Technology in Organizations: Arden University Big Data, IT Security
VerifiedAdded on 2022/11/30
|13
|3719
|409
Report
AI Summary
This report examines the significant role of technology in modern organizations, using Arden University as a case study. It begins by defining and exploring the multifaceted aspects of big data, including its types, features, and its crucial role in decision-making, particularly within educational institutions. The report then delves into the merits of utilizing big data, such as innovation in services, enhanced customer retention, and risk analysis. Furthermore, it discusses information technology security and data privacy measures, including tools like DNS protection and firewalls, while also outlining provisions of the General Data Protection Regulation (GDPR). Finally, the report explains cellular networks, their components, operational principles, and the business benefits they offer, providing a comprehensive overview of technology's impact on organizational efficiency and security.

Technology in
Organization
Organization
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION.......................................................................................................................................3
QUESTION 1..............................................................................................................................................3
Big Data and its role in the Arden University..........................................................................................3
Discussion on merits of using Big Data that is gained by Arden University............................................4
QUESTION 2..............................................................................................................................................5
Explanation of the Information and technology security and measures of the data privacy which
businesses can implement together with some of the provisions of GDPR..............................................5
QUESTION 3..............................................................................................................................................8
What is cellular network, its principles components and how does it works...........................................8
Benefits of cellular network to the business............................................................................................9
CONCLUSION.........................................................................................................................................12
REFERENCES..........................................................................................................................................13
INTRODUCTION.......................................................................................................................................3
QUESTION 1..............................................................................................................................................3
Big Data and its role in the Arden University..........................................................................................3
Discussion on merits of using Big Data that is gained by Arden University............................................4
QUESTION 2..............................................................................................................................................5
Explanation of the Information and technology security and measures of the data privacy which
businesses can implement together with some of the provisions of GDPR..............................................5
QUESTION 3..............................................................................................................................................8
What is cellular network, its principles components and how does it works...........................................8
Benefits of cellular network to the business............................................................................................9
CONCLUSION.........................................................................................................................................12
REFERENCES..........................................................................................................................................13

INTRODUCTION
The technology has played an integral part in the growth and success of the company. It
has helped the businesses to make their working easier. With the deployment of technology into
the organization, there has been rapid change in the working condition which has resulted in
making the daily operations very easy such as collecting and storing data and information in a
speedy manner. The interaction has also become so easy within the organization and outside it
that there is clear channel of communication being built. There has been now up-gradation in the
technology which has made innovation and invention easy in the business that helps in serving
the customers with best and enhances their experience (Sun and et. al., 2018). Arden University
is chosen for this report. It shall deal with big data, it features, role and benefits and IT security
and data privacy measures. It will also deal with cellular network with its principles and
advantages.
QUESTION 1
Big Data and its role in the Arden University.
The combination or the group of data and information which covers the exponentially
grown numbers is maintained for a specific time period, it is known as big data. It is bigger in
size and supports the business in managing the complex data by usage of various tools and
techniques that can help in ensuring the efficient and effective working. There are three types of
big data which includes structured, unstructured and semi structured. The main role of big data is
to help in efficient making of decision and contributes in maintenance of the new opportunities
so that the organization can be enhanced with growth and development (Lele, Lele and Bose,
2019). It plays an essential role of collecting and then storing the information and Arden
University uses big data in its organization which helps in managing the data and information
confidentially. It also helps in protecting the data from unauthorized access and allows accessing
information that relates to staff and the students.
Features of Big data
The technology has played an integral part in the growth and success of the company. It
has helped the businesses to make their working easier. With the deployment of technology into
the organization, there has been rapid change in the working condition which has resulted in
making the daily operations very easy such as collecting and storing data and information in a
speedy manner. The interaction has also become so easy within the organization and outside it
that there is clear channel of communication being built. There has been now up-gradation in the
technology which has made innovation and invention easy in the business that helps in serving
the customers with best and enhances their experience (Sun and et. al., 2018). Arden University
is chosen for this report. It shall deal with big data, it features, role and benefits and IT security
and data privacy measures. It will also deal with cellular network with its principles and
advantages.
QUESTION 1
Big Data and its role in the Arden University.
The combination or the group of data and information which covers the exponentially
grown numbers is maintained for a specific time period, it is known as big data. It is bigger in
size and supports the business in managing the complex data by usage of various tools and
techniques that can help in ensuring the efficient and effective working. There are three types of
big data which includes structured, unstructured and semi structured. The main role of big data is
to help in efficient making of decision and contributes in maintenance of the new opportunities
so that the organization can be enhanced with growth and development (Lele, Lele and Bose,
2019). It plays an essential role of collecting and then storing the information and Arden
University uses big data in its organization which helps in managing the data and information
confidentially. It also helps in protecting the data from unauthorized access and allows accessing
information that relates to staff and the students.
Features of Big data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

There are mainly six characteristics of the big data which is also known as 7Vs that are
illustrated below-
Velocity- The main purpose of big data is to make analysis of the high speed processor
together with 8 seasons that is taken in a speedy manner so that data is generated with
enhanced frequency about health and infrastructure.
Variability- It provides for the essential effect and evolution of the disease and illness. It
helps in maintaining the data regarding seasonal issues of the health.
Value- it states about the longitudinal studies about the relevant information and data so
that these are collected in a accurate manner.
Volume- It supports in monitoring high advancement and important signs in the
technology.
Variety- it states regarding the sources of data that in the unstructured form so that the
heterogeneous taxonomies and frequency is maintained.
Veracity- It states about the quality data for which support will help to make the source
for the unreliable information (Cheng and Zhao, 2018).
Role of big data
The big data is commonly used in the insurance, banking, education and government
areas. Arden University uses big data so that it can track all its record, information and data of
the existing and new students. It also helps in proper maintenance of the data and within time.
The role of Big data in the Arden University is discussed below-
Examination department- The main function of this unit is to set the questions and exam
papers. It also keeps the record of every student. The big data helps in keeping and
maintaining the record of every student together with their performance in the academic
session. The score of each student is also maintained with the help of big data.
Administration department- The main function of this functional area is to maintain
proper record of each student. The big data helps in maintaining the personal and other
details of each student in a proper and confidential manner (Ahson and Ilyas, 2017).
illustrated below-
Velocity- The main purpose of big data is to make analysis of the high speed processor
together with 8 seasons that is taken in a speedy manner so that data is generated with
enhanced frequency about health and infrastructure.
Variability- It provides for the essential effect and evolution of the disease and illness. It
helps in maintaining the data regarding seasonal issues of the health.
Value- it states about the longitudinal studies about the relevant information and data so
that these are collected in a accurate manner.
Volume- It supports in monitoring high advancement and important signs in the
technology.
Variety- it states regarding the sources of data that in the unstructured form so that the
heterogeneous taxonomies and frequency is maintained.
Veracity- It states about the quality data for which support will help to make the source
for the unreliable information (Cheng and Zhao, 2018).
Role of big data
The big data is commonly used in the insurance, banking, education and government
areas. Arden University uses big data so that it can track all its record, information and data of
the existing and new students. It also helps in proper maintenance of the data and within time.
The role of Big data in the Arden University is discussed below-
Examination department- The main function of this unit is to set the questions and exam
papers. It also keeps the record of every student. The big data helps in keeping and
maintaining the record of every student together with their performance in the academic
session. The score of each student is also maintained with the help of big data.
Administration department- The main function of this functional area is to maintain
proper record of each student. The big data helps in maintaining the personal and other
details of each student in a proper and confidential manner (Ahson and Ilyas, 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Discussion on merits of using Big Data that is gained by Arden University.
There are many advantages attached in using big data that is enjoyed by businesses and
corporations. The merits of the big data for Arden University is illustrated thereunder-
Innovation in product or service- Using big data helps the businesses to maintain their
new techniques and ideas of the innovations so that there is customer attraction and there
is also retention of the loyal customer base by upgrading the system. Arden University
uses the big data so that their services are protected by the optimum quality and method.
Improvisation in customer retention- The Big data helps in keeping the record of all the
customers in the preferential manner so that their needs and rights are maintained. The
main role of big data is also to help in analyzing the demand, requirement and needs of
the consumers. Arden University makes best use of the big data so that it can identify the
needs and wants of students regarding the course and then the university can try to
implement it.
Analyzing the potential risk- The main purpose of using the big data is to identify the
risk associated with business and also figure out the solution for it by risk management so
that the business can function effectively (Gong and et. al., 2019). Arden University
makes best use of this so that it can create awareness about the risk factors in order to get
prepared for it in advance.
QUESTION 2
Explanation of the Information and technology security and measures of the data privacy which
businesses can implement together with some of the provisions of GDPR.
IT security is defined as the concept which is referred to the strategic cyber security that
helps in eliminating the access which is unauthorized in the business as it mainly functions with
computer network and data. It supports mainly in maintenance of the relevant and confidential
data and information and also blocks the hackers from the information access. The main purpose
of IT Security is to maintain the integrity of information by storing relevant data and keeping it
safe from unauthorized access. If there is any unauthorized access or hacking of the data, it may
affect the functioning of the business so IT security supports in collecting the personal data so
that it is kept safe from such activities. Arden University uses this IT security so that it can keep
There are many advantages attached in using big data that is enjoyed by businesses and
corporations. The merits of the big data for Arden University is illustrated thereunder-
Innovation in product or service- Using big data helps the businesses to maintain their
new techniques and ideas of the innovations so that there is customer attraction and there
is also retention of the loyal customer base by upgrading the system. Arden University
uses the big data so that their services are protected by the optimum quality and method.
Improvisation in customer retention- The Big data helps in keeping the record of all the
customers in the preferential manner so that their needs and rights are maintained. The
main role of big data is also to help in analyzing the demand, requirement and needs of
the consumers. Arden University makes best use of the big data so that it can identify the
needs and wants of students regarding the course and then the university can try to
implement it.
Analyzing the potential risk- The main purpose of using the big data is to identify the
risk associated with business and also figure out the solution for it by risk management so
that the business can function effectively (Gong and et. al., 2019). Arden University
makes best use of this so that it can create awareness about the risk factors in order to get
prepared for it in advance.
QUESTION 2
Explanation of the Information and technology security and measures of the data privacy which
businesses can implement together with some of the provisions of GDPR.
IT security is defined as the concept which is referred to the strategic cyber security that
helps in eliminating the access which is unauthorized in the business as it mainly functions with
computer network and data. It supports mainly in maintenance of the relevant and confidential
data and information and also blocks the hackers from the information access. The main purpose
of IT Security is to maintain the integrity of information by storing relevant data and keeping it
safe from unauthorized access. If there is any unauthorized access or hacking of the data, it may
affect the functioning of the business so IT security supports in collecting the personal data so
that it is kept safe from such activities. Arden University uses this IT security so that it can keep

the information and data in a safe and secure manner by using the data safe managerial system
that supports in maintenance of the confidentiality and makes the information available that is
stored. It draws the secure network which helps in protecting information from the hackers
(Semin and et. al., 2017).
Data privacy measures are those methods that keep the database files and information
protected. The measures of data privacy are aimed to help in application and control of the
technological advancement and also supports in the allocation of resources in the proper manner.
It is an essential aspect of business as it supports in maintaining integrity and confidentiality of
the data by providing protection to them and securing it from the unauthorized access. It helps in
creating no impact on the business functions. Arden University makes use of the data privacy
measures so that it can preserve the security of data by using various protocols that are essential
so that the information is secured from the ambit of cyber-crimes other types of malicious users
that may harm data (Li and et. al., 2017).
Tools and techniques of the IT security and data privacy measures
There has been rise in the technological up-gradation and advancement that has not only
supported businesses in maintaining data properly but has also given rise to the offences which
are called as cybercrimes. In order to prevent these crimes, there are many tools and techniques
which can be used by corporations for securing an protecting the information from unauthorized
access. These are illustrated below-
DNS protection- Domain name is a type of service which is found in the computers that
comprises of an IP address which helps and supports in the browsing so that all sources
are looted from internet by stating the IP address. It is unique to every computer network.
The DNS protection helps in maintenance of the reliability of data so that it is applied by
the cloud services. It gives an approach with the help of which the security interest can be
maintained in business and protection shall be given to data from the threats. Arden
University uses this tool so that it can keep the data secure and prevent the commission of
the cyber -crime in the educational institutional by blocking the malicious users.
Firewalls and intrusion protection IPS- It is an IT security which helps in monitoring
the outgoing traffic in network and establishes many blockages of action so that data is
that supports in maintenance of the confidentiality and makes the information available that is
stored. It draws the secure network which helps in protecting information from the hackers
(Semin and et. al., 2017).
Data privacy measures are those methods that keep the database files and information
protected. The measures of data privacy are aimed to help in application and control of the
technological advancement and also supports in the allocation of resources in the proper manner.
It is an essential aspect of business as it supports in maintaining integrity and confidentiality of
the data by providing protection to them and securing it from the unauthorized access. It helps in
creating no impact on the business functions. Arden University makes use of the data privacy
measures so that it can preserve the security of data by using various protocols that are essential
so that the information is secured from the ambit of cyber-crimes other types of malicious users
that may harm data (Li and et. al., 2017).
Tools and techniques of the IT security and data privacy measures
There has been rise in the technological up-gradation and advancement that has not only
supported businesses in maintaining data properly but has also given rise to the offences which
are called as cybercrimes. In order to prevent these crimes, there are many tools and techniques
which can be used by corporations for securing an protecting the information from unauthorized
access. These are illustrated below-
DNS protection- Domain name is a type of service which is found in the computers that
comprises of an IP address which helps and supports in the browsing so that all sources
are looted from internet by stating the IP address. It is unique to every computer network.
The DNS protection helps in maintenance of the reliability of data so that it is applied by
the cloud services. It gives an approach with the help of which the security interest can be
maintained in business and protection shall be given to data from the threats. Arden
University uses this tool so that it can keep the data secure and prevent the commission of
the cyber -crime in the educational institutional by blocking the malicious users.
Firewalls and intrusion protection IPS- It is an IT security which helps in monitoring
the outgoing traffic in network and establishes many blockages of action so that data is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

given a protection from the unwanted users. It is aimed to monitor the source of the
network so that the unauthorized access can be identified immediately. For instance,
Arden University uses this tool in order to take the strategic approach in keeping the data
safe from any outside threat. It manages the outgoing traffic by maintaining the safety
procedures in order to keep business data out of the reach of hackers (Jiang Huo and
Song, 2018).
GDPR provisions
The general data protection regulation is that legal framework which is aimed to keep th
processing of the personal data safe and secure. It gives a roadmap to the users as to how
personal information must be processed of the people who are the resident of the European
Union. The provisions of GDPR are narrated below-
Consent- Any business which is engaged in the processing of the personal data and
information is obliged to obtain the valid consent from the person whose information is to
be processed. The consent which is obtained must be specific, free, informed,
unambiguous and taken in the plain language.
Data protection officer- It is requirement in the regulation to make a decision regarding
the appointment of the DPO in the business. It is a public authority that is engaged in the
large scale business so that the personal information of people can be maintained in the
systematic manner and there is proper monitoring of the same. It is a voluntary
appointment of DPO in the company so that information can be monitored in an effective
manner.
Reducing time period for the individual rights- If any person makes a request regarding
accessing the personal information of itself. The business is obliged to provide access to
the person without any undue delay. The statute provides the maximum time period of 1
month from the date of the request.
Extraterritorial effect- The GDPR provisions are applied when there is personal data
processing by any business of European Union irrespective of the fact that whether the
processing is taking place in EU or not. It applies also to businesses which do not belong
to EU but the processing is taking place of EU resident.
network so that the unauthorized access can be identified immediately. For instance,
Arden University uses this tool in order to take the strategic approach in keeping the data
safe from any outside threat. It manages the outgoing traffic by maintaining the safety
procedures in order to keep business data out of the reach of hackers (Jiang Huo and
Song, 2018).
GDPR provisions
The general data protection regulation is that legal framework which is aimed to keep th
processing of the personal data safe and secure. It gives a roadmap to the users as to how
personal information must be processed of the people who are the resident of the European
Union. The provisions of GDPR are narrated below-
Consent- Any business which is engaged in the processing of the personal data and
information is obliged to obtain the valid consent from the person whose information is to
be processed. The consent which is obtained must be specific, free, informed,
unambiguous and taken in the plain language.
Data protection officer- It is requirement in the regulation to make a decision regarding
the appointment of the DPO in the business. It is a public authority that is engaged in the
large scale business so that the personal information of people can be maintained in the
systematic manner and there is proper monitoring of the same. It is a voluntary
appointment of DPO in the company so that information can be monitored in an effective
manner.
Reducing time period for the individual rights- If any person makes a request regarding
accessing the personal information of itself. The business is obliged to provide access to
the person without any undue delay. The statute provides the maximum time period of 1
month from the date of the request.
Extraterritorial effect- The GDPR provisions are applied when there is personal data
processing by any business of European Union irrespective of the fact that whether the
processing is taking place in EU or not. It applies also to businesses which do not belong
to EU but the processing is taking place of EU resident.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Enhancing right of the people-This regulation states many rights to people in respect of
processing of the personal information or data which involves right to portability, right to
access of personal information, right to cause objection on processing of data, right to get
the rectification done of any inaccuracy in data, right to restriction of further processing
and right not get automatic processing (Li, Zhao and Blum, 2018).
Hence, it can be said that the above provided provisions helps in maintaining the personal
data and information and gives special protection. Arden University makes sure that it complies
with each of the provisions of GDPR so that they can offer right to access to each student,
members and staff.
QUESTION 3
What is cellular network, its principles components and how does it works.
It is also known as radio network which is designed with the purpose to help in
distributing the overland ways and methods. The businesses deploy this technology in order to
serve in the fixed locations. It consists of the type of the technology that helps in hierarchical
structure by base transceiver station (BTS) and covers the mobile switching centers. The main
aim of cellular network is to build direct communication channel by using the mobile phones and
other mediums such a chronicle mediums. It consists of the location which is registered by the
use of which the public switch telephone network is maintained. The cellular network maintains
the track of all important and relevant information regarding their location. The devices of
cellular network is maintained by the channels and categorized area that impart the linkage and
control channel through which the wireless communication can be established by way of using
the mobile system in geographical locations. It offers the framework that helps in emitting
frequencies which supports the optimization of limited area. By using the wireless network, the
cellular network makes the personal communication and covets every industry of the economy.
There is the shorter range of transmitter which helps in maintaining the cellular digital pocket
data which provides IT security with the proper mechanism which is made by wireless
frequencies and connection (Cui and et. al., 2017).
Principle components
processing of the personal information or data which involves right to portability, right to
access of personal information, right to cause objection on processing of data, right to get
the rectification done of any inaccuracy in data, right to restriction of further processing
and right not get automatic processing (Li, Zhao and Blum, 2018).
Hence, it can be said that the above provided provisions helps in maintaining the personal
data and information and gives special protection. Arden University makes sure that it complies
with each of the provisions of GDPR so that they can offer right to access to each student,
members and staff.
QUESTION 3
What is cellular network, its principles components and how does it works.
It is also known as radio network which is designed with the purpose to help in
distributing the overland ways and methods. The businesses deploy this technology in order to
serve in the fixed locations. It consists of the type of the technology that helps in hierarchical
structure by base transceiver station (BTS) and covers the mobile switching centers. The main
aim of cellular network is to build direct communication channel by using the mobile phones and
other mediums such a chronicle mediums. It consists of the location which is registered by the
use of which the public switch telephone network is maintained. The cellular network maintains
the track of all important and relevant information regarding their location. The devices of
cellular network is maintained by the channels and categorized area that impart the linkage and
control channel through which the wireless communication can be established by way of using
the mobile system in geographical locations. It offers the framework that helps in emitting
frequencies which supports the optimization of limited area. By using the wireless network, the
cellular network makes the personal communication and covets every industry of the economy.
There is the shorter range of transmitter which helps in maintaining the cellular digital pocket
data which provides IT security with the proper mechanism which is made by wireless
frequencies and connection (Cui and et. al., 2017).
Principle components

There are four necessary elements on which the cellular network is dependent that
involves MTSO which is known as the mobile telephone switching office, public switched
telephone network (PSTN), mobile subscribers unit and the cell sites with various antennas. All
the networking in cellular network are used by various approached like mobile project, mobile
chatting group and many others which helps in maintenance of the proper and effective business
functioning. Arden University is using many approaches of emails, video conferencing, group
chats and Google documents which helps in providing effective education to the students. It
provides the real spreadsheets and the data in respect of institution and education by way of
saving the project notes which can help in providing protection so that proper communication
mechanism is built among students, staff and members by using the cellular networks. It also
enhances the productivity and the performance of University and helps in taking the competitive
edge over others (Riihijarvi and Mahonen, 2018 ).
Benefits of cellular network to the business.
In order to maintain proper cellular network, it is essential to have enhanced range of
network that helps in transfer of data in the speedy manner in the era of technological up-
gradation which includes using the smartphones. It basically helps in transferring the data in the
advanced manner as it is more focused towards the quality maintenance. It is also used for other
purposes other than making the calls. The transfer of data is made by using the stylish range of
phones such as smartphone as it comprises of the improved handset and network. It is focused on
maintenance of effective communication so that there is easy collaboration by the businesses in
respect of technical ideas and inventions. There are many other merits of the cellular networks
which are discussed thereunder-
Enhanced communication- The cellular network has a purpose of building the effective
and clear communication for the business so that they can share relevant information with
the customers and the staff and employees in proper manner. It also helps in maintaining
the scale, value and culture of the company. It involves less cost to maintain and use the
cellular network and also saves time of the people. the businesses deploy this due to its
low cost model so that a proper channel of communication is built.
Response enhancement- the mobile phones are such technology which helps in
improving the employee response which can help in easy working. It helps in making
involves MTSO which is known as the mobile telephone switching office, public switched
telephone network (PSTN), mobile subscribers unit and the cell sites with various antennas. All
the networking in cellular network are used by various approached like mobile project, mobile
chatting group and many others which helps in maintenance of the proper and effective business
functioning. Arden University is using many approaches of emails, video conferencing, group
chats and Google documents which helps in providing effective education to the students. It
provides the real spreadsheets and the data in respect of institution and education by way of
saving the project notes which can help in providing protection so that proper communication
mechanism is built among students, staff and members by using the cellular networks. It also
enhances the productivity and the performance of University and helps in taking the competitive
edge over others (Riihijarvi and Mahonen, 2018 ).
Benefits of cellular network to the business.
In order to maintain proper cellular network, it is essential to have enhanced range of
network that helps in transfer of data in the speedy manner in the era of technological up-
gradation which includes using the smartphones. It basically helps in transferring the data in the
advanced manner as it is more focused towards the quality maintenance. It is also used for other
purposes other than making the calls. The transfer of data is made by using the stylish range of
phones such as smartphone as it comprises of the improved handset and network. It is focused on
maintenance of effective communication so that there is easy collaboration by the businesses in
respect of technical ideas and inventions. There are many other merits of the cellular networks
which are discussed thereunder-
Enhanced communication- The cellular network has a purpose of building the effective
and clear communication for the business so that they can share relevant information with
the customers and the staff and employees in proper manner. It also helps in maintaining
the scale, value and culture of the company. It involves less cost to maintain and use the
cellular network and also saves time of the people. the businesses deploy this due to its
low cost model so that a proper channel of communication is built.
Response enhancement- the mobile phones are such technology which helps in
improving the employee response which can help in easy working. It helps in making
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
effective interaction and communication by many search techniques and tools that can
help in proper business activities. They use tools like laptops, mart phones and chat
platform which are main contributors in the response enhancement.
Collaboration increased with staff- The network of communication contributes in
maintenance of the proper collaboration with the staff and employees so that they can
perform with their best ability, cellular networks helps in increasing collaboration among
staff members.
Increased productivity- The technology relating to mobile phones has contributed to
improving the worker’s performance. Their enhanced productivity contributes in taking
competitive advantage so that positive approach can be taken for working due to proper
communication channel by way of cellular network.
Less cost and time saving technology- The most cost efficient technological up-gradation
is the cellular network that is used by the businesses. It helps the business in expanding
and growth as communication plats an important role in this. It saves time of the
employees as making calls and transferring f data has become easy nowadays (Dai, J.,
and et. al., 2017).
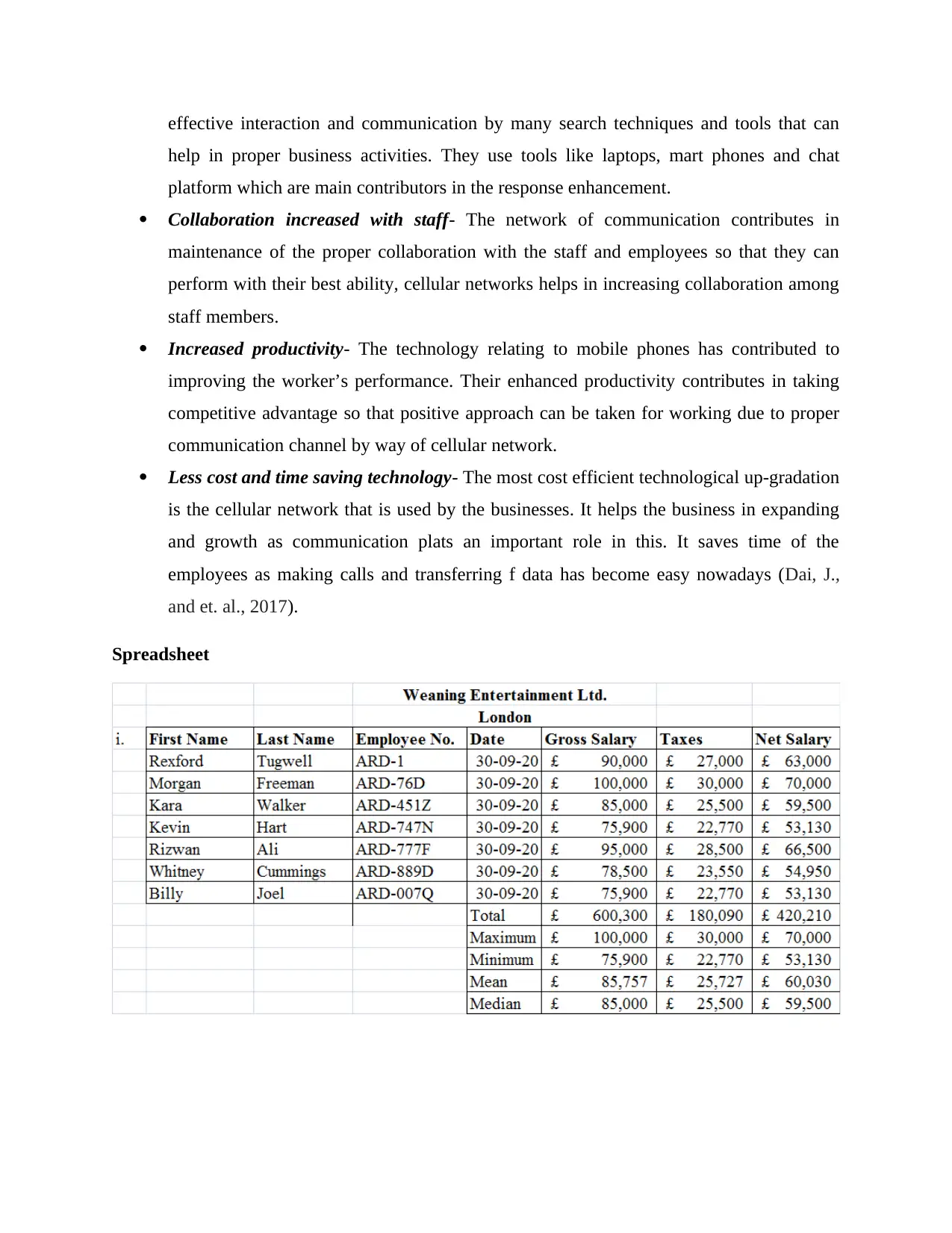
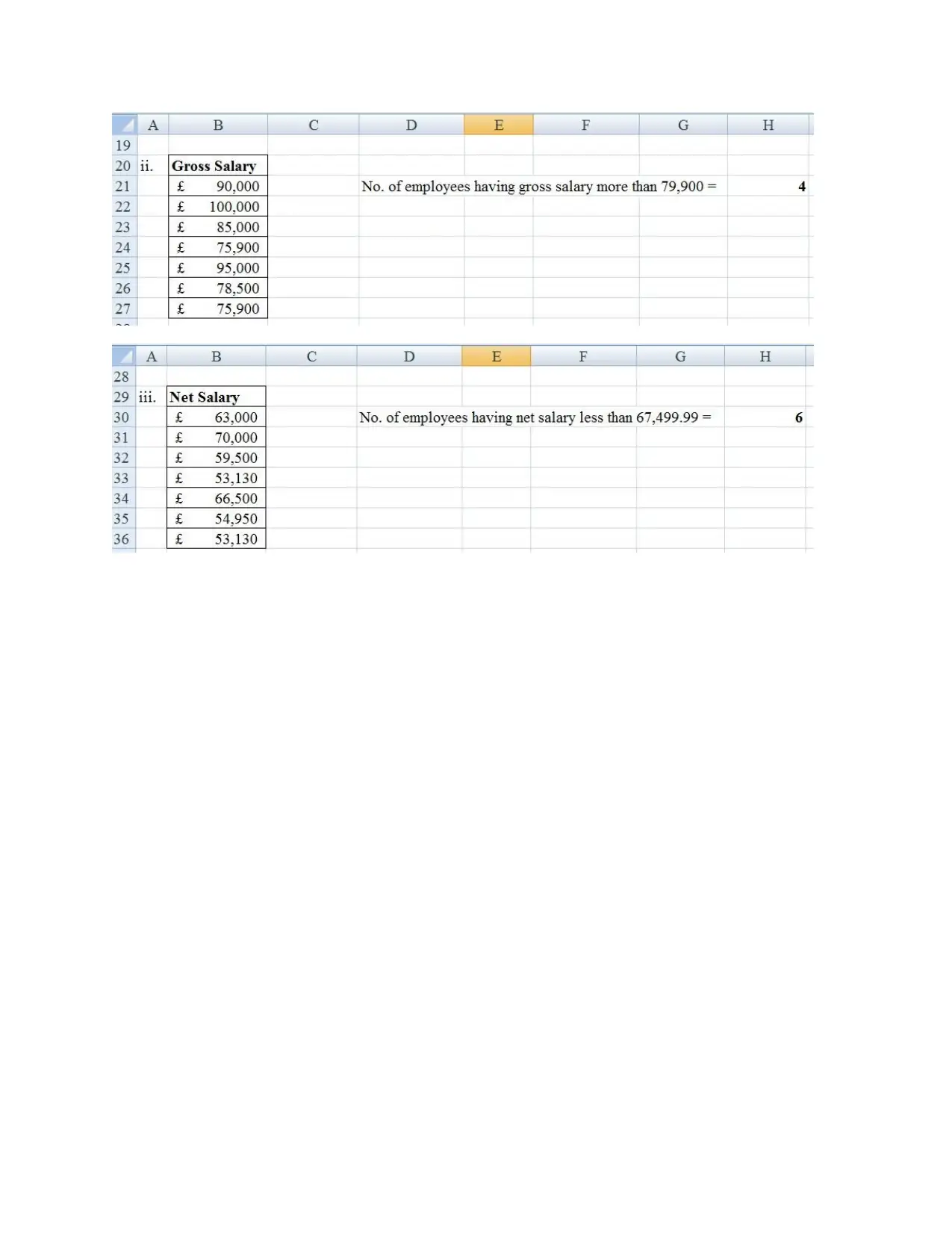
Spreadsheet
help in proper business activities. They use tools like laptops, mart phones and chat
platform which are main contributors in the response enhancement.
Collaboration increased with staff- The network of communication contributes in
maintenance of the proper collaboration with the staff and employees so that they can
perform with their best ability, cellular networks helps in increasing collaboration among
staff members.
Increased productivity- The technology relating to mobile phones has contributed to
improving the worker’s performance. Their enhanced productivity contributes in taking
competitive advantage so that positive approach can be taken for working due to proper
communication channel by way of cellular network.
Less cost and time saving technology- The most cost efficient technological up-gradation
is the cellular network that is used by the businesses. It helps the business in expanding
and growth as communication plats an important role in this. It saves time of the
employees as making calls and transferring f data has become easy nowadays (Dai, J.,
and et. al., 2017).
Spreadsheet
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CONCLUSION
It is summarized from the above report that technology has shaped the business into new
direction and helped them in their growth and expansion. The businesses make use of big data in
order to collect and store the information and protect them from unauthorized access. Its main
role is to maintain the relevant information and keep it safe from any malicious threats and users.
With the increased technology, there is rise in the offences such as cyber-crimes that can be
prevented by IT security and other data privacy measures so that there is no unauthorized access
to the information. The cellular network has made the communication easy which is also
considered as speedy process and saves time of people. it is a cost effective model.
It is summarized from the above report that technology has shaped the business into new
direction and helped them in their growth and expansion. The businesses make use of big data in
order to collect and store the information and protect them from unauthorized access. Its main
role is to maintain the relevant information and keep it safe from any malicious threats and users.
With the increased technology, there is rise in the offences such as cyber-crimes that can be
prevented by IT security and other data privacy measures so that there is no unauthorized access
to the information. The cellular network has made the communication easy which is also
considered as speedy process and saves time of people. it is a cost effective model.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





