Technology in Organisation Report - COM0006NFBNM, Semester 1
VerifiedAdded on 2022/12/13
|13
|3748
|315
Report
AI Summary
This report provides a comprehensive overview of technology's role in organizations, examining the application and impact of big data, IT security measures, and telecommunications. The report begins with a case study focusing on the implementation and benefits of big data within Arden University, including its role in student scholarships, curriculum reassessment, and operational cost savings. The analysis then delves into IT security and data privacy, outlining essential measures such as firewalls and intrusion detection systems, while also explaining the key provisions of GDPR. Finally, the report explores telecommunications, describing cellular networks, their components, and benefits to businesses. The report concludes by summarizing the key findings and emphasizing the importance of technology in organizational success. All the information is provided to help students with their studies and assignments.

Technology in
organisation
organisation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION......................................................................................................................3
Question 1: Case study and questions........................................................................................3
Big Data and its role in Arden University..............................................................................3
Key benefits to Arden University gets after adopting Big Data............................................4
Question 2 – Security and Privacy.............................................................................................5
Explain the IT security and data privacy measures that an organisation must implement
along with provisions of GDPR.............................................................................................5
Question 3 Telecommunication and spreadsheets.....................................................................8
A) Describe a cellular network, its principle components and how it works...................8
B) Explain the benefits of a cellular network to a business.............................................9
CONCLUSION........................................................................................................................10
References................................................................................................................................11
INTRODUCTION......................................................................................................................3
Question 1: Case study and questions........................................................................................3
Big Data and its role in Arden University..............................................................................3
Key benefits to Arden University gets after adopting Big Data............................................4
Question 2 – Security and Privacy.............................................................................................5
Explain the IT security and data privacy measures that an organisation must implement
along with provisions of GDPR.............................................................................................5
Question 3 Telecommunication and spreadsheets.....................................................................8
A) Describe a cellular network, its principle components and how it works...................8
B) Explain the benefits of a cellular network to a business.............................................9
CONCLUSION........................................................................................................................10
References................................................................................................................................11

INTRODUCTION
Technology is vital for an organisation as it help in keeping data, maintain records,
smooth functioning of activities, secure information and so on. Along with this, there are
different technologies adopted by companies for managing data and to execute activities as
well. In the present report, there is discussion about role and advantages of big data. In
addition to this, various information privacy measures and IT security systems used by
organisation in order to protect data is elaborated.
Question 1: Case study and questions
Big Data and its role in Arden University
Data is defined as a set of numbers, characters, or a symbols which can be transmitted
and stored as electrical signals & recorded on optical, magnetic or mechanical media by a
computer. In addition to this, Big Data is basically a vast collection of data which grows
exponentially with the passage of time period. It is a wide & composite data collection which
no traditional information processing systems can efficiently store or process. Moreover,
Regular data is basically similar to big data and is far bigger to put it another way, it is a
range of structured, unstructured data and semi structured from companies which can be
mined for knowledge as well as used in advanced analytics projects like machine learning &
predictive modelling (Choi and et. al., 2018).
Importance of Big Data
Regulates effective work of an organization: Big data enables companies to become
more customer-centric. Historical and real-time data can be used to measure consumer
preferences, helping businesses to update and refine their marketing campaigns and become
more attentive to customer desires and needs (Del Vecchio and et. al., 2018). In regards to
chosen institute, managers takes use of big data for regulating operational affairs of the firm.
This helps in regulating effective work being produced in the organisation and also
contributes its valuable contribution towards better productivity of the organisation as a
whole.
Other sectors: Big data is used by health researchers and doctors to categories disease
risk factors and identify diseases and disorders in particular patients. Furthermore, data
derived from electronic health records (EHRs), social media, the internet, and other sources
Technology is vital for an organisation as it help in keeping data, maintain records,
smooth functioning of activities, secure information and so on. Along with this, there are
different technologies adopted by companies for managing data and to execute activities as
well. In the present report, there is discussion about role and advantages of big data. In
addition to this, various information privacy measures and IT security systems used by
organisation in order to protect data is elaborated.
Question 1: Case study and questions
Big Data and its role in Arden University
Data is defined as a set of numbers, characters, or a symbols which can be transmitted
and stored as electrical signals & recorded on optical, magnetic or mechanical media by a
computer. In addition to this, Big Data is basically a vast collection of data which grows
exponentially with the passage of time period. It is a wide & composite data collection which
no traditional information processing systems can efficiently store or process. Moreover,
Regular data is basically similar to big data and is far bigger to put it another way, it is a
range of structured, unstructured data and semi structured from companies which can be
mined for knowledge as well as used in advanced analytics projects like machine learning &
predictive modelling (Choi and et. al., 2018).
Importance of Big Data
Regulates effective work of an organization: Big data enables companies to become
more customer-centric. Historical and real-time data can be used to measure consumer
preferences, helping businesses to update and refine their marketing campaigns and become
more attentive to customer desires and needs (Del Vecchio and et. al., 2018). In regards to
chosen institute, managers takes use of big data for regulating operational affairs of the firm.
This helps in regulating effective work being produced in the organisation and also
contributes its valuable contribution towards better productivity of the organisation as a
whole.
Other sectors: Big data is used by health researchers and doctors to categories disease
risk factors and identify diseases and disorders in particular patients. Furthermore, data
derived from electronic health records (EHRs), social media, the internet, and other sources
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

offers real-time information on infectious disease risks and outbreaks to healthcare facilities
and government agencies (Ju and et. al., 2018).
Role of Big Data in Arden University
Target student scholarship: Arden University will recognise good students by
giving them a test for which they must score a certain amount of points in order to be
considered for a scholarship. Big data may also be used by institutions to evaluate a student's
previous performance, regardless of the school or college he or she attended. These methods
may help businesses recognise students who are more likely to stick around in college or
university. Furthermore, for the institution's scholarship funds, this solution will have the
highest return on investment.
Seeking attention to those students who needs the most: After the data has been
extensively analysed, it can be used to identify students who will need more attention during
daily school tasks, such as homework, as compared to others who will unquestionably
succeed in their academic careers (Lee and Huh, 2019). These practises, however, raise
ethical questions about whether collecting this form of data on students infringes on their
privacy while also enabling students to be supported in a number of ways.
Reassess curriculum: All of the data collected and stored will help an organisation
create a personalised programme for each student. Big data also allows for specialisation
when a university or college has tens of thousands of students. Blended learning, which
combines online and offline learning, is what institutions are looking for while operating in a
specific marketplace.
Organising customized programs for students: For organising customised
programs inside or outside the university, big data can prove to be an effective tool. It have
its crucial role in arranging effective programs in respect with various university programs
which are organised by the institute itself. It shortens the path for management and avoids
duplication of efforts being produced during the course.
Save on operations: Organizations may also use data analytics to reduce energy
usage and save money. Institutions can build performance models using real-time data from
sensors, metres, and actuators. Models can help with energy use monitoring, forecasting,
assuming, and optimization. They can also identify buildings that are underperforming and
determine what is causing the inefficiencies.
and government agencies (Ju and et. al., 2018).
Role of Big Data in Arden University
Target student scholarship: Arden University will recognise good students by
giving them a test for which they must score a certain amount of points in order to be
considered for a scholarship. Big data may also be used by institutions to evaluate a student's
previous performance, regardless of the school or college he or she attended. These methods
may help businesses recognise students who are more likely to stick around in college or
university. Furthermore, for the institution's scholarship funds, this solution will have the
highest return on investment.
Seeking attention to those students who needs the most: After the data has been
extensively analysed, it can be used to identify students who will need more attention during
daily school tasks, such as homework, as compared to others who will unquestionably
succeed in their academic careers (Lee and Huh, 2019). These practises, however, raise
ethical questions about whether collecting this form of data on students infringes on their
privacy while also enabling students to be supported in a number of ways.
Reassess curriculum: All of the data collected and stored will help an organisation
create a personalised programme for each student. Big data also allows for specialisation
when a university or college has tens of thousands of students. Blended learning, which
combines online and offline learning, is what institutions are looking for while operating in a
specific marketplace.
Organising customized programs for students: For organising customised
programs inside or outside the university, big data can prove to be an effective tool. It have
its crucial role in arranging effective programs in respect with various university programs
which are organised by the institute itself. It shortens the path for management and avoids
duplication of efforts being produced during the course.
Save on operations: Organizations may also use data analytics to reduce energy
usage and save money. Institutions can build performance models using real-time data from
sensors, metres, and actuators. Models can help with energy use monitoring, forecasting,
assuming, and optimization. They can also identify buildings that are underperforming and
determine what is causing the inefficiencies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Key benefits to Arden University gets after adopting Big Data
Arden University uses the big information within their databases in order to provide
better customer service, optimise operations, develop customised marketing campaigns
emphasis on particular customer preferences & ultimately improve revenues. It is analysed
that Businesses that use big data have an ability to attain competitive advantage over those
who don't because, if the data is used correctly, they will make smarter and more informed
business decisions. For instance, big data can give entities with valuable consumer
information which can be used in order to enhance marketing campaigns & tactics for raising
conversion rates and customer satisfaction as well.
The following are some of the advantages that a chosen university receives as a result
of using Big Data:
Solutions to tough situations: Using big data analysis, university coordinators are
able to carry out a variety of difficult tasks in the organisation using simple methods(Del
Vecchio and et. al., 2018). Various tough situations for the university when related to any
legal issue or compliment with regulation. In such when university is ordered to show their
operational working records, big data can prove to very useful to the firm.
Accessible: Searching through a wall-to-wall arrangement of file cabinets is
inconvenient and time-consuming. Since big data relies on a technological system to process,
store, and manage information, it's much easier to find what is required at the moment of time
and is much easier to get access when compared to other method of storing a data.
Saves cost of operations: It proves to be a cost-effective method for reducing
educational institute costs. Maintaining big data processing means that all data and
information is recorded using scientific tools, ensuring that it can survive indefinitely.
Traditional data storage methods, such as storing books or copies, on the other hand, are
expensive and time consuming.
Quick method: Big data is described as the rapid transmission of data that can be
transferred and accessed at any time(Ju, Liu and Feng, 2018). It operates on a technical level
in that a person can run a search task in the system and find the file or data they need in 5-6
clicks, which is a time-saving technique.
Arden University uses the big information within their databases in order to provide
better customer service, optimise operations, develop customised marketing campaigns
emphasis on particular customer preferences & ultimately improve revenues. It is analysed
that Businesses that use big data have an ability to attain competitive advantage over those
who don't because, if the data is used correctly, they will make smarter and more informed
business decisions. For instance, big data can give entities with valuable consumer
information which can be used in order to enhance marketing campaigns & tactics for raising
conversion rates and customer satisfaction as well.
The following are some of the advantages that a chosen university receives as a result
of using Big Data:
Solutions to tough situations: Using big data analysis, university coordinators are
able to carry out a variety of difficult tasks in the organisation using simple methods(Del
Vecchio and et. al., 2018). Various tough situations for the university when related to any
legal issue or compliment with regulation. In such when university is ordered to show their
operational working records, big data can prove to very useful to the firm.
Accessible: Searching through a wall-to-wall arrangement of file cabinets is
inconvenient and time-consuming. Since big data relies on a technological system to process,
store, and manage information, it's much easier to find what is required at the moment of time
and is much easier to get access when compared to other method of storing a data.
Saves cost of operations: It proves to be a cost-effective method for reducing
educational institute costs. Maintaining big data processing means that all data and
information is recorded using scientific tools, ensuring that it can survive indefinitely.
Traditional data storage methods, such as storing books or copies, on the other hand, are
expensive and time consuming.
Quick method: Big data is described as the rapid transmission of data that can be
transferred and accessed at any time(Ju, Liu and Feng, 2018). It operates on a technical level
in that a person can run a search task in the system and find the file or data they need in 5-6
clicks, which is a time-saving technique.

Question 2 – Security and Privacy
Explain the IT security and data privacy measures that an organisation must implement along
with provisions of GDPR
Data security is one of the vital aspect in an organization and is one of the major
priority as well. In the present time period, companies faces many issues such as cyber
attacks which is raising rapidly and affect businesses. It is significant for an organization to
make use of IT security and information privacy measures so that they can protect
information. The information privacy and IT security measures that an organization must
execute are as follows:
Firewalls: In order to protect network, firewalls are vital initiative to consider by an
organization as it control the overall Internet traffic coming and leaving the organization. In
addition to this, a firewall is basically a network security device that monitors outgoing and
incoming network traffic any after this it decide whether to allow as well as block particular
traffic based on the set of security rules(Lee and Huh, 2019). There are different types of
firewalls which are proxy firewall, next generation firewall, stateful inspection firewall,
unified threat management firewall and many more. It is analyzed that a firewall performs
like a traffic system and guard entry point for which IP address are important as it is analyzed
a source just like Postal address shows where a person live. Moreover, it is analyzed that
stateful inspection firewall is one of the effective and secure firewall as its decision indulge
after layers three and four that secure in formation more properly.
Intrusion detection system: It is undertaken as a monitoring system that detect
suspicious activity and create alerts when properly detected. Along with this, security
operation center and incident responders can investigate the reason based on alerts and then
take appropriate measures for declining the level of threat. It is analyzed that intrusion
detection system is mainly designed to develop within various environment and is like cyber
security solutions which can either be host based or network based. Moreover, IDS is also a
listen only device which reports and monitors traffic to an administrator but cannot take
effective actions for preventing measures that exploit system(Kreiling and et. al., 2020).
Furthermore, it only required to detect threats and is located out of band on the network that
means it is not the true real communication path between the receiver and sender information.
Explain the IT security and data privacy measures that an organisation must implement along
with provisions of GDPR
Data security is one of the vital aspect in an organization and is one of the major
priority as well. In the present time period, companies faces many issues such as cyber
attacks which is raising rapidly and affect businesses. It is significant for an organization to
make use of IT security and information privacy measures so that they can protect
information. The information privacy and IT security measures that an organization must
execute are as follows:
Firewalls: In order to protect network, firewalls are vital initiative to consider by an
organization as it control the overall Internet traffic coming and leaving the organization. In
addition to this, a firewall is basically a network security device that monitors outgoing and
incoming network traffic any after this it decide whether to allow as well as block particular
traffic based on the set of security rules(Lee and Huh, 2019). There are different types of
firewalls which are proxy firewall, next generation firewall, stateful inspection firewall,
unified threat management firewall and many more. It is analyzed that a firewall performs
like a traffic system and guard entry point for which IP address are important as it is analyzed
a source just like Postal address shows where a person live. Moreover, it is analyzed that
stateful inspection firewall is one of the effective and secure firewall as its decision indulge
after layers three and four that secure in formation more properly.
Intrusion detection system: It is undertaken as a monitoring system that detect
suspicious activity and create alerts when properly detected. Along with this, security
operation center and incident responders can investigate the reason based on alerts and then
take appropriate measures for declining the level of threat. It is analyzed that intrusion
detection system is mainly designed to develop within various environment and is like cyber
security solutions which can either be host based or network based. Moreover, IDS is also a
listen only device which reports and monitors traffic to an administrator but cannot take
effective actions for preventing measures that exploit system(Kreiling and et. al., 2020).
Furthermore, it only required to detect threats and is located out of band on the network that
means it is not the true real communication path between the receiver and sender information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Apart from the above IT security measures, there are various other measures which an
organization can implement such as updating secure mobile phones, educate employees about
data security, and strong password and so on.
Key Provision of GDPR
General data protection regulation act overhauls information protection legal
framework within Europe and comes into effect on 2018. In addition to this, GDPR
regulation is intended to provide individuals control over their information as now companies
are gathering more personal data. The key provisions of GDPR is given below:
Extra Territorial effect: It is stated that general data protection regulation has extra
territorial effect. It mainly applies to the processing of personal information by an EU
business nevertheless of whether or not the process take place. It means that businesses who
adopt servers outside the EU may fail within the scope of this regulation.
Data protection offer: There are various entities that appointed a data protection
officer which are public authorities, companies that engaged in large scale(Sinha and
Sengupta, 2020). Organization of special categories of personal information or data relating
to criminal offenses or convictions. The main role of data protection officer is to advise
companies on its obligation and to monitor compliance with GDPR.
Consent: The need around consent have been strengthened by general data protection
regulation which means that companies intends to rely on consent for the lawful procedure of
personal information. In addition to this, to be a valid lawful basis for processing information,
consent must be freely given, unambiguous, informed and many more. It is analyzed that
individuals also have the right or authority to withdraw consent at any place of time.
Enhance right for people: It is analyzed that under GDPR, people have the right to
access their personal information, a right to have personal information erase in various cases,
a right to object to information processing, a right to modify inaccuracies within personal
information and many more. On the other hand, while ab individual has the right not to be
subject to profiling which does not apply where the processing is authorized by member state
law or by European law.
Data protection impact assessment: It is analyzed that companies must carry out an
assessment of the influence of processing operations on the protection of personal
organization can implement such as updating secure mobile phones, educate employees about
data security, and strong password and so on.
Key Provision of GDPR
General data protection regulation act overhauls information protection legal
framework within Europe and comes into effect on 2018. In addition to this, GDPR
regulation is intended to provide individuals control over their information as now companies
are gathering more personal data. The key provisions of GDPR is given below:
Extra Territorial effect: It is stated that general data protection regulation has extra
territorial effect. It mainly applies to the processing of personal information by an EU
business nevertheless of whether or not the process take place. It means that businesses who
adopt servers outside the EU may fail within the scope of this regulation.
Data protection offer: There are various entities that appointed a data protection
officer which are public authorities, companies that engaged in large scale(Sinha and
Sengupta, 2020). Organization of special categories of personal information or data relating
to criminal offenses or convictions. The main role of data protection officer is to advise
companies on its obligation and to monitor compliance with GDPR.
Consent: The need around consent have been strengthened by general data protection
regulation which means that companies intends to rely on consent for the lawful procedure of
personal information. In addition to this, to be a valid lawful basis for processing information,
consent must be freely given, unambiguous, informed and many more. It is analyzed that
individuals also have the right or authority to withdraw consent at any place of time.
Enhance right for people: It is analyzed that under GDPR, people have the right to
access their personal information, a right to have personal information erase in various cases,
a right to object to information processing, a right to modify inaccuracies within personal
information and many more. On the other hand, while ab individual has the right not to be
subject to profiling which does not apply where the processing is authorized by member state
law or by European law.
Data protection impact assessment: It is analyzed that companies must carry out an
assessment of the influence of processing operations on the protection of personal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information. In addition to this, businesses will be obliged to consult with data protection
impact assessment in advance of processing in order to mitigate the risk.
Data breach notifications: When a personal information breach arise, businesses
must notify the bridge to data protection impact assessment. If the notification is not
developed within 72 hours, a reason for the delay must be furnished(Humble and Kim, 2018).
The processing of personal information are needed to notify the controller without undue
delay after becoming knowledge of a data breach.
Right to compensation for individuals: This provision states that an individual who
suffered risk and damage which because of infringement of general information protection
regulation has the authority to gain compensation from companies. In order to avoid liability,
company will have to prove that it was not responsible for the raising damage. Moreover,
individuals also have the authority to make a court application in order to appeal certain acts
and decisions of data protection assessment.
Apart from this, there are also other key provisions of GDPR that is obliging
businesses to be clearer about how they use personal data, increase penalties, new obligation
for processors, data protection by design and default, ability to appoint a lead supervisory
authority and many more.
Question 3 Telecommunication and spreadsheets
A) Describe a cellular network, its principle components and how it works.
Cellular network is defined as a radio network distributed Over land through cell where
every cell include a particular location known as base station. In addition to this, it is also
known as mobile network which is a communication network and here in the last link is
wireless. It is stated that when all these cells joined together provide radio coverage on a wide
area. It enable transceivers such as mobile phones, tablets, laptops with mobile broadband,
modems, pagers to communicate with each other and fixed transceivers as well as telephones
anywhere in network. Moreover, cellular network gives subscribers an advanced
characteristics over solutions including decline interference, small battery power usage, larger
geographical area, enhance capacity and so on(Rajan and Dhir, 2020). The components of
cellular network along with how they work is mentioned below:
Principle network of cellular network and how it works
impact assessment in advance of processing in order to mitigate the risk.
Data breach notifications: When a personal information breach arise, businesses
must notify the bridge to data protection impact assessment. If the notification is not
developed within 72 hours, a reason for the delay must be furnished(Humble and Kim, 2018).
The processing of personal information are needed to notify the controller without undue
delay after becoming knowledge of a data breach.
Right to compensation for individuals: This provision states that an individual who
suffered risk and damage which because of infringement of general information protection
regulation has the authority to gain compensation from companies. In order to avoid liability,
company will have to prove that it was not responsible for the raising damage. Moreover,
individuals also have the authority to make a court application in order to appeal certain acts
and decisions of data protection assessment.
Apart from this, there are also other key provisions of GDPR that is obliging
businesses to be clearer about how they use personal data, increase penalties, new obligation
for processors, data protection by design and default, ability to appoint a lead supervisory
authority and many more.
Question 3 Telecommunication and spreadsheets
A) Describe a cellular network, its principle components and how it works.
Cellular network is defined as a radio network distributed Over land through cell where
every cell include a particular location known as base station. In addition to this, it is also
known as mobile network which is a communication network and here in the last link is
wireless. It is stated that when all these cells joined together provide radio coverage on a wide
area. It enable transceivers such as mobile phones, tablets, laptops with mobile broadband,
modems, pagers to communicate with each other and fixed transceivers as well as telephones
anywhere in network. Moreover, cellular network gives subscribers an advanced
characteristics over solutions including decline interference, small battery power usage, larger
geographical area, enhance capacity and so on(Rajan and Dhir, 2020). The components of
cellular network along with how they work is mentioned below:
Principle network of cellular network and how it works

Mobile equipment: It is basically a physical phone which is able to operate on
cellular network. Along with this, it is determined that older phones operated in a single
brand and the new phones are quad band capable, dual band on triple band as well.
Furthermore, each phone is differently determined through international mobile equipment
identity. It is analyzed that through, it can be usually found through extracting the battery of
phone as well as by reading the panel properly.
Cell size and capacity: It is stated that cell size shows amount of cells available in
order to cover geographical area & the capacity accessible to users. Along with this, capacity
in cell is limited through available bandwidth & operational requirements. Moreover, it is
determined that network operator has to size cells for handling expected traffic properly.
Base station controller: It handles allocation of power, radio channels and signals
measurement, frequency handover and distribution from one base station to another. In
addition to this, it reduced number of connections to the mobile switching centre that further
allow for higher capacity connection.
Base transceiver station: It is basically an antenna that is installed on the top of
tower. Along with this, base transceiver station is mobile phone access point and is
responsible for carrying out the communication between mobile network and
phone(Galushkin, 2018). Furthermore it is analyzed that it handles encryption, speech
modulation, speech encoding and so on. Base transceiver station is assigned a cell identity
which denotes a particular location area and gives detail of the cell.
Mobile switching center: It is undertaken as last component of cellular network that handles
called routing, call center, basic switching function and many more. In addition to this, it
handles interface controller handoffs and also coordinates with other mobile switching
centers properly. Furthermore it is analyzed that mobile switching center handles different
base station controller which act as an interface among switching centres.
B) Explain the benefits of a cellular network to a business.
There are several advantages gained by business entity while using cellular network and
is given below:
Large area of network: it is stated that cellular Internet work reaches those parts that is
practically impossible for group members. for example, if a company incorporates wireless
cellular network. Along with this, it is determined that older phones operated in a single
brand and the new phones are quad band capable, dual band on triple band as well.
Furthermore, each phone is differently determined through international mobile equipment
identity. It is analyzed that through, it can be usually found through extracting the battery of
phone as well as by reading the panel properly.
Cell size and capacity: It is stated that cell size shows amount of cells available in
order to cover geographical area & the capacity accessible to users. Along with this, capacity
in cell is limited through available bandwidth & operational requirements. Moreover, it is
determined that network operator has to size cells for handling expected traffic properly.
Base station controller: It handles allocation of power, radio channels and signals
measurement, frequency handover and distribution from one base station to another. In
addition to this, it reduced number of connections to the mobile switching centre that further
allow for higher capacity connection.
Base transceiver station: It is basically an antenna that is installed on the top of
tower. Along with this, base transceiver station is mobile phone access point and is
responsible for carrying out the communication between mobile network and
phone(Galushkin, 2018). Furthermore it is analyzed that it handles encryption, speech
modulation, speech encoding and so on. Base transceiver station is assigned a cell identity
which denotes a particular location area and gives detail of the cell.
Mobile switching center: It is undertaken as last component of cellular network that handles
called routing, call center, basic switching function and many more. In addition to this, it
handles interface controller handoffs and also coordinates with other mobile switching
centers properly. Furthermore it is analyzed that mobile switching center handles different
base station controller which act as an interface among switching centres.
B) Explain the benefits of a cellular network to a business.
There are several advantages gained by business entity while using cellular network and
is given below:
Large area of network: it is stated that cellular Internet work reaches those parts that is
practically impossible for group members. for example, if a company incorporates wireless
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
communication in building then it is convenient to get connected with rest of world from
balcony, rooftop and so on.
Raise mobility: it is analyzed that every organization is associated about productivity of
employees continue to exist at office. In addition to this, when an organazation settle for
wireless connection then staff members get real time information. Apart from this, if a
business has traditional network at workplace then it is not ensure to develop chaotic
workspace.
High flexibility: If a company modify network in future, it is convenient and easy to
control via fire connection(Preece, 2020).But if an organization have cable connection at
work space, it can easily undo the entire procedure which occur cost and high time as well.
Decline ownership cost: It is determined that if a company compare wireless network
with conventional buyers then it is easily able to create a demarcation between costs arise.
Along with this, it is analyzed that wireless connection has high longevity as compared to
traditional network Which in turn help in declining ownership cost in an effective manner.
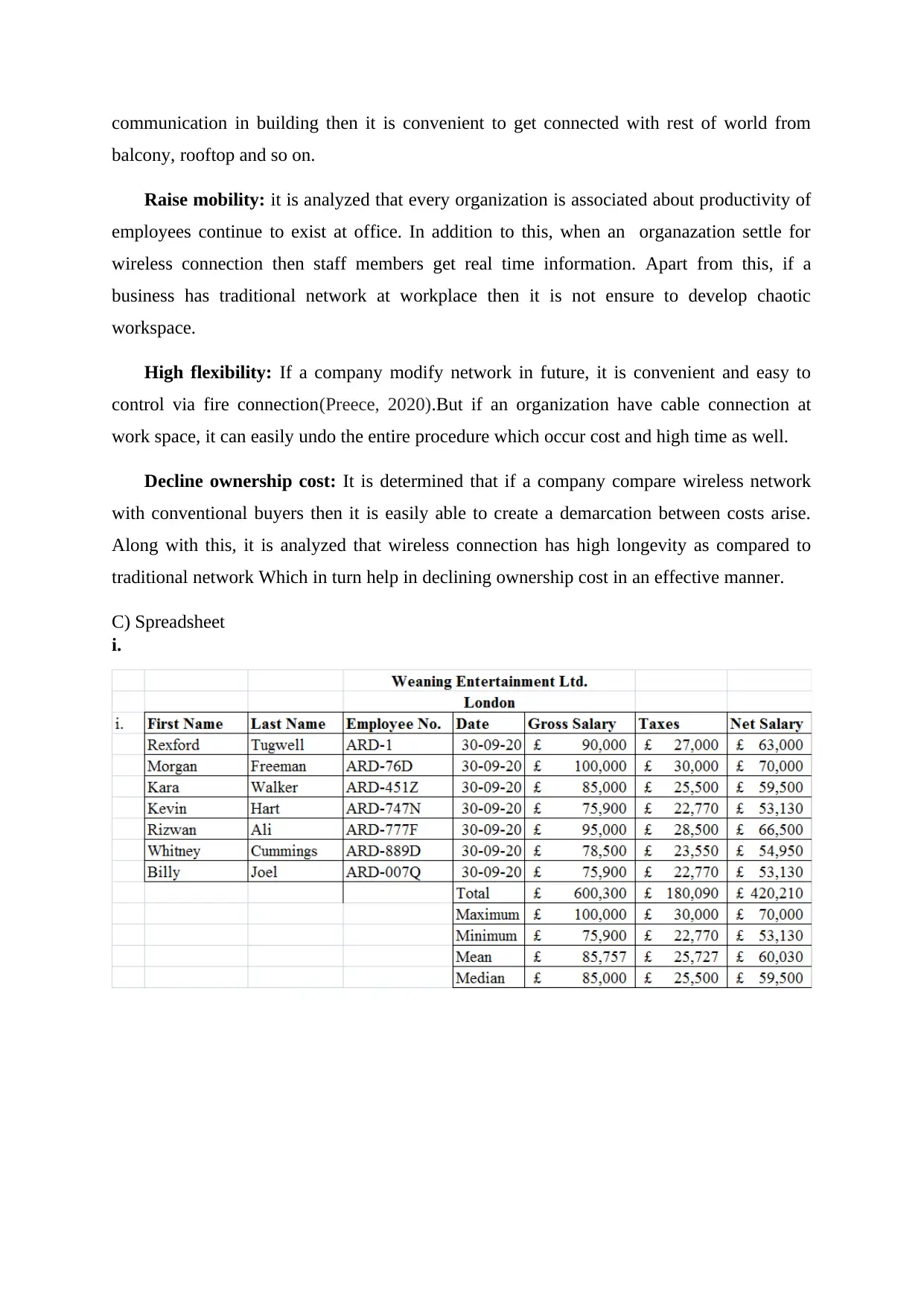
C) Spreadsheet
i.
balcony, rooftop and so on.
Raise mobility: it is analyzed that every organization is associated about productivity of
employees continue to exist at office. In addition to this, when an organazation settle for
wireless connection then staff members get real time information. Apart from this, if a
business has traditional network at workplace then it is not ensure to develop chaotic
workspace.
High flexibility: If a company modify network in future, it is convenient and easy to
control via fire connection(Preece, 2020).But if an organization have cable connection at
work space, it can easily undo the entire procedure which occur cost and high time as well.
Decline ownership cost: It is determined that if a company compare wireless network
with conventional buyers then it is easily able to create a demarcation between costs arise.
Along with this, it is analyzed that wireless connection has high longevity as compared to
traditional network Which in turn help in declining ownership cost in an effective manner.
C) Spreadsheet
i.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
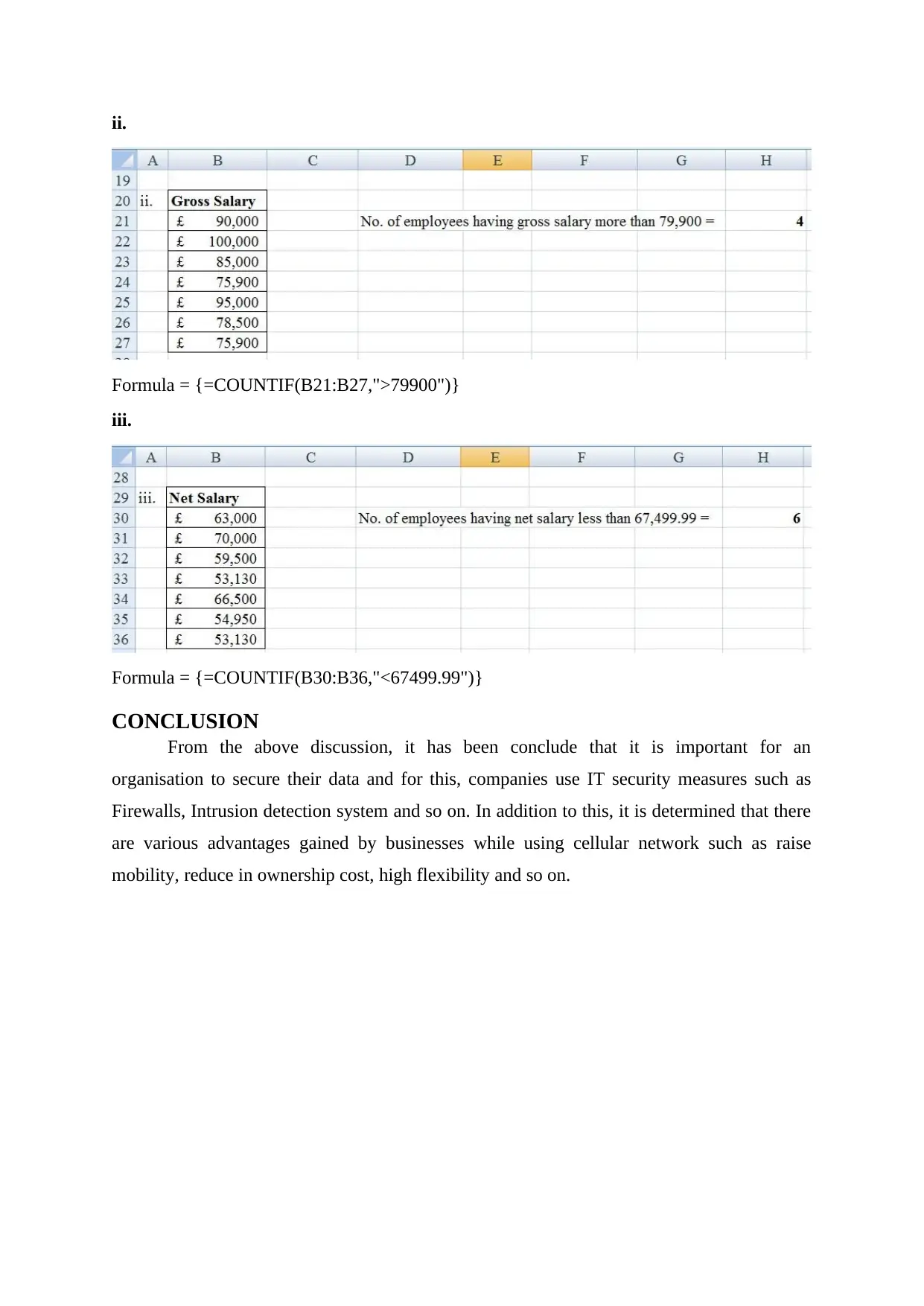
ii.
Formula = {=COUNTIF(B21:B27,">79900")}
iii.
Formula = {=COUNTIF(B30:B36,"<67499.99")}
CONCLUSION
From the above discussion, it has been conclude that it is important for an
organisation to secure their data and for this, companies use IT security measures such as
Firewalls, Intrusion detection system and so on. In addition to this, it is determined that there
are various advantages gained by businesses while using cellular network such as raise
mobility, reduce in ownership cost, high flexibility and so on.
Formula = {=COUNTIF(B21:B27,">79900")}
iii.
Formula = {=COUNTIF(B30:B36,"<67499.99")}
CONCLUSION
From the above discussion, it has been conclude that it is important for an
organisation to secure their data and for this, companies use IT security measures such as
Firewalls, Intrusion detection system and so on. In addition to this, it is determined that there
are various advantages gained by businesses while using cellular network such as raise
mobility, reduce in ownership cost, high flexibility and so on.

References
Books and Journals
Ahson, S.A. and Ilyas, M., 2017. RFID handbook: applications, technology, security, and
privacy. CRC press.
Anthony Jr, B., 2019. Green information system integration for environmental performance
in organizations: An extension of belief–action–outcome framework and natural
resource-based view theory. Benchmarking: An International Journal.
Board, R.D., 2019. The psychoanalysis of organizations: A psychoanalytic approach to
behaviour in groups and organizations. Routledge.
Ciapetti, L. and Perulli, P., 2018. New tech spaces for old tech places? Exploring the network
of research and technology organizations across North Italian Regions. European
planning studies, 26(1), pp.192-211.
Hatami, M. and Momen, A., 2019. The Study of the Impact of Technology and Information
Technology on Entrepreneurship in Organizations.
Hoffman, A.J., 2017. Millennials, Technology and Perceived Relevance of Community
Service Organizations: Is Social Media Replacing Community Service
Activities?. The Urban Review, 49(1), pp.140-152.
Hou, H., 2017, July. The application of blockchain technology in E-government in China.
In 2017 26th International Conference on Computer Communication and Networks
(ICCCN) (pp. 1-4). IEEE.
Loonam, J., Eaves, S., Kumar, V. and Parry, G., 2018. Towards digital transformation:
Lessons learned from traditional organizations. Strategic Change, 27(2), pp.101-
109.
Nobles, C., 2018. Botching human factors in cybersecurity in business
organizations. HOLISTICA–Journal of Business and Public Administration, 9(3),
pp.71-88.
Rumrill, K.K., 2019. How Organizations Can Put Sites First When Implementing New Trial
Technology. Applied Clinical Trials, 28(9), pp.34-34.
Books and Journals
Ahson, S.A. and Ilyas, M., 2017. RFID handbook: applications, technology, security, and
privacy. CRC press.
Anthony Jr, B., 2019. Green information system integration for environmental performance
in organizations: An extension of belief–action–outcome framework and natural
resource-based view theory. Benchmarking: An International Journal.
Board, R.D., 2019. The psychoanalysis of organizations: A psychoanalytic approach to
behaviour in groups and organizations. Routledge.
Ciapetti, L. and Perulli, P., 2018. New tech spaces for old tech places? Exploring the network
of research and technology organizations across North Italian Regions. European
planning studies, 26(1), pp.192-211.
Hatami, M. and Momen, A., 2019. The Study of the Impact of Technology and Information
Technology on Entrepreneurship in Organizations.
Hoffman, A.J., 2017. Millennials, Technology and Perceived Relevance of Community
Service Organizations: Is Social Media Replacing Community Service
Activities?. The Urban Review, 49(1), pp.140-152.
Hou, H., 2017, July. The application of blockchain technology in E-government in China.
In 2017 26th International Conference on Computer Communication and Networks
(ICCCN) (pp. 1-4). IEEE.
Loonam, J., Eaves, S., Kumar, V. and Parry, G., 2018. Towards digital transformation:
Lessons learned from traditional organizations. Strategic Change, 27(2), pp.101-
109.
Nobles, C., 2018. Botching human factors in cybersecurity in business
organizations. HOLISTICA–Journal of Business and Public Administration, 9(3),
pp.71-88.
Rumrill, K.K., 2019. How Organizations Can Put Sites First When Implementing New Trial
Technology. Applied Clinical Trials, 28(9), pp.34-34.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




