COM4061-N: Exploring Hacking & Tinkering - Research Proposal
VerifiedAdded on 2023/06/13
|12
|2164
|242
Report
AI Summary
This document presents a research proposal focusing on the theme of hacking and technological tinkering, submitted for the Research Methods for Computing module (COM4061-N) at the University of Teesside. The proposal includes a literature review analyzing 15 articles and academic papers to explore the concept of hacking, its evolution, and its implications within the information technology landscape. The review covers search strategies employed across various databases such as IEEE, ACM, Sage Journals, ScienceDirect, and Scholarly Articles, detailing the keywords and filters used. It also addresses the inclusion and exclusion criteria for selecting relevant papers, and concludes by identifying limitations in the existing literature, particularly the lack of coverage on the latest hacking technologies and mitigation strategies. The proposal aims to contribute to the understanding of hacking's dual nature, both as a threat and a tool for technological advancement.

Running head: RESEARCH PROPOSAL
University of Teesside
School of Computing
Module: Research Methods for Computing, COM4061-N
Assignment Title: Literature Search/Review and Project Proposal
Hacking and Technological Tinkering
Author’s name
Author’s student number
Readership: Elisabeth Yaneske, Andrew Bingham
Date of Submission:
Part 1 Word Count: 2000 words (excluding references)
Part 2 Word Count: 2500 words (excluding references)
University of Teesside
School of Computing
Module: Research Methods for Computing, COM4061-N
Assignment Title: Literature Search/Review and Project Proposal
Hacking and Technological Tinkering
Author’s name
Author’s student number
Readership: Elisabeth Yaneske, Andrew Bingham
Date of Submission:
Part 1 Word Count: 2000 words (excluding references)
Part 2 Word Count: 2500 words (excluding references)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RESEARCH PROPOSAL
Table of Contents
Part 1: Literature Review.....................................................................................................2
1.1 Introduction....................................................................................................................2
1.2 Search............................................................................................................................3
1.3 Inclusion/Exclusion Process..........................................................................................7
1.4 Conclusion and Limitation............................................................................................8
1.5 Summary........................................................................................................................9
1.6 References....................................................................................................................10
Table of Contents
Part 1: Literature Review.....................................................................................................2
1.1 Introduction....................................................................................................................2
1.2 Search............................................................................................................................3
1.3 Inclusion/Exclusion Process..........................................................................................7
1.4 Conclusion and Limitation............................................................................................8
1.5 Summary........................................................................................................................9
1.6 References....................................................................................................................10

2RESEARCH PROPOSAL
Part 1: Literature Review
1.1 Introduction
Cyber hacking is data breach against the security of information system that is an
emerging problem for industries in the United Kingdom. The cyber-attack or the cyber hacking
is one of the first threat that the current sectors are facing. The hacking process is undertaken by
high operators who are highly trained and are highly skilled (Kim, 2014, p. 67). The cyber-
attacks are increasing day by day, and the cyber-attacks are waged by the services of state
intelligence or the proxies that are one against the government institutions of the countries,
industrial facilities, and the corporations of the nation. There are national power grids that
emerge as a choice given to vulnerability, economic as well as the social disruption caused by
widespread electricity loss. Investing in preventing a company from cyber hacking is less costly
than the failure of the property that is caused by a cyber-attack. After the cyber hack, much time
is spent in fighting with the attack.
Hacking is considered to be a part of computing for more than fifty years, and piracy
consists of many topics that can be studied of. The first known hacking took place in the year
1960 at MIT, and after that hacking, the term hacker was then originated. Hacking is basically an
act by which an attacker finds ways to make the entry in some other’s system or make entry to
computer networks (Rosner et al., 2016, p. 1137). The hacking is unauthorized access to
someone else’s policy or unknown computer network that is done deliberately for harming the
computer system or might be done to steal information from other systems. Hacking is an
unethical way of getting access to other’s system, but sometimes it is considered as legal when
hacking helps to find the weakness in a computer system or a network system for the purpose
Part 1: Literature Review
1.1 Introduction
Cyber hacking is data breach against the security of information system that is an
emerging problem for industries in the United Kingdom. The cyber-attack or the cyber hacking
is one of the first threat that the current sectors are facing. The hacking process is undertaken by
high operators who are highly trained and are highly skilled (Kim, 2014, p. 67). The cyber-
attacks are increasing day by day, and the cyber-attacks are waged by the services of state
intelligence or the proxies that are one against the government institutions of the countries,
industrial facilities, and the corporations of the nation. There are national power grids that
emerge as a choice given to vulnerability, economic as well as the social disruption caused by
widespread electricity loss. Investing in preventing a company from cyber hacking is less costly
than the failure of the property that is caused by a cyber-attack. After the cyber hack, much time
is spent in fighting with the attack.
Hacking is considered to be a part of computing for more than fifty years, and piracy
consists of many topics that can be studied of. The first known hacking took place in the year
1960 at MIT, and after that hacking, the term hacker was then originated. Hacking is basically an
act by which an attacker finds ways to make the entry in some other’s system or make entry to
computer networks (Rosner et al., 2016, p. 1137). The hacking is unauthorized access to
someone else’s policy or unknown computer network that is done deliberately for harming the
computer system or might be done to steal information from other systems. Hacking is an
unethical way of getting access to other’s system, but sometimes it is considered as legal when
hacking helps to find the weakness in a computer system or a network system for the purpose
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3RESEARCH PROPOSAL
testing. This type of hacking is called ethical hacking, and the expert who does the hacking is
known as a hacker. Hackers are usually highly skilled and have the knowledge about the
operation of the system on which the hacking us to take place, finally getting the access to the
computer system.
In this section, a detailed study is conducted about the hacking process, and the tinkering
hacker does on the information technology. To study the tinkering effect of hacking, 15 such
articles and academic papers are analyzed that explains the hacking process elaborately.
1.2 Search
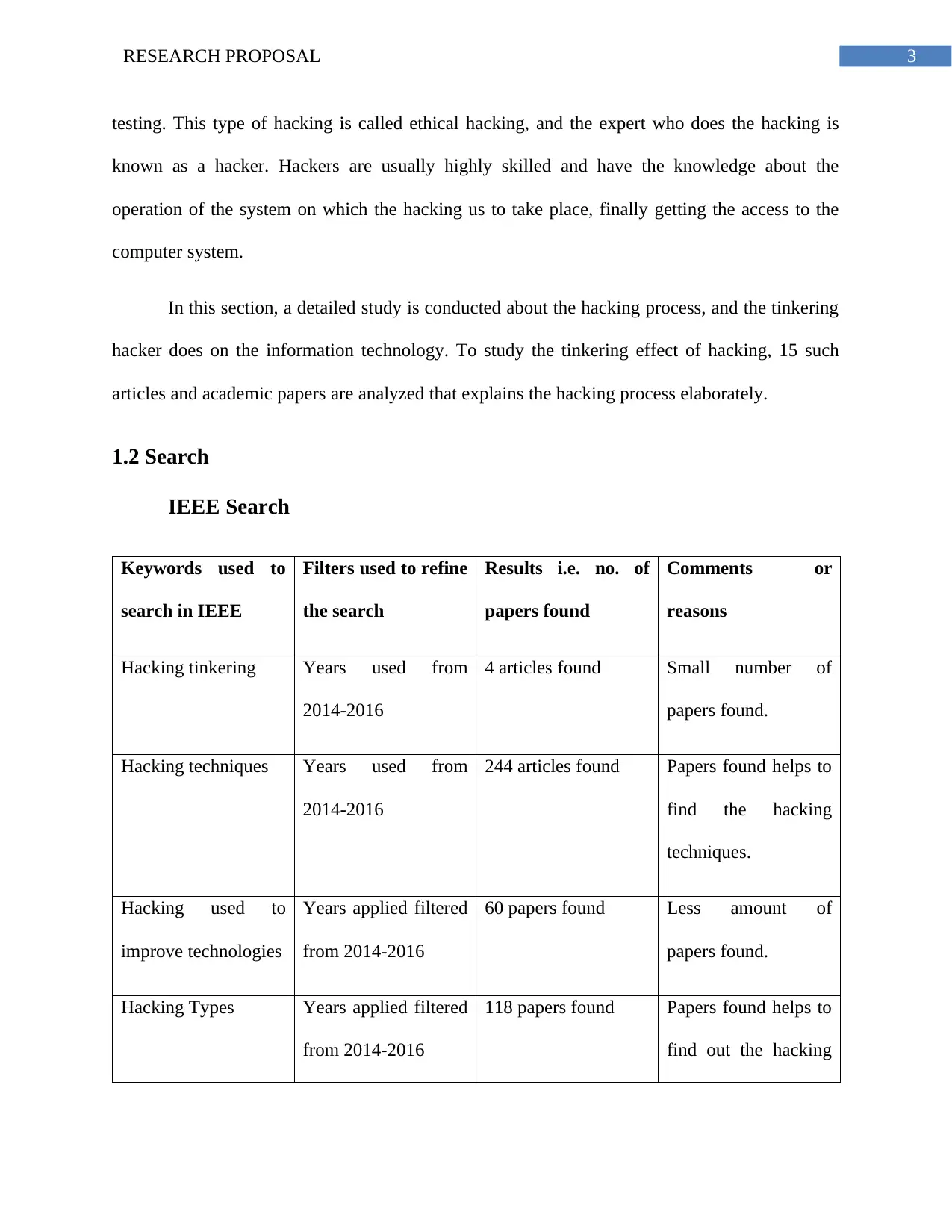
IEEE Search
Keywords used to
search in IEEE
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from
2014-2016
4 articles found Small number of
papers found.
Hacking techniques Years used from
2014-2016
244 articles found Papers found helps to
find the hacking
techniques.
Hacking used to
improve technologies
Years applied filtered
from 2014-2016
60 papers found Less amount of
papers found.
Hacking Types Years applied filtered
from 2014-2016
118 papers found Papers found helps to
find out the hacking
testing. This type of hacking is called ethical hacking, and the expert who does the hacking is
known as a hacker. Hackers are usually highly skilled and have the knowledge about the
operation of the system on which the hacking us to take place, finally getting the access to the
computer system.
In this section, a detailed study is conducted about the hacking process, and the tinkering
hacker does on the information technology. To study the tinkering effect of hacking, 15 such
articles and academic papers are analyzed that explains the hacking process elaborately.
1.2 Search
IEEE Search
Keywords used to
search in IEEE
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from
2014-2016
4 articles found Small number of
papers found.
Hacking techniques Years used from
2014-2016
244 articles found Papers found helps to
find the hacking
techniques.
Hacking used to
improve technologies
Years applied filtered
from 2014-2016
60 papers found Less amount of
papers found.
Hacking Types Years applied filtered
from 2014-2016
118 papers found Papers found helps to
find out the hacking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4RESEARCH PROPOSAL
types.
Phases of Hacking Years applied filtered
from 2014-2016
24 papers found Less number of
papers found.
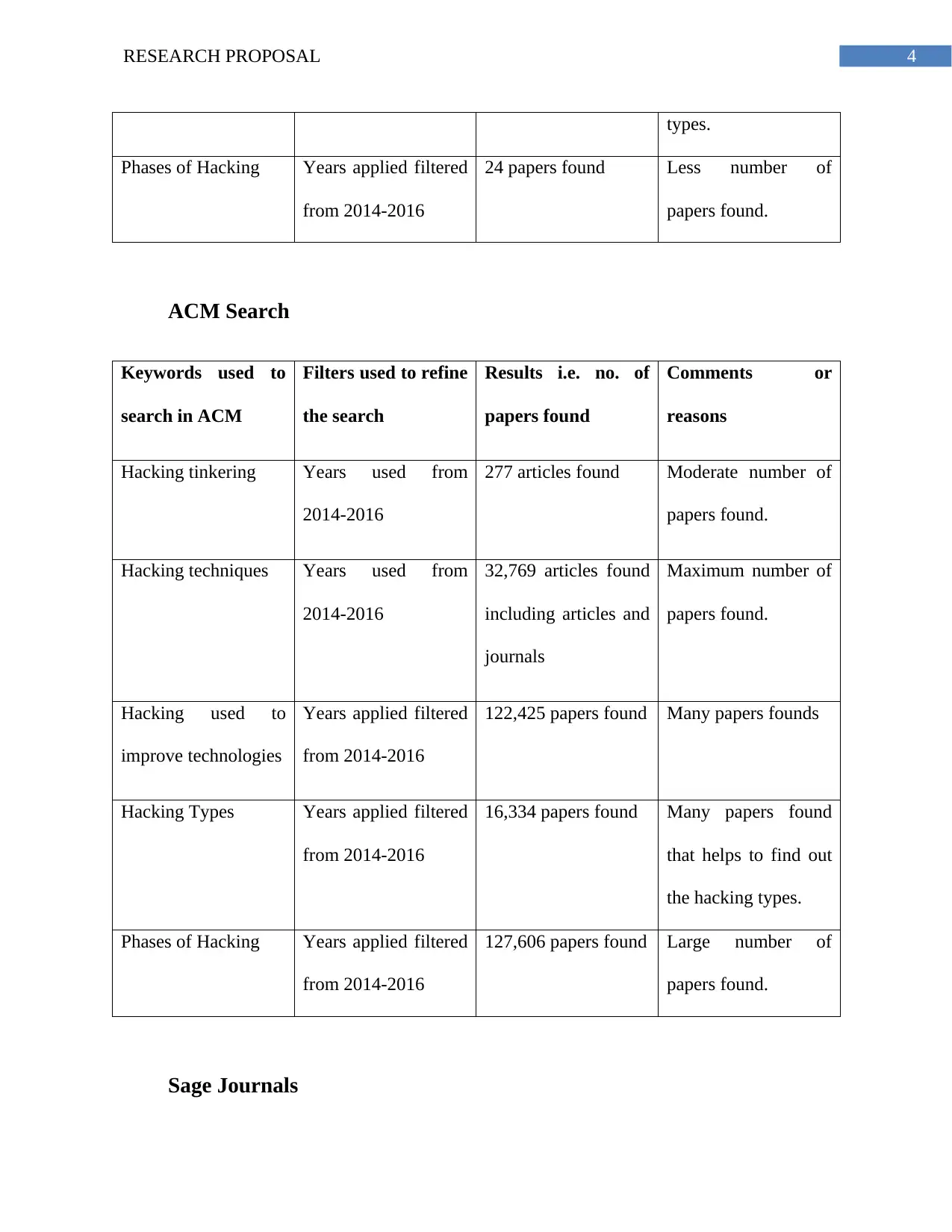
ACM Search
Keywords used to
search in ACM
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from
2014-2016
277 articles found Moderate number of
papers found.
Hacking techniques Years used from
2014-2016
32,769 articles found
including articles and
journals
Maximum number of
papers found.
Hacking used to
improve technologies
Years applied filtered
from 2014-2016
122,425 papers found Many papers founds
Hacking Types Years applied filtered
from 2014-2016
16,334 papers found Many papers found
that helps to find out
the hacking types.
Phases of Hacking Years applied filtered
from 2014-2016
127,606 papers found Large number of
papers found.
Sage Journals
types.
Phases of Hacking Years applied filtered
from 2014-2016
24 papers found Less number of
papers found.
ACM Search
Keywords used to
search in ACM
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from
2014-2016
277 articles found Moderate number of
papers found.
Hacking techniques Years used from
2014-2016
32,769 articles found
including articles and
journals
Maximum number of
papers found.
Hacking used to
improve technologies
Years applied filtered
from 2014-2016
122,425 papers found Many papers founds
Hacking Types Years applied filtered
from 2014-2016
16,334 papers found Many papers found
that helps to find out
the hacking types.
Phases of Hacking Years applied filtered
from 2014-2016
127,606 papers found Large number of
papers found.
Sage Journals
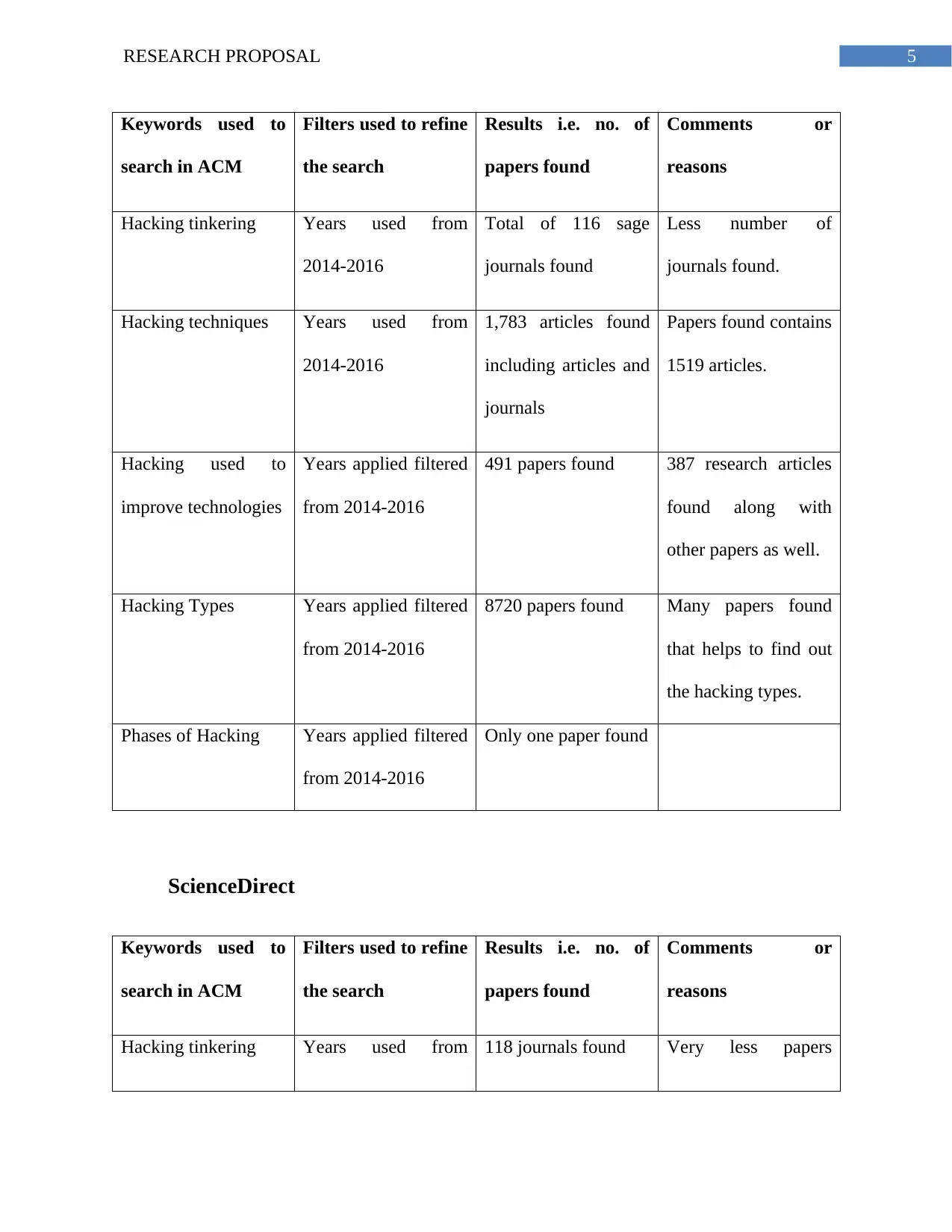
5RESEARCH PROPOSAL
Keywords used to
search in ACM
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from
2014-2016
Total of 116 sage
journals found
Less number of
journals found.
Hacking techniques Years used from
2014-2016
1,783 articles found
including articles and
journals
Papers found contains
1519 articles.
Hacking used to
improve technologies
Years applied filtered
from 2014-2016
491 papers found 387 research articles
found along with
other papers as well.
Hacking Types Years applied filtered
from 2014-2016
8720 papers found Many papers found
that helps to find out
the hacking types.
Phases of Hacking Years applied filtered
from 2014-2016
Only one paper found
ScienceDirect
Keywords used to
search in ACM
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from 118 journals found Very less papers
Keywords used to
search in ACM
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from
2014-2016
Total of 116 sage
journals found
Less number of
journals found.
Hacking techniques Years used from
2014-2016
1,783 articles found
including articles and
journals
Papers found contains
1519 articles.
Hacking used to
improve technologies
Years applied filtered
from 2014-2016
491 papers found 387 research articles
found along with
other papers as well.
Hacking Types Years applied filtered
from 2014-2016
8720 papers found Many papers found
that helps to find out
the hacking types.
Phases of Hacking Years applied filtered
from 2014-2016
Only one paper found
ScienceDirect
Keywords used to
search in ACM
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from 118 journals found Very less papers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
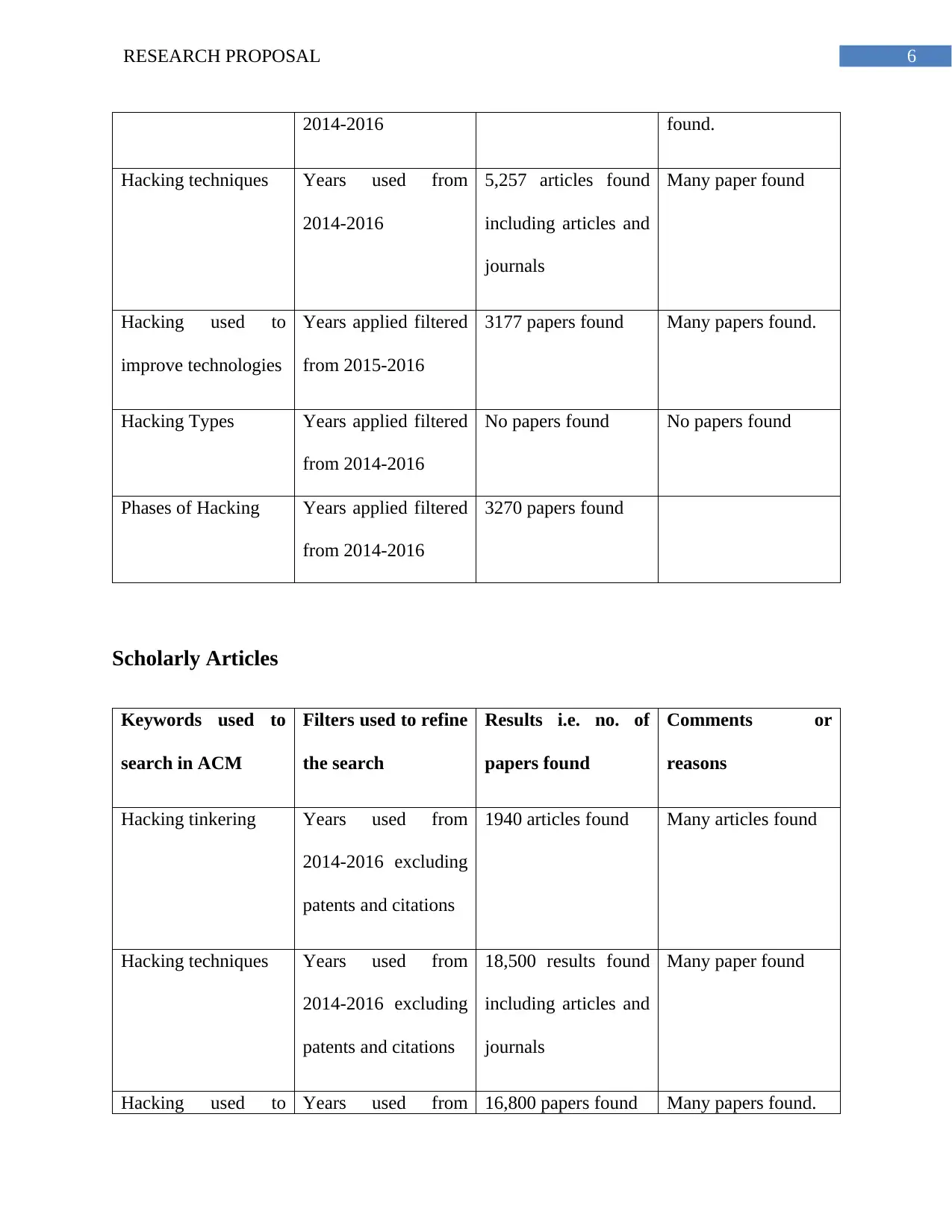
6RESEARCH PROPOSAL
2014-2016 found.
Hacking techniques Years used from
2014-2016
5,257 articles found
including articles and
journals
Many paper found
Hacking used to
improve technologies
Years applied filtered
from 2015-2016
3177 papers found Many papers found.
Hacking Types Years applied filtered
from 2014-2016
No papers found No papers found
Phases of Hacking Years applied filtered
from 2014-2016
3270 papers found
Scholarly Articles
Keywords used to
search in ACM
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from
2014-2016 excluding
patents and citations
1940 articles found Many articles found
Hacking techniques Years used from
2014-2016 excluding
patents and citations
18,500 results found
including articles and
journals
Many paper found
Hacking used to Years used from 16,800 papers found Many papers found.
2014-2016 found.
Hacking techniques Years used from
2014-2016
5,257 articles found
including articles and
journals
Many paper found
Hacking used to
improve technologies
Years applied filtered
from 2015-2016
3177 papers found Many papers found.
Hacking Types Years applied filtered
from 2014-2016
No papers found No papers found
Phases of Hacking Years applied filtered
from 2014-2016
3270 papers found
Scholarly Articles
Keywords used to
search in ACM
Filters used to refine
the search
Results i.e. no. of
papers found
Comments or
reasons
Hacking tinkering Years used from
2014-2016 excluding
patents and citations
1940 articles found Many articles found
Hacking techniques Years used from
2014-2016 excluding
patents and citations
18,500 results found
including articles and
journals
Many paper found
Hacking used to Years used from 16,800 papers found Many papers found.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
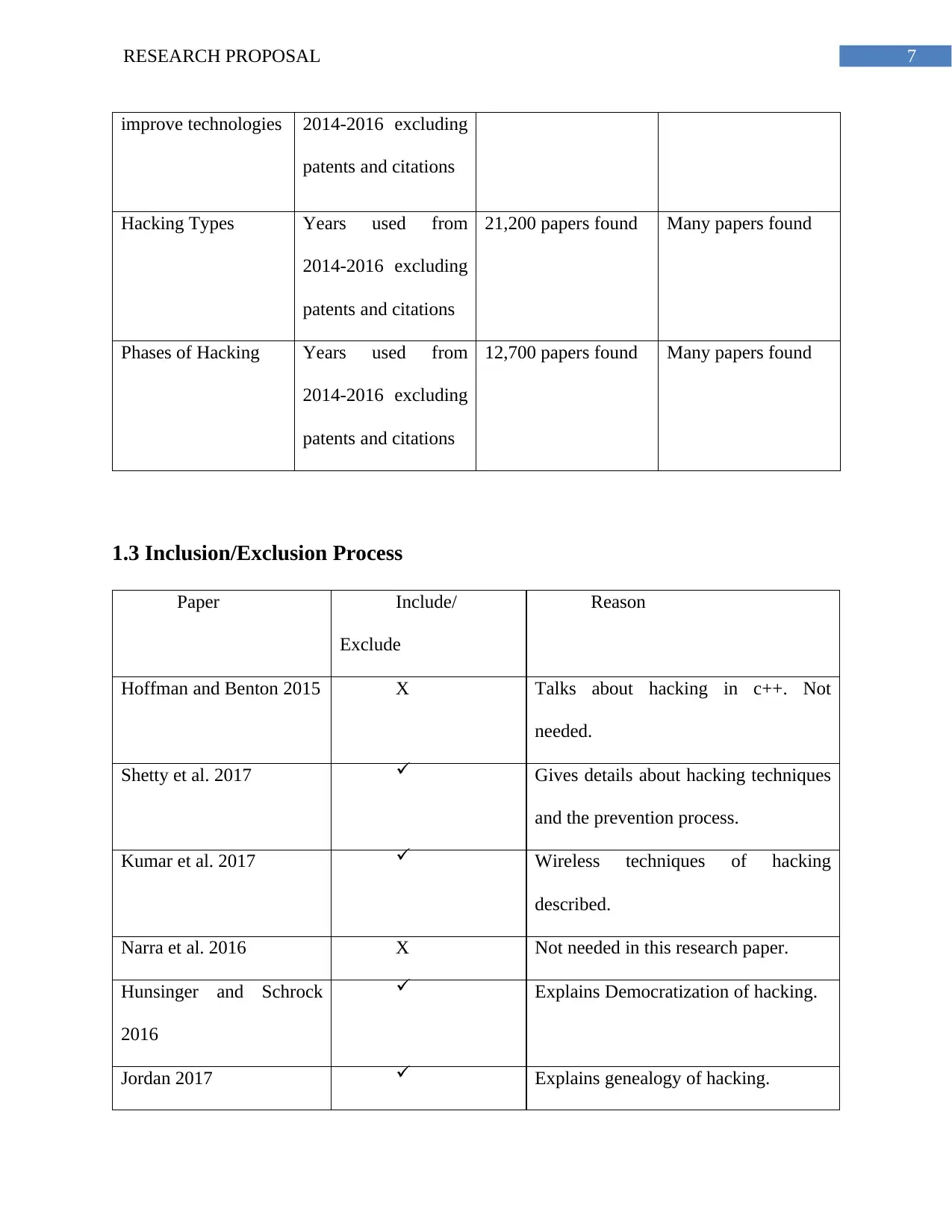
7RESEARCH PROPOSAL
improve technologies 2014-2016 excluding
patents and citations
Hacking Types Years used from
2014-2016 excluding
patents and citations
21,200 papers found Many papers found
Phases of Hacking Years used from
2014-2016 excluding
patents and citations
12,700 papers found Many papers found
1.3 Inclusion/Exclusion Process
Paper Include/
Exclude
Reason
Hoffman and Benton 2015 X Talks about hacking in c++. Not
needed.
Shetty et al. 2017 Gives details about hacking techniques
and the prevention process.
Kumar et al. 2017 Wireless techniques of hacking
described.
Narra et al. 2016 X Not needed in this research paper.
Hunsinger and Schrock
2016
Explains Democratization of hacking.
Jordan 2017 Explains genealogy of hacking.
improve technologies 2014-2016 excluding
patents and citations
Hacking Types Years used from
2014-2016 excluding
patents and citations
21,200 papers found Many papers found
Phases of Hacking Years used from
2014-2016 excluding
patents and citations
12,700 papers found Many papers found
1.3 Inclusion/Exclusion Process
Paper Include/
Exclude
Reason
Hoffman and Benton 2015 X Talks about hacking in c++. Not
needed.
Shetty et al. 2017 Gives details about hacking techniques
and the prevention process.
Kumar et al. 2017 Wireless techniques of hacking
described.
Narra et al. 2016 X Not needed in this research paper.
Hunsinger and Schrock
2016
Explains Democratization of hacking.
Jordan 2017 Explains genealogy of hacking.
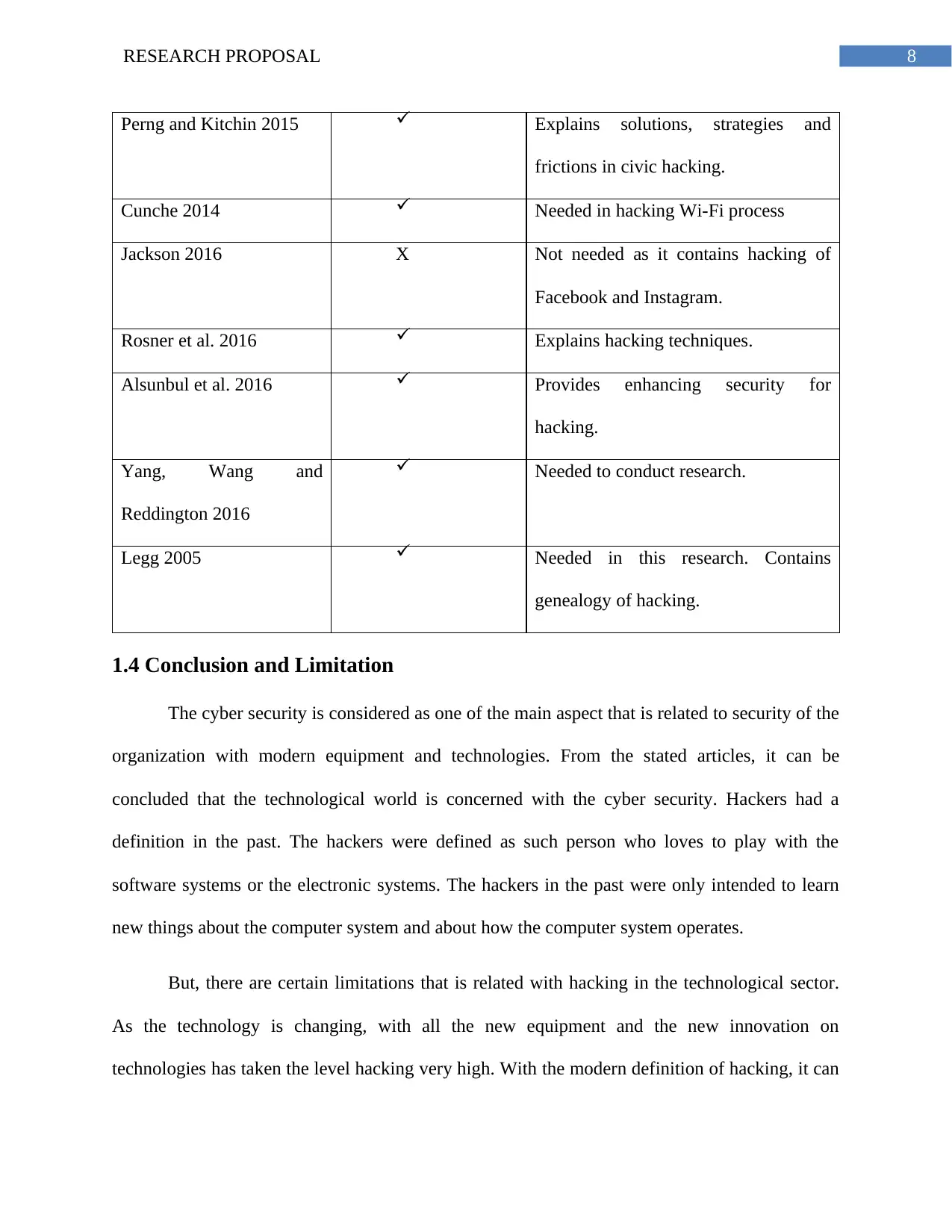
8RESEARCH PROPOSAL
Perng and Kitchin 2015 Explains solutions, strategies and
frictions in civic hacking.
Cunche 2014 Needed in hacking Wi-Fi process
Jackson 2016 X Not needed as it contains hacking of
Facebook and Instagram.
Rosner et al. 2016 Explains hacking techniques.
Alsunbul et al. 2016 Provides enhancing security for
hacking.
Yang, Wang and
Reddington 2016
Needed to conduct research.
Legg 2005 Needed in this research. Contains
genealogy of hacking.
1.4 Conclusion and Limitation
The cyber security is considered as one of the main aspect that is related to security of the
organization with modern equipment and technologies. From the stated articles, it can be
concluded that the technological world is concerned with the cyber security. Hackers had a
definition in the past. The hackers were defined as such person who loves to play with the
software systems or the electronic systems. The hackers in the past were only intended to learn
new things about the computer system and about how the computer system operates.
But, there are certain limitations that is related with hacking in the technological sector.
As the technology is changing, with all the new equipment and the new innovation on
technologies has taken the level hacking very high. With the modern definition of hacking, it can
Perng and Kitchin 2015 Explains solutions, strategies and
frictions in civic hacking.
Cunche 2014 Needed in hacking Wi-Fi process
Jackson 2016 X Not needed as it contains hacking of
Facebook and Instagram.
Rosner et al. 2016 Explains hacking techniques.
Alsunbul et al. 2016 Provides enhancing security for
hacking.
Yang, Wang and
Reddington 2016
Needed to conduct research.
Legg 2005 Needed in this research. Contains
genealogy of hacking.
1.4 Conclusion and Limitation
The cyber security is considered as one of the main aspect that is related to security of the
organization with modern equipment and technologies. From the stated articles, it can be
concluded that the technological world is concerned with the cyber security. Hackers had a
definition in the past. The hackers were defined as such person who loves to play with the
software systems or the electronic systems. The hackers in the past were only intended to learn
new things about the computer system and about how the computer system operates.
But, there are certain limitations that is related with hacking in the technological sector.
As the technology is changing, with all the new equipment and the new innovation on
technologies has taken the level hacking very high. With the modern definition of hacking, it can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RESEARCH PROPOSAL
be stated that hacker is a person or a group of person that that breaks into some unknown system
without the consent of the user and gaining personal information from those systems. Hacking is
basically considered as unethical process and the hackers who are related with the system are
known as crackers or criminals. The hackers breaks into system with intent to get all personal
information of the user. Unethical hacking can be done for fame, revenge or might be for gaining
profit.
1.5 Summary
There are ethical hacker as well that mainly aims to good purpose. The ethical hacking is
mainly intended for the purpose of testing the system or finding out some information for good
need. All hackers do not have same expertise level. The skills of the hackers depends on what
kind of work the hacker wants to try.
After reviewing all the articles related with hacking and tinkering technology, it can be
concluded that hacking can be considered as advantage and disadvantage in technological aspect.
The gap that can be studied from the articles taken is that none of the paper reviews the latest
hacking technology. The way to mitigate the latest types of hacking technologies are also not
explained in the articles studied.
be stated that hacker is a person or a group of person that that breaks into some unknown system
without the consent of the user and gaining personal information from those systems. Hacking is
basically considered as unethical process and the hackers who are related with the system are
known as crackers or criminals. The hackers breaks into system with intent to get all personal
information of the user. Unethical hacking can be done for fame, revenge or might be for gaining
profit.
1.5 Summary
There are ethical hacker as well that mainly aims to good purpose. The ethical hacking is
mainly intended for the purpose of testing the system or finding out some information for good
need. All hackers do not have same expertise level. The skills of the hackers depends on what
kind of work the hacker wants to try.
After reviewing all the articles related with hacking and tinkering technology, it can be
concluded that hacking can be considered as advantage and disadvantage in technological aspect.
The gap that can be studied from the articles taken is that none of the paper reviews the latest
hacking technology. The way to mitigate the latest types of hacking technologies are also not
explained in the articles studied.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RESEARCH PROPOSAL
1.6 References
Alsunbul et al. (2016), January. A network defense system for detecting and preventing potential
hacking attempts. In Information Networking (ICOIN), 2016 International Conference on (pp.
449-454). IEEE.
Hunsinger, J. and Schrock, A. (2016). The democratization of hacking and making.
Joe, M.M. and Ramakrishnan, B. (2014). Enhancing security module to prevent data hacking in
online social networks. Journal of Emerging Technologies in Web Intelligence, 6(2), pp.184-191.
Jordan, T. (2017). A genealogy of hacking. Convergence, 23(5), pp.528-544.
Kim, P. (2014). The hacker playbook 2: practical guide to penetration testing. Secure Planet
LLC.
Kshetri, N. and Voas, J. (2017). Hacking Power Grids: A Current Problem. Computer, 50(12),
pp.91-95.
Legg, C. (2005). Hacking: The performance of technology?.
Marlatt, G.E. (2015). Outlaw Motorcycle Gangs (OMG): A Brief Bibliography.
Perng, S.Y. and Kitchin, R. (2015). Solutions, strategies and frictions in civic hacking.
Powell, A. (2016). Hacking in the public interest: Authority, legitimacy, means, and ends. New
Media & Society, 18(4), pp.600-616.
Rosner, D.K. et al. (2016), February. Out of Time, Out of Place: Reflections on Design
Workshops as a Research Method. In Proceedings of the 19th ACM Conference on Computer-
Supported Cooperative Work & Social Computing (pp. 1131-1141). ACM.
1.6 References
Alsunbul et al. (2016), January. A network defense system for detecting and preventing potential
hacking attempts. In Information Networking (ICOIN), 2016 International Conference on (pp.
449-454). IEEE.
Hunsinger, J. and Schrock, A. (2016). The democratization of hacking and making.
Joe, M.M. and Ramakrishnan, B. (2014). Enhancing security module to prevent data hacking in
online social networks. Journal of Emerging Technologies in Web Intelligence, 6(2), pp.184-191.
Jordan, T. (2017). A genealogy of hacking. Convergence, 23(5), pp.528-544.
Kim, P. (2014). The hacker playbook 2: practical guide to penetration testing. Secure Planet
LLC.
Kshetri, N. and Voas, J. (2017). Hacking Power Grids: A Current Problem. Computer, 50(12),
pp.91-95.
Legg, C. (2005). Hacking: The performance of technology?.
Marlatt, G.E. (2015). Outlaw Motorcycle Gangs (OMG): A Brief Bibliography.
Perng, S.Y. and Kitchin, R. (2015). Solutions, strategies and frictions in civic hacking.
Powell, A. (2016). Hacking in the public interest: Authority, legitimacy, means, and ends. New
Media & Society, 18(4), pp.600-616.
Rosner, D.K. et al. (2016), February. Out of Time, Out of Place: Reflections on Design
Workshops as a Research Method. In Proceedings of the 19th ACM Conference on Computer-
Supported Cooperative Work & Social Computing (pp. 1131-1141). ACM.

11RESEARCH PROPOSAL
Tang, A. (2015). Hacking Back against Cyber Attacks. Chicago Policy Review (Online).
Wood, K.C. (2016). Hacking T cells with synthetic circuits to program antitumor
responses. Science Translational Medicine, 8(362), pp.362ec172-362ec172.
Wu, Y., Fong, S. and Zhuang, Y. (2017), December. General Precautions against Security
Threats for Computer Networks in SMEs: From the Perspective of Big Data and IOT.
In Proceedings of the International Conference on Big Data and Internet of Thing (pp. 134-140).
ACM.
Yang, J., Wang, Y. and Reddington, T. (2016), March. Integrate Hacking Technique into
Information Assurance Education. In Advanced Information Networking and Applications
Workshops (WAINA), 2016 30th International Conference on(pp. 381-387). IEEE.
Tang, A. (2015). Hacking Back against Cyber Attacks. Chicago Policy Review (Online).
Wood, K.C. (2016). Hacking T cells with synthetic circuits to program antitumor
responses. Science Translational Medicine, 8(362), pp.362ec172-362ec172.
Wu, Y., Fong, S. and Zhuang, Y. (2017), December. General Precautions against Security
Threats for Computer Networks in SMEs: From the Perspective of Big Data and IOT.
In Proceedings of the International Conference on Big Data and Internet of Thing (pp. 134-140).
ACM.
Yang, J., Wang, Y. and Reddington, T. (2016), March. Integrate Hacking Technique into
Information Assurance Education. In Advanced Information Networking and Applications
Workshops (WAINA), 2016 30th International Conference on(pp. 381-387). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





