Technology in Organizations Report: Big Data, Security, and Telecom
VerifiedAdded on 2022/12/05
|13
|3672
|312
Report
AI Summary
This report delves into the crucial role of technology within organizations, focusing on its impact on Arden University. It begins with a case study evaluating Big Data, its characteristics (Volume, Velocity, Variety, Value, Veracity, Variability), and its application in the administration and examination departments. The report then explores the benefits of adopting Big Data, such as increased customer retention and innovative products. Furthermore, it defines IT security and data privacy measures, emphasizing tools like firewalls, intrusion protection, and DNS protection, along with key provisions of GDPR. The report also covers telecommunications, defining cellular networks, their components, and their benefits to businesses. Finally, it includes a brief section on spreadsheets, providing a comprehensive overview of technology's multifaceted influence on organizational operations and data management.

TECHNOLOGY IN
ORGANISATIONS
ORGANISATIONS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
TASK 1 – CASE STUDY...............................................................................................................3
Evaluation of BIG Data and its role in Arden university with examples of two departments....3
State the benefits of organizations after adopting Big Data........................................................5
TASK 2 – SECURITY AND PRIVACY........................................................................................5
Define IT security and data privacy measures that must be implemented by business and key
provisions of GDPR.....................................................................................................................5
TASK 3 – TELECOMMUNICATON AND SPERADSHEETS....................................................8
Define cellular network and its principle components................................................................8
Define the benefits of cellular networks to business...................................................................9
Spreadsheet................................................................................................................................10
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11
Books and journals....................................................................................................................11
INTRODUCTION...........................................................................................................................3
TASK 1 – CASE STUDY...............................................................................................................3
Evaluation of BIG Data and its role in Arden university with examples of two departments....3
State the benefits of organizations after adopting Big Data........................................................5
TASK 2 – SECURITY AND PRIVACY........................................................................................5
Define IT security and data privacy measures that must be implemented by business and key
provisions of GDPR.....................................................................................................................5
TASK 3 – TELECOMMUNICATON AND SPERADSHEETS....................................................8
Define cellular network and its principle components................................................................8
Define the benefits of cellular networks to business...................................................................9
Spreadsheet................................................................................................................................10
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11
Books and journals....................................................................................................................11

INTRODUCTION
Technology plays a crucial role in the functioning of the business. Information system is
a system of interacting which helps in setting rules. Information system can also be known as set
of components for collecting, storing and processing data for providing information and digital
products. Technology in organisation is a man mad invention which is rapidly developing and
due to technological advancements, the companies can create new products and services though
which they can meet maximum customer satisfaction (Bjola and Zaiotti eds, 2020). Technology
plays a crucial role in theorganisation as it helps the business in protecting their financial data
and make confidential decisions through which the company can gaincompetitive advantage.This
project report aims to define the roles and responsibilities of technologies in organisation and
Arden University through which the benefits of such technologies can be identified. The report
will depict all information regarding Big data and data privacy measures which can betaken. The
reportalso involves information regarding cellular data, its components and its benefits to
thebusiness.
TASK 1–CASE STUDY
Evaluation of BIG Data and its role in Arden university with examples of two departments
BIG Data
Big data is a group of data which is high in number and keeps growing exponentially
with time period. This data is large in size and is complex to manage for which traditional data
management tools can be used to process such data effectively and efficiently. There are three
types of big data, such as structured, unstructured and semi-structured. With the help of big data,
a business can get better insight which are helpful in forming effective decisions and can create
new businessopportunitieswhich can be analyzed with the help of such data. In other words, it is
related to collecting and storing large amount of data (Callan, Johnston and Poulsen, 2015). In
context of Arden University, it can be seen that big data plays a crucial role through which they
can keep a track of all necessary information and maintainingthe collected data
withconfidentiality and security. This helps the Arden University to monitor and safeguard all
necessaryinformation regarding all employee and students who are involved withinthe
university.
Technology plays a crucial role in the functioning of the business. Information system is
a system of interacting which helps in setting rules. Information system can also be known as set
of components for collecting, storing and processing data for providing information and digital
products. Technology in organisation is a man mad invention which is rapidly developing and
due to technological advancements, the companies can create new products and services though
which they can meet maximum customer satisfaction (Bjola and Zaiotti eds, 2020). Technology
plays a crucial role in theorganisation as it helps the business in protecting their financial data
and make confidential decisions through which the company can gaincompetitive advantage.This
project report aims to define the roles and responsibilities of technologies in organisation and
Arden University through which the benefits of such technologies can be identified. The report
will depict all information regarding Big data and data privacy measures which can betaken. The
reportalso involves information regarding cellular data, its components and its benefits to
thebusiness.
TASK 1–CASE STUDY
Evaluation of BIG Data and its role in Arden university with examples of two departments
BIG Data
Big data is a group of data which is high in number and keeps growing exponentially
with time period. This data is large in size and is complex to manage for which traditional data
management tools can be used to process such data effectively and efficiently. There are three
types of big data, such as structured, unstructured and semi-structured. With the help of big data,
a business can get better insight which are helpful in forming effective decisions and can create
new businessopportunitieswhich can be analyzed with the help of such data. In other words, it is
related to collecting and storing large amount of data (Callan, Johnston and Poulsen, 2015). In
context of Arden University, it can be seen that big data plays a crucial role through which they
can keep a track of all necessary information and maintainingthe collected data
withconfidentiality and security. This helps the Arden University to monitor and safeguard all
necessaryinformation regarding all employee and students who are involved withinthe
university.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Six V’s of big data
Big data can be classified on the basis of their characteristics, which involves volume,
velocity, variety and variability. The characteristicsof big data can also be classified as Six V’s
of big data and it involves:
Value- It is clinically relevant data and ensures longitudinal studies. This factor of big data states
that the data which have been gathered is relevant and accurate (Charles and Stancova, 2016).
Volume- This V of big data involves continuous monitoring vital signs and are high throughput
technologies.
Velocity- This v of big data depicts the high seed processing from fast clinical decision supports
and it also increases the data generation rate by the health infrastructure.
Variety- This depicts the heterogeneous and unstructured data sources and depicts the
differenced in frequencies and taxonomies.
Veracity-This factor of big data depict e data quality is unreliable and the data is collected and is
coming from uncontrolled environments.
Variability-This v of big data depicts the seasonal health effects and disease evolution and
several nondeterministic modes of illness and health. The data big sores such types of
information through which a proper information can be maintained.
Role of big data
The role of big data is increasing day by day, such data is used in different sectors which
involves education industry, insurance industry, banking sector and government industry. The
role of big data in Arden university plays a crucial role and it helps them in saving huge files and
keeping a track of all the data which is important (Coccia, 2016). The role of big data in 2
departments of Arden University are explained below:
Administration department–The role of big data in relation to administrationdepartment of
Arden University is that it helps in maintaining all records ofstudents who have enrolled in the
university and maintain all their records through which a proper information of all individuals
can be maintained.
Big data can be classified on the basis of their characteristics, which involves volume,
velocity, variety and variability. The characteristicsof big data can also be classified as Six V’s
of big data and it involves:
Value- It is clinically relevant data and ensures longitudinal studies. This factor of big data states
that the data which have been gathered is relevant and accurate (Charles and Stancova, 2016).
Volume- This V of big data involves continuous monitoring vital signs and are high throughput
technologies.
Velocity- This v of big data depicts the high seed processing from fast clinical decision supports
and it also increases the data generation rate by the health infrastructure.
Variety- This depicts the heterogeneous and unstructured data sources and depicts the
differenced in frequencies and taxonomies.
Veracity-This factor of big data depict e data quality is unreliable and the data is collected and is
coming from uncontrolled environments.
Variability-This v of big data depicts the seasonal health effects and disease evolution and
several nondeterministic modes of illness and health. The data big sores such types of
information through which a proper information can be maintained.
Role of big data
The role of big data is increasing day by day, such data is used in different sectors which
involves education industry, insurance industry, banking sector and government industry. The
role of big data in Arden university plays a crucial role and it helps them in saving huge files and
keeping a track of all the data which is important (Coccia, 2016). The role of big data in 2
departments of Arden University are explained below:
Administration department–The role of big data in relation to administrationdepartment of
Arden University is that it helps in maintaining all records ofstudents who have enrolled in the
university and maintain all their records through which a proper information of all individuals
can be maintained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Examinationdepartment- The role of big data in relation to examination department of Arden
University is that it helps in keeping a track of all the academic performance of students through
which all students and their scores can be traced and it also helps in improving the performance
of the students.
State the benefits of organizations after adopting Big Data
Some of the benefits of which have been faced by organisation after adopting big data are
explained below:
Increased customer retention- With the help of big data, organisation can meet the
demands of their customers easily by knowing their choice and preference of their
customers through which thy can meet the demands of their customers and meet utmost
customer satisfaction (Durodolu, 2016).
Identification of potential risk- With the help of big data, the risk factors can be easily
identified through which risk management solutions can be developed which will help in
minimizing the effects of such potential risk on the organisation.
Innovative products- Big data helps the organisation in upgrading their existing
products and innovate them into ways through which they can attract more customers and
retain maximum numbersof customers through which they can maintain their brand
image in the industry.
TASK 2 – SECURITY AND PRIVACY
Define IT security and data privacy measures that must be implemented by business and key
provisions of GDPR.
IT security and Data privacy measures
IT security- IT security is a circle of cybersecurity strategies which helps in protecting
uses from unauthorized access to organisational assets which involves computers, networks and
data. This security helps in maintaining integrity and confidentiality of information of the
organisation by blocking access to hackers (Finn and Wright, 2016). In other words, information
security is related to keeping the data safe from any unauthorized access which can also destruct
the functions and managerial activities of the business by collecting their personal data.
University is that it helps in keeping a track of all the academic performance of students through
which all students and their scores can be traced and it also helps in improving the performance
of the students.
State the benefits of organizations after adopting Big Data
Some of the benefits of which have been faced by organisation after adopting big data are
explained below:
Increased customer retention- With the help of big data, organisation can meet the
demands of their customers easily by knowing their choice and preference of their
customers through which thy can meet the demands of their customers and meet utmost
customer satisfaction (Durodolu, 2016).
Identification of potential risk- With the help of big data, the risk factors can be easily
identified through which risk management solutions can be developed which will help in
minimizing the effects of such potential risk on the organisation.
Innovative products- Big data helps the organisation in upgrading their existing
products and innovate them into ways through which they can attract more customers and
retain maximum numbersof customers through which they can maintain their brand
image in the industry.
TASK 2 – SECURITY AND PRIVACY
Define IT security and data privacy measures that must be implemented by business and key
provisions of GDPR.
IT security and Data privacy measures
IT security- IT security is a circle of cybersecurity strategies which helps in protecting
uses from unauthorized access to organisational assets which involves computers, networks and
data. This security helps in maintaining integrity and confidentiality of information of the
organisation by blocking access to hackers (Finn and Wright, 2016). In other words, information
security is related to keeping the data safe from any unauthorized access which can also destruct
the functions and managerial activities of the business by collecting their personal data.

In relation to Tesco Plc, it can be seen that the company focuseson theirIT security
through which they can maintain integrity, availability and confidentiality of the data which is
used by the company. The IT security of Tesco Plc helps in strengthening the network and
protecting the system from unauthorized traffics and malicious contents which canhinder the
confidentiality of the business.
Data privacy measures- Data privacy measures is a method of protecting database, file,
accounts, networks and information by taking several measures and with the help of different
tools which canhelp in controlling, applications andby following different techniques which can
relate to the importance of different data and secure such resources. The main elements of data
privacy measures involve confidentiality, availability and integrity (Garavan and et.al, 2019).
There are several data protection measures which are opted by organisation through which they
can ensure that the data is confidential and is secured from such hackers who can create an
adverse impact on the functioning of the business.
In context of GSK, the company focuses on securing their data by following all protocols
through which they can safeguard all collected datafrom the internet cybercrime and unwanted
malicious users.
Tools and techniques of data privacy and IT security
Due to rapid change in technology and increasing cyber threats, companies take several
measures through which they can prevent such cyber-crimes.There are several tools and
techniques which are used by organisation through which they can secure their information from
unauthorized users, some of the measures of data protection are mentioned below:
Firewalls and Intrusion Protection (IPS)-This technique of data protection and IT
security helps in monitoring all incoming and outgoing network traffics as firewalls
blocks specific actions on a network through which the data can be protected from such
unwanted users (Hassan, Mohd Nasir and Khairudin, 2017).
For example, Beyond Analysis offers strategic and analytical consulting services
and they offered their services to McDonalds through which they can save their data from
cybercrime and secure the data by regularly tracking the ingoing and outgoing networks
through which they can maintain integrity, availability and confidentiality of the data which is
used by the company. The IT security of Tesco Plc helps in strengthening the network and
protecting the system from unauthorized traffics and malicious contents which canhinder the
confidentiality of the business.
Data privacy measures- Data privacy measures is a method of protecting database, file,
accounts, networks and information by taking several measures and with the help of different
tools which canhelp in controlling, applications andby following different techniques which can
relate to the importance of different data and secure such resources. The main elements of data
privacy measures involve confidentiality, availability and integrity (Garavan and et.al, 2019).
There are several data protection measures which are opted by organisation through which they
can ensure that the data is confidential and is secured from such hackers who can create an
adverse impact on the functioning of the business.
In context of GSK, the company focuses on securing their data by following all protocols
through which they can safeguard all collected datafrom the internet cybercrime and unwanted
malicious users.
Tools and techniques of data privacy and IT security
Due to rapid change in technology and increasing cyber threats, companies take several
measures through which they can prevent such cyber-crimes.There are several tools and
techniques which are used by organisation through which they can secure their information from
unauthorized users, some of the measures of data protection are mentioned below:
Firewalls and Intrusion Protection (IPS)-This technique of data protection and IT
security helps in monitoring all incoming and outgoing network traffics as firewalls
blocks specific actions on a network through which the data can be protected from such
unwanted users (Hassan, Mohd Nasir and Khairudin, 2017).
For example, Beyond Analysis offers strategic and analytical consulting services
and they offered their services to McDonalds through which they can save their data from
cybercrime and secure the data by regularly tracking the ingoing and outgoing networks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

traffics of thecompany which will help them in saving and safeguarding the business data
from suchthreats.
DNS protection- Domain Name Service translatesdomain names to IP address which
helps browsers to load internet sources. Each and every internet source have different and
unique IP address. It also ensures reliability of the internet applications and cloud
services. It ensures multilayered approach to security which can form trust and protect
thebusiness data from any form of threats (Heeks, 2017).
For example, Cisco Umbrella offers security against such threats on the internet.
It is one of the simplest form of data protection through which all information and data of
the companycan be secured from any threat which can be caused due to cybercrime.
Cisco Umbrella use internet infrastructure for blocking al malicious destinations before
establishment of any connection.
GDPR and key provisions
It is the acronym of General Data Protection Regulations. It is a legal framework which
define guidelines for gathering and processing of personal information from individualswho
reside in European Union (EU). This act came in act when European Parliament and council
agreed to this law and ensures that the general data must be protected (Lis and Žemgulienė,
2020). There are several key provisions of GDPR, some of the variousprovisions are explained
below:
Data Protection Officer (DPO)- There are several businesseswhich must hire a DPO,
some of the businessinvolves public authorities, large scale business and business which
monitor data for criminal convictions. Various organizations must appoint a DPO on
voluntarybasis who can ensure and monitor all compliance of business and must be able
to take correctivemeasures through which data protection laws and practices are followed
by the organisation and quality customer service is offered.
Consent- This provisionwhich is followed by business ensures that all business rely on
theconsentfor lawful processing of personal data and ensures that people have valid
consent in processing the data.
Enhanced rights for individuals- In accordance to GDPR, individuals must access their
personal data through which they can offer companies have access to their personal data.
from suchthreats.
DNS protection- Domain Name Service translatesdomain names to IP address which
helps browsers to load internet sources. Each and every internet source have different and
unique IP address. It also ensures reliability of the internet applications and cloud
services. It ensures multilayered approach to security which can form trust and protect
thebusiness data from any form of threats (Heeks, 2017).
For example, Cisco Umbrella offers security against such threats on the internet.
It is one of the simplest form of data protection through which all information and data of
the companycan be secured from any threat which can be caused due to cybercrime.
Cisco Umbrella use internet infrastructure for blocking al malicious destinations before
establishment of any connection.
GDPR and key provisions
It is the acronym of General Data Protection Regulations. It is a legal framework which
define guidelines for gathering and processing of personal information from individualswho
reside in European Union (EU). This act came in act when European Parliament and council
agreed to this law and ensures that the general data must be protected (Lis and Žemgulienė,
2020). There are several key provisions of GDPR, some of the variousprovisions are explained
below:
Data Protection Officer (DPO)- There are several businesseswhich must hire a DPO,
some of the businessinvolves public authorities, large scale business and business which
monitor data for criminal convictions. Various organizations must appoint a DPO on
voluntarybasis who can ensure and monitor all compliance of business and must be able
to take correctivemeasures through which data protection laws and practices are followed
by the organisation and quality customer service is offered.
Consent- This provisionwhich is followed by business ensures that all business rely on
theconsentfor lawful processing of personal data and ensures that people have valid
consent in processing the data.
Enhanced rights for individuals- In accordance to GDPR, individuals must access their
personal data through which they can offer companies have access to their personal data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The rights of individual also involves data profitability rights and rights to no profiling
through which t can be ensured that the data of individuals have been protected.
Reduces time period for dealing with individual rights- On the request of customers,
the company must provide required information and the information which is required by
the customer must be offered freely and the organisation cannot refuse to their customers
for the information which have been requested (Mazurkiewicz and Poteralska, 2019).
For example, Marks and Spencer follows all the rules and protocolswhichmust be
followed by the company in ensuring the protection of general data. The company also
emphasis on offering thedesired information on time as the company focuses on the right to
information of the users.
TASK 3 – TELECOMMUNICATON AND SPERADSHEETS
Define cellular network and its principle components
Cellular networks
Cellular network is known as radio network which is distributed over land areas which
are called as cells and each served by at least one fixed location. Cellular network technology
give support to hierarchical structure which is formed by Base Transceiver Station (BTS),
Mobile Switching Centre(MSC), Location Registers in Public Switched Telephone Network
(PTSN). Such networks support cellular devices which helps in making direct communication by
using mobile phones and other electronic gadgets. These networks also monitor and keep track
of information which helps in tracking the location of the device. Cellular devices are equipped
with different channels, these channels are classified under two categories which involves: strong
dedicated control channel and strong paging channel (Nissen and et.al, 2017). Cellular
communication systems are wireless mobile communication system which divides the
geographic area into smaller sections, each with low power wireless transmitter with the aim of
optimizing the use of limited number of frequencies. In other words, cellular network technology
is used for mobile phones and wireless networking and is a personal communication system.
Such networks use lower power shorter range and more transmitters which helps in data
transmissions.Wireless IP also known as Cellular Digital Packet Data (CDPD) helps in securing
data transmission.
through which t can be ensured that the data of individuals have been protected.
Reduces time period for dealing with individual rights- On the request of customers,
the company must provide required information and the information which is required by
the customer must be offered freely and the organisation cannot refuse to their customers
for the information which have been requested (Mazurkiewicz and Poteralska, 2019).
For example, Marks and Spencer follows all the rules and protocolswhichmust be
followed by the company in ensuring the protection of general data. The company also
emphasis on offering thedesired information on time as the company focuses on the right to
information of the users.
TASK 3 – TELECOMMUNICATON AND SPERADSHEETS
Define cellular network and its principle components
Cellular networks
Cellular network is known as radio network which is distributed over land areas which
are called as cells and each served by at least one fixed location. Cellular network technology
give support to hierarchical structure which is formed by Base Transceiver Station (BTS),
Mobile Switching Centre(MSC), Location Registers in Public Switched Telephone Network
(PTSN). Such networks support cellular devices which helps in making direct communication by
using mobile phones and other electronic gadgets. These networks also monitor and keep track
of information which helps in tracking the location of the device. Cellular devices are equipped
with different channels, these channels are classified under two categories which involves: strong
dedicated control channel and strong paging channel (Nissen and et.al, 2017). Cellular
communication systems are wireless mobile communication system which divides the
geographic area into smaller sections, each with low power wireless transmitter with the aim of
optimizing the use of limited number of frequencies. In other words, cellular network technology
is used for mobile phones and wireless networking and is a personal communication system.
Such networks use lower power shorter range and more transmitters which helps in data
transmissions.Wireless IP also known as Cellular Digital Packet Data (CDPD) helps in securing
data transmission.

Principle components
A cellular network is majorly based on four components which are Public Switched
Telephone Network (PSTN) a Mobile Telephone Switching Office (MTSO), cell sites with
antenna systems, Mobile Subscriber Units (MSU).
There are several approaches of how cellular network can be used in business, some of
the approaches involves VoIP phones, Mobile Project and Document Management Suites, voice
assistant, mobile chat groups and others (Nudurupati and et.al, 2016).
For example, the basic G Suite- the personal of organisation can use different approaches
such as email, chat and video to talk with one another and review of collaborative spreadsheets
in preparing group presentation and saving project notes on Google Doc. All such work can be
effectively completed with the help of cellular network, maximum productivity and performance
of the business can be enhanced which will help in gaining competitive advantage.
Define the benefits of cellular networks to business
The use of cellular network is rapidly increasing day by day and such networks has increased
the data transfer speed which is one of the major reason of development and technology and
smartphone devices. There are different technologies which are connected with cellular networks
whichhelps people to connect easily. Some of the advantages of cellular network for business are
explained below:
Better communication- Cellular networks helps in establishment better communication
with customer’s, colleague’s, vendors and other peoples. It is one of the easy way to
share information easily within the organisation. Cellular network helps the organisation
to share the purpose, values, culture, scales and size of the company with all the members
and employees working with the organisation (Raja Sreedharan, Raju and Srivatsa
Srinivas, 2017).
Effective and increased collaboration with Colleagues-Communication network is one
of the major source which helps in telecollaboration as through cellular network,
communication is borderless and helps to connect from anywhere.
Enhanced responsiveness- Cellular network provides access to mobile technology
which helps in improving the rate of employee’s response to the customers and helps in
A cellular network is majorly based on four components which are Public Switched
Telephone Network (PSTN) a Mobile Telephone Switching Office (MTSO), cell sites with
antenna systems, Mobile Subscriber Units (MSU).
There are several approaches of how cellular network can be used in business, some of
the approaches involves VoIP phones, Mobile Project and Document Management Suites, voice
assistant, mobile chat groups and others (Nudurupati and et.al, 2016).
For example, the basic G Suite- the personal of organisation can use different approaches
such as email, chat and video to talk with one another and review of collaborative spreadsheets
in preparing group presentation and saving project notes on Google Doc. All such work can be
effectively completed with the help of cellular network, maximum productivity and performance
of the business can be enhanced which will help in gaining competitive advantage.
Define the benefits of cellular networks to business
The use of cellular network is rapidly increasing day by day and such networks has increased
the data transfer speed which is one of the major reason of development and technology and
smartphone devices. There are different technologies which are connected with cellular networks
whichhelps people to connect easily. Some of the advantages of cellular network for business are
explained below:
Better communication- Cellular networks helps in establishment better communication
with customer’s, colleague’s, vendors and other peoples. It is one of the easy way to
share information easily within the organisation. Cellular network helps the organisation
to share the purpose, values, culture, scales and size of the company with all the members
and employees working with the organisation (Raja Sreedharan, Raju and Srivatsa
Srinivas, 2017).
Effective and increased collaboration with Colleagues-Communication network is one
of the major source which helps in telecollaboration as through cellular network,
communication is borderless and helps to connect from anywhere.
Enhanced responsiveness- Cellular network provides access to mobile technology
which helps in improving the rate of employee’s response to the customers and helps in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
managing work easily. There are different tools which helps employees to interact
through which responsiveness can be increased by search tools which involves instant
chat platforms, laptop, tablets and smartphones (Roth, 2016).
Minimize operation cost and saves time- Cellular network helps in establishing
communication from different locations which minimize the operation cost and save time
in performing the functions. Due to rapidly changing technology one of the major
technological advancement is mobile technology which offers benefits in saving time and
cost.
Increase productivity- Cellular networks and mobile technology helps employees to
perform more with less. It helps in adding values to the activities which will be helpful in
enhancing productivity of the business and gaining competitive advantage. Such
networks help in enhancing employee morale and maintain a positive working scenario in
the organisation (Sagieva and Kotsemir, 2018).
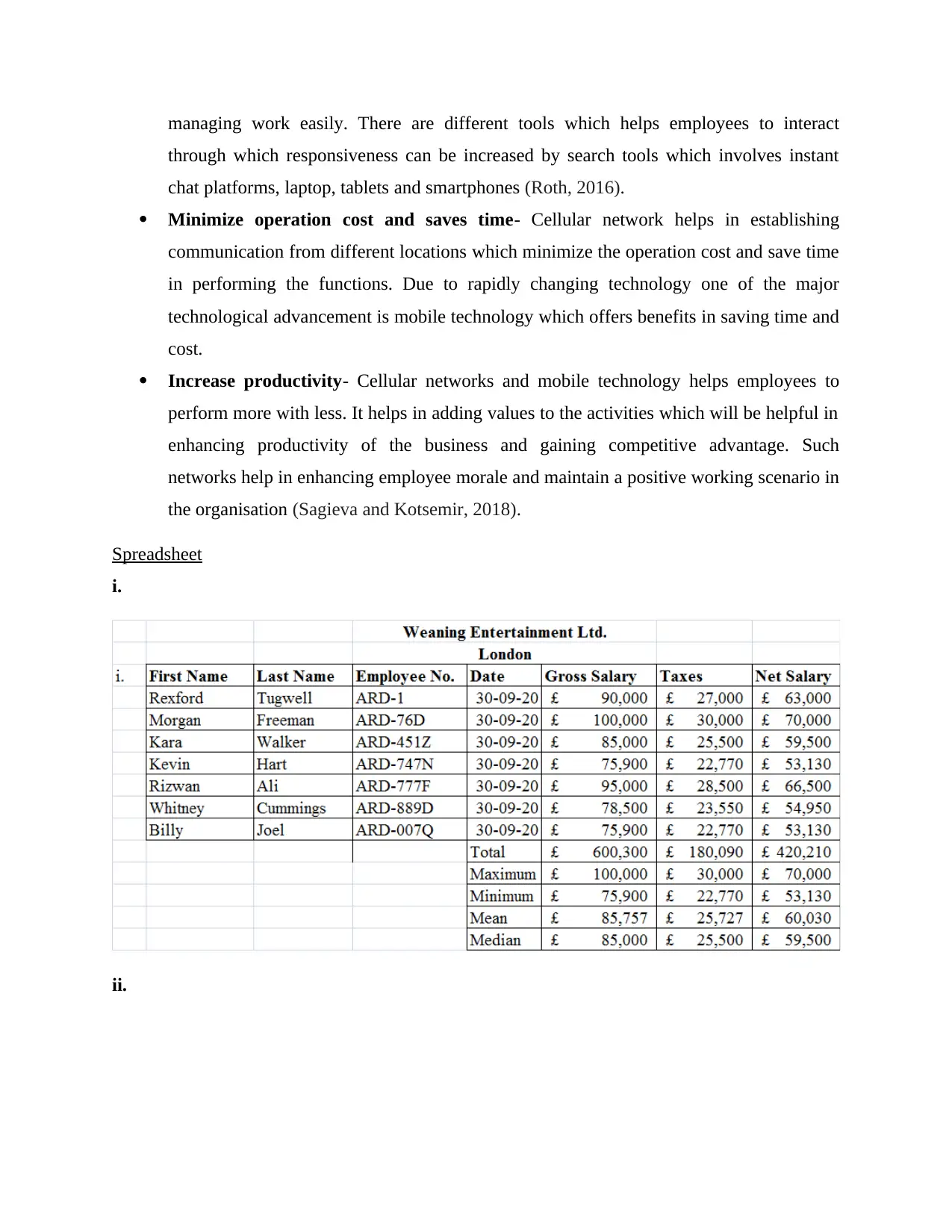
Spreadsheet
i.
ii.
through which responsiveness can be increased by search tools which involves instant
chat platforms, laptop, tablets and smartphones (Roth, 2016).
Minimize operation cost and saves time- Cellular network helps in establishing
communication from different locations which minimize the operation cost and save time
in performing the functions. Due to rapidly changing technology one of the major
technological advancement is mobile technology which offers benefits in saving time and
cost.
Increase productivity- Cellular networks and mobile technology helps employees to
perform more with less. It helps in adding values to the activities which will be helpful in
enhancing productivity of the business and gaining competitive advantage. Such
networks help in enhancing employee morale and maintain a positive working scenario in
the organisation (Sagieva and Kotsemir, 2018).
Spreadsheet
i.
ii.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
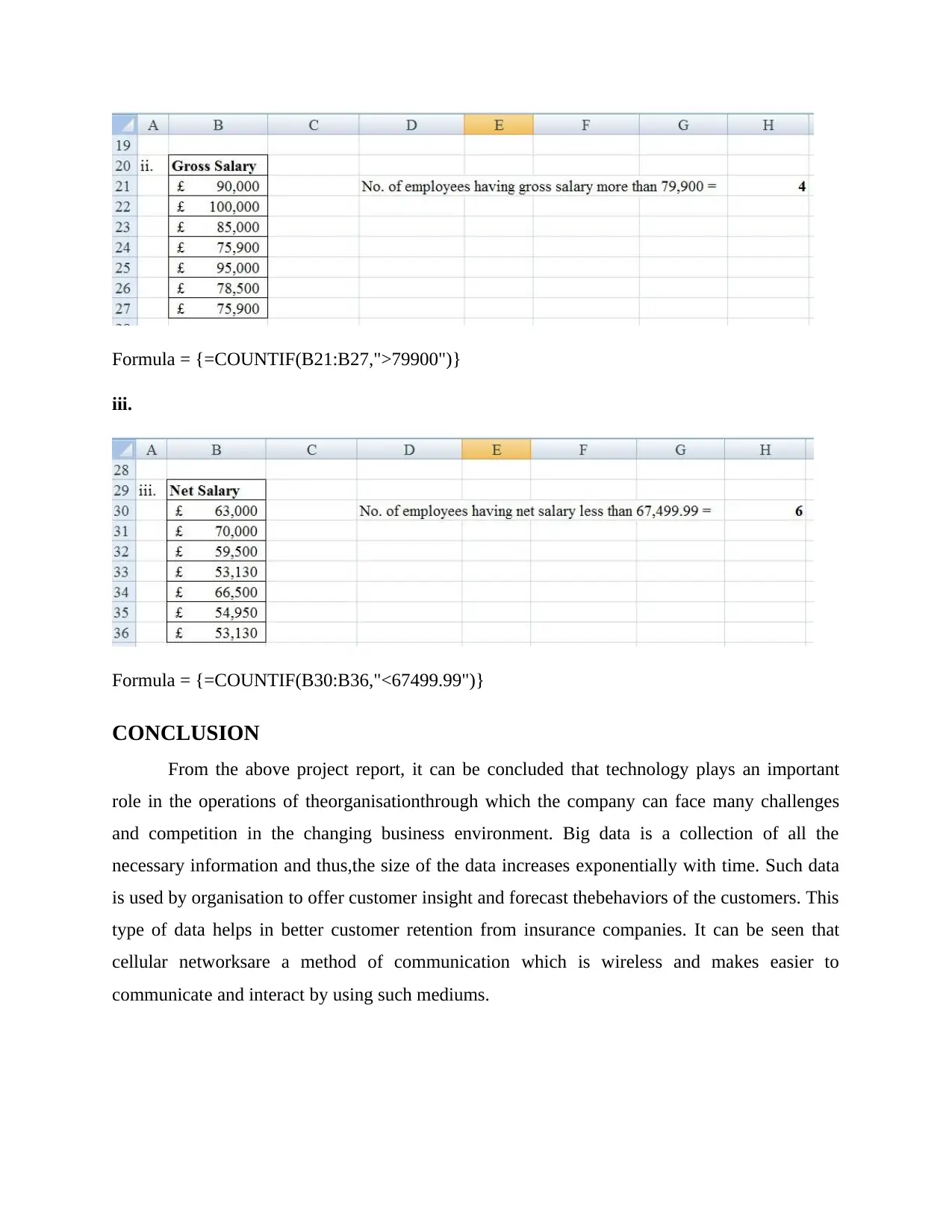
Formula = {=COUNTIF(B21:B27,">79900")}
iii.
Formula = {=COUNTIF(B30:B36,"<67499.99")}
CONCLUSION
From the above project report, it can be concluded that technology plays an important
role in the operations of theorganisationthrough which the company can face many challenges
and competition in the changing business environment. Big data is a collection of all the
necessary information and thus,the size of the data increases exponentially with time. Such data
is used by organisation to offer customer insight and forecast thebehaviors of the customers. This
type of data helps in better customer retention from insurance companies. It can be seen that
cellular networksare a method of communication which is wireless and makes easier to
communicate and interact by using such mediums.
iii.
Formula = {=COUNTIF(B30:B36,"<67499.99")}
CONCLUSION
From the above project report, it can be concluded that technology plays an important
role in the operations of theorganisationthrough which the company can face many challenges
and competition in the changing business environment. Big data is a collection of all the
necessary information and thus,the size of the data increases exponentially with time. Such data
is used by organisation to offer customer insight and forecast thebehaviors of the customers. This
type of data helps in better customer retention from insurance companies. It can be seen that
cellular networksare a method of communication which is wireless and makes easier to
communicate and interact by using such mediums.

REFERENCES
Books and journals
Bjola, C. and Zaiotti, R. eds., 2020. Digital Diplomacy and International Organisations:
Autonomy, Legitimacy and Contestation. Routledge.
Callan, V. J., Johnston, M. A. and Poulsen, A. L., 2015. How organisations are using blended e-
learning to deliver more flexible approaches to trade training. Journal of Vocational
Education & Training. 67(3). pp.294-309.
Charles, D. and Stancova, K. C., 2016. Entrepreneurial discovery process and research and
technology organisations. Governing Smart Specialisation. p.80.
Coccia, M., 2016. Radical innovations as drivers of breakthroughs: characteristics and properties
of the management of technology leading to superior organisational performance in the
discovery process of R&D labs. Technology Analysis & Strategic Management. 28(4).
pp.381-395.
Durodolu, O. O., 2016. Technology acceptance model as a predictor of using information
system'to acquire information literacy skills. Library Philosophy and Practice.
Finn, R. L. and Wright, D., 2016. Privacy, data protection and ethics for civil drone practice: A
survey of industry, regulators and civil society organisations. Computer Law & Security
Review. 32(4). pp.577-586.
Garavan, T. N and et.al., 2019. L&D professionals in organisations: much ambition, unfilled
promise. European Journal of Training and Development.
Hassan, H., Mohd Nasir, M. H. and Khairudin, N., 2017. Cloud computing adoption in
organisations: review of empirical literature. In SHS Web of Conferences (Vol. 34). EDP
Sciences..
Heeks, R., 2017. Information and communication technology for development (ICT4D).
Routledge.
Lis, A. and Žemgulienė, J., 2020. Organisational competence vs transferability of knowledge in
cluster organisations and technology parks. Engineering Management in Production and
Services. pp.83-98.
Mazurkiewicz, A. and Poteralska, B., 2019, September. Identifying and Overcoming Technology
Transfer Barriers at R&D Organisations. In ECIE 2019 14th European Conference on
Innovation and Entrepreneurship (2 vols) (p. 637). Academic Conferences and
publishing limited.
Nissen, B and et.al., 2017, June. New value transactions: Understanding and designing for
distributed autonomous organisations. In Proceedings of the 2017 ACM Conference
Companion Publication on Designing Interactive Systems (pp. 352-355).
Nudurupati, S. S and et.al., 2016. Eight challenges of servitisation for the configuration,
measurement and management of organisations. Journal of Service Theory and Practice.
Raja Sreedharan, V., Raju, R. and Srivatsa Srinivas, S., 2017. A review of the quality evolution
in various organisations. Total Quality Management & Business Excellence. 28(3-4).
pp.351-365.
Roth, S., 2016. Growth and function: a viral research program for next
organisations. International Journal of Technology Management. 72(4). pp.296-309.
Sagieva, G. and Kotsemir, M., 2018. Measuring technological level of organisations:
methodological approaches and assessment. foresight.
Books and journals
Bjola, C. and Zaiotti, R. eds., 2020. Digital Diplomacy and International Organisations:
Autonomy, Legitimacy and Contestation. Routledge.
Callan, V. J., Johnston, M. A. and Poulsen, A. L., 2015. How organisations are using blended e-
learning to deliver more flexible approaches to trade training. Journal of Vocational
Education & Training. 67(3). pp.294-309.
Charles, D. and Stancova, K. C., 2016. Entrepreneurial discovery process and research and
technology organisations. Governing Smart Specialisation. p.80.
Coccia, M., 2016. Radical innovations as drivers of breakthroughs: characteristics and properties
of the management of technology leading to superior organisational performance in the
discovery process of R&D labs. Technology Analysis & Strategic Management. 28(4).
pp.381-395.
Durodolu, O. O., 2016. Technology acceptance model as a predictor of using information
system'to acquire information literacy skills. Library Philosophy and Practice.
Finn, R. L. and Wright, D., 2016. Privacy, data protection and ethics for civil drone practice: A
survey of industry, regulators and civil society organisations. Computer Law & Security
Review. 32(4). pp.577-586.
Garavan, T. N and et.al., 2019. L&D professionals in organisations: much ambition, unfilled
promise. European Journal of Training and Development.
Hassan, H., Mohd Nasir, M. H. and Khairudin, N., 2017. Cloud computing adoption in
organisations: review of empirical literature. In SHS Web of Conferences (Vol. 34). EDP
Sciences..
Heeks, R., 2017. Information and communication technology for development (ICT4D).
Routledge.
Lis, A. and Žemgulienė, J., 2020. Organisational competence vs transferability of knowledge in
cluster organisations and technology parks. Engineering Management in Production and
Services. pp.83-98.
Mazurkiewicz, A. and Poteralska, B., 2019, September. Identifying and Overcoming Technology
Transfer Barriers at R&D Organisations. In ECIE 2019 14th European Conference on
Innovation and Entrepreneurship (2 vols) (p. 637). Academic Conferences and
publishing limited.
Nissen, B and et.al., 2017, June. New value transactions: Understanding and designing for
distributed autonomous organisations. In Proceedings of the 2017 ACM Conference
Companion Publication on Designing Interactive Systems (pp. 352-355).
Nudurupati, S. S and et.al., 2016. Eight challenges of servitisation for the configuration,
measurement and management of organisations. Journal of Service Theory and Practice.
Raja Sreedharan, V., Raju, R. and Srivatsa Srinivas, S., 2017. A review of the quality evolution
in various organisations. Total Quality Management & Business Excellence. 28(3-4).
pp.351-365.
Roth, S., 2016. Growth and function: a viral research program for next
organisations. International Journal of Technology Management. 72(4). pp.296-309.
Sagieva, G. and Kotsemir, M., 2018. Measuring technological level of organisations:
methodological approaches and assessment. foresight.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





