to particular place but with big data the person can easily access the file from any
location without any barrier to growth and understanding. Some of the some of the other benefits
that a big data can provide in Arden University are updating the grading systems, reframing
course materials, customised learning programs etc.
TASK 2 – Security and Privacy
GDPR and data and IT security and privacy
All the Business organisations are now dealing with the large volumes of data related to
personal or the financial data. And with the digitalization among the organisation there is
continuous receiving and transmitting of data through the digital mediums and also collecting
storing and creating the data over the digital and online mediums. The concept of big data and
the emergence of technology in storing and sharing of data within the organisation have
increased the threat of malware activities that are highly risking the loss and stealing of the data
within the organisations (Taylor and Whitton, 2020). Therefore, it has become very essential for
the organisations to implement it security and protection measures in the organisation order to
protect the confidentiality, integrity and availability of the personnel data, data related to the
clients and financial data. The primary aim of IT security is to protect the confidentiality and
integrity of the computer systems and the data stored and processed within it from the malicious
practices. There are many data security technologies of different shapes and forms that are
utilised to protect the data from the external sources and also helps the organisation in
safeguarding the data from inside too. Some of the IT security and data privacy measures that an
organisation must implement are discussed below:
3

Data Encryption: the most well-known measure for the data privacy and IT security is data
encryption which applies the particular code over the individual piece of data by which any
unauthorised person cannot grant an access over the encrypted data without the personal pin or
key developed by the authorised person of the data (Helgadóttir, 2020).
Firewall: The organisations can implement the firewall which can easily protect the cyber
attacks within their personal computer systems and the systems of the organisation. It is the
sophisticated tool for the security of the data as it filters the network traffic and block
unauthorised users from accessing their IP addresses. The firewall blocks the unauthorised IP
addresses.
Secure browsers: Secure browsers: now each and every company is using the internet to
browse various information’s and also to share the information’s therefore it is very impossible
to avoid the hackers or the third party and trends from weakening a security and tracking the
users business activities via internet (Kim, 2021). Companies must implement the use of secure
browsers that does not save any information related to the login ID’s of the employees and does
not track any online activities which could track the business of the organisation there by
restricting the cookies and third party sites. For this company can also ask their employees to use
the safe and secure mode attribute.
Install and maintain antivirus updated: Every device such as computer that are authorized or
granted to access the server or database is considered as a potential access origin for wicked
infiltrations. For example, any device with invalid or out of date antivirus or security tools is a
frail and fragile link which can cause the risk to the safety of the organisation. Therefore, while
comparing various service lenders and picking up the right and authenticate antivirus software is
highly important (Sivaraman and et. al., 2018).
TASK 3 – Telecommunication and spreadsheets
Cellular networks and Components
Cellular network
Cellular network are also recognized as mobile networks which are the network for
communication with wireless connection network circulated over the various ground areas
known as the cells and each one of these cell is served by permanent location transceiver.
Cellular Networks are commonly connected with the most cell phones, smart phones and dial-up
4
encryption which applies the particular code over the individual piece of data by which any
unauthorised person cannot grant an access over the encrypted data without the personal pin or
key developed by the authorised person of the data (Helgadóttir, 2020).
Firewall: The organisations can implement the firewall which can easily protect the cyber
attacks within their personal computer systems and the systems of the organisation. It is the
sophisticated tool for the security of the data as it filters the network traffic and block
unauthorised users from accessing their IP addresses. The firewall blocks the unauthorised IP
addresses.
Secure browsers: Secure browsers: now each and every company is using the internet to
browse various information’s and also to share the information’s therefore it is very impossible
to avoid the hackers or the third party and trends from weakening a security and tracking the
users business activities via internet (Kim, 2021). Companies must implement the use of secure
browsers that does not save any information related to the login ID’s of the employees and does
not track any online activities which could track the business of the organisation there by
restricting the cookies and third party sites. For this company can also ask their employees to use
the safe and secure mode attribute.
Install and maintain antivirus updated: Every device such as computer that are authorized or
granted to access the server or database is considered as a potential access origin for wicked
infiltrations. For example, any device with invalid or out of date antivirus or security tools is a
frail and fragile link which can cause the risk to the safety of the organisation. Therefore, while
comparing various service lenders and picking up the right and authenticate antivirus software is
highly important (Sivaraman and et. al., 2018).
TASK 3 – Telecommunication and spreadsheets
Cellular networks and Components
Cellular network
Cellular network are also recognized as mobile networks which are the network for
communication with wireless connection network circulated over the various ground areas
known as the cells and each one of these cell is served by permanent location transceiver.
Cellular Networks are commonly connected with the most cell phones, smart phones and dial-up
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

devices. The currently deployed wireless networks suggest GSM, LED, IoT and known as
cellular networks are divided into the small size cells over the entire area to connect with the
mobile subscribers that high frequency to provide the data and voice translation services. Each
cell has its own base station. Cellular networks are easy to upgrade tool that are easy to maintain
and wireless without any cables and allow the fast data transmission service (Sun, Strang and
Pambel, 2020).
Principle components of cellular network
The cellular base is the central component of cellular network, which is a fixed
transceiver on a land area also called cells (Bushnaq and et. al., 2020). A device known as
transceiver contains transmitter useful in broadcasting the radio waves and one that interprets the
message is receiver. Both the components of the transceiver are managed in same device and
possess same circuit connection. The Mobile Telephone Switching Office (MTSO) is determined
as the key subcomponent for the cellular network base. The role and responsibility of MTSO is
create a communication link between the numerous mobile devices but due to the decrease in the
distance from the cellular base that is reception, the connection is switched to better and suitable
customer base. The major components of the cellular networks are the public switched telephone
network (PTSN), cell sites with antenna system, mobile subscriber unit (MSU) and a mobile
telephone switching office (MTSO).
Working of cellular network
Firstly the transceiver generates electric signals that is transmitted by the antenna and
converted into the electromagnetic wave which will radiate advocate so what is base which is
again picked up by the receiver antenna there the electromagnetic wave is converted into the
electric signals which helps in the data transmission (Tiew, Lim and Sivagnanasithiyar, 2020).
advantages of Cellular Network
The use of cell network has increased speedily among the business organisation in order to
create the value and worth of the business. The technologies is attached with the cellular
networks such as 4G the four generation data transmission service has speed up the delivery of
high size data. GPS is one of the cellular network technology which stands for the global
positioning system has allowed the business to showcase their position precisely using the
devices all over the globe (Heiberger and Neuwirth, 2010). The wireless networking through the
cellular network has made the business organisation switch towards upgrading and changing
5
cellular networks are divided into the small size cells over the entire area to connect with the
mobile subscribers that high frequency to provide the data and voice translation services. Each
cell has its own base station. Cellular networks are easy to upgrade tool that are easy to maintain
and wireless without any cables and allow the fast data transmission service (Sun, Strang and
Pambel, 2020).
Principle components of cellular network
The cellular base is the central component of cellular network, which is a fixed
transceiver on a land area also called cells (Bushnaq and et. al., 2020). A device known as
transceiver contains transmitter useful in broadcasting the radio waves and one that interprets the
message is receiver. Both the components of the transceiver are managed in same device and
possess same circuit connection. The Mobile Telephone Switching Office (MTSO) is determined
as the key subcomponent for the cellular network base. The role and responsibility of MTSO is
create a communication link between the numerous mobile devices but due to the decrease in the
distance from the cellular base that is reception, the connection is switched to better and suitable
customer base. The major components of the cellular networks are the public switched telephone
network (PTSN), cell sites with antenna system, mobile subscriber unit (MSU) and a mobile
telephone switching office (MTSO).
Working of cellular network
Firstly the transceiver generates electric signals that is transmitted by the antenna and
converted into the electromagnetic wave which will radiate advocate so what is base which is
again picked up by the receiver antenna there the electromagnetic wave is converted into the
electric signals which helps in the data transmission (Tiew, Lim and Sivagnanasithiyar, 2020).
advantages of Cellular Network
The use of cell network has increased speedily among the business organisation in order to
create the value and worth of the business. The technologies is attached with the cellular
networks such as 4G the four generation data transmission service has speed up the delivery of
high size data. GPS is one of the cellular network technology which stands for the global
positioning system has allowed the business to showcase their position precisely using the
devices all over the globe (Heiberger and Neuwirth, 2010). The wireless networking through the
cellular network has made the business organisation switch towards upgrading and changing
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
their infrastructure and business practices in order to attain the benefits from the wireless
networks in their business organisation. The major benefit of the cellular network is the wireless
networking which is faster and cheaper as the installation requires no cables, no wires and
process of installation is quick through internet. Cellular networks provide the flexibility to the
employees and employees of the business as from cellular networks data can be shared and
accessed from any locations which facilitates the growth to the business as it saves time and
money both (Broman and Woo, 2018). Network has also provided the benefit of various wireless
networking tools like server, cloud computing, load management, remote device management
which not only decrease the maintenance time and cost of the business but also so reduce the
load of maintaining networks for the IT Business. Instant data sharing is the very imperative
benefit of cellular network in a business cellular network types the business with the cloud
access by which the employees in employer can access any file at any time without any problem
of requirement of storage in pc.
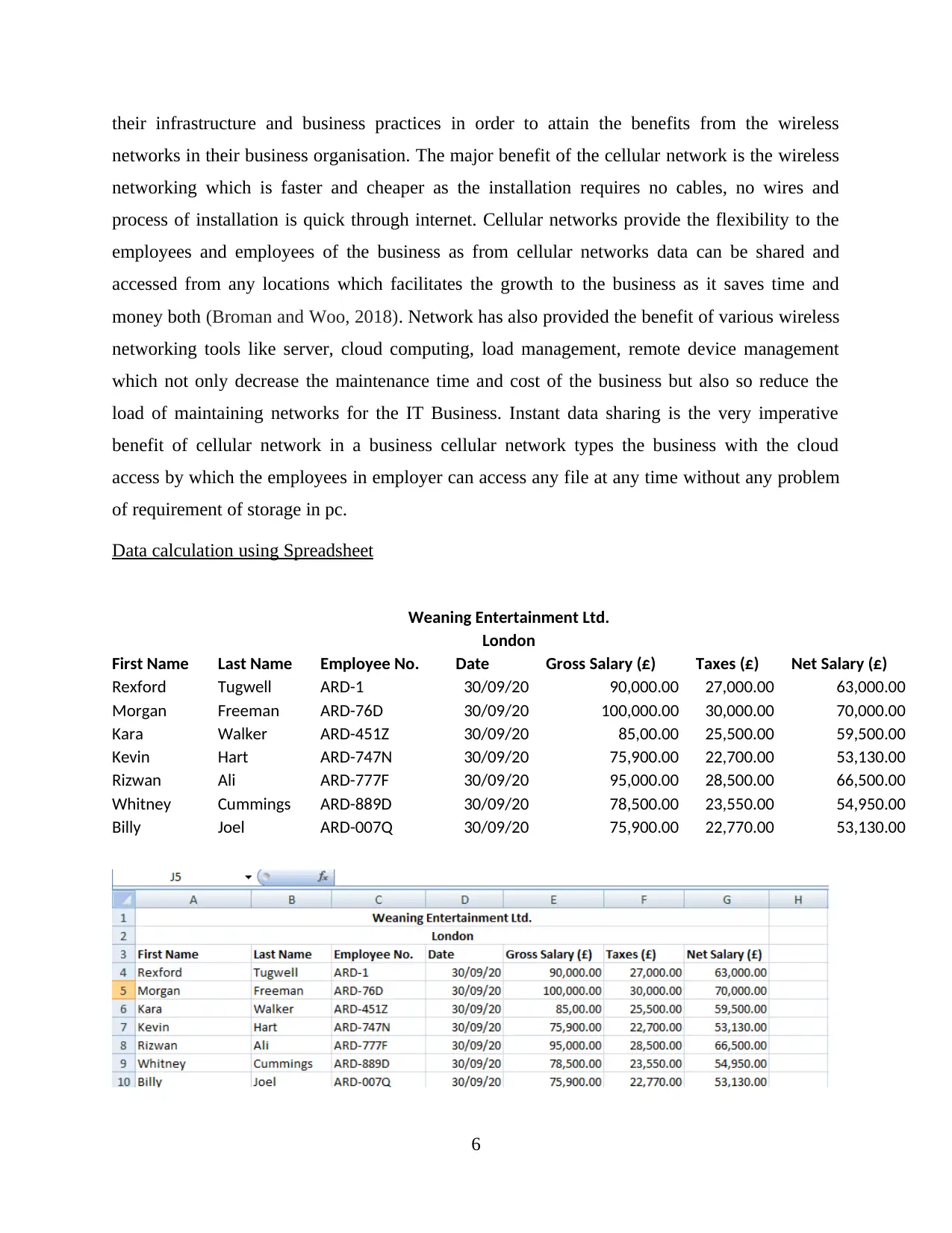
Data calculation using Spreadsheet
Weaning Entertainment Ltd.
London
First Name Last Name Employee No. Date Gross Salary (£) Taxes (£) Net Salary (£)
Rexford Tugwell ARD-1 30/09/20 90,000.00 27,000.00 63,000.00
Morgan Freeman ARD-76D 30/09/20 100,000.00 30,000.00 70,000.00
Kara Walker ARD-451Z 30/09/20 85,00.00 25,500.00 59,500.00
Kevin Hart ARD-747N 30/09/20 75,900.00 22,700.00 53,130.00
Rizwan Ali ARD-777F 30/09/20 95,000.00 28,500.00 66,500.00
Whitney Cummings ARD-889D 30/09/20 78,500.00 23,550.00 54,950.00
Billy Joel ARD-007Q 30/09/20 75,900.00 22,770.00 53,130.00
6
networks in their business organisation. The major benefit of the cellular network is the wireless
networking which is faster and cheaper as the installation requires no cables, no wires and
process of installation is quick through internet. Cellular networks provide the flexibility to the
employees and employees of the business as from cellular networks data can be shared and
accessed from any locations which facilitates the growth to the business as it saves time and
money both (Broman and Woo, 2018). Network has also provided the benefit of various wireless
networking tools like server, cloud computing, load management, remote device management
which not only decrease the maintenance time and cost of the business but also so reduce the
load of maintaining networks for the IT Business. Instant data sharing is the very imperative
benefit of cellular network in a business cellular network types the business with the cloud
access by which the employees in employer can access any file at any time without any problem
of requirement of storage in pc.
Data calculation using Spreadsheet
Weaning Entertainment Ltd.
London
First Name Last Name Employee No. Date Gross Salary (£) Taxes (£) Net Salary (£)
Rexford Tugwell ARD-1 30/09/20 90,000.00 27,000.00 63,000.00
Morgan Freeman ARD-76D 30/09/20 100,000.00 30,000.00 70,000.00
Kara Walker ARD-451Z 30/09/20 85,00.00 25,500.00 59,500.00
Kevin Hart ARD-747N 30/09/20 75,900.00 22,700.00 53,130.00
Rizwan Ali ARD-777F 30/09/20 95,000.00 28,500.00 66,500.00
Whitney Cummings ARD-889D 30/09/20 78,500.00 23,550.00 54,950.00
Billy Joel ARD-007Q 30/09/20 75,900.00 22,770.00 53,130.00
6
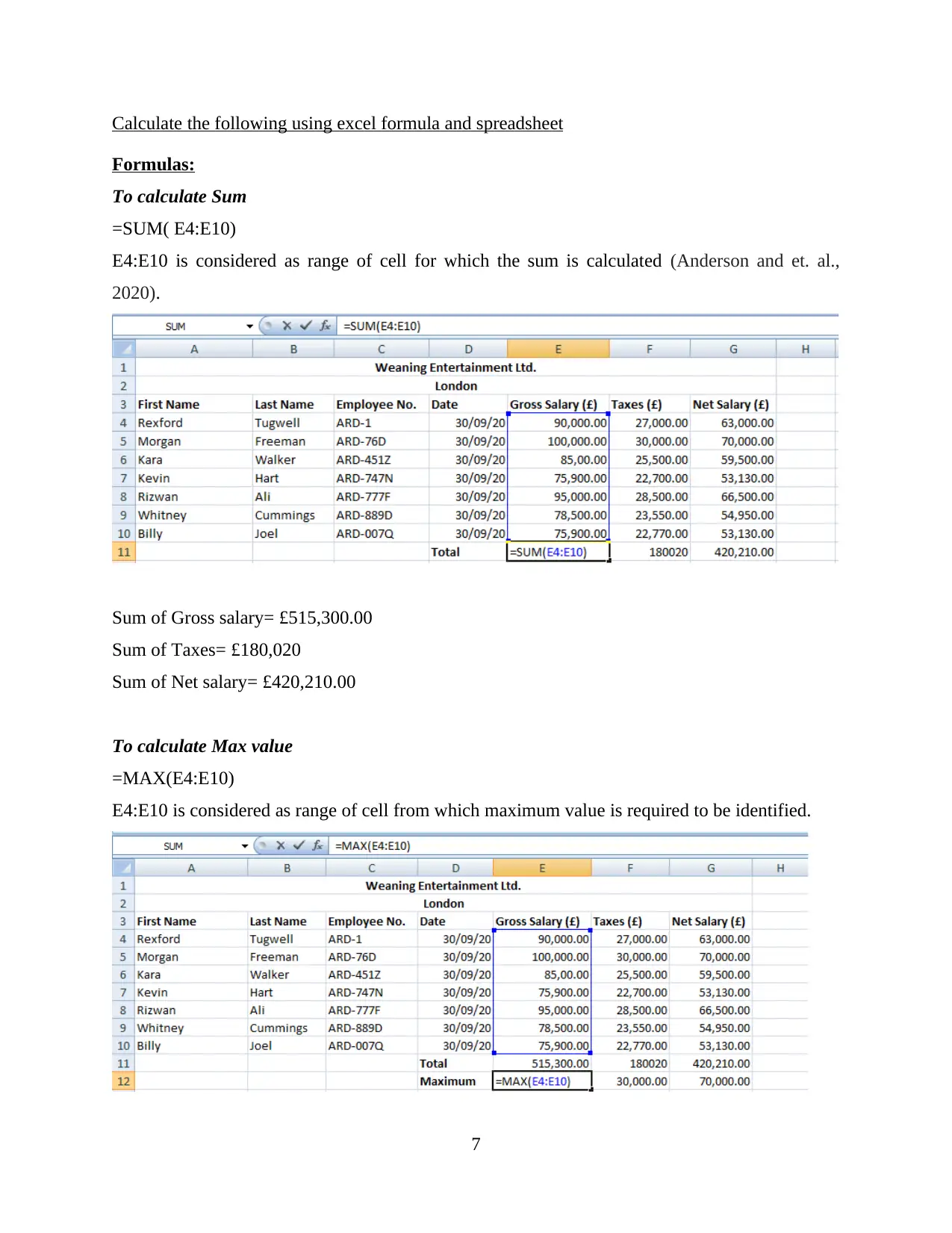
Calculate the following using excel formula and spreadsheet
Formulas:
To calculate Sum
=SUM( E4:E10)
E4:E10 is considered as range of cell for which the sum is calculated (Anderson and et. al.,
2020).
Sum of Gross salary= £515,300.00
Sum of Taxes= £180,020
Sum of Net salary= £420,210.00
To calculate Max value
=MAX(E4:E10)
E4:E10 is considered as range of cell from which maximum value is required to be identified.
7
Formulas:
To calculate Sum
=SUM( E4:E10)
E4:E10 is considered as range of cell for which the sum is calculated (Anderson and et. al.,
2020).
Sum of Gross salary= £515,300.00
Sum of Taxes= £180,020
Sum of Net salary= £420,210.00
To calculate Max value
=MAX(E4:E10)
E4:E10 is considered as range of cell from which maximum value is required to be identified.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
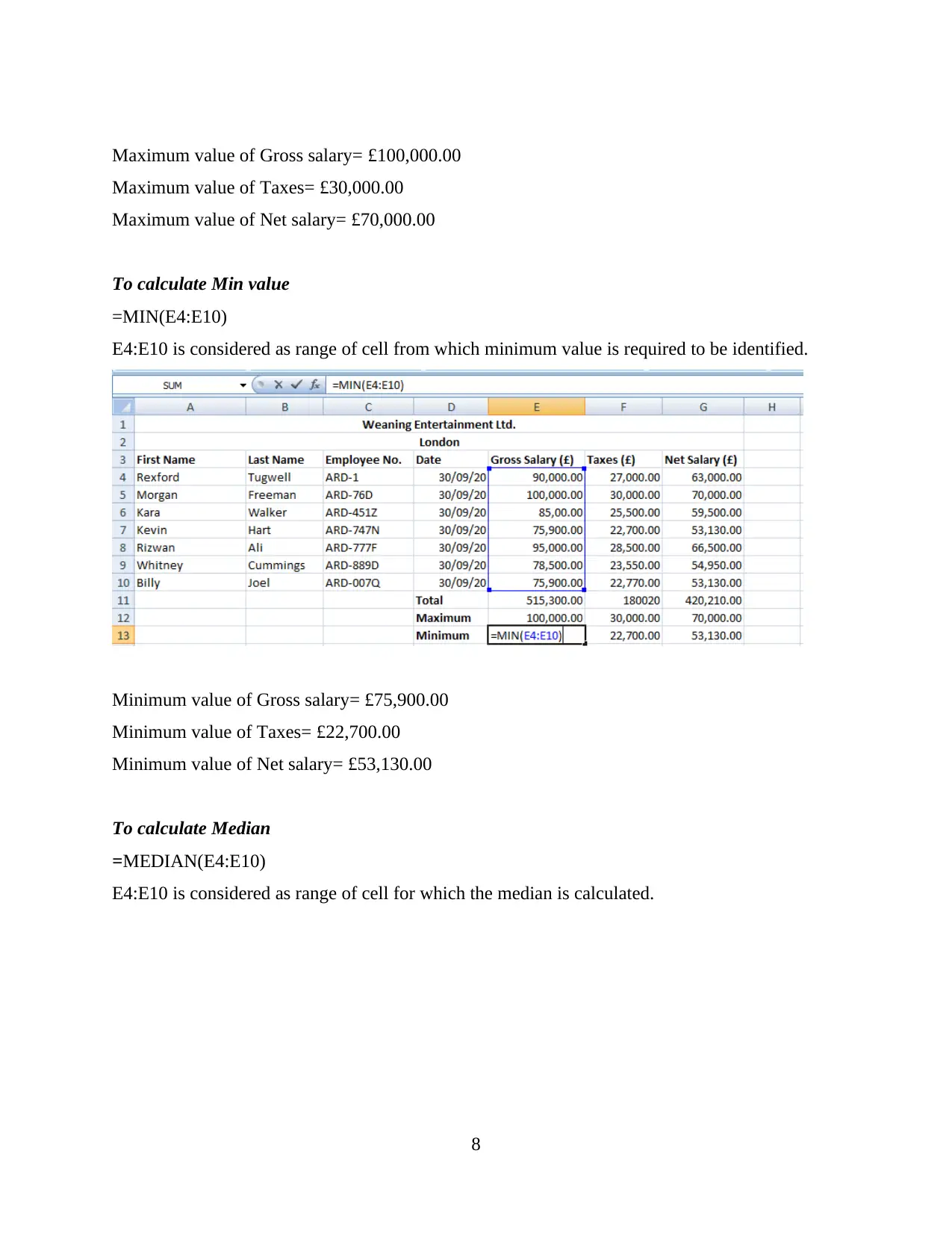
Maximum value of Gross salary= £100,000.00
Maximum value of Taxes= £30,000.00
Maximum value of Net salary= £70,000.00
To calculate Min value
=MIN(E4:E10)
E4:E10 is considered as range of cell from which minimum value is required to be identified.
Minimum value of Gross salary= £75,900.00
Minimum value of Taxes= £22,700.00
Minimum value of Net salary= £53,130.00
To calculate Median
=MEDIAN(E4:E10)
E4:E10 is considered as range of cell for which the median is calculated.
8
Maximum value of Taxes= £30,000.00
Maximum value of Net salary= £70,000.00
To calculate Min value
=MIN(E4:E10)
E4:E10 is considered as range of cell from which minimum value is required to be identified.
Minimum value of Gross salary= £75,900.00
Minimum value of Taxes= £22,700.00
Minimum value of Net salary= £53,130.00
To calculate Median
=MEDIAN(E4:E10)
E4:E10 is considered as range of cell for which the median is calculated.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
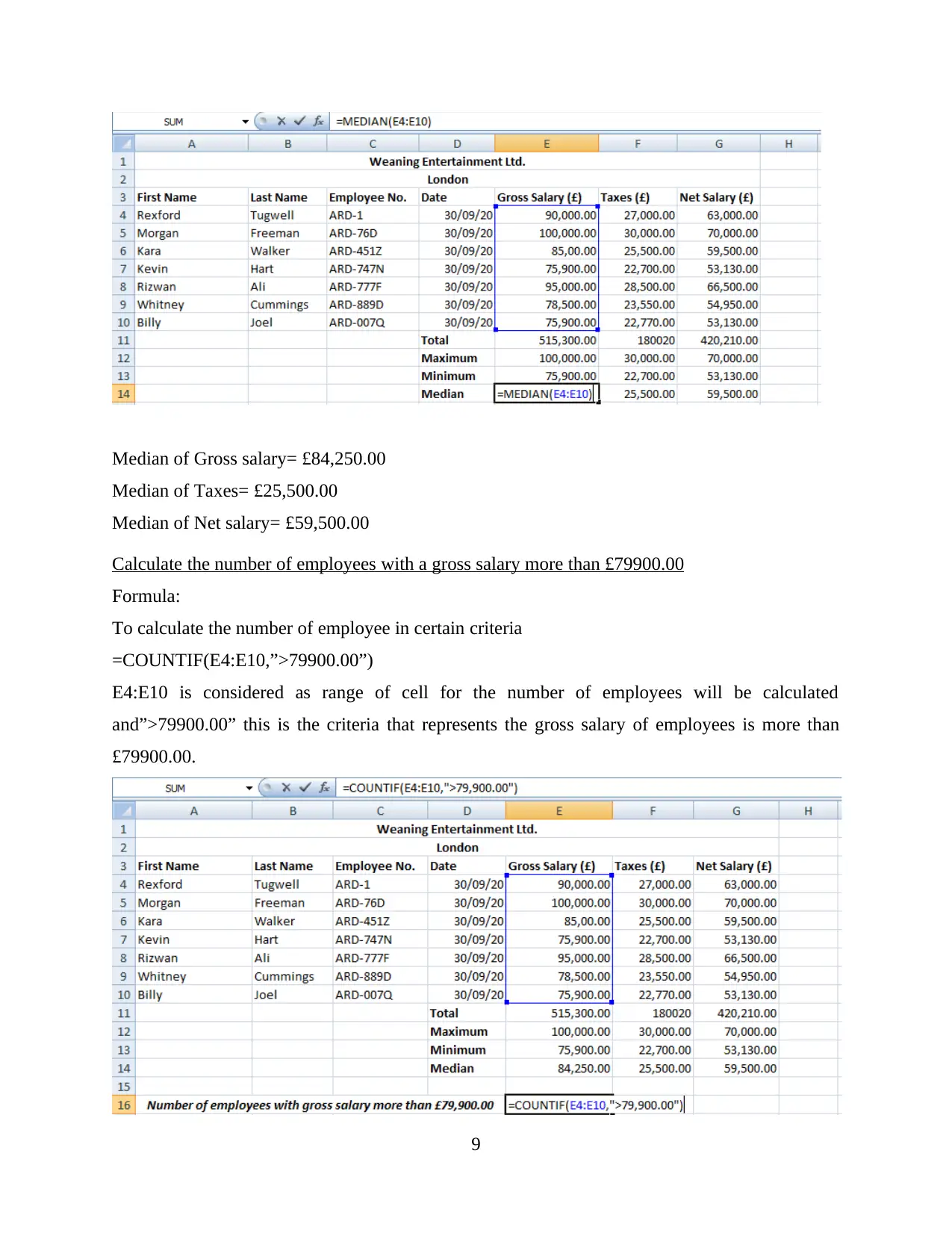
Median of Gross salary= £84,250.00
Median of Taxes= £25,500.00
Median of Net salary= £59,500.00
Calculate the number of employees with a gross salary more than £79900.00
Formula:
To calculate the number of employee in certain criteria
=COUNTIF(E4:E10,”>79900.00”)
E4:E10 is considered as range of cell for the number of employees will be calculated
and”>79900.00” this is the criteria that represents the gross salary of employees is more than
£79900.00.
9
Median of Taxes= £25,500.00
Median of Net salary= £59,500.00
Calculate the number of employees with a gross salary more than £79900.00
Formula:
To calculate the number of employee in certain criteria
=COUNTIF(E4:E10,”>79900.00”)
E4:E10 is considered as range of cell for the number of employees will be calculated
and”>79900.00” this is the criteria that represents the gross salary of employees is more than
£79900.00.
9
The number of employees of Weaning Entertainment ltd. with a gross salary more than
£79900.00 is 3.
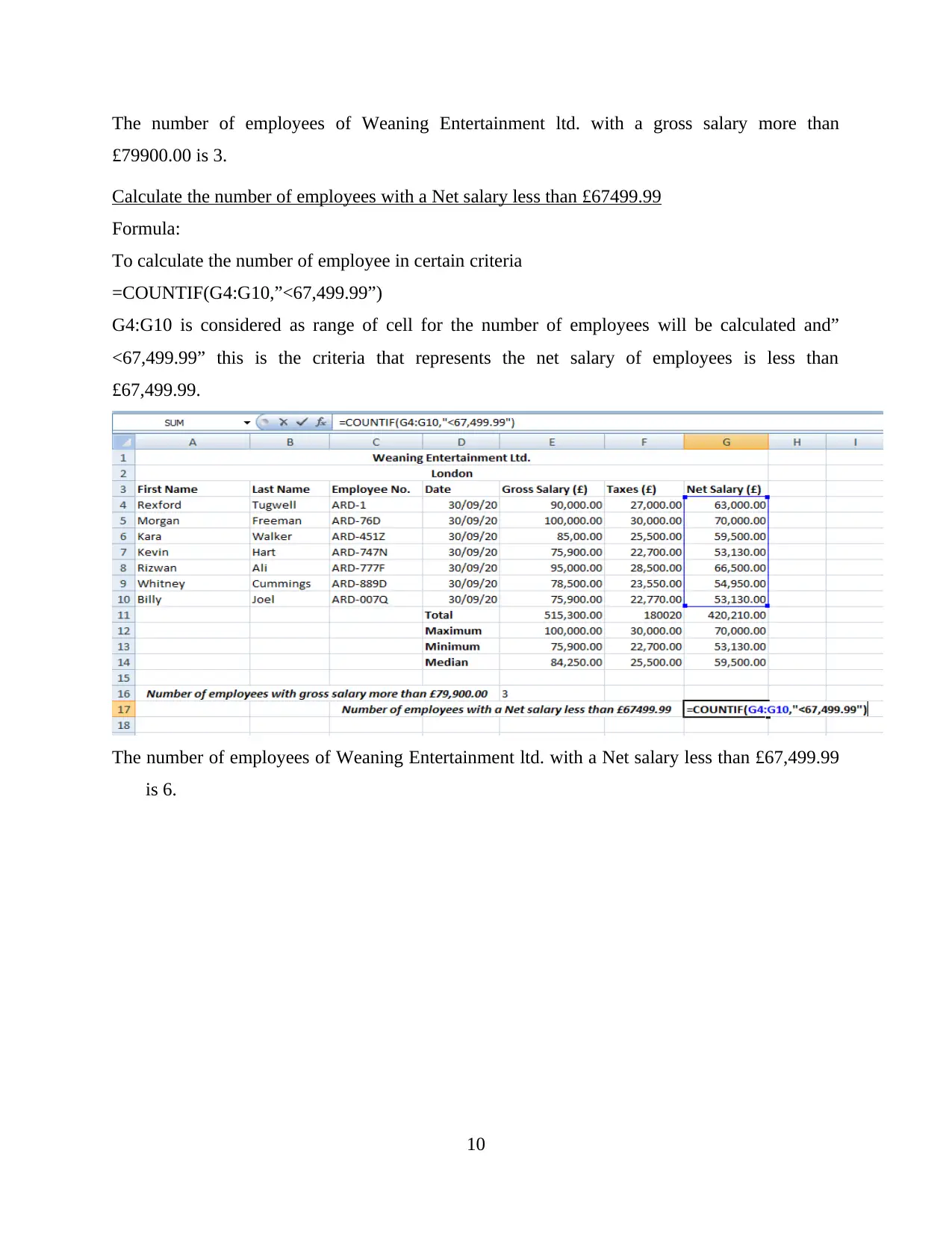
Calculate the number of employees with a Net salary less than £67499.99
Formula:
To calculate the number of employee in certain criteria
=COUNTIF(G4:G10,”<67,499.99”)
G4:G10 is considered as range of cell for the number of employees will be calculated and”
<67,499.99” this is the criteria that represents the net salary of employees is less than
£67,499.99.
The number of employees of Weaning Entertainment ltd. with a Net salary less than £67,499.99
is 6.
10
£79900.00 is 3.
Calculate the number of employees with a Net salary less than £67499.99
Formula:
To calculate the number of employee in certain criteria
=COUNTIF(G4:G10,”<67,499.99”)
G4:G10 is considered as range of cell for the number of employees will be calculated and”
<67,499.99” this is the criteria that represents the net salary of employees is less than
£67,499.99.
The number of employees of Weaning Entertainment ltd. with a Net salary less than £67,499.99
is 6.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





