American Military University: Social Engineering and Security Report
VerifiedAdded on 2022/11/29
|14
|3056
|412
Report
AI Summary
This report delves into the critical domain of social engineering within telecommunications and network security, highlighting its significance as a major concern in the information technology field. It dissects the core concept of social engineering, defining it as the manipulation of individuals to divulge confidential information, and explores the various stages involved in its execution, including information gathering, attack planning, tool acquisition, attack deployment, and knowledge utilization. The report then provides detailed analyses of common social engineering attacks, such as shoulder surfing, phishing, baiting, and scareware, outlining their methodologies and potential impacts. For each type of attack, the report offers practical and actionable prevention strategies, including awareness of surroundings, secure password practices, cautious email handling, and the use of updated security measures like pop-up blockers. The report aims to provide a comprehensive understanding of social engineering threats and equips readers with knowledge to mitigate risks.

Running head: TELECOMMUNICATIONS AND NETWORK SECURITY
Telecommunications and Network Security
[Name of the Student]
[Name of the University]
[Author note]
Telecommunications and Network Security
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1TELECOMMUNICATIONS AND NETWORK SECURITY
Table of Contents
Introduction:....................................................................................................................................2
Discussion:.......................................................................................................................................2
Social engineering working process:...........................................................................................2
Social engineering Attacks:.........................................................................................................4
Social Surf:..............................................................................................................................4
Ways of preventing Shoulder Surfing:....................................................................................4
Phishing:..................................................................................................................................5
Prevention of Phishing:............................................................................................................6
Baiting:....................................................................................................................................7
Prevention of Baiting:..............................................................................................................8
Scareware:................................................................................................................................8
Prevention of Sareware:...........................................................................................................9
References:....................................................................................................................................10
Table of Contents
Introduction:....................................................................................................................................2
Discussion:.......................................................................................................................................2
Social engineering working process:...........................................................................................2
Social engineering Attacks:.........................................................................................................4
Social Surf:..............................................................................................................................4
Ways of preventing Shoulder Surfing:....................................................................................4
Phishing:..................................................................................................................................5
Prevention of Phishing:............................................................................................................6
Baiting:....................................................................................................................................7
Prevention of Baiting:..............................................................................................................8
Scareware:................................................................................................................................8
Prevention of Sareware:...........................................................................................................9
References:....................................................................................................................................10

2TELECOMMUNICATIONS AND NETWORK SECURITY
Introduction:
Social Engineering is generally considered to be process of manipulating peoples for
giving up of their confidential information. The information, which these type of criminal seeks
is seen to be varying however whenever a criminal are associated with targeting an individual,
they generally indulge themselves in tricking the victims in giving away their passwords or any
kind of account related information or might also provide the access of their computers so as to
make the criminals become capable of secretly installing the malicious software (Krombholz et
al., 2015). This malicious software in turn would be associated with providing a full access of the
computer to the criminal or the password or any kind of bank related information enabling them
in having full control of the victim’s computers.
Social engineering tactics is used by the criminals mainly because it can be conducted
easily helping them in exploiting the natural inclination to trust rather than finding of ways to
hack into the software which is a complicated process (Heartfield & Loukas, 2016). The
criminals easily manipulates the users of the computing systems making them revel the
confidential information which is then utilized by the criminals for gaining an access which is
entirely unauthorized to the computer systems.
Discussion:
Social engineering working process:
The working process of social engineering can be categorized into different stages and the stages
have been described below:
Introduction:
Social Engineering is generally considered to be process of manipulating peoples for
giving up of their confidential information. The information, which these type of criminal seeks
is seen to be varying however whenever a criminal are associated with targeting an individual,
they generally indulge themselves in tricking the victims in giving away their passwords or any
kind of account related information or might also provide the access of their computers so as to
make the criminals become capable of secretly installing the malicious software (Krombholz et
al., 2015). This malicious software in turn would be associated with providing a full access of the
computer to the criminal or the password or any kind of bank related information enabling them
in having full control of the victim’s computers.
Social engineering tactics is used by the criminals mainly because it can be conducted
easily helping them in exploiting the natural inclination to trust rather than finding of ways to
hack into the software which is a complicated process (Heartfield & Loukas, 2016). The
criminals easily manipulates the users of the computing systems making them revel the
confidential information which is then utilized by the criminals for gaining an access which is
entirely unauthorized to the computer systems.
Discussion:
Social engineering working process:
The working process of social engineering can be categorized into different stages and the stages
have been described below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3TELECOMMUNICATIONS AND NETWORK SECURITY
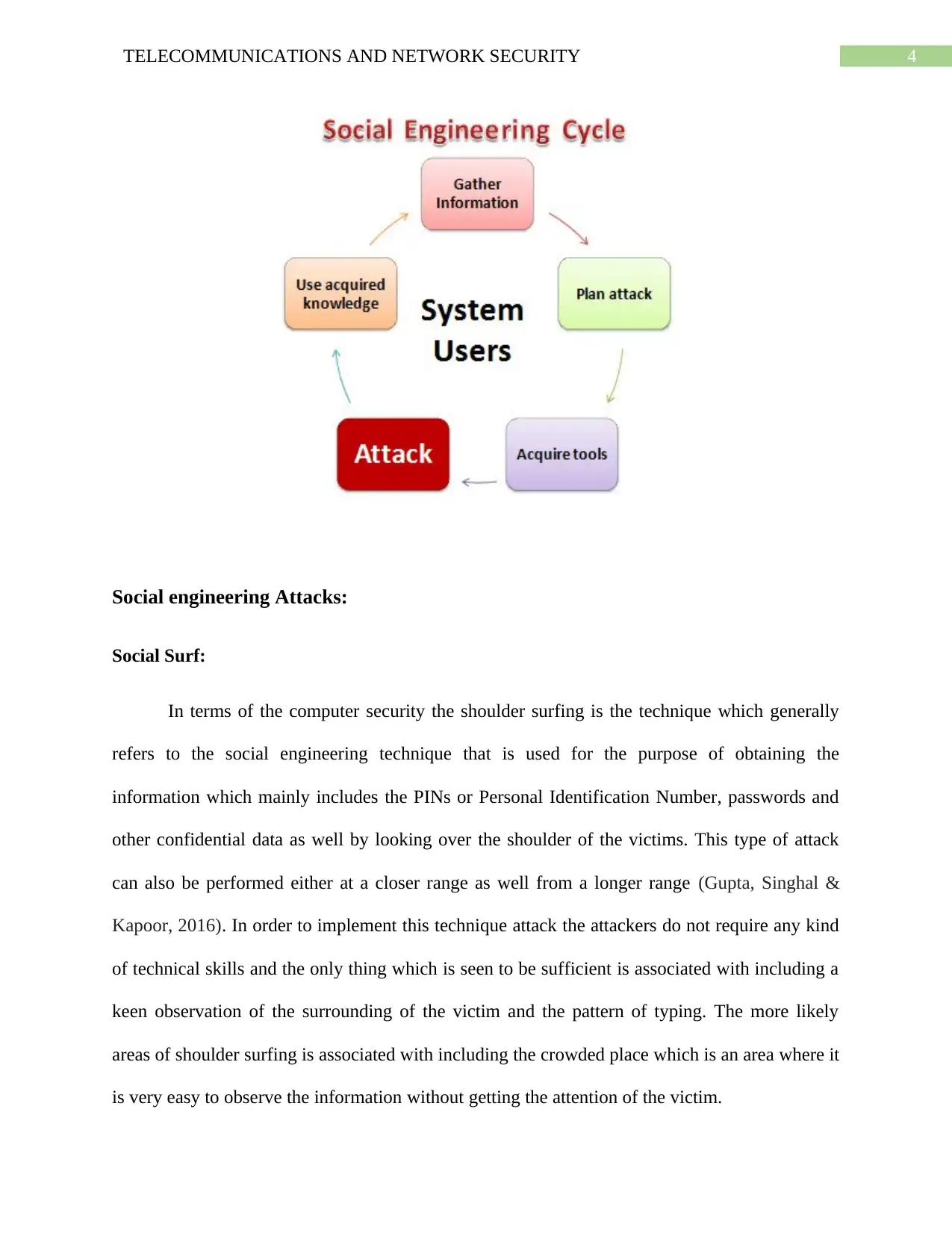
Gathering Information: This is considered to be the first stage and in this process the criminal
learns as much as they can about the victim which they have intended to attack. The information
is generally seen to be gathered from the company websites as well as from other publications
and also sometimes by means of having a conversation with the users of the system which has
been targeted.
Planning an Attack: This is the second stage in which the attacker is associated with making an
outline of the attacking process which they intends to execute for conducting the attack.
Acquiring tools: These is mainly associated with including the computer programs which is to
be used by the attacker so as to launch the entire attack.
Attack: This is the stage in which the exploitation of the weaknesses of the targeted system is
done (Shi et al., 2019).
Usage of the Acquired Knowledge: The information which are gathered at the time of social
engineering tactics like the pet names or birthdates of the organization and many more is
generally seen to be used in the attacks like the guessing of the passwords.
Gathering Information: This is considered to be the first stage and in this process the criminal
learns as much as they can about the victim which they have intended to attack. The information
is generally seen to be gathered from the company websites as well as from other publications
and also sometimes by means of having a conversation with the users of the system which has
been targeted.
Planning an Attack: This is the second stage in which the attacker is associated with making an
outline of the attacking process which they intends to execute for conducting the attack.
Acquiring tools: These is mainly associated with including the computer programs which is to
be used by the attacker so as to launch the entire attack.
Attack: This is the stage in which the exploitation of the weaknesses of the targeted system is
done (Shi et al., 2019).
Usage of the Acquired Knowledge: The information which are gathered at the time of social
engineering tactics like the pet names or birthdates of the organization and many more is
generally seen to be used in the attacks like the guessing of the passwords.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4TELECOMMUNICATIONS AND NETWORK SECURITY
Social engineering Attacks:
Social Surf:
In terms of the computer security the shoulder surfing is the technique which generally
refers to the social engineering technique that is used for the purpose of obtaining the
information which mainly includes the PINs or Personal Identification Number, passwords and
other confidential data as well by looking over the shoulder of the victims. This type of attack
can also be performed either at a closer range as well from a longer range (Gupta, Singhal &
Kapoor, 2016). In order to implement this technique attack the attackers do not require any kind
of technical skills and the only thing which is seen to be sufficient is associated with including a
keen observation of the surrounding of the victim and the pattern of typing. The more likely
areas of shoulder surfing is associated with including the crowded place which is an area where it
is very easy to observe the information without getting the attention of the victim.
Social engineering Attacks:
Social Surf:
In terms of the computer security the shoulder surfing is the technique which generally
refers to the social engineering technique that is used for the purpose of obtaining the
information which mainly includes the PINs or Personal Identification Number, passwords and
other confidential data as well by looking over the shoulder of the victims. This type of attack
can also be performed either at a closer range as well from a longer range (Gupta, Singhal &
Kapoor, 2016). In order to implement this technique attack the attackers do not require any kind
of technical skills and the only thing which is seen to be sufficient is associated with including a
keen observation of the surrounding of the victim and the pattern of typing. The more likely
areas of shoulder surfing is associated with including the crowded place which is an area where it
is very easy to observe the information without getting the attention of the victim.

5TELECOMMUNICATIONS AND NETWORK SECURITY
Ways of preventing Shoulder Surfing:
Shoulder Surfer is associate with prowling the borders of the personal space and the main
goal is associated with including being noticed without being noticed. Some of the ways by
which this can be prevented includes the following:
Users must be aware of the surrounding by means of watching if there is any kind of people
or recording device around them.
By sitting with the back towards a wall in the public places while being associated with
entering personal or financial information in the computer or in mobile phones (Conteh &
Schmick, 2016). It is also recommended to use a VPN when financial transactions are being
conducted over a public Wi-Fi.
Shielding of the keypad is also recommended in the ATM whenever a PIN is to be entered.
It is essential to make sure that a string password is selected so as to make it hard for the
observer to guess what is being entered (Junger, Montoya & Overink, 2017).
A screen protector is to be attached upon the computers so as to make the screens obscure.
Locking the computer screen whenever the user leaves their desks at work.
Looking out for public place whenever there is a need of sharing any kind of financial
information over the phones.
Phishing:
Phishing attacks are considered to be the most common type of attack which is seen to be
associated with leveraging the social engineering techniques. In Phishing the attackers are
associated with the usage of the emails, instant messaging and social media along with SMS for
the purpose of tricking the victims in providing of sensitive information or for making them visit
Ways of preventing Shoulder Surfing:
Shoulder Surfer is associate with prowling the borders of the personal space and the main
goal is associated with including being noticed without being noticed. Some of the ways by
which this can be prevented includes the following:
Users must be aware of the surrounding by means of watching if there is any kind of people
or recording device around them.
By sitting with the back towards a wall in the public places while being associated with
entering personal or financial information in the computer or in mobile phones (Conteh &
Schmick, 2016). It is also recommended to use a VPN when financial transactions are being
conducted over a public Wi-Fi.
Shielding of the keypad is also recommended in the ATM whenever a PIN is to be entered.
It is essential to make sure that a string password is selected so as to make it hard for the
observer to guess what is being entered (Junger, Montoya & Overink, 2017).
A screen protector is to be attached upon the computers so as to make the screens obscure.
Locking the computer screen whenever the user leaves their desks at work.
Looking out for public place whenever there is a need of sharing any kind of financial
information over the phones.
Phishing:
Phishing attacks are considered to be the most common type of attack which is seen to be
associated with leveraging the social engineering techniques. In Phishing the attackers are
associated with the usage of the emails, instant messaging and social media along with SMS for
the purpose of tricking the victims in providing of sensitive information or for making them visit
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6TELECOMMUNICATIONS AND NETWORK SECURITY
malicious URL so as make attempts in making their systems get compromised (Mann, 2017).In
phishing attacks the messages are composed in such a manner that they gain the attention of the
users and many cases this messages are composed for the purpose of stimulating their curiosity
by means of providing them with few information related to a specific topic and by suggesting
the victims to visit certain websites so as to gain further information.
The main aim of the phishing message is to gather the information which is presented by
the users with a sense of urgency so as to make attempts in tricking the victims for disclosing
their sensitive data for the purpose of resolving the situations which would get worse without any
kind of interaction with the victim (Nelms et al., 2016). Additionally the attackers are also
associated with leveraging the shortened URL or embedded links so as to redirect the victims to
a domain malicious in nature which is capable of hosting exploited codes or which might be
acting as a clone of a legitimate website by means of having URL which appears to be legitimate
in nature. The phishing email messages are seen to be having a subject line which is deceptive
and is aimed at enticing the recipients in believing that the email has come from the source
which is a trusted one(Heartfield, Loukas & Gan, 2016). Attackers are associated with a forged
address of the sender or a spoofed identity of an organization and are generally associated with
copying the contents such as the texts, logos, and many more which are seen to be used in the
legitimate websites so as to make the forged website look genuine.
Prevention of Phishing:
There exists numerous way which can be undertaken so as to avoid the risks related to phishing
and this includes the following:
malicious URL so as make attempts in making their systems get compromised (Mann, 2017).In
phishing attacks the messages are composed in such a manner that they gain the attention of the
users and many cases this messages are composed for the purpose of stimulating their curiosity
by means of providing them with few information related to a specific topic and by suggesting
the victims to visit certain websites so as to gain further information.
The main aim of the phishing message is to gather the information which is presented by
the users with a sense of urgency so as to make attempts in tricking the victims for disclosing
their sensitive data for the purpose of resolving the situations which would get worse without any
kind of interaction with the victim (Nelms et al., 2016). Additionally the attackers are also
associated with leveraging the shortened URL or embedded links so as to redirect the victims to
a domain malicious in nature which is capable of hosting exploited codes or which might be
acting as a clone of a legitimate website by means of having URL which appears to be legitimate
in nature. The phishing email messages are seen to be having a subject line which is deceptive
and is aimed at enticing the recipients in believing that the email has come from the source
which is a trusted one(Heartfield, Loukas & Gan, 2016). Attackers are associated with a forged
address of the sender or a spoofed identity of an organization and are generally associated with
copying the contents such as the texts, logos, and many more which are seen to be used in the
legitimate websites so as to make the forged website look genuine.
Prevention of Phishing:
There exists numerous way which can be undertaken so as to avoid the risks related to phishing
and this includes the following:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7TELECOMMUNICATIONS AND NETWORK SECURITY
Always checking the spelling of the URLs provided in the emails links before it is opened or
before entering any kind of sensitive information(Mouton, Leenen & Venter, 2016).
Watching out for the redirects of the URL which might be including the sending of the user
to a different website which is seen to be having an identical design
In case if an email is received from a particular source which is already known to the user but
is seen to be suspicious then it is essential to contact that source by means of a new email
instead of just clicking on the reply option(Bhakta & Harris, 2015).
Personal data must not be posted such as the date of birth or plan of vacation or any other
details such as the address or personal number publically in different social media sites.
Some of the other measures which are to be adopted by the IT security department of an
organization so as to make them themselves proactive in protecting their data have been listed
below:
Sandboxing of the inbound emails, which is associated with including the checking of the
safety of each of the link a user clicks.
Inspection and analysis of the traffic present in the web
Pen testing of the organization so as to look out and identify the weak spots followed by the
usage of the results so as to educate the employees of the organization.
Providing of rewards for any kind of good behaviour perhaps by means of showcasing
rewards such as “catch of the day”, whenever someone spots a phishing email.
Baiting:
Baiting in many way can be considered to be similar to the phishing attacks but still the
thing which is associated with distinguishing them from the other type of social engineering is
Always checking the spelling of the URLs provided in the emails links before it is opened or
before entering any kind of sensitive information(Mouton, Leenen & Venter, 2016).
Watching out for the redirects of the URL which might be including the sending of the user
to a different website which is seen to be having an identical design
In case if an email is received from a particular source which is already known to the user but
is seen to be suspicious then it is essential to contact that source by means of a new email
instead of just clicking on the reply option(Bhakta & Harris, 2015).
Personal data must not be posted such as the date of birth or plan of vacation or any other
details such as the address or personal number publically in different social media sites.
Some of the other measures which are to be adopted by the IT security department of an
organization so as to make them themselves proactive in protecting their data have been listed
below:
Sandboxing of the inbound emails, which is associated with including the checking of the
safety of each of the link a user clicks.
Inspection and analysis of the traffic present in the web
Pen testing of the organization so as to look out and identify the weak spots followed by the
usage of the results so as to educate the employees of the organization.
Providing of rewards for any kind of good behaviour perhaps by means of showcasing
rewards such as “catch of the day”, whenever someone spots a phishing email.
Baiting:
Baiting in many way can be considered to be similar to the phishing attacks but still the
thing which is associated with distinguishing them from the other type of social engineering is

8TELECOMMUNICATIONS AND NETWORK SECURITY
the promise of an item or good which are used by the hackers for the purpose of enticing the
victims, baiters might be associated with offering the users with a free music or movie
downloads and in case if the victims surrender their login credentials to a particular site
(Marczak & Paxson, 2017). Baiting attacks are generally not restricted to the online schemes.
Baiting can be considered to be a real world Trojan horse which is associated with the usage of
the physical media and is dependent upon the curiosity or greed of the targeted user (Ghafir et
al., 2016). This type of attack is associated with leaving of a malware-infected floppy disk, CD
ROMs or USB Flash drives by the attacker in locations where people would find them, which in
turn provides the attacker a legitimate curiosity piquing labels and they wait till the victims takes
the bait.
Prevention of Baiting:
One of the strongest defence against the baiting is associated with including the educating
the users. There is also a need of having an aim of keeping a strong security culture within the
office surroundings(Abramov & Azarov, 2016). Additionally each and every individual should
necessarily be associated with taking into consideration the security as an essential part of the
individual responsibility. Specifically in case of baiting each and every individual should
necessarily be associated with conducting open discussions.
Scareware:
Scareware is considered to be a type of malware which is designed for the purpose of
tricking the victims into purchasing and downloading of the useless software which are also seen
to be potentially dangerous. Scareware which are seen to be associated with the generation of the
pop-ups which resembles the Windows system messages are usually associated with purports to
the promise of an item or good which are used by the hackers for the purpose of enticing the
victims, baiters might be associated with offering the users with a free music or movie
downloads and in case if the victims surrender their login credentials to a particular site
(Marczak & Paxson, 2017). Baiting attacks are generally not restricted to the online schemes.
Baiting can be considered to be a real world Trojan horse which is associated with the usage of
the physical media and is dependent upon the curiosity or greed of the targeted user (Ghafir et
al., 2016). This type of attack is associated with leaving of a malware-infected floppy disk, CD
ROMs or USB Flash drives by the attacker in locations where people would find them, which in
turn provides the attacker a legitimate curiosity piquing labels and they wait till the victims takes
the bait.
Prevention of Baiting:
One of the strongest defence against the baiting is associated with including the educating
the users. There is also a need of having an aim of keeping a strong security culture within the
office surroundings(Abramov & Azarov, 2016). Additionally each and every individual should
necessarily be associated with taking into consideration the security as an essential part of the
individual responsibility. Specifically in case of baiting each and every individual should
necessarily be associated with conducting open discussions.
Scareware:
Scareware is considered to be a type of malware which is designed for the purpose of
tricking the victims into purchasing and downloading of the useless software which are also seen
to be potentially dangerous. Scareware which are seen to be associated with the generation of the
pop-ups which resembles the Windows system messages are usually associated with purports to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9TELECOMMUNICATIONS AND NETWORK SECURITY
be antivirus or anti-spyware software a firewall application or a registry cleaner(Nicholson,
Coventry & Briggs, 2017). The message is typically associated with saying a large number of
problems like the infected files which have been found on the computers and the user is
prompted with a message of purchasing the software so as fix the problem. However in reality
there is no problem which were detected and the software which is purchased might be actually
containing the malware (Edwards et al., 2017). In case if a user falls for this type of scam then
the user would lose all the money paid for purchasing the software which is completely useless
and this software might also make the computer unusable.
Prevention of Sareware:
Usage of updated browsers irrespective of the type of browser that is used. The only thing which
would matter is the browser is kept updated.
Pop-up blocker should be kept on. Which means if a user does not get pop-ups then the user
would not get scareware.
In case if a pop-up is received then it is advised to shut down the browser completely. In case
if it is seen that the pop-up is not allowing the user to close the browser the Alt-Ctrl-Delete
function should be used for shutting down the window.
An anti-virus program should always be used and should necessarily be kept updated.
It is recommended not to click on any of the links which are present in a webpage and shows
the message “warning” that there is a virus(Butavicius et al., 2016). The only thing which is
to be done in this type of situation is close the browser and scan the entire computer for virus.
Any kind of personal information should be provided in any kind of pop-up and it is also
recommended not to click on any of the label which shows “download” or something similar
to it from a suspicious page or site.
be antivirus or anti-spyware software a firewall application or a registry cleaner(Nicholson,
Coventry & Briggs, 2017). The message is typically associated with saying a large number of
problems like the infected files which have been found on the computers and the user is
prompted with a message of purchasing the software so as fix the problem. However in reality
there is no problem which were detected and the software which is purchased might be actually
containing the malware (Edwards et al., 2017). In case if a user falls for this type of scam then
the user would lose all the money paid for purchasing the software which is completely useless
and this software might also make the computer unusable.
Prevention of Sareware:
Usage of updated browsers irrespective of the type of browser that is used. The only thing which
would matter is the browser is kept updated.
Pop-up blocker should be kept on. Which means if a user does not get pop-ups then the user
would not get scareware.
In case if a pop-up is received then it is advised to shut down the browser completely. In case
if it is seen that the pop-up is not allowing the user to close the browser the Alt-Ctrl-Delete
function should be used for shutting down the window.
An anti-virus program should always be used and should necessarily be kept updated.
It is recommended not to click on any of the links which are present in a webpage and shows
the message “warning” that there is a virus(Butavicius et al., 2016). The only thing which is
to be done in this type of situation is close the browser and scan the entire computer for virus.
Any kind of personal information should be provided in any kind of pop-up and it is also
recommended not to click on any of the label which shows “download” or something similar
to it from a suspicious page or site.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10TELECOMMUNICATIONS AND NETWORK SECURITY

11TELECOMMUNICATIONS AND NETWORK SECURITY
References:
Abramov, M. V., & Azarov, A. A. (2016, May). Social engineering attack modeling with the use
of Bayesian networks. In 2016 XIX IEEE International Conference on Soft Computing
and Measurements (SCM) (pp. 58-60). IEEE.
Bhakta, R., & Harris, I. G. (2015, February). Semantic analysis of dialogs to detect social
engineering attacks. In Proceedings of the 2015 IEEE 9th International Conference on
Semantic Computing (IEEE ICSC 2015) (pp. 424-427). IEEE.
Butavicius, M., Parsons, K., Pattinson, M., & McCormac, A. (2016). Breaching the human
firewall: Social engineering in phishing and spear-phishing emails. arXiv preprint
arXiv:1606.00887.
Conteh, N. Y., & Schmick, P. J. (2016). Cybersecurity: risks, vulnerabilities and
countermeasures to prevent social engineering attacks. International Journal of
Advanced Computer Research, 6(23), 31.
Edwards, M., Larson, R., Green, B., Rashid, A., & Baron, A. (2017). Panning for gold:
automatically analysing online social engineering attack surfaces. Computers &
Security, 69, 18-34.
Ghafir, I., Prenosil, V., Alhejailan, A., & Hammoudeh, M. (2016, August). Social engineering
attack strategies and defence approaches. In 2016 IEEE 4th International Conference on
Future Internet of Things and Cloud (FiCloud) (pp. 145-149). IEEE.
References:
Abramov, M. V., & Azarov, A. A. (2016, May). Social engineering attack modeling with the use
of Bayesian networks. In 2016 XIX IEEE International Conference on Soft Computing
and Measurements (SCM) (pp. 58-60). IEEE.
Bhakta, R., & Harris, I. G. (2015, February). Semantic analysis of dialogs to detect social
engineering attacks. In Proceedings of the 2015 IEEE 9th International Conference on
Semantic Computing (IEEE ICSC 2015) (pp. 424-427). IEEE.
Butavicius, M., Parsons, K., Pattinson, M., & McCormac, A. (2016). Breaching the human
firewall: Social engineering in phishing and spear-phishing emails. arXiv preprint
arXiv:1606.00887.
Conteh, N. Y., & Schmick, P. J. (2016). Cybersecurity: risks, vulnerabilities and
countermeasures to prevent social engineering attacks. International Journal of
Advanced Computer Research, 6(23), 31.
Edwards, M., Larson, R., Green, B., Rashid, A., & Baron, A. (2017). Panning for gold:
automatically analysing online social engineering attack surfaces. Computers &
Security, 69, 18-34.
Ghafir, I., Prenosil, V., Alhejailan, A., & Hammoudeh, M. (2016, August). Social engineering
attack strategies and defence approaches. In 2016 IEEE 4th International Conference on
Future Internet of Things and Cloud (FiCloud) (pp. 145-149). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





