Comprehensive Report: IS Security and Risk Management at Telstra
VerifiedAdded on 2023/06/05
|17
|3798
|88
Report
AI Summary
This report provides a detailed analysis of Information System (IS) security and risk management at Telstra Corporation Ltd, a leading telecommunications company in Australia. It covers various aspects including the working mechanism of ransomware and mitigation tools, threats against network routers and switches, reliability and availability of Windows Server 2012 web service, ensuring confidentiality and integrity for staff emails, prioritization of threats and malware for web servers and webmail, approaches for improving email server availability, the impact of employees on information security, log records for monitoring web server and email issues, audit log reports, and network security devices for controlling threats. The report emphasizes the importance of security audits, controls, and business continuity planning for maintaining a robust and secure IS environment within Telstra.

Running head: IS SECURITY AND RISK MANAGEMENT
IS Security and Risk Management: Telstra Corporation Ltd
Name of the Student
Name of the University
Author’s Note:
IS Security and Risk Management: Telstra Corporation Ltd
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IS SECURITY AND RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
1. Working Mechanism of Ransomware with Three Tools for Mitigating Ransomware......2
2. Three Types of Threats against Network Routers and Switches.......................................4
3. Reliability and Availability of Windows Server 2012 Web Service.................................4
4. Ensuring Confidentiality and Integrity for the Staff Emails..............................................5
5. Discussion and Prioritization of Threats and Malware for Web Server and Web Mail....6
6. Two Approaches for Improving Availability of Email Server..........................................7
7. Impact of Employees on Information Security and Risk Management.............................9
8. Illustration of Log Records for Monitoring or Analyzing Web Server and Email Issues. 9
9. Audit Log Reports useful for Audit Analysis and Log Term Problems..........................10
10. Five Types of Network Security Devices for Controlling and Mitigating Threats........11
Conclusion................................................................................................................................12
References................................................................................................................................14
IS SECURITY AND RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
1. Working Mechanism of Ransomware with Three Tools for Mitigating Ransomware......2
2. Three Types of Threats against Network Routers and Switches.......................................4
3. Reliability and Availability of Windows Server 2012 Web Service.................................4
4. Ensuring Confidentiality and Integrity for the Staff Emails..............................................5
5. Discussion and Prioritization of Threats and Malware for Web Server and Web Mail....6
6. Two Approaches for Improving Availability of Email Server..........................................7
7. Impact of Employees on Information Security and Risk Management.............................9
8. Illustration of Log Records for Monitoring or Analyzing Web Server and Email Issues. 9
9. Audit Log Reports useful for Audit Analysis and Log Term Problems..........................10
10. Five Types of Network Security Devices for Controlling and Mitigating Threats........11
Conclusion................................................................................................................................12
References................................................................................................................................14

2
IS SECURITY AND RISK MANAGEMENT
Introduction
Information system is the organized structure, which is useful for assembling,
systemizing, corresponding and finally accumulating any type of sensitive information
(Marchewka, 2014). It is fully automated and thus is used by not taking any manual help of
the working procedure. The information system also consists of the fully computer based
database and thus comprises of the restricted sensors, helping to store information easily and
promptly (Oztaysi, 2014). Decision making process is also enhanced by this system and the
overall time consumption for any data operation is quite less in comparison to other systems.
This report gives a details description on risk or security management for one of the
most famous and important telecommunications company of Australia, called, Telstra
Corporation Ltd. Telstra helps its customers by providing several services of broadband and
telecommunications. Furthermore, they also provide services of information system to the
employees. This report will also describe the security audits, controls and business continuity
planning of Telstra with proper details.
Discussion
1. Working Mechanism of Ransomware with Three Tools for Mitigating Ransomware
Ransomware attack occurs when the victim’s data is being hacked by encryption
mechanism. The working procedure of this attack is extremely simple (Schwalbe, 2015). This
malware utilizes symmetric encryption for recovering the private as well as undistributed data
for decrypting the sensitive data of the victim and hence enhancing vulnerabilities. The most
popular ransomware attacks that have taken place are CryptoLocker and WannaCry.
IS SECURITY AND RISK MANAGEMENT
Introduction
Information system is the organized structure, which is useful for assembling,
systemizing, corresponding and finally accumulating any type of sensitive information
(Marchewka, 2014). It is fully automated and thus is used by not taking any manual help of
the working procedure. The information system also consists of the fully computer based
database and thus comprises of the restricted sensors, helping to store information easily and
promptly (Oztaysi, 2014). Decision making process is also enhanced by this system and the
overall time consumption for any data operation is quite less in comparison to other systems.
This report gives a details description on risk or security management for one of the
most famous and important telecommunications company of Australia, called, Telstra
Corporation Ltd. Telstra helps its customers by providing several services of broadband and
telecommunications. Furthermore, they also provide services of information system to the
employees. This report will also describe the security audits, controls and business continuity
planning of Telstra with proper details.
Discussion
1. Working Mechanism of Ransomware with Three Tools for Mitigating Ransomware
Ransomware attack occurs when the victim’s data is being hacked by encryption
mechanism. The working procedure of this attack is extremely simple (Schwalbe, 2015). This
malware utilizes symmetric encryption for recovering the private as well as undistributed data
for decrypting the sensitive data of the victim and hence enhancing vulnerabilities. The most
popular ransomware attacks that have taken place are CryptoLocker and WannaCry.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
IS SECURITY AND RISK MANAGEMENT
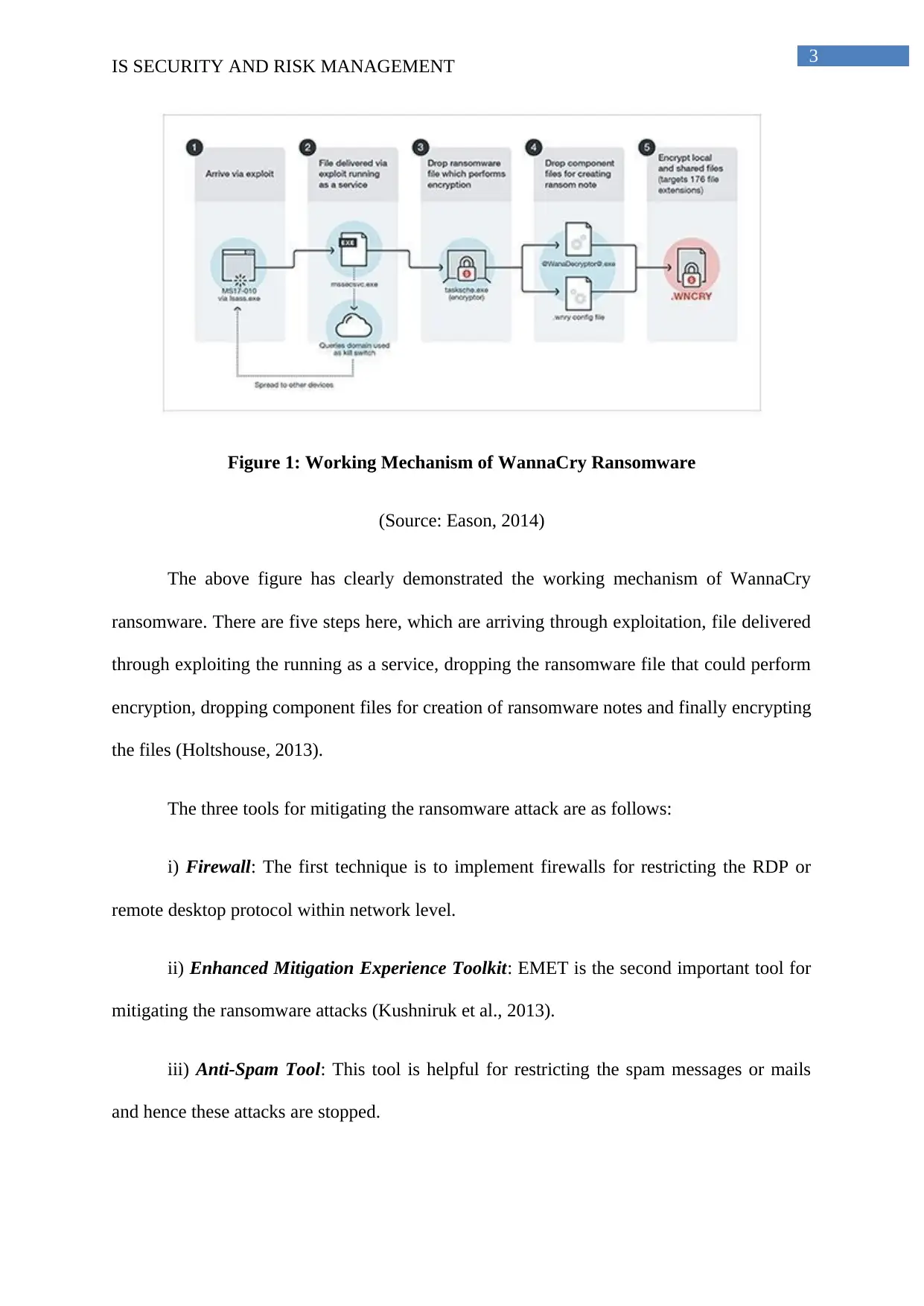
Figure 1: Working Mechanism of WannaCry Ransomware
(Source: Eason, 2014)
The above figure has clearly demonstrated the working mechanism of WannaCry
ransomware. There are five steps here, which are arriving through exploitation, file delivered
through exploiting the running as a service, dropping the ransomware file that could perform
encryption, dropping component files for creation of ransomware notes and finally encrypting
the files (Holtshouse, 2013).
The three tools for mitigating the ransomware attack are as follows:
i) Firewall: The first technique is to implement firewalls for restricting the RDP or
remote desktop protocol within network level.
ii) Enhanced Mitigation Experience Toolkit: EMET is the second important tool for
mitigating the ransomware attacks (Kushniruk et al., 2013).
iii) Anti-Spam Tool: This tool is helpful for restricting the spam messages or mails
and hence these attacks are stopped.
IS SECURITY AND RISK MANAGEMENT
Figure 1: Working Mechanism of WannaCry Ransomware
(Source: Eason, 2014)
The above figure has clearly demonstrated the working mechanism of WannaCry
ransomware. There are five steps here, which are arriving through exploitation, file delivered
through exploiting the running as a service, dropping the ransomware file that could perform
encryption, dropping component files for creation of ransomware notes and finally encrypting
the files (Holtshouse, 2013).
The three tools for mitigating the ransomware attack are as follows:
i) Firewall: The first technique is to implement firewalls for restricting the RDP or
remote desktop protocol within network level.
ii) Enhanced Mitigation Experience Toolkit: EMET is the second important tool for
mitigating the ransomware attacks (Kushniruk et al., 2013).
iii) Anti-Spam Tool: This tool is helpful for restricting the spam messages or mails
and hence these attacks are stopped.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IS SECURITY AND RISK MANAGEMENT
2. Three Types of Threats against Network Routers and Switches
The organization of Telstra Corporation Ltd gives several services of IS for their
employees (Telstra. 2018). The significant exploitations of these services are possible by few
attacks. The most important and noteworthy devices for securing the network are listed
below:
i) Router: This device helps in forwarding the various data packets within computer
network (Laudon & Laudon, 2016). It also performs traffic functionalities and the packets are
then eventually forwarded from any one particular router to the next router. All of the routers
are connected with each and every data line with various networks.
ii) Modem: This particular network security device helps in modulating the carrier
wave signal to properly encode the digitalized information and then demodulate and transmit
the signal.
iii) Ethernet Hub: This Ethernet hub is helpful for connecting to various Ethernet
devices and thus the devices could work as one specific segment of network (Bilbao-Osorio,
Dutta & Lanvin, 2013).
The lack of firewalls or antivirus software is the major cause of vulnerability to abuse
as well as destructions.
3. Reliability and Availability of Windows Server 2012 Web Service
Telstra Corporation Limited is utilizing Windows Server 2012 for appropriately host
the website. The various important requirements that are to be met for these web servers are
reliability and availability (Bloom et al., 2014). The reliability could be stated as the major
ability to use the computerized software and hardware. Thus, reliability is majorly maintained
IS SECURITY AND RISK MANAGEMENT
2. Three Types of Threats against Network Routers and Switches
The organization of Telstra Corporation Ltd gives several services of IS for their
employees (Telstra. 2018). The significant exploitations of these services are possible by few
attacks. The most important and noteworthy devices for securing the network are listed
below:
i) Router: This device helps in forwarding the various data packets within computer
network (Laudon & Laudon, 2016). It also performs traffic functionalities and the packets are
then eventually forwarded from any one particular router to the next router. All of the routers
are connected with each and every data line with various networks.
ii) Modem: This particular network security device helps in modulating the carrier
wave signal to properly encode the digitalized information and then demodulate and transmit
the signal.
iii) Ethernet Hub: This Ethernet hub is helpful for connecting to various Ethernet
devices and thus the devices could work as one specific segment of network (Bilbao-Osorio,
Dutta & Lanvin, 2013).
The lack of firewalls or antivirus software is the major cause of vulnerability to abuse
as well as destructions.
3. Reliability and Availability of Windows Server 2012 Web Service
Telstra Corporation Limited is utilizing Windows Server 2012 for appropriately host
the website. The various important requirements that are to be met for these web servers are
reliability and availability (Bloom et al., 2014). The reliability could be stated as the major
ability to use the computerized software and hardware. Thus, reliability is majorly maintained

5
IS SECURITY AND RISK MANAGEMENT
within this web service. The major factors, which help in determining the reliability factors in
Telstra’s web server, are given below:
i) Continuity in the Internet connectivity.
ii) Proper maintenance of the hardware for maintaining the stability of Windows
Server 2012.
iii) Stability of Hosting Facility (Brooks, 2016).
The next factor of availability is even more important for Windows Server 2012.
i) Continuity in web server availability.
ii) Periodical maintenance of Windows Server 2012.
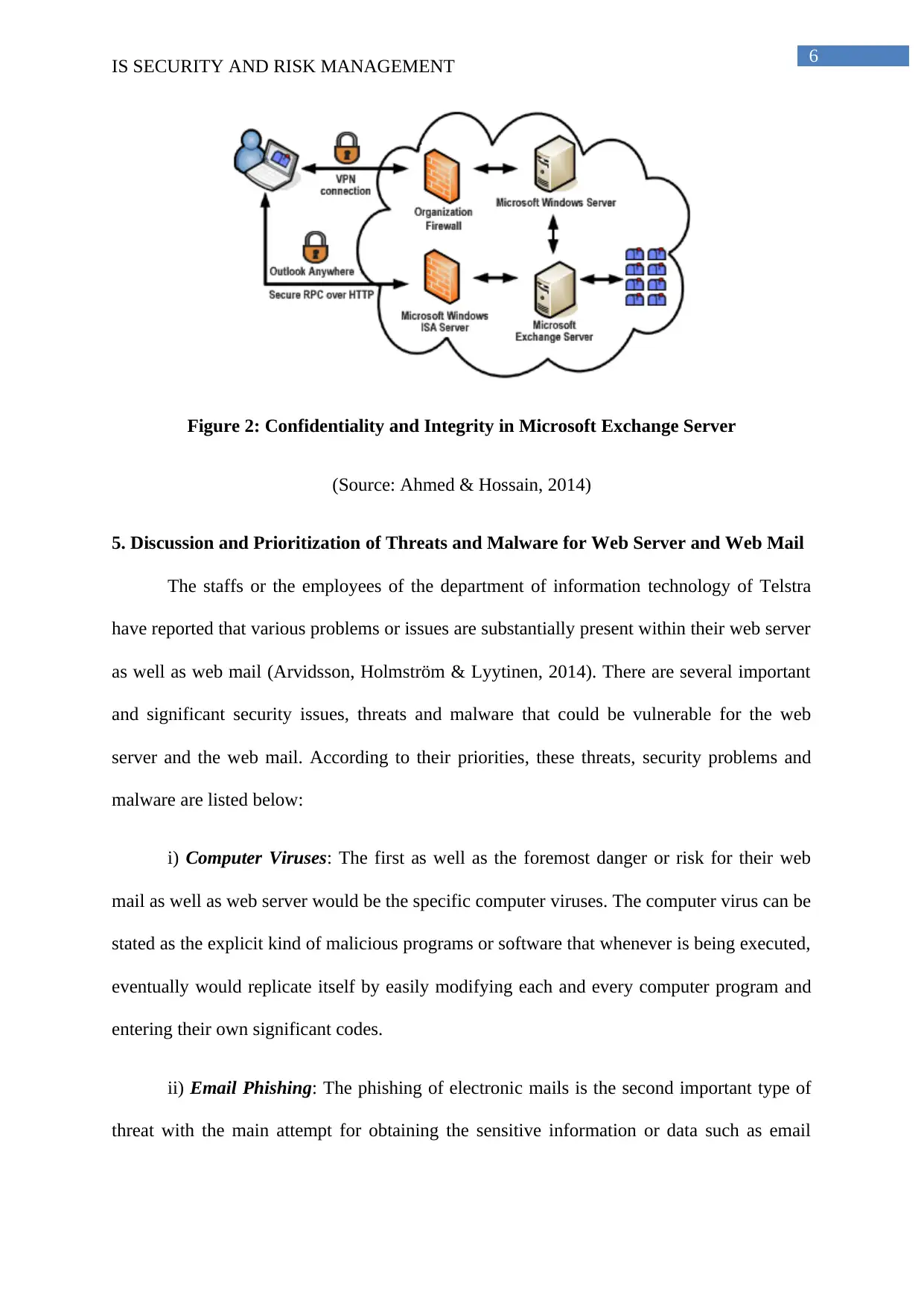
4. Ensuring Confidentiality and Integrity for the Staff Emails
Telstra is subsequently utilizing the Microsoft Exchange Servers for the major
purpose to provide various email services for their staffs (Dahlstrom, Walker & Dziuban,
2013). This particular server is extremely effective and efficient for all companies. The
respective OS of the Microsoft Exchange Server is called the Windows Server and there are
multiple versions of this server. This organization ensures confidentiality and integrity by few
major factors. This confidentiality and integrity are maintained by ensuring that only the
authenticated and authorized users are accessing all emails (Tarhini, Arachchilage & Abbasi,
2015). The other important method for maintaining the authenticity of the emails is
encryption. This particular technique of encryption hides or encodes the confidential data or
information to a cipher text and it becomes impossible for the hacker to guess the original
message.
IS SECURITY AND RISK MANAGEMENT
within this web service. The major factors, which help in determining the reliability factors in
Telstra’s web server, are given below:
i) Continuity in the Internet connectivity.
ii) Proper maintenance of the hardware for maintaining the stability of Windows
Server 2012.
iii) Stability of Hosting Facility (Brooks, 2016).
The next factor of availability is even more important for Windows Server 2012.
i) Continuity in web server availability.
ii) Periodical maintenance of Windows Server 2012.
4. Ensuring Confidentiality and Integrity for the Staff Emails
Telstra is subsequently utilizing the Microsoft Exchange Servers for the major
purpose to provide various email services for their staffs (Dahlstrom, Walker & Dziuban,
2013). This particular server is extremely effective and efficient for all companies. The
respective OS of the Microsoft Exchange Server is called the Windows Server and there are
multiple versions of this server. This organization ensures confidentiality and integrity by few
major factors. This confidentiality and integrity are maintained by ensuring that only the
authenticated and authorized users are accessing all emails (Tarhini, Arachchilage & Abbasi,
2015). The other important method for maintaining the authenticity of the emails is
encryption. This particular technique of encryption hides or encodes the confidential data or
information to a cipher text and it becomes impossible for the hacker to guess the original
message.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IS SECURITY AND RISK MANAGEMENT
Figure 2: Confidentiality and Integrity in Microsoft Exchange Server
(Source: Ahmed & Hossain, 2014)
5. Discussion and Prioritization of Threats and Malware for Web Server and Web Mail
The staffs or the employees of the department of information technology of Telstra
have reported that various problems or issues are substantially present within their web server
as well as web mail (Arvidsson, Holmström & Lyytinen, 2014). There are several important
and significant security issues, threats and malware that could be vulnerable for the web
server and the web mail. According to their priorities, these threats, security problems and
malware are listed below:
i) Computer Viruses: The first as well as the foremost danger or risk for their web
mail as well as web server would be the specific computer viruses. The computer virus can be
stated as the explicit kind of malicious programs or software that whenever is being executed,
eventually would replicate itself by easily modifying each and every computer program and
entering their own significant codes.
ii) Email Phishing: The phishing of electronic mails is the second important type of
threat with the main attempt for obtaining the sensitive information or data such as email
IS SECURITY AND RISK MANAGEMENT
Figure 2: Confidentiality and Integrity in Microsoft Exchange Server
(Source: Ahmed & Hossain, 2014)
5. Discussion and Prioritization of Threats and Malware for Web Server and Web Mail
The staffs or the employees of the department of information technology of Telstra
have reported that various problems or issues are substantially present within their web server
as well as web mail (Arvidsson, Holmström & Lyytinen, 2014). There are several important
and significant security issues, threats and malware that could be vulnerable for the web
server and the web mail. According to their priorities, these threats, security problems and
malware are listed below:
i) Computer Viruses: The first as well as the foremost danger or risk for their web
mail as well as web server would be the specific computer viruses. The computer virus can be
stated as the explicit kind of malicious programs or software that whenever is being executed,
eventually would replicate itself by easily modifying each and every computer program and
entering their own significant codes.
ii) Email Phishing: The phishing of electronic mails is the second important type of
threat with the main attempt for obtaining the sensitive information or data such as email
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IS SECURITY AND RISK MANAGEMENT
details, usernames or passwords only when the attacker disguises himself as one of the most
trustworthy entities (Cheminod, Durante & Valenzano, 2013).
iii) Electronic Mail Spoofing: The third important threat or malware according to the
priority of threat is the electronic mail spoofing. In this attack, the hacker sends mails by
creating a fake email address. As soon as the user clicks on that mail, the authenticity is being
lost eventually.
6. Two Approaches for Improving Availability of Email Server
The respective business continuity planning of the entire department of this IT or
information technology can be made sure by simply providing major fault tolerances and
redundancies (Crossler et al., 2013). The typical email server is available for this organization
of Telstra Corporation Limited and is quite effective for the staffs of this company. However,
often a significant issue arises when this email server is unavailable for the employees and
thus these employees face several issues due to this unavailability. For the purpose of
improving this availability of the email server in Telstra organization, two approaches could
be helpful. These two approaches are listed below:
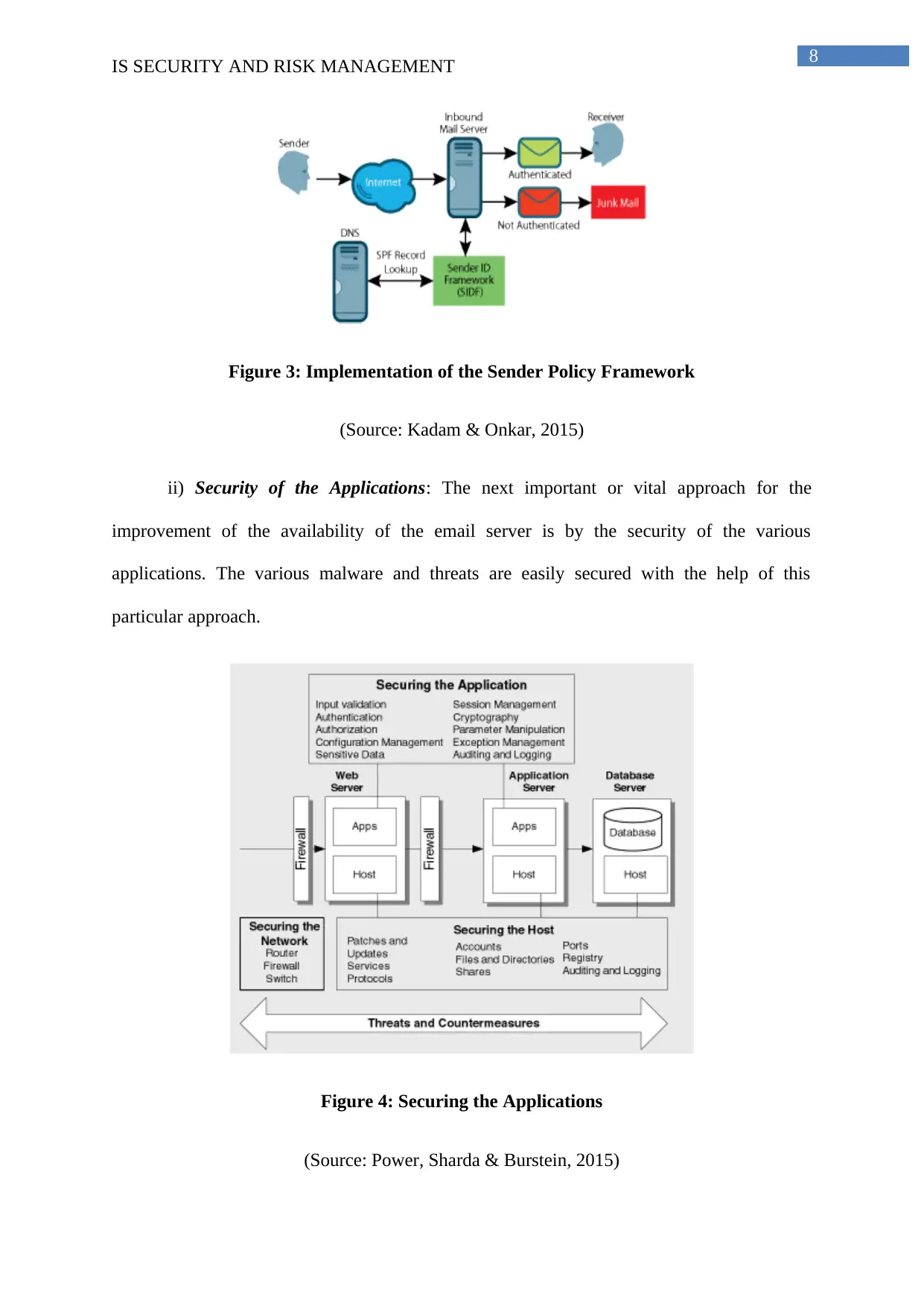
a) Implementation of the Sender Policy Framework or SPF: The first important
approach for improving the availability of the email server in Telstra organization is by
simply implementing the SPF or the sender policy framework (Gallagher & Sixsmith, 2014).
The specific SIDF or the sender identity framework is subsequently present within this sender
policy framework to maintain the authorization and authenticity of their email server. Hence,
the previously existing issue of unavailability of the email server in Telstra is easily being
resolved.
IS SECURITY AND RISK MANAGEMENT
details, usernames or passwords only when the attacker disguises himself as one of the most
trustworthy entities (Cheminod, Durante & Valenzano, 2013).
iii) Electronic Mail Spoofing: The third important threat or malware according to the
priority of threat is the electronic mail spoofing. In this attack, the hacker sends mails by
creating a fake email address. As soon as the user clicks on that mail, the authenticity is being
lost eventually.
6. Two Approaches for Improving Availability of Email Server
The respective business continuity planning of the entire department of this IT or
information technology can be made sure by simply providing major fault tolerances and
redundancies (Crossler et al., 2013). The typical email server is available for this organization
of Telstra Corporation Limited and is quite effective for the staffs of this company. However,
often a significant issue arises when this email server is unavailable for the employees and
thus these employees face several issues due to this unavailability. For the purpose of
improving this availability of the email server in Telstra organization, two approaches could
be helpful. These two approaches are listed below:
a) Implementation of the Sender Policy Framework or SPF: The first important
approach for improving the availability of the email server in Telstra organization is by
simply implementing the SPF or the sender policy framework (Gallagher & Sixsmith, 2014).
The specific SIDF or the sender identity framework is subsequently present within this sender
policy framework to maintain the authorization and authenticity of their email server. Hence,
the previously existing issue of unavailability of the email server in Telstra is easily being
resolved.
8
IS SECURITY AND RISK MANAGEMENT
Figure 3: Implementation of the Sender Policy Framework
(Source: Kadam & Onkar, 2015)
ii) Security of the Applications: The next important or vital approach for the
improvement of the availability of the email server is by the security of the various
applications. The various malware and threats are easily secured with the help of this
particular approach.
Figure 4: Securing the Applications
(Source: Power, Sharda & Burstein, 2015)
IS SECURITY AND RISK MANAGEMENT
Figure 3: Implementation of the Sender Policy Framework
(Source: Kadam & Onkar, 2015)
ii) Security of the Applications: The next important or vital approach for the
improvement of the availability of the email server is by the security of the various
applications. The various malware and threats are easily secured with the help of this
particular approach.
Figure 4: Securing the Applications
(Source: Power, Sharda & Burstein, 2015)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IS SECURITY AND RISK MANAGEMENT
The above mentioned two approaches are extremely popular and significant to
remove the issue of unavailability of email server in Telstra Corporation Ltd.
7. Impact of Employees on Information Security and Risk Management
The employees of Telstra have major impacts in information security. They get the
idea of securing the data or information easily and promptly (Arvidsson, Holmström &
Lyytinen, 2014). Moreover, the services that they are providing are extremely safe and
secured and hence the risk of data loss or identity theft is avoided properly.
The recommendation for managing the risks for reducing the risks of employees or
internal threats in Telstra is that they should implement access controls within their
information systems.
8. Illustration of Log Records for Monitoring or Analyzing Web Server and Email
Issues
The log records within this organization of Telstra are eventually used to monitor or
even analyze the respective email servers as well as the web server. Each and every type of
log record within this company majorly involves the proper security, access and finally event
(Tarhini, Arachchilage & Abbasi, 2015). This type of log record is extremely important for
collecting the history of actions or transactions for resolving any type of problem or issue
within the organizational business. The hardware or the software failures are easily and
promptly eradicated with the help of these log records. These log records are present in all
organizations and in all businesses. These log records even list the various changes in the
database and a stabilized storage format is being maintained. Since, the organization of
Telstra Corporation Ltd helps to provide telecommunications services to the clients, the web
server as well as the email server is to be made secured eventually for avoiding the various
issues related to the previous data (Brooks, 2016). The security, access and event of this
IS SECURITY AND RISK MANAGEMENT
The above mentioned two approaches are extremely popular and significant to
remove the issue of unavailability of email server in Telstra Corporation Ltd.
7. Impact of Employees on Information Security and Risk Management
The employees of Telstra have major impacts in information security. They get the
idea of securing the data or information easily and promptly (Arvidsson, Holmström &
Lyytinen, 2014). Moreover, the services that they are providing are extremely safe and
secured and hence the risk of data loss or identity theft is avoided properly.
The recommendation for managing the risks for reducing the risks of employees or
internal threats in Telstra is that they should implement access controls within their
information systems.
8. Illustration of Log Records for Monitoring or Analyzing Web Server and Email
Issues
The log records within this organization of Telstra are eventually used to monitor or
even analyze the respective email servers as well as the web server. Each and every type of
log record within this company majorly involves the proper security, access and finally event
(Tarhini, Arachchilage & Abbasi, 2015). This type of log record is extremely important for
collecting the history of actions or transactions for resolving any type of problem or issue
within the organizational business. The hardware or the software failures are easily and
promptly eradicated with the help of these log records. These log records are present in all
organizations and in all businesses. These log records even list the various changes in the
database and a stabilized storage format is being maintained. Since, the organization of
Telstra Corporation Ltd helps to provide telecommunications services to the clients, the web
server as well as the email server is to be made secured eventually for avoiding the various
issues related to the previous data (Brooks, 2016). The security, access and event of this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IS SECURITY AND RISK MANAGEMENT
particular organization are required to be kept safe and secured for maintaining the proper
balance within the company. There are some of the major functions of these log records for
Telstra Corporation Limited and these functions are as follows:
i) CreateLogFile: This particular function helps to create new log files of Telstra
organization.
ii) DeleteLogFile: This particular function of log record helps the organization to
delete the various unnecessary log files.
iii) AlignReservedLog: This particular function of log record is helpful for aligning
the reserved log records within the organization of Telstra Corporation Limited (Laudon &
Laudon, 2016).
iv) AllocReservedLog: This specific functionality of log record of Telstra Corporation
Limited helps to allocate the reserved logs subsequently.
The accessing, event as well as security is properly utilized for the purpose of helping
for monitoring and analyzed the several problems regarding the email servers and web
servers within Telstra Corporation Ltd organization.
9. Audit Log Reports useful for Audit Analysis and Log Term Problems
The various kinds of the audit log records could be utilized by the organization of
Telstra with the significant purpose to obtain a better performance by properly analyzing the
audit and hence a proper support to various internal investigations within the organization or
the issues related to log term are completed efficiently (Holtshouse, 2013). The respective
operational trends are eventually intended with this particular phenomenon. The various
problems related to the email server as well as the web servers are easily and promptly
resolved by the specific audit log record. The various systems as well as the account of the
IS SECURITY AND RISK MANAGEMENT
particular organization are required to be kept safe and secured for maintaining the proper
balance within the company. There are some of the major functions of these log records for
Telstra Corporation Limited and these functions are as follows:
i) CreateLogFile: This particular function helps to create new log files of Telstra
organization.
ii) DeleteLogFile: This particular function of log record helps the organization to
delete the various unnecessary log files.
iii) AlignReservedLog: This particular function of log record is helpful for aligning
the reserved log records within the organization of Telstra Corporation Limited (Laudon &
Laudon, 2016).
iv) AllocReservedLog: This specific functionality of log record of Telstra Corporation
Limited helps to allocate the reserved logs subsequently.
The accessing, event as well as security is properly utilized for the purpose of helping
for monitoring and analyzed the several problems regarding the email servers and web
servers within Telstra Corporation Ltd organization.
9. Audit Log Reports useful for Audit Analysis and Log Term Problems
The various kinds of the audit log records could be utilized by the organization of
Telstra with the significant purpose to obtain a better performance by properly analyzing the
audit and hence a proper support to various internal investigations within the organization or
the issues related to log term are completed efficiently (Holtshouse, 2013). The respective
operational trends are eventually intended with this particular phenomenon. The various
problems related to the email server as well as the web servers are easily and promptly
resolved by the specific audit log record. The various systems as well as the account of the

11
IS SECURITY AND RISK MANAGEMENT
various staffs of this particular organization of Telstra Corporation Ltd could be maintained
properly and thus the various organizational transactions could be tracked easily.
10. Five Types of Network Security Devices for Controlling and Mitigating Threats
The network security can be stated as the major activity that is being designed for the
protection of the integrity as well as usability of both network and data. This type of security
also involves technologies of hardware and software (Schwalbe, 2015). The effective and
efficient network security controls the network access and it also targets the variety of risks
and then stops these risks from spreading or entering within the network. Several defence
layers are combined together to form this network security and hence the users could easily
obtain proper access to network resources and carrying out threats and exploitations.
Several devices of network security are present that could be helpful for providing
better efficiency to control the privacy or security within the business operations of Telstra
Corporation Ltd (Oztaysi, 2014). The five major devices of this network security are given
below:
i) Bridges: The first and the most important network security device is bridge. The
typical router helps to link two types of network and then the specified bridge is being
utilized to connect the two sub networks. Thus, this network security is easily and promptly
controlled by the help of network security device, bridge.
ii) Modems: The second important device for securing the network of Telstra
Corporation Limited is a modem (Marchewka, 2014). It is the proper combination of a
modulator and a demodulator. The significant signal within the network of the company is
either modulated or is demodulated with the help of this particular network security device of
modem.
IS SECURITY AND RISK MANAGEMENT
various staffs of this particular organization of Telstra Corporation Ltd could be maintained
properly and thus the various organizational transactions could be tracked easily.
10. Five Types of Network Security Devices for Controlling and Mitigating Threats
The network security can be stated as the major activity that is being designed for the
protection of the integrity as well as usability of both network and data. This type of security
also involves technologies of hardware and software (Schwalbe, 2015). The effective and
efficient network security controls the network access and it also targets the variety of risks
and then stops these risks from spreading or entering within the network. Several defence
layers are combined together to form this network security and hence the users could easily
obtain proper access to network resources and carrying out threats and exploitations.
Several devices of network security are present that could be helpful for providing
better efficiency to control the privacy or security within the business operations of Telstra
Corporation Ltd (Oztaysi, 2014). The five major devices of this network security are given
below:
i) Bridges: The first and the most important network security device is bridge. The
typical router helps to link two types of network and then the specified bridge is being
utilized to connect the two sub networks. Thus, this network security is easily and promptly
controlled by the help of network security device, bridge.
ii) Modems: The second important device for securing the network of Telstra
Corporation Limited is a modem (Marchewka, 2014). It is the proper combination of a
modulator and a demodulator. The significant signal within the network of the company is
either modulated or is demodulated with the help of this particular network security device of
modem.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



