Network Infrastructure Design for Cookie Co: A Comprehensive Report
VerifiedAdded on 2020/05/08
|14
|2965
|34
Report
AI Summary
This report provides a comprehensive analysis of the network infrastructure for Cookie Co, a cookie chain store experiencing network issues. The report begins with an executive summary outlining the proposed solutions for network infrastructure, networked services, and data processing facilities. It includes an IT infrastructure network diagram and explains the benefits of network services such as VoIP, WWW, Intranet, Extranet, Email, and Web services. The report discusses data processing facilities, including data storage solutions and processing models, and offers recommendations for future network infrastructure. The introduction highlights the company's need for a new IT infrastructure to solve network problems and improve company growth. The report details network convergence, unified communications, LAN types, cabling plans, WAN connections, transmission media, and connecting devices. It explains IP and DNS management, networked services (VoIP, WWW, Web services, and Email), and data processing facilities (data storage solutions and data processing models). Finally, the report provides recommendations for maintaining and improving the network infrastructure, including performance enhancements, proactive monitoring, system documentation, and WAN optimization. The report is intended to assist in the design and implementation of a robust and efficient network for the company.
Telecommunications and Networks
Page
Telecommunications and Networks
Page
Telecommunications and Networks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Telecommunications and Networks
Executive summary
The possible solutions for the network infrastructure, networked services and data processing
facilities are discussed. The IT infrastructure network diagram is drawn The network services
such as VOIP, WWW, Intranet, Extranet, Email and Web services and its benefits are explained.
The data processing facilities like data storage solution and data processing model is briefly
discussed. The solutions and recommendations for future network infrastructure for cookie co
are given.
Pagei
Executive summary
The possible solutions for the network infrastructure, networked services and data processing
facilities are discussed. The IT infrastructure network diagram is drawn The network services
such as VOIP, WWW, Intranet, Extranet, Email and Web services and its benefits are explained.
The data processing facilities like data storage solution and data processing model is briefly
discussed. The solutions and recommendations for future network infrastructure for cookie co
are given.
Pagei

Telecommunications and Networks
Table of Contents
1. Introduction......................................................................................................................................1
2. Network Infrastructure..................................................................................................................1
2.1 IT Infrastructure..........................................................................................................................1
2.2 Network convergence and unified communications..................................................................2
2.3 LAN types and cabling plan for the head office and branches...................................................2
2.4 WAN connection for the head office and branches....................................................................2
2.4 Transmission media and connecting devices.............................................................................3
2.5 IP and DNS management............................................................................................................3
3. Networked services........................................................................................................................4
3.1 VOIP.............................................................................................................................................4
3.2 WWW..........................................................................................................................................5
3.3 Web services...............................................................................................................................5
3.4 Email............................................................................................................................................5
4. Data Processing Facilities............................................................................................................5
4.1 Data storage solution..................................................................................................................5
4.2 Data processing model................................................................................................................6
5. Recommendations.........................................................................................................................6
6. Conclusion.......................................................................................................................................6
References...............................................................................................................................................7
Pageii
Table of Contents
1. Introduction......................................................................................................................................1
2. Network Infrastructure..................................................................................................................1
2.1 IT Infrastructure..........................................................................................................................1
2.2 Network convergence and unified communications..................................................................2
2.3 LAN types and cabling plan for the head office and branches...................................................2
2.4 WAN connection for the head office and branches....................................................................2
2.4 Transmission media and connecting devices.............................................................................3
2.5 IP and DNS management............................................................................................................3
3. Networked services........................................................................................................................4
3.1 VOIP.............................................................................................................................................4
3.2 WWW..........................................................................................................................................5
3.3 Web services...............................................................................................................................5
3.4 Email............................................................................................................................................5
4. Data Processing Facilities............................................................................................................5
4.1 Data storage solution..................................................................................................................5
4.2 Data processing model................................................................................................................6
5. Recommendations.........................................................................................................................6
6. Conclusion.......................................................................................................................................6
References...............................................................................................................................................7
Pageii
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Telecommunications and Networks
1. Introduction
The Cookie Co is a cookies chain store. It has a slow network connection.so it received some
collision in the voice calls. It made a problem for customers and staffs. The Cookie Co is decided
to design a new IT infrastructure for solving these network problem. The Network structure will
be designed to improve the company growth. The Wide Area network will be used to connect a
network of all the branches of cookie co to the head office. The transmission media, DNS
management, IP and connecting devices will be used for the further process. The WWW, Email,
VOIP and Intranet network services will be used. The problem of cookie co Staff and customers
can be solved by the new IT network structure.
Page 1
1. Introduction
The Cookie Co is a cookies chain store. It has a slow network connection.so it received some
collision in the voice calls. It made a problem for customers and staffs. The Cookie Co is decided
to design a new IT infrastructure for solving these network problem. The Network structure will
be designed to improve the company growth. The Wide Area network will be used to connect a
network of all the branches of cookie co to the head office. The transmission media, DNS
management, IP and connecting devices will be used for the further process. The WWW, Email,
VOIP and Intranet network services will be used. The problem of cookie co Staff and customers
can be solved by the new IT network structure.
Page 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Telecommunications and Networks
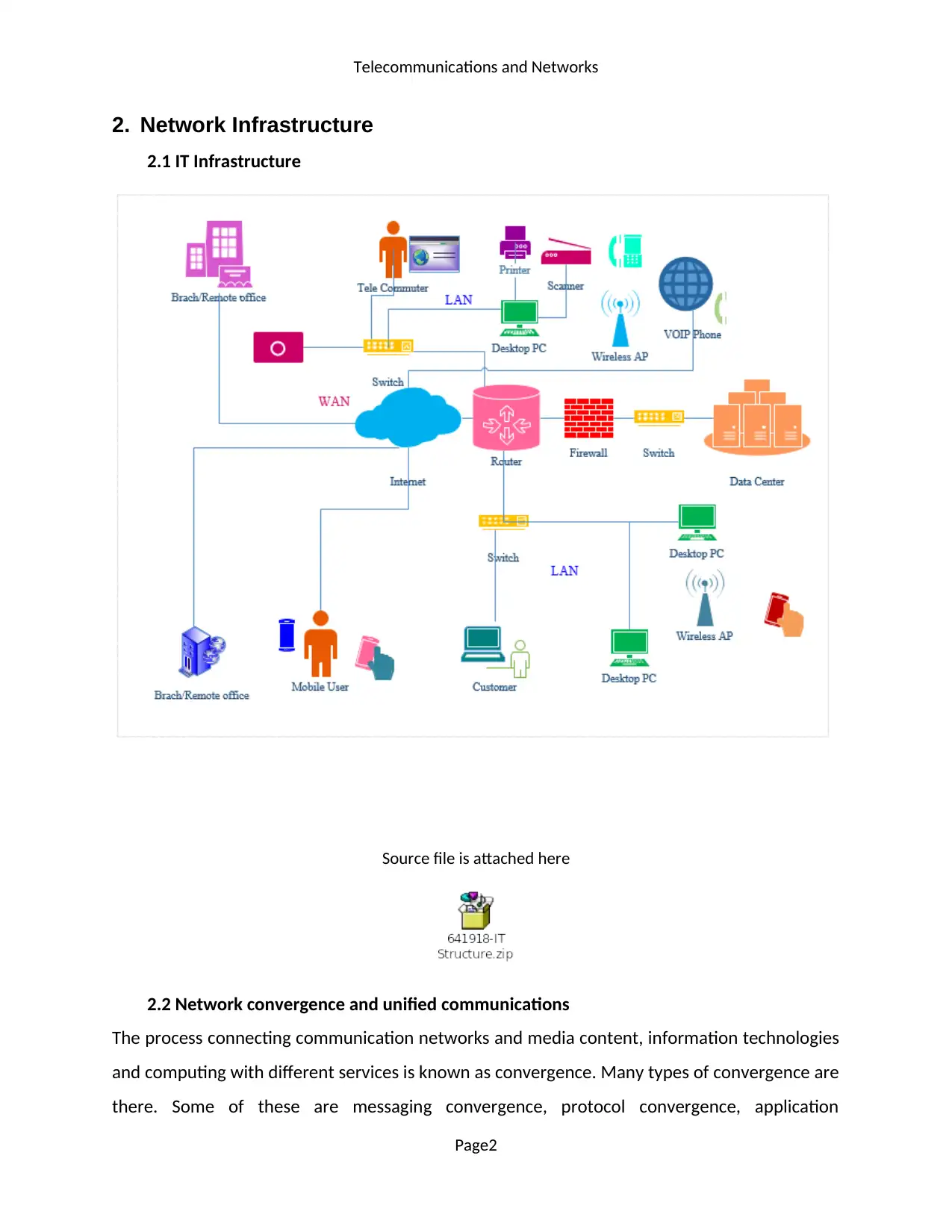
2. Network Infrastructure
2.1 IT Infrastructure
Source file is attached here
2.2 Network convergence and unified communications
The process connecting communication networks and media content, information technologies
and computing with different services is known as convergence. Many types of convergence are
there. Some of these are messaging convergence, protocol convergence, application
Page2
2. Network Infrastructure
2.1 IT Infrastructure
Source file is attached here
2.2 Network convergence and unified communications
The process connecting communication networks and media content, information technologies
and computing with different services is known as convergence. Many types of convergence are
there. Some of these are messaging convergence, protocol convergence, application
Page2

Telecommunications and Networks
convergence, technological convergence etc. The communication convergence is used for
enabling services to broadcast media telecommunication media and electronic media. It
provides service for voice telephony using the internet. Unified communications are used in
business trend, to integrate and simplify all types of communication. By using UC program, the
user could read the voice message in the e-mail. The VOIP, mobile computing, voice to text
conversion, convergence technique and presenting are the principles of UC technology. The
incorporation of data and telephony technique is known as convergence (Baldus and
Heckmann, 2017).
2.3 LAN types and cabling plan for the head office and branches
Local Area Network (LAN) link sets of PCs and low-voltage devices composed
crosswise tiny distances to share info and funds. The LAN is maintained and managed in the
enterprises. The LANs have connected the WAN by using routers (Milovanov, 2015).
Types of LAN
1. Ethernet
2. Token Ring
3. Token Bus
4. FDDI
Applications of LAN
1. To make the communication as a cheap and easy.
2. To share the internet.
3. For centralizing the data.
4. To provide the data security.
5. To share the resource.
Cables used for design the network structure
Two types of cables are used for connecting the hubs and switches to the systems (Lan
Harremanak, 2016).
1. Crossover cables- the two of wires crossed.
Page3
convergence, technological convergence etc. The communication convergence is used for
enabling services to broadcast media telecommunication media and electronic media. It
provides service for voice telephony using the internet. Unified communications are used in
business trend, to integrate and simplify all types of communication. By using UC program, the
user could read the voice message in the e-mail. The VOIP, mobile computing, voice to text
conversion, convergence technique and presenting are the principles of UC technology. The
incorporation of data and telephony technique is known as convergence (Baldus and
Heckmann, 2017).
2.3 LAN types and cabling plan for the head office and branches
Local Area Network (LAN) link sets of PCs and low-voltage devices composed
crosswise tiny distances to share info and funds. The LAN is maintained and managed in the
enterprises. The LANs have connected the WAN by using routers (Milovanov, 2015).
Types of LAN
1. Ethernet
2. Token Ring
3. Token Bus
4. FDDI
Applications of LAN
1. To make the communication as a cheap and easy.
2. To share the internet.
3. For centralizing the data.
4. To provide the data security.
5. To share the resource.
Cables used for design the network structure
Two types of cables are used for connecting the hubs and switches to the systems (Lan
Harremanak, 2016).
1. Crossover cables- the two of wires crossed.
Page3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Telecommunications and Networks
2. Straight through cables -all of the wires run straight.
2.4 WAN connection for the head office and branches
WAN stands for Wide Area Network. It is an infrastructures network. It is used to spans the
huge geographic zone such as states, cities, or countries. It is used to provide the private
connection for the business and it is public to link smaller networks together. The WAN links
some LANs. The technology is high speed and relatively expensive. The branch offices are
usually located at isolated geographical positions, associated to the main headquarters through
WAN (Wide Area Network). Branch workplace generally has fewer employers than the Head
Office (Central Office). The network assets in Area office are inadequate to the users at Branch
Office. Branch Offices ordinarily host fewer vital servers. The Wan connects all the branch
offices to the head office with security. The security for the all the systems is provided by the
firewall authentication. The customers and the traveling employees are connected to the main
office via VPN (Virtual Private network) protected broadband network. The three topologies are
used to link the multiple branch office to the head office via WAN (Liu et al., 2010).
Topologies
1. Hub-and-Spoke Site-to-site Wide Area Network Topology
2. Partial-Mesh Site-to-site Wide Area Network Topology
3. Full Mesh Site-to-site Wide Area Network Topology
2.4 Transmission media and connecting devices
The transmission medium is used to connect devices in the network structure. By using
transmission medium, the data are transmitted from one device to the other devices. Some of
the transmission medium devices are cables, routers, hub, switches, gateways and bridges etc.
Mostly the cables are used in the wired network. Hub connects the more devices to the
network using fiber optic Ethernet cable. It sends the data to each port. Switch performed
similar to the hub, but it provides better performance (FU and ZHOU, 2013). To manage the
network traffic, bridges are used.it is used to reduce the congestion. It is used to subdivide the
complex network into segments. It increases the network speed. Routers are used to link
Page4
2. Straight through cables -all of the wires run straight.
2.4 WAN connection for the head office and branches
WAN stands for Wide Area Network. It is an infrastructures network. It is used to spans the
huge geographic zone such as states, cities, or countries. It is used to provide the private
connection for the business and it is public to link smaller networks together. The WAN links
some LANs. The technology is high speed and relatively expensive. The branch offices are
usually located at isolated geographical positions, associated to the main headquarters through
WAN (Wide Area Network). Branch workplace generally has fewer employers than the Head
Office (Central Office). The network assets in Area office are inadequate to the users at Branch
Office. Branch Offices ordinarily host fewer vital servers. The Wan connects all the branch
offices to the head office with security. The security for the all the systems is provided by the
firewall authentication. The customers and the traveling employees are connected to the main
office via VPN (Virtual Private network) protected broadband network. The three topologies are
used to link the multiple branch office to the head office via WAN (Liu et al., 2010).
Topologies
1. Hub-and-Spoke Site-to-site Wide Area Network Topology
2. Partial-Mesh Site-to-site Wide Area Network Topology
3. Full Mesh Site-to-site Wide Area Network Topology
2.4 Transmission media and connecting devices
The transmission medium is used to connect devices in the network structure. By using
transmission medium, the data are transmitted from one device to the other devices. Some of
the transmission medium devices are cables, routers, hub, switches, gateways and bridges etc.
Mostly the cables are used in the wired network. Hub connects the more devices to the
network using fiber optic Ethernet cable. It sends the data to each port. Switch performed
similar to the hub, but it provides better performance (FU and ZHOU, 2013). To manage the
network traffic, bridges are used.it is used to reduce the congestion. It is used to subdivide the
complex network into segments. It increases the network speed. Routers are used to link
Page4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Telecommunications and Networks
different routers.it receives and sends the data from the correct users. The routers have the
ability to connect different network if the protocol of the networks is same. But the gateway
has the ability to connect different network with different protocols of the network. The
mainframe network used the gateway for making the connection with another network (VoIP
and Voice over LTE, 2015).
2.5 IP and DNS management
DNS Management
The secure, multi-platform and scalable, DNS is used to perform the following
operations by its tools. Comprehensive API is used to accomplish DNS via the end user. The
memory effectiveness and lookup quickness is improved. It has the auditing and diagnostic
tools to certify the domain and data integrity level. By using easy to use interface, it centrally
manage the servers (Harth and Maynard, 2014).
The challenges in DNS managements are
1. Improvement of data consistency through millions of zones and domain records
2. Reducing the response time of management and creation of domain.
3. Managing the growth in domain loads by typical BIND results.
4. Certifying the changes at DNS are circulated across servers correctly and quickly.
Benefits of DNS management
1. It is used to support all business and residential requirement of DNS.
2. It provides unmatched scalability and perfect performance.
3. Satisfy all the DNS requirement.
IP managements
To manage the IP address in the network, managing IP space, planning and tracking is
needed. The IP address management is a tedious process and it is needed one. It takes longer
Page5
different routers.it receives and sends the data from the correct users. The routers have the
ability to connect different network if the protocol of the networks is same. But the gateway
has the ability to connect different network with different protocols of the network. The
mainframe network used the gateway for making the connection with another network (VoIP
and Voice over LTE, 2015).
2.5 IP and DNS management
DNS Management
The secure, multi-platform and scalable, DNS is used to perform the following
operations by its tools. Comprehensive API is used to accomplish DNS via the end user. The
memory effectiveness and lookup quickness is improved. It has the auditing and diagnostic
tools to certify the domain and data integrity level. By using easy to use interface, it centrally
manage the servers (Harth and Maynard, 2014).
The challenges in DNS managements are
1. Improvement of data consistency through millions of zones and domain records
2. Reducing the response time of management and creation of domain.
3. Managing the growth in domain loads by typical BIND results.
4. Certifying the changes at DNS are circulated across servers correctly and quickly.
Benefits of DNS management
1. It is used to support all business and residential requirement of DNS.
2. It provides unmatched scalability and perfect performance.
3. Satisfy all the DNS requirement.
IP managements
To manage the IP address in the network, managing IP space, planning and tracking is
needed. The IP address management is a tedious process and it is needed one. It takes longer
Page5

Telecommunications and Networks
spreadsheets to done this job perfectly. Address Commander is intended to identify the
exclusive IP address management requirements of service workers (Zhai and Liu, 2007).
The challenges in IP managements are
1. The DNS and DHCP management service costs reduction.
2. Provide the visibility of IP addresses spaces.
3. The tracing blocks between frequent enterprise clients and regional
arrangements.
4. Powerfully combining and organizing unusual IPv4 addresses.
5. Reducing IPAM faults that shake network consistency (Bader, 2012).
Benefits of Address commander
1. Enables the acceptance of IPv6.
2. Reduce costs connected to IP address management.
3. It is used to reduce the errors occurred at the address assignment process.
4. It is used to support service providers with redundancy and scalability.
5. Network Services
3. Networked services
3.1 VOIP
Voice over Internet Protocol is the abbreviation of VoIP. It allows the users, to create
calls by using Broadband Internet instead of using analog or conventional phone. It converts the
sound in the form of digital speech communication. To transfer the communication internet
Broadband is used. By using VOIP, one could make the call on the computer through the
internet. VoIP telephone is great for industries because it has field employees or employees
who travel a lot. Calls could be distracted to wherever in the domain. It is done by the cloud-
hosted VoIP handset features. The VoIP has some profits for several companies (Email overload
at work: an analysis of factors associated with email strain, 2010).
Page6
spreadsheets to done this job perfectly. Address Commander is intended to identify the
exclusive IP address management requirements of service workers (Zhai and Liu, 2007).
The challenges in IP managements are
1. The DNS and DHCP management service costs reduction.
2. Provide the visibility of IP addresses spaces.
3. The tracing blocks between frequent enterprise clients and regional
arrangements.
4. Powerfully combining and organizing unusual IPv4 addresses.
5. Reducing IPAM faults that shake network consistency (Bader, 2012).
Benefits of Address commander
1. Enables the acceptance of IPv6.
2. Reduce costs connected to IP address management.
3. It is used to reduce the errors occurred at the address assignment process.
4. It is used to support service providers with redundancy and scalability.
5. Network Services
3. Networked services
3.1 VOIP
Voice over Internet Protocol is the abbreviation of VoIP. It allows the users, to create
calls by using Broadband Internet instead of using analog or conventional phone. It converts the
sound in the form of digital speech communication. To transfer the communication internet
Broadband is used. By using VOIP, one could make the call on the computer through the
internet. VoIP telephone is great for industries because it has field employees or employees
who travel a lot. Calls could be distracted to wherever in the domain. It is done by the cloud-
hosted VoIP handset features. The VoIP has some profits for several companies (Email overload
at work: an analysis of factors associated with email strain, 2010).
Page6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Telecommunications and Networks
Benefits of VOIP
1. Cost is low.
2. Compactness
3. Rigidity
4. Multi-functional
3.2 WWW
WWW stands for World Wide Web. It is a place for recognizing the web sources and
documents via URLs. It is used for connecting more interconnected computers to the internet.
It has a collection of resources and documents. The internet resources are telnet, FTP,
Hypertext audio, video, and remote sites (Peer Review, 2013).
3.3 Web services
Web services are used to integrate the web-based applications. It is done by WSDL, SOAP,
UDDI and XML standards at IP backbone (Sinha and Kr. Isaac, 2015).
Benefits
1. Minimize equipment costs for innovative product growth.
2. Offered to all individuals and organization.
3. Cost is low, so smaller suppliers and partners could be incorporated.
4. It provides the remote access for the business.so it increases the offsite customers also.
3.4 Email
Email stands for Electronic mail. Email services provide access to the user to send, review and
store the messages via internet, from anywhere by their login (IEEE Cloud Computing, 2013).
Benefits of Email services
1. It is very fast to provide the information.
2. It is the convenient one.
3. It stores the files or documents permanently.
Page7
Benefits of VOIP
1. Cost is low.
2. Compactness
3. Rigidity
4. Multi-functional
3.2 WWW
WWW stands for World Wide Web. It is a place for recognizing the web sources and
documents via URLs. It is used for connecting more interconnected computers to the internet.
It has a collection of resources and documents. The internet resources are telnet, FTP,
Hypertext audio, video, and remote sites (Peer Review, 2013).
3.3 Web services
Web services are used to integrate the web-based applications. It is done by WSDL, SOAP,
UDDI and XML standards at IP backbone (Sinha and Kr. Isaac, 2015).
Benefits
1. Minimize equipment costs for innovative product growth.
2. Offered to all individuals and organization.
3. Cost is low, so smaller suppliers and partners could be incorporated.
4. It provides the remote access for the business.so it increases the offsite customers also.
3.4 Email
Email stands for Electronic mail. Email services provide access to the user to send, review and
store the messages via internet, from anywhere by their login (IEEE Cloud Computing, 2013).
Benefits of Email services
1. It is very fast to provide the information.
2. It is the convenient one.
3. It stores the files or documents permanently.
Page7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Telecommunications and Networks
4. The cost is low.
4. Data Processing Facilities
4.1 Data storage solution
The data center usage is presently undertaking a change because of the growing usage
of 'cloud' organization, applications and facilities. In Intel’s experiments, main in measured
environment and then in creation data center, SSD arrays transported the following advantages
through equivalent enterprise-class CD based loading up to 5x performance rise on the random
disk input/output tasks; minimized read/write latency and reduced the greater latency; quicker
transition from idle to run state and no rise in seek time as enterprise capacity is advanced.
Fewer intervals in patching systems; capacity and performance to handle workloads; and an
easy setup than a traditional NAS or SAN solution (Gharavi and Hu, 2017).
According to CEO of RTW Hosting, Mike Wills, substituting a traditional NAS or SAN with a
hybrid collection like X-IO's can transport 15-20 times the performance, along with a 60 %
development in power efficiency. Wherever an improved balance of reading/write presentation
and storage capacity is necessary, the tiered hybrid method could be the way to move. For
most the businesses, the way to the cloud initiates in an on-premise data center, which typically
executes a combination of siloes, traditional, virtualized 'private cloud' and enterprise
applications workloads. The latter are frequently founded on VMware's exclusive VCloud
technology (Kochel, Ladd and Rudolph, 2012).
4.2 Data processing model
P2P (peer to Peer)
Page8
4. The cost is low.
4. Data Processing Facilities
4.1 Data storage solution
The data center usage is presently undertaking a change because of the growing usage
of 'cloud' organization, applications and facilities. In Intel’s experiments, main in measured
environment and then in creation data center, SSD arrays transported the following advantages
through equivalent enterprise-class CD based loading up to 5x performance rise on the random
disk input/output tasks; minimized read/write latency and reduced the greater latency; quicker
transition from idle to run state and no rise in seek time as enterprise capacity is advanced.
Fewer intervals in patching systems; capacity and performance to handle workloads; and an
easy setup than a traditional NAS or SAN solution (Gharavi and Hu, 2017).
According to CEO of RTW Hosting, Mike Wills, substituting a traditional NAS or SAN with a
hybrid collection like X-IO's can transport 15-20 times the performance, along with a 60 %
development in power efficiency. Wherever an improved balance of reading/write presentation
and storage capacity is necessary, the tiered hybrid method could be the way to move. For
most the businesses, the way to the cloud initiates in an on-premise data center, which typically
executes a combination of siloes, traditional, virtualized 'private cloud' and enterprise
applications workloads. The latter are frequently founded on VMware's exclusive VCloud
technology (Kochel, Ladd and Rudolph, 2012).
4.2 Data processing model
P2P (peer to Peer)
Page8

Telecommunications and Networks
Each computer and devices present in the peer to peer network is called as the peer. Each
peer has equal rights. It is used for sharing the bandwidth of the network, processor usage and
disk storage between peers. It is scalable. The addition of new peer to this network is easy. If
any peer in the network is shut down, the other peer in the network continues the process of
that peer.
C/S (Client/Server)
Servers are used to managing Network traffic, drivers and printers. Clients are used to
running applications. If the client and server are placed on one computer, that is known as
single seat setup. Clients depend on the servers for resources (devices, files and processing
power) (Weiß, 2015).
5. Recommendations
1. It is recommended that the core network infrastructure should be maintained and
increased.
2. Performance improvement and proactive monitoring should be recommended for the
present network infrastructure.
3. It is suggested that the system documentation should be created and maintained.
4. It is recommended that the present WAN optimization technology should be maintained
and enhanced.
5. The excellent knowledge on security, framework, features and network architecture should
be recommended.
6. The economic contribution and social value that is communicated to the local council,
funders, general public and local business should be demonstrated.
7. Be ensure that the required skills to focus resources, construct strong relationships,
navigate change efficiently and demonstrate the social value.
8. It is recommended that, should be working with independent funders to invest in social
activities.
9. It is suggested that should be working with socially active groups like across regional and
local areas, collective voice possesses effects while influencing decisions.
Page9
Each computer and devices present in the peer to peer network is called as the peer. Each
peer has equal rights. It is used for sharing the bandwidth of the network, processor usage and
disk storage between peers. It is scalable. The addition of new peer to this network is easy. If
any peer in the network is shut down, the other peer in the network continues the process of
that peer.
C/S (Client/Server)
Servers are used to managing Network traffic, drivers and printers. Clients are used to
running applications. If the client and server are placed on one computer, that is known as
single seat setup. Clients depend on the servers for resources (devices, files and processing
power) (Weiß, 2015).
5. Recommendations
1. It is recommended that the core network infrastructure should be maintained and
increased.
2. Performance improvement and proactive monitoring should be recommended for the
present network infrastructure.
3. It is suggested that the system documentation should be created and maintained.
4. It is recommended that the present WAN optimization technology should be maintained
and enhanced.
5. The excellent knowledge on security, framework, features and network architecture should
be recommended.
6. The economic contribution and social value that is communicated to the local council,
funders, general public and local business should be demonstrated.
7. Be ensure that the required skills to focus resources, construct strong relationships,
navigate change efficiently and demonstrate the social value.
8. It is recommended that, should be working with independent funders to invest in social
activities.
9. It is suggested that should be working with socially active groups like across regional and
local areas, collective voice possesses effects while influencing decisions.
Page9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





