Analysis of IS Security and Risk Management: A Telstra Case Study
VerifiedAdded on 2023/03/20
|15
|3667
|42
Case Study
AI Summary
This assignment presents a comprehensive case study on Telstra's information system (IS) security and risk management. It begins with an introduction to Telstra's role as a telecommunications service provider and highlights the importance of information security. The discussion section analyzes the threats and vulnerabilities associated with network devices such as routers and switches, including improper configuration and potential denial-of-service attacks. It then explores mitigation techniques, emphasizing the use of firewalls and intrusion detection systems (IDS) to secure the network. The case study also examines the role of Windows Server 2016 in providing secure web services and discusses the impact of employees on information security, emphasizing the need for training and awareness to prevent cyberattacks. Additionally, it provides recommendations for risk management, including employee training and the use of backup devices. The assignment covers various aspects of IS security, including network security, employee training, and risk management strategies, providing valuable insights into real-world security challenges and solutions.

Running Head: ANALYSIS OF IS SECURITY AND RISK MANAGEMENT IN TELSTRA
ANALYSIS OF IS SECURITY AND RISK MANAGEMENT IN TELSTRA
Name of the Student
Name of the University
Author Note
ANALYSIS OF IS SECURITY AND RISK MANAGEMENT IN TELSTRA
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Company and product selection.............................................................................................2
Evolution of IS/IT strategy.....................................................................................................4
Major challenges facing business...........................................................................................5
Recent scenario of IS/IT for organization..............................................................................6
Role of IS/IT in contemporary environment..........................................................................6
Management IS for managing and controlling organization system.....................................7
Execution of IS/IT strategy should be presented...................................................................9
Conclusion................................................................................................................................10
References................................................................................................................................11
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Company and product selection.............................................................................................2
Evolution of IS/IT strategy.....................................................................................................4
Major challenges facing business...........................................................................................5
Recent scenario of IS/IT for organization..............................................................................6
Role of IS/IT in contemporary environment..........................................................................6
Management IS for managing and controlling organization system.....................................7
Execution of IS/IT strategy should be presented...................................................................9
Conclusion................................................................................................................................10
References................................................................................................................................11

2
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Introduction
The information system services that are provided by an organization help it to increase the
business and also facilitate the business processes within the organization. Telstra is an
organization that is the one of the leading carrier of the telecommunication service provider.
The organization allow wide range of facilities to the customers an d the staffs that are related
to the information security. There is a huge range of the use of the network devices within the
organization which includes routers and the switches which increases the threat of the cyber
attack within the organization. The installation of the security devices can minimize threat of
the cyber-attacks within the organization. Most of the cyber attacks are done using the
malicious contents spreading with the websites and the email chains which can affect the data
of the organization. The organization can use the Windows 2016 severs for hosting its
website that is a secure way. There can be several impacts of the employees on the
information security of the selected organization and the risk can be reduced with the use of
proper risk management strategies. Windows server 2016 have different tools for the purpose
of auditing that will be used for monitoring the web servers and the mail servers within the
organization. The organization Telstra deals with many servers to continue with its activities
and thus face several threat from the cyber-attacks. Thus it can implement the Windows
server 2016 and proper employee training to minimize such risk and vulnerabilities (Ishikawa
and Sakurai 2017).
Discussion
Threat and vulnerabilities of the network devices
There are several risk that comes with the network device like routers and switch.
The routers and the switches are used in large scale within the organization. They are the
most important network devices within the organization. The threat that are associated with
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Introduction
The information system services that are provided by an organization help it to increase the
business and also facilitate the business processes within the organization. Telstra is an
organization that is the one of the leading carrier of the telecommunication service provider.
The organization allow wide range of facilities to the customers an d the staffs that are related
to the information security. There is a huge range of the use of the network devices within the
organization which includes routers and the switches which increases the threat of the cyber
attack within the organization. The installation of the security devices can minimize threat of
the cyber-attacks within the organization. Most of the cyber attacks are done using the
malicious contents spreading with the websites and the email chains which can affect the data
of the organization. The organization can use the Windows 2016 severs for hosting its
website that is a secure way. There can be several impacts of the employees on the
information security of the selected organization and the risk can be reduced with the use of
proper risk management strategies. Windows server 2016 have different tools for the purpose
of auditing that will be used for monitoring the web servers and the mail servers within the
organization. The organization Telstra deals with many servers to continue with its activities
and thus face several threat from the cyber-attacks. Thus it can implement the Windows
server 2016 and proper employee training to minimize such risk and vulnerabilities (Ishikawa
and Sakurai 2017).
Discussion
Threat and vulnerabilities of the network devices
There are several risk that comes with the network device like routers and switch.
The routers and the switches are used in large scale within the organization. They are the
most important network devices within the organization. The threat that are associated with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
router and the switch is the wrong configuration of the these devices (Huq 2016). The
placement of these devices in the proper network topology is important to ensure the security
that is meant to be there. The wrong placement allows the attackers to get an attacking
surface. If the router is explosive to the interface of the internet or any illicit network this
increases the vulnerability If the attacker get the access of the routing or the switch devices
that can enables the denial of services within the systems of the organization (Engqvist and
Mori Soto 2017). If the servers of the organization are accessible then the network devices
cannot be compromised. The authentication step that need to be performed with these
network devices also increases the threats. If a local account is used by the router and the
switches the threat increases as the local account cannot be locked and the same account can
be used by a variety of peoples. If the attackers get the access to these devices these will
increase the vulnerabilities to the cyber attacks (Szewczyk and Macdonald 2017). The data of
the organization can be hacked that can be huge loss to the organization. The attackers can
keep the electronics data of the organization as hostage and can demand money for giving
back the data access. The organization can suffer huge loss due to these threats and
vulnerabilities.
Devices that will ensure mitigation of these Threats
The network security devices increases the security of using these network devices thus
minimizing the threats and vulnerabilities that are associated with it. The use of proper
network security device can help in diminishing the risk. The two network security devices
are as follows:-
1. Firewall:- These network security device help in isolating one network device from
the other. The firewalls can be installed in the router or the switches to reduce the risk.
There is an availability of the software and the hardware appliances can be used to
separate the different types of networks within the organization (Pathan 2016). These
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
router and the switch is the wrong configuration of the these devices (Huq 2016). The
placement of these devices in the proper network topology is important to ensure the security
that is meant to be there. The wrong placement allows the attackers to get an attacking
surface. If the router is explosive to the interface of the internet or any illicit network this
increases the vulnerability If the attacker get the access of the routing or the switch devices
that can enables the denial of services within the systems of the organization (Engqvist and
Mori Soto 2017). If the servers of the organization are accessible then the network devices
cannot be compromised. The authentication step that need to be performed with these
network devices also increases the threats. If a local account is used by the router and the
switches the threat increases as the local account cannot be locked and the same account can
be used by a variety of peoples. If the attackers get the access to these devices these will
increase the vulnerabilities to the cyber attacks (Szewczyk and Macdonald 2017). The data of
the organization can be hacked that can be huge loss to the organization. The attackers can
keep the electronics data of the organization as hostage and can demand money for giving
back the data access. The organization can suffer huge loss due to these threats and
vulnerabilities.
Devices that will ensure mitigation of these Threats
The network security devices increases the security of using these network devices thus
minimizing the threats and vulnerabilities that are associated with it. The use of proper
network security device can help in diminishing the risk. The two network security devices
are as follows:-
1. Firewall:- These network security device help in isolating one network device from
the other. The firewalls can be installed in the router or the switches to reduce the risk.
There is an availability of the software and the hardware appliances can be used to
separate the different types of networks within the organization (Pathan 2016). These
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
also eliminate the traffic within the network that also reduces the risk. Therefore the
unwanted or the malicious traffic can be filter out before it enter the network of the
organization. Depending on the firewall policy that verify the traffic that is entering
the network which enables the security (Raj, Bharti and Thakur 2015). The two
firewall policies that are used includes whitelisting which allow the firewall to do not
give entry to the traffic that is unacceptable and eliminating them. And the other
policy is the Blacklisting that allow the entry of all the network except that are
unacceptable. There are mainly four types of the firewall that includes firewalls for
the filtering of the packets, stateful filtering of packets, proxy firewalls and the web
application firewalls (AlHogail 2015). All these are the different types of filtering that
filters the packets that are available. The filtering of the packets that are done on the
basis of the IP address of the incoming packets , IP address of the destination, the
protocols of the internet that is contained within the packets (Puthal et al, 2016).
2. Intruding Web application firewalls:- This functions by identifying the malicious
activities and the cyber attacks that can take place within the network of the
organization (Kearns 2016). These also reduces the probability of the future attacks
within the organization.
These provides the Information system security management team of the organization
to identify their risk and the vulnerabilities (Khan et al 2017). The categories into
which intrusion detection system can be categorized are IDS systems that are based
on the hosts, Network based IDS, and a system that prevent intrusion. The wireless
intrusion system is also available that can minimize the risk by identifying the same.
The threats that comes from the malicious contents that comes from the emails can be
reduced. The illicit websites that are accessed also detected by this system (Chen,
Ramamurthy and Wen 2015).
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
also eliminate the traffic within the network that also reduces the risk. Therefore the
unwanted or the malicious traffic can be filter out before it enter the network of the
organization. Depending on the firewall policy that verify the traffic that is entering
the network which enables the security (Raj, Bharti and Thakur 2015). The two
firewall policies that are used includes whitelisting which allow the firewall to do not
give entry to the traffic that is unacceptable and eliminating them. And the other
policy is the Blacklisting that allow the entry of all the network except that are
unacceptable. There are mainly four types of the firewall that includes firewalls for
the filtering of the packets, stateful filtering of packets, proxy firewalls and the web
application firewalls (AlHogail 2015). All these are the different types of filtering that
filters the packets that are available. The filtering of the packets that are done on the
basis of the IP address of the incoming packets , IP address of the destination, the
protocols of the internet that is contained within the packets (Puthal et al, 2016).
2. Intruding Web application firewalls:- This functions by identifying the malicious
activities and the cyber attacks that can take place within the network of the
organization (Kearns 2016). These also reduces the probability of the future attacks
within the organization.
These provides the Information system security management team of the organization
to identify their risk and the vulnerabilities (Khan et al 2017). The categories into
which intrusion detection system can be categorized are IDS systems that are based
on the hosts, Network based IDS, and a system that prevent intrusion. The wireless
intrusion system is also available that can minimize the risk by identifying the same.
The threats that comes from the malicious contents that comes from the emails can be
reduced. The illicit websites that are accessed also detected by this system (Chen,
Ramamurthy and Wen 2015).

5
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Availability of web services using the Windows server 2016
The availability of the web services can be ensured by the organization by hosting its
website in Windows 2016 server. The system ensures several policies that will ensure that the
organization provides the important functionality of the web related services (Svidergol et al.
2018). There are different policies that are ensured by the different startup policies that can be
automatic, default and manual. These ensures that each activity is performed by choosing
proper balancing sheets, functionality and the security of the websites (Modi 2017). The
organization prefer ore secured server which will protect the surface from the attacks. The
server provide a guidance to the organization to decide that which specific service is needed
to be disabled so that security can be ensured. The each system within this server is
categorized as-
1. Should disable – An organization that focuses on the security prefer to disable the
service and will forgo its functionality.
2. Okay to disable services can be used by the organization but it bwill better to disable
the same as it do not ensure security totally.
3. Do not disable services are the important services and the functionality of those
services are important and hence it should not be disabled.
4. The services that have no guidance should not be changed as the impacts of the
functionality of these services is not evaluated (Patra, Naveen and Prabhakar 2016).
The features that are provided by the windows 2016 server includes the configuration of the
active directory federation service that authenticate the user that are not stored in the
directories. The window defender is enabled by default and is an installable feature of the
windows (Rubel and Venkatesh 2017). It also allow the remote desktop services and also
have the storage devices. It also authenticate the HTTP application that are publishing in the
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Availability of web services using the Windows server 2016
The availability of the web services can be ensured by the organization by hosting its
website in Windows 2016 server. The system ensures several policies that will ensure that the
organization provides the important functionality of the web related services (Svidergol et al.
2018). There are different policies that are ensured by the different startup policies that can be
automatic, default and manual. These ensures that each activity is performed by choosing
proper balancing sheets, functionality and the security of the websites (Modi 2017). The
organization prefer ore secured server which will protect the surface from the attacks. The
server provide a guidance to the organization to decide that which specific service is needed
to be disabled so that security can be ensured. The each system within this server is
categorized as-
1. Should disable – An organization that focuses on the security prefer to disable the
service and will forgo its functionality.
2. Okay to disable services can be used by the organization but it bwill better to disable
the same as it do not ensure security totally.
3. Do not disable services are the important services and the functionality of those
services are important and hence it should not be disabled.
4. The services that have no guidance should not be changed as the impacts of the
functionality of these services is not evaluated (Patra, Naveen and Prabhakar 2016).
The features that are provided by the windows 2016 server includes the configuration of the
active directory federation service that authenticate the user that are not stored in the
directories. The window defender is enabled by default and is an installable feature of the
windows (Rubel and Venkatesh 2017). It also allow the remote desktop services and also
have the storage devices. It also authenticate the HTTP application that are publishing in the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
website of the organization (Panek 2018). Thus it help the organization for hosting their
official website and thus provides security to the same.
Impact of the employees on the information security
The employees have an impact on the information security of the organization. The
activities that are intentional or mistakenly have an severe impact on the cyber security of the
organization. For example the creation of weak password or surfing the malicious email
contents can increase the cyber security risks of the organization. Giving proper training to
the employees to spread awareness among them about the cyber attacks is important so that
they do not use those illicit websites. The training that the employees get should enable them
to think proactively about the activities that they are undertaking (Posey, Roberts and Lowry
2015). The employee need to detect the threat of the cyber attack and be responsive enough
to fight against it. Some employees within the organization have a criminal mentality that can
also become dangerous because they have the information about the data within the
organization. They need to be informed enough about the phishing activities that are going
inside the organization. The employees are responsible enough about the phishing activities
within the organization (Soomro, Shah and Ahmed 2016). The employees need to encourage
the safe mailing experience and safe use of the internet.
Availability of web services using windows 2016
The availability of the web services can be ensured by the organization using
Windows server 2016. The server also ensures the availability of the monitoring services of
the internet and the intranet of the organization. These monitor the performance of the
organization. It also help in checking the availability of the webpages that are static and
dynamic. It monitor the internet with the help of the authenticated protocols that monitor the
resources for 24* 7. These also makes sure that the data of the organization is prevented
from the illegal activities or the malicious activities that are taking place within the websites.
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
website of the organization (Panek 2018). Thus it help the organization for hosting their
official website and thus provides security to the same.
Impact of the employees on the information security
The employees have an impact on the information security of the organization. The
activities that are intentional or mistakenly have an severe impact on the cyber security of the
organization. For example the creation of weak password or surfing the malicious email
contents can increase the cyber security risks of the organization. Giving proper training to
the employees to spread awareness among them about the cyber attacks is important so that
they do not use those illicit websites. The training that the employees get should enable them
to think proactively about the activities that they are undertaking (Posey, Roberts and Lowry
2015). The employee need to detect the threat of the cyber attack and be responsive enough
to fight against it. Some employees within the organization have a criminal mentality that can
also become dangerous because they have the information about the data within the
organization. They need to be informed enough about the phishing activities that are going
inside the organization. The employees are responsible enough about the phishing activities
within the organization (Soomro, Shah and Ahmed 2016). The employees need to encourage
the safe mailing experience and safe use of the internet.
Availability of web services using windows 2016
The availability of the web services can be ensured by the organization using
Windows server 2016. The server also ensures the availability of the monitoring services of
the internet and the intranet of the organization. These monitor the performance of the
organization. It also help in checking the availability of the webpages that are static and
dynamic. It monitor the internet with the help of the authenticated protocols that monitor the
resources for 24* 7. These also makes sure that the data of the organization is prevented
from the illegal activities or the malicious activities that are taking place within the websites.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
The business can avoid the breakdowns that provides scrutiny for ensuring the security. They
also provides a large hosting space for storing the information within the websites. Before
marking the website as unavailable there is 10 redirects. The 24 hours monitoring allows to
trouble shoot the downtime and also induce the metrics like recording of the errors and the
issues of the networks.
Risk management recommendation to reduce the risk of employee
The employees of the organization need to provide proper training to reduce the risk within
the organization. The employees need top be concerned about the malicious mails of the
websites. The employees need to be aware enough to detect the activities that will increase
the threat of the cyber attacks. The employees need to may also have the authority to report
such activities within the organization. If the organization train the employees about the
malicious chain of the email that have the ability to hack the systems of the organization they
can avoid opening such emails. The backup devices need to be present that can restore the
data in case an attack is taken place and the employees need to handle the devices efficiently.
The employees are mainly responsible to handle the cyber environment that persists within
the organization. The employees need to understand the threat that can arise within the
organization. The organization also need to do the recruitment more efficiently that can
reduce the risk to the organization that can be there if the employees have a criminal
mentality. The important or the vital data should not be provided to all the employees and it
need to be constrained only with the top management and executives of the organization. The
training that is provided need to be efficient enough to change the approach of the employees
of the organization towards the cyber security issues.
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
The business can avoid the breakdowns that provides scrutiny for ensuring the security. They
also provides a large hosting space for storing the information within the websites. Before
marking the website as unavailable there is 10 redirects. The 24 hours monitoring allows to
trouble shoot the downtime and also induce the metrics like recording of the errors and the
issues of the networks.
Risk management recommendation to reduce the risk of employee
The employees of the organization need to provide proper training to reduce the risk within
the organization. The employees need top be concerned about the malicious mails of the
websites. The employees need to be aware enough to detect the activities that will increase
the threat of the cyber attacks. The employees need to may also have the authority to report
such activities within the organization. If the organization train the employees about the
malicious chain of the email that have the ability to hack the systems of the organization they
can avoid opening such emails. The backup devices need to be present that can restore the
data in case an attack is taken place and the employees need to handle the devices efficiently.
The employees are mainly responsible to handle the cyber environment that persists within
the organization. The employees need to understand the threat that can arise within the
organization. The organization also need to do the recruitment more efficiently that can
reduce the risk to the organization that can be there if the employees have a criminal
mentality. The important or the vital data should not be provided to all the employees and it
need to be constrained only with the top management and executives of the organization. The
training that is provided need to be efficient enough to change the approach of the employees
of the organization towards the cyber security issues.

8
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Windows server 2016 supported with different tools for auditing
There are different tools that are present in the Windows 2016 server that includes the
following:-
Active directory Auditing and compliances:- It help the organization to compile with the
regulatory requirements of the organization. It provides the data that help in the security
auditing.
Auditing of the Windows files server.- These detects the authorized and unauthorized
documents access by the employees or any staffs of the organization. These also change in
the original structure of the files due to malicious contents (PONGSRISOMCHAI and
NGAMSURIYAROJ 2019).
Tracking of the actions of the user logins- It efficiently tracks the information about the
logons within the server of the organization and these help it to detect the logon on the
unusual time, These also record the login time that will help to detect the timestamp of the
attack. It also deals with determining the peak hours of the attack. Thus this help in effective
and efficient determination of the user logons.
Auditing of the management of the users- It keep the track of what users are performing
within the servers. It also provide the study of the changes that are taking place and thus help
in recognizing the malicious worms or illicit website opening within the network server of the
organization.
Scheduling of the change report of the active directory- It provides a web interface where the
reports of the event log data extraction is presented (Leitold et al. 2015).
Thus it help in auditing the activities within the server of the organization to identify the
malicious attack within the organization.
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Windows server 2016 supported with different tools for auditing
There are different tools that are present in the Windows 2016 server that includes the
following:-
Active directory Auditing and compliances:- It help the organization to compile with the
regulatory requirements of the organization. It provides the data that help in the security
auditing.
Auditing of the Windows files server.- These detects the authorized and unauthorized
documents access by the employees or any staffs of the organization. These also change in
the original structure of the files due to malicious contents (PONGSRISOMCHAI and
NGAMSURIYAROJ 2019).
Tracking of the actions of the user logins- It efficiently tracks the information about the
logons within the server of the organization and these help it to detect the logon on the
unusual time, These also record the login time that will help to detect the timestamp of the
attack. It also deals with determining the peak hours of the attack. Thus this help in effective
and efficient determination of the user logons.
Auditing of the management of the users- It keep the track of what users are performing
within the servers. It also provide the study of the changes that are taking place and thus help
in recognizing the malicious worms or illicit website opening within the network server of the
organization.
Scheduling of the change report of the active directory- It provides a web interface where the
reports of the event log data extraction is presented (Leitold et al. 2015).
Thus it help in auditing the activities within the server of the organization to identify the
malicious attack within the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Conclusion
It can be concluded from the above report that the information system also brings
several cyber security issues. The network devices that are present within an organization like
Telstra can make the organization more prone to the attacks. The cyber attackers get a way to
enter the network reach of the organization through the weak network devices. The study also
reflects the network security tools that can be undertaken the threat and the risks of the cyber
attacks that will take place within the organization. The network devices are very much
vulnerable to the attacks. The organization can also adapt the Windows server 2016v for
hosting the we site. Doing the same will help the organization to avoid the risk of the
malicious attack within the organization. The organization can also ensure availability of the
website throughout the day to its user using the Windows service 2016. The employees are
very responsible to detect and report the attack. The activities of the employees also affect the
cyber security hygiene of the organization. The risk management strategies need to be there
that will reduce the risk. Employee training is very essential to reduce such risks. There are
several tools for auditing that are available in the Windows server 2016 that will help the
organization to detect the problems in the web servers as well as in the email servers. Thus
we can conclude the organization can reduce the probability of an attack within the
organization by undertaking several approaches. The security of the organization data is very
important for the organization growth. Adapting certain steps will help the organization to
increase the growth of the organization. Thus it is very important for the organization to
implement the requirements that is needed to ensure the security within the organization to
protect the data of the organization so the it can carry with its activities without disruption
due to cyber attacks.
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Conclusion
It can be concluded from the above report that the information system also brings
several cyber security issues. The network devices that are present within an organization like
Telstra can make the organization more prone to the attacks. The cyber attackers get a way to
enter the network reach of the organization through the weak network devices. The study also
reflects the network security tools that can be undertaken the threat and the risks of the cyber
attacks that will take place within the organization. The network devices are very much
vulnerable to the attacks. The organization can also adapt the Windows server 2016v for
hosting the we site. Doing the same will help the organization to avoid the risk of the
malicious attack within the organization. The organization can also ensure availability of the
website throughout the day to its user using the Windows service 2016. The employees are
very responsible to detect and report the attack. The activities of the employees also affect the
cyber security hygiene of the organization. The risk management strategies need to be there
that will reduce the risk. Employee training is very essential to reduce such risks. There are
several tools for auditing that are available in the Windows server 2016 that will help the
organization to detect the problems in the web servers as well as in the email servers. Thus
we can conclude the organization can reduce the probability of an attack within the
organization by undertaking several approaches. The security of the organization data is very
important for the organization growth. Adapting certain steps will help the organization to
increase the growth of the organization. Thus it is very important for the organization to
implement the requirements that is needed to ensure the security within the organization to
protect the data of the organization so the it can carry with its activities without disruption
due to cyber attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
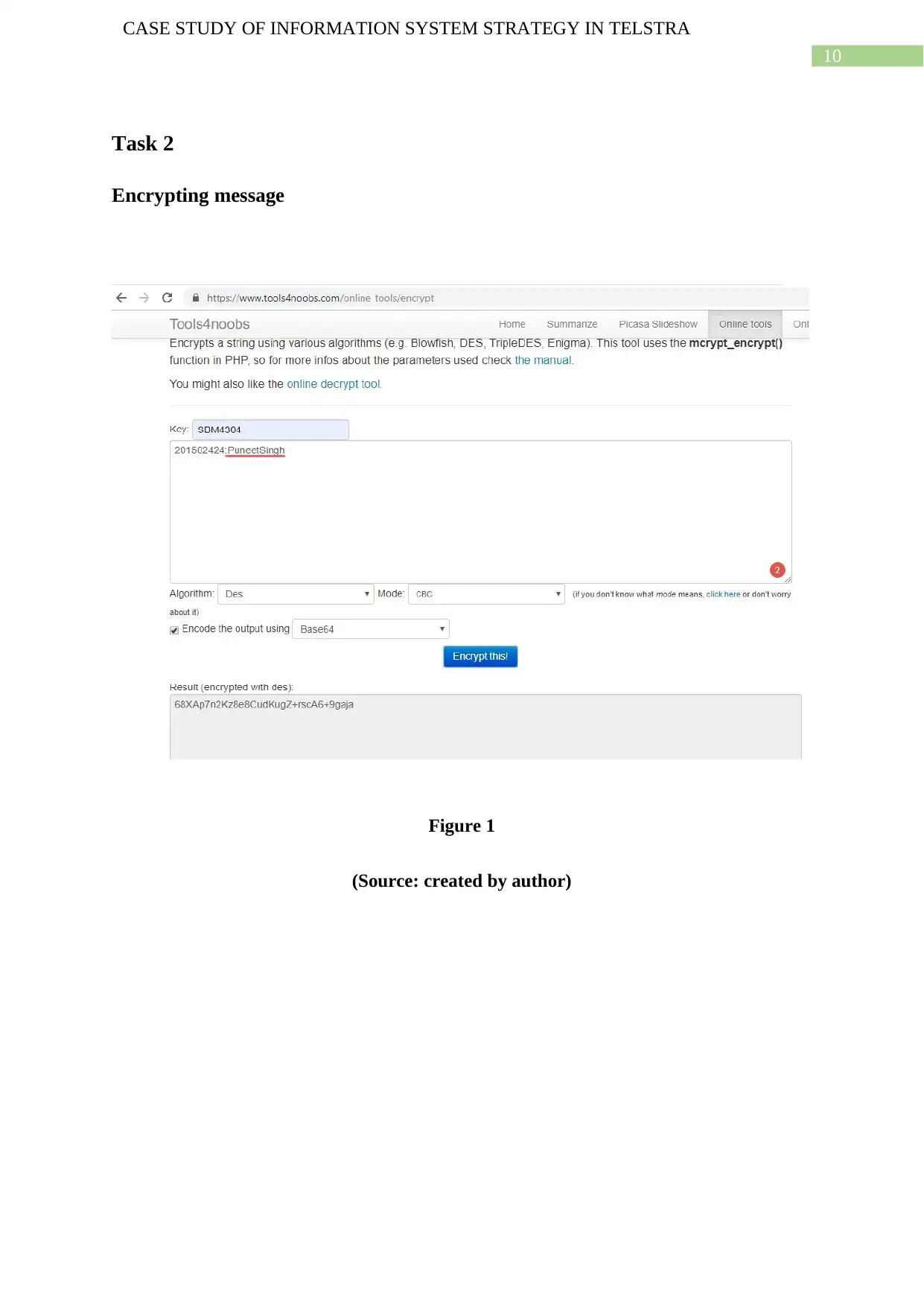
Task 2
Encrypting message
Figure 1
(Source: created by author)
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Task 2
Encrypting message
Figure 1
(Source: created by author)
11
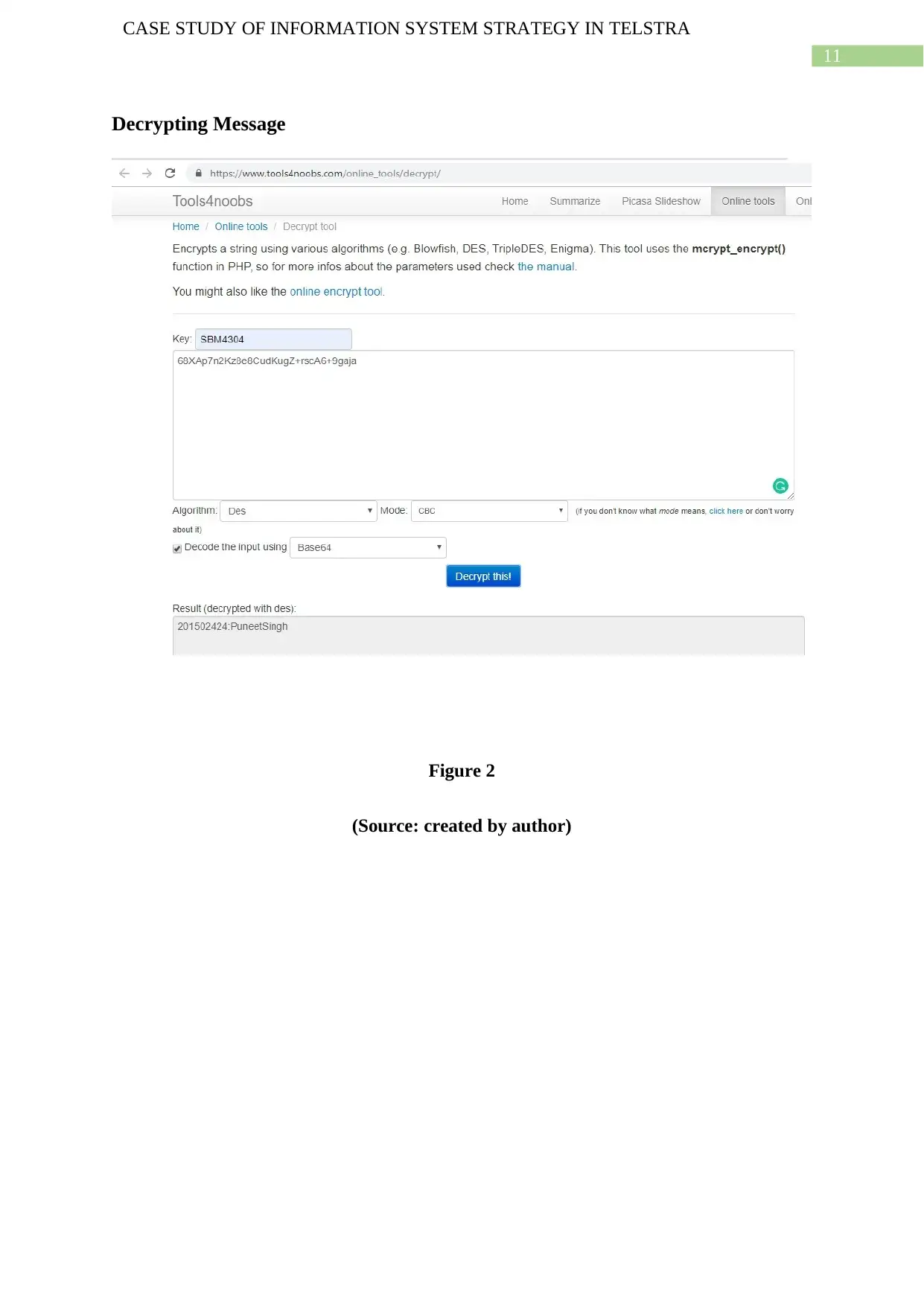
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Decrypting Message
Figure 2
(Source: created by author)
CASE STUDY OF INFORMATION SYSTEM STRATEGY IN TELSTRA
Decrypting Message
Figure 2
(Source: created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



